New Princess Ransomware Surfaced Earlier than Reports Suggest
News broke out mid-August that Princess Evolution, a revamped form of the infamous Princess Locker ransomware that was first seen several years ago, is back with a fresh toolkit (see this article for example).
News coverage at the time suggested that the Princess Evolution ransomware had only recently surfaced. However, after further digging into the “newly uncovered” iteration of the ransomware, DarkOwl analysts discovered that Princess Evolution has actually been offered on darknet marketplaces dating as far back as this past April.
What is the Princess Ransomware?
Princess Evolution is a form of ransomware that encrypts most files on the infiltrated computer system and holds them hostage until the targeted user pays enough money to regain access to them. During the encryption process, the ransomware changes affected file extensions to a randomly generated string of characters.
To notify the targeted party that their files have been compromised, users are notified via a ransom note telling them that their files are locked, followed by instructions on where and how to pay the ransom sum. As of August 8 2018, users were instructed to pay the amount of 0.12 bitcoin (equivalent to US$773 as of that date). The malicious software is currently being advertised on 0day forum as RaaS (ransomware as a service) and is soliciting associates to help spread the malware to unsuspecting victims.
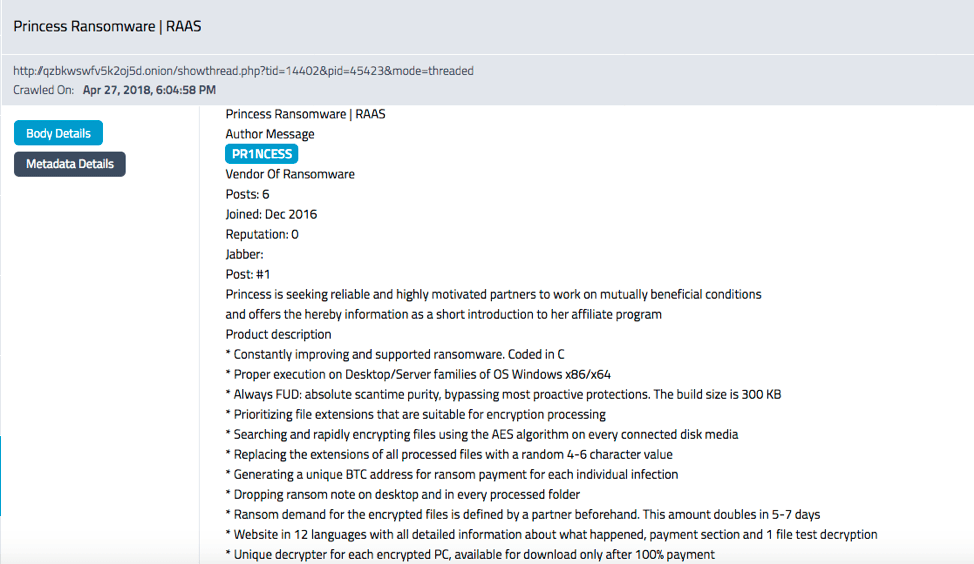
Screen capture of a DarkOwl Vision result – scraped in April of this Year – that depicts the ransomware Princess Evolution being sold on a darknet marketplace.
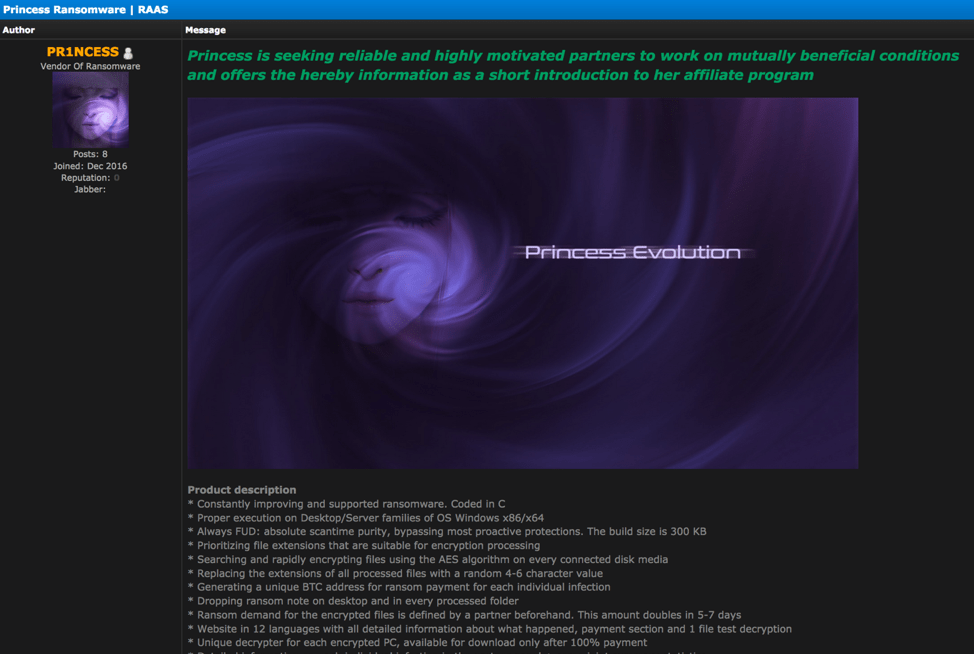
A similar posting on 0day forum; responses haven’t slowed down since the original post earlier this year.
