CONTI Ransomware Ceasefire, Rebrand, or News Media Hype
June 09, 2022
The recent buzz around Conti poses questions about what is really going on with the notorious ransomware group
In late May, information security researchers reported the administrative panel for Conti’s official Tor website, Conti News, was shut down. The service site for negotiations was also offline, prompting widespread social media speculation and news reporting that the infamous ransomware group had disbanded or shutdown.
However, at the same time, Conti’s darknet-based blog – which they primarily announce their victims and leak their stolen data – continued operating without interruption. While the blog did remain live, there was a noticeable decrease in victim announcements during an 8-day window between the 12th and 20th. Other than this brief slow-down in victim shaming, DarkOwl analysts are not aware of the existence of an official statement from Conti indicating their operations have been interrupted. The group continues to post new victims and leak data on their site.
Since May 19th, Conti has announced 24 new victims as of time of publication.
Recent Victims
Costa Rica declared a state of national emergency May 8th due a widespread ransomware attack carried out by Conti. The cyber attack started with the Ministry of Finance, and eventually spread to other Costa Rican government agencies including the tax systems. The government refused to pay the $10 million demanded extortion, even after Conti attempted to get Costa Rican citizens to encourage the government to pay the ransom. When that effort failed, Conti simply moved on to attack websites from the Peruvian government.
Since the controversial attacks in Costa Rica, Conti has not slowed its operations and continues to target several corporations located in NATO-aligned western countries. This includes victims from the transportation sector in Europe, such as a popular airline in the UK, a car dealership chain in Norway, and a mega-yacht supplier in Italy.
A Consequential Breach of Trust and Dox of the Team
At the beginning of the war in Ukraine, Conti was one of the first ransomware groups to publicly announce their support of Russia. Almost immediately, a Ukrainian-based ‘security researcher’ took to Twitter to leak Conti’s critical data. The leak contained Conti’s ransomware source code, details of their internal operations, botnet infrastructure, and private jabber chats and PII from members of the team.
Similar leaks followed for members of the FSB-backed Trickbot group, including dossiers of their members. Private chats from TrickBot and internal operations data from Conti showed a strong operational partnership between the two groups. Following the consequences of their pro-Russian stance, Conti retracted their allegiances claiming they “do not ally with any government and we condemn the ongoing war.”
The impact of the group’s internal leaks continue to ripple across the underground and damage the reputation of Conti on the darknet. Technical ‘red-teaming’ materials from the group are consistently circulated and re-shared across popular darknet forums. Recently, rumors emerged that Conti had shifted to using Emotet for its ransomware campaigns after Trickbot’s sensitive information was shared.
Conti’s Public-Affiliation with STORMOUS Group
Another ransomware group to publicly announce their support of Russia’s invasion, STORMOUS, suffered a similar fate to Conti. The group, which operates primarily on Telegram, posted a marketing graphic depicting their and Conti’s logos, solidifying a Russia-aligned partnership. Not long after announcing their pro-Russian stance, their Tor v3 web service hacked and leaked by another group known as Arvin Club.
STORMOUS targeted Coca Cola in late April, but on May 10th, STORMOUS randomly announced they had suspended operations. They subsequently posted a public apology to their victims, hinting that they would return in the future with bigger attacks against western countries.
