Round-up of the Latest Ransomware Gangs Operating on the Darknet
Ransomware as a service (RaaS) gangs readily use darknets like the Tor Project for coordinating their attacks. DarkOwl analysts frequently observe threat actors discussing vulnerabilities and attack vectors, contracting with initial access brokers (IABs) for exposed credentials and access, negotiating directly with victims for ransom payments, and publicly shaming victims through releasing information about attacks and selling/auctioning extorted data. Since the disappearance of Maze Cartel last year and DarkSide this year – shortly after the attack on Colonial Pipeline that crippled a U.S. fuel supply line – DarkOwl has observed many RaaS threat actors come and go, rebranding with nuanced differences. Affiliate programs also increase the presence of new RaaS partners operating similar global campaigns.
This round-up will introduce the new and emerging RaaS groups that DarkOwl has observed as actively operating on the darknet today.
LV Blog
Threat actors behind the LV ransomware appear to have deployed their own personalized version of the 2.03 source binaries developed by the infamous REvil/Sodinokibi ransomware group. The LV ransomware group appears to be targeting victims in France as indicated by their latest public announcements.
Pictured (above) RaaS Group: LV Blog
Arvin Club
Arvin Club, a group that touts the mantra “Born to Connect” [translated from Persian], launched their own services on Tor, with victim data and other well-known data leaks including RockYou2021 and the Compilation Of Many Breaches (or COMB).
Arvin Club’s Telegram Channel has been active much longer than their Tor onion service and is quite popular. The channel predominantly contains re-shares of other data leaks (including the information stolen from the Ministry of Intelligence of Iran), press reports of significant cyber attacks, and onion service URLs for popular ransomware groups.
On the 5th of July, Arvin Club announced a statement refuting rumors accusing them of cooperating with the Iranian government.
“In the recent hacking case, we are accused of collaborating with the Iranian government. We do not accept this and deny it. We did not buy any data from anyone.”
Pictured (above) RaaS Group: Arvin Club
Xing is a self-claimed Chinese-language ransomware assessed to be an affiliate of the Avaddon/MountLocker ransomware family. Shortly after DarkSide hit Colonial, Xing hit another critical company to the pipeline industry, with an entry on its Tor service for Linestar Integrity Services, known for providing maintenance, compliance, auditing, and IT services to pipeline clients.
Interestingly, they refer to their victims as “participants” as if they had a choice in being targeted by the ransomware variant.
Pictured (above) RaaS Group: Xing
LockBit 2.0 – Reboot
Last summer, LockBit along with Sekhmet were allegedly key members of the Maze Cartel, e.g. ransomware affiliate program. LockBit 2.0 is a reboot of the original group’s activities with a new Tor onion service and call for “partners” keeping with the affiliate RaaS model of most darknet ransomware groups.
In their Conditions for Partners and Contacts press release they list “encryption speed and self-spread functions” as “unparalleled benefits of their ransomware software and include a list of software tests performed to back their claims.
