Darknet Threat To IoT Realized with Recent CCTV Attack on Prison Security System
DarkOwl’s unparalleled reach into the Darknet Illuminates Threat To IoT as Realized with Recent CCTV Attack on Prison Security System.
In recent years, the cybersecurity industry has repeatedly warned of an increase threat against Internet of Things (IoT) devices. With Ring doorbells, smart refrigerators, IP-enabled cameras and baby monitors, and wi-fi enabled programmable thermostats, the modern western home is a hacker’s playground with multiple attack vectors to choose from. Cybercriminals and hacktivists readily seize upon more lucrative and scalable victims, with cloud-based IoT servers regularly targeted and databases of IoT data exposed – like that of enterprise security camera system provider Verkada, which had 150,000 systems compromised back in the spring of this year during #OperationPanopticon.
Iranian-based cyber hacktivists, known as Edalat-e Ali, or “Ali’s Justice” elevated such vulnerabilities last month, compromising an Iranian prison system’s closed-circuit television (CCTV) to expose widespread abuse and inhumane prison conditions.
DarkOwl has also discovered that the tools to carry out such IoT exploitation campaigns are readily available for sale on the darknet.

Figure 1: Camera in Tesla Factory Compromised in #OperationPanopticon
Background: The Iranian hacktivists who compromised the CCTV networks
The Edalat-e Ali hacktivist’s Telegram channel, created on August 19th, launched their attack against the Evin Prison and a photo surfaced of the prison control room with their logo on the screens in their earliest posts. They claim to have “hundreds” of gigabytes of data. In less than two weeks, the Telegram channel has amassed over 30,000 followers and includes numerous leaked videos.

Figure 2: Evin Prison Control Room with Justice Ali’s Logo on their Screens (Source)
QUICK FACTS
-
While the hackers call themselves, Edalat-e Ali, or Justice for Ali – some reports reference another Iranian hacker collective known as Tapandegan
-
Justice for Ali is a reference to the son-in-law of the Prophet Muhammad, who was an imam revered by Shia Muslims.
The description provided in their Telegram channel reads as follows:
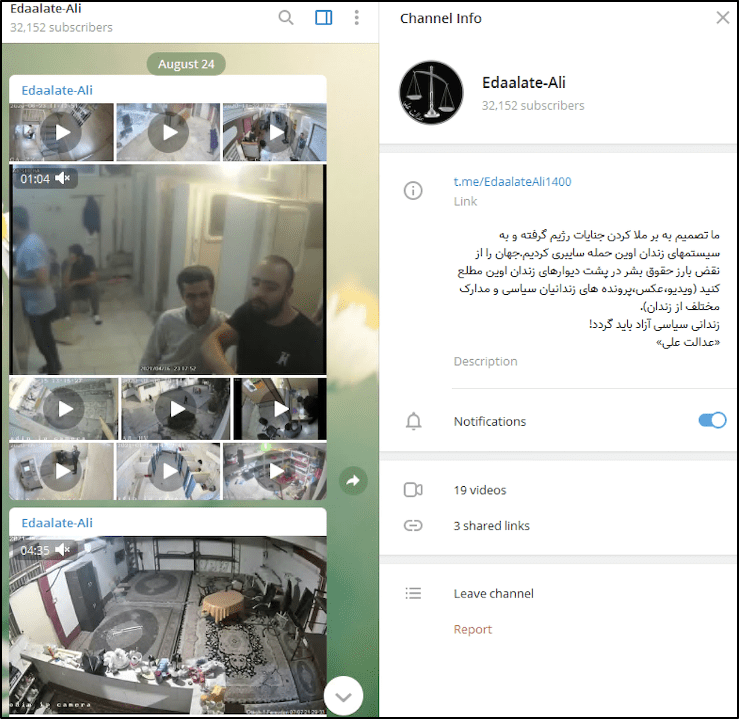
Figure 3: Telegram Channel of the Iranian team that accessed Evin Prison’s CCTV system (Source)
ما تصمیم به بر ملا کردن جنایات رژیم گرفته و به سیستمهای زندان اوین حمله سایبری کردیم.جهان را از نقض بارز حقوق بشر در پشت دیوارهای زندان اوین مطلع کنید (ویدیو،عکس،پرونده های زندانیان سیاسی و مدارک مختلف از زندان).
زندانی سیاسی آزاد باید گردد!
«عدالت علی»
[Translated to English]
We decided to resolve the regime’s crimes and attacked Evin prison systems. Inform the world of obvious human rights violations behind the walls of Evin prison (video, photo, political prisoner records and various documents from prison).
Free political prisoner must be!
“Justice Ali.”
