Darknet Whack-A-Mole – Chasing Criminal Markets
Keeping current and making sense of recent news surrounding Darknet Marketplaces is a challenge for even the most active and engaged Tor enthusiasts. In this blog, DarkOwl analysts dive into the latest dark web market exit scams, the recent, widespread law enforcement operations and their impact, and how cryptomarkets will continue to be a significant segment of darknet hidden services available to underground and would-be criminals.
Below is a timeline of the primary events leading up to, and resulting from the recent turbulence surrounding many darknet marketplaces.
April, 2019
Dream Market Announces Closure & Never Returns
In late March 2019, Dream Market, one of the oldest cryptomarkets announced that it would be ceasing its current operations on 30 April 2019. The announcement was made by the developer and admin, known as Speedsteppers. The statement also mentioned an eventual re-branding as a new Tor hidden service and address. For over a year, Dream Market had suffered from extraordinary DDoS attacks resulting in over 600+ mirror links circulating around the dark web for the marketplace.
In early April, Europol confirmed a significant multi-national darknet drug operation resulting in 61 arrests and the confiscation of 50 dark web accounts used for illegal activity. Along with the agents from the Federal Bureau of Investigation (FBI), U.S. Drug Enforcement Agency (DEA), and Canadian Police, Europol law enforcement officers executed 65 search warrants, seized almost 300 kg of drugs, 51 firearms, and over €6.2 million Euros ($6.95 million USD) of cryptocurrency, cash, and gold. Given Dream Market’s prominence in the dark web community, it is a reasonable assumption that some, if not many, of these arrests were vendors active on Dream. Although there is no mention of Dream Market in the Europol report, it’s well known the market place has been a target for law enforcement for some time. Further, the aforementioned new Dream Market onion addresses have had no activity.
Immediately after the announcement, rumors circulated across popular dark web forums about the Dream Market closure being led by law enforcement or an inside exit scam. In April, many users had issues withdrawing money from their Dream Market wallets. Some moderators scammed vendors via support ticket notification, informing the vendor that funds withdrawal can be restored only after the vendor supplies their password and last used bitcoin address.
DarkOwl covered the details of Dream’s less than graceful shutdown in “Insider Report: Darknet reacts to Dream Market announcement.”
While it’s unknown whether or not law enforcement infiltrated Dream Market’s servers directly, two independent cyber security researchers circulated detailed analysis revealing some very specific details regarding Dream Market’s admin, SpeedSteppers, de-anonymizing him as Mark DeCarlo based on the domain registrations for several surface websites, one specifically shared in 2018 with Dream users contained a link to a clearnet forum called deepwebnetwork.com. [Source1, Source2]
On a hidden service popular with “doxxers”, an anonymous hacker briefly posted an IP address for Dream Market. When accessed directly using the leaked IP address, the Dream Market login screen is available along with familiar Tor network addresses listed on the left sidebar of the page.
