Increased Threat to Food Delivery Services on the Darknet
In a time when society is more reliant than ever on personal food delivery and shopping services such as Seamless and Instacart, darknet criminals also have increased their reliance on exploiting these applications for continued financial gain.
The potential for fraudulent activity includes purchasing goods with hacked accounts on these services, abusing the vendor’s refund policy, and even more advanced techniques such as API traffic interception for malicious injection or targeted data manipulation.
DarkOwl has observed an increase in the prevalence of food delivery and personal shopping service accounts on offer across a number of darknet marketplaces.
DarkOwl confirmed an increase in food delivery service provider mentions in not only major darknet marketplaces but also in criminal carding forums and illicit digital good trades on anonymous websites. Of the vendors we looked at, Seamless and Caviar appear to have the most remarkable increase in the number of documents in DarkOwl Vision mentioning compromised accounts, with Instacart, Uber Eats, Just Eat, and DoorDash close behind.
To conduct our analysis, we looked for instances of each food delivery service provider appearing in our database of darknet documents (Vision), from year to year. Vision is comprised of content scraped directly from pages on the darknet, such as pages on Tor. As per the graph below, we are then able to see how many mentions there were of each company in our database to estimate what percentage of darknet pages mentioned these companies during that time.
For example, of all the pages of darknet content DarkOwl has collected that mention DoorDash or DoorDash accounts to-date, 33% of page results were observed on the darknet in 2019 and 67% were from 2020. This is also notable insofar as it indicates that DarkOwl did not observe DoorDash accounts appearing on the darknet until 2019, so they are evidently a new and increasingly popular target.
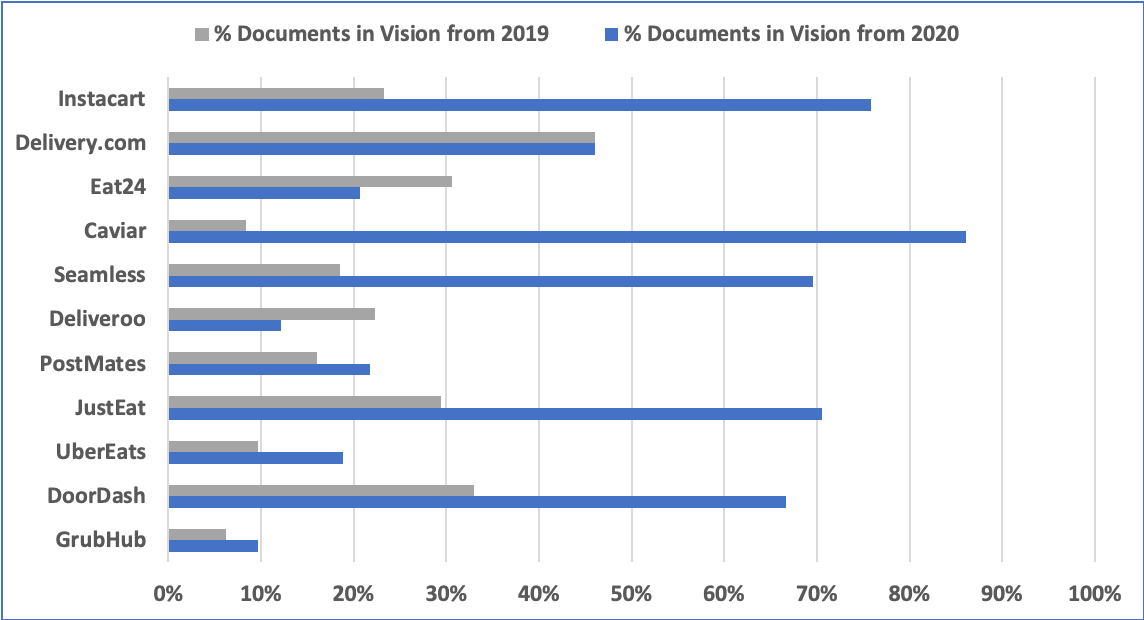
Figure 1 – Percentage Documents in DarkOwl Vision mentioning the Service Provider or their Commercial Domain from 2019 – 2020
Our analysts also note that the 2020 data included in this analysis is only through the end of July, meaning that many of these vendors will likely surpass (or continue to surpass) their 2019 numbers by an even greater extent by year’s end. Interestingly, DarkOwl also observed PostMates and UK-based Deliveroo food delivery services mentioned in fraud-focused conversations on criminal forums but in less volume than in 2019.
