REvil hackers continue to wrack up high-profile targets with ransomware attacks
Since first leaking highly-sensitive personal information pertaining to Lady Gaga, the threat actor group has since targeted Sherwood Food Distributors and Donald Trump. Our team has been monitoring the situation closely and will continue to update here as new developments arise.
UPDATES (LATEST JUNE 2, 2020)
REvil Hackers Begin Auctioning Compromised Data
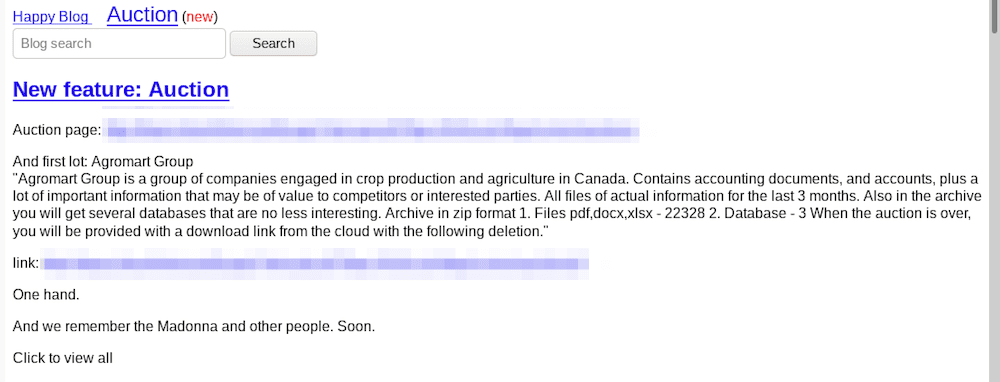
While US cities degenerate into destructive police protests and rioting, the REvil hackers show no sign of slowing, adding more victims to their darknet website in recent days. They also introduced an “auction” feature to their website, with Canadian agriculture company Agromart Group’s data as their first lot, starting bids at $50,000 USD.
SODINOKIBI USED AGAINST AGROMART GROUP
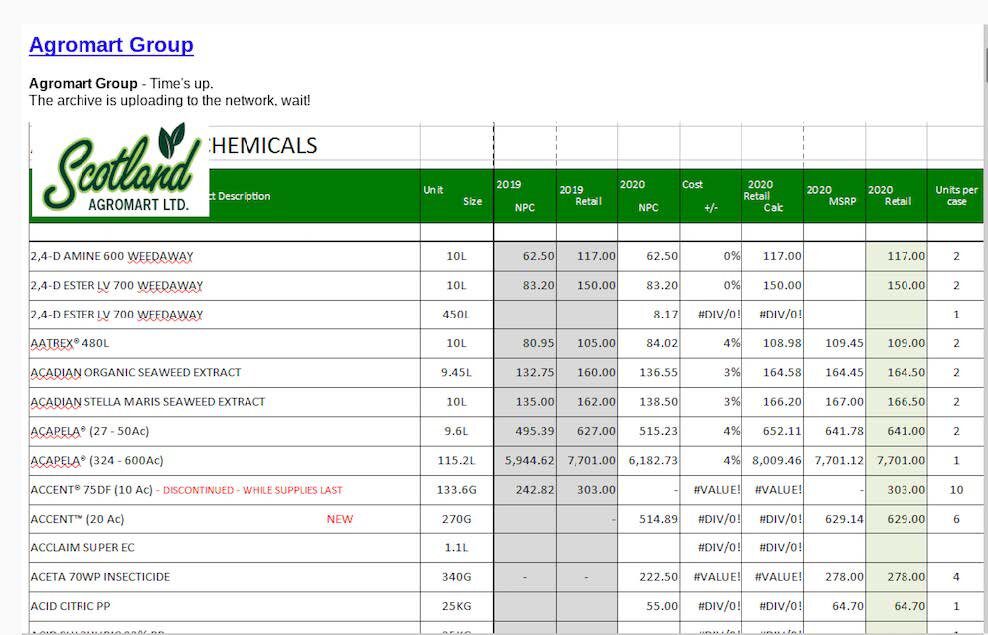
Agromart Group is a Canadian agriculture company with offices in Ontario. The Happy Blog post for Agromart suggests the hack of the group of several companies (including Scotland Agromart Ltd.) likely occurred on or around 26 May 2020. The hackers state they have corporate documents and accounts with over 22,000 files and 3 databases. There are several accounting spreadsheets included in the screenshots included as evidence of the legitimacy of the attack. The spreadsheet appears to consist of a list of Agromart’s customers and their orders. There was also a document labeled “Personal Net Worth Statement” with details of an employee’s personal financial information. It’s unclear whether or not this attack has or will impact Canada’s farming industry.
Early Tuesday morning, the hackers debuted an “auction” section of their darknet blog featuring Agromart, indicating a divergence from the Russian Jokerbuzz darknet auction hidden service mentioned in the Grubman Shire announcement. The minimum deposit in Monero (XMR) is $5,000 USD with a suggested starting price for the files and databases of $50,000 USD. The auction’s “blitz” price is $100,000 USD and will last only a week. The hackers also included links to purchase the Monero cryptocurrency, preferring Monero to Bitcoin transactions.
TELECOMMUNICATIONS AND ENERGY FIRMS NOT IMMUNE
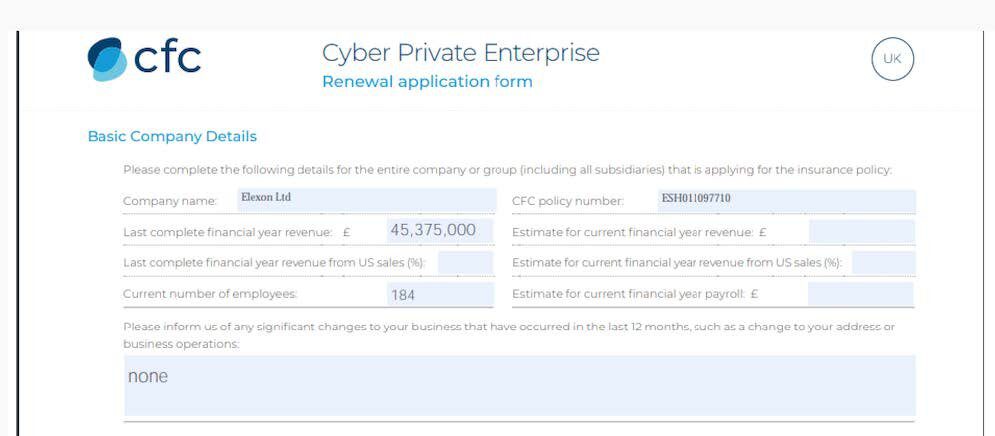
Hackers also posted links to South African telecommunications and mobile phone provider, Telkom, as well as British energy reporting and accounting company, Elexon. The announcement for Telkom’s hack was brief while the hackers included a link to “sample” files from Elexon’s corporate network and multiple screenshots. One included a renewal application form for CFC’s Cyber Private Enterprise, suggesting the company held an insurance policy for such a cyber attack.
According to their public website, Elexon admitted the attack on their internal networks occurred on 14 May 2020 and there was no risk to the public or loss of customer-level data.
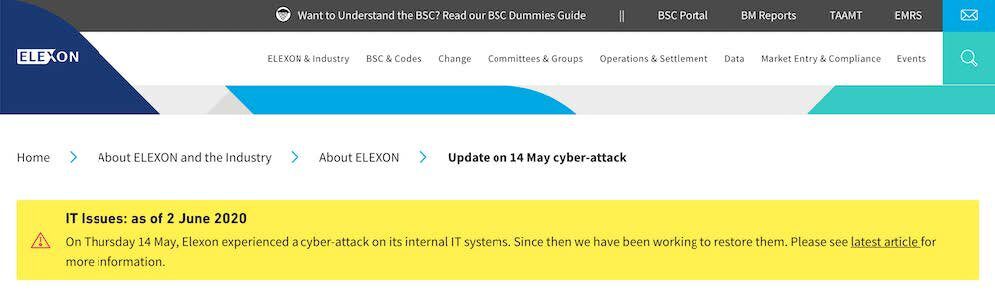
“We have identified the root cause and are now resolving the
issue. As we do not hold any customer level data, there is no
risk to the public.ELEXON is not part of the real time physical flow of electricity
from power stations to consumer. Therefore there is no impact to
power supplies.”
Several Law Firms Added in Recent Days
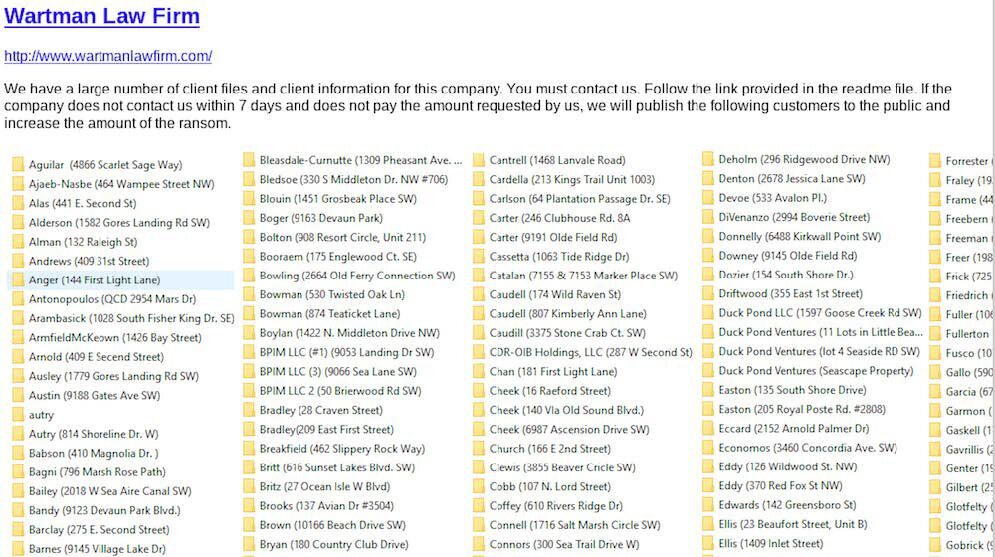
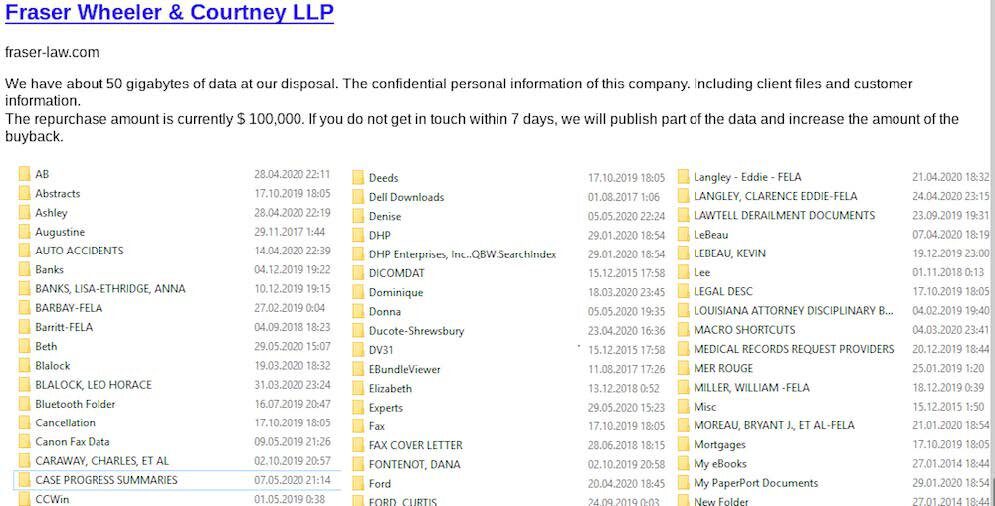
The REvil hackers also debuted hacks from additional US law firms: Indiana-based Wartman Law Firm and Fraser Wheeler and Courtney LLP in Louisiana. The post for Wartman indicates there are several hundred folders of customer and client data compromised and the law office has a week to respond with payment. The hackers state the Fraser Wheeler and Courtney data leak is over 50 GB with a repurchase price of $100,000 USD.
