Q3 2023: Product Updates and Highlights
October 13, 2023
Read on for highlights from DarkOwl’s Product Team for Q3, including new exciting product features.
New Leak Context Feature
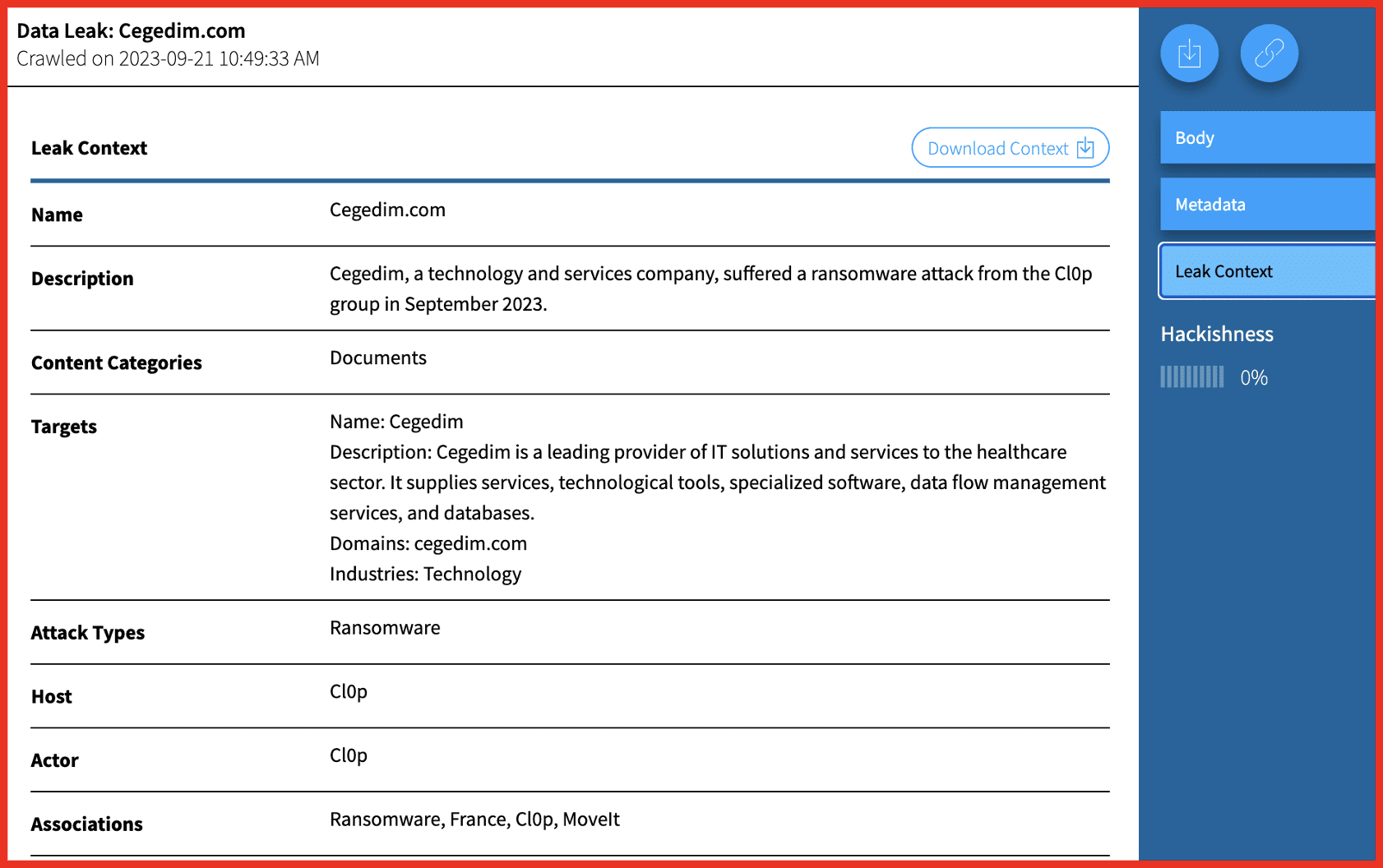
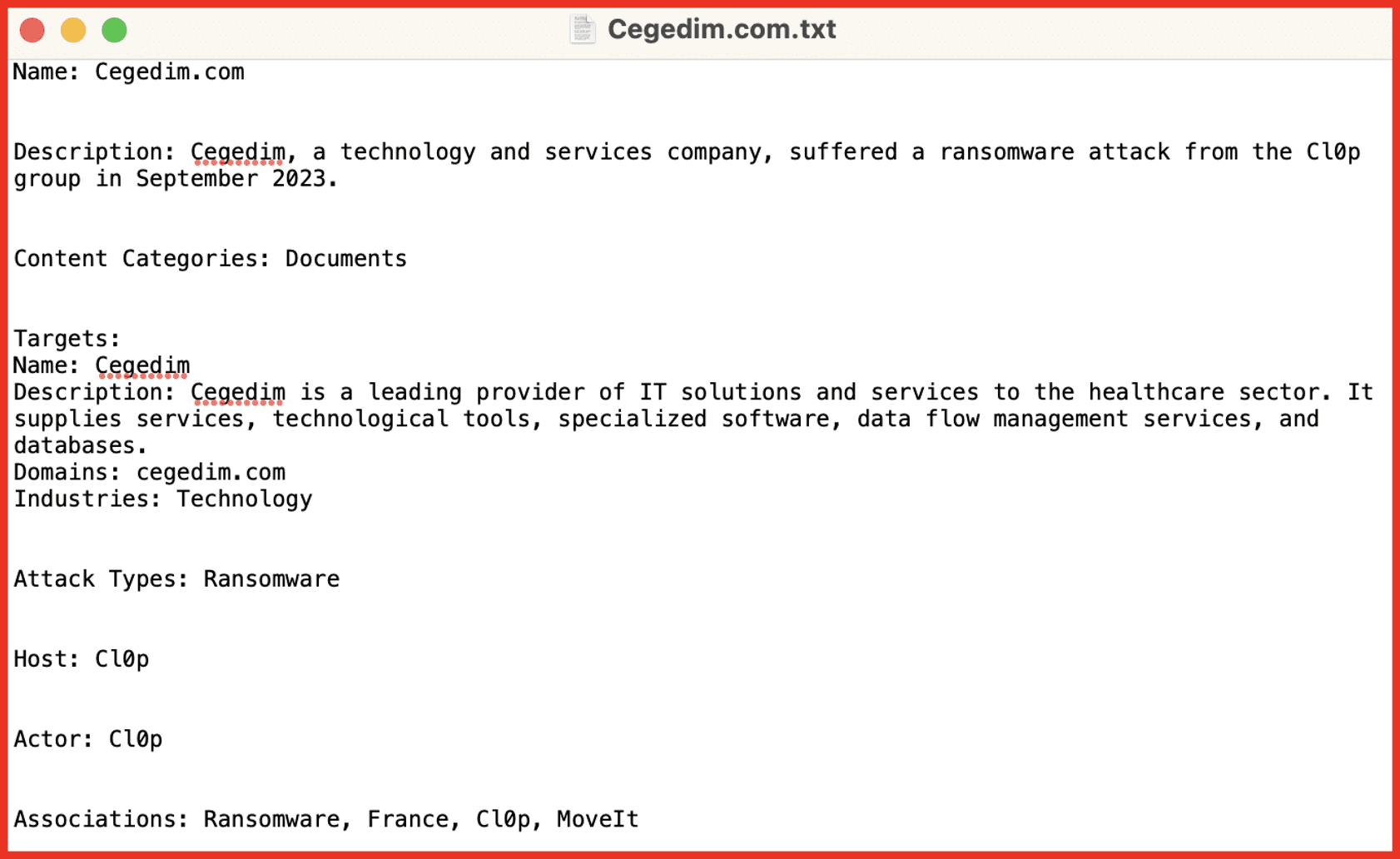
When your search results are from data leaks, you can now review additional information curated by DarkOwl analysts, giving you enrichment on the data leak, “Leak Context”. This new section includes a description of the leak, details on the the target organization, date posted, date of event (if known), and the type of content exposed. Additionally, there is a new option to Download Context (as a .txt file) to include in reports or briefings. An example from Vision UI can be seen below. Beyond the UI, Leak Context is also available programmatically through a new Leak Context API endpoint.
