All Your Passwords Belong to Us
May 05, 2022
In honor of World Password Day – a date established in 2013 by Intel Corporation to foster security awareness – the content team at DarkOwl decided to compile some interesting statistics based on the email and password entities available in the DarkOwl Entity API.
DarkOwl’s Entity Volume
Every day we hear of another commercial data or app breach. At this point, everyone can assume their email address and/or password has been leaked on the darknet or deep web. DarkOwl has collected and tokenized over 8.68 billion (with a “B”) email addresses. 5.46 billion of those emails include a password. 57% of those email addresses include a ‘plaintext’ or legible password.
But My Password is Complex!
If you’re still using your cat’s name followed by the exclamation point (“Fritzie!”), your password is not complex, and you have most likely already experienced an account compromise. But, you’re not alone. Complex, lengthy passwords are not the norm across DarkOwl’s data.
The most common password length is 8 characters.
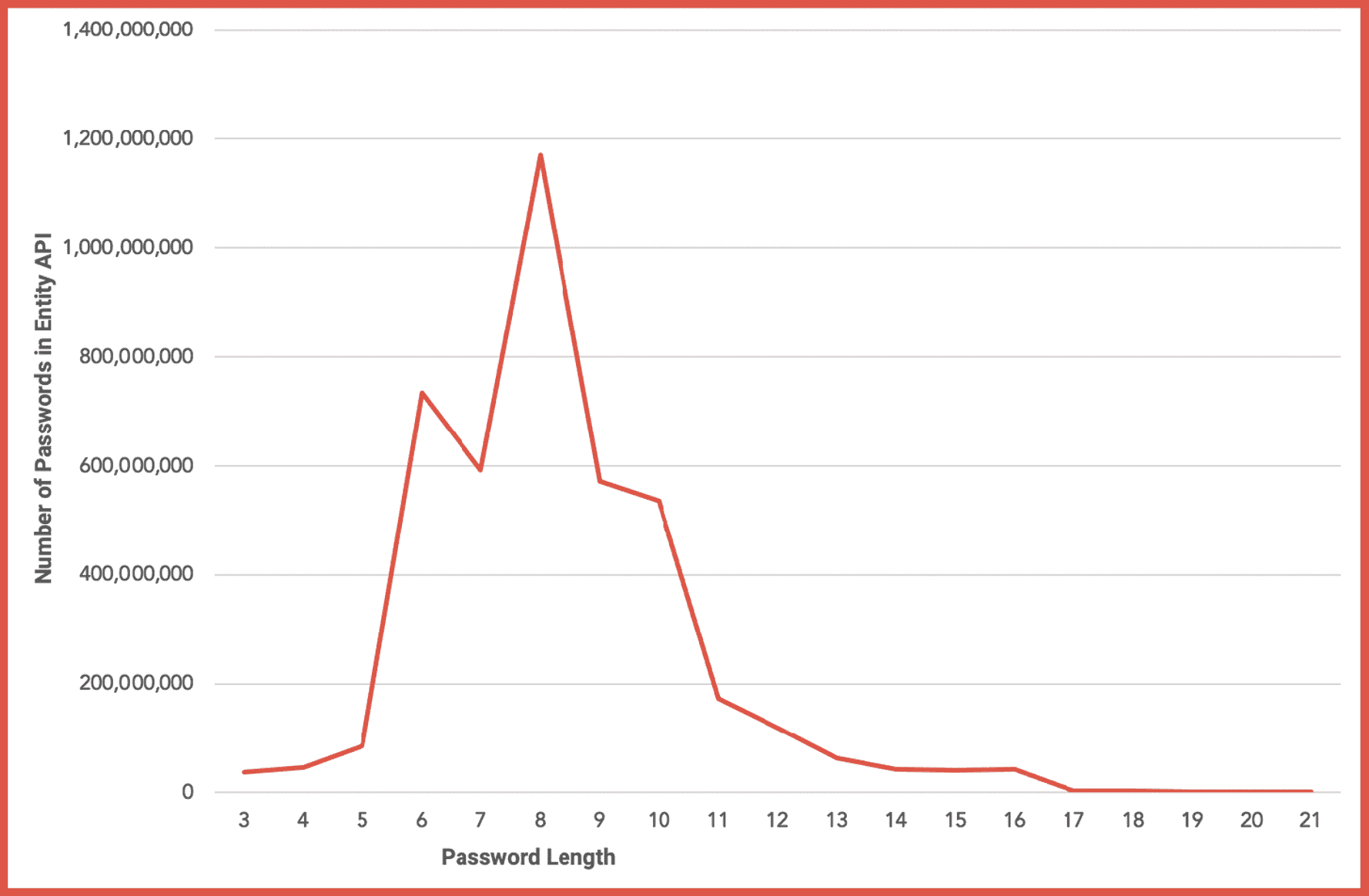
Figure 1: Distribution of Password Volume by Password Character Length
Is an 8-character length password strong enough?
