Popular Cybersecurity Threats & Topics Being Discussed on the Darknet
October 27, 2022
To round out Cybersecurity Awareness Month, we’ve gathered some of the hottest cybersecurity topics being discussed amongst actors on the darknet and deep web.
Cybersecurity awareness month has been enlightening for consumers and businesses alike. Many information security professionals and vendors have shared many guides this October on topics like multi-factor authentication, zero-trust, and other cyber resilience measures to hopefully help soften the impact of a significant corporate cybersecurity incident. The adage, ‘it’s not a matter of if you will be breached, but when…” might feel more and more realizable as the list of ransomware and corporate network attack victims continue to grow.
So, before the month’s end – in the spirit of spreading collective awareness – our analysts took a closer look some of the most popular cybersecurity threats and threat actor attack vectors discussed on the darknet.
Ransoming – Linux
There’s no question that ransomware continues to be one of the most popular threats utilized against commercial organizations, especially small and medium sized businesses that lack the enterprise-level information security budgets. Threat actors are increasingly interested in exploiting Linux-based systems and servers, and, lately, DarkOwl analysts have directly witnessed an increase in technical conversations related to the subject. Lockbit was one of the first ransomware strains to specifically target virtual Linux-based VMware ESXi servers, encrypting the vCenter infrastructure and virtual machines (VMs). Other ransomware gangs like BlackBasta have followed suit using SSH vulnerabilities and compromised credentials to deliver the ransomware to the server.
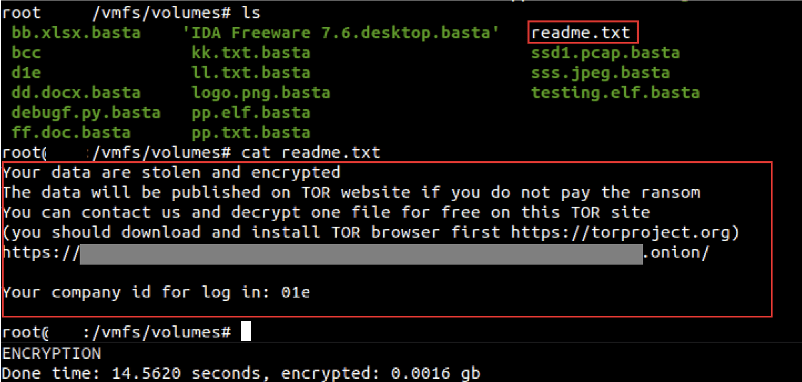
Figure 1 – Source: MalwareBytes
While many corporations run Windows or Mac client machines, Linux servers are the predominant server of choice for backend operations in enterprise commercial systems, hosting critical intellectual property and sensitive data. The type of data available in a ransomware campaign involving Linux servers attracts ransomware groups for the higher probability of ransom payment and the potential exploitation of sensitive information for cyber espionage.
Go Phish – Attackers continue to target marketing tech such as Google Adwords
Phishing is still a widely utilized and prominent attack vector discussed on the darknet for gaining unauthorized access corporate networks. Threat actors discuss phishing methods, offer “MASTERCLASSES” on the subject for sale in decentralized marketplaces, and regularly advertise phishing email templates for major commercial entities like Google, Apple, and Microsoft.
Some commonly discussed phishing methods are designed to target corporations’ social media accounts held by marketing departments. Others intentionally leverage social media relationships like employees’ LinkedIn connections to trick the victim into clicking on a document shared by a ‘friend.’
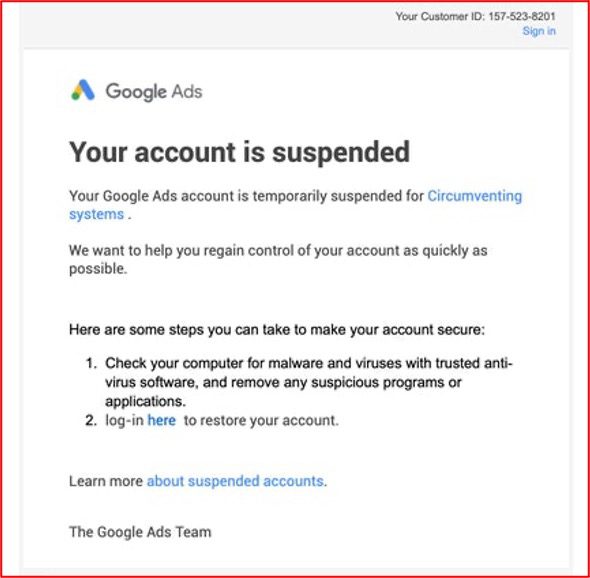
Figure 2 – Source: Tor Anonymous Network
In the example below, threat actors directly leverage Google ADSENSE Adwords for serving up phishing URLs. These are deployed to unsuspecting victims who inadvertently select the malicious URL because it appears at the top of their search.
[ORIGINAL POST]
“Ответы: 1
Форум: Поиск партнеров,инвесторов, поставщиков
КУПЛЮ Настройка рекламы Google ADSENSE
Ищу профессионала, кто создаст рекламу по продаже ПРАВ,ВУ в гугле адс.
Способ оплаты:
1. Фиксированная оплата за настройку и пропуск рекламы в гугле.
2. % от продаж ( при блоке рекламы, вы сами запускаете новую рекламу) – Хороший выхлоп.
P/S. Писать строго, кто разбирается в данной теме по…”
[TRANSLATED]
“Answers: 1
Forum: Search for partners, investors, suppliers
BUY Google ADSENSE Ad Settings
I am looking for a professional who will create an advertisement for the sale of rights, WU in Google ads.
