Russians on the Darknet Part I
International media recently highlighted the perils of Russian government sponsored cyber espionage operations against US elections in 2016, and the potential risks to the upcoming US midterm election this week.
With increasing concern over the validity of the US election process, DarkOwl analysts decided a review of Russia’s footprint across the darknet could provide insight on how operations on this scale are conducted.
By the Numbers
Russia-based anonymous websites comprise over 36% of the DARKINT™ collected by DarkOwl. DarkOwl has successfully indexed over 300 million pages across anonymous and deep web networks in the Eastern Slavic language of Russian. Russian hacking and carding forums accessible from the surface web account for 92% of the deep web content in DarkOwl’s Vision.
There are significantly more Russian hidden services in Tor than sites on i2p or Zeronet, suggesting Russian darknet users prefer Tor over i2p. Russian-language eepsites account for only 10% of the i2p content archived in DarkOwl Vision. Russian activity on the anonymous network, Zeronet is negligible.
What we know the Russians have been involved in…
Enter “Russian hacking” into any surface web search engine and you will undoubtedly receive millions of results about Russia’s malicious cyber operations ranging to undermining the US democratic election process through to targeting of the US utility grid. Most recent indictments highlighted charges against seven Russian intelligence officers with hacking anti-doping agencies who used sophisticated equipment to target the organizations’ wireless (wi-fi) network. (Source)
TargetTechnique2014-2016 Hacks Against US Utilities (Link)Compromised Network Credentials via Simply Email Phishing2016 Election DNC (Guccifer) (Link)Vulnerability with DNC’s Software Provider, NGP VANUS State Voter Registration (Link)Structured Query Language (SQL) InjectionWorld Anti-Doping Agencies (WADA) (Link)Wireless Network SniffingUS Thinktanks (Hudson Institute/ International Republican Institute) (Link)Domain Phishing
When you dig into the shadows of forums and chatrooms accessible only via the darknet, only security researchers and law enforcement are actively chatting and posting about vulnerabilities to critical US systems and infrastructure. In order to discover clues about what the Russians might be up to, one would need the keywords associated with the technical specifics of the tools and techniques required to carry out such sophisticated operations.
Reports regarding the recent Word Anti-Doping Agencies (WADA) hacks stated the Russians employed a wireless network sniffing device installed in the back of the operatives’s car for access to the WADA networks . The hackers also used a mixture of malware including Gamefish, X-tunnel, and Chopstick code, the majority of which have been seen before and used on other Russian-linked cyberattacks. (Source)

Figure 1: Russian GRU mobile Wi-Fi attack (Courtesy of Dutch Ministry of Defense)
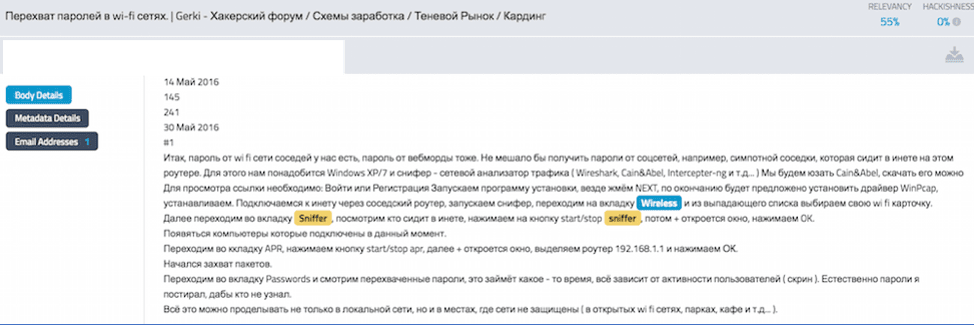
Figure 2: Russian forum discusses how to use such a device to intercept passwords for wi-fi networks
(DarkOwl Vision Doc ID: 536bb1af90f7d52b28430510685c1b51)
As evident by recent attacks against US thinktanks, the Hudson Institute and the International Republican Institute, the Russians are well known for their employment of targeted spear-phishing campaigns based upon a thorough reconnaissance and well-orchestrated intelligence collection operation prior to any network subversion. Spear-phishing is a type of hacking based on social engineering, similar to email phishing, but directed towards a specific individual or entity within a network or organization. A leaked NSA document revealed how offensive cyber officers from Russia in 2016 sent election officials emails with a MS Word attachment that was infected with a trojan of a Visual Basic script that would launch a program opening communications back to the hackers’ IP address.
