A Look Back at the Top Darknet Events of 2021 & Predicting Upcoming Trends
As companies across all industries continue to prepare and bolster their security structure for 2022, DarkOwl analysts have performed a review of key darknet-oriented security events from the past year and summarized them in the list provided below.
For each summary, our analysts also provided a predictive forecast estimating whether the type of threat would continue in 2022. Each event is scored with either the assessment “likely to decline”, “likely to continue” or “likely to escalate.” Additional predictions are found at the end of the look-back analysis.
1. Ransomware Groups Lethality Increases Through Sophisticated Persistence and Detection Evasion
In 2021, ransomware-as-a-service (RaaS) gangs stepped up their operational playbook by utilizing backdoors to maintain persistent access to their victims – which allowed them to retain access both during an attack campaign and then potentially long after ransom payment was applied and decryption keys were released.
One of the most noteworthy examples of this is the widely known botnet Trickbot, which was weaponized and has since been assessed as the arsenal’s of Conti and Diavol RaaS gangs. Dubbed as “Trickboot,” this backdoor operative infects the UEFI/BIOS bootkit. DarkOwl archived their research and observations from the darknet in their WhitePaper titled: Establishing Footholds: A look at Ransomware-as-a-Service from 5,280 Feet earlier this year.
Korean researchers also published their discovery that malware could be installed on some solid-state drives (SSDs) in devices with “flex capacity”, a hidden area called over-provisioning for use by the device manufacturer for optimization. In December 2021, BleepingComputer highlighted that while the technology to conduct such attacks was readily available, there is no indication any such attacks are occurring in the wild – just yet.
THREAT STATUS: LIKELY TO ESCALATE
2. InsureTech Industry Booms In Attempt Underwrite Policies for Cyber Attacks Against Commercial Organizations
A decade ago, we had no construct of the concept of “Cyber Insurance”, nor ever thought such a policy would ever be required. Underwriters are now faced with the challenges of determining the security risks facing an organizations with little statistical data and actuary information to work from. Despite these challenges, the insurtech industry is booming in a race to quantify the risks an ever-evolving threat presents to their clients and themselves.
This year, we witnessed cyber insurer, CNA become a victim of ransomware after Russian criminals encrypted their network with the Phoenix Locker. CNA reportedly paid $30 Million USD to the criminals to gain access to their systems. Shortly after, REvil was spotted taunting their victims with their own cyber insurance policies in attempts leveraged them to pay higher ransoms.
THREAT STATUS: LIKELY TO CONTINUE
3. Critical Supply Chain Attacks Highlight Vulnerability of Software Dependent Systems
2021 was definitely the year of supply chain attacks. Between Kaseya, Accelion, and rounding out the year with log4Shell, cyber criminals uncovered how effective malicious software updates and unpatched dependent software vulnerabilities really were.
- REvil is believed to have exploited over 2,000 victims after replacing Kaseya’s Virtual System Administrator (VSA) software auto-update with their ransomware program.
- Luckily, developers appear to have won the race to patch an Apache log4j vulnerability, with CISA officially stating that other than an attack against the Belgium Ministry of Defence, most log4Shell type-attacks have had minimal impact, e.g. cryptomining, etc.
- DarkOwl uncovered dozens of mentions of malicious Github repositories containing log4j-related exploits on darknet malware forums and discussion groups.
Unfortunately, vulnerabilities similar to the log4j attack vector – malicious remote code execution using the Java Directory Naming Interface – has been uncovered affecting the H2 Java SQL console as well.
THREAT STATUS: LIKELY TO ESCALATE
4. Data Brokers and Access as a Service Surge as Major Darknet Commodity
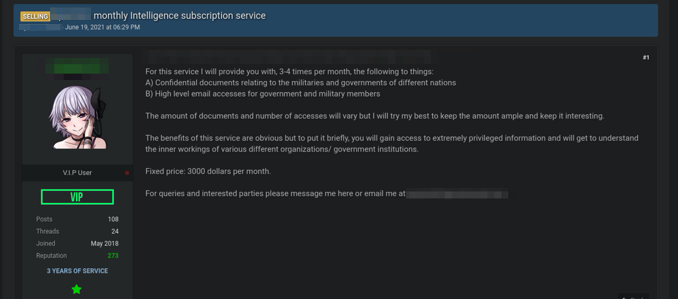
Data brokering has been a viable darknet commodity with offers for databases for sale regularly across darknet and deep web forums. During 2021, DarkOwl observed “access-as-a-service” develop as a major darknet commodity serving RaaS operators and organized cyber criminal groups. For example, some “initial access brokers” offered for auction a domain administrator credential for a potential multi-million dollar victim on some popular darknet forums. Such credentials sell quickly at upwards of $30,000 USD.
