Analysis of Ukrainian Data Released on the Darknet in Lead-up to Russian Invasion
DarkOwl is aware that as of February 23rd, 2022 Ukraine’s digital infrastructure came under further significant DDoS attacks, with several government and financial websites under duress. Hours later Russia launched direct kinetic attacks against strategic targets around the country and ground forces crossed the border on multiple fronts. Ukraine’s critical infrastructure is under direct attack, martial law declared, and civilians are struggling to withdraw funds from ATMs. Our analysts will continue to update with key insights from the darknet as they become available.
Information related to January Ukrainian cyberattacks found on the darknet
In mid-January 2022, open-source and public news media reported that several Ukrainian government networks had been compromised during a series of cyberattacks the night of 13th-14th of January, including deployment of what security researchers have identified as the “WhisperGate” malware. Within hours of the attack, data described as originating from the Ukrainian government appeared on forums across the darknet and deep web.
DarkOwl observed a surge in Ukrainian government related leaked data in January, but has not uncovered conclusive evidence this data was stolen during the cyberattacks days before or merely released immediately after as part of a psychological intimidation campaign against the people of Ukraine.
Additional Ukrainian government and civilian data appeared on a Tor onion service called “Free Civilian,” that DarkOwl assesses to be possibly affiliated with a threat actor using the moniker “Vaticano” on Raid Forums. The user was banned from the well-known deep web forum late January 15th, by moderator Jimmy02, who stated:
“For one reason or another I have determined that this is a bad database, this could mean its a fake or just a shitty sample.”
Given increasing international tensions and the on-going cyberattacks against Ukraine, DarkOwl analysts compiled and reviewed Ukraine-related data on popular deep web forums and Tor hidden services shared in recent weeks. Most of the data “archives” consisted of raw text files, emails, spreadsheets, SQL databases, scanned photographs and PDF files containing various types of personally identifying information (PII).
While many of the leaked archives of data were created within a few hours of the attacks in mid-January, there are no indications they were directly obtained as a result of the attacks.
Mid-January Cyberattacks and Website Defacements
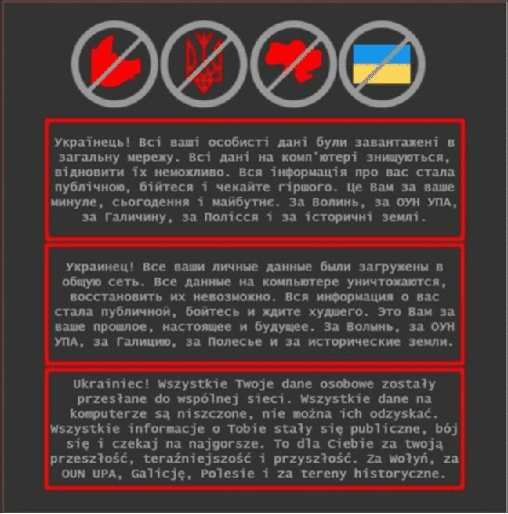
On 13th-14th of January, 2022, multiple Ukrainian government, non-profit, and information technology organizations experienced cyberattacks and public-facing website defacements. The attackers used a ransomware-esque malware attack, rendering many systems inoperable in addition to defacing official government websites across the country loading an ominous message in Ukrainian, Polish, and Russian.
“Ukrainians! All your personal data was uploaded to the internet,” the message read. “All data on the computer is being destroyed. All information about you became public. Be afraid and expect the worst.”
Microsoft’s incident responders indicated the destructive malware campaign was designed to mimic extortion-based ransomware, by deleting critical files, locking down the systems, and loading a ransom note demanding $10,000 USD in Bitcoin. The ransom demand was for show and irrelevant to the attackers’ intentions.
The Security Services of Ukraine (SBU) reported they were investigating the matter closely together with the State Service of Special Communications and the Cyber Police and believed that over 70 organizations across Ukraine had been targeted by “special services of Russia” the night of the attacks on 13/14 January. While 10 organizations were subject to “unauthorized interference” no personal data had been compromised or leaked. (Source)
Cyberattack Methods Analyzed and Possibly Reused
Cybersecurity units at Microsoft, Crowdstrike, and Palo Alto Networks have published expert descriptions of the threat attack vectors deployed on the night of the January 13 cyberattacks against cyber targets across Ukraine. Technical analysis suggests a vulnerability in the OctoberCMS content management system allowed for the website defacements. The attackers also utilized the WhisperGate destructive wiper malware family to lock down the networks in a ransomware-style campaign.