Across the board, using DarkOwl Vision, we saw an average 230% increase in darknet mentions of most of the major food delivery and personal shopping providers between last year and this year.
Examples of Compromised Accounts Being Advertised
On the darknet marketplace Infinity Market alone, DarkOwl discovered 8 different vendors selling a mix of hacked mainstream food delivery service accounts, including, DoorDash, Grubhub and Caviar. The average price ranges from $1.50 to $10 USD per account and successful use depends on the user not recently changing their password, as is often the case, rendering the account useless. The value of the accounts is determined by a number of factors including the ‘freshness’ of the account and the number of completed orders fixed to the account, as well as and most importantly, the volume of personally identifiable and financial information attached.
In mid-June, a new user on Raid Forums posted numerous DoorDash email addresses and passwords along with their account balances free for criminal use. With the account login credentials and an account with a saved credit card on file, the cybercriminal can easily change the delivery address and use the account to purchase food for delivery fraudulently.
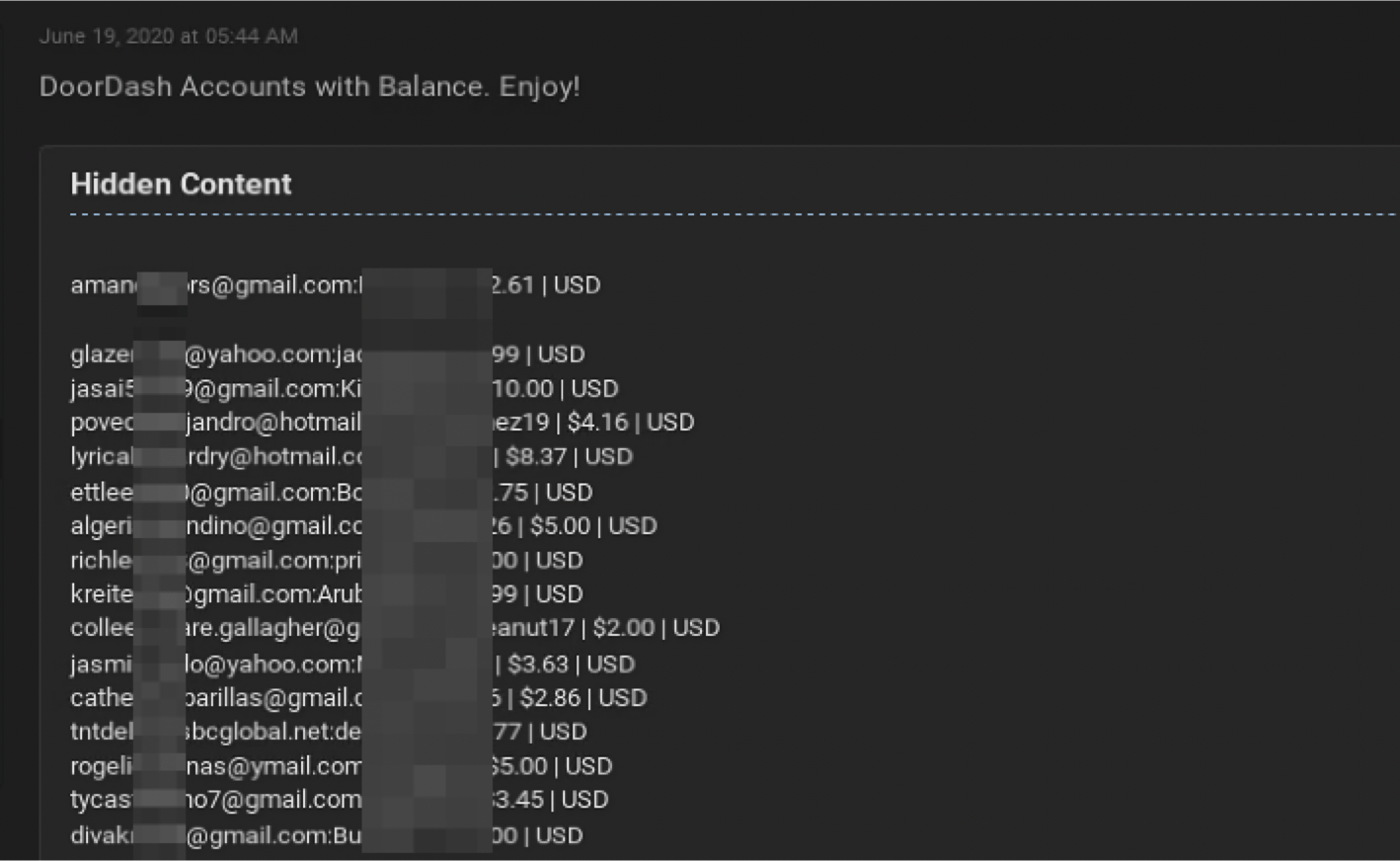
Figure 2 – Compromised DoorDash accounts on the darknet (including email and password) and associated balances for each account
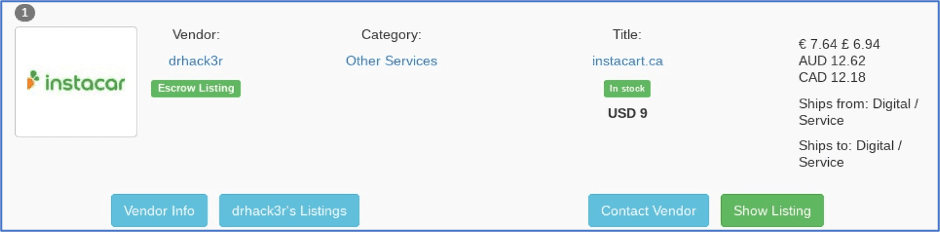
Figure 3 – Instacart consumer accounts offered for sale on White House Market
According to reporting from late July, some 278,531 Instacart consumer grocery shopping accounts were found to be for sale on the darknet, for as little as $2 per account. The information includes the customer name, email address, the last four digits of their credit cards, the order history for the account, and some other shopping-related data. The validity of the account information has been verified by two Instacart customers whose details are up for sale, and this information is not old.