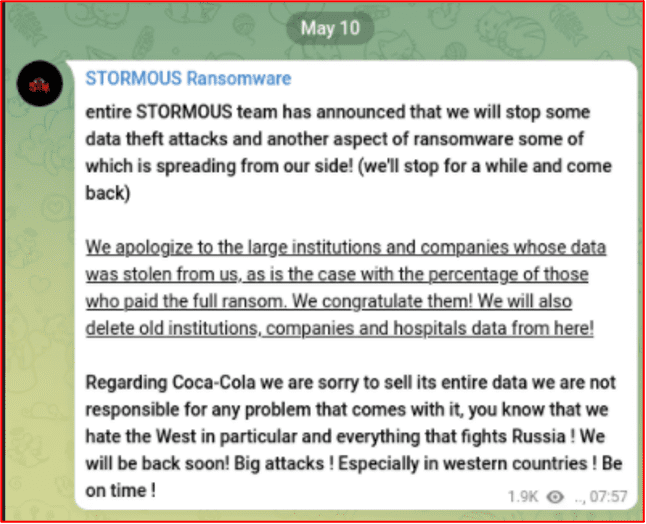
NB65 Weaponizes Conti Source Code Against Russia
Network Battalion (NB65) successfully deployed Conti’s leaked ransomware source code with a modified cipher. The group has since carried out over half a dozen or more attacks against targets across Russia.
Most recently, NB65 targeted a several IT/MSPs in Russia by encrypting their network and exfiltrating over 350 GB of data. They claimed to have simply relieved one of the Russian companies of their principal corporate communication information systems, e.g. Teams, replacing the names of channels and groups with “hacked by NB65.”
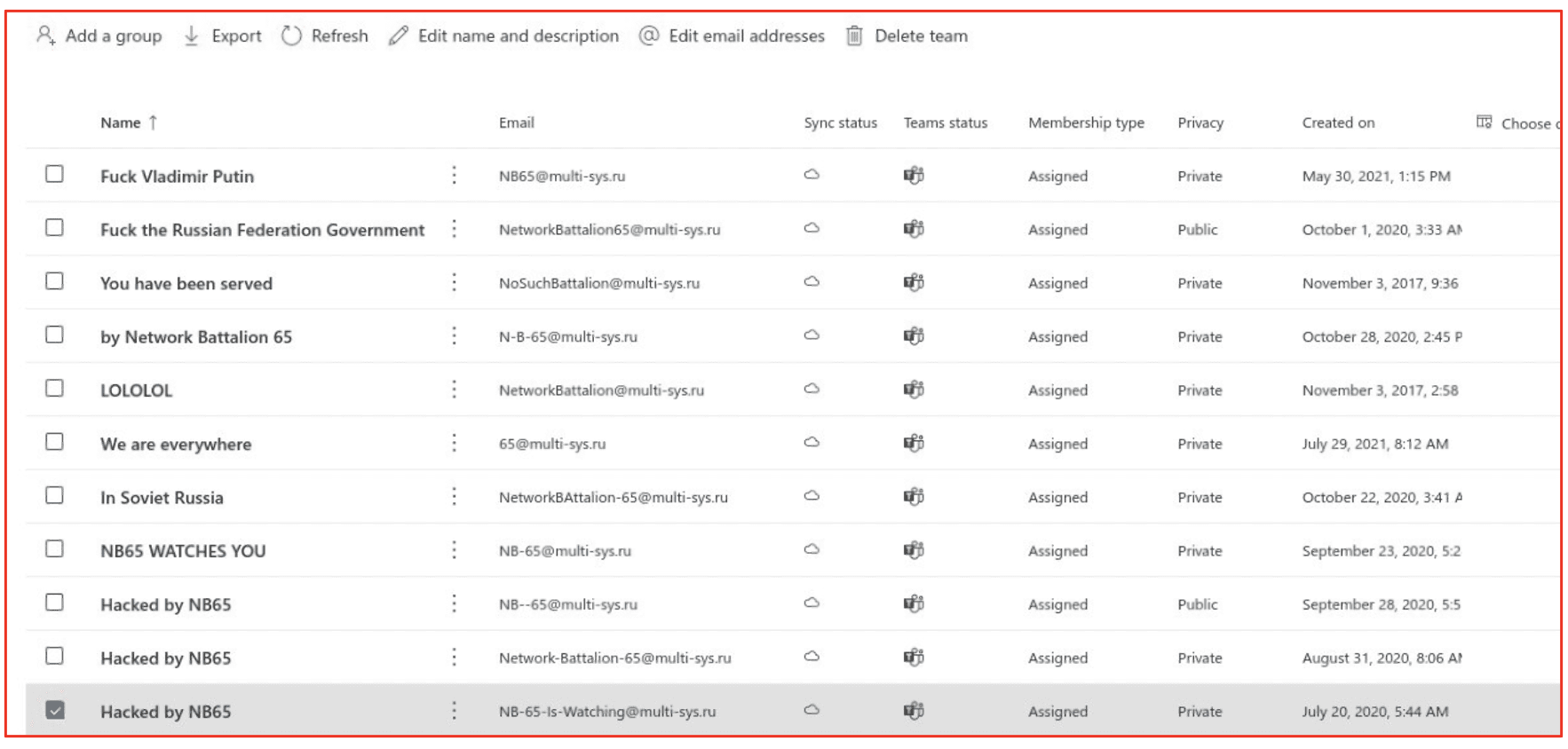
NB65 wrote on social media:
“Epic failure of incident response…We decided to relieve you of you Sharepoint sites, Azure AD connections, and all of your user OUs. Credential reuse is awesome! Don’t blame Nikolai, he didn’t know. Teams might be struggling.”
