Darknet Threat Actor Report: LAPSUS$
In order to curate interesting darknet data collection from sources across the deep web, Tor, I2P and other “darknets” our analysts regularly follow “darknet threat actors” that openly discuss and disseminate stolen critical corporate and personal data.
In December 2021, DarkOwl witnessed increased activity on the darknet regarding the cybercriminal gang known as LAPSUS$. The group appears to have preference for attacking Portuguese-speaking organizations using data extortion-style campaigns and leverage compromised AWS servers where possible. Thus far, LAPSUS$’s attacks seem to have little critical impact to the victim’s organizational operations, with seasoned darknet community members stating the group is “amateur.”
DarkOwl believes the cybercriminal group has potential to become a formidable darknet threat actor with the increasing frequency of attacks in recent weeks. The lethality and economic impact of the attacks against their victims have yet to be determined.
Vodafone Telecommunications in Portugal
Since last December, the darknet threat actor group known as LAPSUS$ has been actively targeting Portuguese speaking services across Latin America and Portugal including prominent media and telecommunications companies on both continents.
Most recently, between 7 and 8 February, Vodafone Portugal – a subsidiary of Vodafone Group in the UK – stated in a press release the company was subject to a “deliberate and malicious cyberattack with the aim of causing damage and disruption.” Open-source reports indicate the attack impacted Vodafone’s 4G/5G voice and SMS service as well as its television services, but no ransom was demanded. While there is limited information about the attack in the press, Vodafone persists no subscriber or sensitive customer data was accessed or stolen.
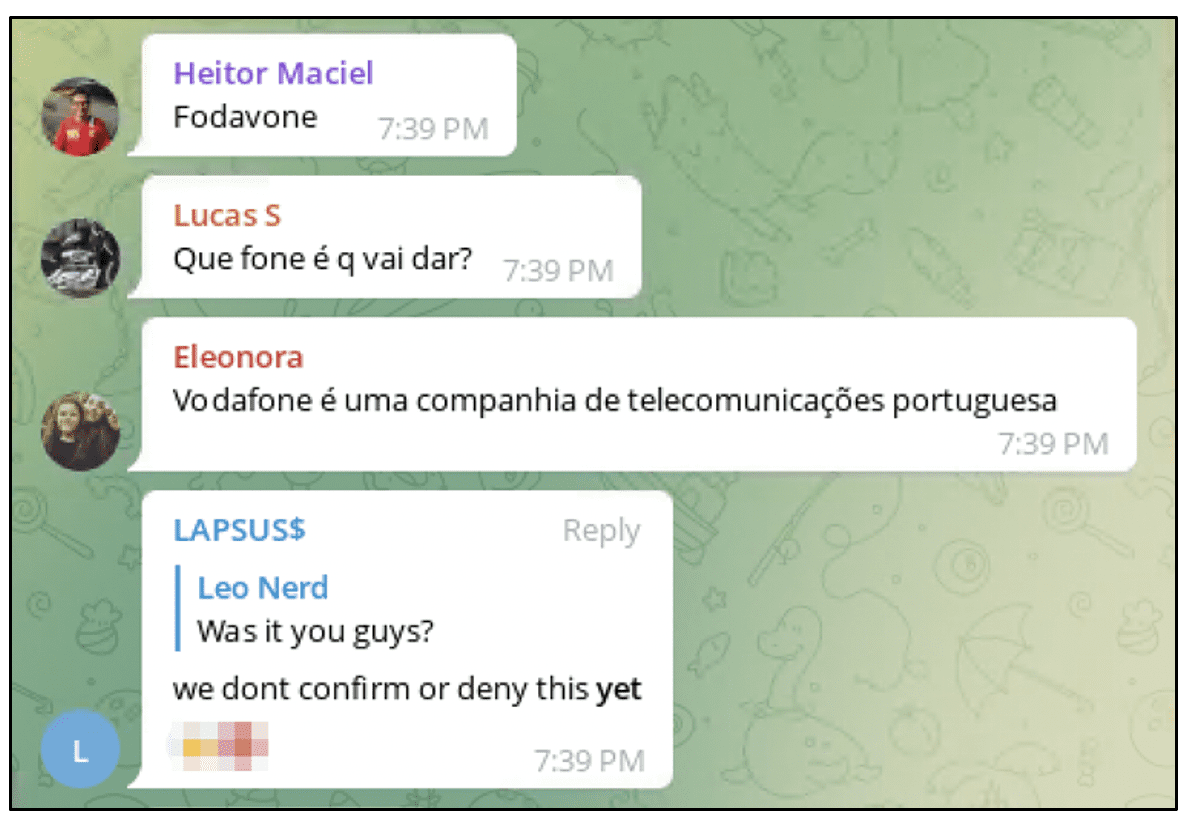
On the LAPSUS$ Telegram channel, the group posted Vodafone with the eyes emoji without directly claiming credit for the attack. When someone directly asked if they were responsible for the Vodafone outage affecting millions of mobile phone subscribers, they stated:
“we don’t confirm or deny this yet.”