Other criminals offer subscription model data services with persistent access to sensitive and confidential intelligence for a monthly fee.
THREAT STATUS: LIKELY TO ESCALATE
5. Infamous REvil Gang Finally Shut Down, But Over a Dozen New RaaS Gangs Emerge Shortly After
In October, Tor sites for REvil went officially offline signaling an end to their operations after the FBI compromised the server backups for the notorious RaaS gang. DarkOwl witnessed and detailed darknet forum drama shortly after their disappearance.
Despite their departure from the RaaS scene, LockBit has stepped up to assimilate the surviving REvil affiliates and has increased their operations considerably.
DarkOwl has detected over a dozen new Raas groups emerge in the last 90 days including Sabbath, Cerber 2021, and Khosari.
THREAT STATUS: LIKELY TO CONTINUE
6. Attacks Against Healthcare Organizations by Cyber Criminals and RaaS Groups Despite Claims They Would Not Target Medical Industry
In the last year, attacks against HealthCare groups have increased exposing a significant volume of patient personally identifiable information (PII) in the dark web.
Hundreds of hospitals have been impacted by ransomware resulting in turning away patients who need critical care. It’s unclear how many deaths and/or preventable injuries have occurred as a result of ransomware and cyber criminal campaigns against medical institutions.
DarkOwl has observed several adjunct medical groups, optometry, pharmacy, and DNA diagnostics centers’ data for offer on darknet markets.
Previously, RaaS gangs had demonstrated some veil of morality claiming they would not target the medical industry.
THREAT STATUS: LIKELY TO ESCALATE
7. Unemployment and COVID Related Fraud Skyrocketed
In 2021, darknet fraudsters continued to exploit government subsistence programs for unemployment and small business funding. DarkOwl estimates the going rate for a detailed unemployment fraud method varies between $200 and $300 USD and offered specifically by state, suggesting that different state unemployment systems may require unique techniques for direct exploitation.
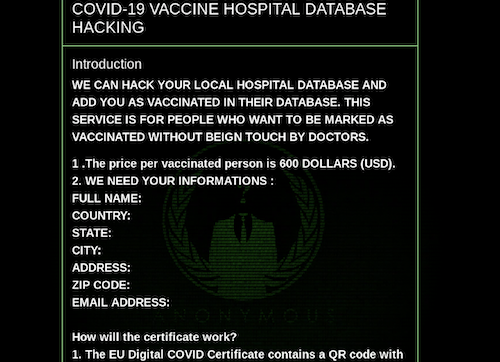
Further, DarkOwl uncovered that the darknet has numerous offers for COVID testing and vaccination related fraud such as negative PCR test results for testing and COVID vaccine certificates for as little as $150 USD.
THREAT STATUS: LIKELY TO DECLINE
8. Increase in Darknet Marketplaces Use of Alternative Cryptocurrencies
DarkOwl found that the total number of darknet marketplaces tripled by the end of the year and 86% of the active markets support Monero in addition to Bitcoin. In recent years, darknet criminals have been demanding currency alternatives to the traceable Bitcoin be available and Monero appears to be the leading contender in darknet marketplaces.
Many of the markets also accept Litecoin, but less-trusted coins are also seeing some acceptance. Global Dreams Market surprisingly accepts DogeCoin and Evil Corp Market began accepting Dash earlier this year.
Additionally, the infamous darknet marketplace, AlphaBay came back to life and re-surged use of I2P peer-to-peer network.
THREAT STATUS: LIKELY TO CONTINUE
9. Colonial Pipeline Ransomware Attack Highlighted Critical Infrastructure Risk
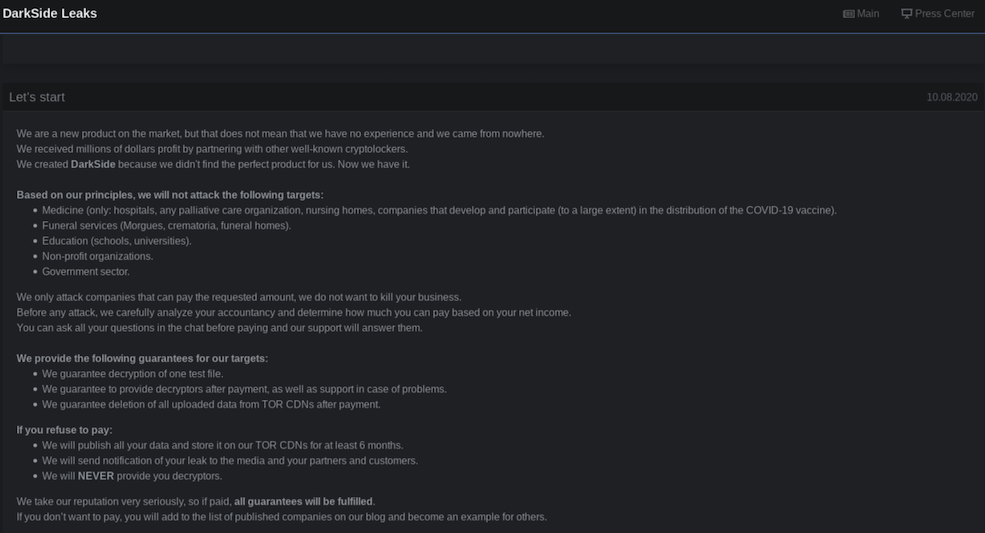
In early May 2021, Colonial Pipeline was forced to shutdown its pipeline after suffering a ransomware attack carried out by the RaaS organization known as DarkSide. The criminal gang successfully accessed Colonial’s networks simply using the credentials for an old VPN account that the group had discovered on the darknet. Colonial did not have multi-factor authentication (MFA) turned on for the account, which could have prevented the intrusion.