As of this update, DarkOwl has observed 41 data leaks posted to the REvil / Sodinokibi ransomware hackers “Happy Blog.” The post numbering system is up to 76, and we assess there are a large number of corporate victims either not yet mentioned or paid the ransom and avoided public inclusion to the darknet blog.
Given the volume and frequency of new postings, the threatening language used on recent public announcements and the latest introduction of the “auction” feature to their website, it is evident the hackers are feeling more emboldened and confident in the success of their extortion endeavors.
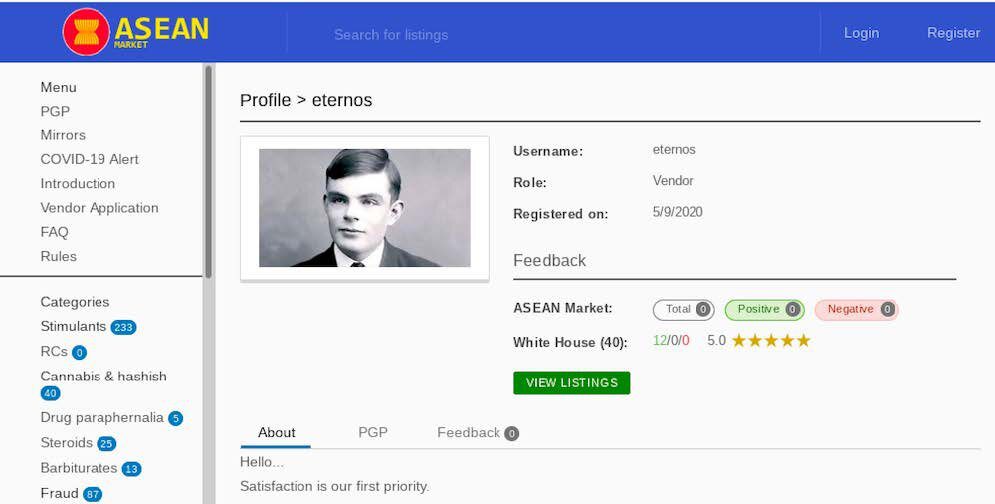
DarkOwl also discovered that a previous victim’s data, the National Eating Disorders Association (NEDA) archived by DarkOwl Vision in late March yet since removed from the Happy Blog, has recently appeared on a darknet marketplace not previously assessed to have affiliation with the REvil hackers.

A vendor using the moniker, “eternos” registered to ASEAN market in early May and the listing for the NEDA association’s database appeared shortly thereafter for as little as $99 USD. There is no intelligence to suggest “eternos” is associated with the REvil hackers, as the database could have been collected by an independent darknet group from links shared earlier on REvil’s Happy Blog or harvested from the NEDA network completely independent of the REvil ransomware attack of the organization.
New Targets Announced over Memorial Day Weekend
While the US celebrated Memorial Day weekend, the REvil/Sodinokibi hackers continued to target corporations around the globe. On Monday, May 26, 2020, the hackers announced another new victim, a law firm called Vierra Magen Marcus LLP. The hackers posted then announced their next new target, Titan Entertainment, late Tuesday, May 27, 2020. Since DarkOwl Vision’s first capture of the “Happy Blog” V3 hidden service in late February 2020, we know of at least 32 victims of the Sodinokibi ransomware since the website launched, an average of 2.6 successful infections worth public disclosure per week.
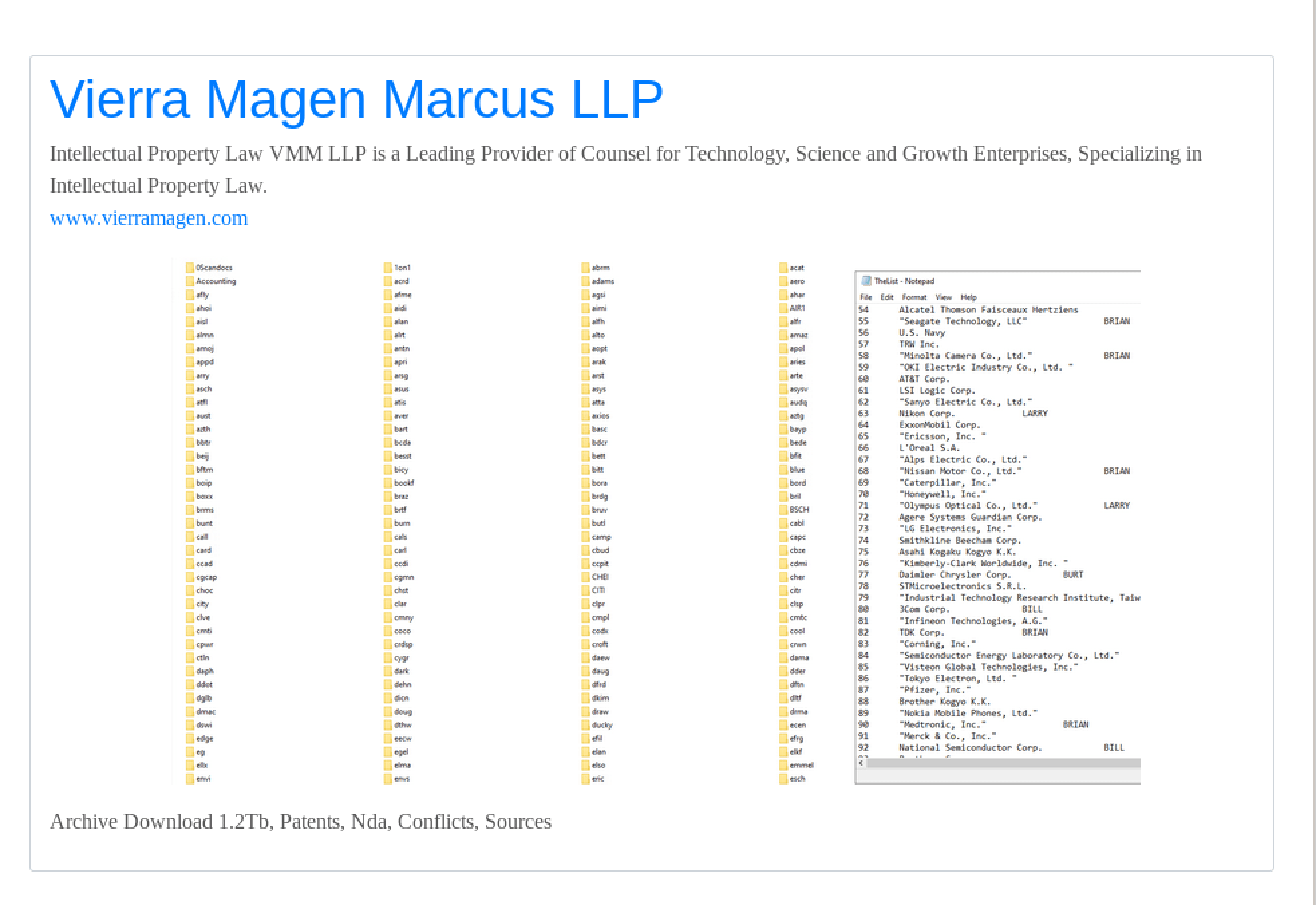
VIERRA MAGEN MARCUS LLP
Vierra Magen Marcus LLP is another California-based intellectual property law firm with an extensive client lists across “Technology, Science, and Growth Enterprises.” The hackers refer to their extorted archive including 1.2 terabytes of documents including patents, non-disclosure agreements, and conflict resolution legal documents.
