Darknet Threats to Cloud-based Platforms and Applications
DarkOwl has investigated threats to cloud-based platforms and applications discussed on the darknet in order to identify threat actors that are specifically targeting cloud environments. Our investigation includes a broad range of cloud environments; from compromising personal iCloud accounts to hacking large-scale infrastructures such as Microsoft Azure and Amazon Web Services (AWS).
Attack Methodology
Understanding the attack vector against cloud-based platforms is the first step to understanding where to start the darknet research. Fortunately, there are many discussions across the information security community on technical approaches to penetrating a cloud-based network for malicious intention.
As with any information network, one of the simplest ways to gain access is through targeted social engineering and/or credential compromise. Social engineering AWS/Azure network users through the use of fabricated emails, calls or social media is a proven approach to obtaining user credentials. If a user has API keys for accessing the platform, general phishing techniques can be easily employed to gain access to the user’s computer and other accounts, where the attacker could then pull the API keys for said AWS user. One hacker emphasized the importance of learning as much as you can about a target organization in social engineering, highlighting that AWS is no exception. Threat actors target information such as AWS account ids, Amazon Resource Names (ARNs), IP addresses, Role Names, and other related AWS information in order to start an attack on the network [ref].
Some hackers have successfully employed sending SMS text messages to targeted network users. The SMS includes a malicious link that “appears to be a legitimate platform notification” for password reset, and in the process, the authentication credentials are captured. Amazon includes a number of user-friendly URLs for accessing the AWS console or AWS SSO user panels. The following URLs could be adapted for targeted phishing or once the target name is identified the threat actor could attempt to brute force the legitimate links:
IAM User Sign-In Link (name): https://name.signin.aws.amazon.com/console
IAM User Sign-In Link (account id): https://accountid.signin.aws.amazon.com/console
AWS SSO Start Page: https://name.awsapps.com/start
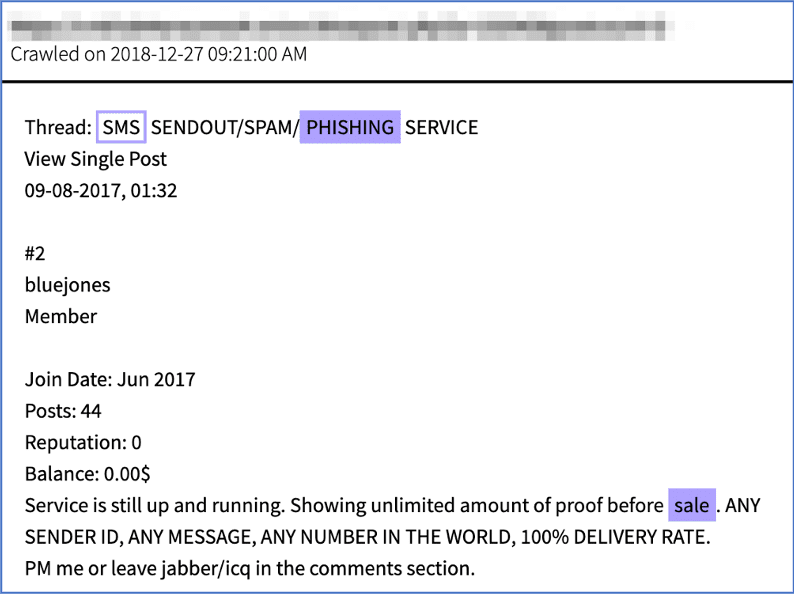
Figure 1: Source, DarkOwl Vision DocID: 9d47d601acbbb5c3e8cedc4e3f574352
Other malicious threat actors, such as the hacker behind the RouteX Malware, have successfully accessed cloud accounts through the reuse of compromised account usernames and passwords and automated “credential-stuffing.”
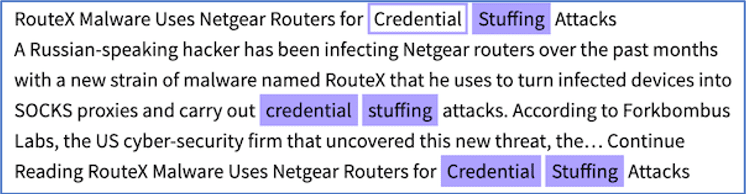
Figure 2: Source, DarkOwl Vision DocID: 73b071f96795871a39411fc9fd4ee70b
Despite repeated warnings from the infosec community, it is well known that most people still continue to reuse passwords, jeopardizing the security of their cloud-based platform accounts. (Source: a136a0a1fb206b55f06084f100ab4cbc)
Methodology – API Keys
Some cloud services, like AWS, utilize API keys to allow technical users to connect and control cloud servers without a username and password. These are random, yet unique, strings of numbers and letters that allow the user to connect to the server. API keys are an easy starting point for compromising an AWS instance and the darknet contains thousands of such mentions. Telegram group MrChecker.net sells AWS keys for as cheap as 15 USD, while other hackers post stolen keys to darknet paste sites for future use. (Source: cbe876388ac06e2caddc6c69f516a310)