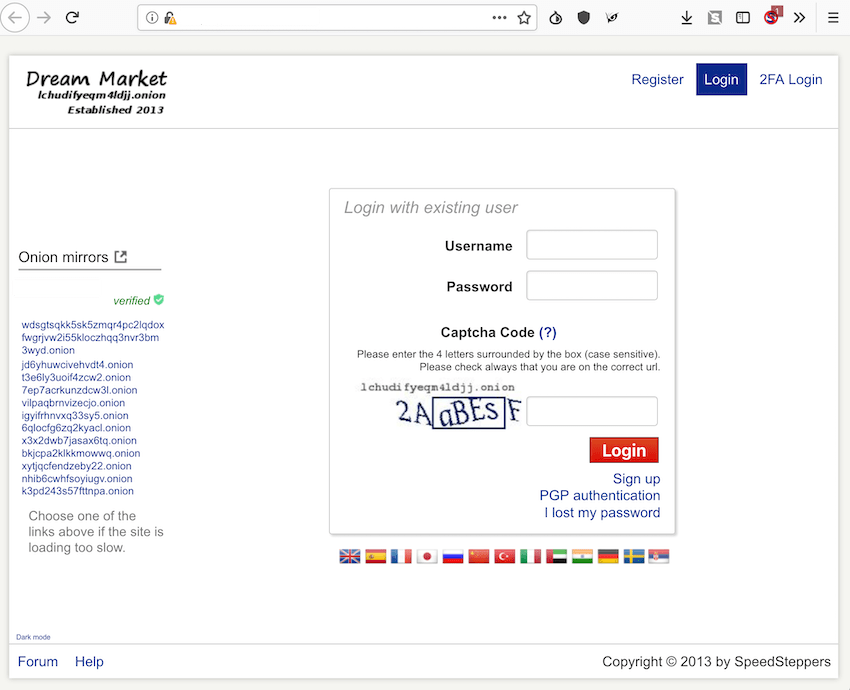
Figure 1 Direct Access to Dream Market via Leaked IP Address
Given the report on SpeedStepper was published in January, the weird behavior of moderators trying to scam vendors, along with an inactive URL for “Dream’s Partner” it would not be surprising if law enforcement infiltrated Dream Market months ago and operated it similar to the shutdowns of Alphabay and Hansa as led by the Dutch National Police in the summer of 2017.
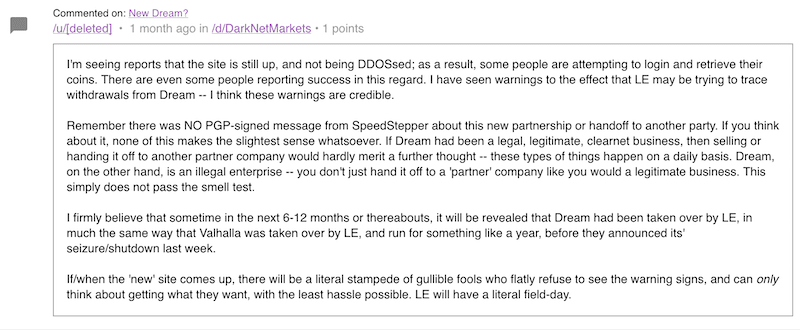
Figure 2 Source: Dread Forum on Tor (/post/52f54402d99bd51d4b74)
Wall Street Market Exit Scams Then BKA Announces Seizure
As one would expect, Wall Street Market (WSM) surged in popularity almost immediately after Dream’s announced shutdown. Most every social platform recommended vendors and potential buyers move to WSM and/or Empire to conduct their online market business.
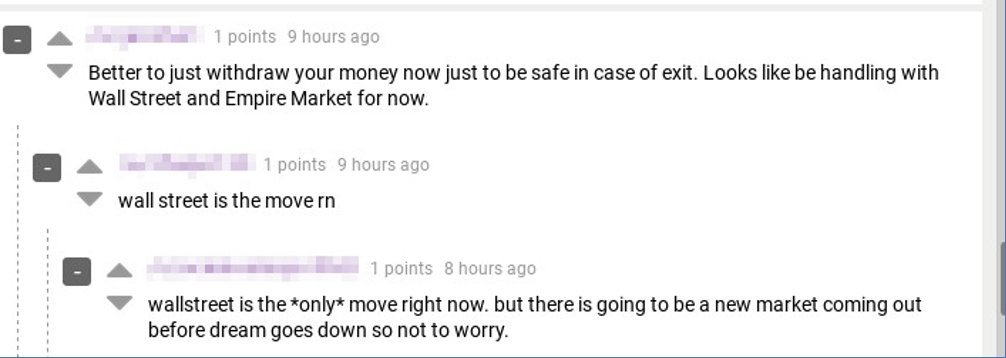
Figure 3 Dread users discuss WSM as the Dream alternative for trading.