The strength of an 8-character password depends on the motivation and the tools available to the cybercriminal targeting your account. There are plenty of password ‘cracking’ tools readily available to hackers to conducting dictionary and brute force style password attacks. Some of the most popular tools include:
- John the Ripper
- Cain & Abel
- OphCrack
- THC Hydra
- Hashcat
- Brutus
- RainbowCrack
- CrackStation
Even the most sophisticated password crackers will need significant processing power and time to successfully break long, complex passwords. Unless an 8-character password includes numbers and symbols, the password can be potentially brute forced.
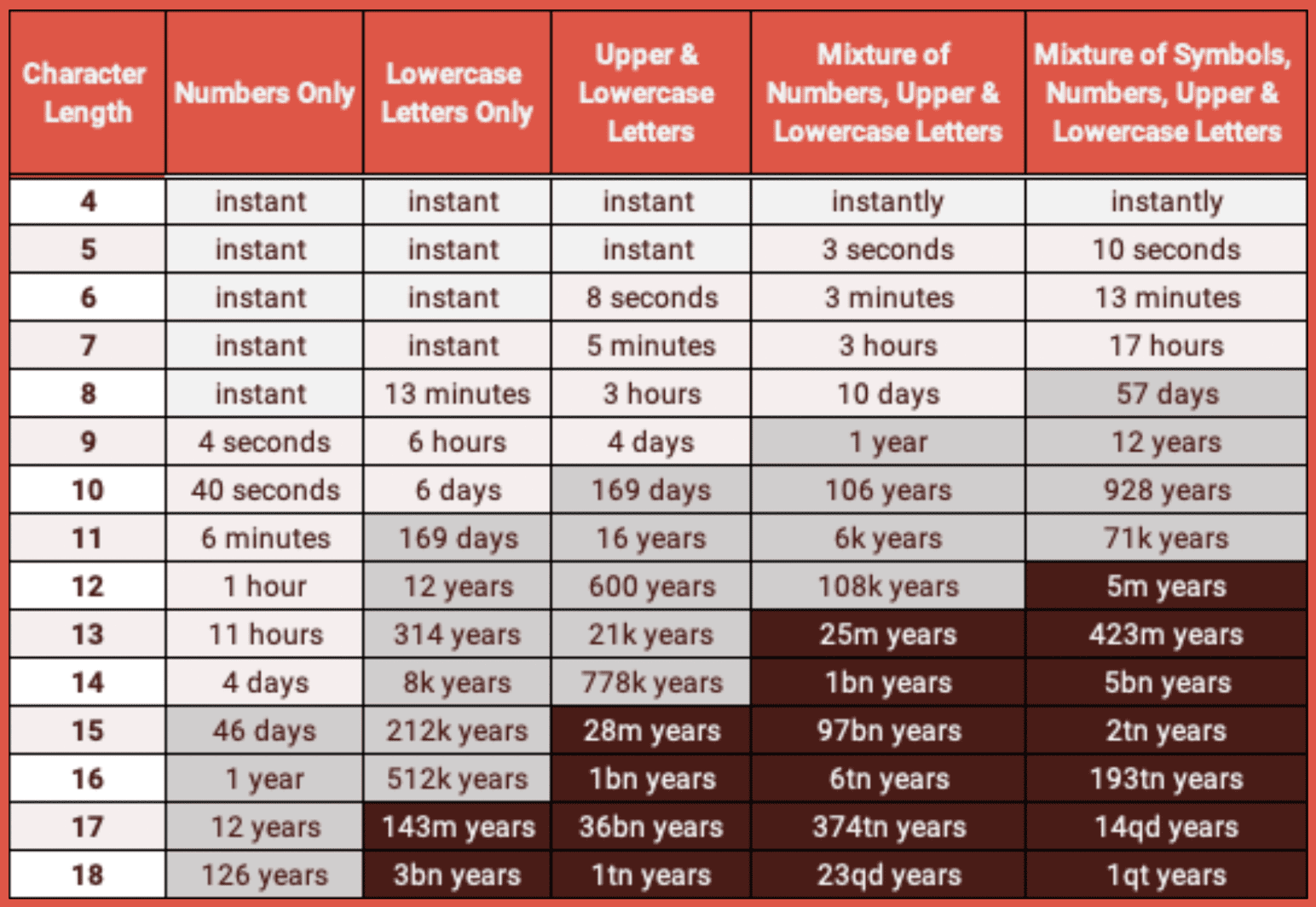
Figure 2: Time to Crack Passwords of Varying Degrees of Character Length and Complexity
Over 4 billion of the passwords (4,285,451,030) available in DarkOwl’s Entity API are 32 characters or less. 662,341,057 passwords could be classified as extreme and greater than 32 characters in length.
