The Digital Economy of Disinformation: Darknet Threat to Election Security
In previously published analysis, we outlined the economies of social media and disinformation-as-a-service on the darknet, highlighting how there is now a significant ecosystem across the underground internet feeding the enterprise of mis-and disinformation for financial profit and political gain.
With the 2020 Presidential and General Election rapidly approaching, we decided to take a closer look in this report at the vulnerabilities to election security openly discussed on the darknet, including voter registration data and security risks to ballot tallying technologies, along with recommendations on the remediation both concerned individuals and state election officials can take.
Editors Note: DarkOwl is politically neutral and has no intention to further promote misinformation that the upcoming U.S. election is in jeopardy with increased use of mail-in ballots, but instead using a wide-body of intelligence, primarily captured by the company’s 24/7/365 crawls of the darknet and deep web, seeks to inform and educate the public and the information security community of information available on the darknet and our subsequent intelligence findings and recommendations.
Ballot Tallying Technology Discussions on the Darknet
PRIMER ON ELECTION TECHNOLOGIES
Election day ballot marking and tallying technology in use widely varies from state-to-state:
Optical Scan Paper Ballot Systems
These include both mark sense and digital image scanners where voters manually mark paper ballots that are hand fed into and tabulated with these scanners at the polling location or transferred to and collated at a centralized location.
Direct Recording Electronic (DRE) Systems
These use touchscreen terminals to record the votes, which are stored in the device’s internal memory and then transferred to a centralized location for tabulation. Some of these systems use internal modems for wireless data transmission. Most DREs include a paper receipt or ballot of the voter’s selection, but as many as 15 states have districts that use DREs without paper trail.
Ballot Marking Devices (BMD) and Systems
These are designed to help disabled voters who might be unable to vote using other methods. Some of these devices include a touchscreen interface with audio and other features similar to DREs.
Punch Card Voting Systems
These require the voter to punch holes in cards using a supplied punch device. Cards are then feed into a computerized vote tabulating device or counted manually in a ballot box. These systems are less common in the U.S.
TIP: You can check what voting options are available to you here: https://verifiedvoting.org/verifier/#mode/navigate/map/ppEquip/mapType/normal/year/2020DARKNET CHATTER INCLUDES DISCUSSIONS ON ELECTION TECHNOLOGY VULNERABILITIES
While a few states still rely on the manual counting of paper ballots, most lean on a number of ballot tallying technologies manufactured by three principle vendors: Election Systems and Software (ES&S), Dominion Voting, and Hart InterCivic. We have observed darknet chatter around all three of the aforementioned ballot tabulation vendors.
The security and veracity of these election technologies have been widely discussed equally at information security conferences and in underground communities of the darknet. Some technology exploitation demonstrations in the past resulted in big sweeping changes in the technologies employed by some specific states. For example, in 2017 Virginia’s Department of Elections recommended decertifying all of the state’s DRE machines after hackers at DefCon’s Voter Village that summer “pwned” them in record time exploiting numerous vulnerabilities in the systems.
Many DREs include printers that produce a paper trail for election auditing, but there are no options for comparing what is printed on the paper with the voter’s selections and what has been stored in the machine’s attached memory card that is used for the official record. Voters can increase their ownership of their vote by verifying that the information printed on a receipt or paper ballot after using the DRE is accurate before handing it over to the poll workers for official casting.
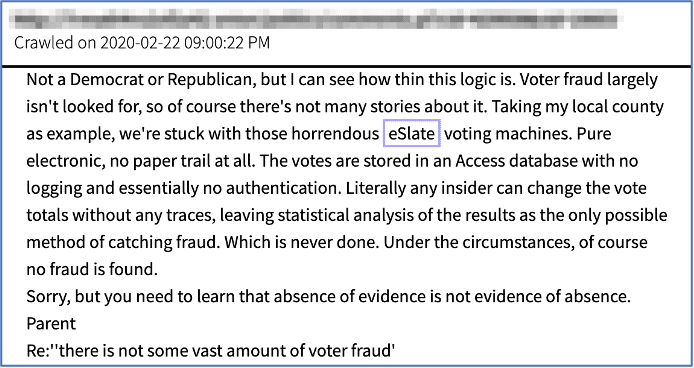
Pictured: “The absence of evidence is not evidence of absence” — A darknet user comments that fraud is completely possible with the eSlate voting machine’s dependence on Microsoft Access databases without encryption or authentication.
