BULLETIN: New COVID Vaccination Certificate Scam Targets European Hospitals
DarkOwl has recently discovered a cyber-criminal group offering to hack hospitals located across the European Union (EU) to access and falsify vaccination records for willing buyers on the darknet.
In contrast to the paper-based vaccination cards that continue to be the standard across the United States, the EU recently launched a “Digital COVID Certificate” that features a mobile app for quickly verifying one’s COVID vaccination, PCR testing, or virus recovery status. The EU’s program features a QR code with a unique digital signature for each individual, to supposedly prevent falsification and facilitate free movement throughout 27 countries within the EU. Sixteen (16) non-EU countries have also been added to the digital passport scheme including Israel, Norway, Turkey, and Panama.

False digital vaccination records listed at $600 USD in bitcoin
Known simply as “xgroup,” the criminals behind this EU-centric fraud scheme claim to be able to access EU-based local hospital digital vaccination records on behalf of their darknet customers. All the process claims to require of the customer is that they submit their personal information (along with payment) so that it can then supposedly be added to their local hospital’s vaccination records database. This information is then theoretically accessible by the EU Digital Certificate application as each issuing body – such as a hospital, test center, or health authority – has its own digital signature key that communicates with the program.
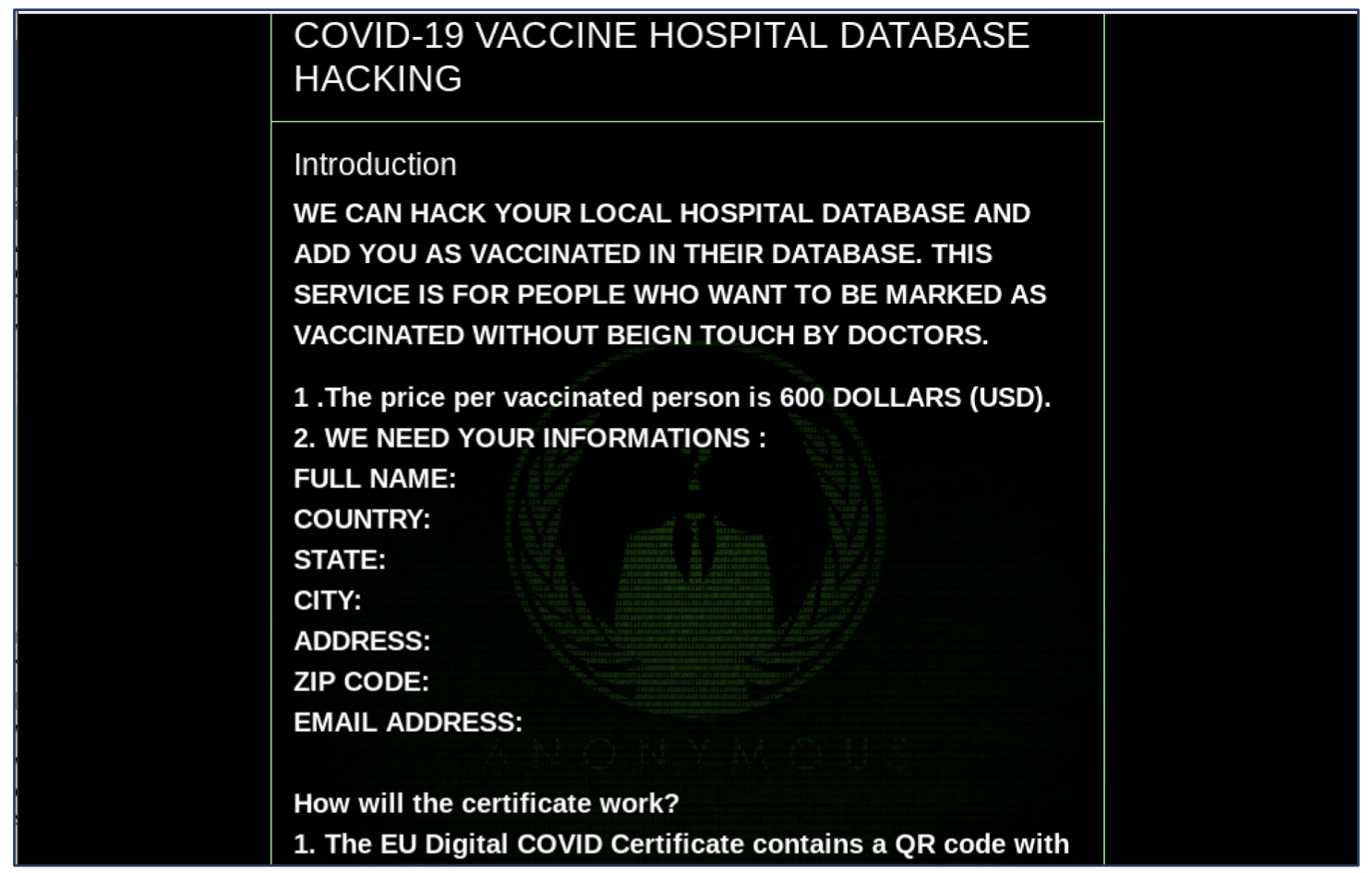
COVID-19 Vaccine Hospital Database Hacking from Tor
Who is Xgroup?
