Not so Anonymous: Critical Vulnerabilities in Darknet Tools Could Expose Its Users
In recent weeks, analysts at DarkOwl have witnessed a number of vulnerability issues in key utilities used for dark web (i.e. deep web and darknet anonymous network) intelligence collection and analysis. Last week, analysts found the official Chrome extension for MEGA.nz’s file sharing service was harvesting sensitive user data; while Tor Project’s latest browser release based on Firefox Quantum, was deployed with default settings that could potentially compromise users’ identities.
On which side is the Tor Project?
The Tor Project is a non-profit organization that prides itself on providing users free software and an open network for securely browsing the Internet. Tor’s Browser, developed collaboratively with Mozilla, allows users with any operating system (OS) to freely visit clearnet, deep web, and darknet anonymous websites or sites that might be blocked in countries with Internet censorship. With little to no configuration changes nor detailed understanding of networking protocols, Tor Browser prevents somebody watching your Internet connection from learning what sites its users visit and thwarts the sites its users visited from discerning one’s physical location through location identifiable information such as IP and/or MAC Addresses.
Digital Fingerprints
One historical security feature of Tor Browser has been user agent obfuscation. Every browser sends its user agent (UA) to every website it visits. The UA is a string of text that identifies the browser and the operating system to the web server, or host of the website visited. There are millions of different UA combinations given how they change with both software and hardware. The web server uses this information for a variety of purposes. In the Surface Web, website creators use the UA to help optimally display the website to different browsers for the “best possible browsing experience.” Knowing the UA also assists when a web server hosts both desktop and mobile versions of a site, e.g. serving up content adjusted for the screen size of the device.
Example User Agents
For more example user agents check out this site.
The default Tor Browser user agent has historically included a mixture of Mozilla and Windows OS UA’s with the following string: Mozilla/5.0 (Windows NT 6.1; rv:52.0) Gecko/20100101 Firefox/52.0. The revision “rv:52.0” and “/52.0” strings correlate to the version of Tor browser installed. 52.0 corresponded Tor Browser 7.0a4. In the recent 5 September release of Tor Browser 8.0/8.5a1, the user’s actual OS is exposed in the UA.
Exposing this information presents risk to Tor users. Darknet web servers could maliciously use this information to identify anonymous users or link users based on speech and UA across multiple forums and chatrooms. While including the user’s OS in the UA does not reveal one’s physical location, in a world where anonymity is irreplaceable, this issue could prove disastrous.
In order to update or change the UA in Tor Browser, the following steps are required:
-
Enter about:config in the URL bar and accept the risks
-
Search for: general.useragent.override, right click on the user agent, and select Reset.
If you want to replace the UA with another unique or custom text string, right click on the user agent and choose “Modify.” The pop-up that displays is editable. Enter whatever string you wish, then click OK.
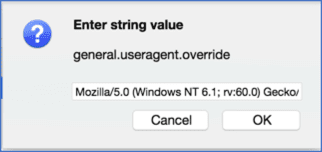
Figure 1 Tor Browser about:config useragent override popup
Tor users who want to delay their upgrade to 8.0/8.5a1, might want to reconsider as Zerodium released yesterday on Twitter details around a NoScript “bug” discovered in all Tor Browser 7.x versions that subjects the user to embedded code on the hidden service regardless of whether or not NoScript was “actively blocking all scripts.” (Source)
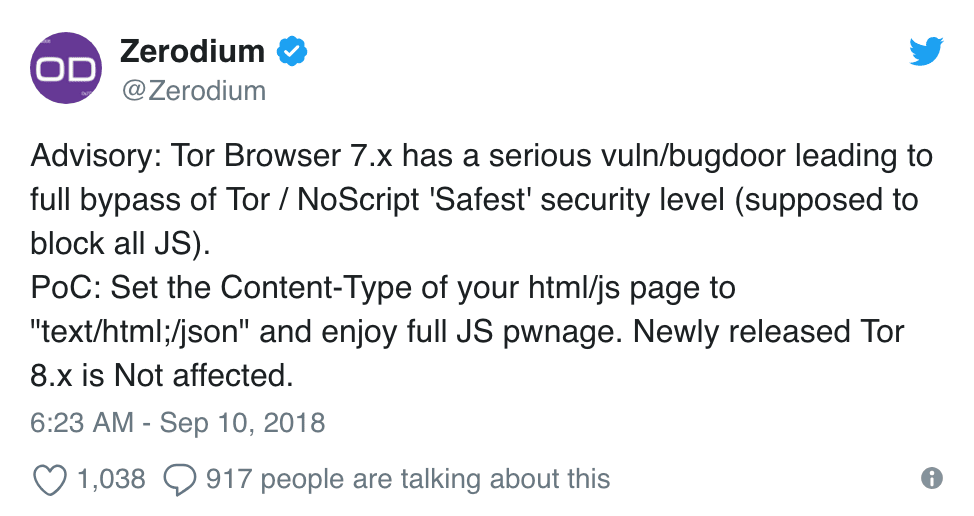
Figure 2 Zerodium Tweet posted on 10 September 2018 (Source)
Javascript = Yes? Or No?