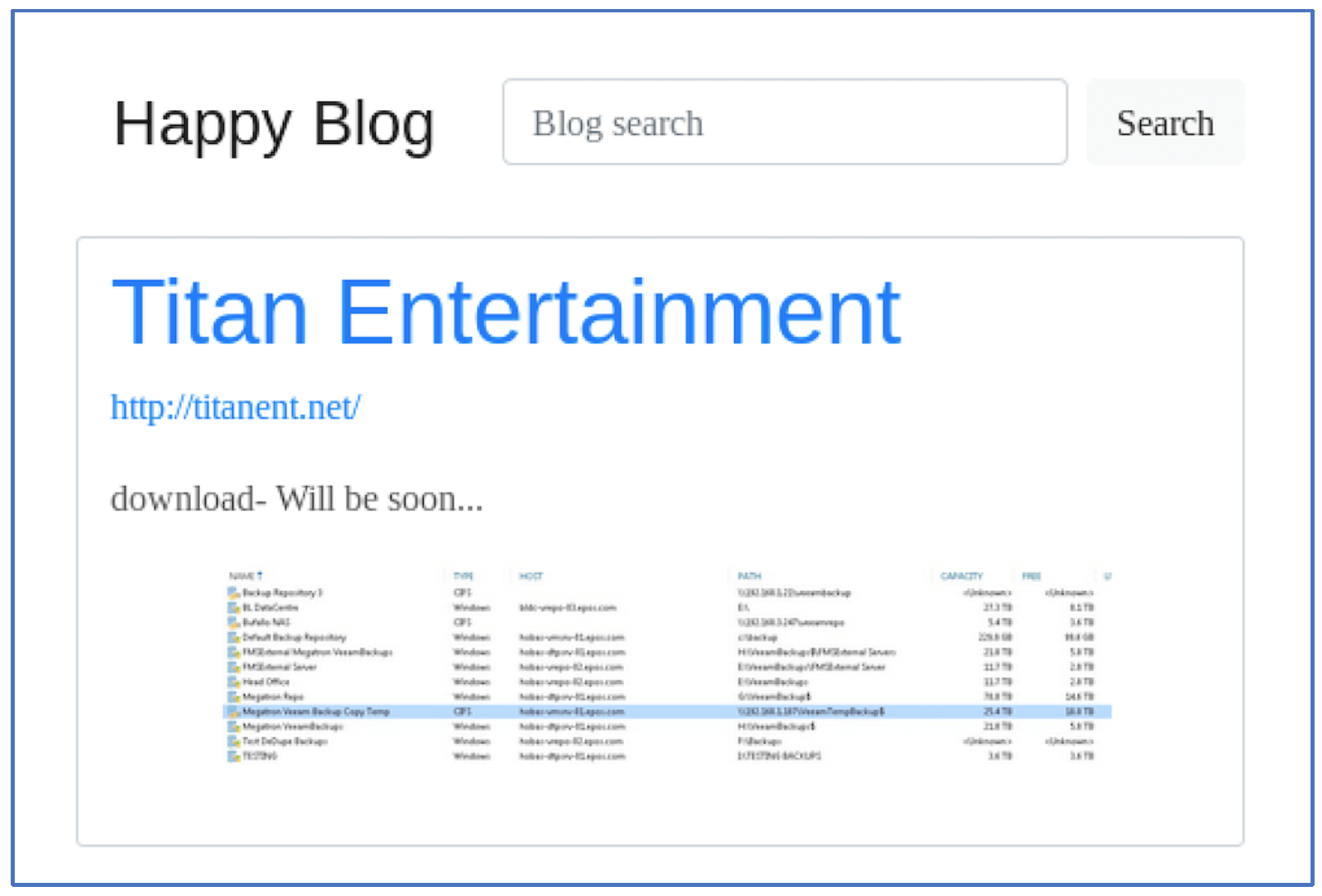
TITAN ENTERTAINMENT
Late Tuesday, the hackers added another Victim, Titan Entertainment, based out of London, UK with only the URL for the company’s website and the text, “download- Will be soon…” The screen capture provided by the hackers appears to include a list of servers from the company and their associated backups along with internal IP addresses of the compromised systems. As of time of writing, the website URL for Titan Entertainment listed on the Happy Blog is unresponsive.
FARO Technologies, a Leading 3D Printing/Manufacturing Company, is Latest Victim of REvil Hackers’ Ransomware Attacks
UPDATE: As of May 27th, Happy Blog no longer contains the post discussed below, suggesting FARO may have paid the ransom demands.
On May 20th, sometime between 11:31 MST and 2:38 MST, the hacking group known as REvil posted an announcement to the darknet forum Happy Blog stating that they had identified and compromised a new target, FARO Technologies. The hackers stated that FARO Technologies has 24 hours to pay their ransom demands, or they would leak 1.5 TBs of FARO’s data to the public. It is unclear how files REvil has total.
This announcement comes as the hackers continue to target the high-profile law firm Grubman Shire Meiselas & Sacks – and leak highly sensitive data pertaining to their celebrity clientele.
Per their website, FARO is the world’s most trusted source for 3D measurement, imaging and realization technology. The company develops and manufactures leading edge solutions that enable high-precision 3D capture, measurement and analysis across a variety of industries including manufacturing, construction, engineering and public safety.
Sometime after making this initial announcement, REvil updated their post to state they were giving FARO Technologies an additional 20 hours due to “a minor technical issue.” Then, in a subsequent post, they stated the following:
“FARO Technologies has exactly 3 hours, after which we will publish a link to the data here. FARO Technologies, if you do not know where to find the instructions, contact your employee [redacted]. He has already visited website, seen the instructions and knows what to do.”
On May 21st, REvil published the below announcement claiming that FARO had failed to meet their ransom demands, including a link to the data files. It is unclear what measures each party took to remediate this situation, though it appears that at some point, FARO’s parent company became involved. To our knowledge, REvil has never stated how much money they have demanded of their hostage.
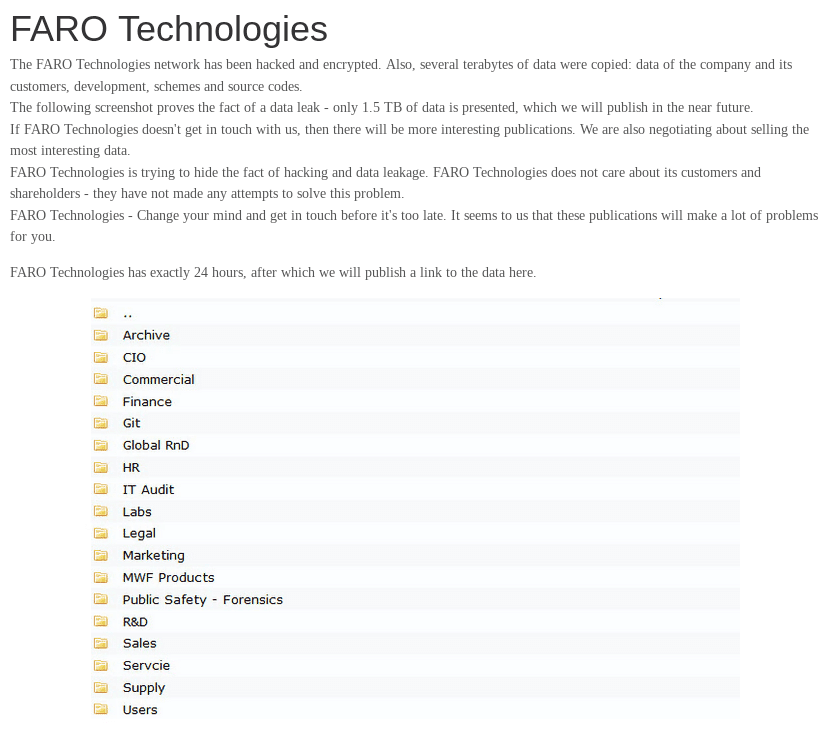
May 19th/20th – Screenshot of initial announcement, and an image of the data they claimed to have belonging to FARO Technologies
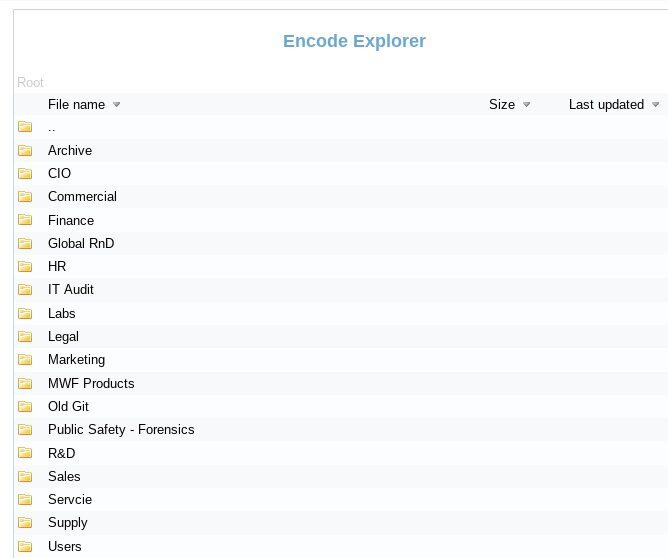
May 21st – Screenshot of the actual data files that the criminal actors released to the public after claiming that FARO would not pay their extortion demands
Items of note in the file-tree shared as a preview of what will allegedly be included in the 1.5 TB data drop include: IT audits, forensic information pertaining to public safety, global research and development files, legal records, and user data.
REvil Announces Next Target will be Madonna and Claims They’ve had Offers for Buyers for Trump Data
May 18: Just before 7:00PM UTC, DarkOwl Analysts observed an update to Happy Blog with the following announcement. In it, REvil states that Madonna is their next target, and that they will be auctioning off her personal files on the 25th of May. There is no reference to the ongoing ransomware attack they have conducted on Grubman Shire Meiselas & Sacks (GSM), indicating the hackers may be pivoting their approach to making a profit off of selling the personal data of high net worth individuals (instead of just attempting to exploit GSM with ransomware payments).
The hackers are starting the bidding for Madonna’s confidential data at $1 Million dollars.
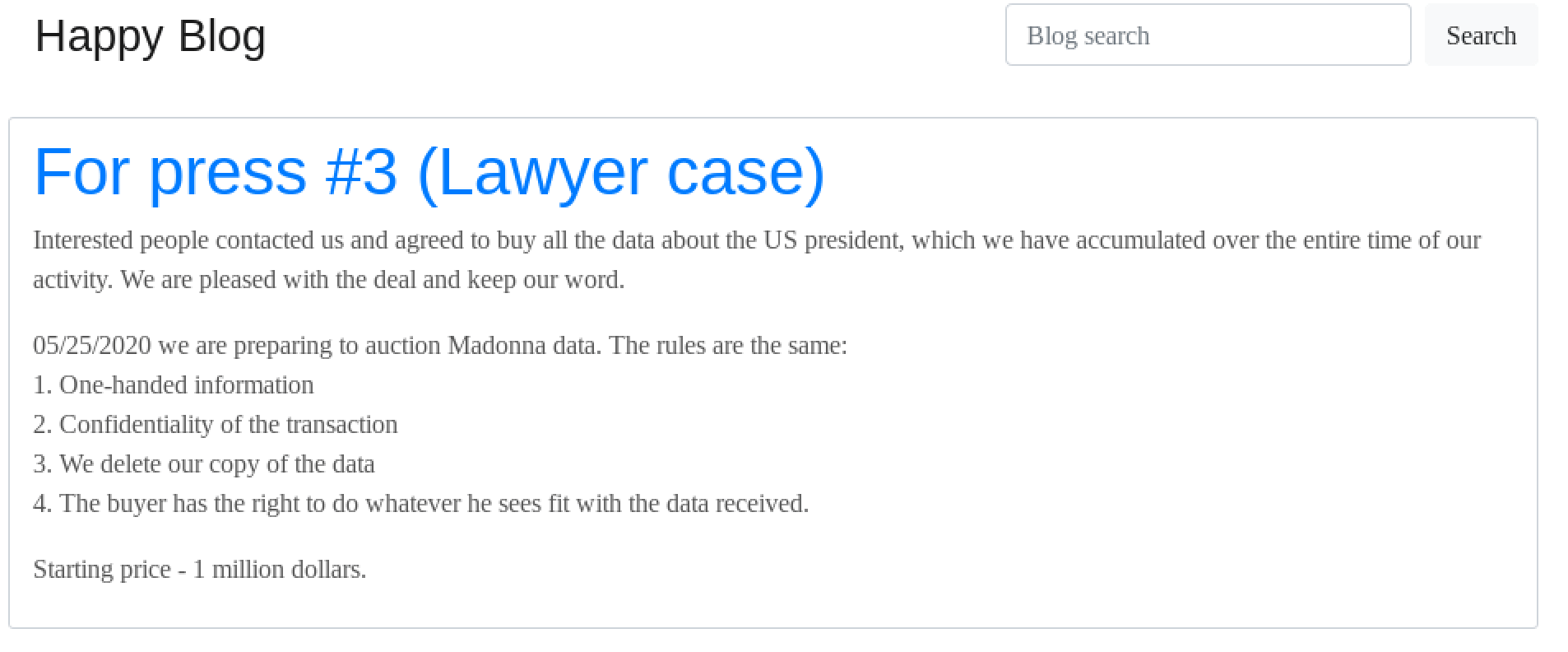
Third Press Release from REvil announcing their next target will be music artist Madonna
The hackers also stated that they have far more information pertaining to Donald Trump than was released in their initial drop, and that they have received several offers from buyers who want the full extent of the information REvil has “accumulated” over time.