Payment method:
1. Fixed payment for setting up and skipping ads in Google.
2. % of sales (with an ad block, you launch a new ad yourself) is a good exhaust.
P/S. Write strictly to those who understand this topic by…”
Source: DarkOwl Vision
These elaborate phishing campaigns frequently result in successful corporate email compromise and occur daily. What’s more, they are getting increasingly sophisticated with targeted spear-phishing methods employed.
Phishing via SMS, (a.k.a smishing) has increased in popularity.
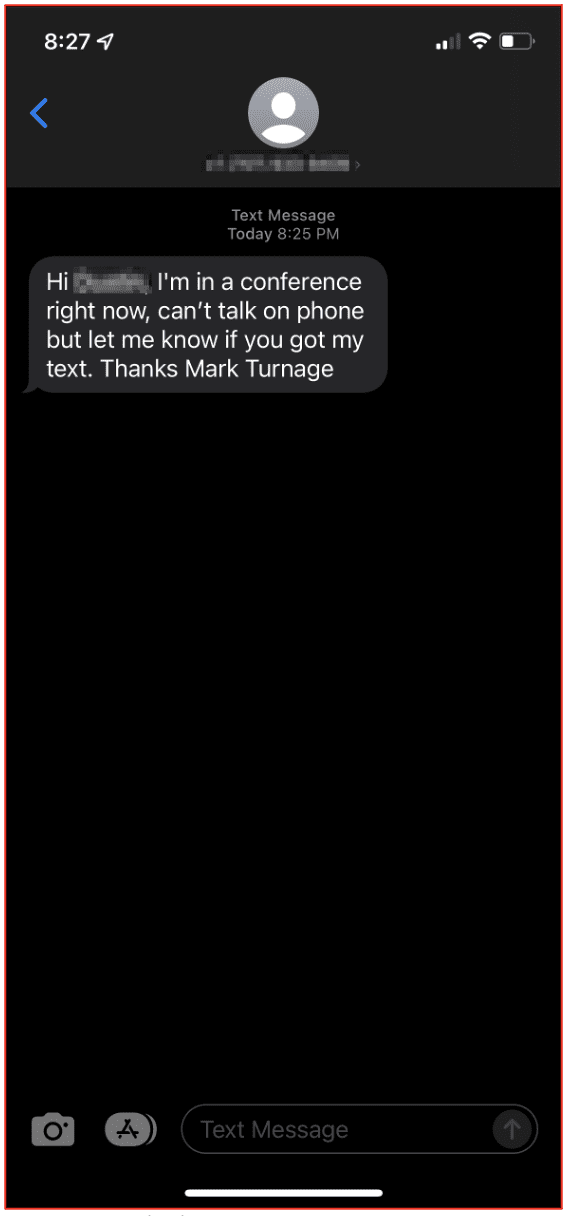
One example of a successful smishing campaign we’ve seen discussed on the darknet has been a fake emergency ‘smishing’ text from executives sent to employees in the organization, designed to not only confirm the phone number of the employee, but potentially drop malware via a follow-up malicious link.
DarkOwl IT provided the example to the right, which depicts an attempted smish of a DarkOwl employee using an executive’s identity.
Server Vulnerabilities – Microsoft Exchange
Like the Linux server ransomware strains, darknet threat actors active seek server-specific vulnerabilities for potential exploitation and server data compromise. DarkOwl analysts have lost count of the number of Microsoft Exchange-related compromised organizational data leaks that surfaced by hacktivists participating in the Ukraine-Russia cyberwar. Over a dozen exchange vulnerabilities added to the NVD in 2022 and even more in 2021, provide threat actors plenty of opportunity for remote code execution (RCE), privilege escalation, file read-write access and arbitrary file deletion on a compromised Exchange server.
Most of the RCE vulnerabilities include malware delivery via PowerShell. Microsoft security advisories strongly suggest that Exchange Server customers disable remote PowerShell access for non-administrative privileged users in their organizations.
While ProxyNotShell is getting lots of recent attention, some of the Exchange vulnerabilities DarkOwl has captured discussed do not always require authentication to execute malicious code. Proof of concept code is also often referenced on darknet discussion forums and Telegram channels, making the vulnerabilities even easier for less adept cybercriminals.
Several of the large database leaks observed by DarkOwl because of a successful Exchange server attack are dumps of every email and attachment from every inbox on the compromised on-prem server. These vulnerabilities do not apply to Microsoft Online or Microsoft 365 cloud mail services.
Server Vulnerabilities – Atlassian Confluence
Another server vulnerability that is being discussed in darknet discussion forums is a remote code execution vulnerability that affects Confluence Server and Data Center (described as CVE-2022-26134 by the NVD).
As of this summer, the vulnerability has reportedly been patched by Atlassian with the release of versions 7.4.17, 7.13.7, 7.14.3, 7.15.2, 7.16.4, 7.17.4 and 7.18.1; however, the vulnerability is still explored by cyber criminals.
In fact, multiple threat actors – with varying motivations and intentions – have expressed specific interest in Confluence-related security vulnerabilities. Another, tagged 26138, involved a hardcoded password for the user account, disabledsystemuser. Threat actors believed to be likely associated with nation state actors and users with specialties in cryptomining have indicated this vulnerability allows for production environments to be compromised, new administrator accounts created, and malicious access to corporate networks granted.The ransomware gang, AvosLocker targeted vulnerable Confluence servers with their command and control at scale earlier this summer.
As attack vectors continue to evolve, having eyes on the darknet is critical for any company looking to establish a comprehensive cybersecurity posture. To learn more about how the darknet applies to your use case, request a time to chat with one of our team members.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















