Review of Ransomware Gang Activity Since Ukraine Invasion
In light of disturbances in the darknet due to nationalistic fractures amongst ransomware and cybercriminal groups, DarkOwl analysts did a cursory review of activity across ransomware-as-a-service (RaaS) gangs since the invasion of Ukraine.
We reviewed the number of reported victims by RaaS groups and the location of the victims, and determined the following:
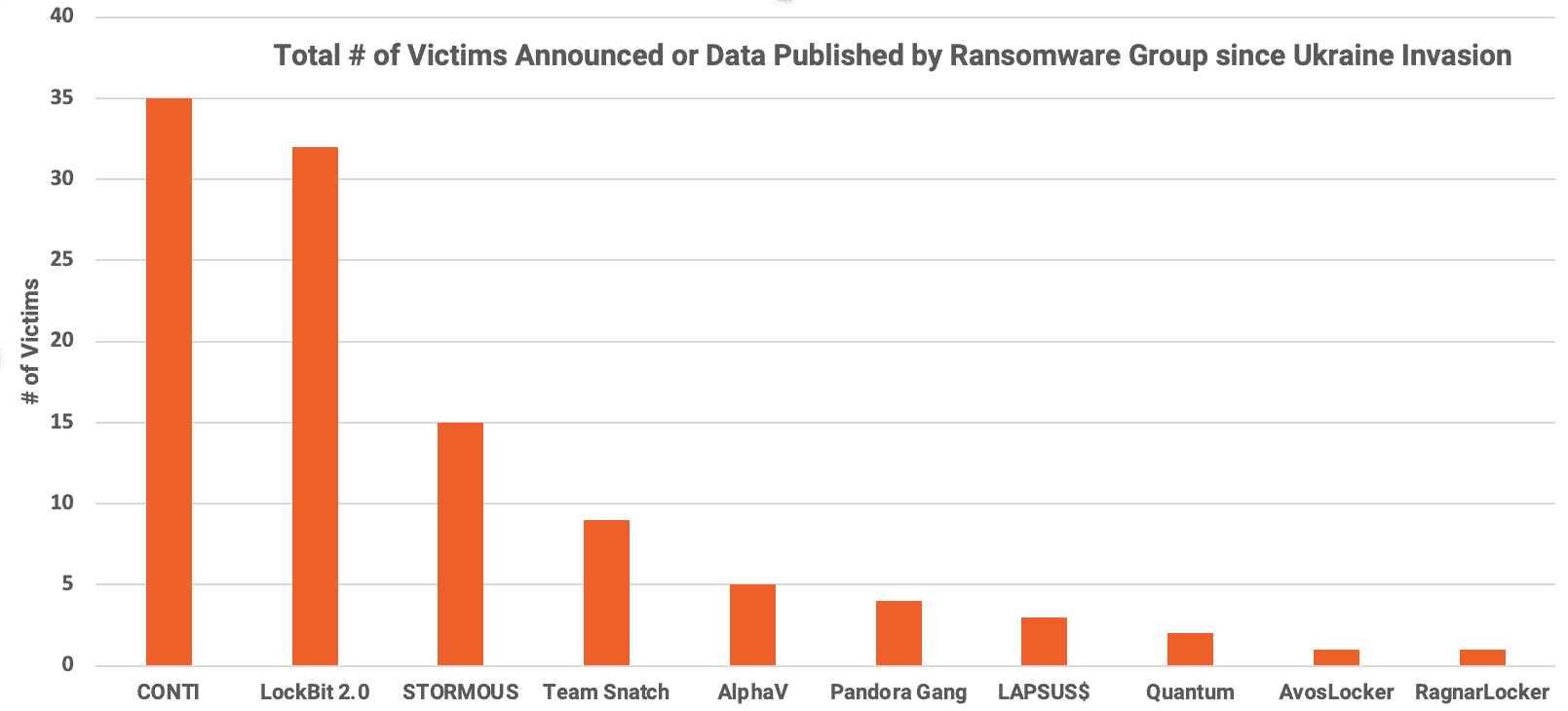
- Conti and Lockbit 2.0 lead in total number of victims announced since the 24th of February, 2022.
- Conti was offline for almost a week due to infrastructure leaks and fractures with their Ukrainian-aligned affiliates. Since March 1st, the group has resumed locking and leaking victims’ networks around the world.
- Several key Tor services for well-known RaaS gangs, including Pay2Key, Blackbyte, Cuba, are online and active; however, they have not shared any victim’s data since the invasion on February 24th, 2022.
- A new RaaS group called Pandora Gang hit multiple victims in a matter of days, including two victims from Japan.
- STORMOUS ransomware has been heavily targeting Ukraine.
- STORMOUS most recently attacked 4A Games (Ukraine) and EPIC Games (US).
- Given the severity of the attacks against Nvidia and SAMSUNG, LAPSUS$ is now being categorized as a RaaS gang, even though they do not have an affiliate program that we are aware of.