Vision UI & Vision API Updates
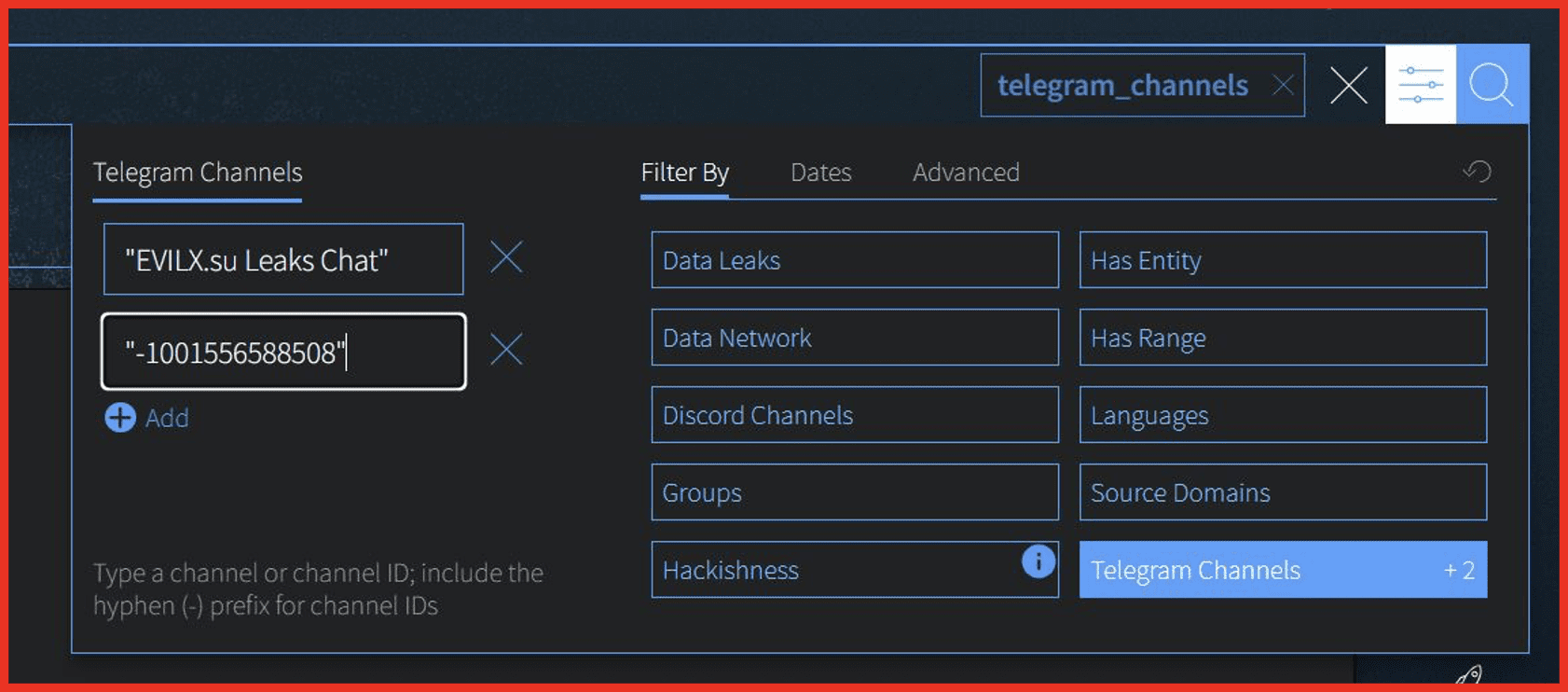
Chat Channel Filters
Filter your search to one or more channels or servers from Telegram or Discord using the Filter Menu in the UI or new API parameters. This allows you to track individual channels of interest instead of the whole chat network.
Chat Users Search
A new Chat Users search option allows you to find discussions from particular usernames or user IDs within Telegram or Discord.
