April Fools? How Threat Actors Try to Trick You With Phishing Emails
Threat actors get crafty with their phishing scam techniques, which is no laughing matter.
April 01, 2023
Diving into Phishing Trends by Categorizing Phony Emails
To learn more about trends in the phishing and spam email landscape, our analysts created accounts for fake email addresses that were posted on the darknet. These addresses were mainly sourced from combolists, which are large batches of credentials that typically came from a variety of different breaches or otherwise illicitly obtained methods.
Over the course of the year, 1,407 emails were sent to these email addresses. Given the context they were found in, these emails likely only exist to be used by threat actors much like other combolists that are posted on the dark web. That is, to be run through a credential stuffing tool to find successful email/password combos and commit account takeover, or to target the addresses with malicious phishing emails.
To demonstrate examples of the kinds of dubious emails our analysts received, we ranked them by most popular to least popular and assigned them with the following categories: Personally Identifiable Information (PII) Stealers, Fraud, Malware, and Spam.
Read on to see what type of scam and spam emails were the most popular amongst threat actors over the past year, and to see what key trends our analysts observed in the world of phishing.
1. Sales Spam (26%)
Type: Spam
Of the 1,407 emails, a whopping 365 of them were generic sales spam with no clear motive. This suggests the reason for sending them was unlikely to be to commit fraud.
365 of the emails were sales/personal services spam
2. Survey Scams (17.5%)
Type: PII Stealer, Fraud
Most of these emails invited the recipient to take a survey to win a gift card to popular stores like Walmart, Ace Hardware, and so on. This can be used to gather personal information from the target to execute more refined spearphishing in the future, or leveraged for account takeover.
245 of the emails were survey scams
3. “I hacked you” Scams (16.8%)
Type: Fraud
“I hacked you” scams typically contained some sort of variation of threat such as “I caught you on webcam” – with the sender threatening to release “footage” or encrypt the recipients computer unless they pay a Bitcoin ransom. There were a significant higher number of emails in this category than observed in previous years.
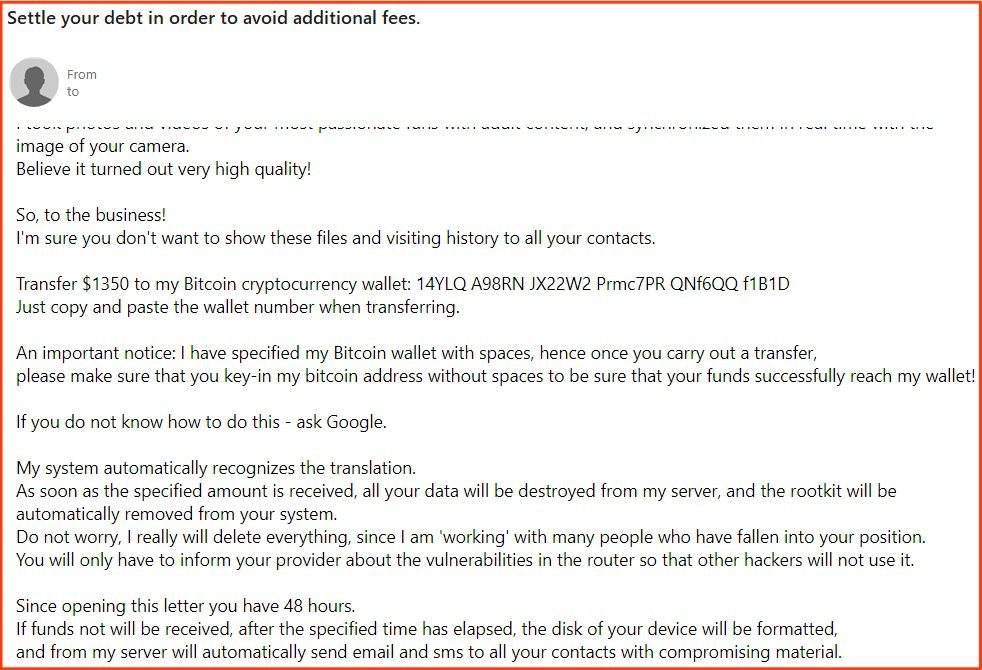
237 of the emails were “I hacked you” scams
4. “You’ve won free stuff” Scams (7%)
Type: Malware
97 of the emails claimed that the recipient had won some type of reward, including reward points, commercial goods, rebates, and so on. Once the target clicks the link or opens the attachment to claim their “free stuff”, they end up installing ransomware instead.