Xgroup hosts a dedicated V3 hidden service on Tor where they advertise a range of “hacking services.” In addition to the COVID vaccination record hack, they claim to offer school grade alterations, social media account hacking, and financial debt clearing.
There is no proof of the legitimacy of xgroup’s skills. DarkOwl has captured mentions of their email address across various forums and services on Tor since July 2021, though it is unclear how long they were in operation before that. Our analysts also observed that in mid-July, xgroup were recruiting members with “social engineering skills,” and in late August they were raising donations for their next attack – including quotes from hacktivist organizations like Anonymous.
"Message for all the governments of the world. We recognize you as serious opponents, and do not expect our campaign to be completed in a short time frame. However, you will not prevail forever against the angry masses of the body politic. Your choice of methods, your hypocrisy, and the general artlessness of your organization have sounded its death knell. You have nowhere to hide because we are everywhere." - Xgroup (Sourced from DarkOwl Vision Darknet Data)The group self-promotes their abilities to “hack social networks” and “destroy someones life” including creating financial and legal issues and spreading disinformation on social media.

Source: DarkOwl Vision Document
Another COVID Scam?
DarkOwl has long observed scammers on darknet and continues to see fraudsters offer goods and services for sale, take a customer’s money, and then never deliver the purchased product. Thus it has not been surprising to see this same tactic being applied rampantly as it has throughout the pandemic, during which time we’ve seen a surge in COVID related scams for things like KN95 masks, coronavirus-infected blood, and black-market COVID vaccines
Xgroup’s fraud scheme is only applicable to European countries as the United States does not have nation-wide digital vaccine record system nor vaccination records stored at local hospitals. The scheme also explicitly refers to the EU Digital COVID Certificate program.
Given that this scheme targets EU-based customers, it is peculiar that the offer lists the address requirements using the US mailing address format and not European which require postcodes instead of zip codes, listed before the city or town, and house names and multi-lined street addresses.
This, along with the fact that the price listed in US Dollars, suggests this could very well be simply a scam originating from criminals located in the United States.