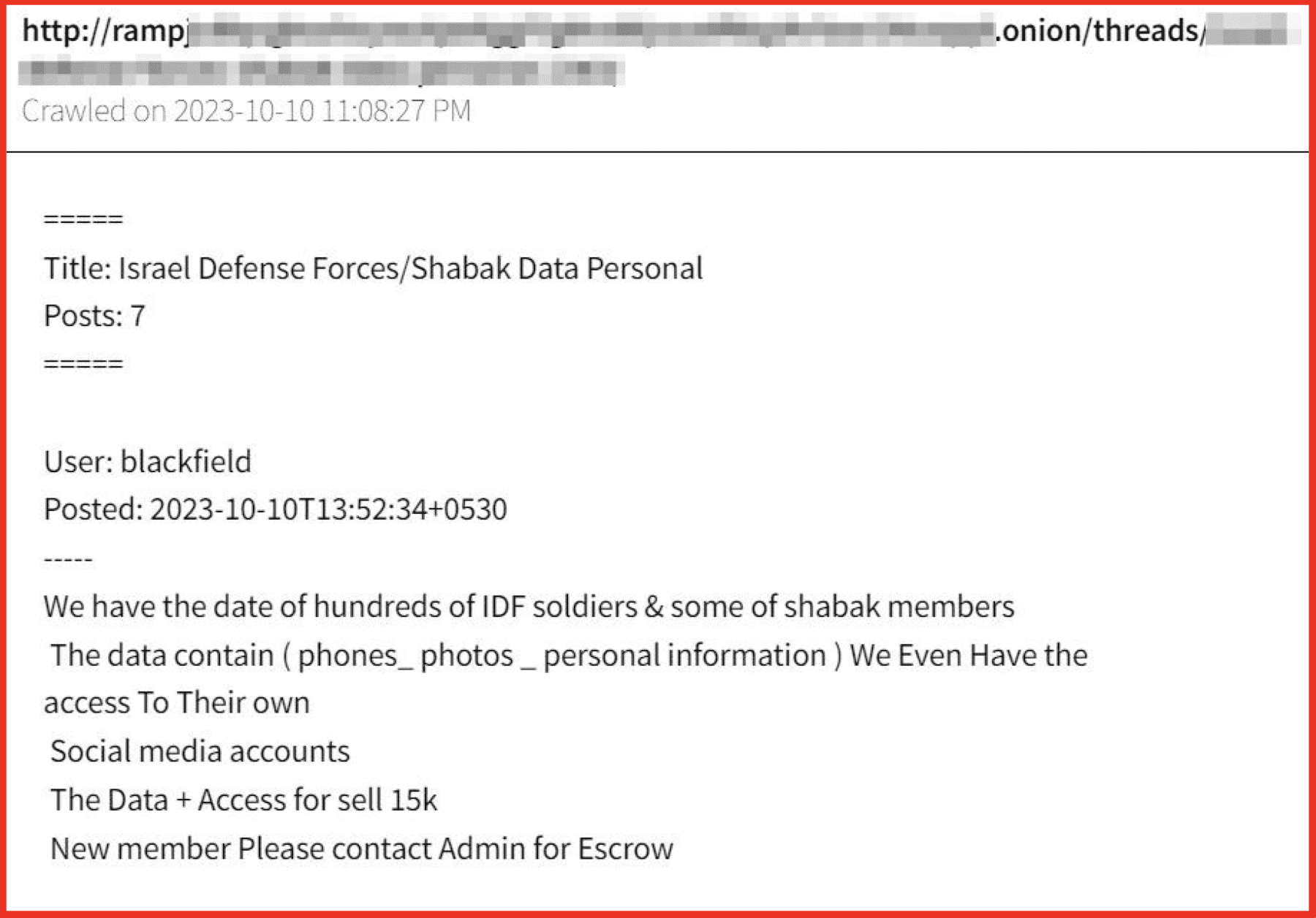
Enhanced Forum Presentation
More than 100 forums are now in our new thread-view structure. This allows users to easily distinguish thread Titles, number of Posts (at time of collection), Users, Post Dates, and the Post Bodies.
Lexicon Updates
DarkOwl Vision’s DARKINT Search Lexicon is an easy-to-use tool intended to help users find interesting content within our database. This quarter, the team built out 99 additional Lexicon queries to help our clients find the most important sites to them, including:
- 15 new ransomware entries
- 46 new forum entries
- 38 new market entries
Clients can always submit content for us to add. Curious what DarkOwl means by “DarkInt?” Check out our full write up.