The group also leaked documents from the prison from early 2020, where Evin Prison officials expressed concern over potential foreign military attack. This leak suggests that Edaalate-Ali possibly accessed their internal data storage systems in addition to their CCTV security footage. (Source)
Darknet Tools of the Trade to Exploit IoT
Coincidentally, on the same day that the Edalat-e Ali group appeared on Telegram, a vendor known as “thedangeroustomato” posted an offer for a 2021 CCTV exploit on the new Canadian-centric darknet marketplace called “We The North.”
The CCTV exploit is available for a mere $10.50 USD and claims it is “skid-friendly” with the exploit delivered to the victim network via a malicious PDF and two python scripts.
According to DarkOwl Vision’s database, the vendor has very few listings and not much history using that moniker across other darknet forums and marketplaces.
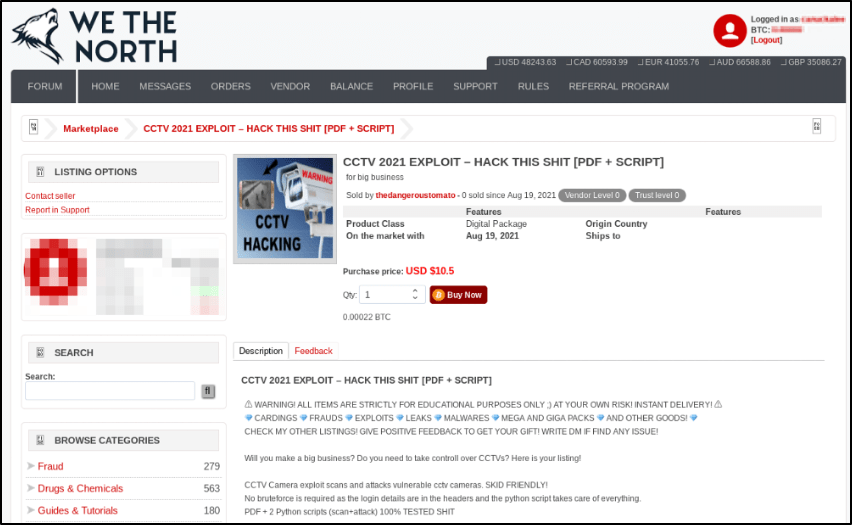
Figure 4: CCTV Exploit Listed on the Darknet Marketplace, We The North (Source: DarkOwl VIsion)
DarkOwl assesses with medium confidence that the “We The North” darknet marketplace is likely a thematic spin-off of Canadian Headquarters, another Canadian-based darknet marketplace that reportedly “exit scammed” a few weeks ago, but has recently resurfaced on a new v3 Tor onion service. The new Canadian HQ market has a new user database (e.g. old credentials do not work) with a “Coming Soon” banner on the main shop front.
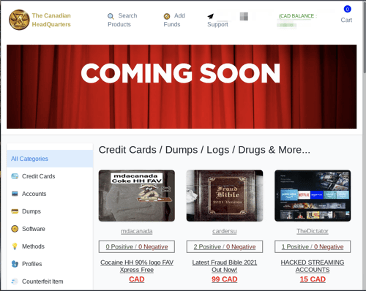
Figure 5: Canadian Headquarters New Market Relaunch Post-Exit Scam
Cyber Threat Actors Will Continue to Target CCTV Vulnerabilities
DarkOwl has not confirmed whether this specific exploit was employed against the Iranian Evin Prison hack. However, the low cost to procure, ready availability of such tools via python scripts, and flurry of international news media covering the prison CCTV hack success, suggest further attacks against similar CCTV security systems are likely if not highly encouraged by darknet cyber criminals.
For example, darknet forum and chatroom members celebrated the Verkada attack against Tesla and Cloudflare earlier this year in March, 2021. A member of the DDoSSecrets Telegram group, known for releasing geopolitically controversial content on the darknet, claimed that APT-69420, known as “Arson Cats” were responsible for the IoT device breach and shared images from the victim devices in defiance against global mass surveillance. According to one chatroom, employees at Verkada supposedly revealed the use of the Verkada’s “Super Admin Tool” was widespread and a compromised admin credential could have been the origins of the device attack.
The U.S. Justice Department indicted 21-year-old Swiss-based female hacker Till Kottman with the crimes against Verkada shortly after the leaks appeared. According to open-source reports, her group, designated APT-69420 Arson Cats, is a small collective of “primarily queer hackers, not backed by any nation state, is motivated by the desire for fun, being gay and a better world.”
Curious about something you read? Interested in learning more? Contact us to find out how darknet data applies to your use-case
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















