Review of CL0P’s Zero-Day Exploit Against MOVEit
Updated August 02, 2023
Reviewing Victims on DarkOwl’s DarkSonar API
While ransomware attacks have continued to grow in 2023, the recent attacks leveraged by CL0P against the MOVEit file transfer software have garnered much publicity. Additionally, the zero-day exploit against the MOVEit software has led to huge data theft and extortion attacks.
On June 7th, CL0P began posting the names of the victims they had successfully targeted. By July 11th, they had listed 140 companies which had been compromised. These companies were from a variety of industries as illustrated in Figure 1. These attacks highlight the risk posed to organizations through third parties who have access to sensitive information relating to some of their clients.
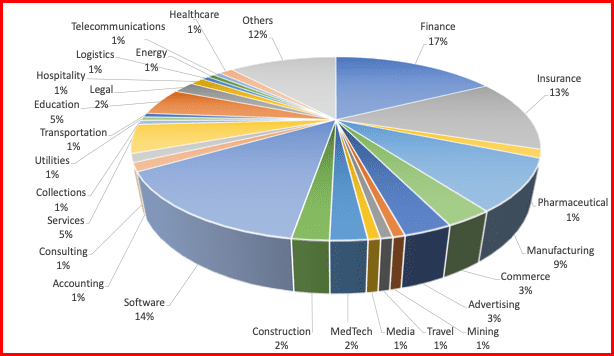
Figure 1: Breakdown of industries targeted by CL0P
DarkOwl’s DarkSonar risk signal can be used to forecast cyber threats to an organization by measuring the relative risk rating for an individual domain. Additionally, organizations can measure the risk of third parties who have access to sensitive data. An elevated signal is a cause for concern as it shows a dramatic increase in relative risk, providing warnings of potential threats. We tracked DarkSonar in the weeks and months leading up to the attack for all 140 company domains to see if there was an elevated signal. The results are shown in Table 1. Of the companies attacked, 10% had no email exposure. Of the remaining companies, we found an elevated signal (≥1) within the 4 months leading up to an attack for 67% of the organizations. In addition, 94% of organizations had a signal that was trending upwards.