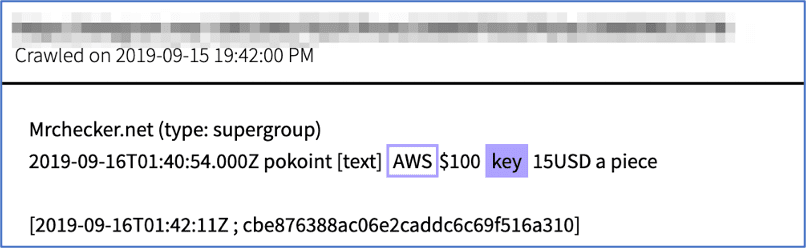
Figure 3: Source, Offer for AWS Keys for sale on Telegram Supergroup
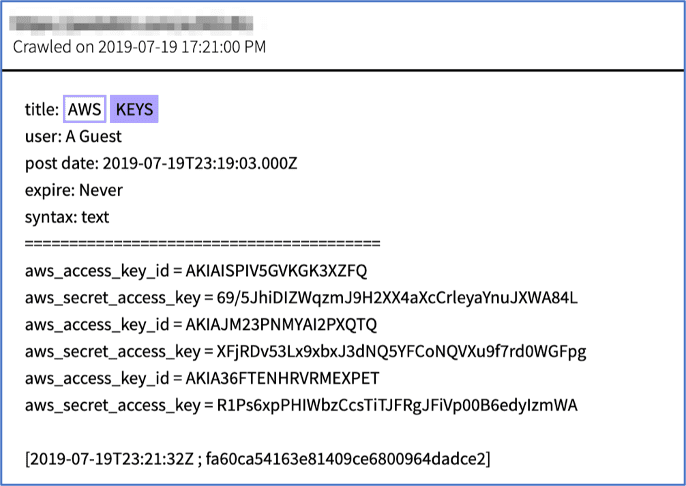
Figure 4: Source, Listing of Secret AWS Keys on Deep Web, DarkOwl Vision DocID: fa60ca54163e81409ce6800964dadce2
Some developers have accidentally committed their AWS EC2 access keys to file sharing websites like GitHub. According to open source reporting, clever threat actors are employing bots to persistently scan GitHub to find unprotected AWS access keys.
One open-sourced tool widely disclosed was the Python script TruffleHog. In recent months, GitHub user, Crypto-Breaker, committed an entire repository called “My Arsenal of AWS Security Tools” that could easily be adapted for exploitation of AWS buckets. Some AWS users have argued that Amazon now actively searches GitHub for compromised committed secret keys, shutting down the potentially compromised account and notifying the user automatically before a large AWS bill could be accumulated by a malicious threat actor.
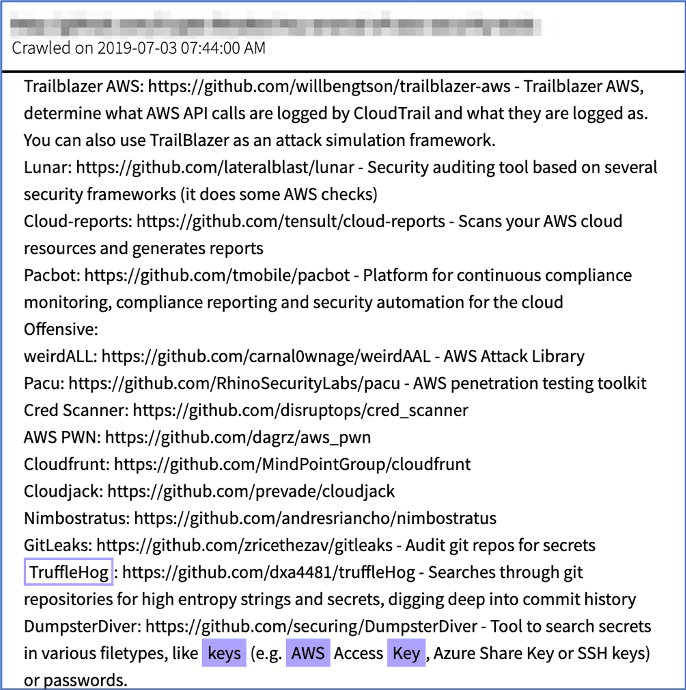
Figure 5: Source, DarkOwl Vision DocID: 7730edcec2ea299da0103e9e344bdad3
Attack Methodology – Third Party Software and Web Applications
One security researcher discussed in detail the exploitation of Server-Side Request Forgeries (SSRF) to conduct privilege escalation. A SSRF is an arbitrary web request from a compromised server to a target network. Making arbitrary requests against the target IP, e.g. replacing http(s):// with file://, can yield invaluable information like session keys and AWS container credentials. The IAM credentials can also be harvested through HTTP requests to a server’s meta_data URL and gain access to the same temporary credentials that the application uses. For example the URL:

will return a JSON object that contains an AWS access key ID, secret access key, and session token, which allows whoever made that request access to the AWS environment.
Coupling these techniques with tools like boto3, a python script for interacting with the AWS API, further malicious calls can be performed, including defacing the domain of the S3 website [source]. The Telegram channel, exploithub, discusses SSRF’s against Azure as well as other critical vulnerabilities in cloud-based platforms.

Figure 6 Example code Extracted from boto3
Attack Methodology – Malicious Injection
AWS and Azure both are vulnerable to CSV injection techniques to compromise cloud-based servers. Ready-Hacker-One includes Cross-site request forgery (CSRF) and CSV injection payloads in their “Everythingpayloads” GitHub (Source: f78043b645a4e1ce2c66e3aaf4783748) while Rhino Security details the features of the vulnerabilities in AWS and Azure in multiple open source reports. For example, the following command will download an executable from a remote server using PowerShell and then run it on the target user’s computer. The external web server is served over HTTP and automatically redirects to my malicious .exe file, because due to Azure’s validation, forward and backward slashes break this vulnerability [source].

