Darknet Criminals Capitalize on Tax Fraud in U.S.
DarkOwl has evidence that criminals from the darknet are actively exploiting the American Treasury Department and its Internal Revenue Service (IRS). Many actors are advertising offers for ‘refund methods’ for sale in fraud communities across the darknet and adjacent chat platforms such as Telegram. Fraudsters have also detailed how to directly utilize tax preparation software such as TurboxTax to steal refunds for quick, but fraudulent financial gain.
Other underground fraud methods such as ‘glass checks,’ are increasingly popular. DarkOwl has observed several victims’ tax payment checks to the IRS and/or state revenue departments have been stolen and sold on the darknet for financial exploitation.
One of the primary financial economies of the darknet is fraud, and tax fraud is a booming sub-economy that is constantly evolving. Our analysts have provided the below as the result of our latest observations in regards to tax fraud on the darknet.
Fraud on the Darknet
The brokerage of corporate and private information is one aspect of fraud we see realized in leak after leak of corporations and consumers’ private information. However, the fraud industry is much larger than data alone. This ever-growing segment of the darknet encapsulates not only the carding industry and associated banking malware and exploit development, but also what we casually refer as the ‘get-rich-quick’ schemes that prey on loopholes in payment interfaces and programs.
During the pandemic, we observed an influx of new ‘get-rich-quick’ fraudsters entering the darknet -capitalizing on vulnerabilities in the US government subsidized funding programs for those financially impacted by COVID-19. We also witnessed programs such as the Small Business Administration (SBA)’s Paycheck Payment Program (PPP) and state-level Pandemic Unemployment Assistance (PUA) regularly mentioned across Telegram with regular ‘sauce’ offers and updates available. We detailed how some of these programs were exploited our in-depth report last year.
According to public media sources and recent academic reporting, it is estimated that the US paid out at least 10-15% of the $800 billion USD PPP in fraudulent payments. PUA fraud estimates are closer to $400 billion USD.
Many of the same fraudsters who buy, trade, and sell methods for pandemic-related financial fraud schemes, also advocate, and disseminate tax refund fraud methods in the underground.
Current Tax Fraud Mentions
Most of the fraud IRS methods on Telegram include offers for “fullz” for the IRS tax refund walk through method. “Fullz” is darknet community slang for ‘full information’ and usually includes an individual’s full name, social security number (SSN), date of birth, physical address, credit card number, and other key identification information to conduct identity theft.
According to DarkOwl Vision, the price of ‘fullz’ has decreased in recent years with US citizen ‘fullz’ readily available for less than $20 USD. More expensive ‘fullz’ will also include a copy of the victim’s driver’s license or falsified bank statements for additional identity verification.
In addition to individual ‘fullz’, some underground data brokers sell ‘access’ to drives and databases with significant volumes of PII. A couple of years ago, a RaidForums member using the moniker “fairbanksfires” advertised an offer to purchase access to stolen devices associated with an online tax filing company in the United States.
This cybercriminal could provide its buyer access to millions of US social security numbers, email addresses, passwords, and bank routing and account numbers for extensive tax fraud for years to come.