Figure 2 demonstrates that passwords including numbers and symbols are harder to crack than letters alone. DarkOwl’s data contains a significant volume of passwords with some degree of complexity but only 637 million plaintext passwords would be classified as “strong.”

Strong passwords defined as containing special characters, digits, lowercase, uppercase, and length greater than 8 characters.
Passwords That Age Us
Do you have a favorite year that you include in your password for uniqueness? Perhaps it’s your birthday year or anniversary. Both are very common. We found over 707 million passwords include a year string that starts with “19XX” or “20YY.”
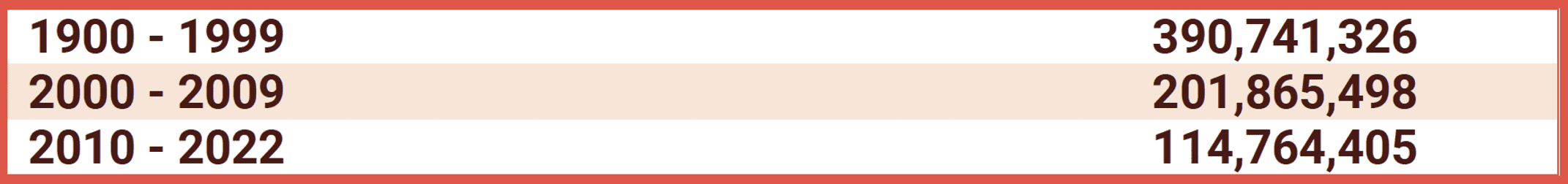
According to our data distribution, peak volumes of passwords include the data range of 1980 to 1994. The most frequent years we observed were:
1990: 14,006,141
1987: 13,795,566
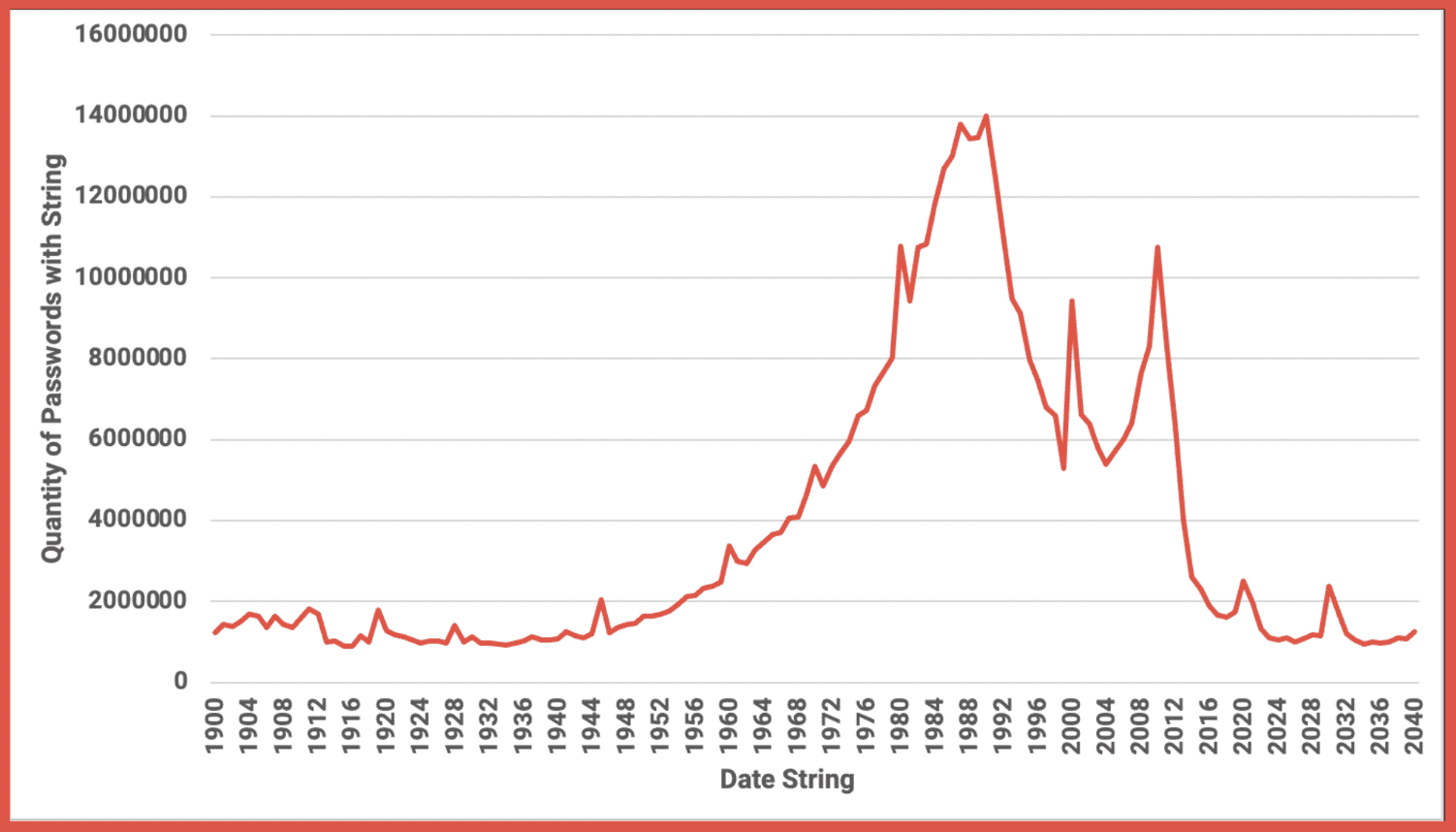
Figure 3: Distribution of Passwords Containing a Date (Year) String
QWERTY is Simply Lazy
The “QWERTY” keyboard layout originated in the late 1860s and was designed to help people type and translate Morse code faster. Regardless of its origins, people heavily rely on the top row of the American keyboard characters in many password fields; 5,793,906 passwords in DarkOwl Entities API contains the6-character string “qwerty.”
Even worse is sequential numbers with 29,010,394 consisting of “123456” and 11,718,471 going to the trouble to add the whole number set, “123456789.”
DarkOwl has collected 5,857,363 passwords using the laziest password of all: the word, “password.”
Hashed Passwords > Plaintext
Billions of leaked plaintext passwords are tragic, no matter the complexity, character length, or whether a date string or qwerty is included. Therefore, if you suspect a plaintext password you use or have used in a commercial webservice has been compromised, change it immediately and cease using it on any authentication logins. Credential stuffing campaigns exploit password reuse and utilize email address and password combinations to attempt logins outside of the source of the original leak.