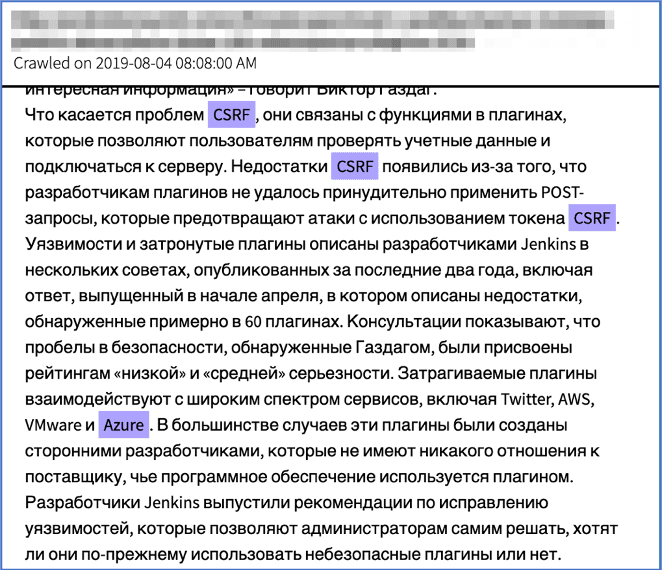
Figure 7: Source, DarkOwl Vision DocID: 40ce4e6a9e2e7ca1b5460bdca7fb9c82
Darknet forum user, Everest_RR, started a thread discussing how CSRF exploitation could produce credentials and a starting point for server-attack through over 100 Jenkins plug-ins (Figure 7). Plugin developers failed to enforce POST requests that prevent attacks using the CSRF token. These third-party plug-ins interact with most popular cloud-based architectures such as Twitter, AWS, VMware and Azure.
Azure Vulnerabilities on the Darknet
Hackers frequently discuss vulnerabilities on the darknet for various platforms. A recent Azure vulnerability, CVE-2019-1306, “Azure DevOps and Team Foundation Server Remote Code Execution Vulnerability” was explicitly posted to a hacker forum on the darknet by the user known by the moniker, PresidentXS. An attacker successfully exploiting this vulnerability allows for malicious code execution on an ADO service account.
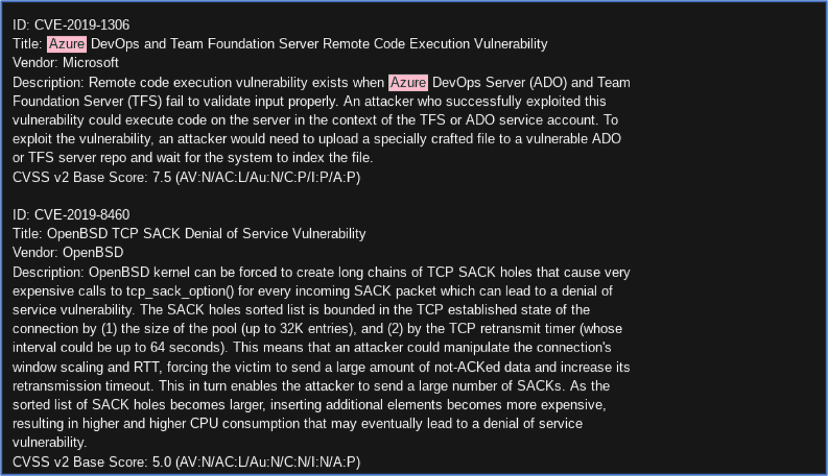
Figure 8: Source, DarkOwl Vision DocID: 2f579f9a1711a11e065983edc3641293
Earlier this year, Russian hackers on the darknet forum Dublikat discussed Azure Stack vulnerabilities documented in CVE-2019-1234 (Source: d25c98cc06300c5a8e3dcbd1a6ebf606). Such discussion threads in DarkOwl Vision are useful for reviewing comments, exploring applications, and use cases for the vulnerability specifically.
![Figure 9: Source, Captured from darknet forum: https://dublik2uqiorycsj[.]onion/threads/ujazvimosti-v-microsoft-azure-pozvoljali-zaxvatyvat-chuzhie-servery.155202](https://www.darkowl.com/wp-content/uploads/2021/12/cloud-threat-9.png)
Figure 9: Source, Captured from darknet forum: https://dublik2uqiorycsj[.]onion/threads/ujazvimosti-v-microsoft-azure-pozvoljali-zaxvatyvat-chuzhie-servery.155202
In 2018, a user on a popular darknet security forum, Torum, expressed interest in attacking an online web server located on the Azure platform. The purpose of the forum thread was less to discuss the attack vector, but more for the solicitation of assistance in the venture. The user, badass888, listed a number of “illegal sports betting” software websites that they wanted to replicate, but the threat actor needed to hack Azure’s cloud platform to gain access to the website databases and source code. It is unclear from the comments whether the hacker managed to find help, but malicious intent is present.