LAPSUS$’s Flurry of Activity Since December 2021
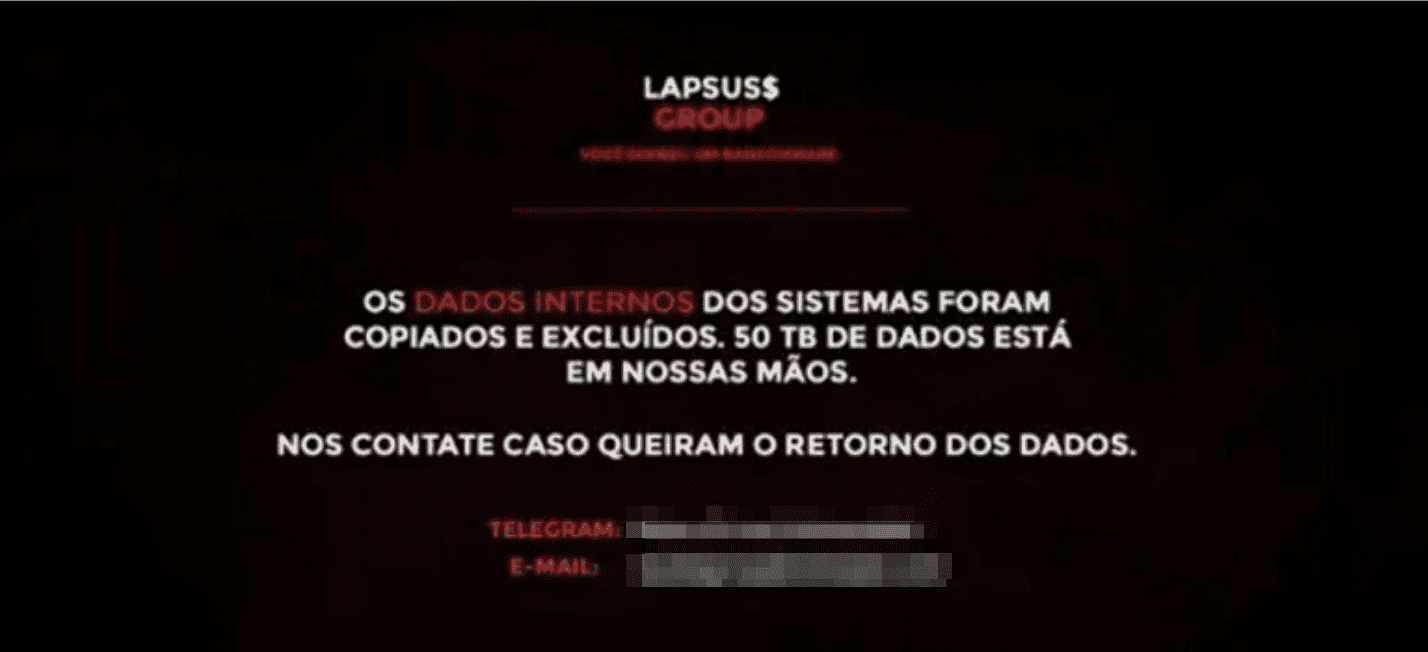
DarkOwl analysts began closely following LAPSUS$ across the darknet, deep web, and adjunct communication platforms since they claimed responsibility for a major cyberattack against the Brazilian Ministry of Health in mid-December. The cyberattack, allegedly “ransomware in nature” compromised Brazil’s Ministry of Health COVID vaccination records database, deleting the entire database contents, and defacing its website with the following message:
[TRANSLATED]
“The internal data of the systems were copied and deleted. 50 Tb of data is in our hands. Contact us if you want the data back”
The Brazilian government acknowledged their web services were offline and inaccessible to users for a short period of time without directly admitting it was LAPSUS$ who carried out the attack. The attack was like other ransomware/extortion-based attacks in the reported deletion of data; however, there was never a monetary ransom demand stated nor evidence of the group possessing the data or sharing compromised records on the darknet – despite cheers from their online supporters to release information on President Bolsarno’s vaccination status.