Texas reportedly had issues in the 2018 midterms with its Hart eSlate voting machines as voters in more than 80 counties reported seeing their choices flip to the other party’s candidate for Senate when they tried to cast a straight ticket. Hart InterCivic responded as user error and touch screen sensitivities.
A similar issue was experience in NorthHampton County, Pennsylvania when election officials had to move to hand counting paper ballots well into the morning after their ES&S’s ExpressVote XL machines were acting “finicky” and deleting candidate selections.
Hart’s eSlate machines are widely criticized in comments across anonymous discussion forums in the darknet. One anonymous user commented that fraud was completely possible with the machine’s dependence on Microsoft Access databases without encryption or authentication.
A prominent malware developer on the deep web recently suggested that his customized Remote Access Trojans (RATs) could be easily used to infect election systems as they asserted the machines were likely still vulnerable to Remote Code Execution exploits via the Windows LNK files, also known as shortcut files. However, Microsoft released patches for both Windows 7 and Windows 10 operating systems earlier this year, to which DarkOwl assesses election officials and technology vendors would very likely patch their systems accordingly well before the general election, thus the successful use of such a threat is highly improbable.
Users on a darknet hacking forum discuss that antivirus and malware detection software is not usually available on the older DRE systems such as ES&S’s DS850 8000 ballot-per-hour central counting machine. The post author stated how malware infection would require physical access to the machine or a compromised insider to load any malicious software. They also discussed adding an air-gap module to the malware via a “replacement USB” drive to the state’s elections office, including sending the USB using packaging to replicate the voting system manufacture tagged as a “firmware update.”
As reported at the end of September, someone recently stole two ES&S USB drives and a laptop belonging to an on-site employee for the company from an elections warehouse in East Falls Philadelphia. According to ES&S’s website, their ExpressVote XL machines are shipped with proprietary USB flash drives containing encrypted data signed with FIPS-compliant, security keys to prevent tampering and the possibility of overwrite or change to the system firmware, even if malware is loaded on a replacement USB sent to the officials.
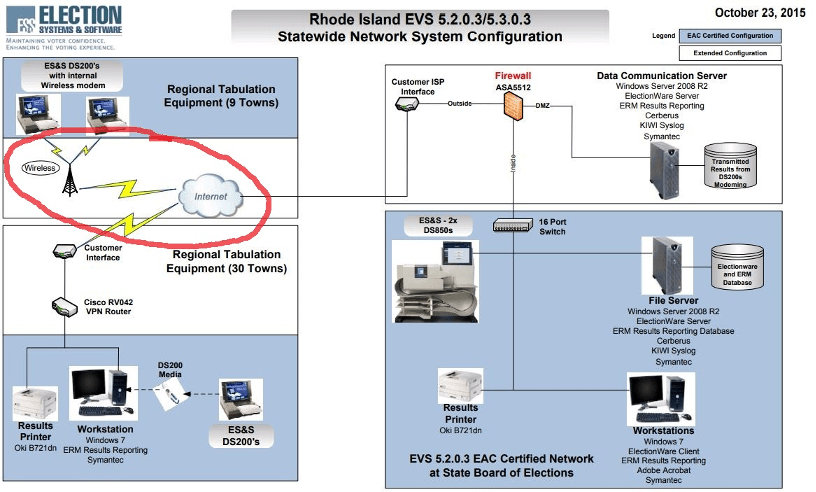
Pictured: Early ES&S system deployment diagram that suggest many older devices were equipped with an internal modem for communicating results to a centralized communications server at the state board of elections for preliminary dissemination and predictions for media outlets. (Source)
The threat to the security of voting and tabulation machines is exponentially reduced by keeping the devices off of the internet and restricting physical access to trusted employees and election workers. Early system deployment diagrams provided by ES&S (and obtained by Vice) suggested many of their older devices were equipped with an internal modem for communicating results to a centralized communications server at the state board of elections for preliminary dissemination and predictions for media outlets.
These diagrams also suggest they rely on Windows 2008 R2 server and Windows 7, which would have most likely been updated by the 2020 election year.
Kevin Skoglung from the National Election Defense Coalition (NEDC), an election security advocacy group stated they found over 35 voting systems left online across 10 different states for several months. Some of the machines discovered online, likely due to technical maintenance and calibration servicing, were in crucial swing states like Florida and Michigan.