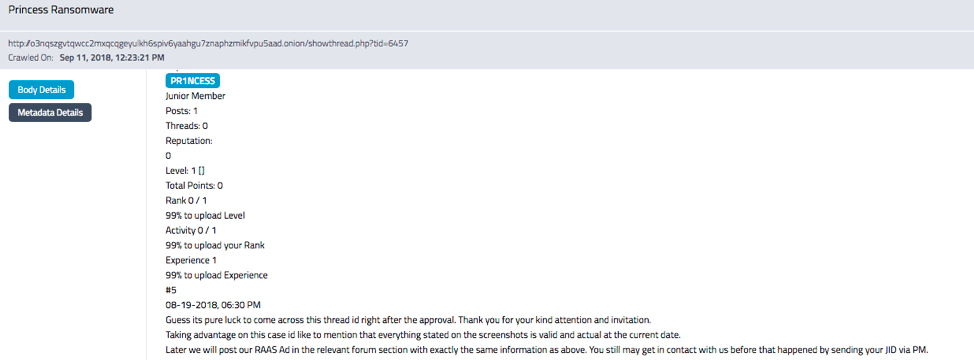
Interested members are instructed to leave their Jabber ID as a thread comment or to send it in a private message to the 0day account “PR1NCESS.” Our analysts calculate that there have been over one hundred comments from individuals interested in joining the campaign since the original post scraped by DarkOwl Vision in April.
Images: (Above, Right) Profiles of PR1NCESS on Codex and Kickass forums.
What is 0day?
0day is a popular darknet carding and hacking forum first established in 2015. Users are required to register an account before accessing any content on the forum. Additionally, once registered, user accounts must go through an activation process to receive full access to the forum.
The forum’s main purpose is to act as a marketplace for buyers and sellers of illicit goods, such as stolen credit cards, hacked accounts for legitimate websites, malwares and exploits, as well as other services. Some prolific sellers also advertise their own websites in the message boards.
The below image shows just a sample of the items offered for sale on 0day, as captured in DarkOwl Vision.
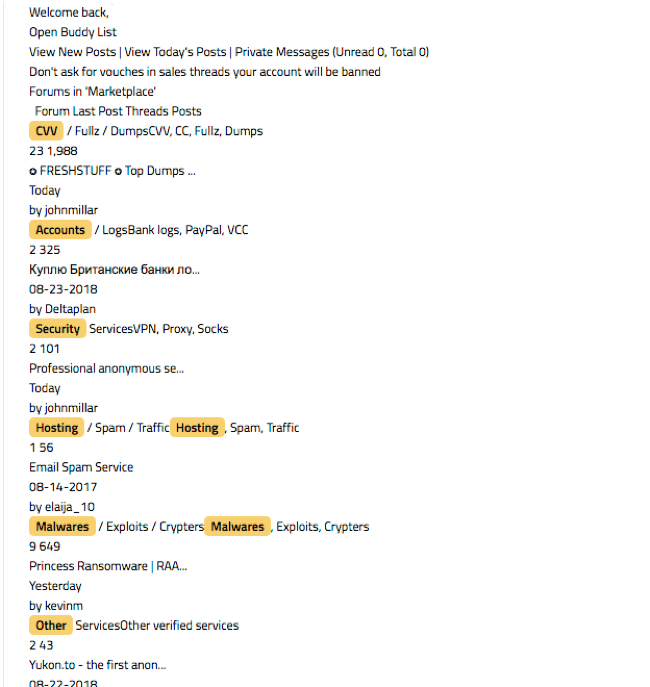
Example of items being sold on the 0day forum.
So, what should you do if you find yourself infected with the Princess Evolution ransomware? We recommend that you refer this article, which has a great step-by-step guide for regaining control of your computer and your files: https://www.pcrisk.com/removal-guides/10531-princess-ransomware. And, as always, organizations should continue to be proactive against ransomware threats by adhering to security best practices and actively educating all of their employees on their internal security plan.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