According to Microsoft, WhisperGate involved two stages: the first stage overwrites the master boot record (MBR) with a ransom note; and, the second stage downloads a data-corruption malware named Tbopbh.jpg that overwrites targeted files with a fixed number of 0xCC bytes. Incidentally, the malicious file was downloaded from a Discord server.
By utilizing open source intelligence and DarkOwl Vision, our analysts discovered multiple instances of MBR-style attacks – including an attack against Banco de Chile attack from 2018. WhisperGate also shares strategic similarities with previous PotNetya attacks used against Ukraine back in 2017.
DarkOwl also noticed a cybersecurity researcher (@Petrovic082) using the hashtag #KillMBR on Twitter which they linked to potential malicious executables associated with the malware family. Users active on Chinese bulletin boards have since been closely analyzing the uploaded executables for reuse and virus detection. (Source)
Breaking news indicates Russia deployed a new hard disk wiper malware variant called HermeticWiper (KillDisk.NCV) across strategic cyber targets on the 23rd of February prior to the full-scale military invasion of Ukraine sovereign territory.
Analysis of Leaked Data Found in the Dark Web
On the 14th of January, the now-banned Raid Forums user known as Vaticano posted what appeared to be a user SQL database for the my.diia.gov.ua website. This leak surfaced within hours of the ransomware attack and website defacement on the DIIA server in Ukraine, although the raw user database from DIIA appears to have been created in late December.
Other users on Raid Forums doubted the veracity of the data posted by Vaticano, asking “where is the full data base?” calling it “bullshit and fake advertising,” “not true and old information,” or that the “data is identical to the old leak.”
In response to the criticism, Vaticano shared additional databases from their “archive” described as “medstar.sql” and “somefilesfromnotcatholic.zip” discussed below.
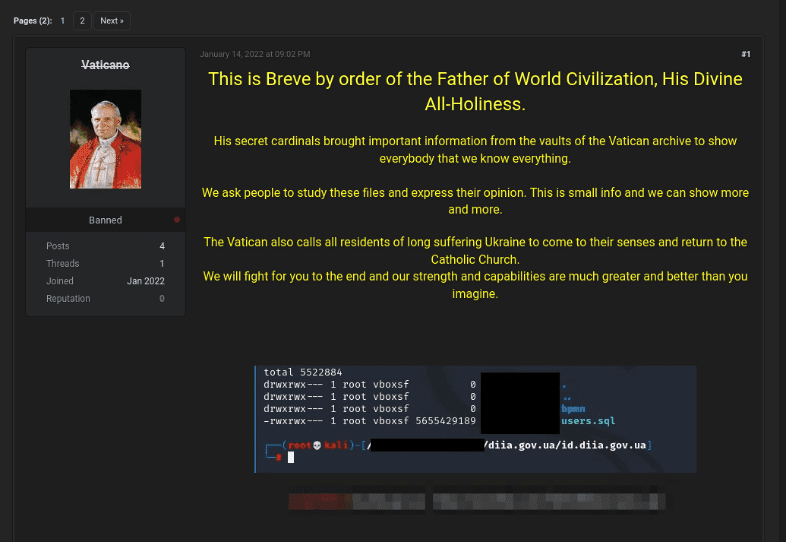
my.diia.gov.ua
According to the leaked data, a DIIA SQL database, users.sql, was generated via a PostgreSQL database dump, and dated 24 December 2021, 12:17:17 EST. A table, public.users, appears to contain email addresses, passwords, dates of birth, phone numbers, home addresses, passport numbers, ID card numbers, and foreigners’ document numbers. The SQL file is likely an excerpt of a larger database. DarkOwl found 103 email addresses for users of the service, with most consisting of accounts from personal email providers such as gmail.com and ukr.net.
medstar.sql
The website, medstar.ua is a commercial cloud-based ‘digital-medicine provider’ with telemedicine, prescription, medical imaging, and laboratory medical services in Ukraine.
The medstar.sql leaked database does not contain any header information to denote the name of the tables or date of extraction. However, the SQL table appears to be a registry of 669 medical appointments with the patient’s personal information, e.g. full name, date of birth, phone number, address, age, gender, and even photo with links to an external website domain: health.mia.software containing their image and scans. The doctor’s information is also included with each record, with 606 doctors affiliated with the territorial medical association of the Ministry of Internal Affairs. The appointments covered a range of specializations such as therapy, neurology, infectious diseases, etc.