The group posted a statement on Telegram indicating that they had gained access to the Ministry of Health’s Amazon Web Services (AWS) and claimed they did not want to post evidence of their access because they still had access to the system despite the Ministry of Health restoring their services.
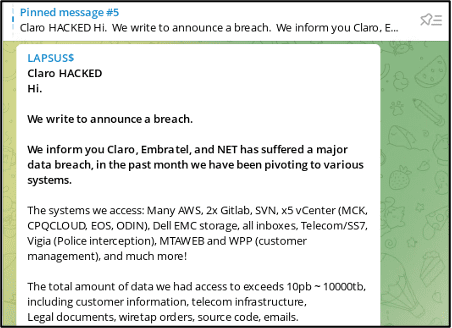
On Christmas Eve, the LAPSUS$ group attacked Claro and Embratel Telecommunications companies in Brazil reportedly stole over 10 PB (10,000 TB) of sensitive corporate information and SIM details for Claro customers across mass data storage systems such as: AWS, 2x Gitlab, SVN, x5 vCenter (MCK, CPQCLOUD, EOS, ODIN), Dell EMC storage, and Telecom/SS7.
The group shared screenshots detailing their level of access to the Claro network infrastructure and data on the dark web. We are still investigating how the group originally gained access to Embratel and Claro’s infrastructure. The group emphasized the extent of their access in the companies, highlighting they had access to over 1,500 virtual machines in use by Embratel and 23 unique hosts (IP addresses). From the screenshots, DarkOwl confirmed they used Windows Remote Desktop application to connect to many of the compromised computers within the Claro Network on their web browser. The screenshots included network management utilities for the network and their SIM network.
They also shared screenshots from a Powerpoint presentation they found on Claro’s network that detailed how law enforcement intercepts phone calls, SMS messages, and Claro customer network activity.
(Note: the images below have been blurred intentionally so as not to reveal PII)
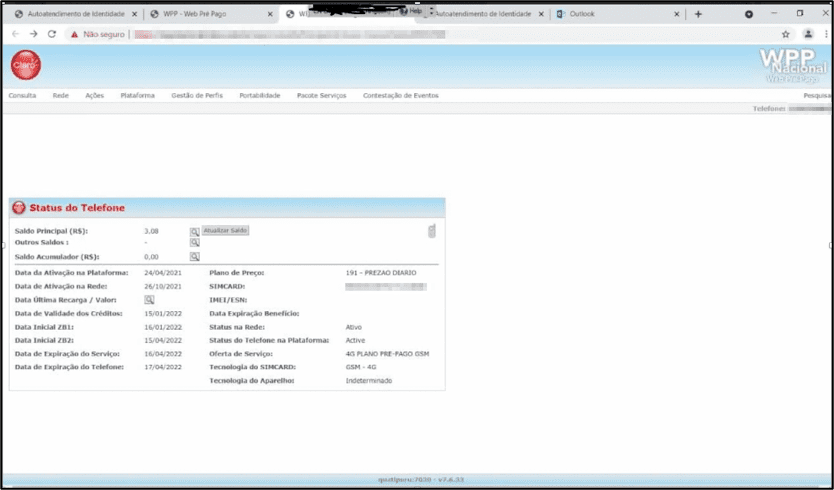
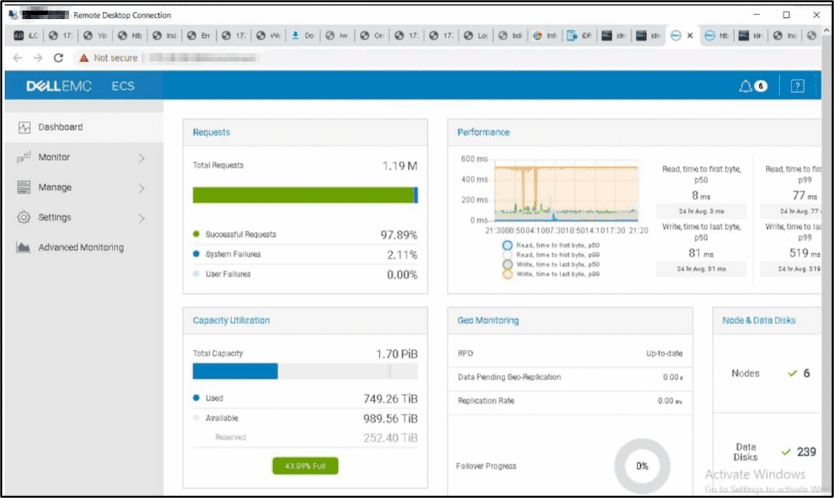
It is unclear from the screenshots shared whether members of the LAPSUS$ group used their local machines or a virtual environment to carry out the attacks. Nevertheless, the desktop of the browser screenshot suggests the OS was Windows and the temperature was 4 degrees Celsius at 21:56 on December 25, 2021.