97 of the emails were “you won free stuff” scams
5. Phone Scams (6.8%)
Type: Malware, PII Stealer
Designed to get around endpoint security, fake invoice for software subscriptions with a real toll-free “customer assistance” number. Once the victim calls, the operator usually attempts to social engineer them into revealing PII, or trick them into installing ransomware. Overall, we saw a big uptick in these compared to previous years – with many leveraging big names such as Geek Squad, McAfee, and Norton.

96 of the emails were phone scams
6. “Generic” Scams (4.8%)
Type: PII Stealer, Fraud
A significant portion of the email data set fell into the category of “generic” – including scams and “advanced fee” schemes. These are mainly weaponized to steal personal information and commit financial fraud or identity theft.
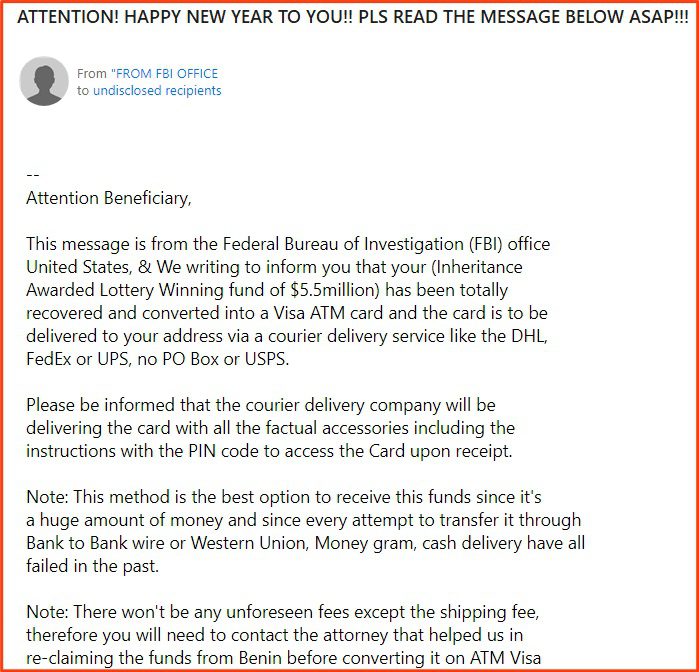
68 of the emails were of the old-school variety, such as 419 scams
7. Counterfeit Spam (4.1%)
Type: Spam, Fraud
These emails advertise below-market rates for high-end brands that are ultimately for counterfeit goods. Of the 58 sent to our analysts, most advertised for well-known luxury brands such as Louis Vuitton and Ray-Ban.
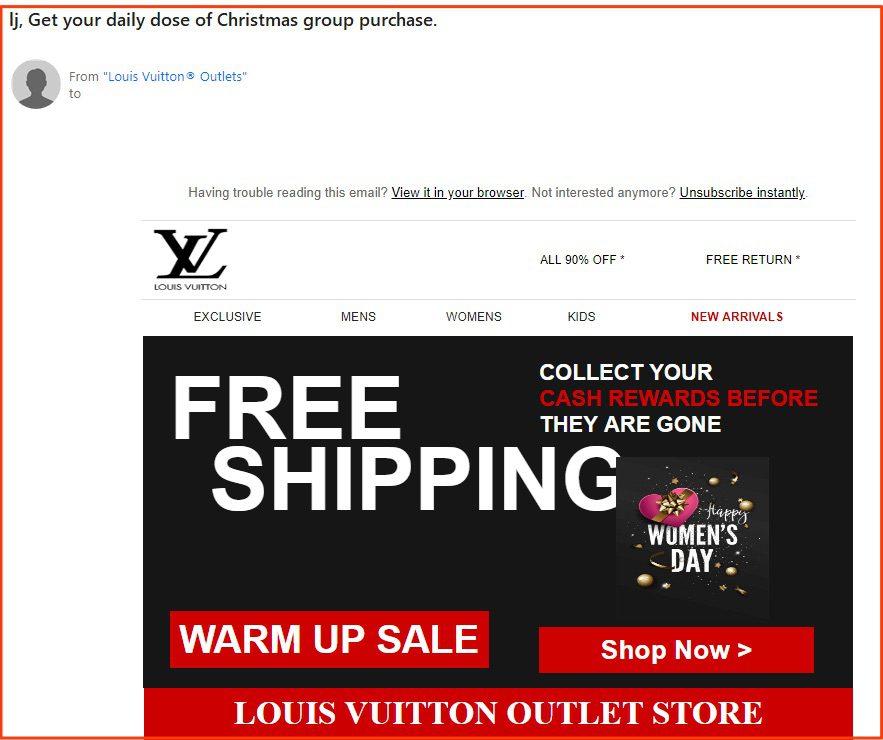
58 of the emails were counterfeiting spam
8. Junk Car Scams (3.7%)
Type: Fraud
“We’ll buy your car” scams continue to be pretty consistent in popularity – though they may not be reported about as often as some of the other categories on this list. For further reading on this topic, our analysts suggest this resource that outlines 5 common scams for prospective call sellers.