In the second press release they published, they address the fact that they have been accused of “bluffing,” maintaining that the full extent of the information they have on Trump is damaging and will lead to public disgrace and financial loss.
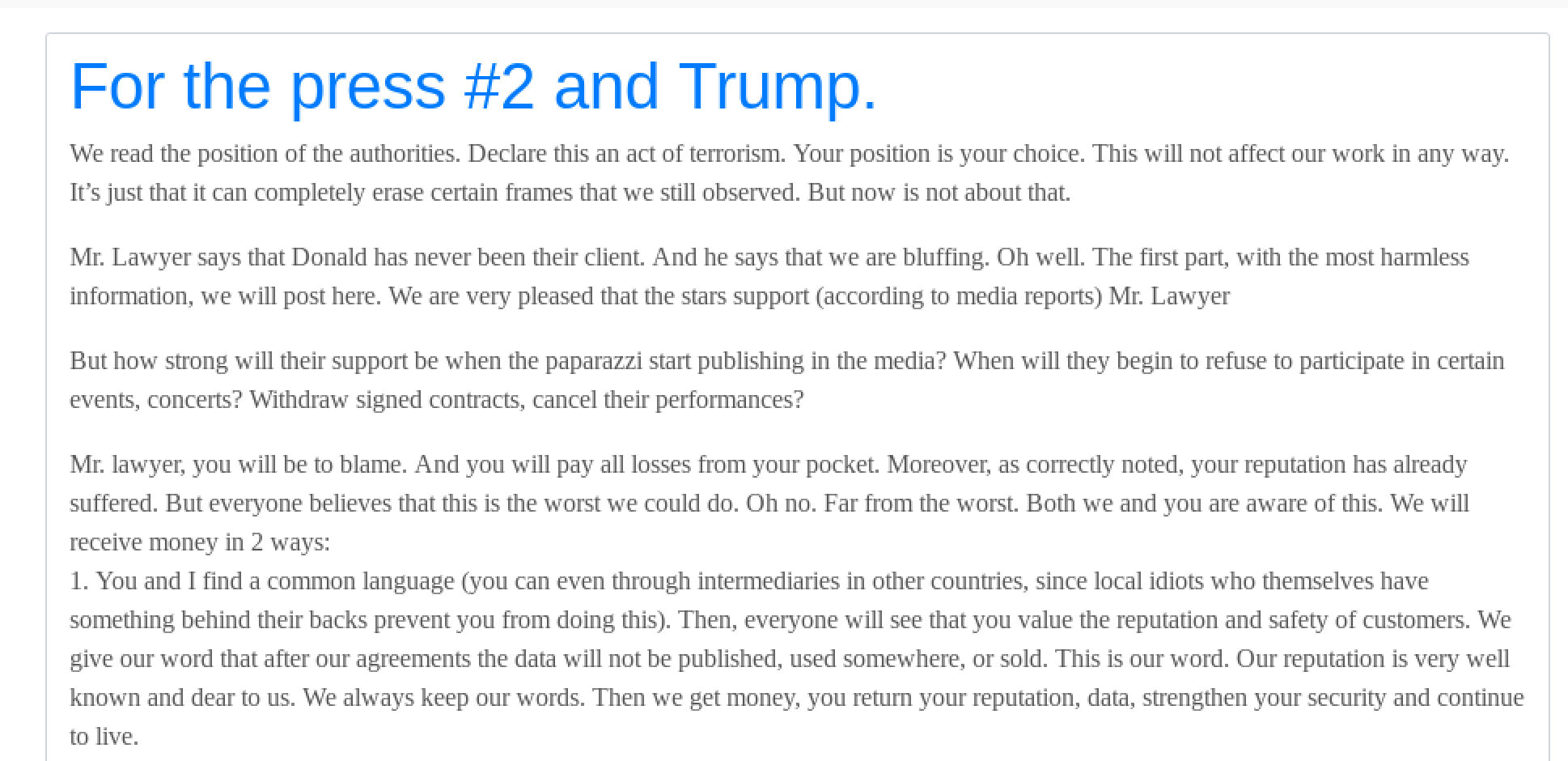
Second Press Release from REvil, defending the legitimacy of the files they have that pertain to Donald Trump
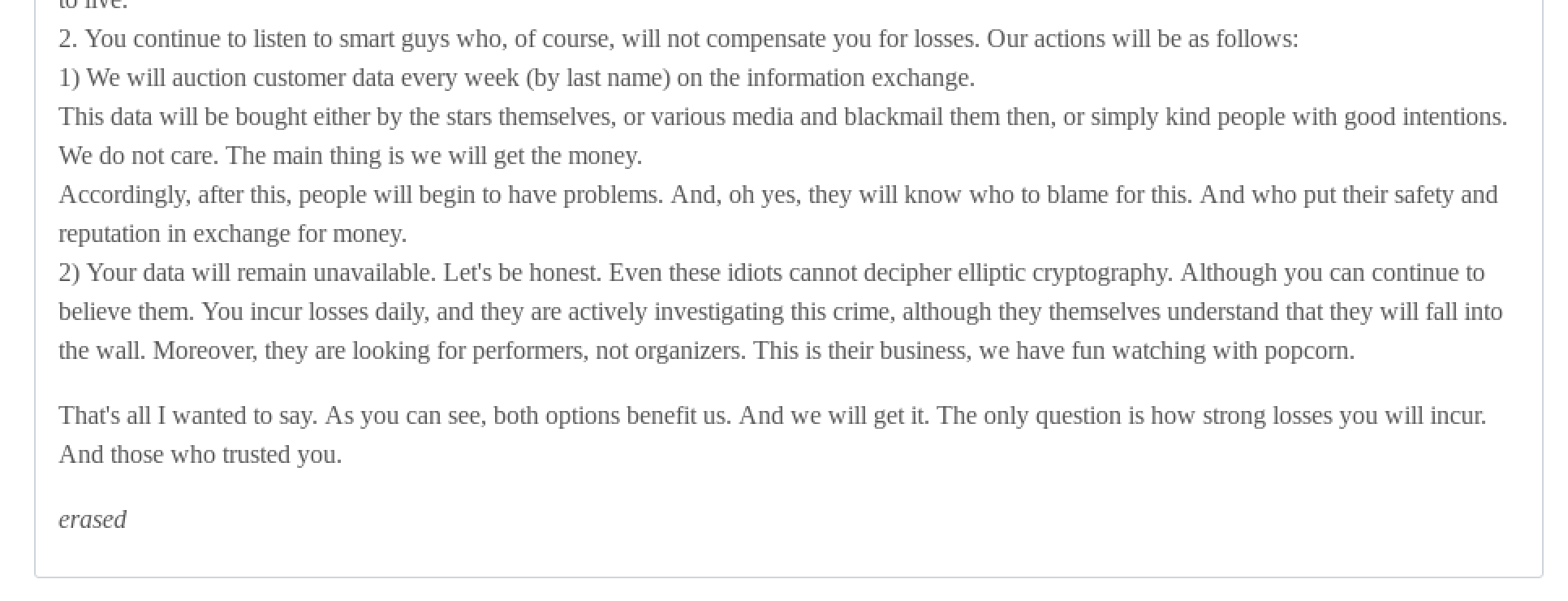
Second Press Release from REvil, defending the legitimacy of the files they have that pertain to Donald Trump
REvil also outlines how they do not plan to cease their ongoing Ransomware attack, but do plan on profiting from the money they can make from selling individual client data – regardless of whether GSM has paid their ransom demands.
ORIGINAL POST:
Hollywood Law Firm Hacked; Personal Data of High Profile Individuals Exposed
On May 11, 2020, lawyers for the Hollywood elite, Grubman Shire Meiselas & Sacks (GSM) confirmed publicly they were in the midst of a cyber ransomware attack, with hackers holding hostage some 756 GB of sensitive client data, contracts, and personal information harvested from their main website server, www.gsmlaw.com, which remains offline.
The hackers, believed to be from Eastern Europe, demanded a ransom of $21 Million USD putting the law firm and their clients in a precarious position during already stressful times due to the COVID-19 pandemic.
