Cyber Insurance and the Darknet
July 15, 2022
Cyber insurance is an increasingly popular topic of conversation across the information security community, as the frequency of attacks against organizations has steadily increased in recent years. The probability of a successful attack, resulting in the unauthorized access of an organization’s data, applications, services, network infrastructure or devices, or worse – the theft or loss of proprietary or sensitive data – is exponentially increasing in the post-pandemic world where work-from-home and hybrid work/home office environments have been normalized challenging an organization’s cyber-defense posture.
According to Accenture, 66% of small businesses have experienced a cyberattack, with the average cost of a malware attack on a company (regardless of size) hitting $2.6 million, signaling that cyber insurance policies are now essential for an organization to prevent significant financial business impact or even bankruptcy.
Coalition’s 2022 Cyber Claims Report confirmed the attack trends with their data indicating that small businesses are consistently targeted more frequently than medium and large organizations. They also report that claims increased in severity by 54% in 2021, with the average cost approaching $360,000 USD for companies with revenues more than $100M.
What Is Cyber Liability Insurance and What Does it Cover
Cyber liability insurance is a form of insurance available for individuals and businesses to purchase to help reduce the negative financial impacts and risks of conducting day-to-day activities on the Internet. Cyber insurance is rooted in errors and omissions (E&O) insurance which generally protects against a company’s faults and defects in their products and services.
Any organization or business that operates predominantly on the Internet, collects or retains customer data such as personally identifiable information (PII) or protected health information (PHI), interfaces with the payment card industry, or stores sensitive proprietary data and digital intellectual property on a company network connected to the Internet should consider purchasing a cyber liability insurance policy.
In the event of a cyberattack, the theory of E&O coverage kicks in to support a sole proprietor or business who cannot fulfill their contractual obligations with their network and systems offline. Similarly, the coverage can help cover costs to litigate claims resulting in the failure of service performance or product delivery due to the cyber security incident.
Cyber liability insurance covers most of the financial costs associated with a cybersecurity incident and data breach. This could include:
- extortion payments associated with a ransomware attack
- digital forensics and incident response team costs to remediate an event or recover compromised data
- paying legal fees and/or fines as a result of privacy violations
- monitoring the credit for, and restoring the identities of compromised customers or employees with exposed PII
- cyber terrorism attack
- procuring replacement hardware or compromised computer information systems
- notifying stakeholders of the security incident and breach of confidential information
Some cyberattacks include cyber espionage that doesn’t result in an overt cybersecurity incident and IT network failure. Does your cyber liability insurance policy cover your employees’ personal information showing up in the underground without the knowledge of your IT department?
The US Federal Trade Commission (FTC) advises that policy holders should check to make sure their insurance covers:
- cyberattacks against resources located anywhere in the world and not geographically limited
- legal costs if incident results in lawsuit or regulatory investigation, e.g. includes “duty to defend” wording
- offers a breach hotline available 24/7, 365 days a year
- cyberattacks on your data held by vendors and other third-parties
- lost income due to business interruption
- crisis management and public relations
Types of Cybersecurity Insurance Coverage
Policies covering cyber incidents are generally written as either first- or third-party coverage or both. First-party coverage protects the infrastructure and data owned by the policy holder’s organization. This coverage includes data related to an organization’s employees and customers. Third-party coverage is a form of liability coverage associated with the consequences of the exposure of an organization’s customer and vendor data.
Often when a cyberattack occurs it is the sensitive customer data or employee PII that is most valuable to the threat actor where the database is quickly commoditized in the darknet and traded or sold in underground data marketplaces and forums.
Unfortunately, many organizations under protect themselves getting first-party coverage only, when third-party is more comprehensive by orders of magnitude and applicable to the modern cybersecurity use case. Furthermore, traditional E&O policies do not cover the loss of third-party data.
Insurance Carriers, Brokers, Underwriters, and Reinsurers
While cyber liability insurance is offered by most major insurance carriers, we quickly realized that those shopping for cyber liability policies can easily get confused by the different roles and responsibilities of the various insurance players. During our research on the cyber insurance industry, we encountered several different stakeholders that could have vested interest in the cybersecurity risks associated with potential insurance claims.
Insurance Carriers – also referred to as the insurance provider, an insurance company, or agency – is the financial security behind the coverage provided in an insurance policy in the event of a cybersecurity incident. The insurance carrier issues the policy, charges the premiums to the policy holder, and covers payments from claims against the policy.
Insurance carriers issuing cyber liability insurance policies must remain hyper-vigilant on the evolving security risks facing their policy holders. They will establish pre-policy issuance security risk assessment protocols, evaluation criteria, and periodic auditing of their policy holders. In the US, insurance carriers are often described as “admitted” and non-admitted insurance providers which differentiates in whether they are ‘backed by the state’ financially and in compliance with regulations outlined by the policy holder’s state Department of Insurance.
