Killnet and Anonymous Sudan: Identified Link
June 26, 2023
Using DarkOwl Vision, DarkOwl analysts have been monitoring activity related to the Killnet group and identified threats made in the past week relating to the European financial system. As part of this analysis, DarkOwl analysts have identified a link between Killnet and the group Anonymous Sudan.
The First Telegram Post
A post appeared on Telegram on June 15th from the Russian news site Mash which indicated that the threat actor groups REvil, Killnet and Anonymous Sudan were combining in order to mount an attack against European financial institutions. The Mash article was re-posted on both the Anonymous Sudan Telegram channel and the Killnet channel.
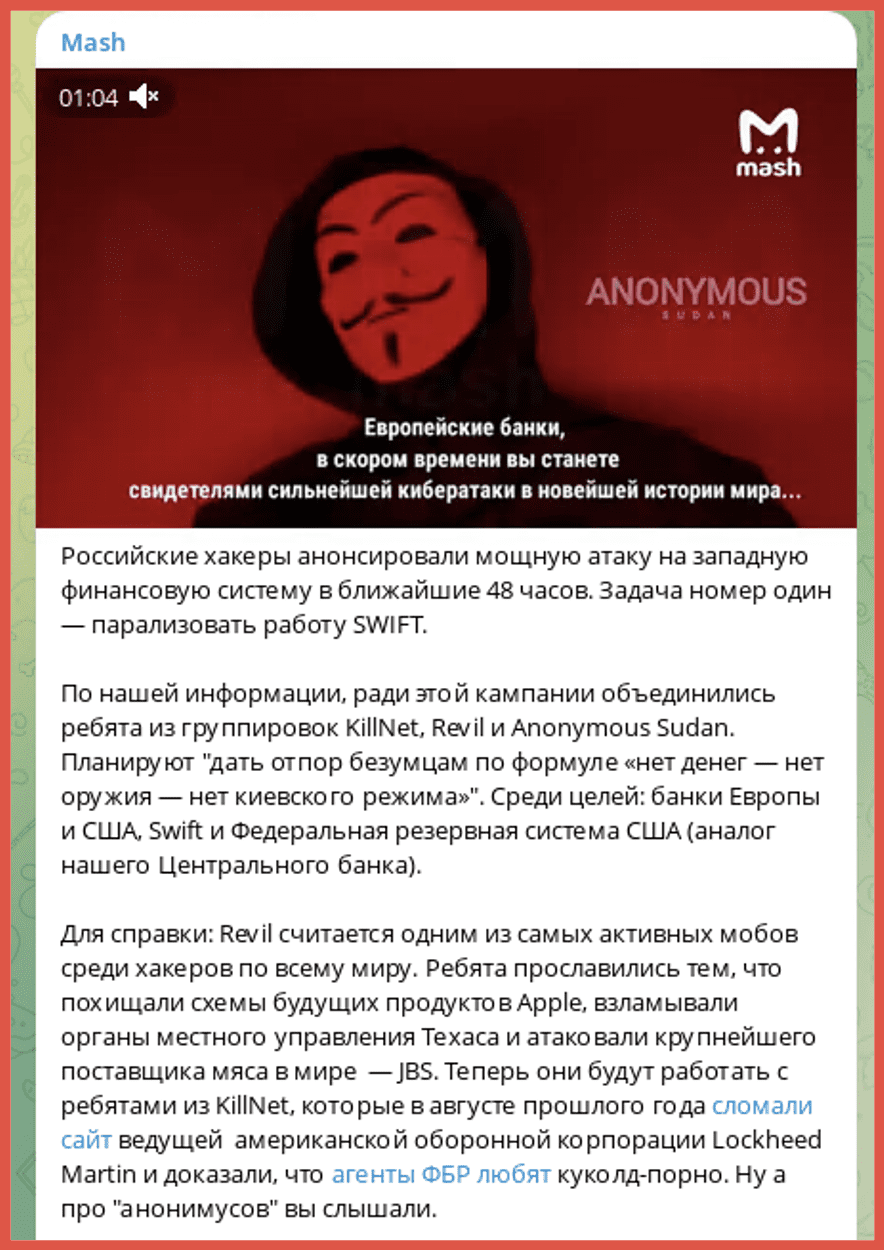
The original posts indicated that attacks against the Europe financial institutions would begin in 48 hours from the news article.
No clear indication has been provided of what the nature of the attacks would be but Killnet has historically been responsible for DDoS attacks (Distributed Denial of Service Attack), in which a malicious attack on a network that is executed by flooding a server with useless network traffic, which exploits the limits of TCP/IP protocols and renders the network inaccessible. Most of the posts that have been made have also been posted on the channels of both Killnet and Anonymous Sudan indicating that there is some collaboration behind the admins of these channels.