53 of the emails were junk car scams
9. Fake Lawsuit Scams (3%)
Type: PII Stealer
“You could be eligible for compensation” – these types of infostealers usually falsely claim the victim could be eligible for compensation if they participate in a phony lawsuit.
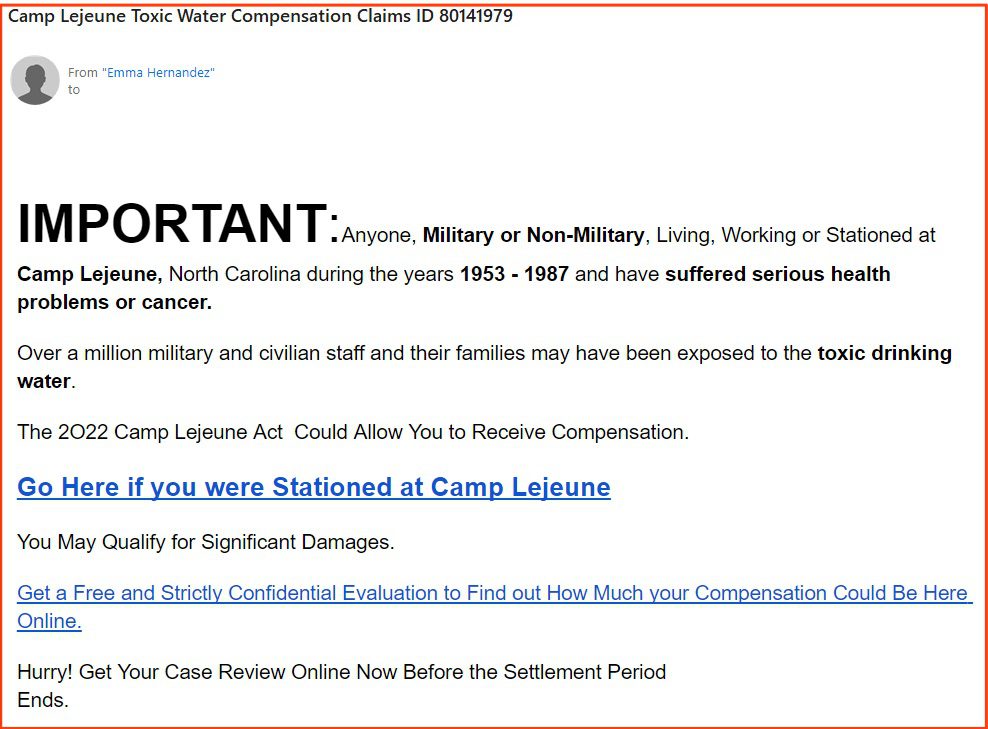
42 of the emails were fake lawsuit scams
10. Elder Abuse Scams (2%)
Type: PII Stealer, Fraud
Our analysts identified 28 emails that were directly targeting seniors. Most of these could be identified by keywords such as “senior”, “55+”, “timeshare”, “retirement”, and “over 60”. This suggests that not only is this attack vector still as popular as ever, but that actors are being quite blatant in their marketing towards this demographic.