| Elevated Signal (≥1) | Signal Trending Upwards | |
| All Attacks | 60% | 84% |
| All Attacks for Domains w/ Email Exposure | 67% | 94% |
Table 1: True Positive rates (positive accuracy) for elevated signals and upward trending DarkSonar signals
A prior independent third-party analysis of DarkSonar showed that a trending upward signal is also a significant indicator of risk. Thus, we explored not only an elevated signal prior to the attack, but also an upward trending signal. We calculated the trend line in the 4 months leading up to the attacks to determine the number of upward trending signals. For the companies with an elevated signal or an upward trending signal, we saw a true positive rates between 84% and 94%.
Breaking down the results across the industries with the most attacks, we see the positive accuracies shown in Figure 2. While this requires further analysis, it does point to some industries where DarkSonar may have the potential to be a higher indicator of risk.
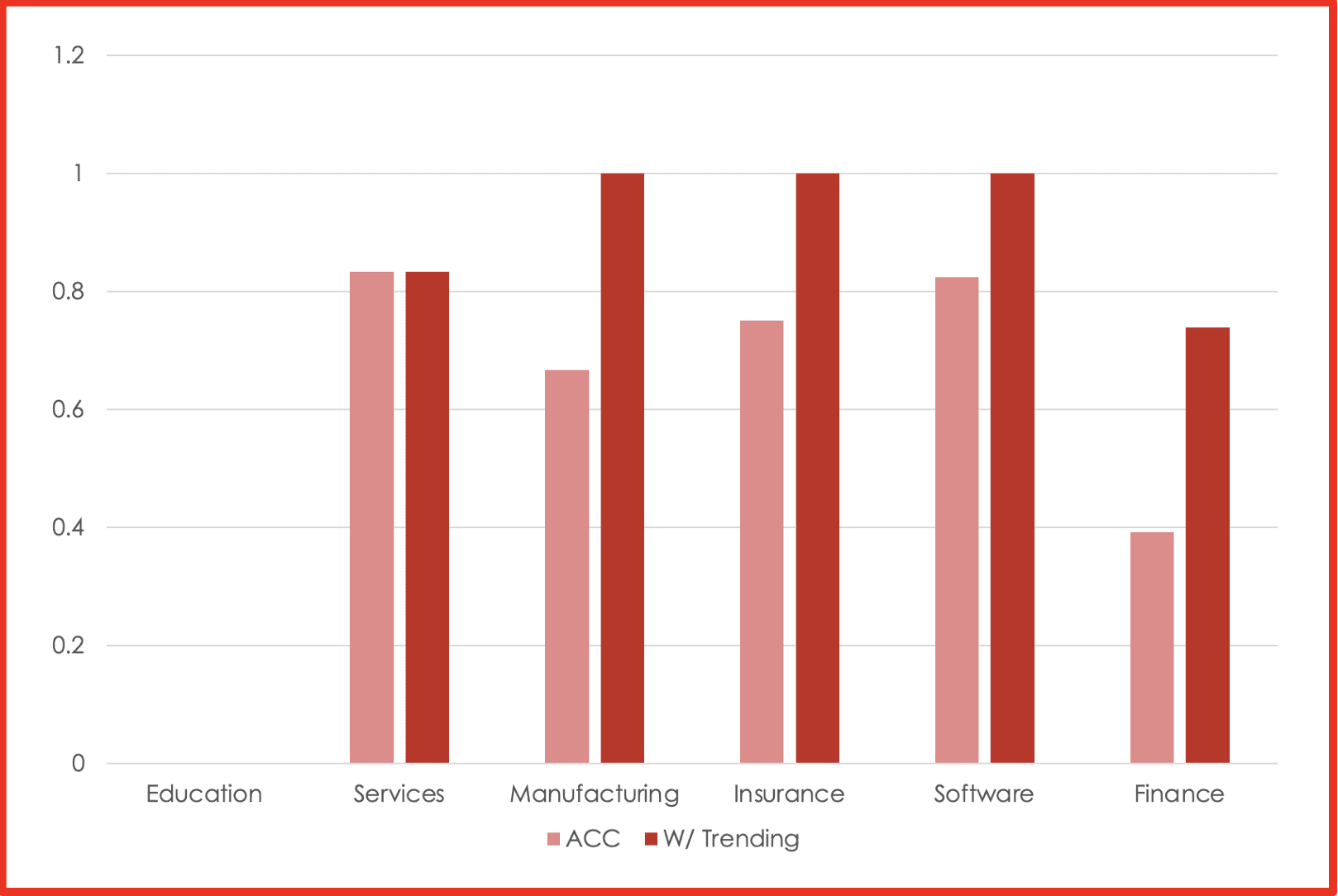
Figure 2: Positive accuracy across the main industries
To learn more about how DarkSonar may predict future attacks on your organization, contact us.
Review of CL0P’s Zero-Day Exploit Against MOVEit
Original Post: July 25, 2023
Ransomware attacks continue to grow in 2023, with the number of attacks taking place this year surpassing those at the same stage last year. One of the most successful groups this year has been CL0P which leveraged a zero-day exploit against MOVEit, a managed file transfer software which has led to huge data theft and extortion attacks.