Applying some simple OSINT analysis using historical weather databases, we discovered São Paulo, Brazil did not have weather conditions at that date/timestamp, but London, United Kingdom experienced similar weather patterns. This either means that the LAPSUS$ Group includes members from around the world or their computing environments are set to the UK/GMT time zone.
Regardless of their physical location, the LAPSUS$ group has preference for attacking Portuguese-speaking organizations on both the South American and European continents. Representatives of the group speak English on their Telegram channel.
In early January, the group conducted similar defacements to the Ministry of Health in Brazil for Impresa, a major media outlet, parent to SIC and Expresso in Portugal. The group’s access to Expresso’s direct digital resources was extensive. During the attack LAPSUS$ members sent phishing SMS texts to Expresso’s subscribers, posted tweets from the news media’s verified Twitter account, and defaced its Twitter account, pasting to the top of the page the phrase:
“Lapsus$ is officially the new president of Portugal.” (Source)
Information security researchers have noted that the text on the defacement is ‘Brazilian’ Portuguese – instead of Portuguese from the European continent – increasingly the likelihood the threat actors are based out of Brazil. LAPSUS$ claimed in their defacement they had access to their cloud services at AWS.
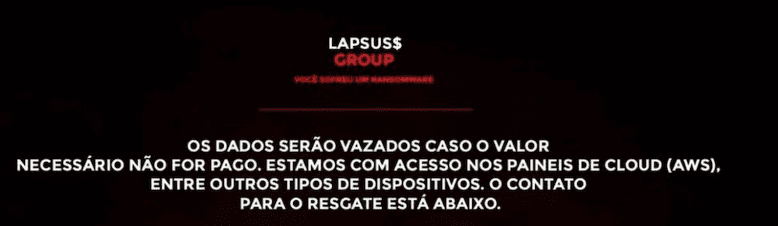
[TRANSLATED]
The data will be leaked if the necessary amount is not paid. We have access to the ‘cloud’ panels (AWS). Among other types of devices, the contact for the ransom is below.
Note from our analysts: When we think of “exposed credentials” we generally think of e-mail or server authentication data, e.g. username, e-mail address and/or password. The darknet is also haven for other types of critical corporate data credentials, including developer AWS cloud account identifiers, such as: Keys and Secrets for S3 buckets and web services.