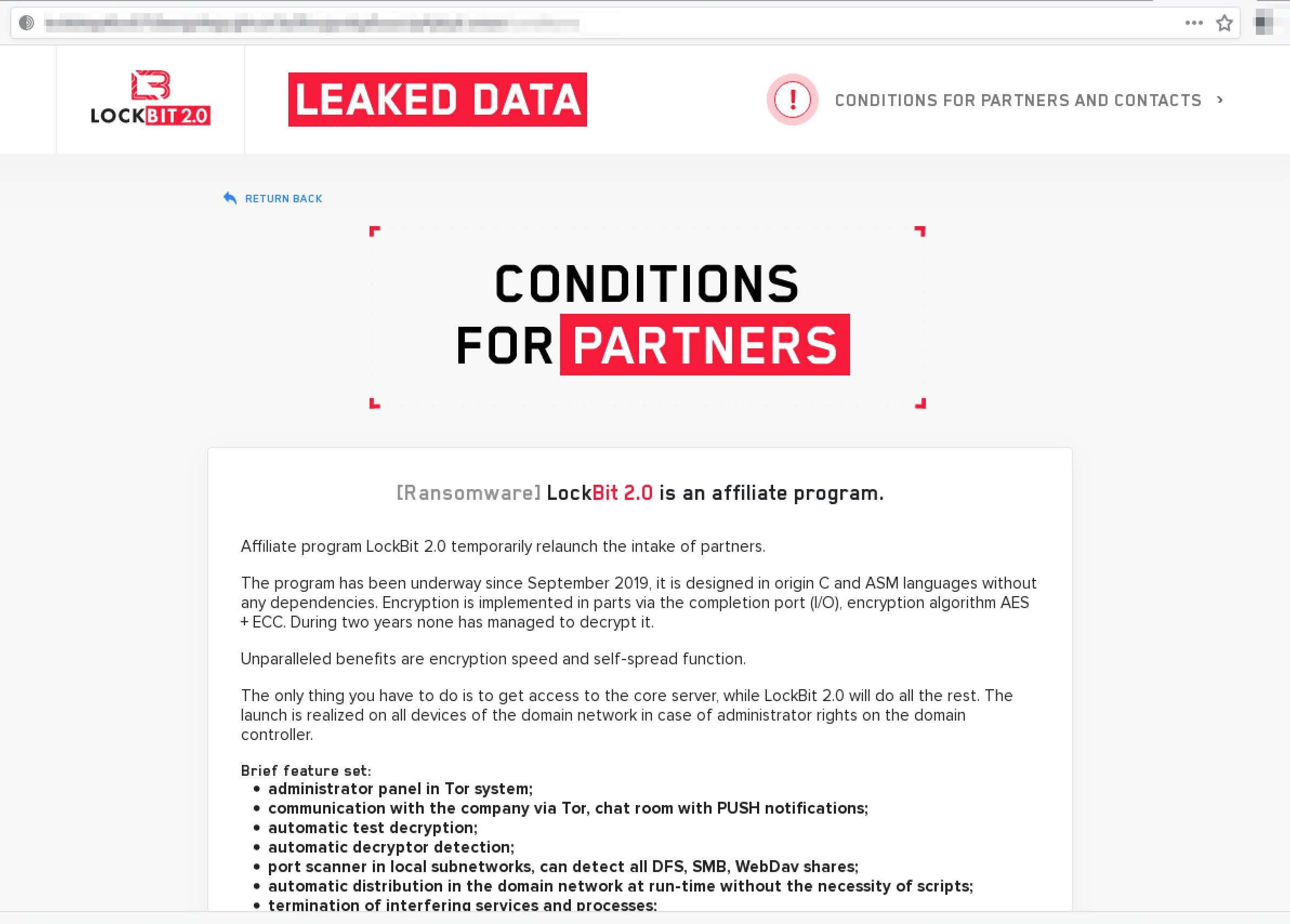
Pictured (above) RaaS Group: LockBit 2.0
Lorenz / SZ40
Lorenz’s Tor service features the tagline “Nothing personal, it’s strictly business” with an extensive list of victims in their short time of operation, launching back in April 2021. In late June, Dutch cybersecurity researchers at Tesorion released a decrypter that they were able to develop after extensive reverse engineering of this malware variant.