A new telegram channel was set up purporting to be from the group REvil. This channel welcomed Killnet and also posted a poll for followers of the channel to vote on which financial system in Europe they would like to be targeted. Other than an image of cryptocurrency nothing else has been posted on this channel to date.
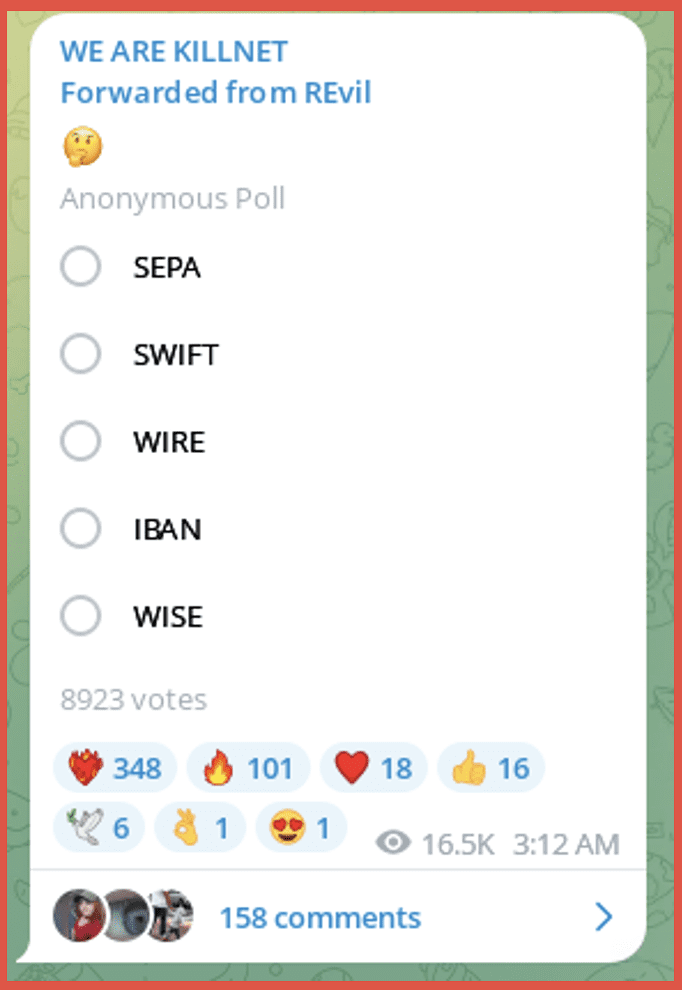
Who is REvil?
REvil is a group that conducted ransomware attacks and was assessed to be based in Russia. The group was successful in targeting a number of corporate organizations including Apple, JBS and Colonial Pipeline. In 2021 the group appeared to be disbanded by joint law enforcement actions and their infrastructure was dismantled. It is unclear if the actors reported to be part of this action were previous members of the REvil group or if they are using their name due to their notoriety.
While there has been some reposting of REvil posts on the Killnet and Anonymous Sudan channels the REvil channel has not reposted anything from the other groups. Furthermore, in later posts by Killnet and Anonymous Sudan REvil is not mentioned which may indicate they are less involved in the activity.
Anonymous Sudan and Killnet Acting Together
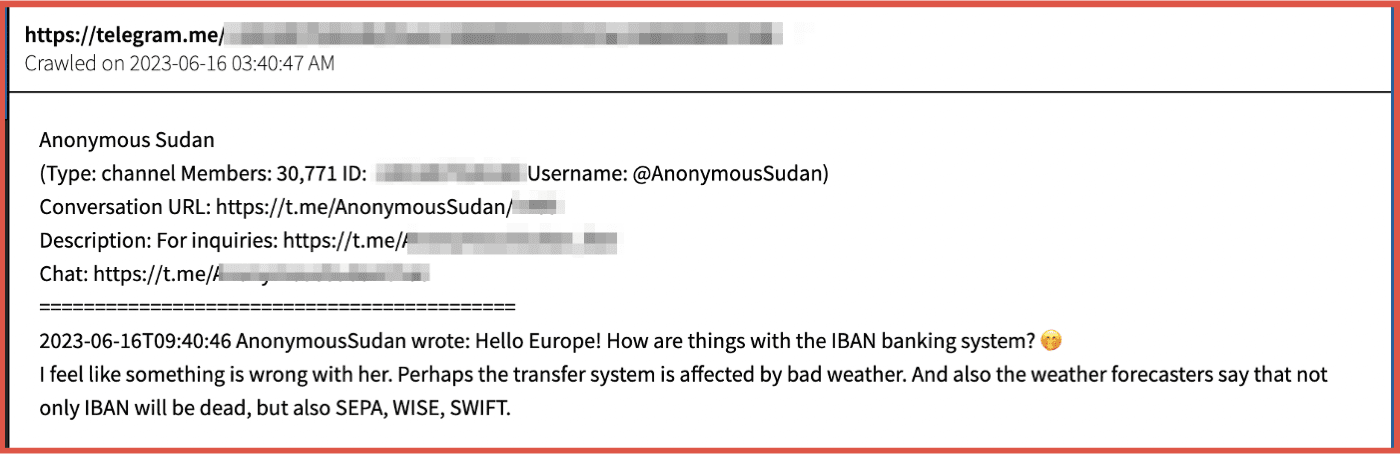
On June 16th, both Anonymous Sudan and Killnet posted a message suggesting that there were issues with the IBAN banking system. No reporting was identified that indicated that this was the case. The below screenshot is from DarkOwl Vision.