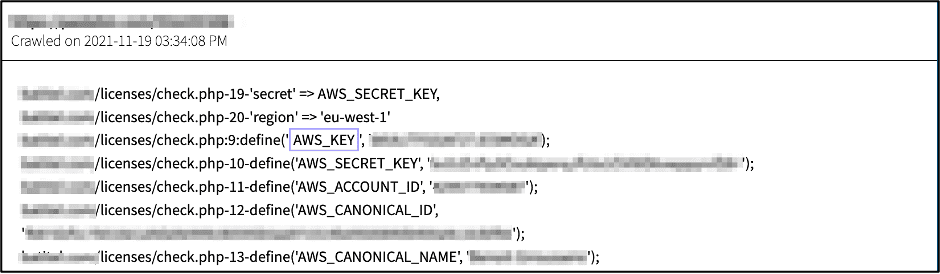
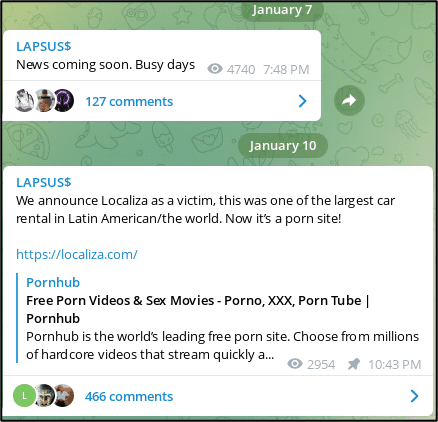
Barely a week after the attacks, LAPSUS$ announced on their Telegram channel their next victim had been Localiza Rent a Car SA. The attack appeared to be a DNS spoofing attack on their website, redirecting Localiza website visitors to a porn site instead.
According to open-source reporting, the company reported a “partial interruption” and there was no evidence any customer data or sensitive information was stolen. No ransom demand was made either.
Less than two weeks later, LAPSUS$ shared a Twitter post from Portugal-based Francisco Martins speaking of how the Grupo Cofina attack was against the company and not an attack on press freedom and another post referencing a popular Cofina journalist. LAPSUS$ never officially claimed responsibility for attacking the Portuguese media outlet that impacted multiple digital content platforms including: Correio da Manhã (Morning Mail), Sábado (Saturday) magazine, Jornal de Negócios (Business Journal), Diário desportivo Record and CMTV. (Source)
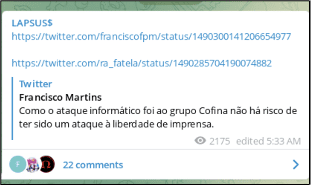
Technical specifics of the attack against Cofina are still murky, with little to no information coming directly from LAPSUS$. Security researchers note similarities in the “no ransom demand” style of ransomware, e.g. file corruption and extortion carried out by LAPSUS$, and the fact the group hit other major Portugal-based media companies merely weeks before.
Portugal’s Judicial Police (PJ) are actively investigating the incident and it is not proven LAPSUS$ carried out the attack. The group could be posting to their Telegram to infer their connection without proof and gain criminal credibility.
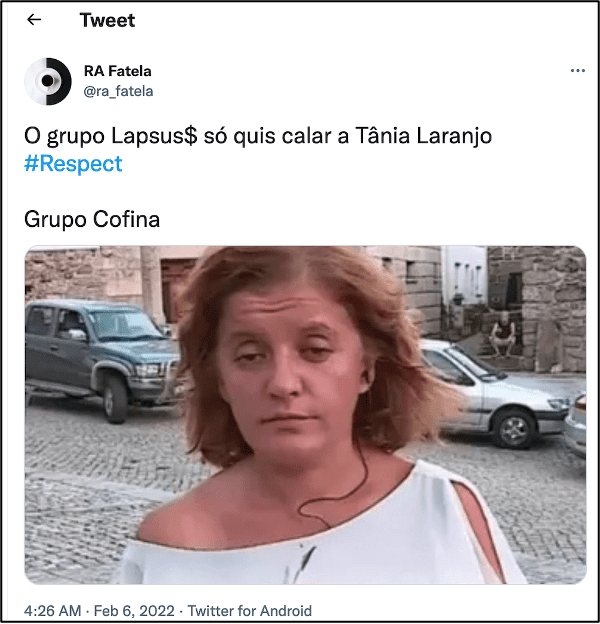
[TRANSLATED]
“The Lapsus group just wanted to shut up Tânia Laranjo #Respect”
Additional Historical Evidence Surfaces
Using DarkOwl Vision, DarkOwl detected previous activity from the LAPSUS$ on the deep web and darknet including posts in July 2021 on RaidForums and other darknet forums claiming they had compromised networks and stolen data for the FIFA soccer games from EA. On those posts, they shared their PGP Key, signed the posts “LAPSUS$”, and logged into the forums using the pseudonym, 4c3.