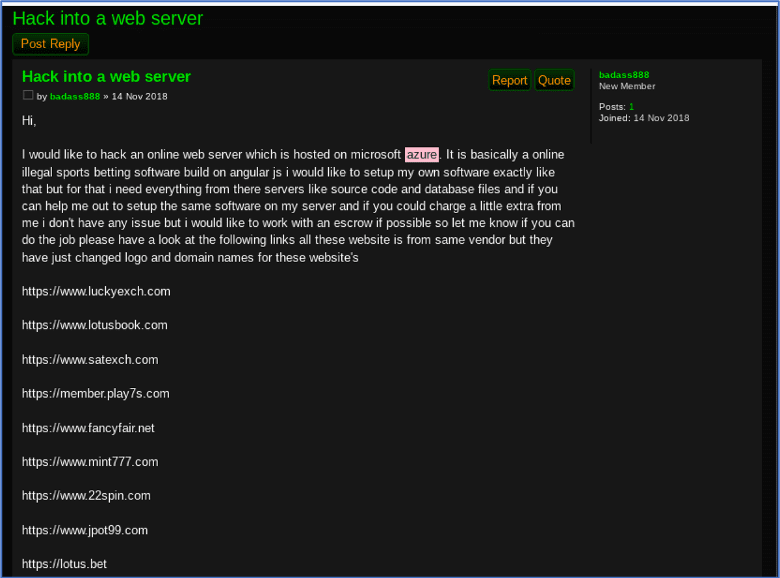
Figure 10: Source, DarkOwl Vision DocID: 5bc5355f20e410d114720b273b1cca0
Google Cloud
Google’s Cloud service “Google Drive” is also regularly targeted by threat actors on the darknet. One Russian forum user, “KeyBox,” recently offered an unlimited “Google Drive” monthly service that is cheaper than Google’s data storage plans. Their services are available on keybox.pp.ua and further discounts are on offer.
Это супер выгодно – по подписке 1000 Gb дискового пространства стоит около 1000 руб в месяц, а здесь вы платите один раз и получаете Безлимитный Google Drive.
Translation: This is super profitable – by subscribing 1000 Gb of disk space costs about 1000 rubles per month, but here you pay once and get Unlimited Google Drive.

Figure 11: Source, DarkOwl Vision DocID: 61cf92e1a44cb234e5966549eda52350
CloudFlare
Another popular topic on the darknet is how to bypass “CloudFlare” website content delivery networks.
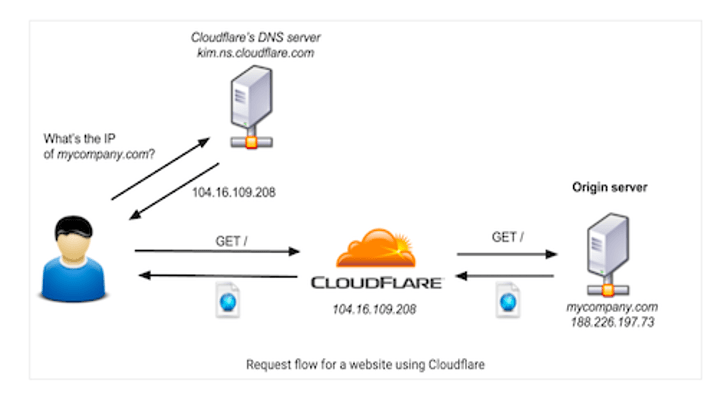
Figure 12: Source, DarkOwl Vision DocID: 56155bc8726d266a810b9fab514cfea6
Cloudflare acts as an intermediary between a client and a server, often using a reverse proxy to mirror and cache websites. Cloudflare was established to track malicious cybercriminal behavior and prevent criminals from the originating server’s content.
According to one darknet user, “CloudFlare is a big pain to us hackers.” Torigon user xData_ recently posted an informative thread on multiple CloudFlare bypass methods. The thread details tools for different platforms as well has host discovery methods, including SSL vulnerabilities and subdomains pointing back to the main host IP.
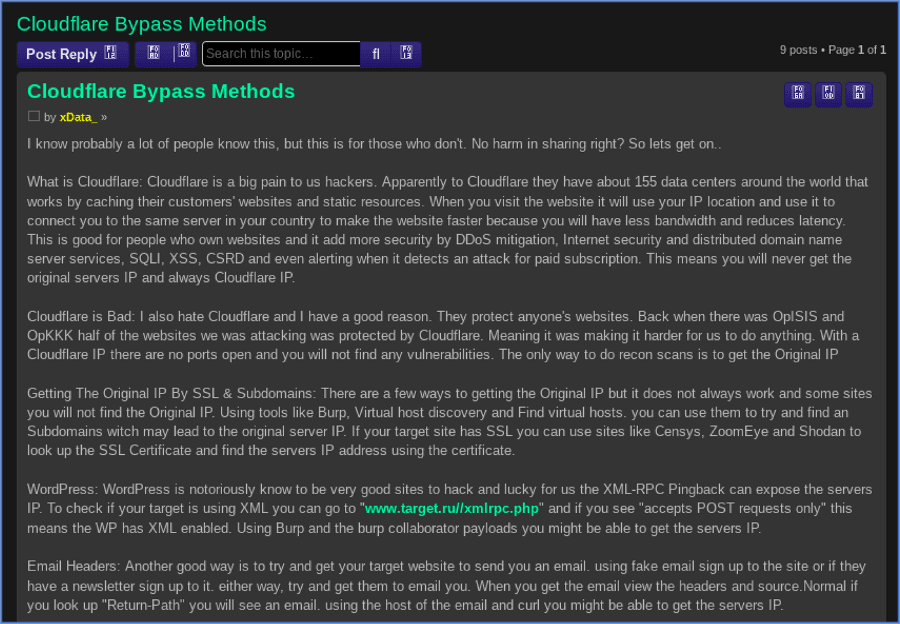
Figure 12: Source, DarkOwl Vision DocID: 56155bc8726d266a810b9fab514cfea6
There are numerous tools readily available for bypassing CloudFlare protections. Most of the software is hosted on GitHub repositories and APIs. The Censys API is regularly referenced by threat actors to expose target IP address through the SSL certificate data. For example, once a list of potential origin servers (IPv4 hosts) has been obtained, some scripts will call each one of them and compute the similarity of the response with the response sent by the original domain, using a structural similarity function designed on purpose for comparing websites similar to the Levenshtein distance calculation.