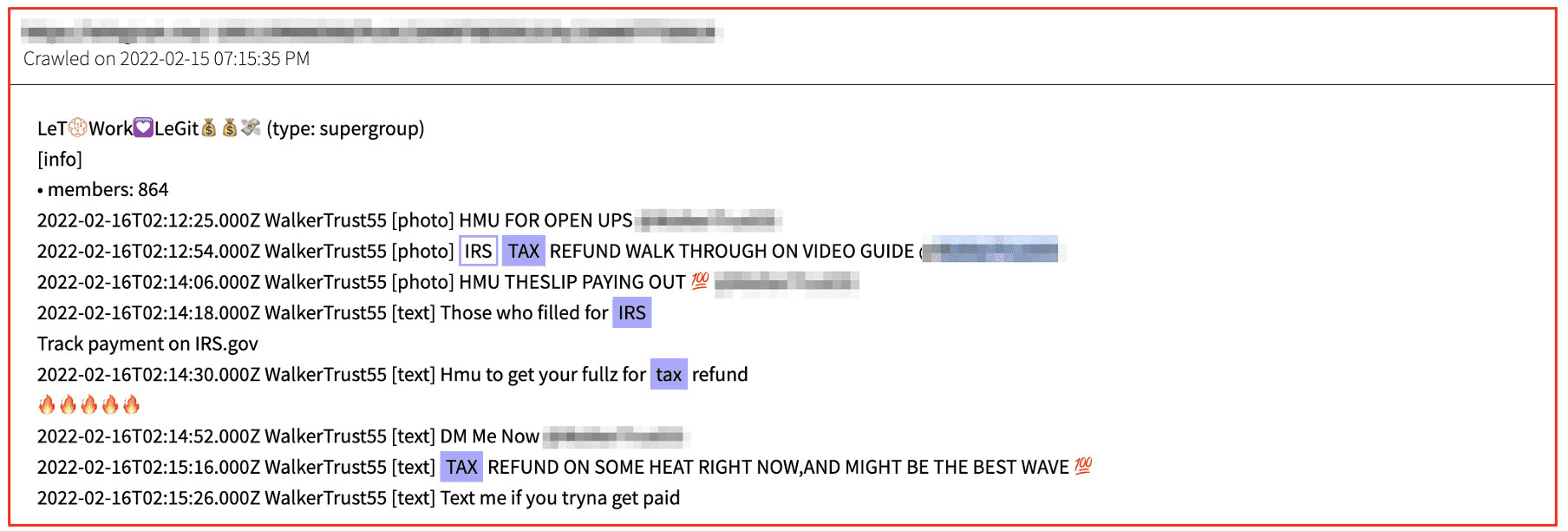
IRS Method using Fullz’ Identity
The most common ‘irs method’ and tax refund fraud method costs no more than $150 USD. Other personalized offers for IRS tax fraud includes not only the ‘fullz’, but supporting falsified self-employed business licenses, 1099 and W2 forms generated by the fraudster to supplement the IRS tax forms and increase potential for higher refund amounts. Most methods upon purchase detail how to perform an OSINT background search on the ‘fullz’ information provided to locate the employer of the fullz or their previous employer.
The web service FreeERISA is often mentioned which provides free access to registered users all form 5500s filed with the Department of Labor for most all companies across the United States, including tax identification numbers. Methods further detail how to estimate tax credits and beneficiary information to submit into the return to maximize the refund amount.
One user shared a video on a Telegram channel using this method that demonstrated a fraudulently filed Federal tax return with a refund amount more than $20,000 USD and the California State return was close to $3,500 USD.
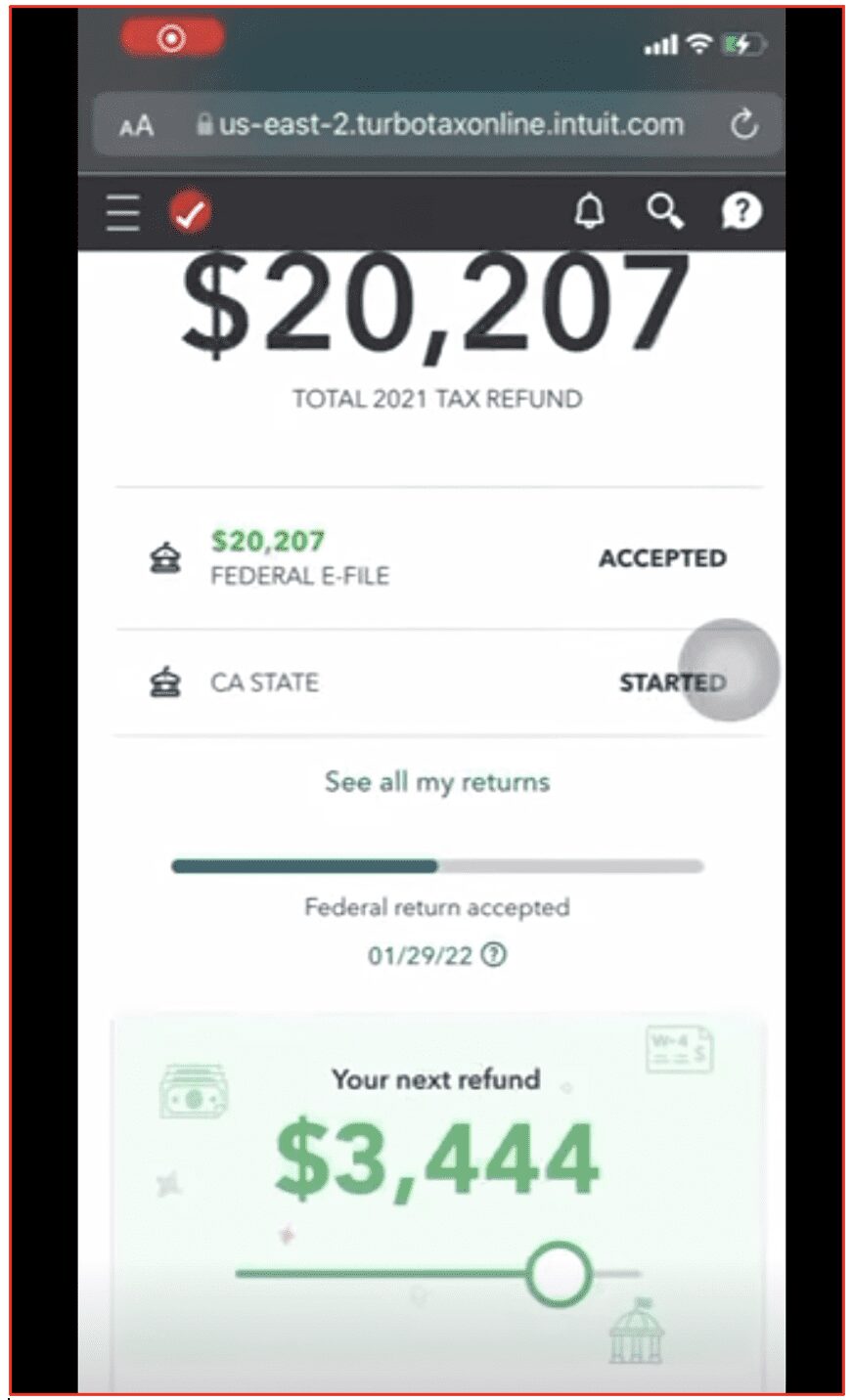
Another fraudster’s IRS method advises the buyer to use known persons that have little to no credit history but will pass SSN validation checks in tax account software applications. They recommend using their own children’s, elderly parents’, grandparents’ or distant familial associations’ SSNs and identities for higher success of the tax fraud method.
IRS Method using Buyer’s Identity
This method is directly tied to the buyer’s identity and SSN and involves utilizing automated tax software like TurboTax and TaxAct to obtain a refund of upwards of $20,000 USD in combined federal and state funds. This method caveats up-front that this method will lead to the IRS eventually catching on and will force the buyer repay the amount refunded during this tax year. The purpose of this method is to give the buyer financial relief for an estimated two to six years before audit is highly likely.
Any W2 can be utilized for this method – or one can be obtained from the fraudster directly. The buyer does not actually have to be employed to use this method. The fraudster stated that the buyer may enter any amount in the Wages, Tips, and Compensation field of the W2, but the amount should not exceed $100,000 USD. The exact percentages for federal and state social security wages and tax withheld calculations are provided in the method as guidance for the buyer’s fraudulent W2 entries.
The fraudster suggested adding real life or ‘fullz’ dependents to increase the refund amount.