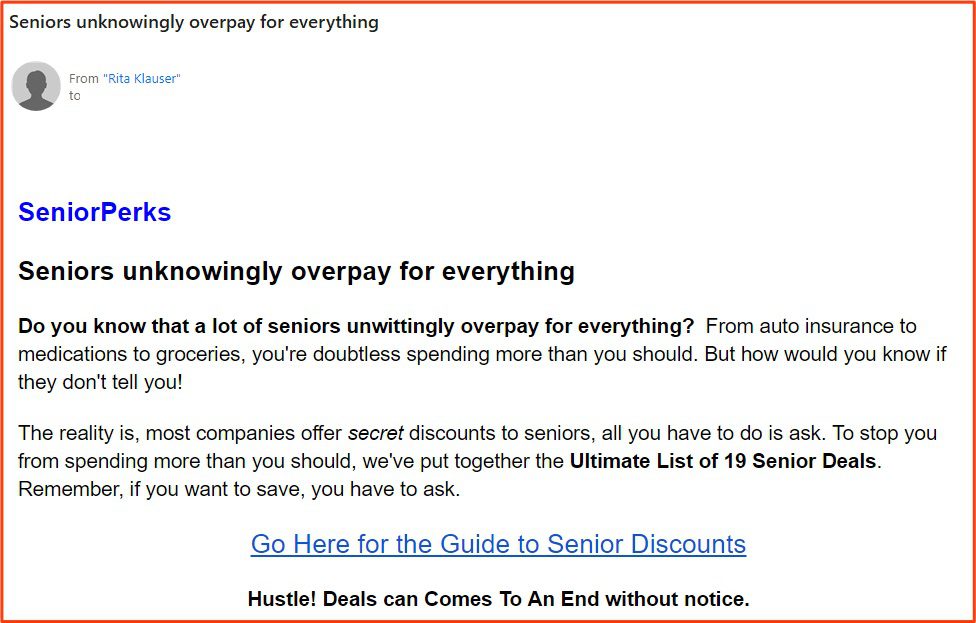
28 of the emails were scams targeting seniors
11. “Cheating” Scams (2%)
Type: Malware
Many of these emails touted a tool that claimed it could enable the recipient could see or verify the (likely) phony claim that their spouse or partner is cheating on them by installing spyware on their computer.
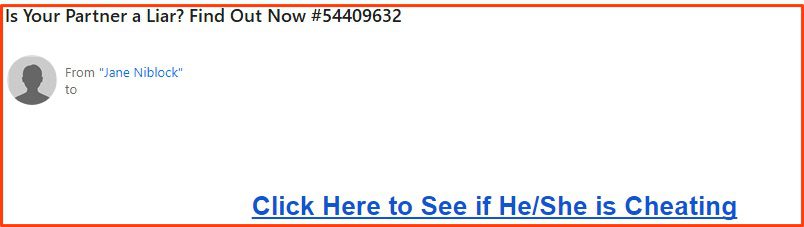
28 of the emails were “cheating” scams
12. Fake Notifications Scams (1.6%)
Type: Malware
The 23 emails that fell in this category included phony alert emails claiming that the recipient had unread notifications from popular services such as Tinder, Reddit, Whatsapp, and LinkedIn. Popular subject lines contained some variation of “12 unread messages” or “You’ve matched with someone”, etc.
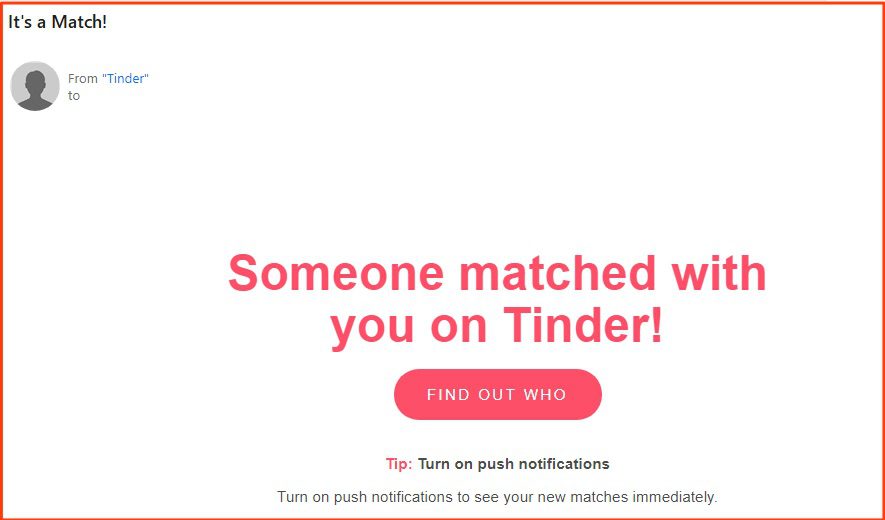
23 of the emails were fake notifications scams
13. Romance Scams (1.4%)
Type: Fraud
Seeing as how romance scams have tripled in popularity in the past few years, our analyst expected to see more of this type of phishing scheme.