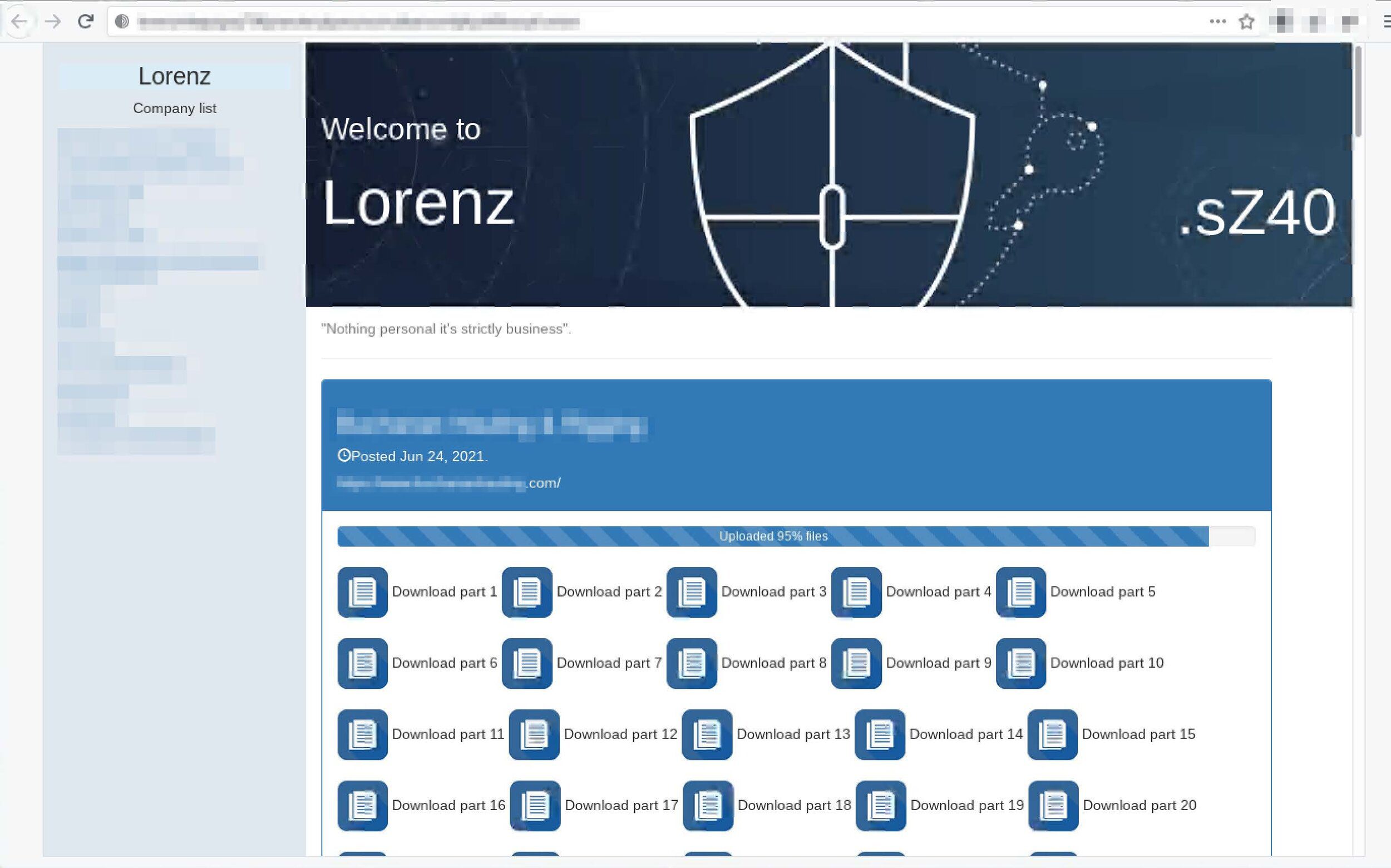
Pictured (above) RaaS Group: Lorenz
HiveLeaks
The Hive ransomware group appeared in June with little self-proclamation but instead jumping right into leaking victim data. Each victim post includes the date it was encrypted and the date when the data will be disclosed in the event of non-payment. They are credited with the security breach of software and data solutions provider, Altus Group, which took place in mid-June.