The latest appointment date in the database was November 30, 2021, suggesting this file was likely created sometime in December before the new year.
somefilesfromnotcatholic.zip
The files contained in the archive somefilesfromnotcatholic.zip are all date/timestamped: January 15th 2022 / 12:48. The archive consists of five folders, each containing 20 subfolders spanning several years of various official letters, photographs, and applications for government services. One folder contained letters directed to the Ukrainian Ministry of Internal Affairs requesting the production of specific license plates for individuals. The data archive includes several Ukrainian citizens’ personal information such as phone numbers, email addresses, driver’s licenses, passports, and national identification information related to vehicle registration and driving. The latest data file in the archive was date/timestamped: November 15th, 2021/19:58.
Notably, the archive appears to be a sample of a larger dataset of vehicle data the threat actor has in their possession.
mail.minregion.gov.ua
Less than 18 hours later and on the original thread, Vaticano shared an archive of supposedly stolen emails from the Ukrainian Ministry of Community and Territories Development server, mail.minregion.gov.ua. The sample included 79 email messages (.msg files) with various correspondences between employees of the organization in November and December 2021. The messages appear to have originated with one email address, and the latest message was dated December 20th, 2021, 14:17:18 EET.
It’s unclear if this a subset of a larger volume of emails the threat actor has access to, or whether they only had access to one user’s mailbox within the organization. DarkOwl was able to extract 425 unique group and individual e-mail addresses from the archive shared.
diia_filestorage_db01.rar
Shortly before getting banned on Raid Forums, the user Vaticano shared yet another database on the original thread, labelled, diia_filestorage_db01.rar. The archive consists of 81JSON files with records containing unidentified applicant user information, e.g. full name, date of birth, passport number, phone number, email address, physical address, photo, and COVID vaccination and medical data privacy consent. The latest applicant record was dated October 22nd, 2021.
According to their website, DIIA is a mobile app developed by the Ministry of Digital Transformation of Ukraine and launched in 2020. It allows Ukrainian citizens to upload digital versions of their official documents in their smartphones, instead of carrying physical ones, for identification and verification purposes. It’s likely that this dataset is a sample of a larger set of files held by the threat actor. DarkOwl found 77 unique personal email addresses for Ukrainian citizens in the database, mentioned mostly from gmail.com and ukr.net.
Free Civilian
Within a week of Vaticano’s exile from Raid Forums, the Tor onion service “Free Civilian” appeared online offering to sell various databases from government organizations across Ukraine along with a personal statement detailing the drama between the admin of the Tor service and the moderators of Raid Forums, declaring the forum is no longer “the island of freedom” anymore. (Source: DarkOwl Vision)
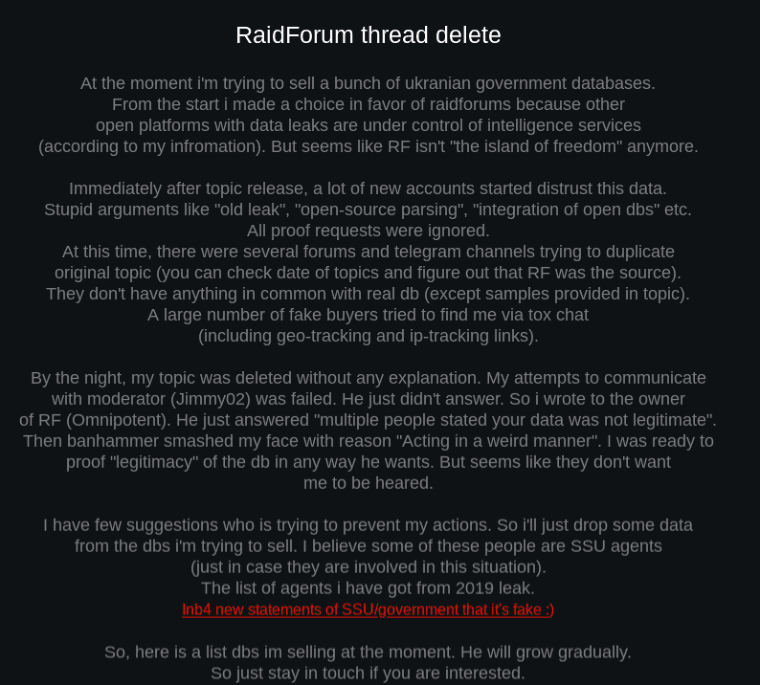
Additional data proofs on the Free Civilian onion service confirmed that the leaks Vaticano shared on Raid Forums were smaller samples of data from larger databases they had access to and were offering for sale on the darknet site.