In late April, peaking at an estimated 5,400 vendors, 1.15 million customers, and well over $10 million in cryptocurrency, WSM admins conducted a classic darknet “exit scam.” The estimated market value is totaled somewhere between $11 and $15 million USD. The three admins diverted these funds into their own crypto accounts while claiming the market was in “maintenance mode.” All the while unaware that law enforcement was secretly monitoring their accounts.
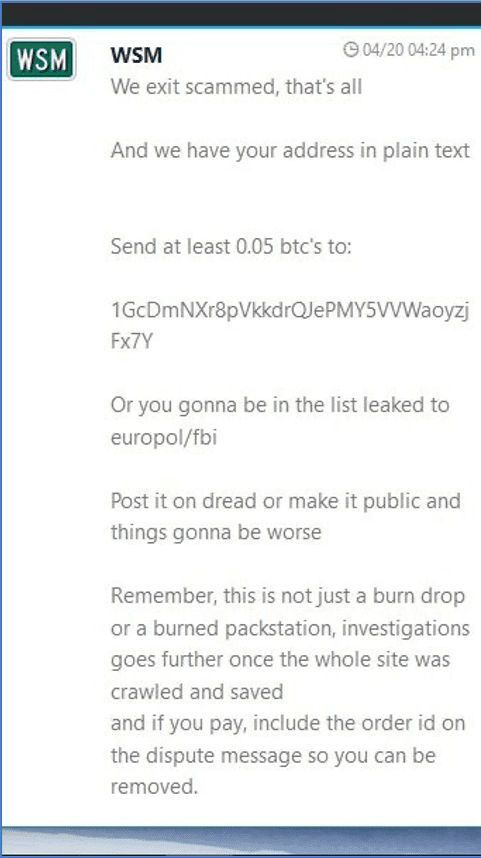
In the midst of the exit scam, one of the site’s moderators, Med3l1n, clearly angry over the exit scam, began blackmailing WSM vendors and buyers, asking for 0.05 bitcoin (at the time ~$286 USD). They threatened to disclose to law enforcement the identities of WSM vendors and buyers which made the mistake of sharing various personal details in support tickets in an unencrypted form.
It is unclear if these extortion attempts succeeded, but days later, Med3l1n also published an IP address for a server located in the Netherlands and login credentials for the WSM backend on a popular darknet forum knownas Dread. Further, they invited nefarious actors to take down the market.
The IP address is in the same network range of another IP address that leaked from the Wall Street Market backend two years ago. Although the authorities discovered the address of the server in other ways, according to public affidavits.
Within days, Med3l1n, identified as Marcos Paulo De Oliveira-Annibale, 29, of Sao Paulo, Brazil, was arrested by German authorities along with the three market administrators, all from Germany:
-
Tibo LOUSEE (coder420), 23-year-old from Kleve, Germany;
-
Jonathan KALLA (kronos), 31-year-old from Wurzburg, Germany;
-
Klaus-Martin FROST (theone), 29-year-old from Stuttgart, Germany.
All three face charges in both Germany and the United States after a series of missteps in their operational security led authorities to their IP and physical addresses. The market seizure and arrests were a culmination of a two-year investigation involving agents from the DEA, the FBI, the U.S. Internal Revenue Service, the U.S. Homeland Security Investigations, the U.S. Postal Inspection Service, the U.S. Department of Justice, the Dutch National Police (Politie), Europol, and Eurojust.
During the investigation, authorities discovered the admins also operated darknet marketplace, German Plaza Market (“GPM”), which launched sometime in early 2015 and shut down due to an “exit scam” in approximately May 2016. Agents successfully correlated wallet addresses for GPM with those of WSM in the investigation connecting the administrators.
Law enforcement obtained one of the administrator’s home IP address, correlated to and registered in the name of the suspect’s mother, through a cooperating VPN provider he used. The IP address was used to access certain administrator-only components of the WSM server infrastructure. KALLA later admitted that he was the administrator for WSM known as “Kronos.”