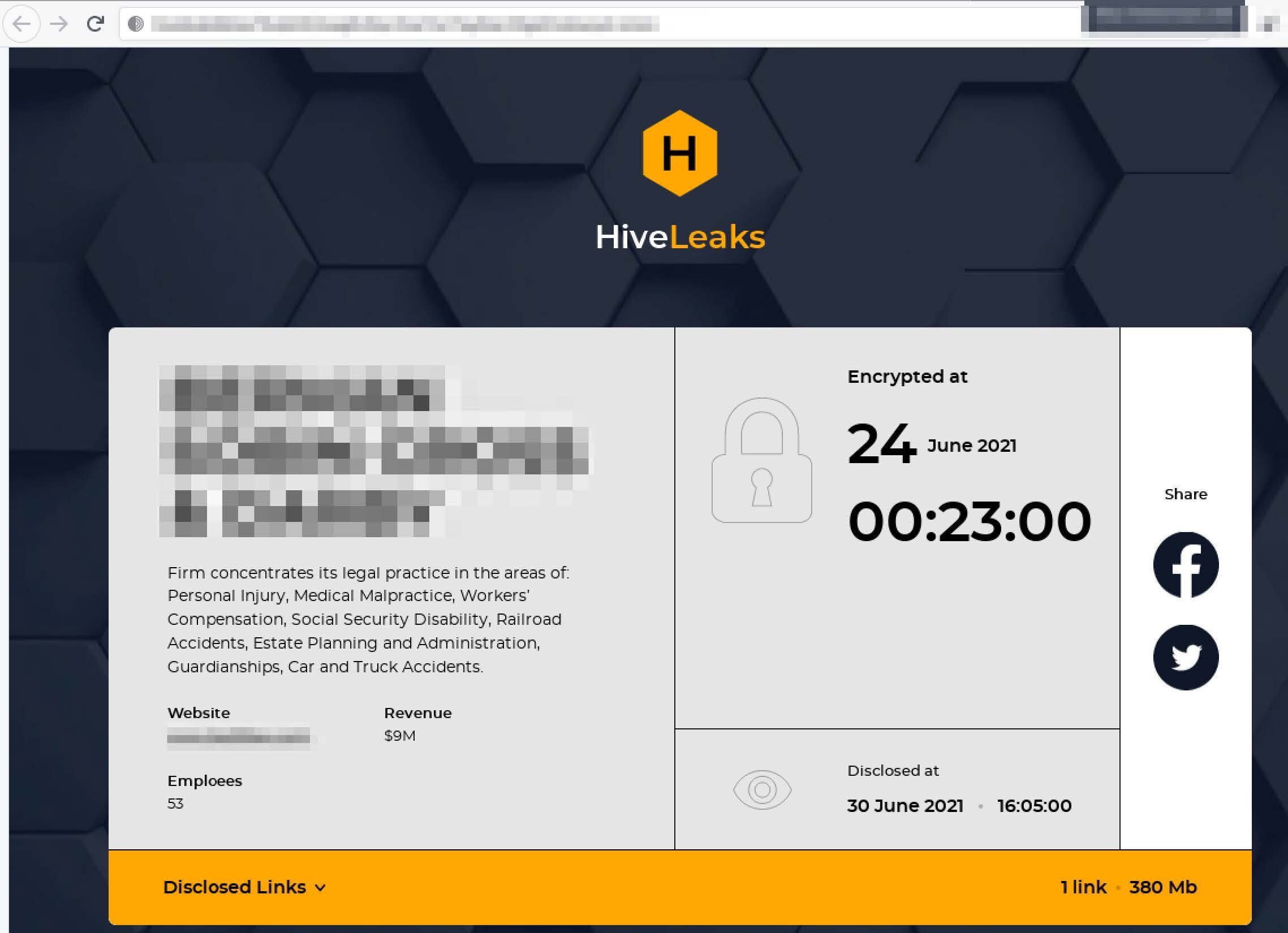
Pictured (above) RaaS Group: Hive
Prometheus
Prometheus arrived in early 2021 with claims that they were a “group of REvil.” DarkOwl analysts noticed this association had been removed from their domain in late June, perhaps due to the increased publicity REvil has received for attacks against Kaseya and JBS.
According to open-source reporting, the Prometheus ransomware variant has possible associations with the Thanos ransomware variant.