On the Tor onion service, the size of the databases for sale were significantly larger than the samples shared on Raid Forums. The DIIA database size was 765 GB and offered for sale at $85K USD, with a price increase to $125K USD by early February. Another database, titled, “e-driver.hsc.gov.ua” database containing Ukrainian driver and vehicle information was listed at 431GB and offered for sale for $55K USD. The samples from Free Civilian correlated to the samples Vaticano provided in the somefilesnotcatholic.zip archive on Raid Forums.
Free Civilian lists several other databases for sale summarized below:
- wanted.mvs.gov.ua – Ukraine’s government database of criminal records.
- health.mia – Ministry of Internal Affairs servers hosting patient health data.
- mtsbu_samples_db – Ukraine’s Motor (Transport) Insurance Bureau.
As of the date of publication, both the DIIA and e-driver.hsc.gov.ua databases were marked as sold.
More Ukraine Data Surfaces
Banning Vaticano did not stop Ukraine-related data from appearing on Raid Forums. Another user shared a sample called “PFU of Ukraine” which consists of a text file containing over 53,000 names of individuals in Ukraine and phone numbers.
DarkOwl uncovered 156 unique email addresses in the file. The domain pfu.gov.ua is associated with the Ukrainian government’s pension fund website.
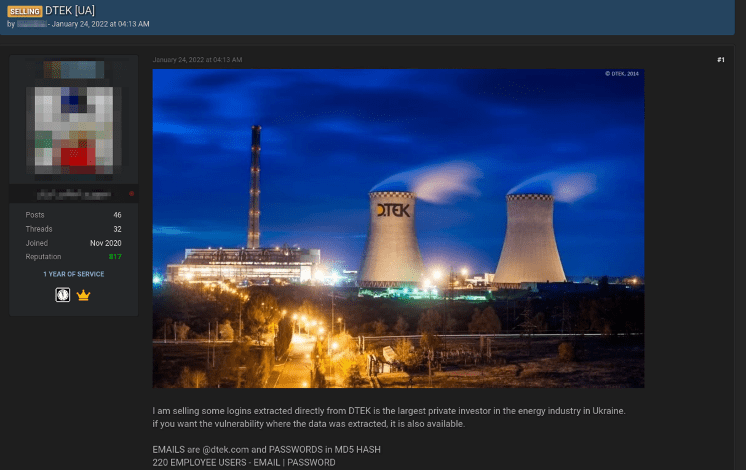
Days after the PFU leak, a post titled, DTEK[UA] appeared with the offer to sell over 200 credentials exfiltrated from employees at a large energy investor in Ukraine. The post also stated the vulnerability used to extract the data was also available. The Raid Forums user has history on the forum authoring at least 46 posts. (Source: DarkOwl Vision)
A leak titled “Ukrainian Police Dox” also emerged containing a zip file of various PDFs with PII for officials dated October 2020.
There is no evidence to conclude any of the recently shared data was sourced during the mid-January cyberattacks.
The Ukrainian data leaks in January were not the first time Ukrainian government and citizen data has been exposed in the underground. Last year, DarkOwl captured numerous spreadsheets and database archives allegedly affiliated with Ukraine disseminated and discussed on a Telegram channel known for stolen data brokerage.