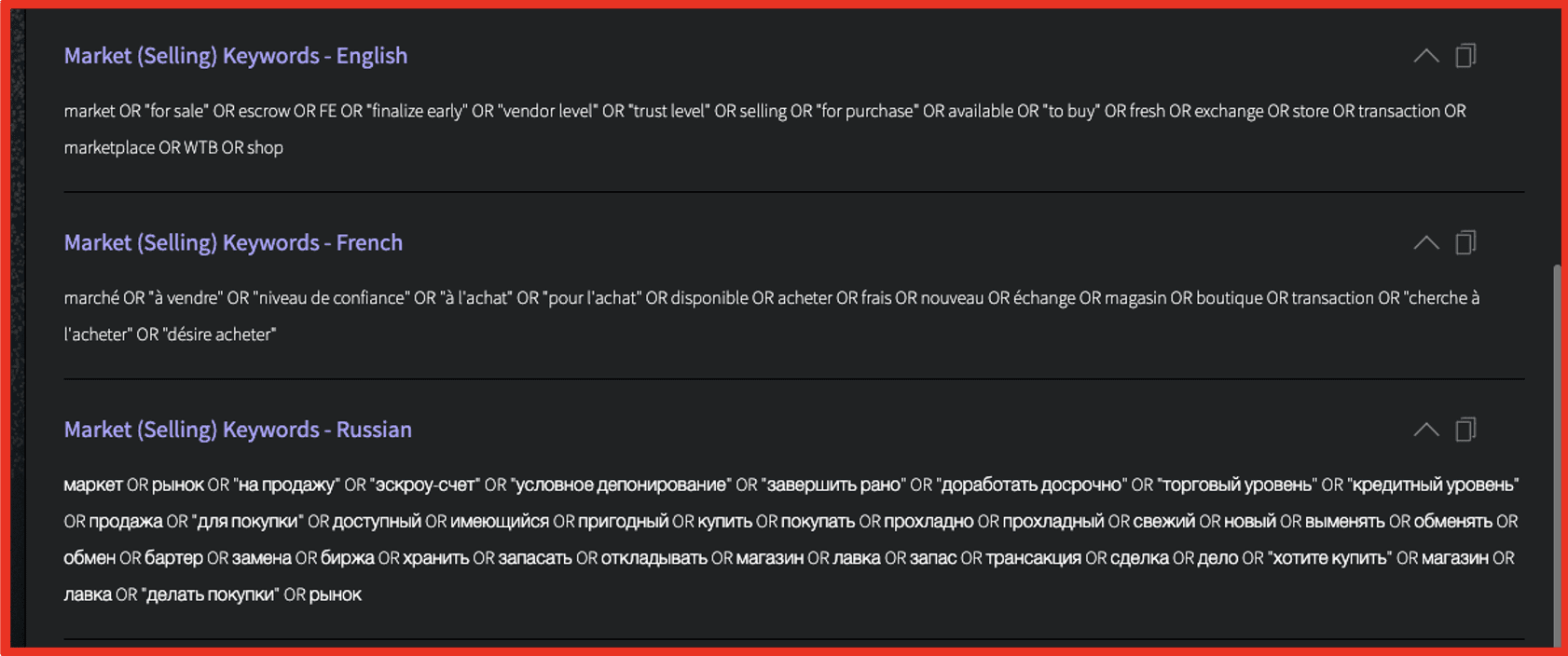
Translations
The team has added 10 new translated Search Blocks, including Russian, Spanish, and French, with more on the way!
Leaks of Interest Collected
Nato Data
Data allegedly retrieved from NATO’s Cooperation on Opportunities and Innovations (COI) portal that was leaked on SeigedSec’s Telegram channel in July 2023. According to the post, “this attack on NATO has nothing to do with the war between Russia and Ukraine, this is a retaliation against the countries of NATO for their attacks on human rights…” Data includes hundreds of documents.
5M Shanghai Suishenma
Suishenma is the Chinese name for Shanghai’s health code system, which the city of 25 million people, like many across China, established in early 2020 to combat the spread of COVID-19. All residents and visitors have to use it. The leak includes scan time, if they are a foreigner, company name, name, credit card and scan method.
cegedim.com
Cegedim, a technology and services company, suffered a ransomware attack from the Cl0p group in September 2023. The leak contained multiple documents, including financial information, email addresses, IP addresses.
pwc.com
PWC was a victim of the MoveIT vulnerability executed by the ransomware group CL0P. The leak contains a number of documents relating to the organization as well as email addresses, IP addresses, and technical information.
duolingo.com
In January 2023, an actor was selling the scraped data of 2.6 million Duolingo users on the BreachForums hacking forum. Subsequently the data, including names, emails, languages learned, and other Duolingo-related information, became available without payment.
On the Horizon
Be the first to hear an exciting announcement from the DarkOwl team – we are about to launch something you will not want to miss! To get a preview of this new release, schedule a time to speak to one of our team members.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