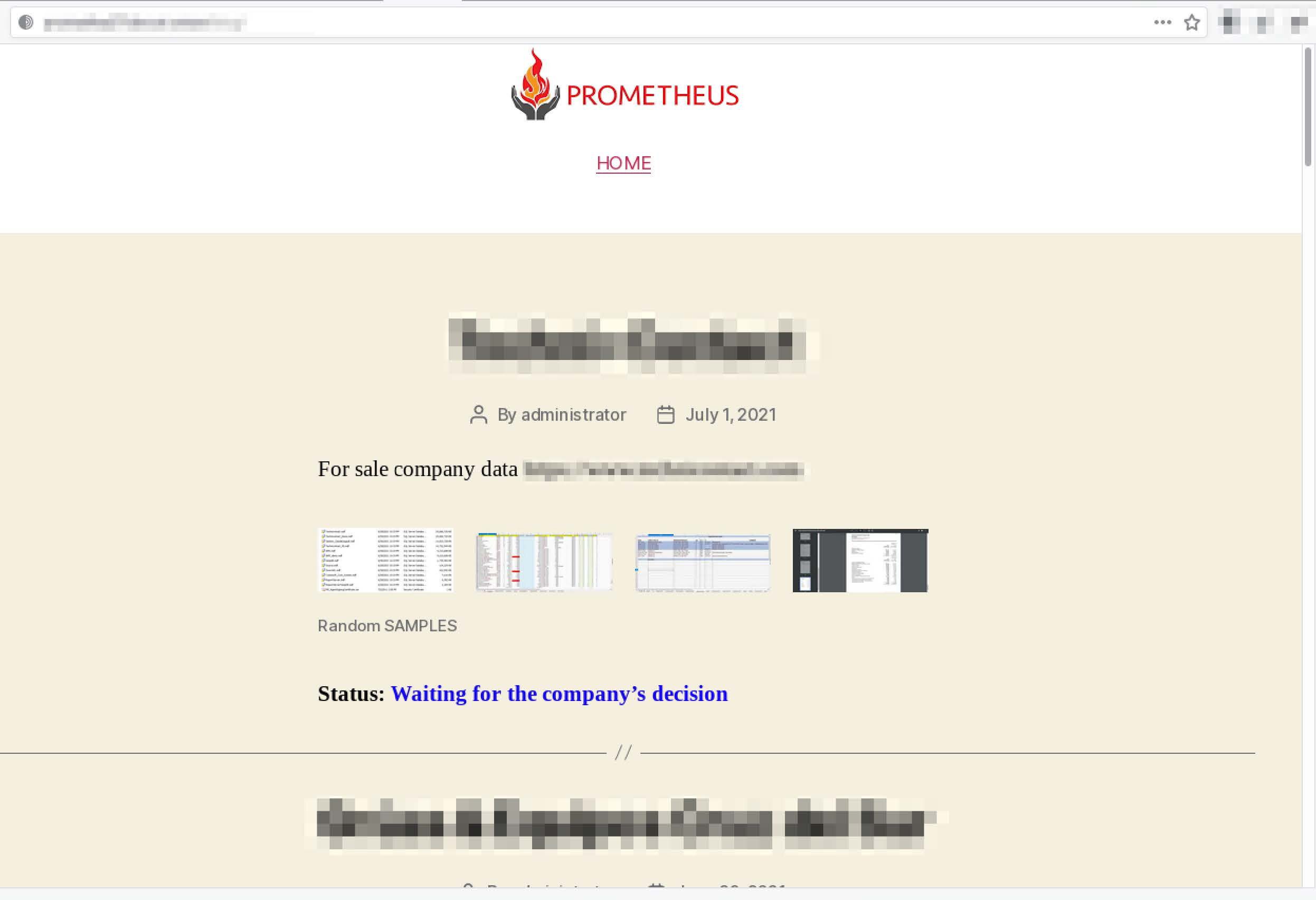
Pictured (above) RaaS Group: Prometheus
The image below is the logo for Prometheus ransomware in early June advertising their association with REvil. This designation has been removed from their Tor onion service.

Grief
The Grief ransomware has marketing and branding down to it a tee, with its “Grief came to …” theme for its public shaming of victims. The ransomware group’s latest Tor service also include infographics to illustrate the financial and economic impacts of not paying ransomware.