Another issue DarkOwl analysts found with the latest Tor Browser release is the default configuration settings for Javascript. Tor users are mixed between browsing with or without Javascript enabled. As Tor becomes more inclusive of media and dynamic content, more and more Tor websites include embedded Javascript code. If Javascript is disabled, then the web sites may appear to be broken, missing content, prevent authentication, and frustrate the most patient of Tor users. However, the community should also recognize that Javascript is a vulnerable vector that is leveraged by blackhat attackers. In 2014, law enforcement utilized injected Javascript code to infect everyone who visited any Tor server hosted by “Freedom Networking” with malware that exposed their real IP address. (Source)
In Paolo Mioni’s article entitled “Anatomy of a malicious script: how a website can take over your browser” the author gutted what seemed like an innocuous embedded piece of Javascript to outline how the elementary script was configured to redirect the user to a specific URL and could be simply adapted to arbitrarily inject other malicious scripts such keyloggers and cryptominers. (Source)
Coinhive, tagged as one of the largest threats to web users in the Spring of 2018, is an online crypto-service which provides cryptocurrency miners crypto mining malware, that can be installed on websites via embedded Javascript. The JavaScript miner runs in the browser of the website visitors and mines coins on the Monero blockchain. Unfortunately, the Coinhive code has been exploited by hackers for use as malware to hijack the end customer’s personal data and processor resources. This summer, independent security researcher, Scott Helme identified more than 4,000 websites, including many belonging to the UK government, infected with Coinhive malware.
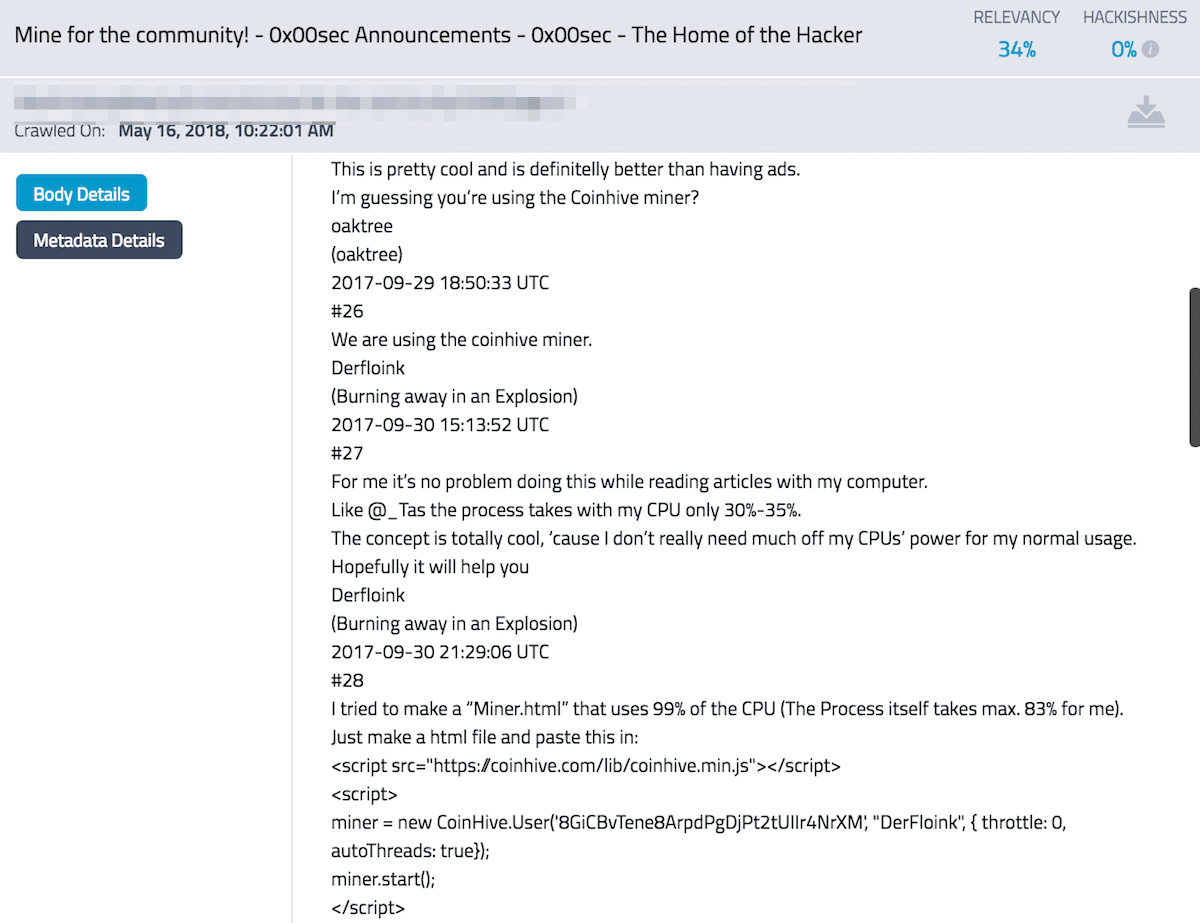
Figure 3 Darknet Forum where Coinhive Exploit use is Discussed (633c61aaa0289fa0572b15b163f11b04)
Not MEGA.nz too…
MEGA.nz is a controversial but free cloud storage service, similar to Dropbox, that is a popular resource for blackhat and whitehat hackers. Over the last few years, data from many of the major commercial data breaches has been reliably posted to the MEGA.nz storage site and links shared across darknet forums. Despite previous concerns regarding the security of using the website, it proved a fruitful resource for personally identifiable information (PII) and credential data collection. Last