Another extremely popular resource and regularly referenced cloudflare bypass is “CloudFail” created by the hacker m0rtem. CloudFail is considered a “tactical reconnaissance tool” for target data collection. The script uses Tor to mask all requests and conducts misconfigured DNS scans with DNSDumpster.com. After the crimeflare.com database is also scanned for subdomains, the subdomains are brute forced. CloudFail is capable of attacking upwards of 2,500 subdomains at one time.
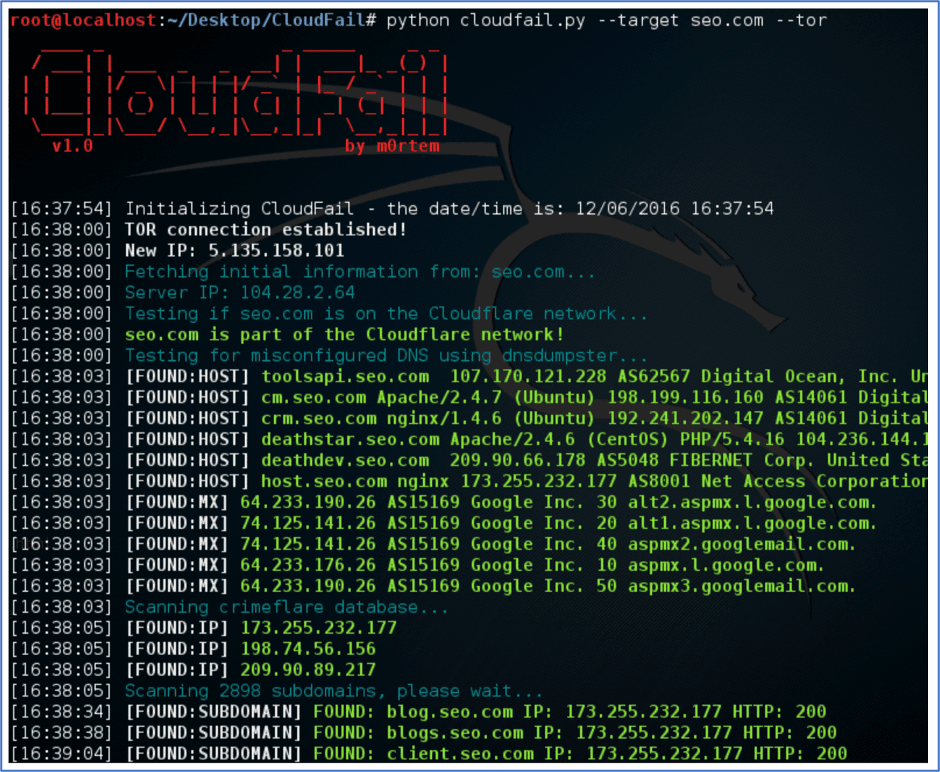
Figure 13: Source, Screen capture of Cloudfail.py (Source: github.com)
The subdomain discovery methods discussed in xData_’s thread are in full use as captured by multiple DarkOwl Vision results. There are several hundred examples like the figures below where the subdomain IP has been identified along with the CloudFlare protection flag (off or on). Another threat actor did a similar subdomain analysis of the social media platform Snapchat in late 2019. (Source: 42995a33628e79b929ee7708999f0ebc). Most results with the format: <<Subdomain IP Cloudflare>>, do not list an author; however, in November 2019, PostNL’s subdomains were exploited by a user with the moniker, ProxyManiac. This threat actor also identified some 300+ websites hosted on Bulletproof Hosting in another deep web data dump. (Source: 813aacb2d453e10ed8d0c2a2c9e63426)
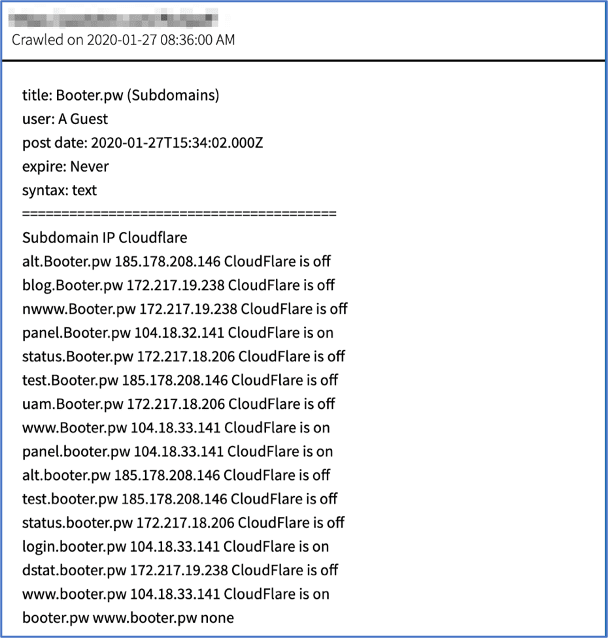
Figure 14: Source, DarkOwl Vision DocID: 4aac980c425b46fd027aad24569249bb
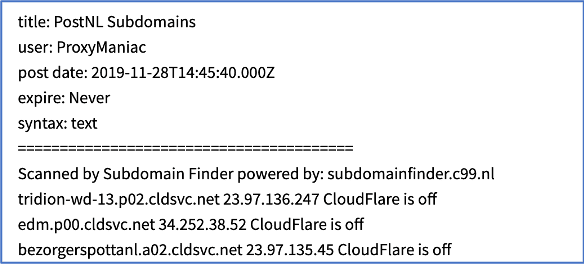
Figure 15: Source, DarkOwl Vision DocID: 2a87de7ad872ebec6b3bc422840b2a32
iCloud