Insurance Broker is an agent who sells or purchases insurance policies on behalf of another. An insurance broker specializes in the nuances and complexities of the insurance industry and knowledgeable of security risk management to advise on the type and amount of coverage required for a cyber liability insurance policy. They serve as a “consultant” and insurance representative to the insured policy holder.
Underwriters include persons assigned and qualified to initially assess, evaluate, and assume the security risk of another party for a fee or percentage commission from the policy value. The underwriter may work directly for the insurance carrier or independently contract to the insurance issuing organization as a freelance underwriter. The most commonly relatable example is health insurance underwriters who closely evaluate an applicant’s risk posture via detailed questions of the potential policy holder’s age, health conditions, and family medical history.
In cybersecurity, an underwriter has the responsibility to perform comprehensive risk assessments of cyber liability insurance policy applications for potential security risks that are increasingly complex and challenging to predict based on traditional risk modeling methodologies.
As claims increase in value the application process for new policies is increasingly rigorous with insurance carriers requiring underwriters gather supplementary ransomware-based questionnaires and proof of business continuity plans and security incident response plans from insurance applicants.
Third-Party Administrator often called TPAs, are professional, state-licensed organizations that support the insurance carrier in administrative services related to insurance. They most often are responsible for handling claims on behalf of the carrier including the evaluation of the legitimacy of the claim, processing the claim, making financial determinations, and reporting to regulation authorities. While TPAs are historically involved in the health insurance industry, there is a growing group of cybersecurity-specific TPAs that exclusively focus on managing cyber and privacy breach claims.
Reinsurers refer to the reinsurance companies, or more simply, the insurance providers for the insurance companies. According to the Corporate Financial Institute, a primary insurer – the insurance carrier – transfers policies, or insurance liabilities – to a reinsurer through a process called cession, or “ceding”. On average, insurance carriers cede an estimated 50% of the policy premiums they collect to the reinsurance market. Reinsurers’ revenue is directly tied to the quality of the risk assessments performed for policy holders on the front end and the amount of financial capital available, either from the reinsurer or third-party capital sources.
Why Does the Darknet Matter to Cyber Insurance Professionals?
Data, information, and subsequent cyber intelligence derived from sources in the darknet, deep web, and criminal chat communities can help cyber insurance underwriters, insurance carriers, and reinsurers develop more robust and highly predictive security risk models. Higher fidelity risk models help price premiums to minimize claims payments benefiting the insurance carriers and their reinsurers accordingly.
The types of data from the darknet that might be utilized in security risk models can be as simple as the volume of policy holder’s organizational employee email addresses exposed on the darknet to more complex models which account for brand and reputational risks, mentions of executive leadership, network infrastructure like domain names and IP addresses, and exposed proprietary organizational data stolen through a pre-existing breach cyberattack.
Pre-policy evaluations can include darknet exposure data to assess the level of compromise of the applicant organization and determine whether prior breaches exist to the applicant policy holder – which is often excluded in cyber liability insurance policies. Pre-existing breach data for the pending policy holder’s vendors and supply chain can also drive security risk modeling and the potential risk must be financially compensated for.
Reinsurers also should independently monitor for darknet exposure and mentions of the insurance carriers they cover as well as their high-valued policy holders. Ransomware threat actors have actively targeted insurance carriers and exploit their policy holder information to leverage for subsequent attacks and drive negotiations with their extortion victims using their policy information as leverage for higher extortion payments.
Insurance Carriers are not Immune to Showing up in the Darknet
In 2021, Avaddon compromised a division of the global insurance carrier, Axa Group in Malaysia and reportedly exfiltrated over 3TB of claims data and medical records of their policy holders.
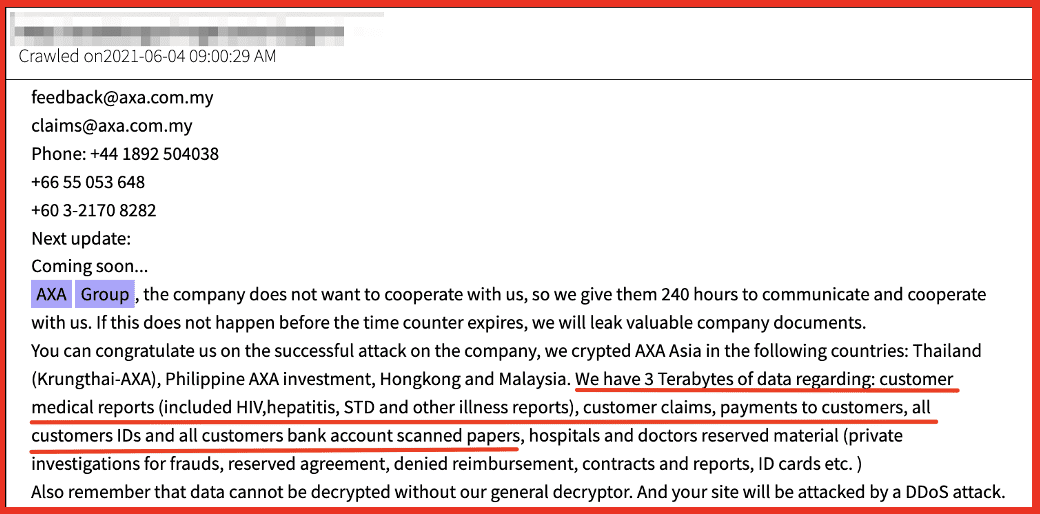
Figure 1: Axa Group Ransomware Announcement, Source: DarkOwl Vision
Most recently, the reincarnated “Happy Blog” restarted by REvil after Russia invaded Ukraine, targeted a family-focused insurance broker in Ohio giving the threat actors direct access to sensitive PII of their clients for subsequent fraud or digital identity theft.