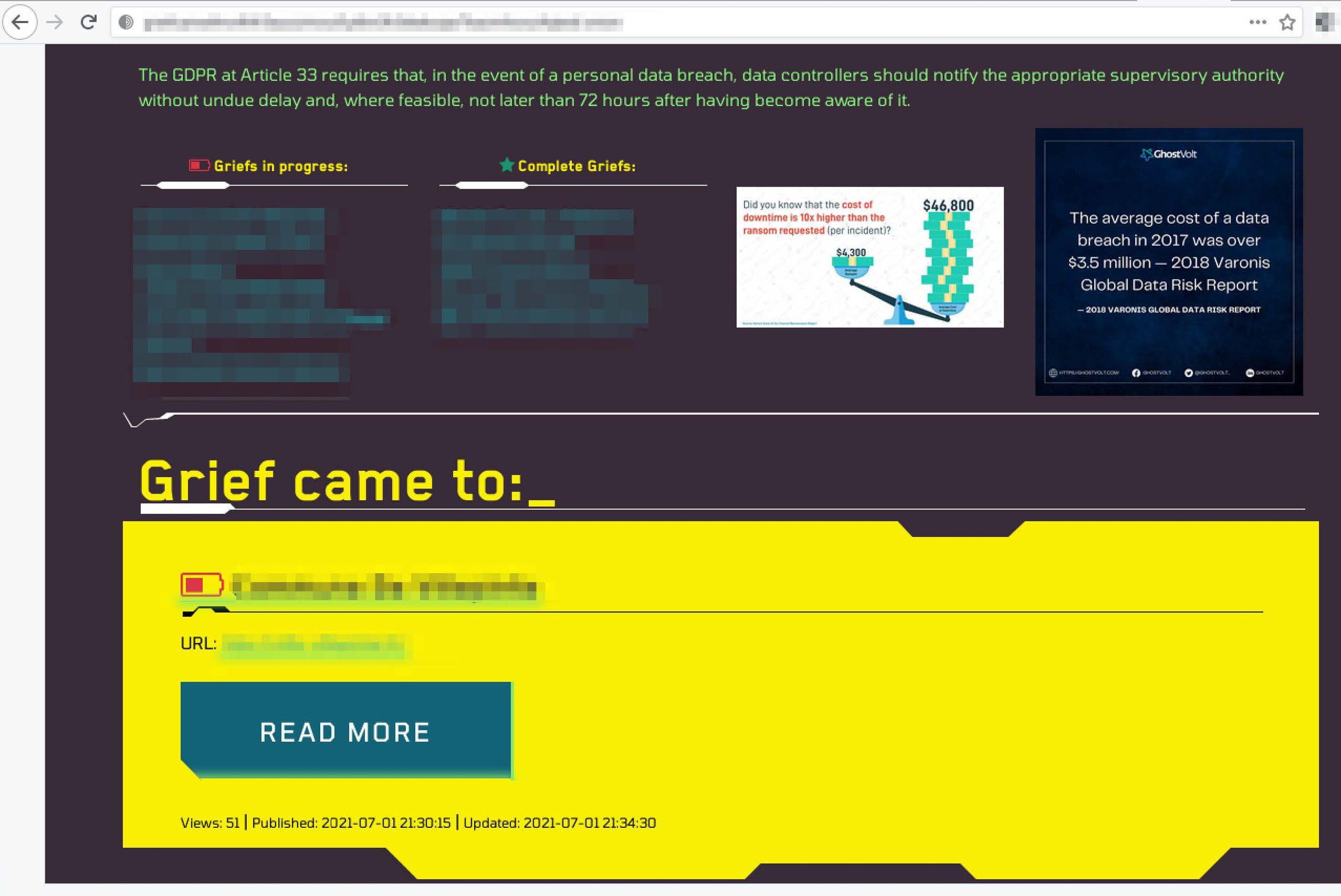
Pictured (above) RaaS Group: Grief
Vice Society
Not much is known about the latest newcomer to the ransomware community, Vice Society. They do not have any partners listed on their Tor service which features the tagline, “With Love!” Known victims include more than one school district, suggesting they are not interested in very lucrative ransom payouts. Vice Society is assessed to be a possible spin-off of the Hello Kitty ransomware variant based on similarities in the techniques used for Linux system encryption.
Pictured (above) RaaS Group: Vice Society
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