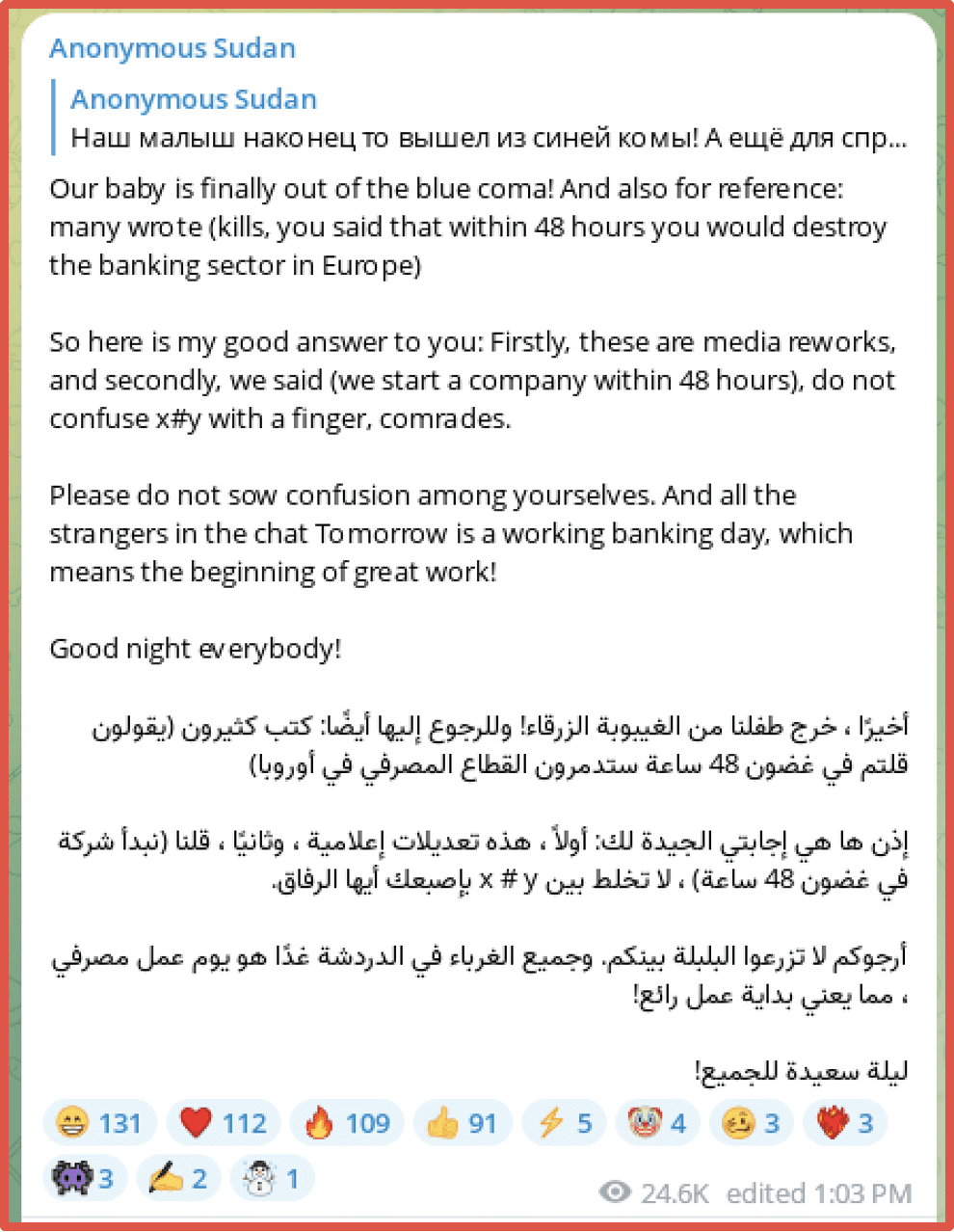
On June 19th, Anonymous Sudan made a post which was provided in both Arabic and English that indicated an attack was imminent and that the timeframe that was reported was made by the media and that they indicated that their attacks would happen in a timeframe not that the results would be evident.
