Maze Hackers Release Press Statement on their Darknet Website Naming New Victims
On July 9th 2020, the hackers behind the infamous and malicious Maze ransomware-as- a-service (RaaS) malware released a press statement on their Tor hidden service outlining new terms and conditions for their operations in light of the economic crisis and global pandemic.

Figure 1: Screenshot of Maze Statement
The press announcement further included instructions for their latest ransomware victims, including five key points outlining a post-hack timeline for victim negotiations and subsequent data publications. The announcement listed their intended victims – alleging they had already been compromised – and now are seeking payment from them before releasing their data to the public. These victims include large corporations such as Xerox and LG ELECTRONICS.
The hackers stated they will publish notice of successful hacks along with the victim’s name within three days of the attack. The victim organization must start communication within the 72-hour period post hack. The list of organizations they publicly announced as their targets included in the following screenshot:
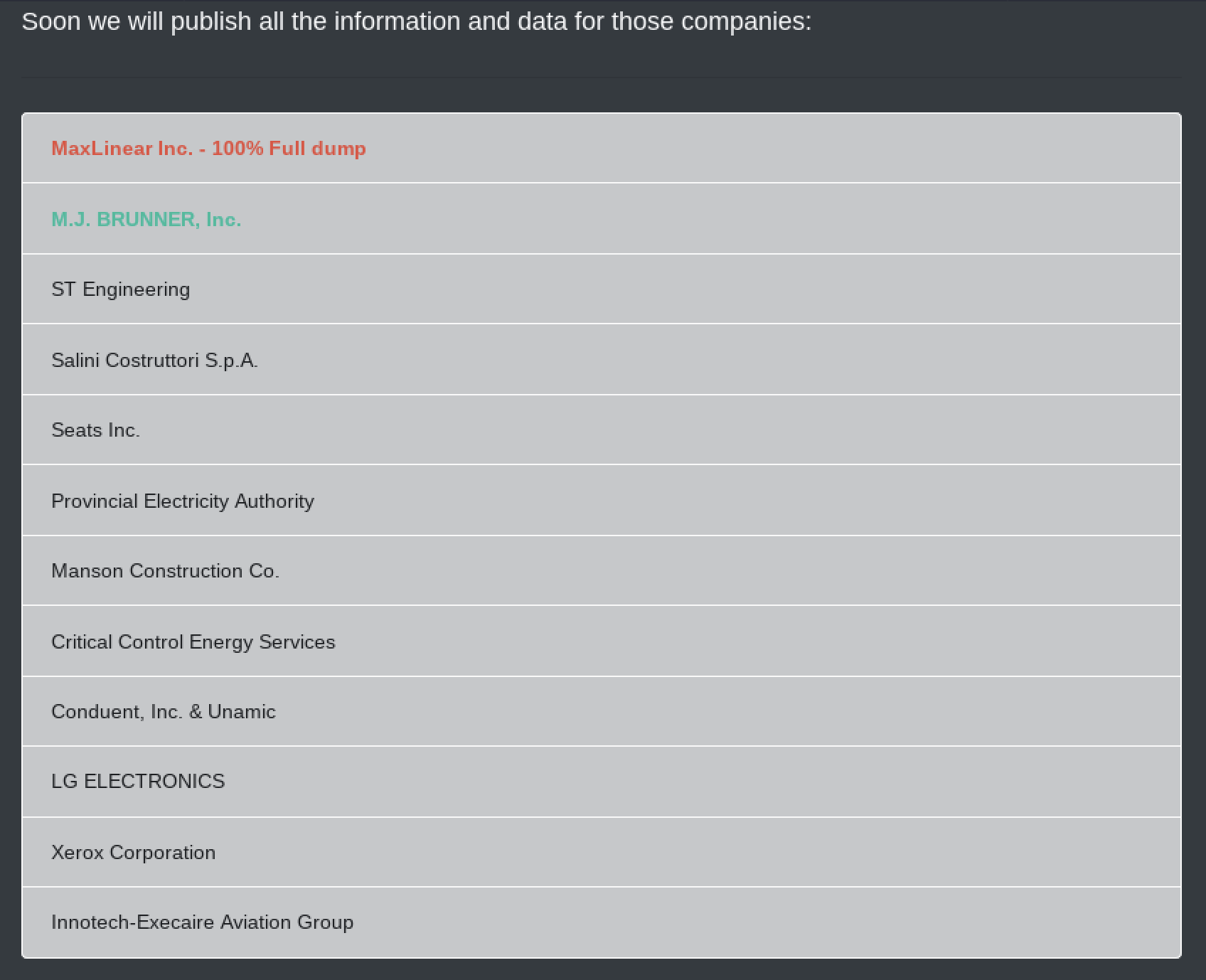
If successful negotiations do not occur within ten days, Maze claims that all of the organization’s ransomed data will subsequently be released to the public. This is contrary to the REvil hacker’s approach of auctioning or selling the compromised data (as opposed to releasing it for free). The Maze hackers also allude to “no more delays of a month or two” suggesting some compromised organizations were possibly using stall tactics to delay publicizing the attack.
Presumably as a means of further intimidating their victims, the Maze hackers also state that upon data release for reach of their victims, they will also be contacting their victim’s partners, clients, and regulators to increase the impact of their attack and damage to the reputation of the compromised organization and company value.
The hackers included a closing statement on how they are proud of their reputation and that ironically, “honesty is their revenue” along with a list of a dozen organizations they are extorting that would soon have their data published.

Figure 2: Screenshot of Maze Statement
DarkOwl analysts noted that the language used in the hackers’ press release lacked proper grammar confirming English is likely not the hackers’ first language. The hackers also elaborated how the victim’s inability to connect to the Maze website chat or negotiate due to fear is their own fault — even stating they are not “physiologists” (probably intending here to state psychologists) and are unable to understand their victim’s behavior patterns.

Figure 3: Screenshot of Maze Statement
NOTE: DarkOwl has chosen to include the names of the most recent victims in this blog at present due to the fact that they are publicly available.
For more information about Maze and other RaaS sold or traded on the darknet, contact us to setup a trial using Vision to monitor and alert you if your company is being targeted or mentioned on the darknet.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