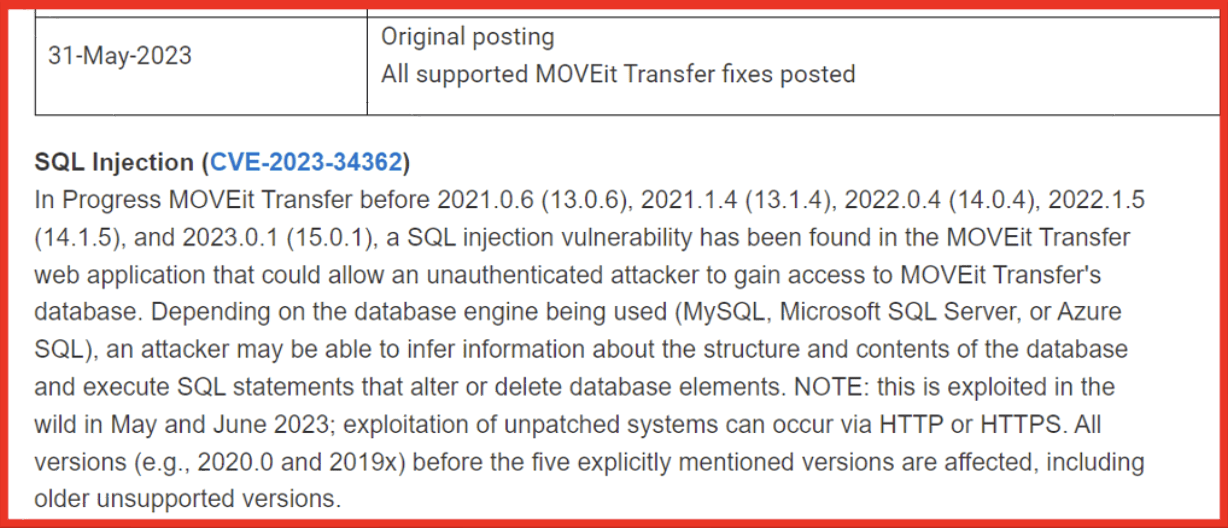
Figure 1: Initial vendor alert on the newly discovered MOVEit vulnerability; Source: Community Progress
CL0P have been active since early 2019 conducting both ransomware and extortion attacks, highlighting the fact that they are financially motivated. They have been known to make large scale demands to release data, in 2020 they became one of the first ransomware groups to demand over $20 million. While law enforcement activity has identified some members of the group, they continue to be active.
DarkOwl analysts have been actively monitoring CL0P, and the leak site to which they post victim data. On June 6th, 2023, they claimed responsibility for the use of the privilege escalation vulnerability in the MOVEit Transfer. In their post they threatened to post the stolen data if victims did not pay an extortion fee and also provided instructions for how to make payments. Security researchers have indicated that CL0P are likely to raise $75 million from their extortion attacks.

Figure 2: Instructions on making payment; Source: CL0P blog
On June 7th, they began posting the names of the victims they had successfully targeted. As of July 24th, they have added 187 victims’ names, however a number of other organizations have indicated that they are also victims of the attack. The group appears to be slowly releasing names, holding back those which could be considered more high profile. It is not currently clear how many organizations they were successfully able to compromise. The group have been teasing new victims and also what data will be included in the document leaks.
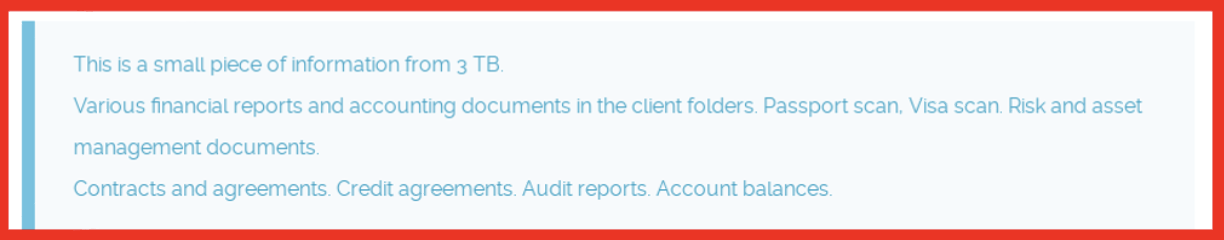
Figure 3: Teasing data threatened to be released; Source: CL0P blog
As of July 24th, only 11 victims have been removed from the leak site, which would suggest that they paid the extortion fee or are currently in negotiations with the threat actor. Full data has been provided for 21 victims and partial data has been released for a further 65. DarkOwl’s assessment of the victims indicates that the industry most impacted by this attack is finance.
Although some government and law enforcement agencies have self-reported as victims of the MOVEit campaign, no victim data has been provided. CL0P issued a notice on their website indicating that although they have successfully targeted government and law enforcement sites they will not be releasing this information as their intentions are purely financial in nature.

Figure 4: CL0P’s notice that they are not interested in government data; Source: CL0P blog
However, it does seem that CL0P may have fallen victim to too much success. Their leak site appears to have been overwhelmed by the amount of media attention they have received. The site has regularly gone down, there is often a queue to enter the site, and the download of data is very slow, offering an advantage to the victims that means it is not easy for people to download the information which has been stolen. It could be argued that it is not worth paying the extortion fee if no one can access the data. This could be why so few victims have been removed from the site.