Given the propensity for commercial data breaches, most authentication and digital identification protection platforms strongly suggest users passwords are stored in a hashed format instead of plaintext to reduce the likelihood of immediate malicious use upon compromise.
6% (518,566,724) of the passwords available in DarkOwl’s Entity API are hashed passwords.
In cryptography, hashing involves using a mathematical algorithm to map data of any size into a bit string of a fixed size. In password hashing, a ‘hash’ consists of a unique digital fingerprint (of a fixed size) corresponding to the original plaintext password which cannot be reversed. There are several different types of ‘hashing algorithms’ available for encrypting passwords.
The most common hash in DarkOwl’s data is MD5 followed by SHA-1.
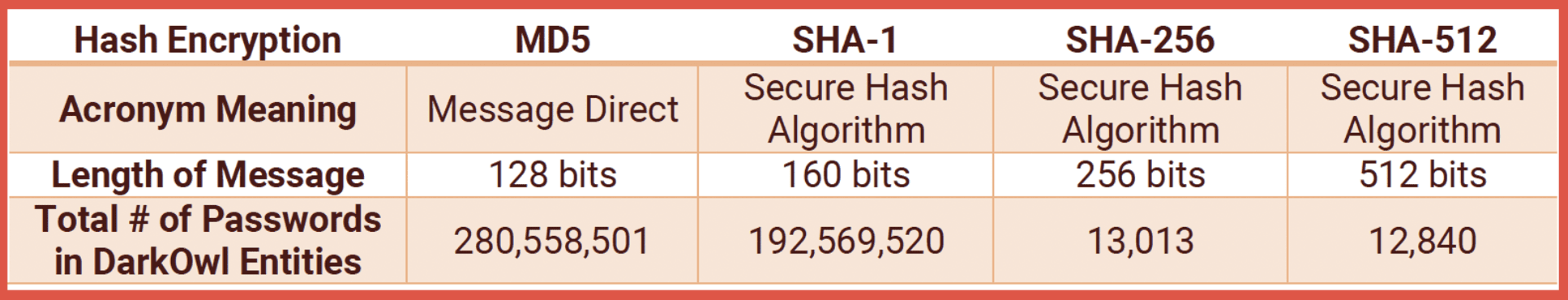
Some MD5 hashes in phpBB and WordPress appear as 34 characters instead of 32. DarkOwl has 345,431 hashed passwords consisting of 34 characters.
Both MD5 and SHA-1 have been deemed vulnerable as they are subject to collision attacks and dehashing. One of the most popular password hacking programs to date, Hashcat, contains lookup tables for popular wordlists, like RockYou allowing for the original plaintext password to be deciphered.
Password Strengthening Tips
Although you can’t prevent commercial services getting breached and usernames, email addresses, and password combinations getting leaked, you can follow some simple steps to ensure you employ robust password hygiene and reduce the risk of a password getting brute forced or exploited in a credential stuffing campaign.
- Use an automated complex password Manager like Lastpass, BitWarden, or 1Password.
- Don’t reuse passwords. Have unique password for every login and streaming service you sign up for.
- Choose passwords at least 16 characters in length.
- Include symbols and numbers for increased complexity.
- Avoid using passwords with dictionary words or names.
- Don’t use sequential numbers or the word “password”
- Don’t use the year of your birth or anniversary in your password.
- Turn on multi-factor authentication (MFA) for important accounts like financial and banking sites.
Celebrating World Password Day
Today’s World Password Day is a perfect time to pause and review the security – or lack thereof – of your most common password habits. After reading this blog, we invite to you to consider taking the following actions today:
- Review passwords stored in your keychain, password managers, or sticky notes.
- Change any passwords you might be reusing across multiple sites.
- Share password tips on social media with friends and family.
- (#WorldPasswordDay)
- Transform a weak password into a strong one using the password strengthening tips above.
- Turn on MFA for all important accounts.
Curious about something you read? Interested in learning more? Contact us to find out how darknet data applies to your use case.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