DarkOwl has been unable to confirm the Instacart offer for the volume of Instacart accounts available and Instacart denied a breach of their systems occurred. Instacart stated that the account data was likely generated as a result of credential stuffing using previously compromised information publicly available.
One Way Criminals Make Money From These Accounts: Refund Policy Fraud
Underground cybercriminals have also uncovered ways to bypass most of the major food delivery service’s refund policies and now offer step-by-step instructions for single, one-time use or the opportunity to use third-party anonymous accounts for executing the order and the refund, while skimming either a flat rate or a percentage of the refund as commission for facilitating the refund fraud.
Refund brokers who charge a flat rate for orders up to a certain value, likely operate a larger criminal enterprise, whereas others charging upwards of 45% per transaction, suggests they rely on issuing a fewer number of refunds with higher profit margin.
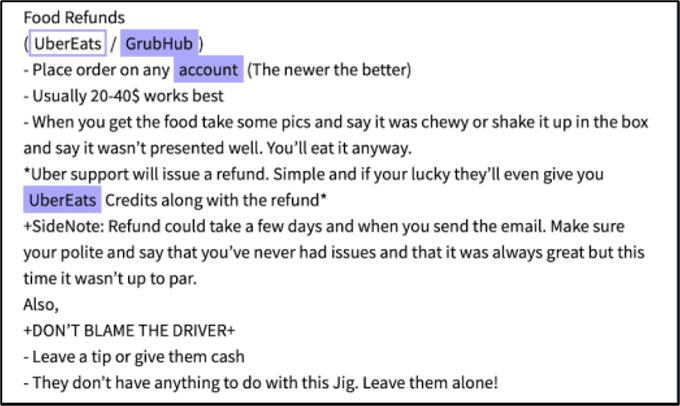
Figure 4 – UberEats & GrubHub Fraud Guide for Single-Use. Source: DarkOwl Vision (976763716e16fa2f111a0dd6aebe903a)
In May, Instacart refunds for upwards of $700 USD, along with Uber Eats for $200 and Shipt for $500, were offered for sale by a user known as @DDsRefundVouches on the popular chat application Telegram.
Frauding refund policies presents an opportunity to resale the credit as gift cards, a popular money laundering currency on the darknet and deep web.