Figure 5: Waiting page; Source: CL0P blog
Perhaps as a result of this issue on their darknet site, coupled with known slowness on TOR, the group have started releasing some of the data on clear websites. It is not yet clear if that will make the victim data more readily available.
The MOVEit attack has also highlighted the risk posed to organizations through third-parties, high profile consultancy companies have been included in the CL0P leaks, which are likely to contain information relating to some of their clients. Some of the reported victims, which have not yet appeared on the list use vendors that are known or have been reported to be breached.
Below is an example of a media item discussing a vendor breach that affected other organizations:
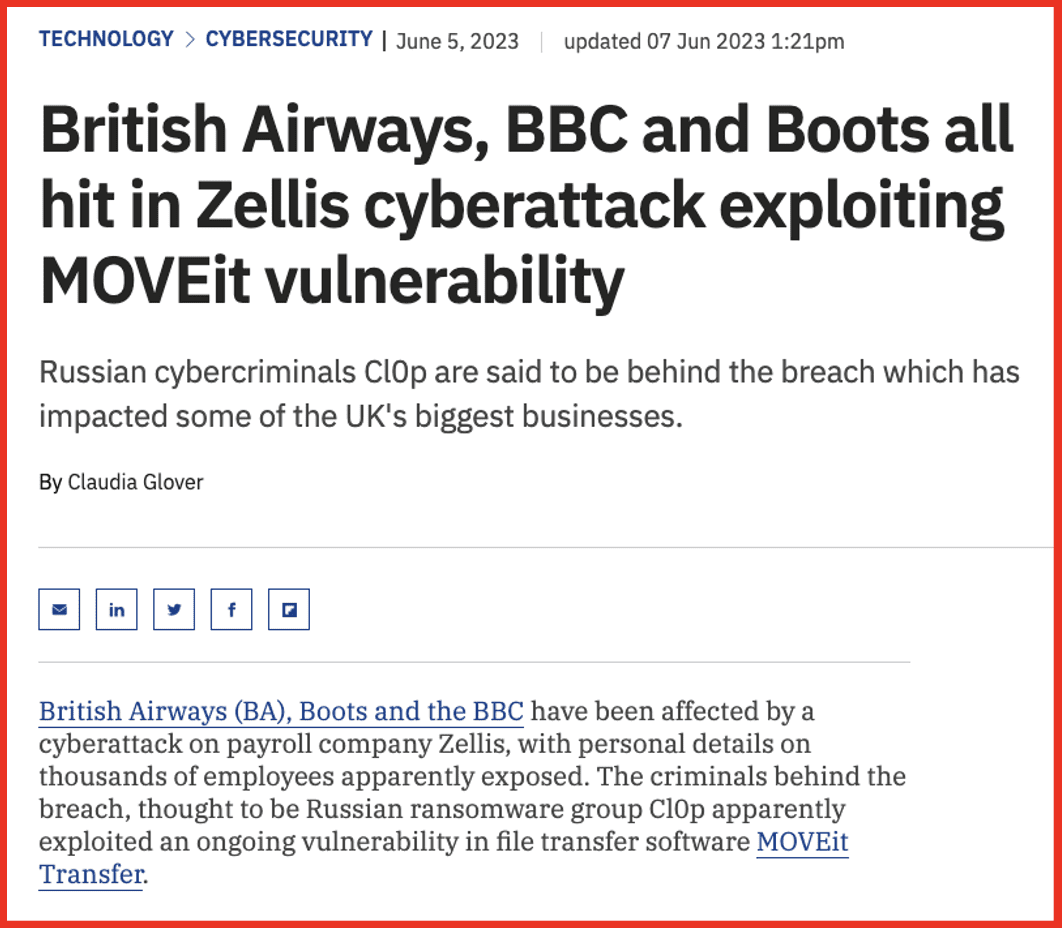
Figure 6: Source: TechMonitor
DarkOwl collects data released by ransomware groups in order to identify what information has been released, what victim data has been present and what risk it may pose to the organization. As well as the named victims, this data can also include large amounts of third-party data. It is therefore important to access this to enable searches for mentions of all organizations. DarkOwl can help your organization be alerted if their information appears in any of the data that we collect and further, how to turn that data into actionable threat intelligence.
Schedule a time to chat with us to learn more.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