Personal Apple iCloud accounts are a popular target among darknet hackers. For example, one of the most popular questions observed by DarkOwl analysts active in underground chatrooms is “How do I hack my girlfriend’s iphone?”. Torigon user, Roxy, recently posted a link to an iCloud bypass utility for accessing personal iCloud accounts. The software is advertised to work on iPhone models 5s to X. (Source: e456dc53f7840f85609783e97038156a)
![Figure 16: Source, Captured from Torum: http://torigonn6jdlsmga[.]onion/viewtopic.php?f=78&p=1859&t=503](https://www.darkowl.com/wp-content/uploads/2021/12/cloud-threat-18.png)
Figure 16: Source, Captured from Torum: http://torigonn6jdlsmga[.]onion/viewtopic.php?f=78&p=1859&t=503
Most Russian forums include service advertisements; like the August 2017 offer below by scriptseller2018. This advertisement detailed the steps for exploiting an Apple ID and iCloud account all packaged together and included in a script the hacker was selling on the forum (Source: bee9c6a7875239502c5e3115fdab144e)
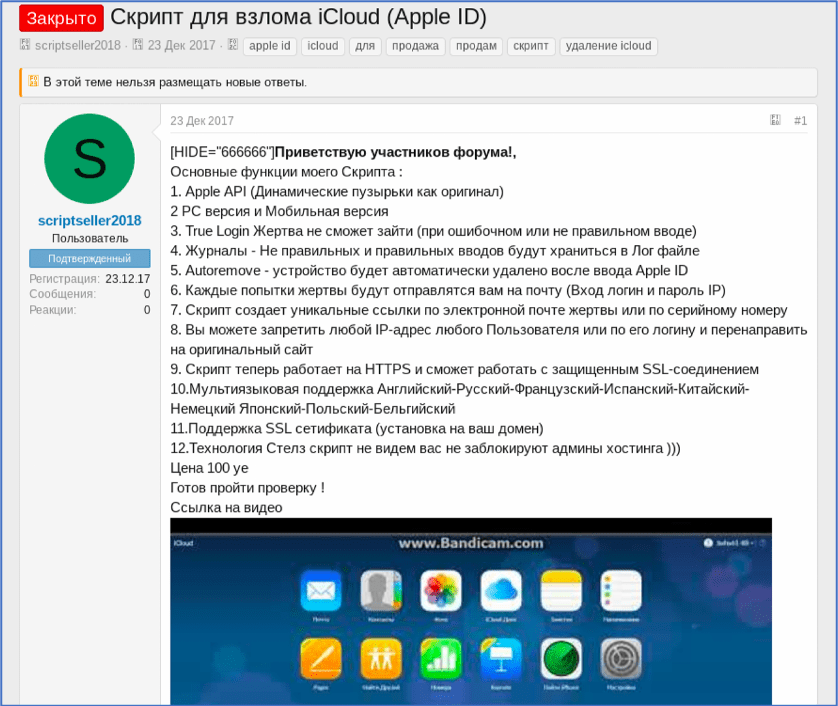
Figure 17: Source, DarkOwl Vision DocID: bee9c6a7875239502c5e3115fdab144e
Abuse of Cloud Resources
While not a direct threat to cloud subscribers, abuse of cloud resources is a concern for cloud providers, particularly for providers that offer IaaS (Infrastructure as a Service) and PaaS (Platform as a Service) models. The most prevalent way this occurs on the darknet is through the sale and usage of dedicated cloud servers, often referred to as “dedics”. There are many examples of users on the darknet that are offering these services.
One notable example is user extremalspeed, who posts advertisements for his services on Russian hacking forums such as Exploit.in and UFOLabs. Deep web forums such as Raidforums are also riddled with similar advertisements.