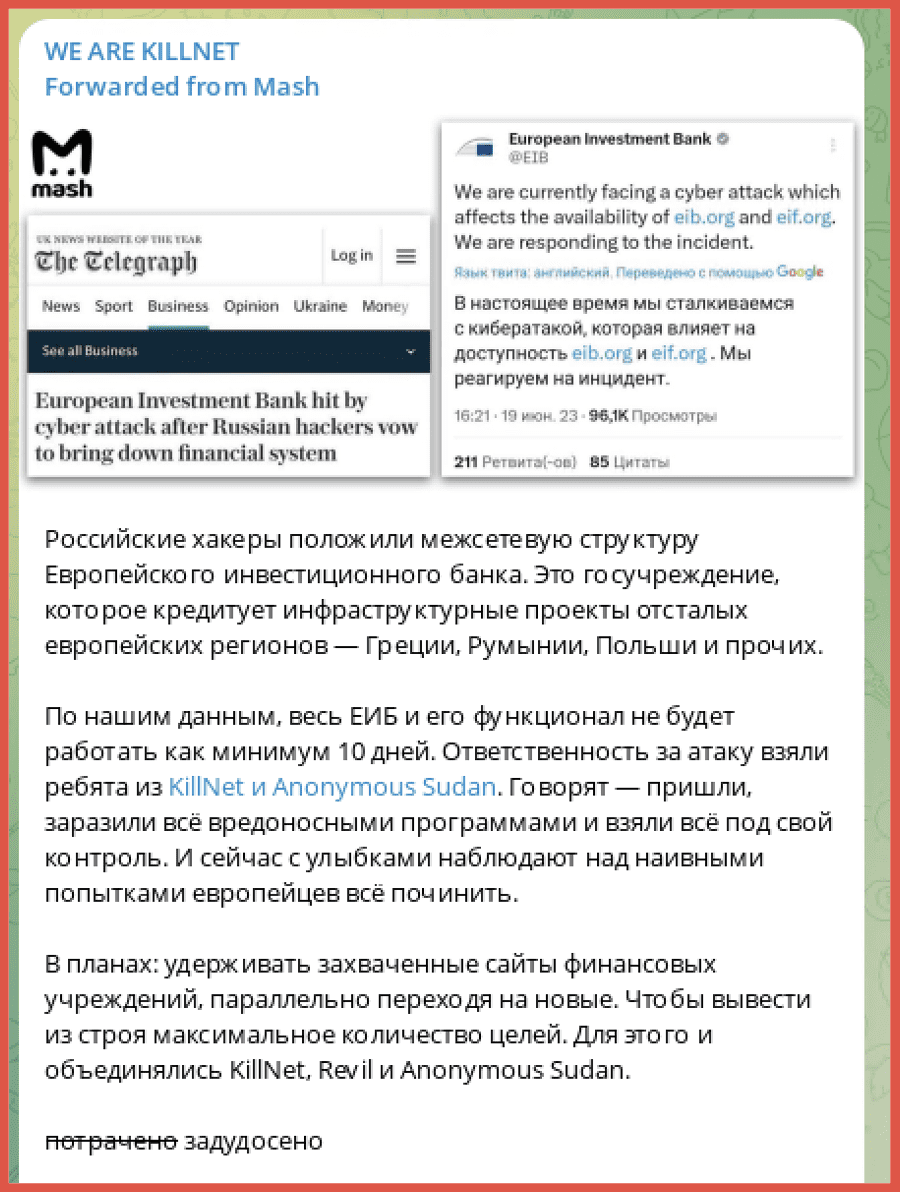
On June 19th, Killnet claimed that they had attacked the European Investment Bank. They provided a post indicating that the attack against the European banking system had begun and provided a screenshot from Wikipedia providing details of the European Investment bank. The message was signed by both Killnet and Anonymous Sudan.