Could Conti’s ceasefire be simply a by-product of on-going darknet drama between ransomware threat actors?
A now-removed post on Conti’s victim site dated May 17th suggests there was some drama brewing between Lockbit, Blackcat (a.k.a. AlphaV, alfa) and Conti. The post claimed that affiliates of Lockbit “steal chats and deceive their advertisers” suggesting that AlphaV and Lockbit are scammers.
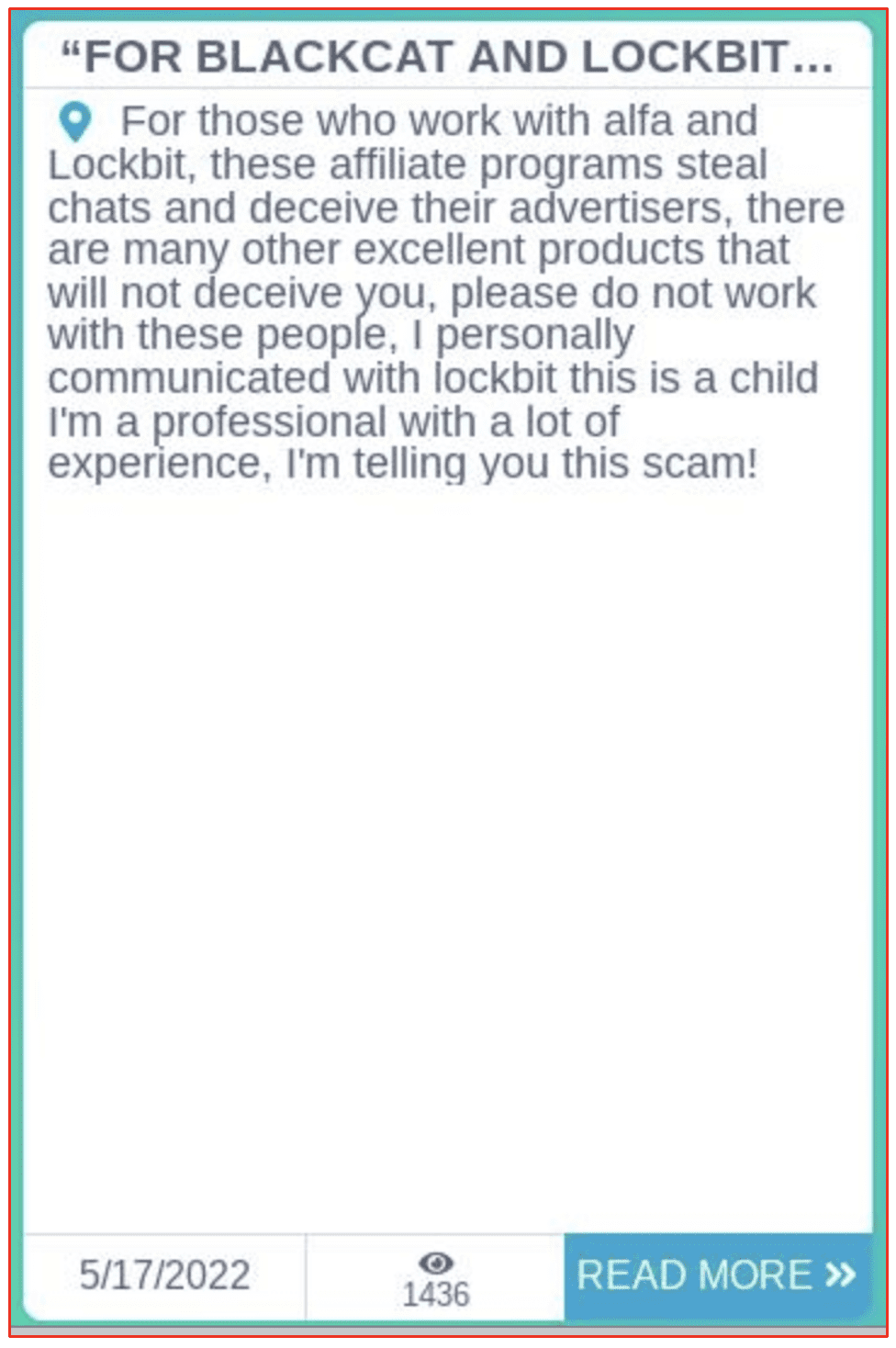
Shortly after, a Lockbit representative on a darknet forum encouraged ‘salary employees’ of Conti to contact them on qTox to “discuss a mutually beneficial cooperation … with subsequent employment for a more profitable job.”
Классическая информационная пропагандисткая война, кураторы из ФСБ подсказали? Ваши офисы с зарплатными пентестерами разворошили, и вы думаете, что в вашу мусорскую контору пойдут работать нормальные пацаны? Какие же вы профессионалы если в ваших слитых переписках с жабера вы неоднократно пиздаболили своим жертвам о скачанных данных? Как можно верить тем, кто не позволяет адвертам принимать оплату на свой кошелек? Чтобы честно управлять партнёркой нужно быть очень старым? В моём возрасте мне хватает ума не трогать чужие деньги и беречь свою репутацию 3 года. Вы думаете, что после ваших политических игрищ вам перестали платить и попытавшись переманить адвертов с других партнёрок вам будут больше платить? Жалкое зрелище. Приглашаю всех офисных зарплатных сотрудников конти ко мне в токс, обсудим с вами взаимовыгодное сотрудничество, с последующим трудоустройством на более выгодную работу.
[Translation]
“A classic information propaganda war, did the curators from the FSB suggest? Your offices with salary pentesters have been stirred up, and do you think that normal guys will go to work in your garbage office? What kind of professionals are you if in your merged correspondence with jabber you repeatedly fucked up your victims about the downloaded data? How can you believe those who do not allow advertisers to accept payments to their wallet? Do you need to be very old to manage an affiliate program honestly? At my age, I’m smart enough not to touch other people’s money and protect my reputation for 3 years. Do you think that after your political games, they stopped paying you and trying to lure advertisers from other partners, they will pay you more? A pitiful sight. I invite all office salary employees of Conti to my tox, we will discuss mutually beneficial cooperation with you, with subsequent employment for a more profitable job.”
A more recent post on a popular darknet forum suggested that all of this was all hype. Another user stated that the offline panels could simply be an indication that the group was changing their infrastructure.
