Analysis of E-mail Domain Preferences by Ransomware Operators
To learn more about the technology habits of ransomware operators, DarkOwl analysts conducted a brief survey of content issued by RaaS groups over the last few years and collated mentions of any email domains they provided for victims to initiate contact with them. The data we analyzed included ransomware notes harvested from multiple darknet sources from 2016 through the first two quarters of 2021.
The chart below depicts the results of our findings, and demonstrates which email services were and/or are popular amongst ransomware gangs over the past several years.
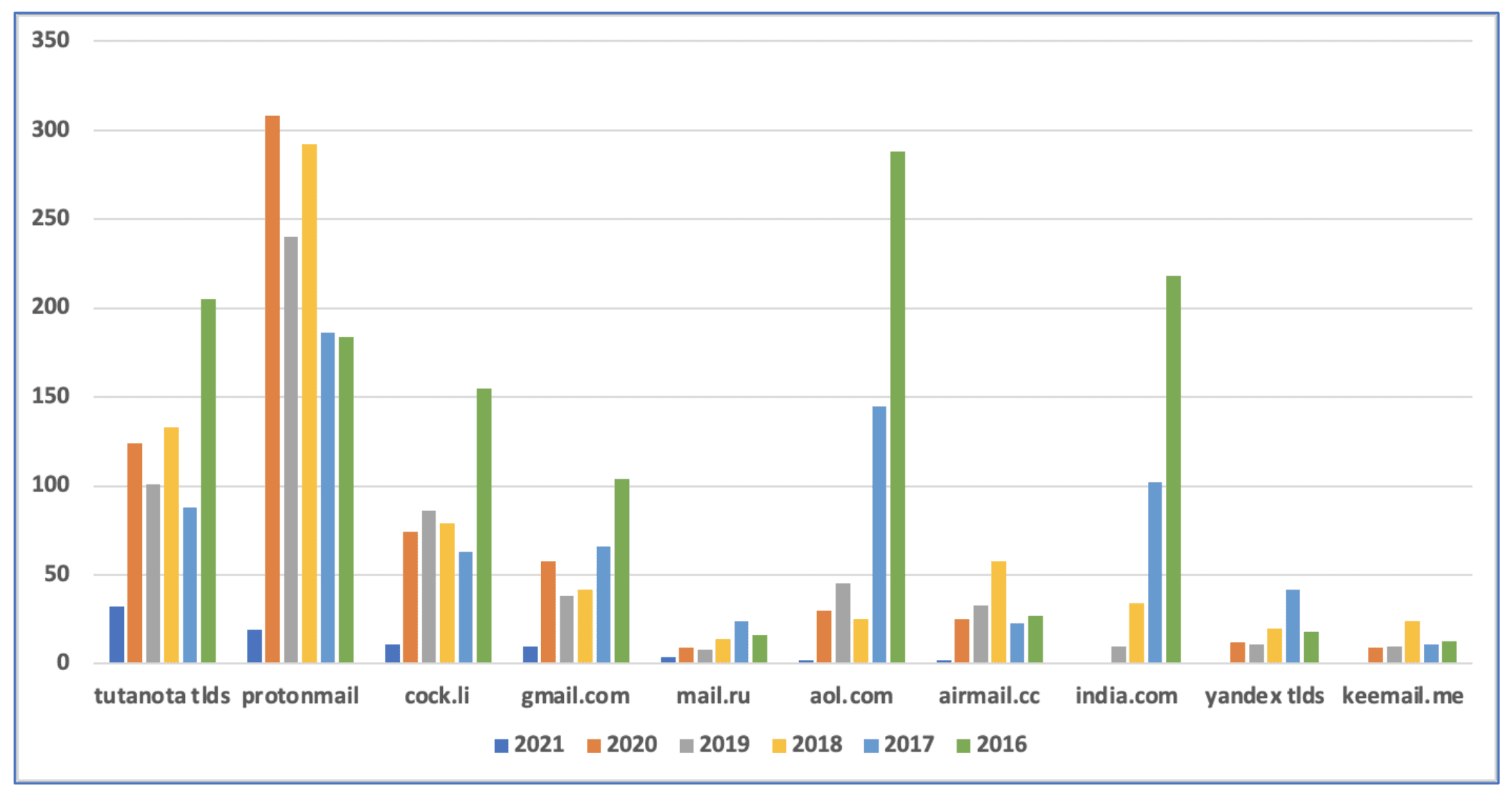
Distribution of E-mail Domain Preferences by Ransomware Group by Calendar Year
Quick Takeaways
-
Since 2019, ransomware criminal gangs prefer the Swiss-based Protonmail and German-based Tutanota encrypted e-mail services over other e-mail service providers. The data included in this analysis summed the domains mentioned across all service provider TLDs, e.g. .ch, .io, .pm, etc.
-
E-mail service providers AOL and India.com were most popular in 2016 and 2017 but use of these providers have dropped off considerably in recent years.
-
Google’s Gmail has experienced moderate, alibeit consistent use by many ransomware criminal groups.
Tutonata emerges as most popular email service in 2021 thus far
For the first half of 2021, Tutonata appears to be leading Protonmail in total email accounts mentioned across notes published in the first two Quarters of 2021. Both email services have been the subject of controversy over recent years, including last December when open source reporting indicated that the German government had been forcing Tutanota to setup backdoors, enabling law enforcement to monitor and read e-mails in plain text.