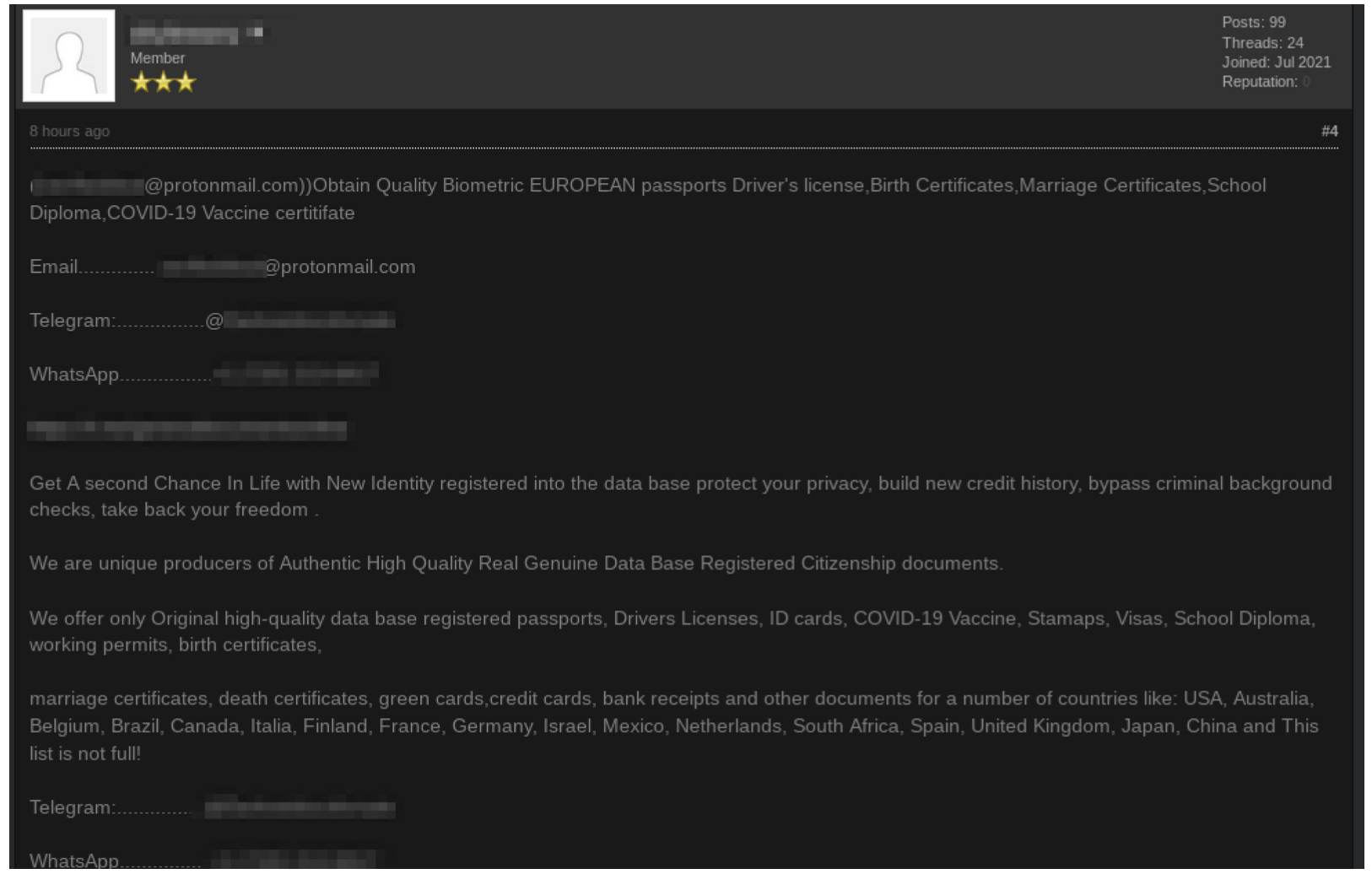
Similar Identity and COVID Vaccine Scams Offered on the Darknet
Risk to the EU Digital COVID Certification Program
The EU Digital COVID Certificate program and the idea of “digital vaccination passports” is cause of increasing controversy across the world with many claiming an invasion of health privacy, a threat to personal freedom, and opportunity for discrimination against those without ready access to vaccination centers and mobile smartphones. Similar digital vaccination records systems are in place across the US such as New York’s Excelsior Pass that queries the state’s centralized department of health records. California has a similar online portal for residents to verify their vaccination status with a QR code, called “Digital COVID-19 Vaccination Record.”
While any such digitally-based record system is susceptible to hackers or threat-actors, DarkOwl assesses the overall risk to the EU Digital COVID Certificate program is minimal. As ominous a threat as criminals offering to “hack local hospitals” may seem, we suspect there is a low probability that many darknet fraudsters are actively attempting to gain illicit access to local healthcare computer networks in order to deliver what has been advertised to their customers. In contrast, ransomware groups originating in the darknet pose a legitimate risk to hospitals and healthcare groups worldwide.
Curious about something you’ve read? Contact us to learn more about how darknet data applies to your use-case.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