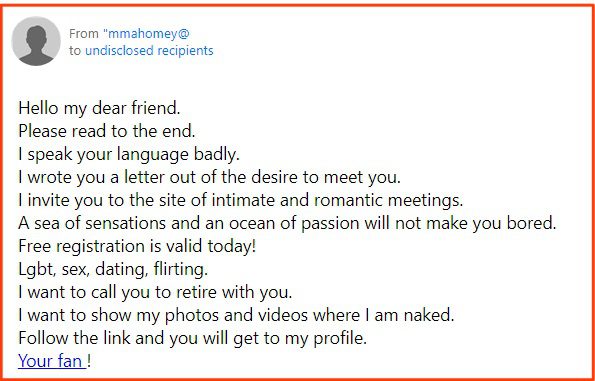
20 of the emails were romance scams
14. Fake Invoice Scams (1.3%)
Type: Fraud, Malware
These emails were consistent with the typical invoice scams that have been popular in past years. They are typically blasted out to businesses or email addresses that look like the might be accounts payable, office managers, or other administrative invoice and include a “real” invoice for nonexistent goods or services.
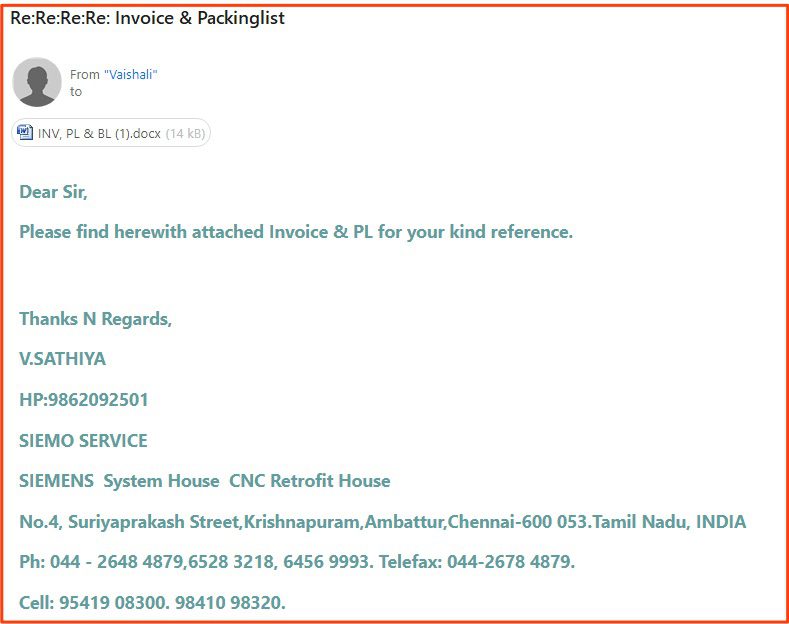
19 of the emails were fake invoice scams
15. CCW/2A Spam (.7%)
Type: PII Stealer
This type of scam is not one that our analysts have observed very often, if at all, before this analyses. These phishing emails mainly offered assistance in obtaining concealed carry permits. Most likely, this is a PII stealer scheme.