While the reason for the decline in Protonmail’s popularity can not be stated definitively, the fact that the service has been the subject of debate is likely a contributing factor. In 2019, some users across the darknet and Reddit began spreading rumors that ProtonMail was likely a law enforcement honeypot – citing how its Tor service redirects back to the surface web upon account creation. Theories that developers at MIT with oversight from the NSA, CIA, and DARPA assisted CERN with Protonmail’s source code and encryption development. Further arguments included how Protonmail stores email data and metadata in formats similar to those that Edward Snowden had stated the CIA requires. (Source)
This debate is heated and greatly divided with many stating the Privacy WatchDog Blog detailing how Protonmail is a honeypot is anti-Protonmail propaganda website, spreading FUD and baseless conspiracy theories. Additional reports suggest that the CIA for decades has utilized front-companies and technical organizations based in Switzerland to spy on European governments, adding fuel to the paranoia and conspiratorial chatter.
Future Predictions
While the trends for email address domains observed during the first two quarters of 2021 are consistent with preferences in recent years, this data analysis further predicts that the total number of email addresses from ransomware victim notes for 2021 will be likely less than totals observed from previous years.
We predict this due to the volume of ransomware groups utilizing alternative communication methods with their victims. DarkOwl has observed numerous links to Telegram accounts and real-time chats directly hosted Tor darknet onion services to conduct ransom payment negotiations in lieu of traditional e-mail based communications.
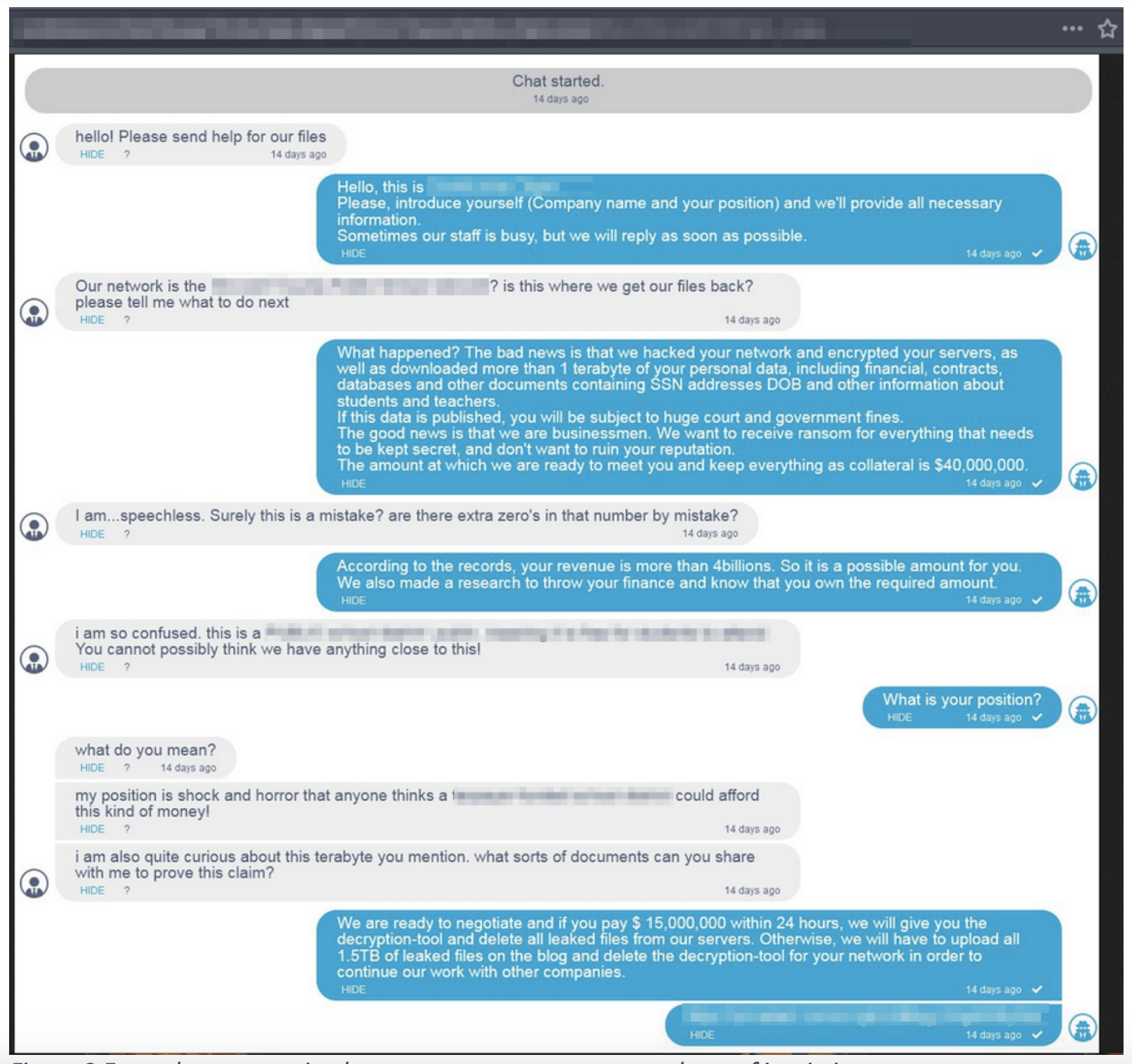
Example conversation between ransomware gang and one of its victims on a chat service
Curious about something you read? Interested in learning more? Contact us to find out how darknet data applies to your use-case
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