As a point of technical interest, the complaint filed with the US District Court in California included a footnote that the US Postal Service was responsible for the blockchain transaction analysis for FROST, and “de-mixed” the flow of transactions to ascertain that the monies from two different wallets ultimately paid FROST’s account [Source]. Researchers from Korea University published a paper in May 2018 outlined a de-mixing algorithm that could identify the relationships between the input and output addresses of the popular dark web mixing service called Helix with a 99.14% accuracy rate [Source].
Another administrator accessed the market IP address to connect to the WSM infrastructure using a device called a UMTS-stick7. This device is a USB-powered modem for remotely connecting to the internet. This UMTS-stick was registered to a suspected fictitious name, and the BKA executed multiple surveillance measures to electronically locate the specific UMTS-stick. The UMTS-stick was active at a residence of LOUSEE in Kleve, Northrhine-Westphalia (Germany), and at a local information technology company, where LOUSEE was employed as a computer programmer. LOUSEE was in possession of the UMTS-stick of interest upon arrest.
The PGP public key for “TheOne” is the same as the PGP public key for another moniker on Hansa Market, “dudebuy”. Interpol and Dutch police shutdown Hansa darknet market in July 2017, as part of Operation Bayonet. A financial transaction connected to another crypto-wallet used by FROST was linked to “dudebuy”. Investigators identified a wallet used by FROST that subsequently received Bitcoin from a wallet used by WSM for paying commissions to administrators. Records obtained from the Bitcoin Payment Processing Company revealed buyer information (connected to Hansa Market, seized in 2017) for a Bitcoin transaction as “Martin Frost,” using the email address [email protected]. A second link connecting FROST to the administration of WSM is based on additional Bitcoin tracing analysis.
May, 2019
Finnish Customs Seizes Valhalla (Silkkitie)
During the same week reports of WSM’s collapse surfaced, Europol released an official statement that Finnish customs (Tulli) in close cooperation with the French National Police (La Police Nationale Française)seized Valhalla, also known as, Silkkitie sometime earlier in the year. The report did not mention many specifics, other than Finnish federal authorities have the entire Valhalla server and its contents, along with a significant drug confiscation. DarkOwl Vision indicates the marketplace went offline sometime in early March.

The May 3rd Europol report stated:
“After the Silkkitie (Valhalla) site was shut down by the authorities, some of the Finnish narcotics traders moved their activities to other illegal trade sites in the Tor network, such as Wall Street Market”
..suggesting the potential for international law enforcement’s concerted attempts to funnel users to a targeted market for takedown.
Valhalla marketplace was one of the oldest markets on the dark web, listing over 30,000 products by some statistics. Its activity started in October 2013 as a Finnish-only site called Silkkkitie.
FBI Targets Deep Dot Web
On the 6th of May, two DeepDotWeb (DDW) administrators were arrested facing charges of kickbacks by earning millions in commission by referring users to specific darknet marketplaces. The seizure of DeepDotWeb alarmed the dark web community as it did not host any illicit content directly, but instead provided paying users with indexed and catalogued access to dark net market hidden service URLs – complete with ratings and reviews. DDW admins received money for registrations using the referral addresses hyperlinked. Authorities claim that DDW administrators made millions of dollars using this criminally innovative ‘picks and shovels’ approach to illegal online trading. Coincidently, while DDW was being shutdown, popular dark web community forum, Dread experienced heavy DDoS attacks and was unable to support logins for over a week, causing many to suspect it too had been compromised. DarkOwl analysts speculate that Dread’s DDoS was intentional to prevent vendors and buyers to coordinate on interrupted sales and illegal trading.