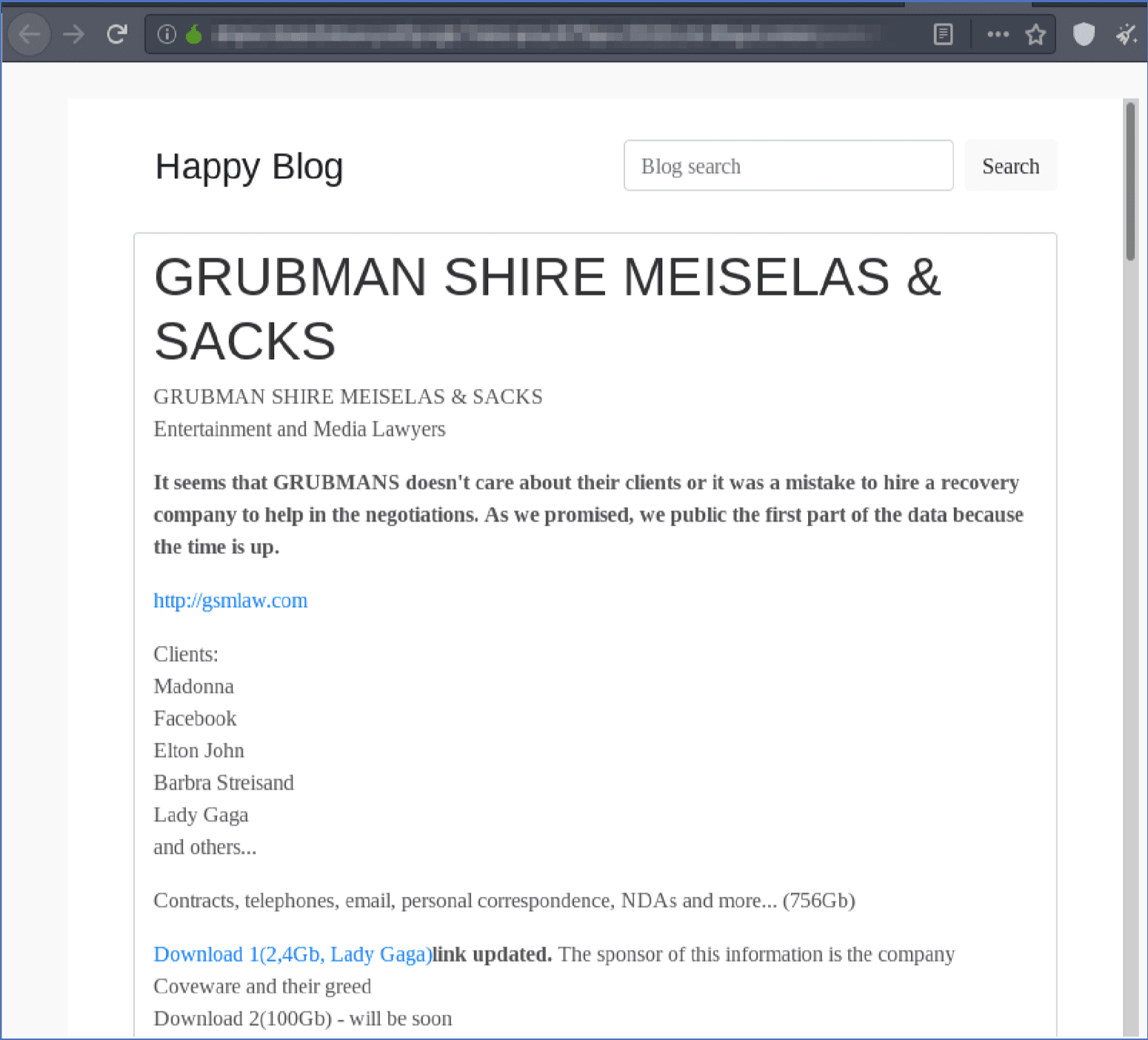
Hackers Post Entertainment & Media Lawyers Data on Darknet, Date: May 14, 2020
Despite where the owners of the law firm are in negotiation with the hackers and whether or not the FBI has become directly involved, the hackers have already started publishing data from the ransomed servers on the darknet. DarkOwl analysts discovered a Tor hidden service the hackers maintain called “Happy Blog.” It was there that they announced their hack of the GSM hack in early May, and continues to be where the group routinely publishes updates. The hackers’ announcement lists many of GSM’s exclusive clients such as: Madonna, Facebook, Elton John, Barbara Streisand, and Lady Gaga along with 9 inactive, but prepared links for separate data leaks.
The underground website also includes screen captures of over 176 folders listed on the compromised server and what appears to be signed contracts and agreements from Christina Aguilera in 2013 and Madonna’s World Tour 2019/20. There are numerous other famous actors and musicians from Hollywood mentioned.
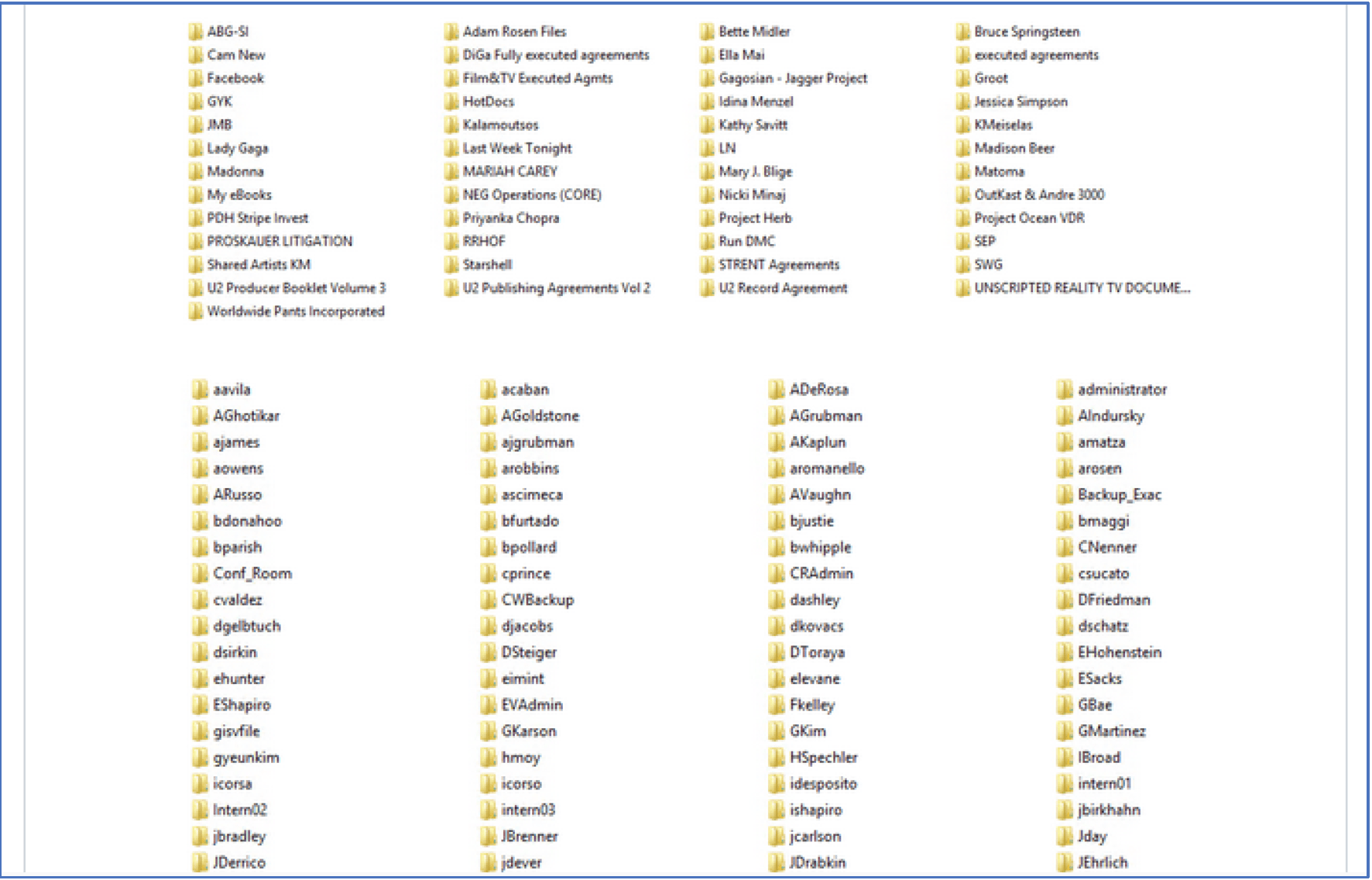
Sample of the Folders Hacked from the Entertainment Lawyer’s Server

Agreements with Clients Shared on the Darknet to Legitimize the Attack
Lady Gaga Data Exposed
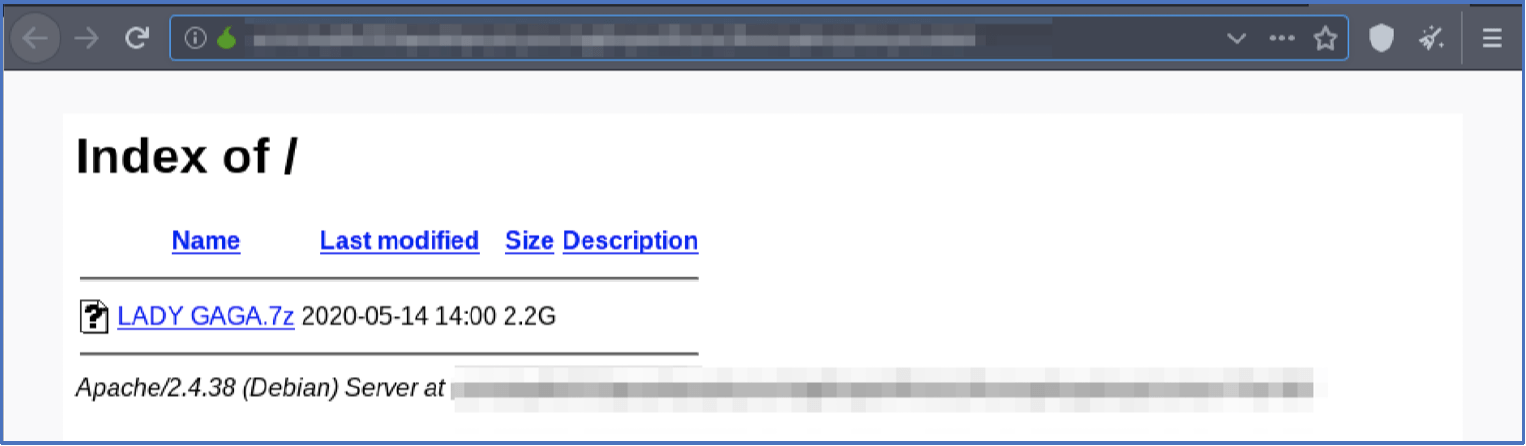
Lady Gaga data leaked by Hackers in 2.2GB file
DarkOwl analysts also discovered the first of the 9 data leaks had been released at 2:00pm UTC on Thursday, May 14, 2020 and included over 2 GB of data related to entertainer, Lady Gaga, due to release a new album at the end of the month. Along with the data leak, the hackers updated the website to state, “we public the first part of the data because the time is up” (confirming that English is not their native language).