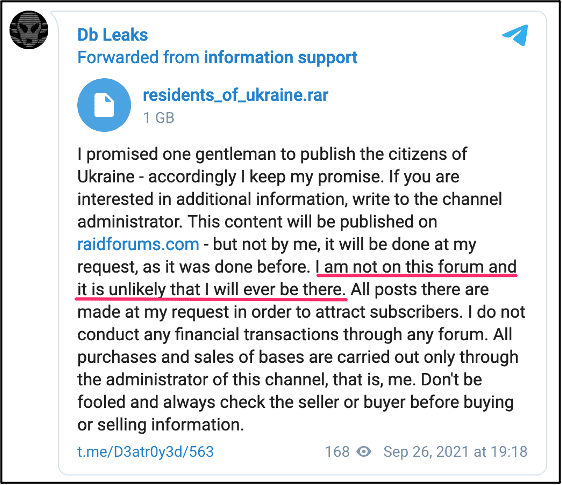
DarkOwl also follows the popular Telegram channel, DB Leaks (a.k.a. @d3atr0y3d)who shares posts in English and in Russian and uploads files believed to have been captured from compromised sites and servers around the world. Coincidentally, they shared the same DIIA archive shared by Vaticano on the 23rd of January, within days of the appearance of the Free Civilian Tor service. (Source: DarkOwl Vision)
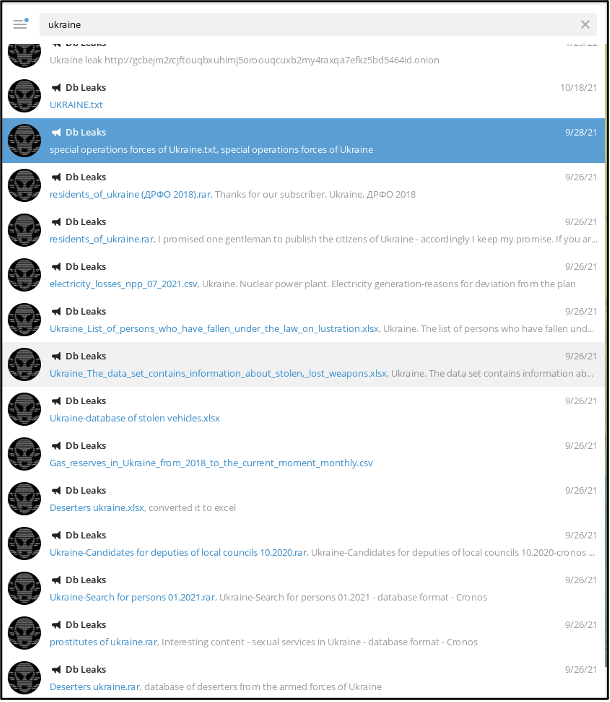
Furthermore, in fall 2021, they uploaded several Ukraine-specific databases including a list of personnel assigned to the Special Operation Forces of Ukraine and Ukrainian candidates for local parliamentary elections. The figure below includes more examples of the types of data they shared.
The channel has also posted leaked databases from targets inside Russia, including the list of donors to the FSK, the non-profit, Anti-Corruption Foundation, setup by Alexei Navalny.
Interestingly, during the second half of 2021, several other Raid Forums users circulated information about Ukraine’s nuclear power plant, a spreadsheet of stolen and lost weapons in Ukraine, residents of Ukraine, and companies registered in Ukraine along with information pertaining to the country’s financial and economic activity. (Source: RaidForums)
Closer analysis revealed these archives were re-shares of various posts on the DB Leaks Telegram channel dropped earlier in 2021, perhaps by proxies of @d3atr0y3d or one of their associates (information support) at their request directly.
Who is Vaticano?
Vaticano, the Raid Forums user who caught the attention of DarkOwl analysts in mid-January, created their account on the deep web forum within hours of their first post and has no prior history on the forum. The Vaticano persona includes an avatar of the Pope surrounded by flames along with calls for the people of Ukraine to return to the Catholic Church.
Vaticano discouraged another user on the forum from leaking manuals for Polish Army logistical resources in an attempt to align with the original messaging of the website defacements in 2022 to blame Poland for the attack. (Source)
Another user on the forum tried to vouch for Vaticano commenting that they knew he was in Russia.
“Lolz guru, my friend knows this user. He is in Russia.”
Vaticano further attempted to cloud their origins in a comment after sharing the sample of minregion email server messages, requesting if anyone could “read their language”, referring to the Ukrainian text in the email messages from the compromised email accounts.
The Tox ID listed on the Free Civilian Tor service and potentially administrated by Vaticano, does not match the Tox ID included in the ransomware note deployed the night of the mid-January attack.
Polish “DIS” connection
The mid-January Ukrainian government website defacements included references to several controversial historical events between Ukraine and Poland. It mentioned Volyn, a part of Poland that Ukraine annexed in 1939 and the Organization for Ukrainian Nationalists (OUN), which was a far-right political group that operated in the region of Galicia –part of Poland before WWII.
Research suggests that such allusions were likely part of a Russian-originated false-flag operation to incriminate Poland for the January attacks. Polish journalists noticed that the Polish translation of the threatening message was a non-native speaker and likely produced using Google Translate.
Cyberattacks Continue
On the 14th-15th of February 2022, Ukraine’s Ministry of Defense, its Armed Services along with Privatbank, Oschadbank, and Monobank financial institutions, experienced severe DDoS attacks resulting in the organizations being taken offline. According to open-source reporting, many Privatbank users received fake text messages stating the bank’s cash machines were out of service, which caused additional stress on the bank’s network – with a surge of users checking their account balances at ATM locations around the country.