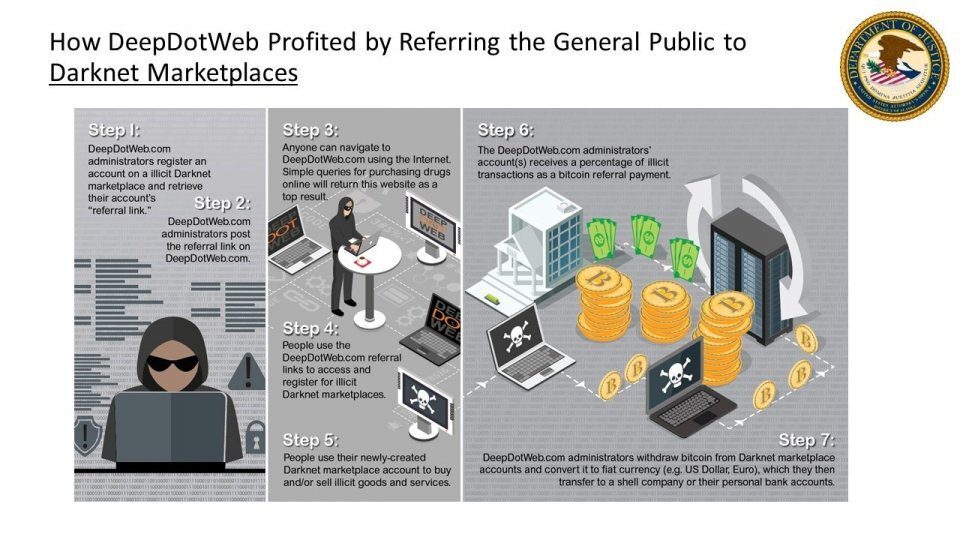
Figure 4 Source: https://www.europol.europa.eu/newsroom/news/deepdotweb-shut-down-administrators-suspected-of-receiving-millions-of-kickbacks-illegal-dark-web-proceeds
CGMC Disappears Overnight
On or about May 10th, 2019 Cannabis Growers & Merchants Co-op(CGMC), silently disappeared without notice. At first, users claimed the market had completed an exit scam as they had lost the ability to withdraw funds, contact support, and initiate the process for a refund. It was later determined that the admins, Marko and Rory, felt pressure from the WSM and DDW seizures that it was time to gracefully leave the business. On the night of the self-shutdown, admins cancelled all pending orders and returned funds to the customer, released all escrow and cash to the vendors. Days after the shutdown, a signed PGP message from Rory asked for the community’s positive vibes for their services and customers joked about seeing them stroll on the beaches of Seychelles.
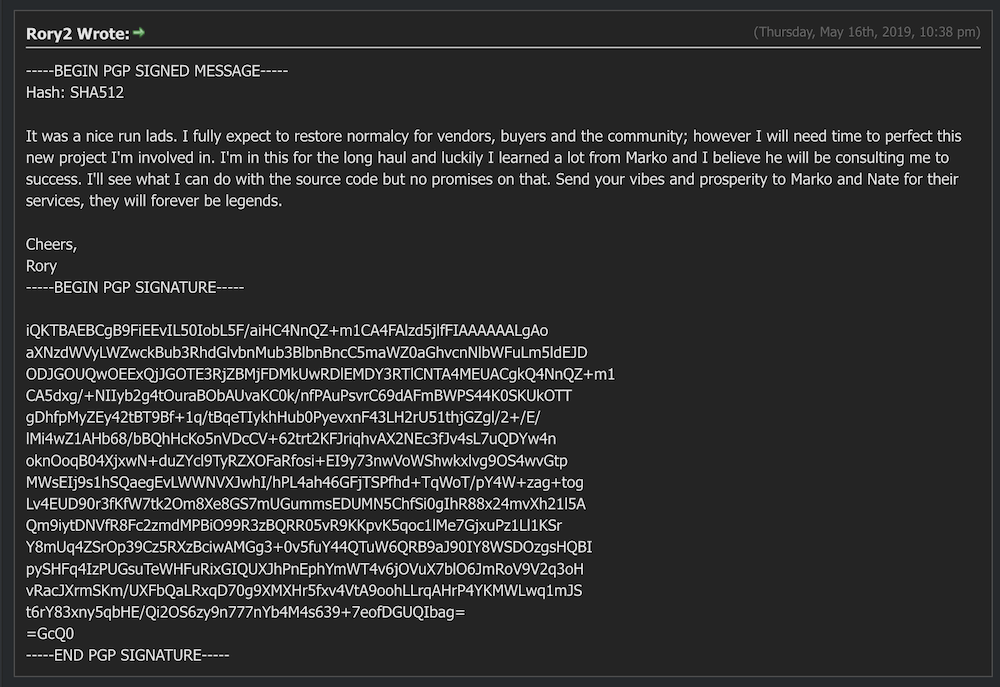
Users across other darknet communities scrambled to find their favorite vendors as this was all about the same time Dread was under DDoS and inaccessible for coordination. Many darknet vendors reposted their PGP signatures and offered to continue to serve customers without the markets, trading directly with their previous customers via encrypted communications.