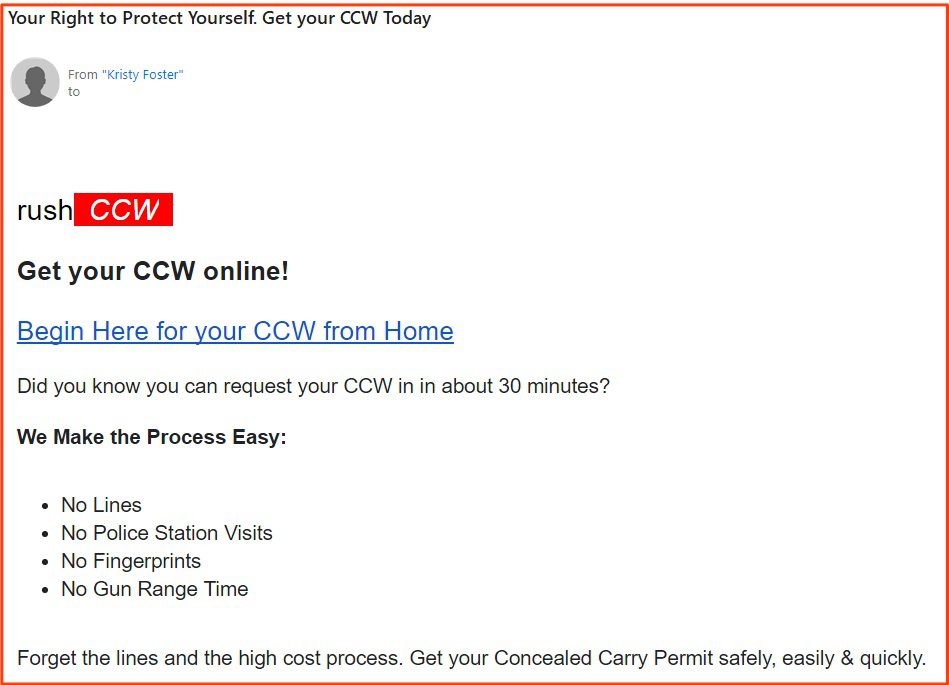
10 of the emails were CCW/2A spam
16. Unclaimed Assets Scams (.5%)
Type: PII Stealer, Fraud
Many of the unclaimed asset scam emails claimed that the recipient was entitled to property from either inheritances, or from unallocated government holdings. In the example below the sender broadens the asset to “unidentified property” – making the chances that a target might think it could apply to them more likely.
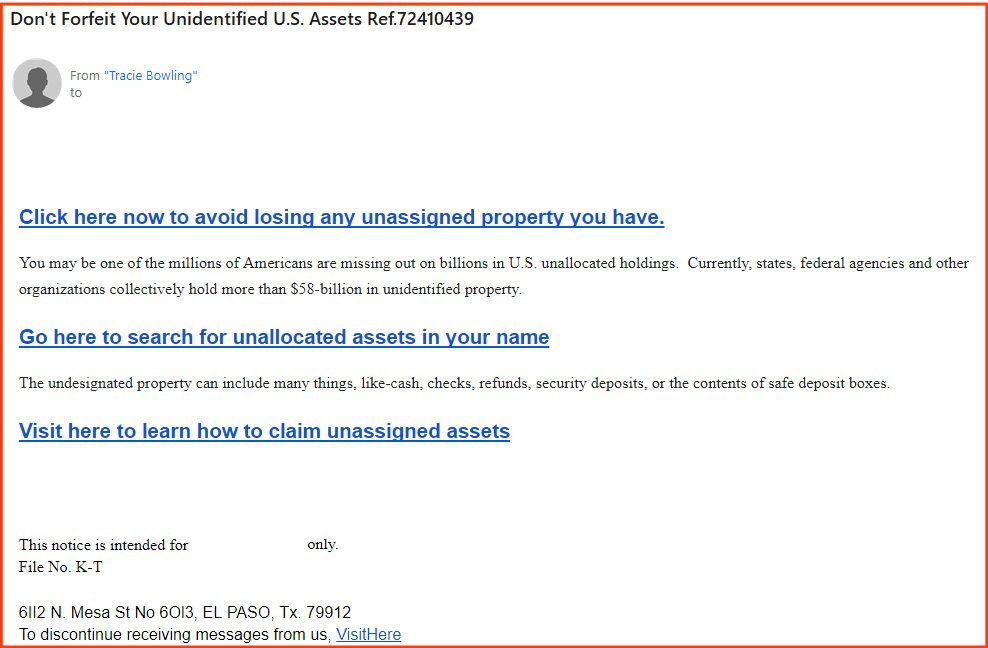
8 of the emails were unclaimed assets scams
17. Scam Job Offers (.3%)
Type: PII Stealer, Fraud
Only four emails consisted of fake job postings. Given the overall uptick in scams of this nature, this was fewer than our analysts expected.