This summer, the NEDC sent coalition letters to states across the country outlining a list of immediate actions to secure the voting process before the 2020 general election: (Source: https://www.electiondefense.org/reports)-
Ban all voting technologies that are connected to the Internet or disconnect their modems immediately, and scan systems for viruses that may have already been inserted. -
Place sufficient emergency back-up ballots for all voters in case electronic voting machines break down, or for those who don’t wish to vote on touch screen voting machines. -
Print hard copy back-up of electronic poll books in all precincts. -
Disinfect and limit the use of touchscreen machines to mitigate the spread of COVID-19 and avoid long lines on election day.
Darknet Exposure of Voter Registration Data and Election Technology Company Credentials
EXPOSED ELECTION VENDOR DATA & THIRD PARTY RISK
All three of the principle ballot tabulation vendors have darknet exposure of corporate credentials, e-mail addresses and passwords, of their employees.
-
Exposed ES&S Credentials: 468
-
Exposed Dominion Voting Credentials: 94
-
Exposed Hart InterCivic Credentials: 218
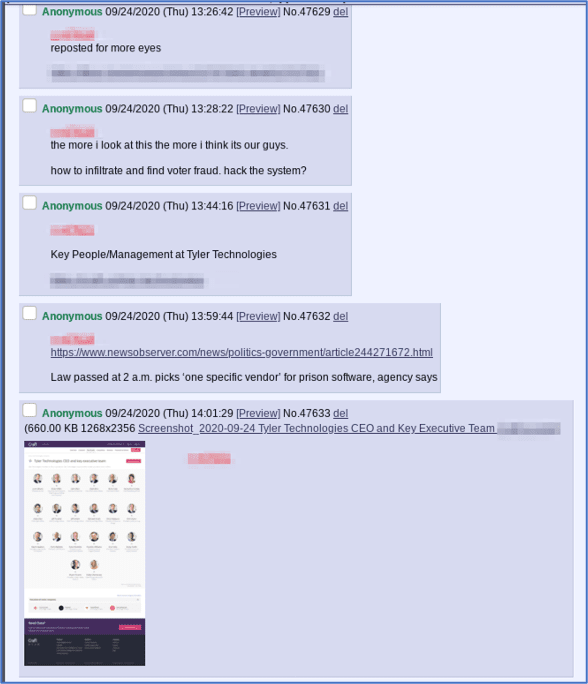
“The more I look at this the more I think it’s our guys. How to infiltrate and find voter fraud, hack the system?”
Corporate exposure of employee information is often the first step for exploiting a target corporation, via directed spear-phishing and social engineering. Tyler Technologies, a Texas-based software company whose products are used to display state and local election results, has over 2,000 corporate e-mail addresses in DarkOwl Vision’s database as of time of writing.
While their exposed credentials may not be related to this recent incident, it is worth noting that only a few weeks ago, in late September, Tyler Technologies was hit with RansomExx, a malicious strain of ransomware that began circulating the darknet in late May and early June of this year.
The ransomware, specified as “ransom.exx” in the source code, is distributed through an unsecured RDP configuration, opening a malicious attachment via email, fake updates and downloads, and malicious advertising. Tyler Technologies ended up paying the ransom to recover the encrypted data.
[Pictured] Anonymous users, aka “anons” on a darknet controversial imageboard and safe haven for Q-conspiracy theorists, discussed the Tyler Technologies breach within hours of Reuters’ public announcement of the attack against Tyler Technologies.
One user surmised the attack might have originated within the Q-community while another posted multiple doxes, identifying key management and leadership at the company.
EXPOSED VOTER DATA
U.S. voter registration information has been widely circulated across darknet forums and channels for potentially nefarious purposes. Earlier this year, DarkOwl detected U.S. voter registration databases for the states of Michigan, Florida, North Carolina, and Colorado being shared freely and sometimes sold on popular deep web forums, but this was certainly not the first exposure of U.S. voter registration data on the darknet.