One CGMC vendor shared:
The sellers are in the same situation, but I can confirm:
1. All the escrow was released and cashed (the money went to my wallet)
2. Pending orders the money was returned to the customer
3. All orders from Monday to Thursday are sent
I do not think it’s an exit scam, I think it’s a problem with the website and they’re working on fixing it.
If the market were to close Marko would have warned. Let’s wait a few days to see what happens.
If the situation is not fixed open store in another market. Please, if any of my clients reads this message, verify that the PGP is authentic.
June 2019
Libertas Moved to I2P Then Shutdown due to Inactivity
In late May, Libertas, a Monero-only marketplace, moved its hidden service marketplace from the Tor network to the peer-to-peer-based I2P network, citing “flaws in the Tor network” as justification. They also referenced an unconfirmed Tor vulnerability that international authorities have used to reveal hidden service’s real-world IP address. Libertas provided detailed instructions for its users to successfully setup I2P within Tor Browser to access this faster and hopefully more secure version of its marketplace.
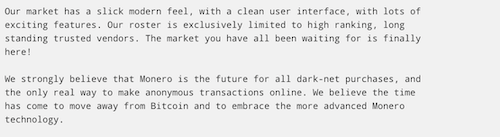
Libertas has historically been one of the most unique cryptomarkets in the dark web, being one of the first ever to only accept Monero instead of Bitcoin like other marketplaces. In their market announcement over a year ago, Libertas admins suggested that Monero was the “only real way to make anonymous transactions online” including the many ways they ensured the security of the servers supporting Libertas darknet market.

Figure 5 Libertas Original Welcome Message on their Market Forum
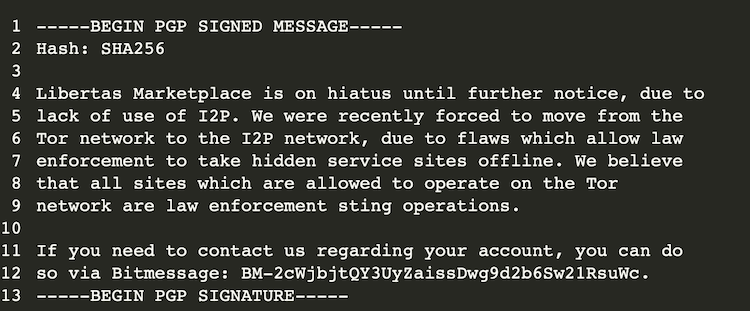
On June 19th, less than a month of operating on I2P, Libertas admins announced they were shutting down until further notice, due to the lack of use of I2P. They reaffirmed their belief that all Tor network-based hidden services which are allowed to operate are law enforcement sting operations.
Other Tor users have discussed migrating to I2P and encouraged other marketplaces to do so in forums and discussion boards, suggesting that Tor is neither safe nor robust enough from DDoS attacks to host large-scale crime-focused services. Unfortunately, the complexity of setting up I2P has discouraged its broad-based use on scales comparable to the Tor network.