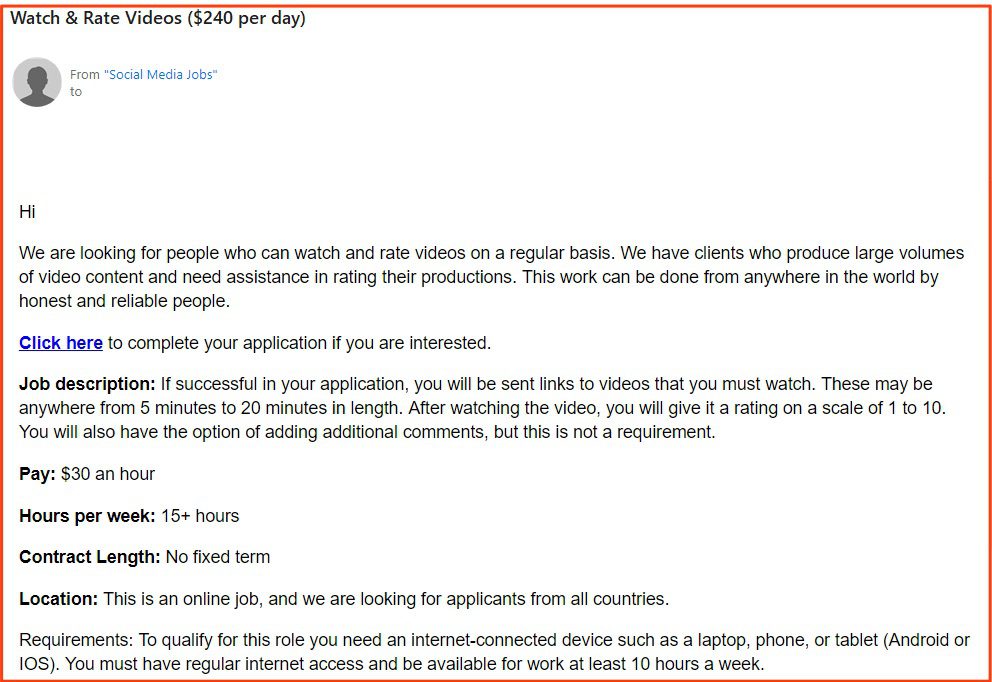
4 of the emails were job scams
18. IRS Scams (.2%)
Type: PII Stealer, Fraud
Given that this data set included two tax seasons, it was surprising to see how few IRS scams there were. Specifically, our analysts found the lack of specific “IRS” and “tax/taxes” keywords in emails’ subject lines to be significant.
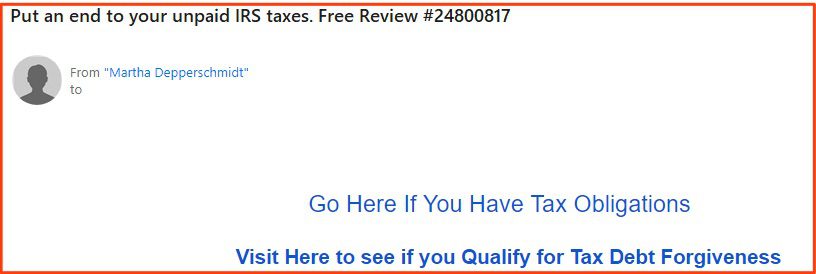
3 of the emails were IRS scams
19. Other Malware (.2%)
Type: Malware
These emails contained malicious links that were likely ransomware. Their phishing pretexts didn’t fit into any of the other categories.
3 of the emails contained malware but didn’t fit into any of the other categories above
Further Observations
Sales spam still dominates, and phone scams are on the rise
After categorizing and ranking these emails, our analysts made note of several key observations:
IRS Scams are down – Tax fraud phishing campaigns that specifically mention taxes or the IRS are way down from previous years. This is likely due to IRS messaging and warnings, which seem to have done their job in at least deterring actors from using this method so heavily.
Phone Scams are are more popular – Phone number malware campaigns, designed to get around endpoint security, are becoming more prevalent.
Less emails marked as “High Priority” – Of all the emails, only 4 were marked as “High Priority,” which is a shift since previous years. In the past, this was a common tactic to create a sense of urgency and improve open rates.
“I hacked you scams” proving to be lucrative – We saw a huge uptick in this type of email over the past year. In this type of scam, the sender usually blasts emails out to massive list and might only get money back from one or two people. Their uptick in popularity indicates that the financial reward from even just a handful of victims is lucrative enough to incentivize more threat actors to use this method.
Never ever open email attachments – While only 7.53% of analyzed emails had an attachment, every single one of those contained malware. The takeaway? Assume that all attachments are malicious unless you are able to verify otherwise in a safe sandboxed environment.
Research indicates that the most successful attack vectors include exploitation of email credentials, either via phishing attacks or account takeover. Take control by gaining situational awareness of your companies darknet exposure by contacting us here.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