A review of the data revealed there exists over 3,000 files across 350 folders which includes but is not limited to: W9 forms, expense reports, producer agreements, certificates of engagements, and confidentiality agreements over the last decade. Of particular concern is the folder listed, “Gaga Medical Confidentiality Agreements” that most likely includes some of the most personally identifiable information for the mega entertainer, such as her social security number.
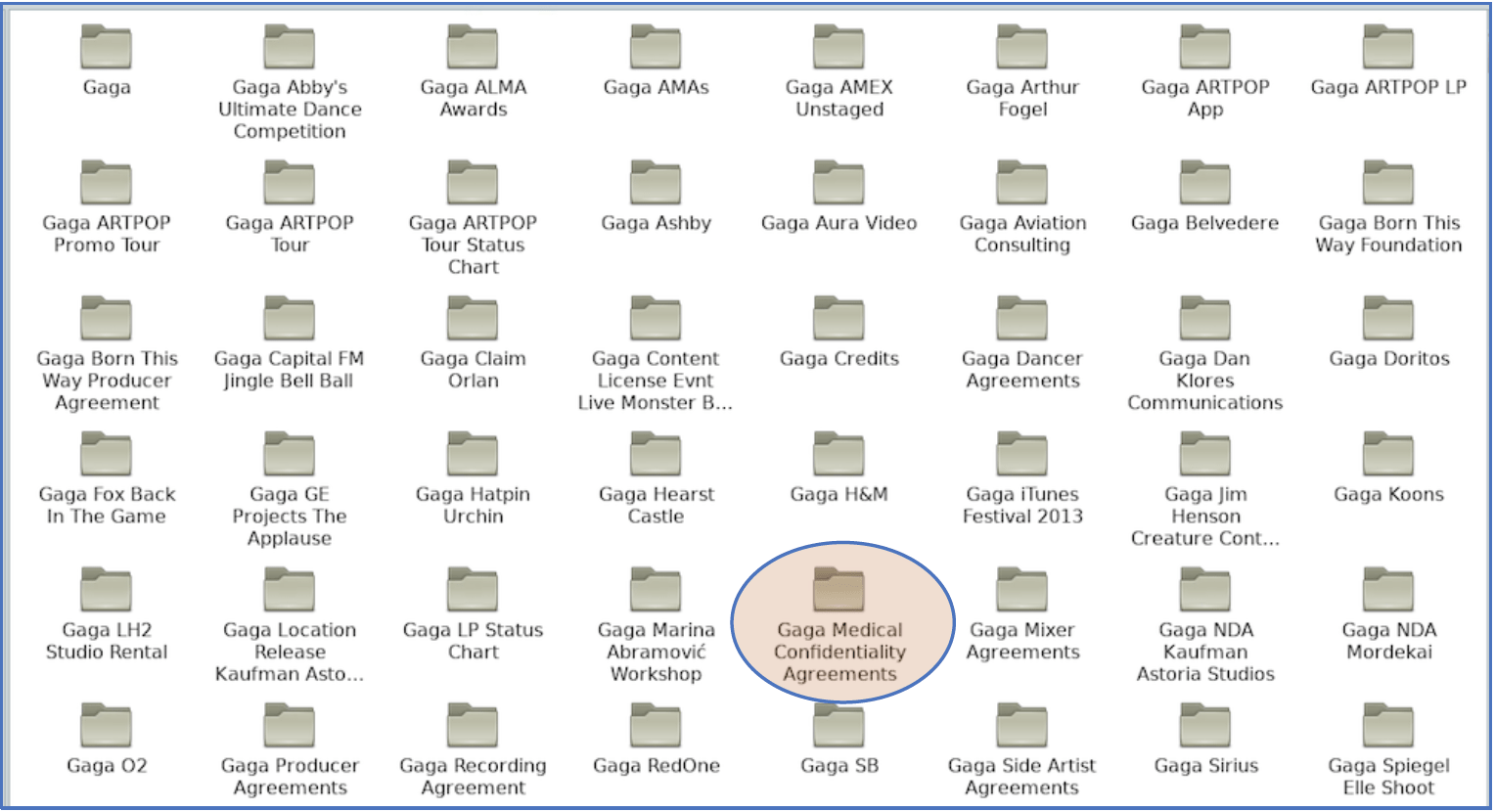
Sample listing of some of the folders from Lady Gaga Data Leak on May 14th, 2020
The Next High Profile Individual Data-Drop: Donald Trump
On May 14, 2020, the hackers responded even more seriously, doubling the ransom in a new message stating, “The ransom is now [doubled to] $42,000,000 … The next person we’ll be publishing is Donald Trump. There’s an election going on, and we found a ton of dirty laundry on time.” According to PageSix, the hackers added, “Mr Trump, if you want to stay president, poke a sharp stick at the guys, otherwise you may forget this ambition forever. And to you voters, we can let you know that after such a publication, you certainly don’t want to see him as president … The deadline is one week.”
DarkOwl Analysts have confirmed that the second drop did contain information pertaining to Donald Trump. While he was not a client of GSMs, there were leaks of associates of his that reference him, as well as leaked correspondences between GSM and other clients in which either Trump or Trump’s Entertainment holding company were mentioned.
Since Trump was not a client of GSM, the second REvil drop is not like Lady Gaga’s, and his personal files were not made public in any way. Regardless, DarkOwl analysts are currently in the process of reviewing the leaked correspondences for items of note. This blog will be updated accordingly as we do so.
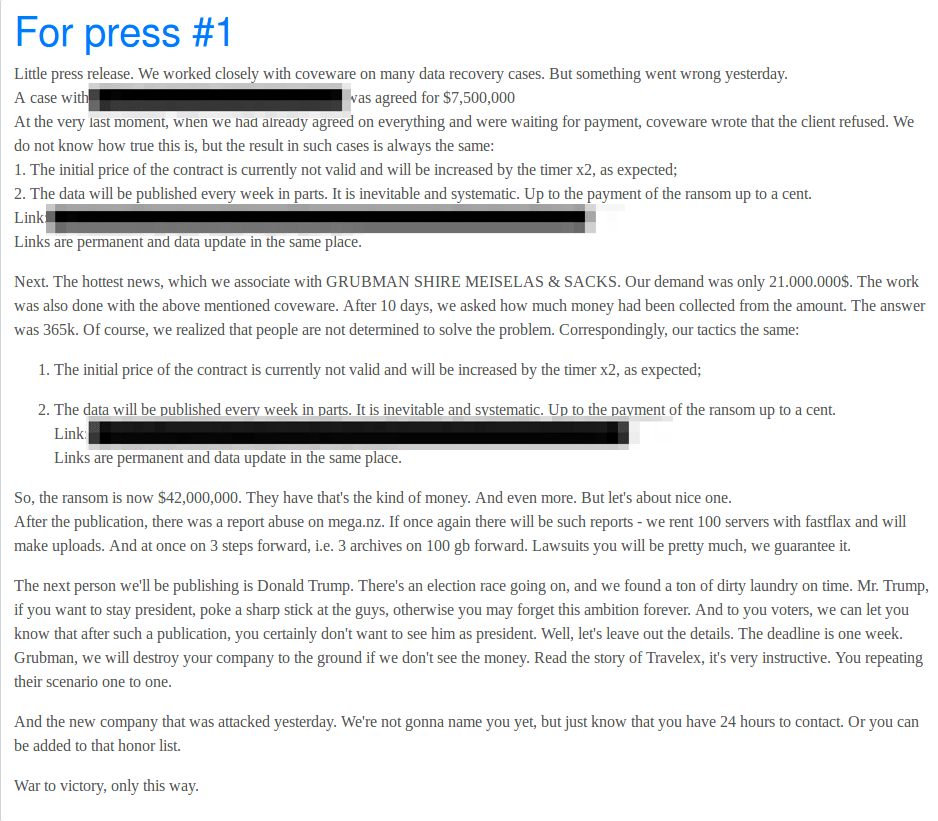
“Small Press Release” Posted on Happy Blog announcing that the next target would be Donald Trump
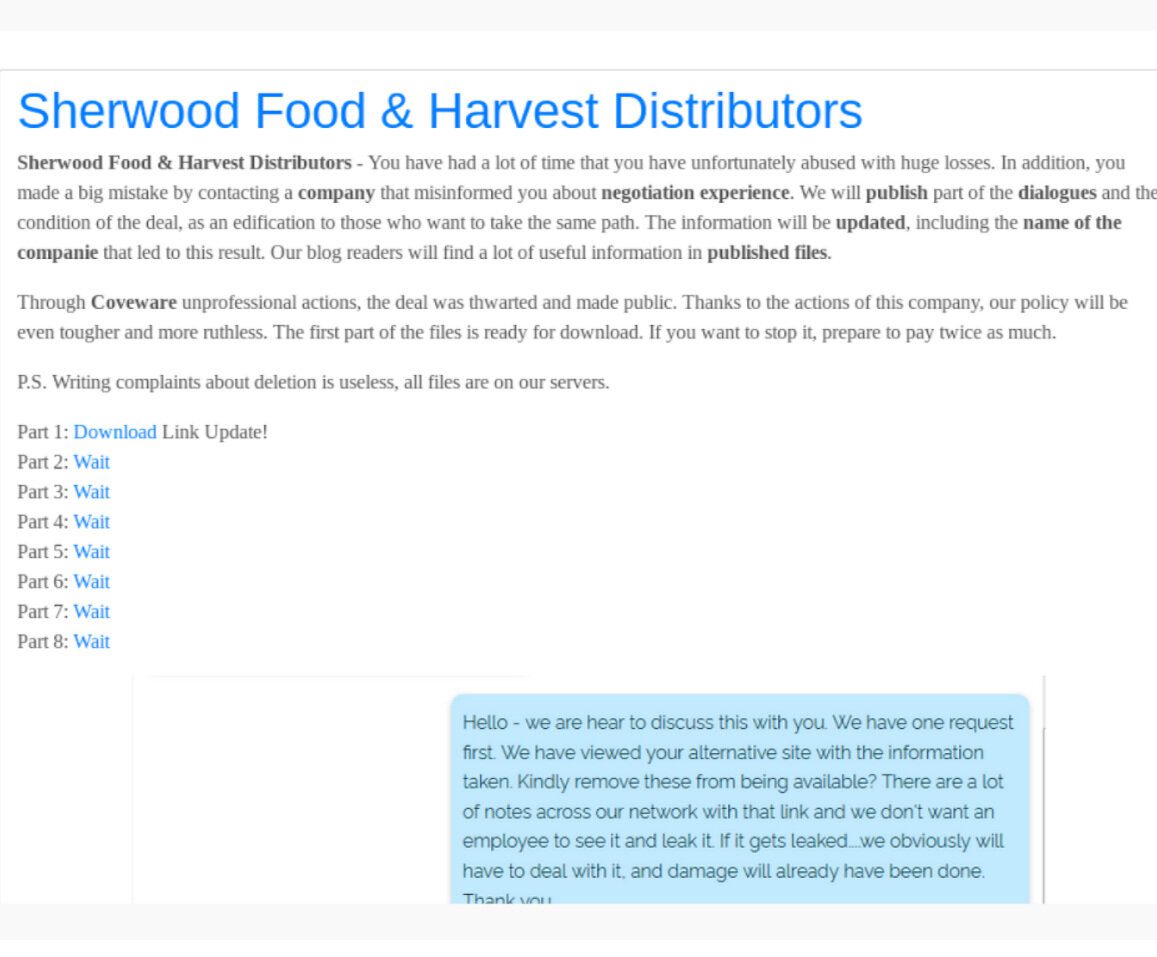
REvil Announces New Target: Sherwood Food Distributors, LLC
UPDATE: As of (approximately) May 20th, Happy Blog no longer contains the post discussed below, suggesting Sherwood may have paid the ransom demands.