Today: What Market Places Are Still Operational?
Empire Market
Despite its legacy and familiar user interface dedicated to the late Alex Cazes from AlphaBay, Empire recently has been under heavy DDoS causing it to surge in mirror link generation to mitigate. DarkOwl has knowledge of 135 unique V2 and V3 addresses for the cryptomarket, but believes that over 30% of those could be phishing addresses. In recent weeks, Empire forums have been bombarded by hundreds of complaints that account wallets have been consistently scammed, even after verifying links as legit. RapTOR directory services alleges that Empire has indeed exit scammed and any working links will lead to currency loss. The dark web community is contentious over the lack of support from staff and instability of the market.
Empire’s head moderator se7en claims most of the complaints are from customers using “phishing” market links instead of verified ones, but the tune is all too familiar to the behavior of other markets. Empire recently added two-factor authentication (2FA) as an additional security protocol, but a former Empire-mod posted a detailed paste on how easy the 2FA is bypassed, stating “the end user is always the weakest link to a system,” in a recent report by DarkNetLive.
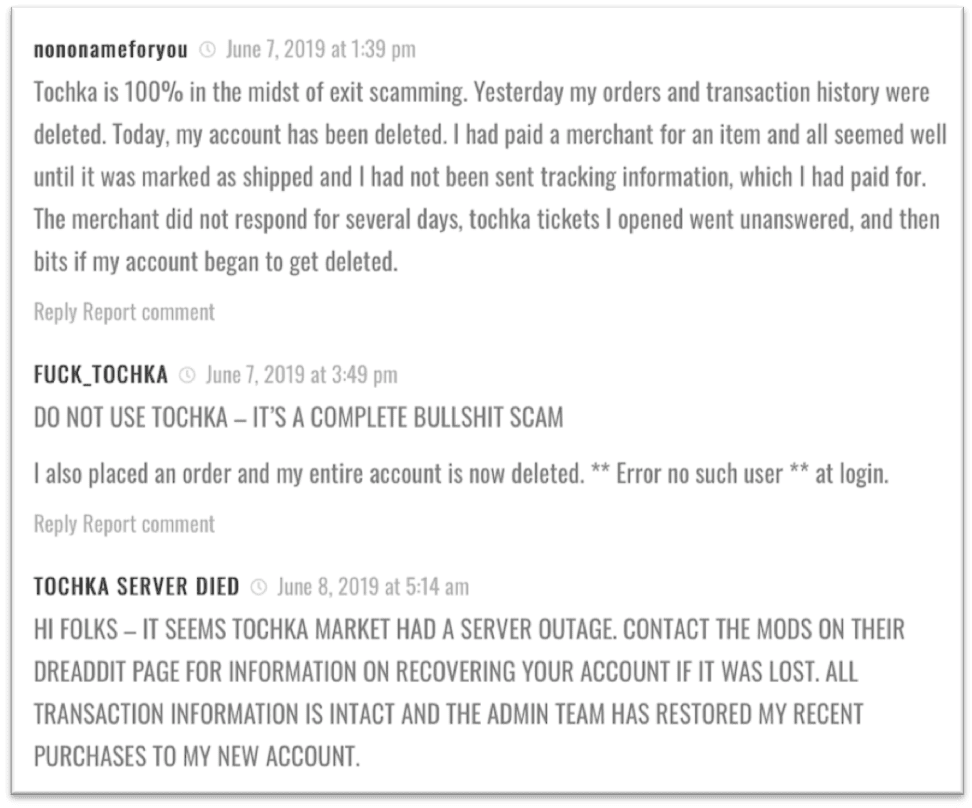
Tochka / Point
With recent market confiscations, Tochka (Point) could now be considered one of the oldest operational darknet cryptomarkets as it started in early 2015 emphasizing a “community-like” culture with classified advertisements and low vendor registration requirements.