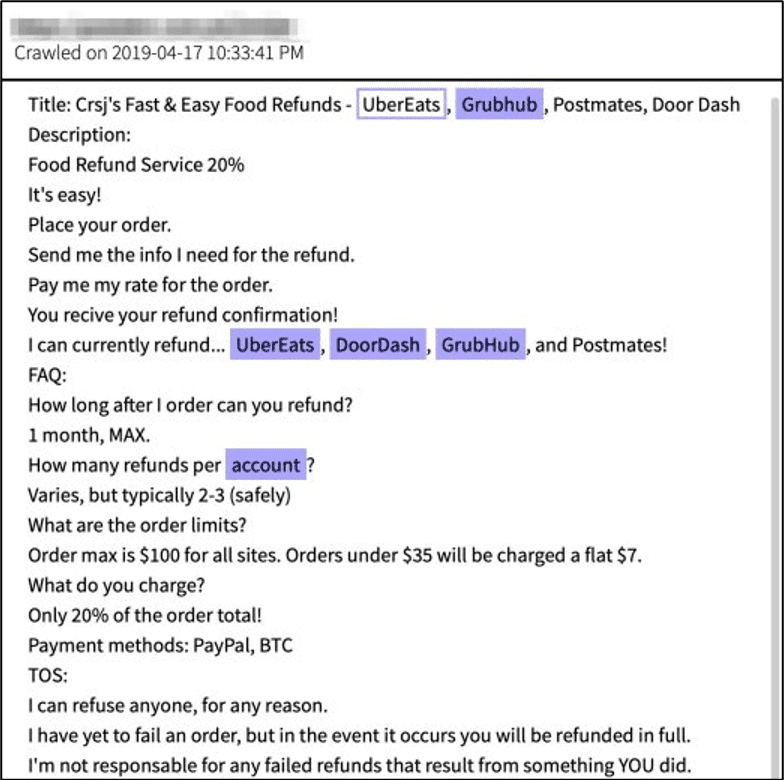
Figure 5 – Crsj’s Fast & Easy Food Refunds Mentioned on the darknet. Source: DarkOwl Vision (369383f52e069a2c9865185b95096374)
Food Delivery Account Vulnerability: API Cracking & Shopping Bots
Some more advanced hackers are more interested in the technology to exploit these personal services and many have expressed interest in the underlying API for traffic interception. This would give the criminal access to the customer’s personally identifiable information such as name, address, e-mail address and payment information.
A user on a hacker forum expressed interest in “cracking” the Just Eat food delivery service in the UK and the forum community offered a number of solutions depending on whether the purpose is to order for free or steal refund. One user “BigLad465” found a Deliveroo (another UK-based food delivery service) exploit that could capture a customer’s credit card for as little as £35 ($45 USD) for use on future food deliveries on another account or using the compromised account to request refunds on previous orders.
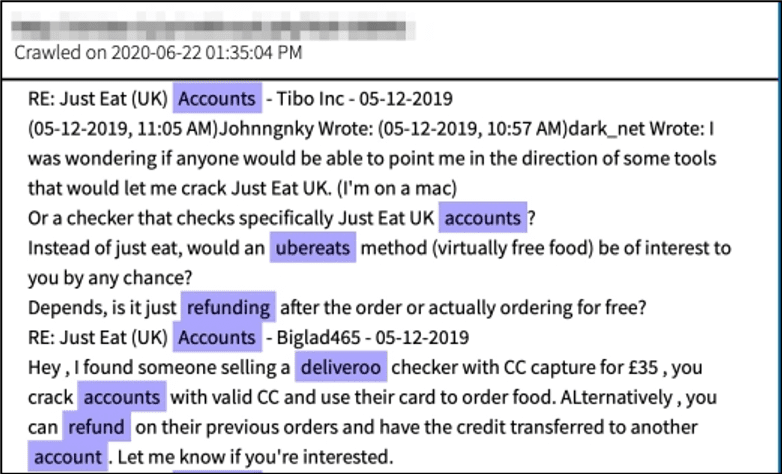
Figure 6 – Interest in hacking Just Eat UK. Source: DarkOwl Vision
Grocery shopping services like Instacart and Delivery.com are equally at risk for this type of criminal behavior. In late April, an anonymous user pasted the Javascript source code to automate the creation of Instacart accounts. The purpose of creating mass-volume of Instacart accounts was not identified in the post, but the username associated with the post is “ddanhviet” who has posted numerous scripts related to online shopping, product recommendations and user reviews including Home Depot and Tmall, a Chinese-based online shopping website.
Many of the app-interception and manipulation discussions sit on the Surface Web in websites such as Reddit and in social media. In early June, a Reddit user asked specifically about the Instacart API, looking to intercept traffic between Instacart servers and the shopper API. Some of the comments included Charlesproxy and Wireshark as potential solutions. Another Reddit thread from May talked of Instacart bots from a supplier known as HaxEdge Solutions to steal large-value batches.