Last August, DarkOwl observed a senior and extremely active user on Raid Forums offer a database containing over 40 Million Privatbank users’ personal information including their name, date of birth, and phone number. This dataset could have easily been utilized to target Privatbank customers in this information operations campaign against Ukraine. (Source: DarkOwl Vision)
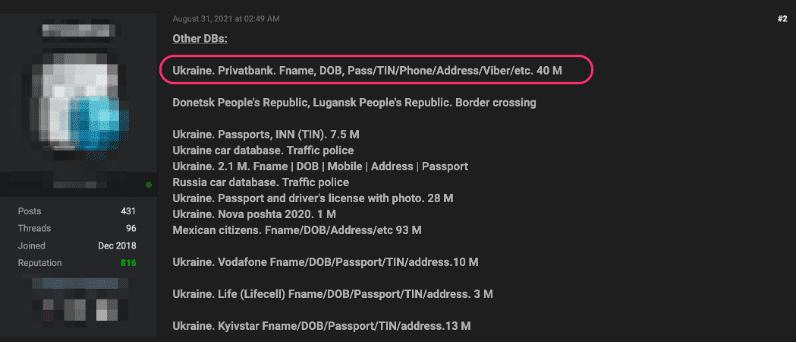
The date of the DDoS attack, while it could be insignificant, is exactly one month after the defacement and malware attacks in January. The malfeasance from the DDoS was not large enough to be categorized as a full cyberattack, but with geopolitical tensions rising to possibly the brink of war, the campaign was likely apart of a larger asymmetric psychological operation.
US Intelligence reporting of the second wave of cyber attacks in February assessed that Russia’s Main Intelligence arm, GRU was responsible.
Propaganda and Disinformation
The sheer volume of propaganda in open-source reporting renders correlating darknet findings against OSINT around the conflict challenging, if not impossible. Tor discussion forums known for historical propaganda circulation are surprisingly absent of any Ukraine-specific reporting in recent months while some users on Telegram shared fake photos of mushroom clouds inciting fear that Russia had used a nuclear weapon against eastern Ukraine.
One could interpret the lack of information as stemming from the possibility that the Russians did not have need in using typical darknet services for dissemination; the disinformation and misinformation campaigns are directly targeting other sources and platforms; or, it is already embedded within other news media sources. According to Reuter’s, Ukraine’s Deputy Secretary of the National Security and Defense Council, Serhiy Demedyuk, officially attributes the 13/14 January defacements to a cybercriminal group operating out of Belarus identified as UNC1151.
“This is a cyber-espionage group affiliated with the special services of the Republic of Belarus.”
Mandiant assesses that UNC1151, also identified as the “Ghostwriter” campaign, as responsible for direct espionage and obtaining confidential information for Belarusian dissidents, media entities, and journalists. Other research indicates that UNC1151 are potentially affiliated with Russia-supported anti-NATO disinformation campaigns that have been in circulation over recent years, replacing genuine articles on news sources with fake ones and spreading false quotes of political and military officials across Lithuania, Latvia, and Poland. However, direct attribution of UNC1151’s role in recent cyberattacks in Ukraine is indeterminate.
DarkOwl also found a darknet threat actor group known as Cyberpartisans trying to help defend Ukraine from Russia’s aggressions. The group claimed responsibility for an attack against the Belarusian rail network system to stymie Russia’s movement of troops towards Ukraine, despite the movement of troops via rail would not be a necessity for an invasion. The Cyberpartisians self-identify as a pro-democracy group of hacktivists, and last year tapped Belarus’s Ministry of Internal Affairs phone lines, leaking conversations between officials about organized protests against the country’s infamous dictator on Telegram.
In recent weeks, Lukashenko has been overtly supportive of Putin, jointly overseeing strategic military exercises in Belarus, including launches of Russia’s hypersonic missiles in a public show of the two countries’ alliance and continued cooperation. Belarus will undoubtedly play a critical role in the region in the events unfolding.
DarkOwl is monitoring the darknet as the conflict in Ukraine ripples throughout the European continent impacting the global economy and stressing international partnerships and alliances. We anticipate a fluctuation in underground network and criminal activity across Tor and other anonymous networks in the near term. We also forecast the KillMBR/KillDisk destructive wiper malware and attack methodologies debuted in Russia’s asymmetric operations against Ukraine’s critical digital infrastructure to be widely adopted by other criminal gangs and nation-state sponsored cyber operatives in future campaigns.
Curious about something you read? Interested in learning more? Contact us to find out how darknet data applies to your use-case.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