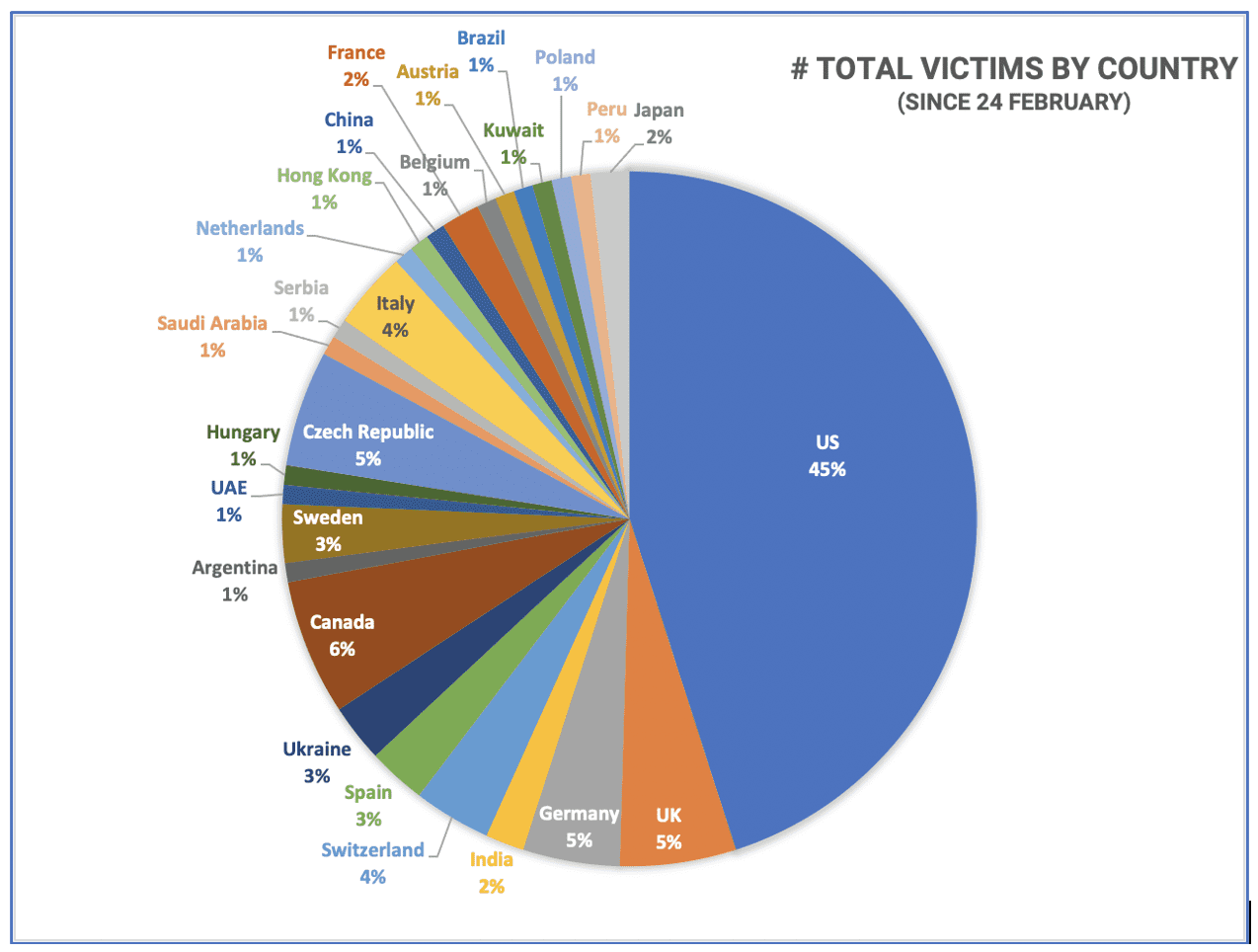
- US, Canada, UK, Czech Republic, and Germany have the highest volume of ransomware victims in the distribution of victims by location published in the last two weeks.
- Many ransomware victims have direct connection to US and Western critical corporate/government operations and supply chains.
NOTE: The charts below do not take into consideration attacks by Russia against Ukraine networks in conjunction with HERMETIC WIPER attacks or leaks released by Free Civilian. The totals, as reported by the Ukraine government, would exceed that of those counted here for the US.
LAPSUS$ Group: Additional Findings
The cybercriminal group LAPSUS$ has ramped up their activities since the invasion – emboldened by their attacks against Nvidia and SAMSUNG.