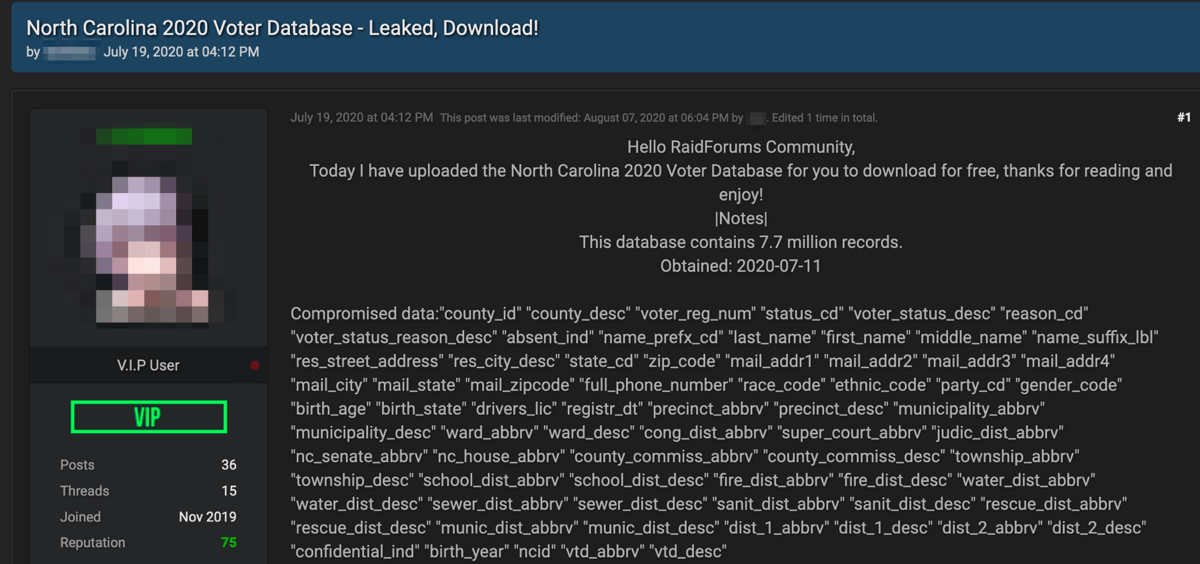
Pictured: Darknet advertisement for voter North Carolina registration databases
In the leaked police files known as the “BlueLeaks” files, that were released on the darknet earlier this year, official documentation speaks of how state voter registration data could be misused and specifically mentions how a malicious actor could leverage voter names, e-mail addresses, and telephone numbers to connect with new audiences and market personalize advertisements according to their views on specific topics, propensity to vote, and other factors. This information coupled with a foreign adversary’s disinformation campaign could be utilized to register fake social media accounts, seed content, and amplify distribution of content of interest to targeted audiences.
In 2018, a verified user using the pseudonym Omnipotent shared Kansas’ database of 4.1 million voters’ registration data including voter IDs, full names, physical addresses, previous addresses, dates of birth, genders, voter status and voter history. Omnipotent suggested the data was collected by gaining access to the state’s official SSH and SFTP servers and downloaded the data directly.
While most threat actors are less interested in disinformation and would utilize voter registration data for financial gain via identity fraud or scamming, one darknet source suggested that if any state’s SFTP and servers were insecure to the point of file download and SSH access, then there was nothing preventing the voter registration databases from also being altered. By introducing minor errors to key districts, especially in swing states, as little as 1% of the total records, or preventing as few as 1 in 100 voters from voting, due to errors in their recorded registration information, could change a state’s outcome on election day.
Luckily, most states have the option for provisional ballots and any voter registration discrepancies can be resolved with verification of identity. The FBI has validated that some states’ voter registration servers have been infiltrated in recent years, but in a recent advisory suggests that any release of such widely publicly available data has no potential impact to the credibility of the democratic election process. (Source)
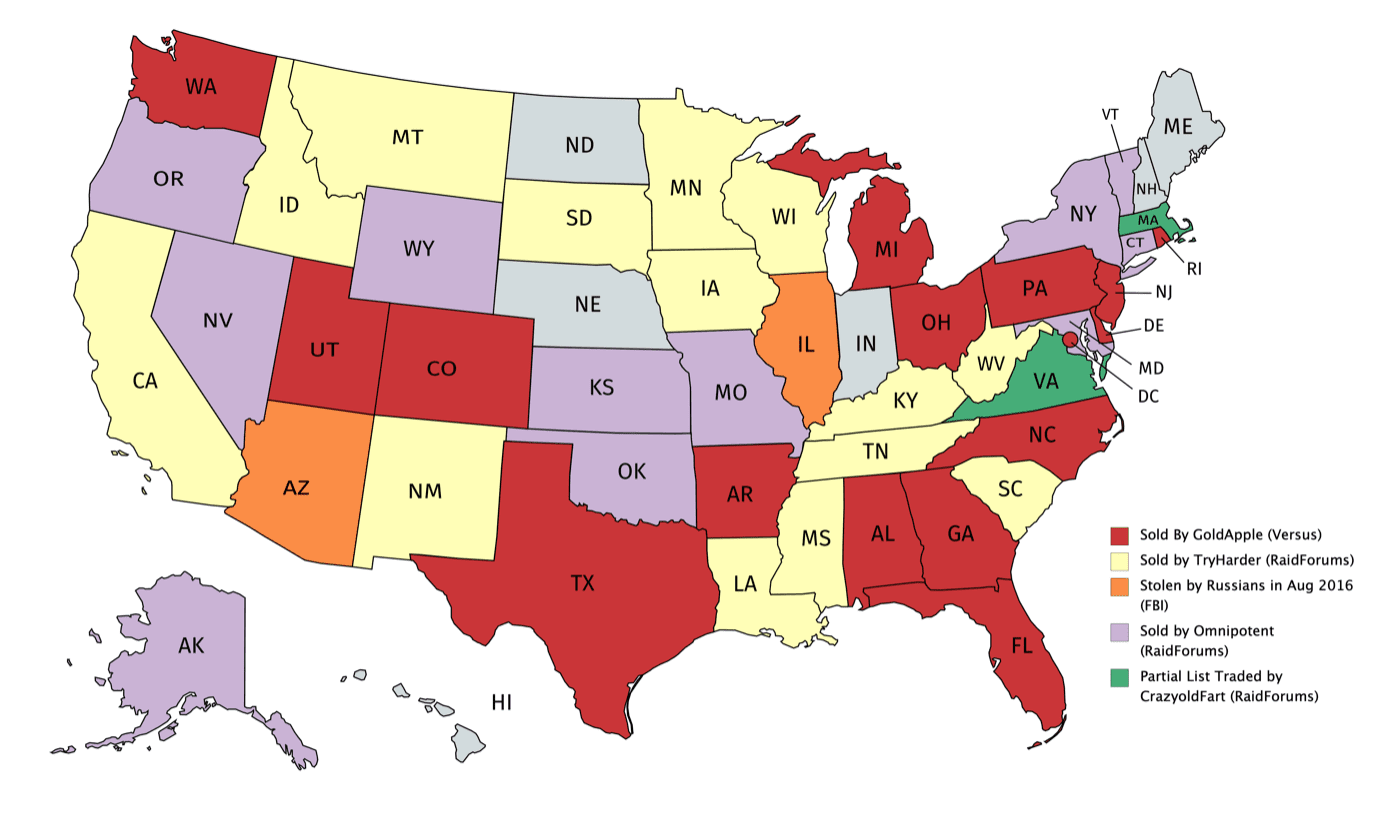
Pictured: Voter registration databases traded on the darknet, color-coded by darknet vendor and forum (unless otherwise specified).
Disinformation on Election Credibility likely to persist into media coverage on night of election