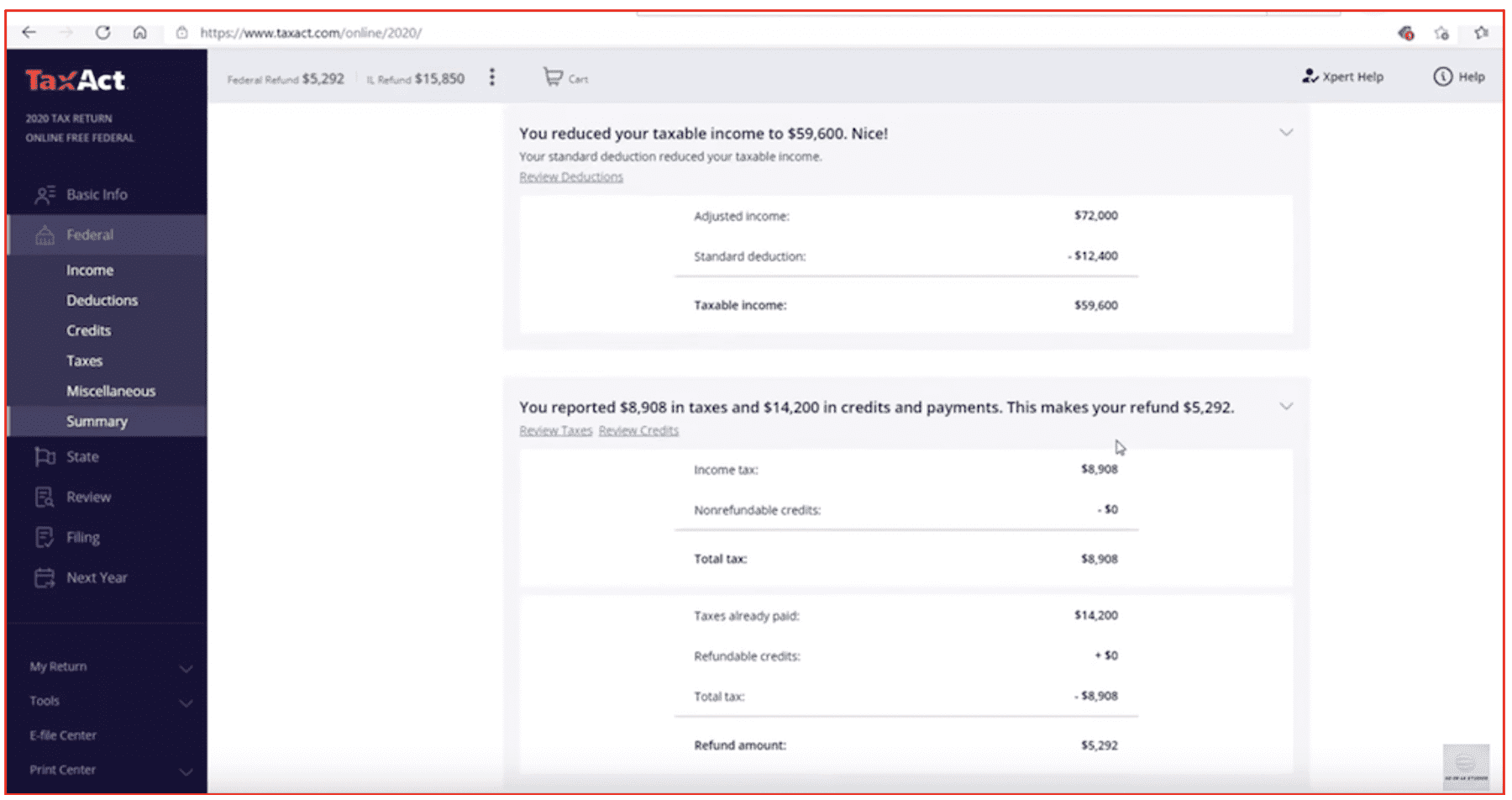
The fraudster was upfront that this method is only recommended for the worst-case buyer in extreme financial duress, e.g. has no money whatsoever, homeless, or unable to make ends meet and needs money quickly.
Competitive Fraudsters
Naturally, fraud vendors are incredibly competitive with each other and speak out against other popular fraud shops and declare that most methods are scams. DarkOwl noticed one user on Telegram berating the widely discussed ‘irs method’ avowing their method alone was the ‘real method’ and payments are readily available in 48 hours.