week, DarkOwl analysts discovered a compromised version of the official Google Chrome extension for MEGA.nz, version 3.39.4, was published with malicious codes to harvest user credentials and private keys for cryptocurrency accounts. ZDNet broke the news of the hacked extension indicating that for the four hours after it was uploaded to Google’s Chrome Web Store, the extension sent users’ stolen data to a server located at megaopac[.]host, hosted in Ukraine. (Source)
Unsurprisingly, MEGA.nz has expressed significant dissatisfaction with Google over this security breach blaming Google’s recent policy to disallow publisher signatures on Chrome extensions. An updated version of the extension, v3.39.5 is now available on the Chrome Web Store.
While the Firefox version of the MEGA plugin was not compromised, Mozilla recently removed 23 Firefox Add-ons that illegally tracked user’s browser data. In August, Mozilla released a list of compromised add-ons which included one called “Web Security,” a security-centric Firefox extension with over 220,000 users, that was caught sending users’ browsing histories to a server located in Germany.
DarkOwl Vision recently archived a May-2018 post from Junior Member on a popular darknet forum offering custom Chrome malware. The self-promoted malware developer advertised a trojanized YouTube Video Downloader in their post, but emphasized their ability to develop custom malware, supporting the possibility that even more compromised Chrome extensions like MEGA.nz could be published in the future.
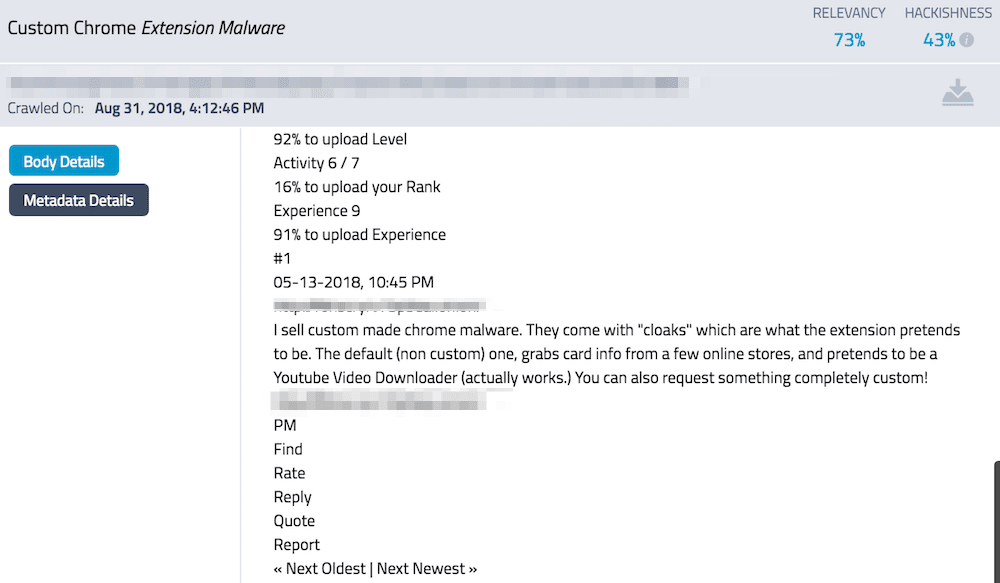
Figure 4 Darknet Forum Post about Custom Chrome Extension Malware (c726797ae6dcd1ac889aff630d2855eb)
Anonymity Impossible
The unfortunate and harsh reality in the world of the deep web and darknet anonymous networks is that anyone on these networks whether they be privacy conscious individuals, journalists, whitehat or blackhat hackers, must remain vigilant and hyper-aware that the tools and resources that advertise anonymity and security may be secretly exposing critical information of its users. Virtual Private Networks (VPNs) and Virtual Machines along with persistent endpoint protection may be the new norm for individuals who navigate potentially dangerous networks and sites; whereas DarkOwl Vision provides secure access to over 650 Million darknet and deep web pages to those who want to avoid the risk all together.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases