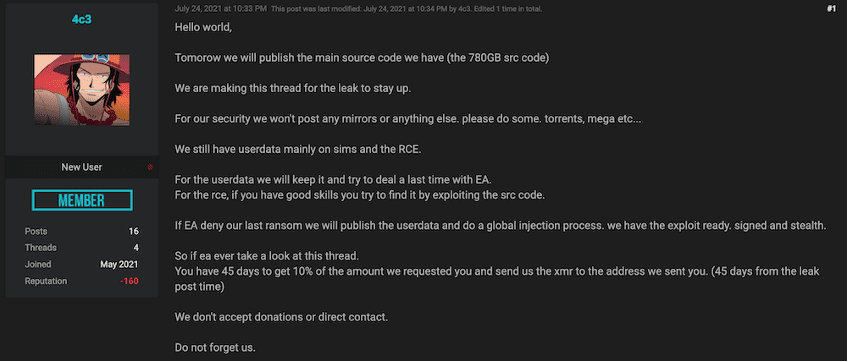
Posts from the group on another darknet forum last summer were shared in the English language detailing to EA that they found a Remote Code Execution (RCE) vulnerability in the “frostbite engine” and they had no intention to target console users. This is a typical approach to trying to extort a company for specific vulnerability, e.g. “malicious bug bounty.”
In August 2021, the LAPSUS$ group ended up leaking the EA/FIFA data they had stolen after their attempt at extorting the company for $28 Million USD had failed to materialize. (Source: Raid Forums)
Users on RaidForums indicated the 4c3 moniker for LAPSUS$ on the forum was also tied to a CryptBB staff member known as Cyberjagu who was also trying to sell the EA source code. 4c3 denied any connection. According to open-source reporting, analysts with Blackberry’s Research and Intelligence Division confirmed Cyberjagu is some sort of “intermediary” for the cybercriminal group behind the EA/FIFA attack.
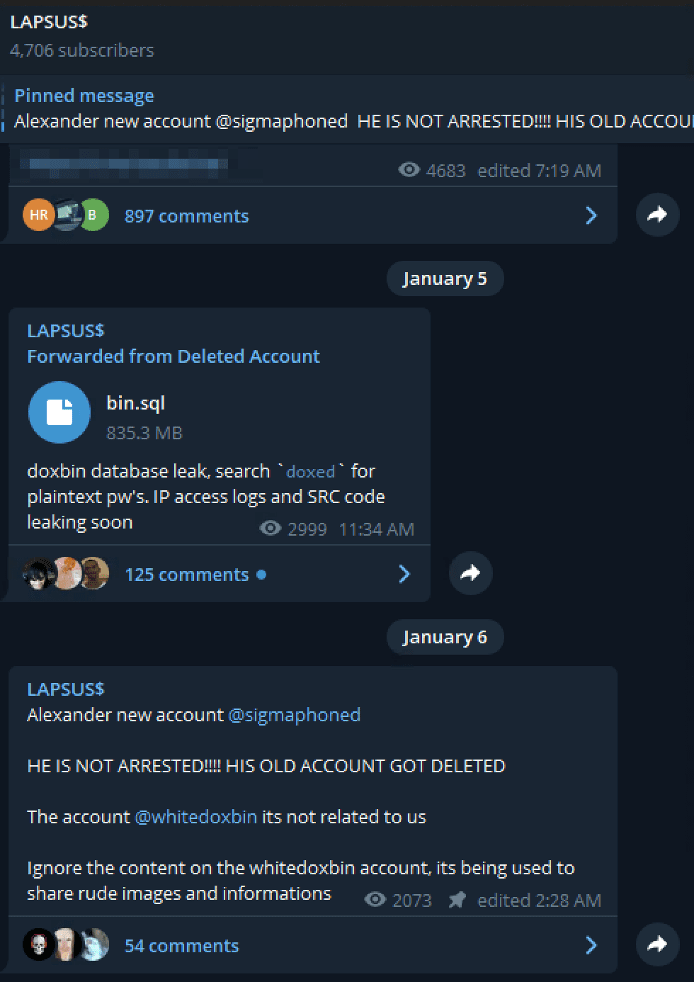
Drama Between Doxbin & LAPSUS$
In early January, the “dox” of a potential LAPSUS$ member surfaced on the controversial deep web paste site known as “Doxbin” and has received over 7,000 views as of time of writing. The dox – intentionally not included here – suggested the LAPSUS$ member was actually a 16-year-old teenager residing in Kidlington, UK and regularly used the pseudonym(s) SigmA, wh1te, and Breachbase in the underground. The dox may have been leaked in retaliation after LAPSUS$ shared hacked internal docs from Doxbin on their Telegram channel on the 5th of January.
According to the LAPSUS$ Telegram channel and the LAPSUS$ Twitter, SigmA (@sigmaphoned/Alexander) might be a “high-ranking” member of the LAPSUS$ group. Since late January, many of the users on Telegram have been trying to reach SigmA, but he’s not responding to messages. The January dox suggested might be in the process of relocating to Spain with his family. (Source: DarkOwl Vision)

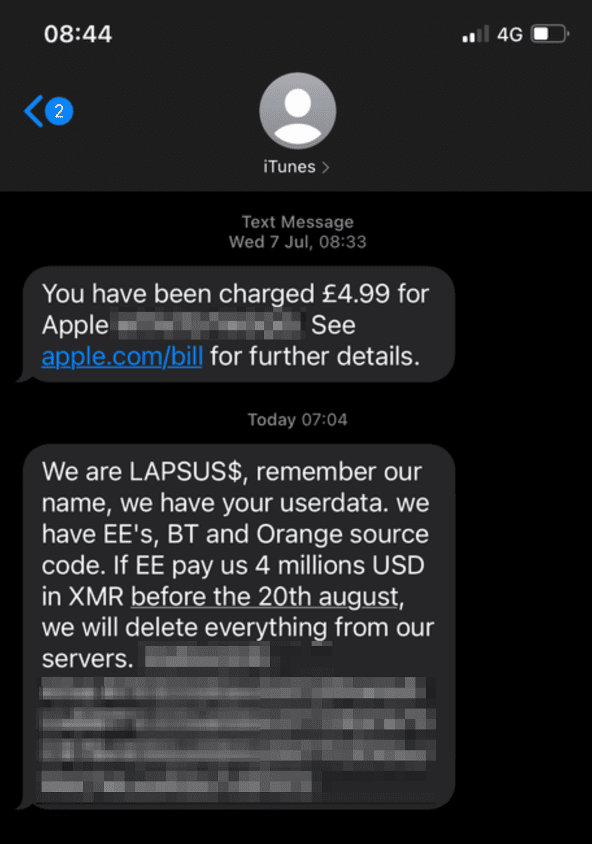
A Preference for Monero Leads to a Telecommunications Phishing Campaign
Last summer, LAPSUS$ also posted a Monero address on a deep web forum discovered by DarkOwl Vision. The same address was also included in numerous scam/phishing reports from users with British mobile telecom providers, EE and Orange. In July, users from EE reported receiving an ominous message from LAPSUS$ demanding EE pay them “4 millions USD” after making normal iTunes purchases. Perplexing to users, the texts arrived from historical “iTunes messaging” phone numbers.
Curious about something you’ve read? Interested to learn more? Contact us to learn how darknet data applies to your use case
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