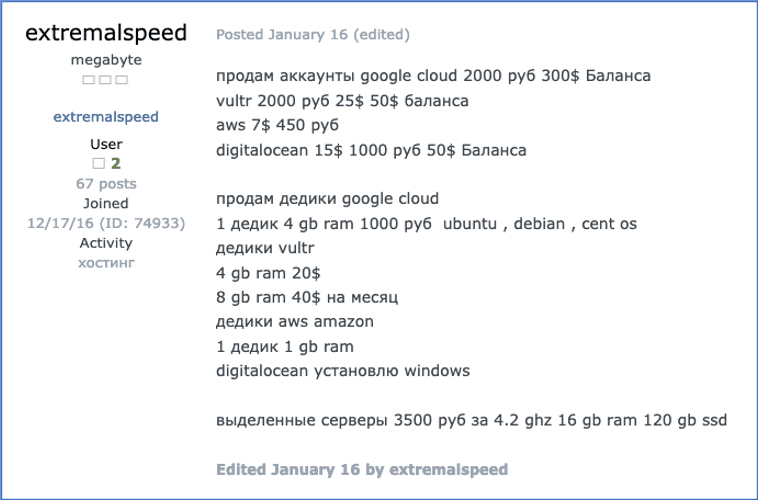
Figure 18: Source, User extremalspeed offering dedicated servers on Google Cloud, Vultr, Digital Ocean, and AWS, DarkOwl Vision Document ID: 51597bc6ec8f321cc2c9a66db8dae3aa
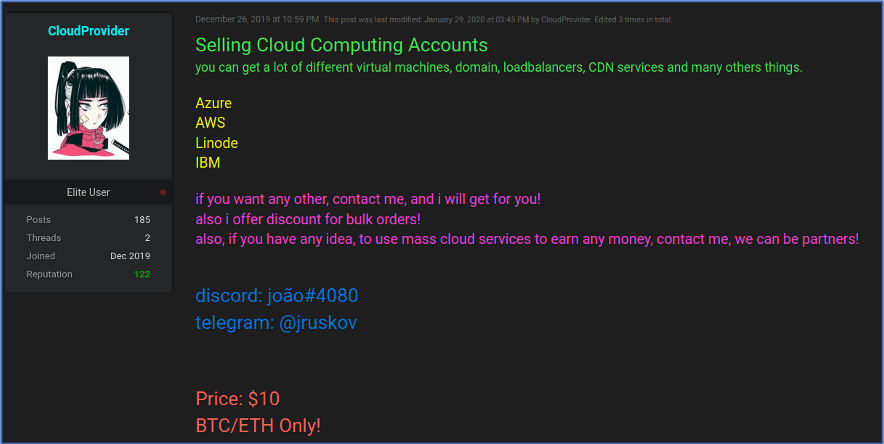
Figure 19: Source, Raidforums user CloudProvider selling cloud computing accounts from multiple sources. DarkOwl Vision DocID: b6a95f5d0283d001458c0f00ee794a08
Organizations are not the only ones taking advantage of cloud computing; from cracking passwords and encryption keys to hosting exploits and stolen data, hackers are no longer limited to using their own hardware for malicious purposes. There are many tutorials posted to the darknet that describe how to take advantage of free credits offered by cloud providers. User therigbys, of now defunct “KICKASS” forum, notes that there are specific advantages to using Alibaba cloud for spamming purposes – “You can use the credit to own servers, they have quality IP, you can use to spam with little red flags.” Cloud providers are also being used to host phishing sites; Exploit.in forum member the-one expressed plans to host Office 365 phishing pages on Azure.
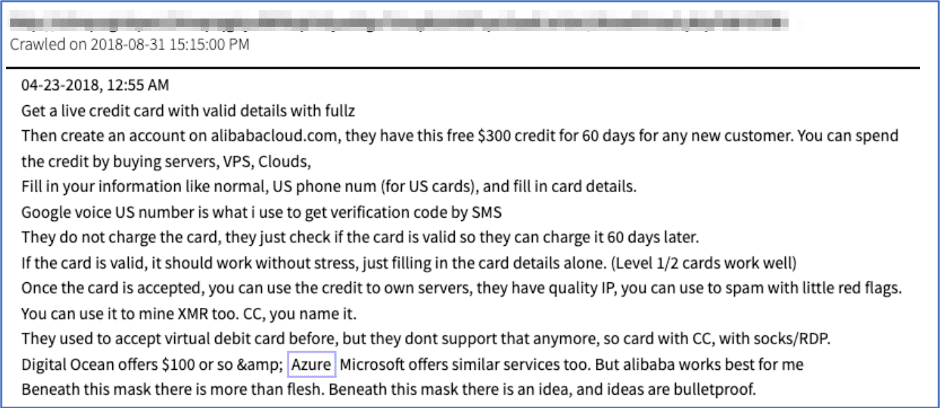
Figure 20: Source, A tutorial on how to use cloud computing credits for malicious purposes, DarkOwl Vision Document ID: a987d3f5159f5b2c38e6611e9eec1c4d
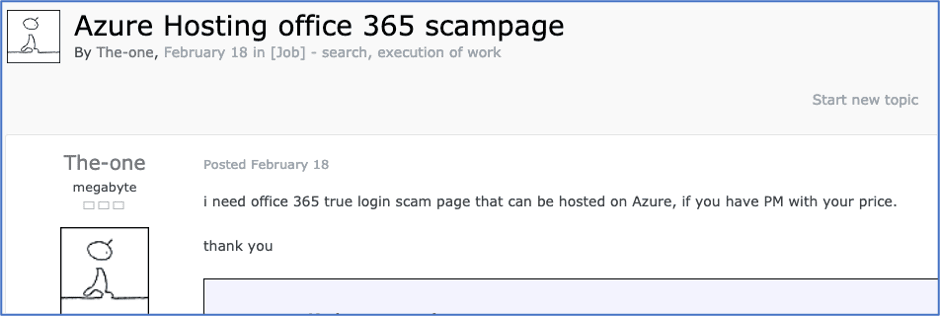
Figure 21: Source, User The-one looking to buy an office 365 phishing page that can be hosted on Azure, DarkOwl Vision DocID: b61a5a1d19ffa519b8897792a9f49011
Selling Access to Personal Cloud Services
Some hackers sell access to their personal cloud of data dumps, such as DrDastan on Raidforums. This type of service is usually advertised as a subscription service and the seller usually claims to regularly post updates with fresh data.