The channel then provided posts which appeared to show that there was an error on a European Investment Bank page.

They then reposted another article from the Mash Telegram channel which indicated the European Investment bank was being targeted by Russian cyber criminals. This included images from the Telegraph, a UK newspaper, and a tweet by the European Investment Bank indicating that they were a victim of a cyberattack. Open-source reporting indicates that the cyberattack was affecting the availability of some of the bank’s websites.
The attack on the European Investment Bank appears to have only effected their websites and is likely a DDoS attack. This is activity both Killnet and Anonymous Sudan have conducted in the past and it is unclear if they have other capabilities that they will utilize. It is possible that the groups were utilizing the name of REvil to suggest they had further capabilities given the groups previous reputation, but there is no data to support this at this time.
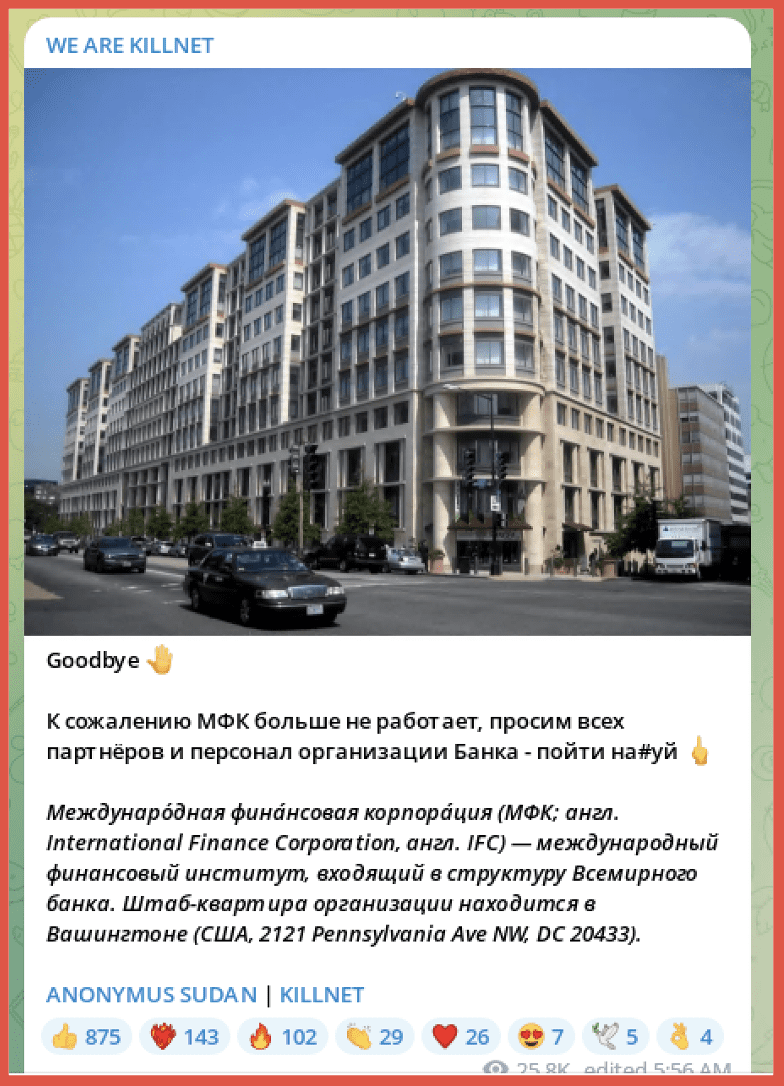
Posted on June 21, Killnet made a claim that the International Finance Corporation (IFC) had been taken down.
[TRANSLATED IMAGE]
Goodbye 🤚
Unfortunately, the IFC is no longer working, we ask all partners and staff of the Bank’s organization to go #uy 🖕
The International Finance Corporation (IFC; English International Finance Corporation, English IFC) is an international financial institution that is part of the World Bank. The headquarters of the organization is located in Washington (USA, 2121 Pennsylvania Ave NW, DC 20433).
No evidence was provided to confirm this attack and no reporting has been identified to indicate that the IFC has been successfully targeted.
Other posts on the Telegram channels are targeting other organizations, reposts from other sources or requests for donations to be made.
Conclusion
While these groups have claimed that they will bring down the European financial system there is little evidence to suggest that they are following through with the threat, furthermore the capabilities that these groups have historically utilized suggest that any attacks which take place are likely to be a DDoS attack. DarkOwl will continue to monitor for any further activity.
Don’t miss an update. Subscribe to our weekly newsletter.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