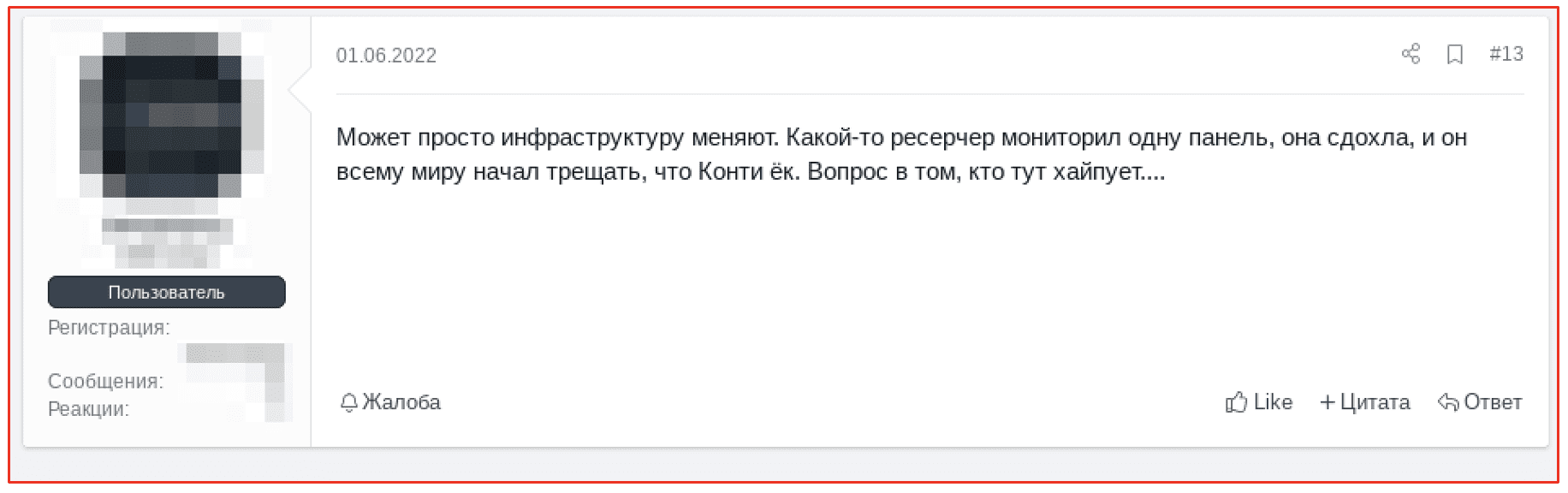
[Figure Translation]
“Maybe they’re just changing the infrastructure. Some researcher was monitoring one panel, it died, and he began to crack all over the world that Conti quit. The question is who is hyping here…”
It is important to consider that Conti is still precariously caught in the crossfire between running a criminal ransomware empire, and public opinion – which is largely against Russia. Popular pushback against Conti could be a factor in shutting down the Russian-associated brand. Any combination of these might have prompted the group to take a step back from the limelight, regroup, and rebrand. Furthermore, there is always the possibility that law enforcement operations are covertly influencing these events.
In the past, shutting down ransomware groups has proved almost impossible. Following their attack on Kaseya, REvil shut down and REvil affiliates were arrested in the following months. Analysts have confirmed that the REvil gang is back as of April 2022, possibly at the behest of the Kremlin to carry out Russia’s national cyber initiatives. The former ransomware group DarkSide went offline after hacking Colonial Pipeline, only to resurface under new names.
Reports that Conti has shut down or broken up do not mean the threat of this ransomware group and its operators has passed. History dictates that it is common for ransomware groups to re-emerge. It’s possible that, after a period of reorganization and lapse in activity, a Conti-affiliate or Conti-equivalent group will return. Some research suggests that Conti is directly or indirectly linked to other popular ransomware, like AvosLocker, Hive, BlackByte, and Karakurt. AvosLocker and Hive have been extremely active in recent weeks, with Hive following Conti’s attacks against the Costa Rican government by compromising at least 30 servers in Costa Rica’s Social Security Funds program known as CCSS in late May.
DarkOwl will continue to monitor Conti and Conti-affiliated groups. Victim announcements can be pulled using our latest product Ransomware API. Contact us to learn more.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