“you’d never get paid with the irs method”
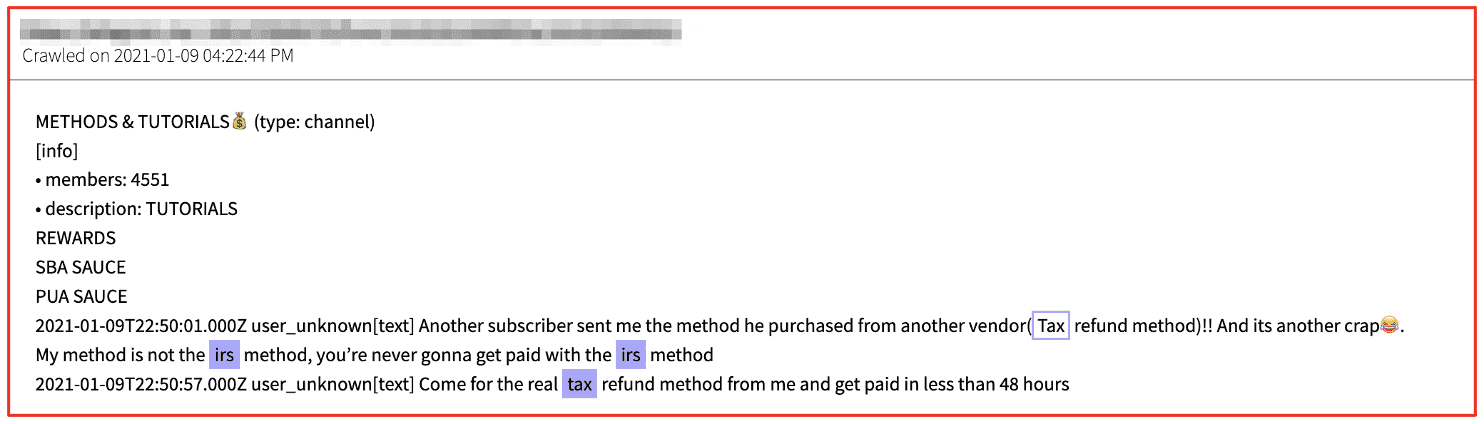
‘Glass Fraud’ Catches IRS Payments Mailed via USPS
A new fraud method involves the physical theft of mailed paper checks inside US Postal System (USPS). According to fraudsters, the method is commonly called ‘glass’ because “the checks always clear” and often requires an insider threat, e.g. cooperative postal workers who provide copies of the universal mailbox access keys or steal the mail directly and turn it over to the fraudsters for resale.
The fraudster sells the check to the buyer for some base price or percentage of the value of the check, usually via Bitcoin or similar cryptocurrency. The stolen checks are then digitally altered and deposited into mule-controlled bank drops that payout the specified amount of the check to the buyer via their preferred method of choice, such as: cash, Western Union, or CashApp. The buyer assumes the risk that the check will not go through, but because the victim is completely unaware their check has been stolen, it is most likely not yet cancelled. It is only until the payment is never received to the payee’s address, that they realize they are a victim of fraud.
Although this method does not directly target the IRS and tax refunds specifically, many of the stolen checks include tax payments submitted via physical checks via the US mail.
The screenshots of the ‘glass check’ examples below are two of dozens we found on a popular fraud Telegram channel. Many paper checks included payments to the IRS or the state revenue departments for thousands of dollars in value.
The sell value of the check is directly proportional to the value of the check itself with a $2,000+ tax payment check selling for more than twice as much as the $843 USD one. Some of the checks also included the signee’s social security number in the memo line which could be used for additional identity theft and fraud. We’ve intentionally obfuscated any identifying information for the checks we included here, but the dates and check payment amounts are clearly visible.

Curious about something you read about tax fraud or the darknet? Interested in learning more? Contact us to find out how darknet data applies to your use case.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