While voter registration data can obviously be used to conduct targeted disinformation campaigns, it is important to understand the other vectors with which disinformation can be spread by leveraging other security vulnerabilities described in this report. For example, in the case of Tyler Technologies, actors could potentially take advantage of these known vulnerabilities to intercept early voter reporting data and manipulate it before it reaches the media, which could then lead to unintentional false reporting by the press on which incumbent is in the lead. This could be especially impactful to would-be voters, who may choose not to cast their vote if they think their candidate is leading by a wide enough margin.
It is also worth noting that the attack on Tyler Technologies took place within days of the FBI and its Cybersecurity and Infrastructure Security Agency (CISA) issuing a public warning that they had intelligence indicating that foreign actors would likely spread disinformation the day of and days immediately after the election, specifically regarding the election’s credibility – in an effort to actively undermine the democracy of the country.
Knowing the scale of disinformation-as-a-service offerings available on the darknet the use of proxy media outlets for foreign propaganda information operations and the economies of bulk social media accounts in support of disseminating and controlling a false narrative, it is understandable why the FBI emphasized the importance of using only the most reliable information sources and not sharing and circulating controversial information about the election.
DarkOwl would add the emphasis of importance of voting early regardless of what preliminary local media outlets may suggest about the projected outcomes of an election. The FBI has released a further advisory on how foreign information proxies, including pseudo-academic online journals may be leveraged to disseminate articles with misleading and unsubstantiated information in order sow disbelief in democratic election process.
Given the depth of political dissent DarkOwl has observed across darknet forums and discussion boards, domestic terrorist groups and conspiracy theorists will also inadvertently support these narratives and further exacerbate discord across the country through social media platforms and large group chats.
The best way to avoid becoming a victim and pawn in the ongoing psychological, via information, warfare around us is to cast your vote, refuse to engage, disseminate or proliferate any controversial election information on social media; remain calm and unite with those that you may deeply disagree with – remembering the words of Helen “Jo” Cox that “we are far more united and have far more in common than that which divides us.”