Unfortunately, in early June, many users reported that the marketplace was a complete scam with numerous orders, wallets, and accounts deleted in recent weeks. Comments on a forum suggested that the Tochka had suffered a server crash in early June resulting in the loss of several transactional records and to contact the moderators active on Dread for assistance. Unfortunately, this week, Dread has also been under heavy DDoS and users are unable to submit complaints or receive technical support.
Other dark web markets worth mentioning
-
Genesis – Javascript required market with increasing popularity due to recent news coverage. Online and active.
-
Dark Market – Appeared in May 2019 with admins Sassy & Dark. Now accepts Monero and primarily trades in digital goods (over 1000 listings).
-
Luna – Marketplace that required wallet registration for non-vendors and offered Monero and “locktime” to secure transactions. Offline as of early June.
-
Core – Offline in mid-June after heavy DDoS attack.
-
Cryptonia – Typical dark web cryptomarket experiencing heavy DDoS in recent weeks. Admins pride themselves on their market manifesto that states their movement will never be corrupted by greed. Online and active.
-
Berlusconi – Recently added Multi-Sig wallets and states that they will no longer offer weapons & explosives by the end of June.
-
Nightmare – Experiences regular periods of heavy DDoS. Recently redesigned and returned with new UI and “dark mode.” One of the largest active markets with 65,000+ users, 3,000+ vendors and more than 50,000 listings.
-
Rapture – Rumored to have been built on the source code leaked from Trade Route. Many users thought Rapture exit scammed in late 2018, but returned recently stating they were under heavy DDoS. Offline as of time of writing.
-
Agartha – Similar design to the Agora Reloaded Market that exit scammed. Online and active with no complaints.
-
Apollon – Typical dark web cryptomarket operating since 2018. Possibly connected to former RAMP shop. Surge of users (over 40,000) due to Dream announcement.
-
Enterprise – Brand New as of June 2019. Operational but very few listings.
-
Deep Mart – Appeared in early 2019. Believed to be a scam market based on reviews.
-
The Majestic Garden – In May, TMG moved to only V3 Tor URLs and registration is closed due to surge of registrations after Dream announcement. Online and serving customers.
-
Nirvana Market – Brand new market as of June 2019.
-
Canazon – Features primarily drug vendors. Operational since 2018. Online and active.
-
Silk Road 3.1 – Operational and now accepts Monero. Online and active.
-
UnderMarket 2.0 – Market featuring counterfeiting and fraud items. Javascript required for some portions of the market. Online and operational.
-
The French Connection – One of the oldest operating markets (over 5 years). Does not ship to the US. Online and active.
-
Yellow Brick Road – Invite-only market by vendors. Online and operational.
Since 2019, DarkOwl Vision has knowledge of and successfully crawled over 3,000 dark web cryptomarket addresses — over 1800 of them in the month of June due to heavy DDoS mitigation. Libertas administrators expressed legitimate concerns about Tor’s vulnerabilities to DDoS and host IP address exposure, apparent by the crippling DDoS attacks on many of the markets and critical community forums like Dread market.
While many of the historically active markets have voluntarily closed their doors, it is evident by the introduction of multiple markets in recent months, along with the surge of customer and vendor registrations well exceeding thousands of users, that the criminal darknet market community will not be deterred by international law enforcement operations and will resort to direct encrypted communications with their suppliers if necessary.
Update (7/2/2019)
After allegedly negotiating with would-be DDoS attackers, it would appear that Dread market is back online…for now. Check back here for continued updates as our analysts uncover more information.
The market segment of the dark web is the most volatile and dynamic of all types of hidden services available. The status of any of the markets mentioned in this report can change without any notice. This report only covered the status of English-speaking marketplaces and a follow-up report covering non-English cryptomarkets, such as Russia’s MEGA, will be published in the near future. Please continue to check back for updates.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