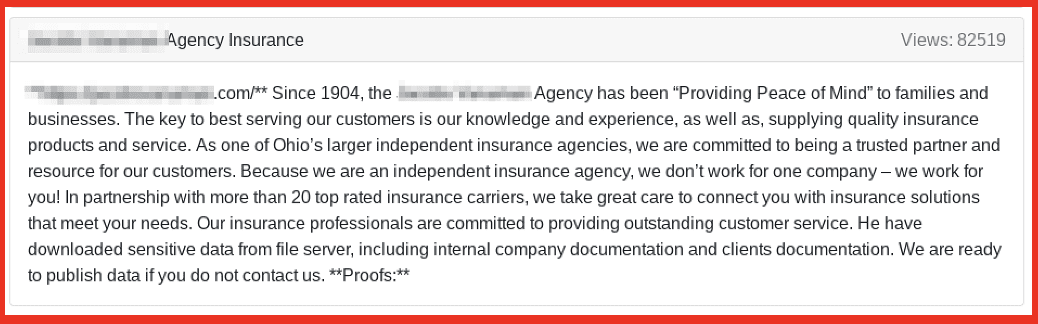
Figure 2: Source REvil Blog on Tor
Victim data can emerge on the ransomware shame sites exclusively hosted on Tor in the darknet or data marketplaces, like Industrial Spy. One of the “free” offers on Industrial Spy includes a prominent Third-Party Administrator in India, MDINDIA. The proofs include a significant volume of claims carried out by the organization.
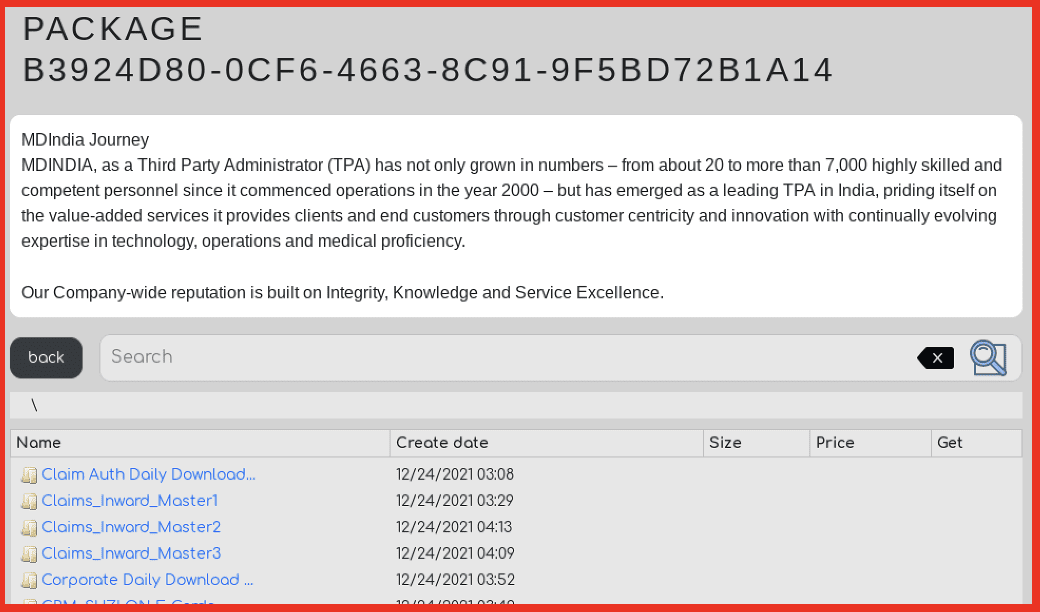
Figure 3: Source: Industrial Spy
There is an increasingly complex interrelationship between data from the darknet and the organizations involved in issuing cyber liability insurance policies and managing claims. Darknet data can help drive better risk decisions in issuing policies and persistent monitoring for on-going security risks to insurance carriers, brokers, and their policy holders. The cyber liability insurance market is evolving as result of threat actors on the darknet and increased attacks resulting in significant financial claims.
Next: stay tuned for our upcoming content that will take a closer look at some things that are excluded from cyber insurance policies.
Learn how DarkOwl enables cyber insurance carriers, reinsurers, and technology platforms to leverage darknet data to better identify, benchmark, and measure the risk associated with underwriting cyber liability. Contact us to learn more.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