The HaxEdge Solutions website discusses how they are able to conduct e-mail monitoring, social media hacking, expunge criminal records, and recover lost money due to scams. Despite their morally questionable services offered, HaxEdge does not have a noteworthy darknet footprint in DarkOwl Vision.
“Based on our expertise and experience with codings and several algorithms, we are able to input any backdoor command on security systems to achieve our results. People need hacking for several reasons and thatʼs why we set up our agency to serve as the unconventional way out. We offer variety of hack services depending on your request, our hackers will document your inquiry and provide a functional process to get a solution.“
”
In recent months, there has been a surge in Instacart related batch-stealer apps and many have come and gone, sometimes using slightly varied titles, such as Ninja Hours, Ninja Shoppers and Ninja Shopper. DarkOwl discovered nearly a dozen active platforms in mid-May advertising openly on YouTube and social media platforms. Contact information for these apps links them to users spanning the U.S., including New York, Savannah, Georgia and Northern California.
Detailed tutorials on how to use the third-party bots and batch stealers are available across a variety of YouTube channels for the apps. In the case of Ninja Shoppers, which was recently covered by Bloomberg News, the app is free to download, but users must be ‘’activated in a private group” in order to be granted permission to pay for a user authentication token. Once logged-in, the program prompts the user to find Instacart orders available near their location, according to a YouTube video viewed more than 13,000 times in the past three months.
Identifying one criminal exploiting food delivery accounts: Ninja Shopper
Ninja Shopper is one of the most prominent and popular Instacart order (batch) stealing programs available on the market. The app developer accepts Bitcoin and Zelle payments and sales for as little as $600 USD with a phone number located in the New York area.
Figure 7 – One of a number of YouTube tutorials on how to use the third-party bots and batch stealers to exploit food delivery refunds.
With minimal OSINT investigating, DarkOwl analysts uncovered an application in a GitHub repo with a similar name originated two years ago called “batchgrab” from a Brazilian programmer, using the moniker, felix b1scoito. Other repositories in his GitHub include auto-clickers, e-mail spammers, and DDoS tools.

Figure 8 – Image of the individual that is potentially behind the “b1scoito” moniker Source: youtube.com
The moniker “b1scoito” has a large darknet presences across major deep and dark web hacking forums. They previously talked of intercepting the Netflix API and demonstrates proficiency in a number of key programming languages. Using other digital fingerprints revealed through pivoting with DarkOwl Vision, analysts found links to a programmer on a YouTube channel that included a Portuguese-speaking tutorial on AdvancedBots only a couple of months ago, an inactive Twitter account and Surface Web URL with numerous references to the b1scoito alias.
Ninja Shopper is not the only Portuguese-speaking bot on the market. Others such as Robô Instacart had a short lifespan on YouTube and Reddit in late May (shown below).
As outlined in the recent article published by Bloomberg, their journalists connected with an Instacart bot-seller that DarkOwl discovered by phone in late July and the man spoke first in Portuguese and then in English, confirming to them he was selling a bot for those amounts. He declined to answer additional questions after learning that the information would likely be publicized.
Figure 9 – One of a number of YouTube tutorials on how to use the third-party bots and batch stealers to exploit food delivery refunds.
Potential Impacts to Account Holders
Food delivery services with mobile-phone apps are in widespread use. For example, according to a survey conducted by U.S. Foods back in mid-2019, survey data indicated that they average person has at least two food delivery apps and uses them upwards of three times per month. Furthermore, one could reasonably expect that usage has increased even more in 2020 with local restaurants dining rooms shutdown and country-wide quarantines due to COVID-19.
It is reasonable that criminals will continue to exploit these accounts in the future, beyond simple account hijacking or scamming vendor refunds. Further potential impacts include:
-
Access to PII (Personally Identifiable Information) could be exploited and used to make fraudulent purchases. (i.e. hackers with access could access your credit card info, home address and other addresses you’ve ordered from, etc.)
-
Information gleaned from your account could be used for highly targeted phishing attacks. (i.e. hackers could send an email appearing to come from a restaurant you frequent using detailed information from your order to execute a phishing attack.)
-
Free Food! We have observed interactions on the darknet of individuals discussing how they’ve simply usurped an account to order food for themselves and others.
In light of this knowledge, heightened personal security would be to never reuse passwords that might already have been compromised nor save personal credit card information on commercial accounts such as this. We also advise that users of these services take heightened caution when opening and clicking on links in emails purportedly coming from these services, as they may be phishing attempts.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