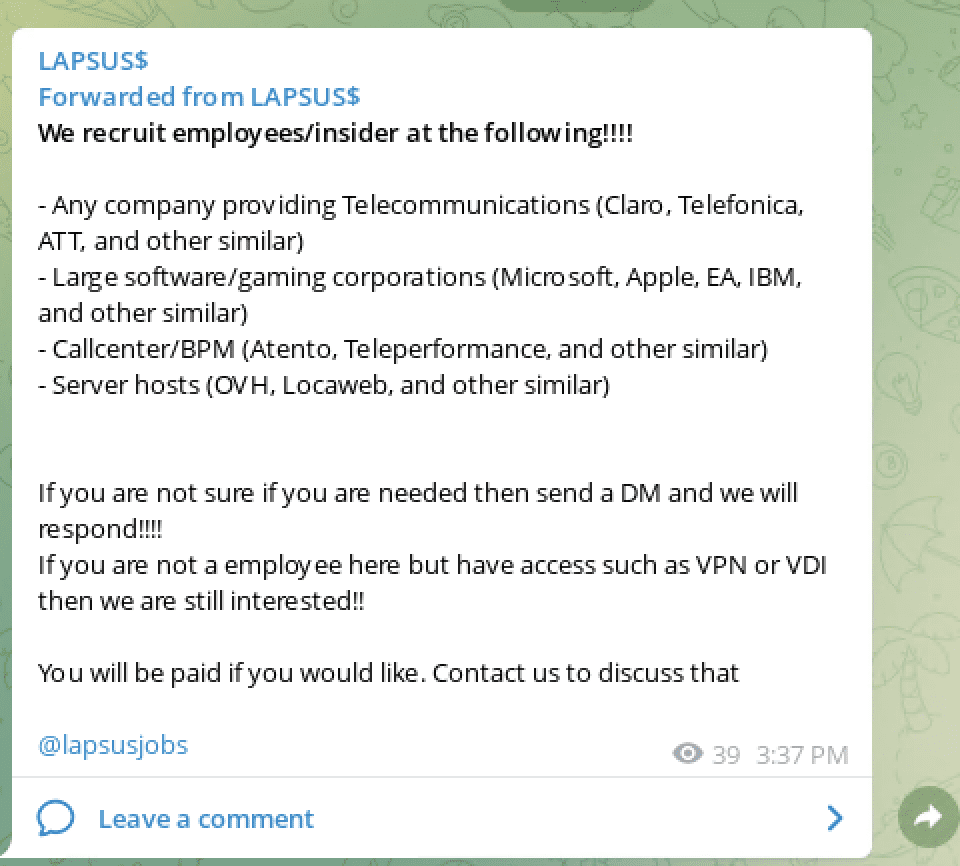
They recently solicited experts in various specific industries for their next victim selection, possibly looking for insiders to assist. Telecommunications, software development/gaming, hosting, and call-centers were among the industries requested.
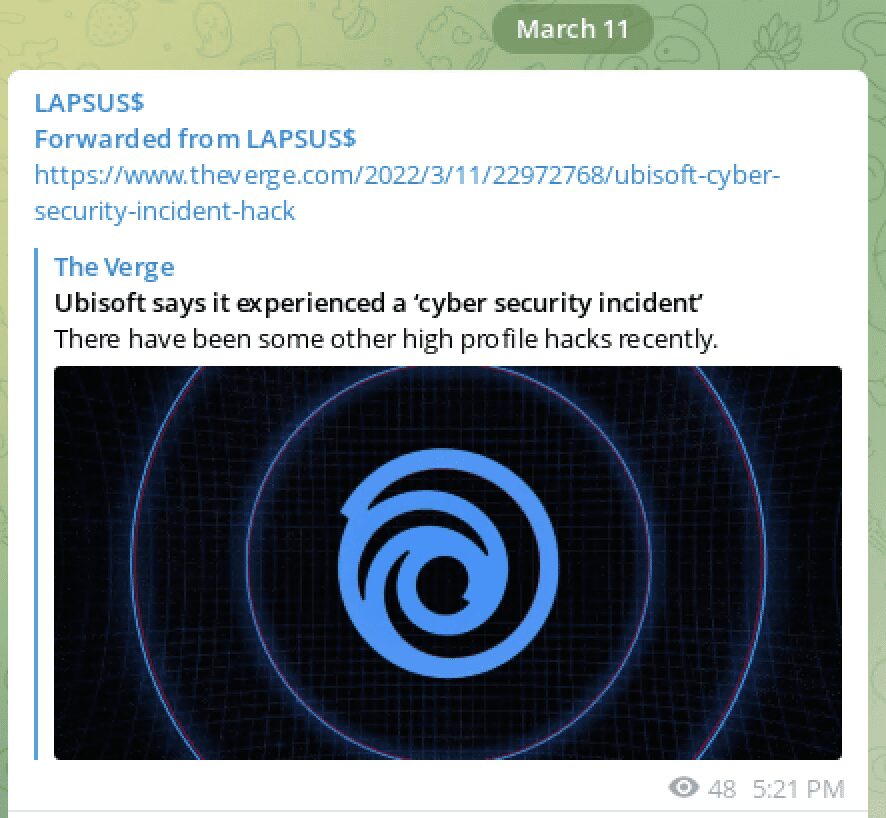
Over the weekend, LAPSUS$ also implied they were responsible for recent “cybersecurity incident” with Ubisoft.
DarkOwl will continue to monitor RaaS activity and update as new information becomes available.
Curious about something you read? Interested in learning more? Contact us to find out how darknet data applies to your use-case.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