The shutdown caused shortages of fuel across the Southeastern United States and resulted in increased fuel prices and economic impact for months afterwards.
The ransomware attack highlighted how vulnerable critical infrastructure is and the immediate and pressing need to shore up critical utilities and telecommunications infrastructure networks from future attacks. Not only are the services rendered unusable for a significant amount of time, but the financial impacts ripple throughout the economy and destabilize the supply chain.
THREAT STATUS: LIKELY TO CONTINUE
10. 8kun Reputation Hit by Jan 6th Insurrection; Surge in Activity Across Alternate Darknet Imageboards
After the violent siege on the U.S. Capitol on January 6th did not result in former President Trump being declared winner of the 2020 U.S. Presidential Election, 8kun enthusiasts and Qanon followers from the murkier corners of the dark web were greatly disenchanted that Q’s predictions of a real-life political “reckoning” for the alleged deep state cult never were realized.
As a result, in 2021, 8kun (a.k.a. 8chan, led by Ron and Jim Watkins) became less popular in the darknet as many MAGA believers who frequented the dark web service left to return to their lives and the reality that Biden was officially U.S. President.
There was also plenty of fear at increased law enforcement surveillance on the board as they searched for alleged participants in the January 6th riots.
This fear also led to many ‘anons’ dispersing to other existing Imageboards on the darknet and the formation of new “chans” around the deep web. In the summer of 2021, DarkOwl identified over two dozen new Imageboards — not affiliated with 4chan or 8kun — many in non-English languages supporting the refugee. Over the year, board chatter focused around COVID-specific conspiracies and misinformation campaigns centered on vaccine safety and efficacy as well as international rules regarding quarantine, travel, and vaccine mandates.
THREAT STATUS: LIKELY TO CONTINUE
11. Iran and Israel Continue Shadow Cyber War
In the last year, DarkOwl has witnessed a surge in Iranian and Israeli-specific leaks on the darknet signally an escalation of the shadow cyber war between the two countries. Similarly, new ransomware groups, like Moses Staff — likely affiliated with Pay2Key and/or BlackShadow — attack critical targets in Israel without demanding ransom payment, suggesting the attack is politically, not financially motivated. In November, Israel’s Cyber Unit claimed responsibility for shutting down websites for BlackShadow after the cyber criminals leaked the user database from a popular LGBTQ+ dating app, Atraf, in Israel.
In October 2021, over 4,300 gas stations across Iran was inoperable due to a cyberattack, possibly as a result of on-going conflict with Israel. Shortly after, on the anniversary of the death of Iranian general Qassem Soleimani, two Israeli media websites were defaced with an ominous message on his behalf and an image of a fist and missile striking Israel’s nuclear facility at Dimona.
The two countries show no sign of slowing down their cyberattacks against each other and security researchers around the world fear their conflict will impact Western nations’ infrastructure at some point in the future.

THREAT STATUS: LIKELY TO ESCALATE
12. Tor Deprecation Changed The Shape, Volume, and Perceptions of the Darknet
Last October, users of the darknet braced themselves for the deprecation of the historical v2 “hidden” onion service expecting a concerted network shift to the more secure v3 onion service domain architecture. With many relays still operating versions of old Tor executables, that did not exclude routing v2 services, many domains we expected to disappear overnight persisted, weeks later. After the Tor Project released version 11.0.1 of the Tor Browser Bundle, all historical onion services were no longer accessible from the web browser. DarkOwl estimates this resulted in the disappearance of over 64,000 active domains.
In addition to Tor, privacy enthusiasts and long-time darknet users have been eagerly exploring other anonymous “dark” networks, including meshnets like Yggdrasil and web 3.0 networks like Peernet. We anticipate use of such networks to increase in the near future.
THREAT STATUS: LIKELY TO ESCALATE
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