The same group of hackers who just released highly sensitive data relating to Lady Gaga as a part of their ongoing extortion attempt of Grubman, Shire, Meiselas and Sacks have posted on the darknet that they are holding another company for ransom – Sherwood Food and Harvest Distributors. The threat actors posted a notice about their new target around 3pm MST 5/15.
This notice contained a link to download a portion of Sherwood’s proprietary files as “previews” which they plan on releasing one at a time (8 in total). The first link to leaked information contains roughly 2,300 files. These files contain highly sensitive data including cash-flow analysis, sub-distributor info, detailed insurance information, proprietary vendor information – including for that of Kroger, Albertsons, Sprouts – scanned drivers license images for drivers in their distribution networks, etc. The threat actors also posted a conversation they had with Coveware, a leading ransomware mitigation company, dating back to at least May 3rd.
This shows Sherwood has been aware of and dealing with this attack for over a week, and had not made this information public. While the threat actors only posted Coveware’s side of the conversation, it is clear that Coveware attempted to negotiate by acting as a middleman between Sherwood, their board, and the attackers. Also of note is that Grubman, the law firm, also utilized Coveware’s services, which is worth keeping in mind considering these are two supposedly unrelated companies/targets.
Announcement on Happy Blog that Sherwood Food Distributors were the latest targets of REvile hackers
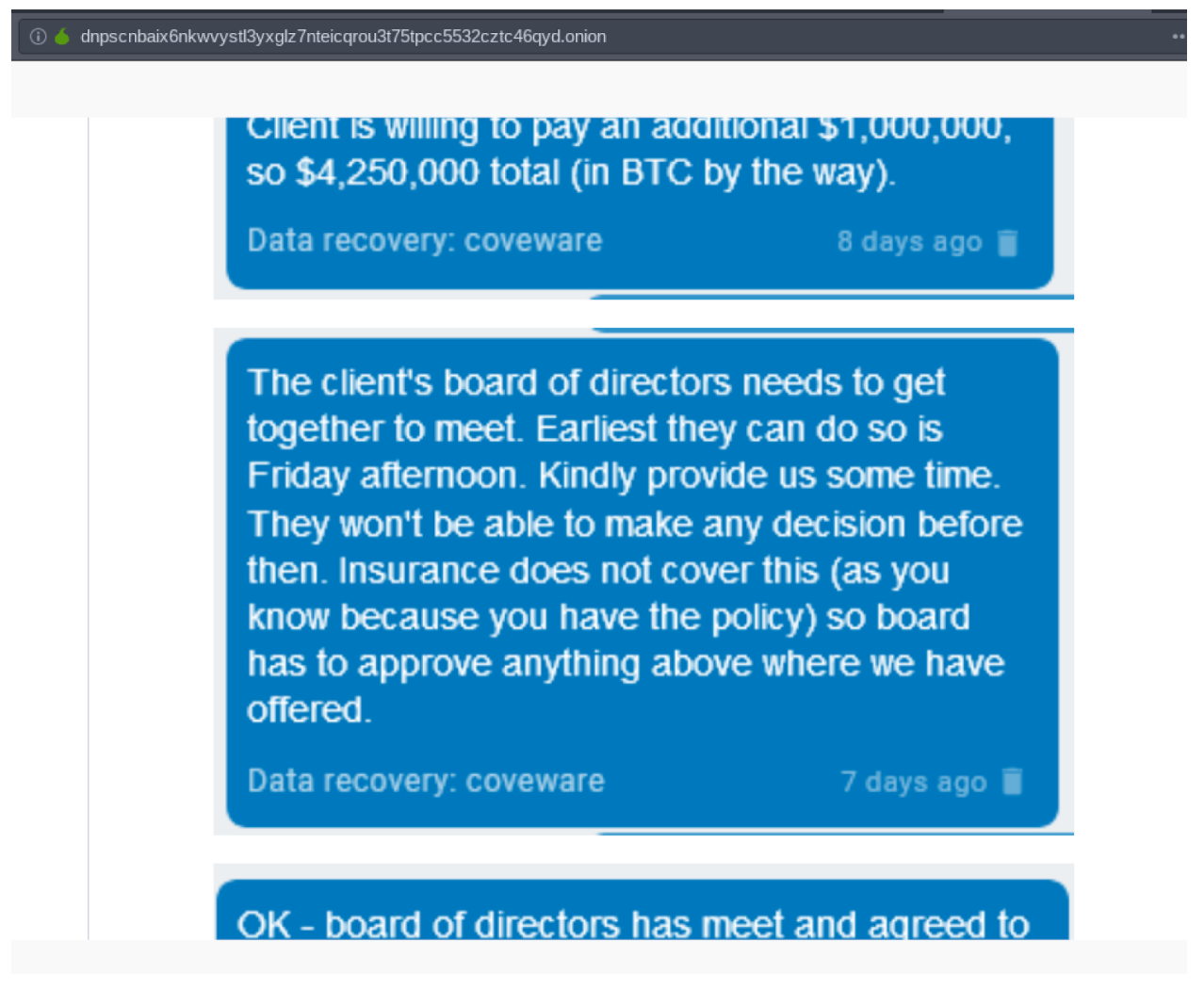
Screen captures of the conversation the hackers had with Coveware, a 3rd party ransomware mitigation firm
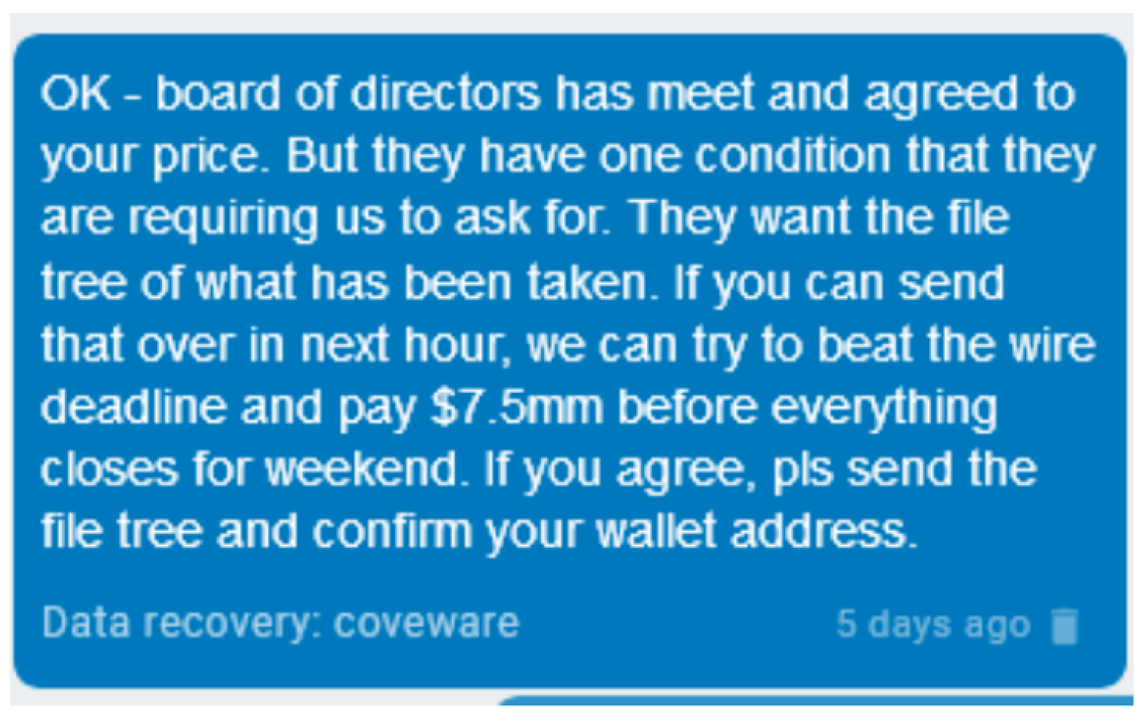
Screen captures of the conversation the hackers had with Coveware, a 3rd party ransomware mitigation firm
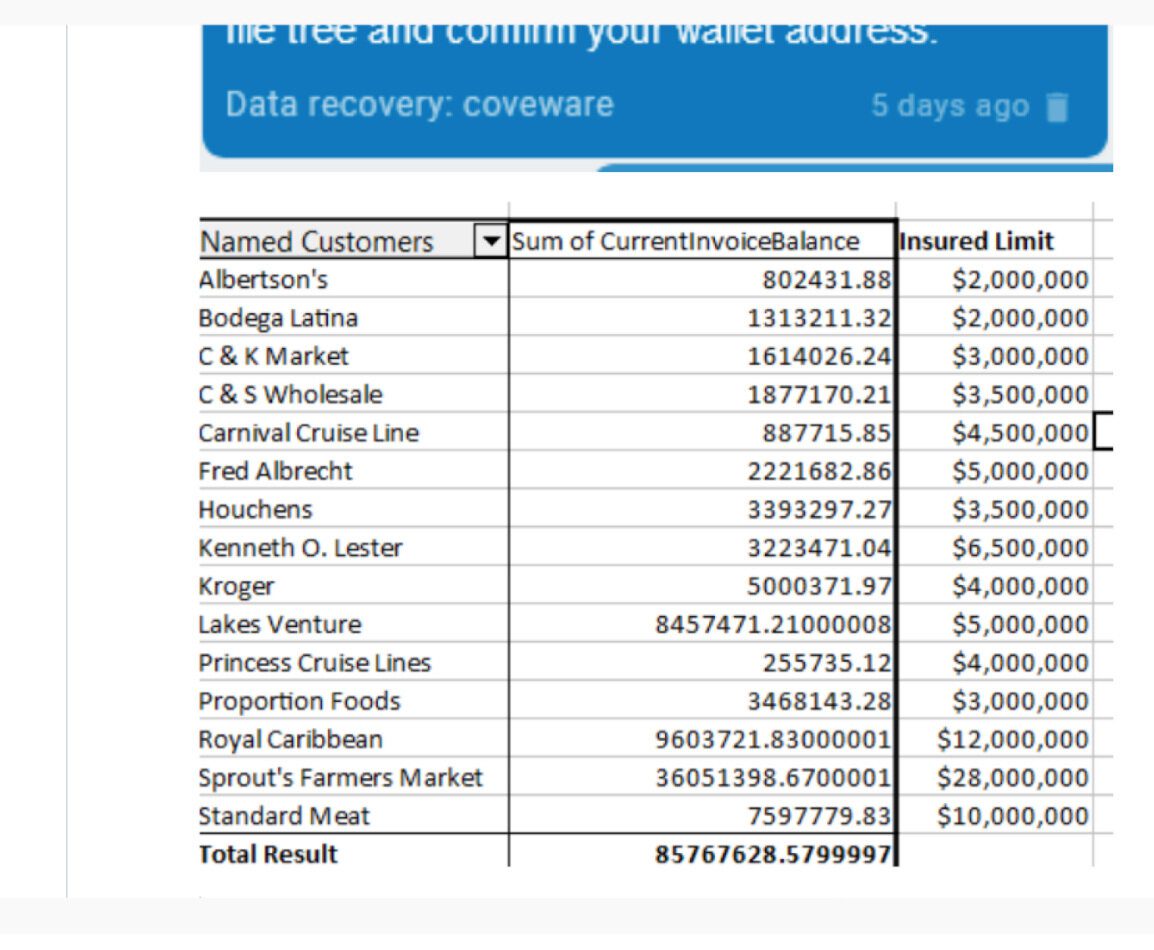
Sample Sherwood data that the REvile sent to Coveware to show them that their threats were serious
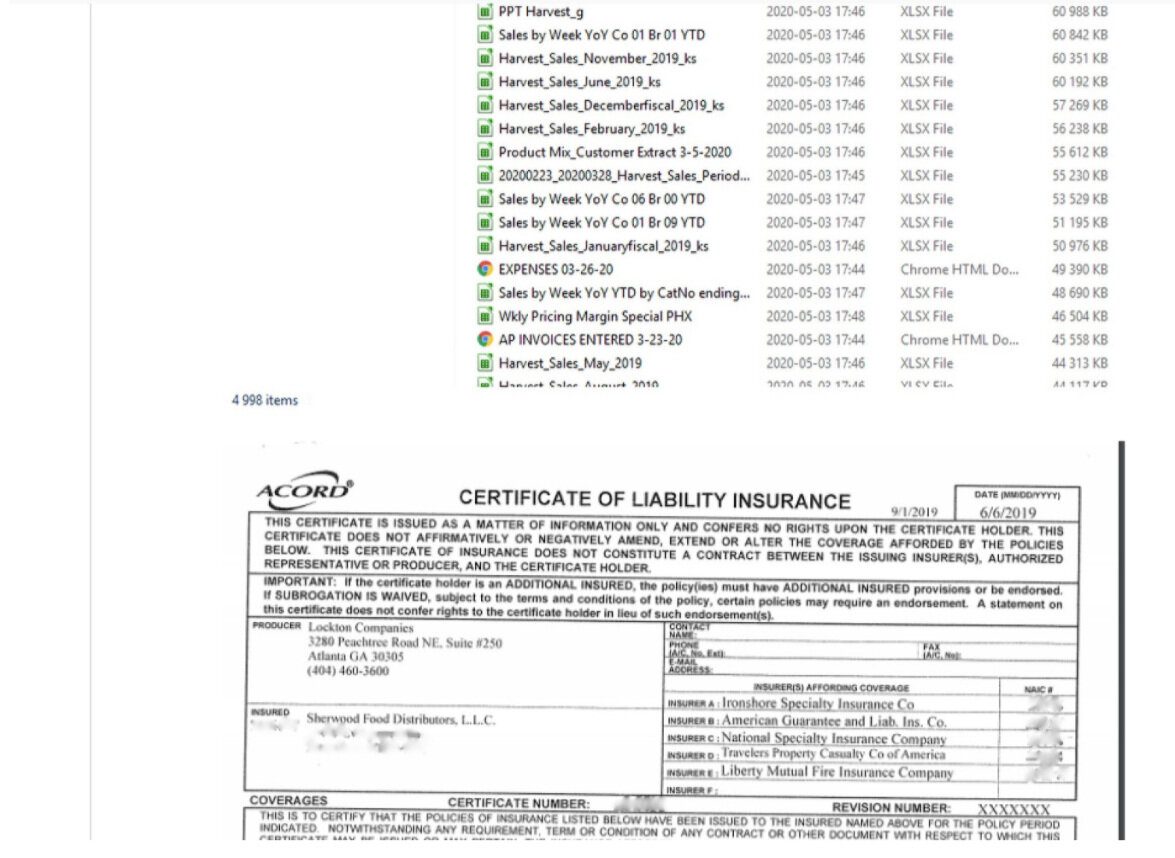
Sample Sherwood data that the REvile sent to Coveware to show them that their threats were serious
Who are these Hackers?
According to open source reporting, the hackers responsible for the ransomware are reportedly known as REvil or Sodinokibi, who infamously attacked foreign exchange company, Travelex late last year with similar ransomware. Travelex paid the hackers $2.3 Million of the $6 Million USD in ransom demanded.