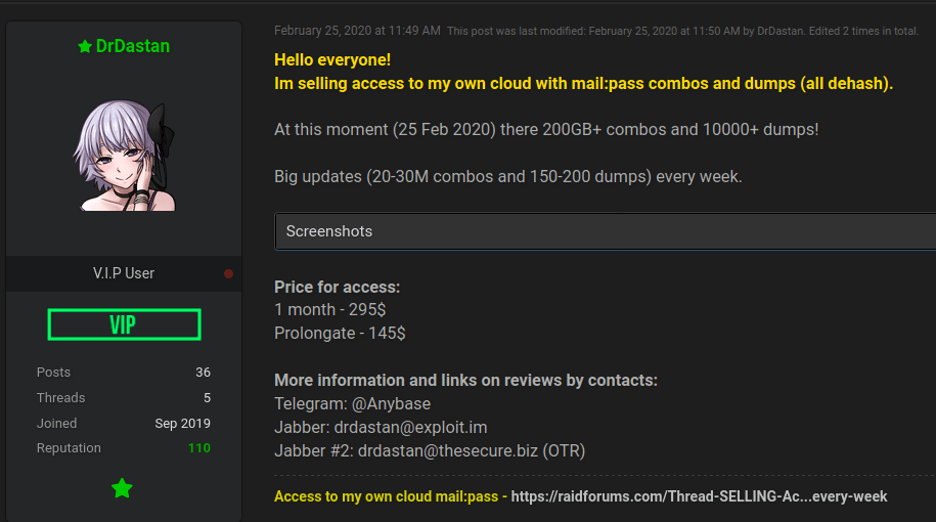
Figure 22: Source, Raidforums user selling access to their personal cloud of data dumps. DarkOwl Vision DocID: 438f8f9e5126f6aa72c42d5f440fd796
Selling Access to Compromised Servers and Accounts
In recent years, hackers have made many headlines for selling access to an organization’s compromised servers and servers hosted on the cloud are no exception. The following two examples are from hacker forum Exploit.in. In the first example, threat actor Buffer is selling access to an education institute’s platform, which he claims gets 35 million visits per day. In the second example, threat actor onfrich is selling access to Azure server panels of a hospitality company.
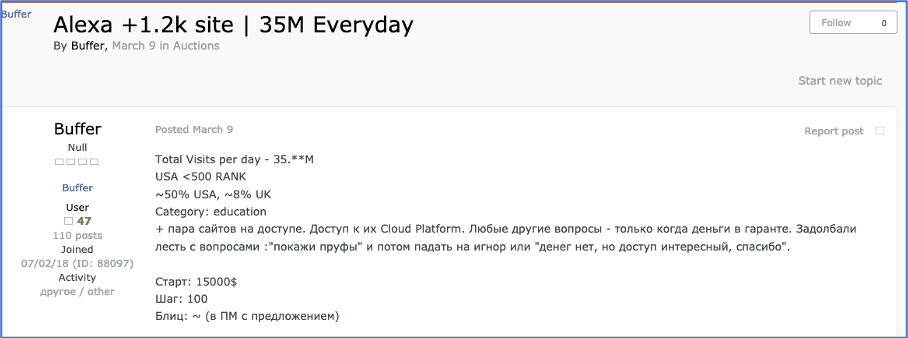
Figure 23: Source, Exploit.in user Buffer selling access to an education institute’s cloud platform, DarkOwl Vision Document ID: c5766f4e3f21384f83dfb1fa28aea8e5

Figure 24: Source, Threat Actor onfrich selling Access to Azure server panels of a hospitality company. DarkOwl Vision DocID: e7dd5705b3e45f05ae456bba9941c5c4
In 2019, a user on deep web crime forum, sinister.ly using the moniker, momxia, posted an offer for Google Accounts with $100 USD credit.
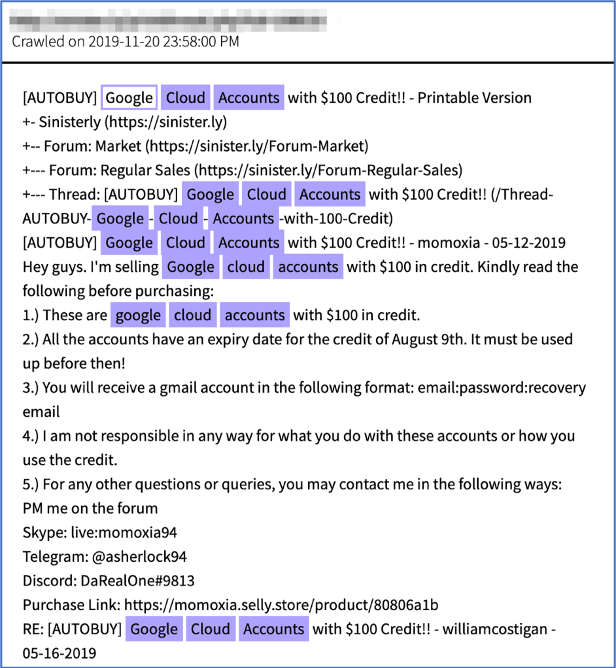
Figure 25: Source, DarkOwl Vision DocID: 8b70f34c4b2e09572bdba0bf775384b0
The advertisement included multiple methods to contact them, along with a surface web link to their online store. According to their Selly Store located on the surface web, the Google cloud accounts were available for sale at the price of $6.00 USD. As of time of writing, the seller’s website indicated they were out of stock.
![Figure 26: Source, Surface Web screen capture of the same list on momxia’s selly store. Source https://momoxia.selly[.]store/product/80806a1b](https://www.darkowl.com/wp-content/uploads/2021/12/cloud-threat-28.png)
Figure 26: Source, Surface Web screen capture of the same list on momxia’s selly store. Source https://momoxia.selly[.]store/product/80806a1b
See this research featured in the newly released IBM’ X-Force Cloud Threat Landscape Report 2020
Curious to learn more about our darknet data? Have any questions for our analysts? Contact us.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