FOREIGN ADVERSARIES TAKE CREDIT“In 2016, the U.S. was unprepared at all levels of government for a concerted attack from a determined foreign adversary on our election infrastructure,”-Senator Richard Burr (R-NC) member of the Senate Intelligence CommitteeIn another popular darknet discussion board, one user discussed how in 2012, Vladimir Putin publicly decried how the U.S. had encouraged local protestors to claim Russia’s presidential elections were rigged and suggested that Putin was actively seeking payback by discrediting American elections. This was further supported by a lengthy post on a now defunct darknet forum back in 2016, by a Russian darknet threat actor on how easily the U.S. election system could be hacked by Putin and his cyber warriors. The author, using the moniker alex_61, outlined flaws in the voter registration process and duplication of registration data across states, the exploitation of absentee ballots, the ease at which DRE software at the time based on Windows 2000 could be compromised remotely via the polling location’s wi-fi, sending “fake” software upgrades that contain malware to the state election officials, and the lack of national election oversight and auditing as potential opportunities for mass manipulation that the Russian government was fully capable of. REMEDIATION: Security recommendations for voters and election officials
As we mentioned throughout the report, despite threats to the US election systems discussed on the darknet, there are plenty of steps voters and election officials can and are actively taking to mitigate any risks to the credibility of the election. Voters can proactively take steps to ensure their information is accurate on their voter registration rosters.
Check your voter registration information online ASAP
-
All U.S. voters should confirm the accuracy of their voter registration information before arriving to their local voting sites on election day. If voting in person, bringing photo identification and proof of residence with you to the voting site helps in the case any errors require a provisional ballot. Instructions on how to verify one’s registration information by state can be found at: https://www.usa.gov/confirm-voter-registration
While ballot tallying and DRE machines are not connected to the internet during active elections on November 3rd, districts across states are actively securing their information networks to prevent any disruption or intrusion. MSSPs such as DarkOwl’s partner, CyberDefenses, LLC, help harden election networks and setup redundant network systems as day-of distributed denial of service (DDoS) attacks have occurred in previous election cycles. They also proactively provide education to election officials and poll workers on best physical and network security practices, help reorganize their networks to the most secure configurations, and conduct information assurance testing of many of state’s election networks across the country.
During conversations with CyberDefenses, LLC, technical leadership advise a top down strategy for the Secretaries of States they support and are less worried about physical network security and more concerned about election credibility disinformation campaigns by foreign and domestic threat actors. Earlier this year, they witnessed a concerted Black SEO campaign, like those advertised on underground forums and marketplaces, where threat actors intentionally buried the official vote411.org domain, a key national-level election information website, using SEO manipulation. Fake domains containing incorrect information, resolving to IP addresses across Russia, appeared ahead of the official website in Google search results until counter-SEO was implemented. BlackSEO and URL hijacking are key tools of many disinformation as a service offerings across the darknet. Domestic terrorists and foreign threat actors are also actively conducting heavy reconnaissance of election networks to uncover potential vulnerabilities that can be leveraged in an election credibility disinformation campaign.
Any risk to the security of voting machines is proactively remediated by many election officials and their technical support in the weeks leading up to the election, on making sure all electronic voting machines have been updated with the latest versions of application software and firmware with minimum exposure to the internet. Election officials, their technical support and on-site machine vendors conduct software updates by bringing small numbers of the machines online to push the installs and immediately taking them offline to reduce the network exposure of the devices.
Election vendor officials are also advised to be suspicious of and verify any and all packages received from device vendors or third-parties, no matter how credible they appear to ensure any mailed USB “firmware updates” are legitimate and not a malicious phishing attempt.
On the day of the election, officials are also advised to place sufficient emergency back-up ballots for all voters in case electronic voting machines break down or behave unpredictably. Officials should also print hard copy back-ups of the electronic poll books in all precincts for any real-time registration or poll book roster manipulation. Many districts also rely on “sneaker-net” the day of the election calling in and hand-carrying ballot tallies to avoid any inadvertent data exposure.
Consider your voting options depending on where you live
As an individual if you have concerns about the security of your local election systems in use, first, if paper ballots are printed as formal record of your candidate selections, then take time to review what has been recorded carefully after using a DRE machine. Secondly, if you live in one of the few states that only have DREs without paper trails or one of the handful of states that still have some districts with DREs without a paper trail contact your state representatives and insist on a public audit.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