There are several mentions of the ransomware developers across English and Russian speaking darknet forums and marketplaces.
-
The hackers sponsored a hacking competition worth $15,000 on darknet forum, XSS in January 2020, according to multiple sources.
-
In April 2020, BleepingComputer and numerous darknet news sources also confirmed the ransomware hackers would from now on only accept Monero for their ransoms, as they believed, quite confidently that Bitcoin was traceable by law enforcement.
-
The hackers are believed to have also authored GandCrab, a popular ransomware as a service (RaaS) that circulated the internet from January 2018 until May 2019, when the hackers suddenly announced they were shutting down their operations.
The Sodinokibi ransomware authors and their associates have been widely distributing the ransomware through infected Javascript on WordPress websites. Upon installation on the victim machine, it deletes all Shadow Volume Copies, disables the Startup repair in Windows and then begins encrypting all the files on the system hard drive.
Once the malware completes its encryption process, Sodinokibi modifies the desktop wallpaper, adding a ransom note, which contains instructions about the decryption process. The ransom note also includes instructions on how to make the payment to have the files decrypted, including unique keys and links to the payment site (likely Monero).
Reception to REvil’s latest antics have not been great. Members of XSS forum have expressed displeasure to how much attention this has brought them, posting:
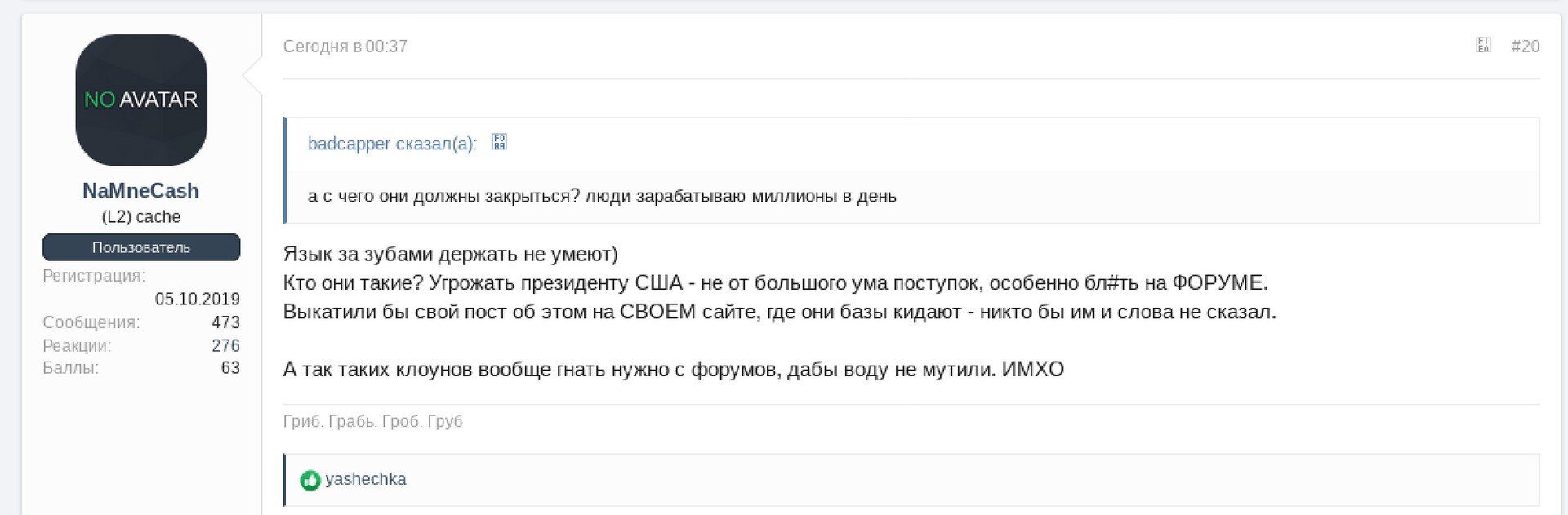
Translation: “hey can’t keep their mouths shut)
Who are they? Threatening the President of the United States is not a very smart thing to do, especially BL#t on the FORUM. They would have rolled out their post about it on THEIR website, where they throw bases – no one would have said a word to them.
And so such clowns generally need to be driven from the forums, so that the water is not muddied. IMHO”
DarkOwl Analysts continue to dig into this hacking group to see what we can uncover. Stay tuned for updates as we will continue to update this blog with new findings.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases
![[Image Source]](https://www.darkowl.com/wp-content/uploads/2021/12/Screen-Shot-2020-05-18-at-9.11.23-AM.png)















