Into the Darknet: What is MTV?
This week we relaunch our “Into the Darknet” blog series that will not only provide a better understanding of the darknet’s history, users, uses and purpose, but will also take an in-depth look at other hot topics in DARKINT, cybersecurity, including malware, toolkits, viruses, cryptocurrency, marketplaces and OPSEC.
In this post, we take a high-level look at malware, toolkits and viruses (MTV), as they are some of the most commonly discussed, released and exchanged tools on the darknet.
Our analysts have adopted the term “MTV” to refer generally to a collection of malware, toolkits and viruses that are used to test, penetrate, exploit or compromise personal or commercial information systems and data. Common systems where MTV could be employed include desktop computers, laptops, servers, network devices, routers, firewalls, printers, WiFi adapters, tablets and smartphones.
WHAT IS MTV?
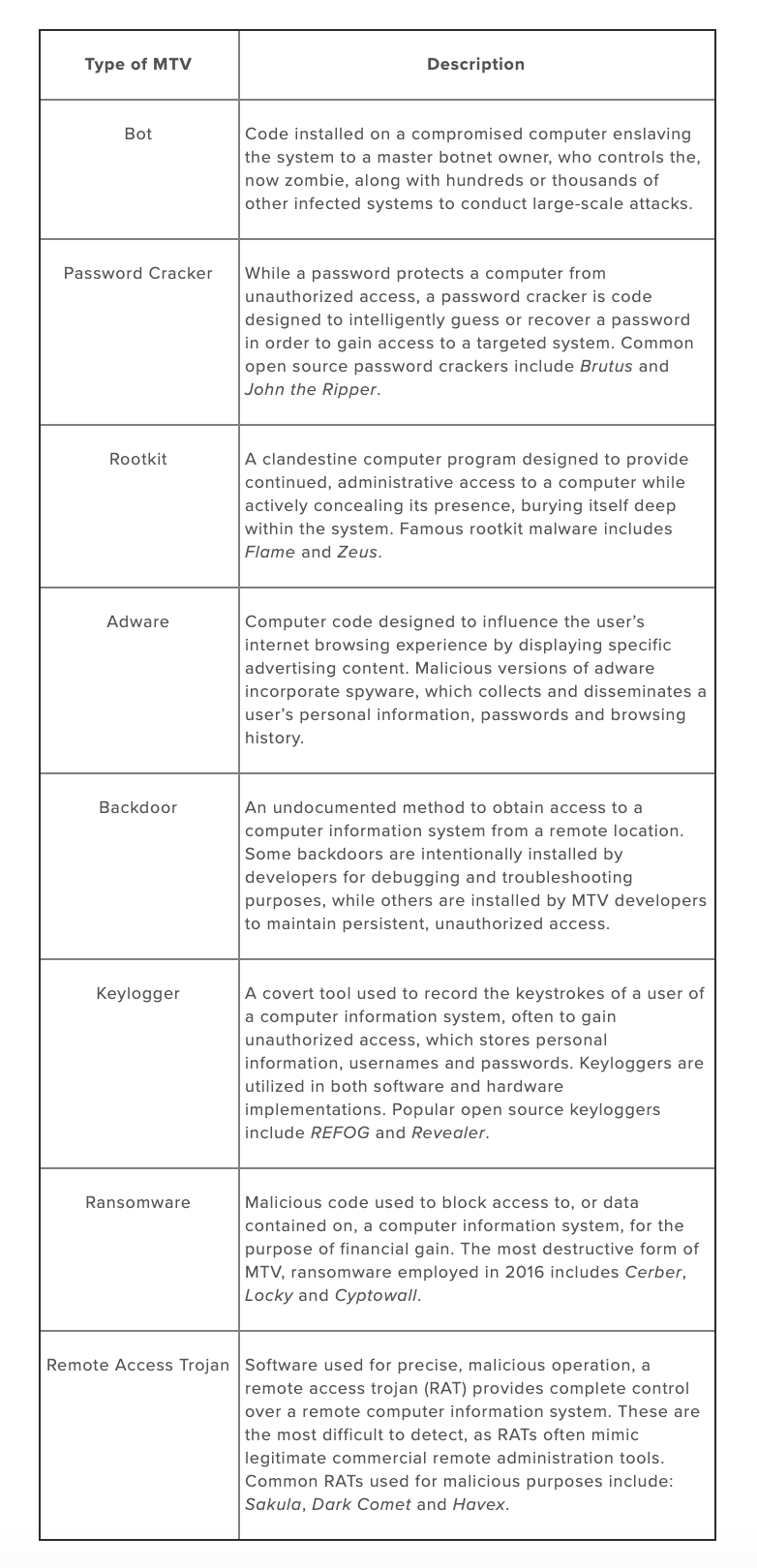
MTV is, and includes, any type of software code used either for good (information assurance) or bad (malicious) purposes, such as: Bots, Password Crackers, Rootkits, Adware, Backdoor Access, Keyloggers, Ransomware and Remote Access Trojans.
The average hacker will have some or all of these handy in his or her arsenal of tools to use against targeted information systems and will often utilize a variety of MTV in a full-fledged attack, depending on the intent of the operation.
Both penetration testing and risk analysis activities, like those conducted by the DarkOwl Cybersecurity teams, utilize these MTV tools for preventative purposes, to detect security holes which could lead to a compromised network. For example, THC Hydra (an open-source password cracking tool) can be used to test the strength of users’ passwords on private or commercial networks.
Malicious hackers, cyber spies and cyber criminals, however, can easily use this same code to exploit user accounts with weak credentials.
A brief History of MTV
The first example of malware debuted in the early 1980’s as a software video game piggyback, displaying the now-infamous Elk Cloner poem and corrupting the Apple boot sector.
“It will get on all your disks
It will infiltrate your chips
Yes it’s Cloner!It will stick to you like glue
It will modify ram tooSend in the Cloner!”
In the late 1990’s and early 2000’s, both the MTV market and the hacker community exploded with the propagation of the internet, aggressive social engineering tactics and the exploitation of spam emails for malware distribution.
By the mid-to-late 2000’s, malware like Conficker and Sinowal demonstrated how aggressively a virus can spread, and remote command and control, enabled via clandestine communication and package concealment was born.
As antivirus companies grew to counter these emerging threats, the hacker community accepted the challenge and created even more sophisticated and difficult to detect MTV.
Accessing valuable protected information
As society has become more dependent on online activity, our digital footprints, or online presences, have expanded. A lucrative market for the trade in this information existing on the darknet, with high value placed on personally identifiable information (PII), among other bits of data.
Malicious hackers and cyber criminals require a variety of MTV tools, such as network discovery tools, password crackers and backdoor access programs, in order to gain unauthorized access to key systems containing this valuable data.
These attackers establish a persistent presence via advanced persistent threats (APT) and remote access tools (RAT) to evade detection – and mitigate any IT security measures in place there to stop them.
Once connections are established and secured, hackers launch automated data mining programs to harvest valuable information, like PII, and send it to a remote server for final dissemination or leverage.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases