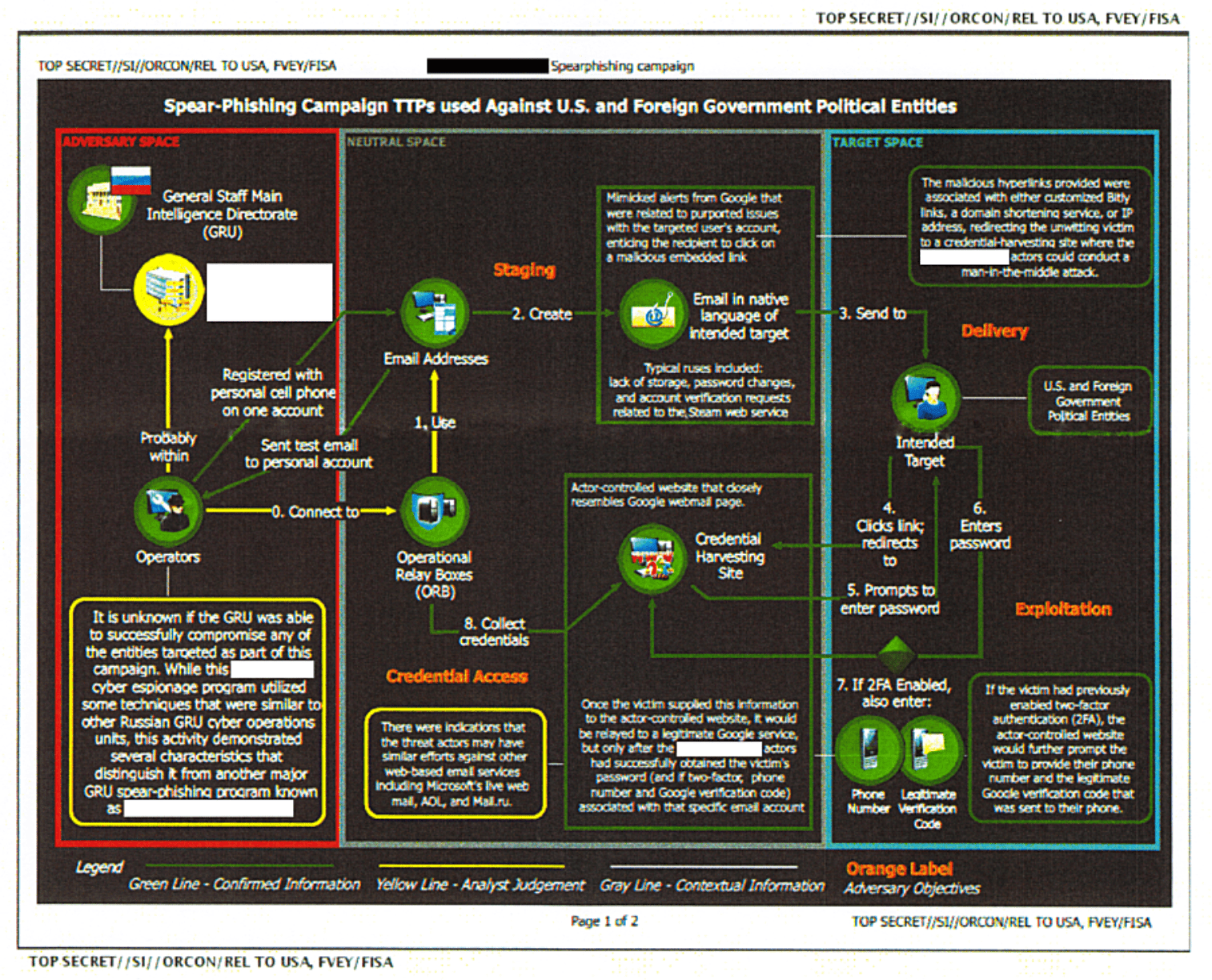
Figure 3: Detailed Tactics, Techniques and Procedures Used by the Russians to Target US Election Officials in 2016 (courtesy of The Intercept) (Read more)
The sheer volume of compromised email credentials posted for sale in Russian marketplaces and shared on authenticated hacking forums is alarming. 103 .gov email results in DarkOwl Vision contain the phrase “election” in their domain address (*@election*.gov) and could provide a valid starting point for any of the specific state election servers.
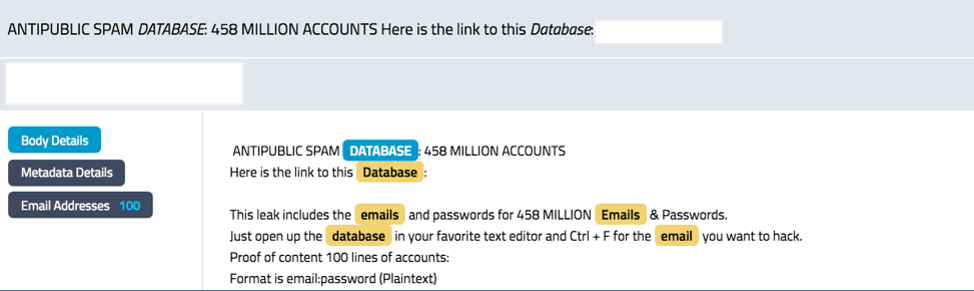
Figure 4: Advertisement of database with 458 Million Emails and Passwords for Sale in DarkOwl Vision
In the voter registration system hack in 2016, threat actors utilized simple whitehat vulnerability tools such as Acunetix, network discovery and exploitation kits like DirBuster, SQLMap, and SQLSentinel. Russian speaking hacker, Rasputin, infamously employed a proprietary-developed SQL injection exploit to successfully breach and harvest credentials from U.S. Election Assistance Commission (EAC) servers including accounts with administrative privileges. (Source)
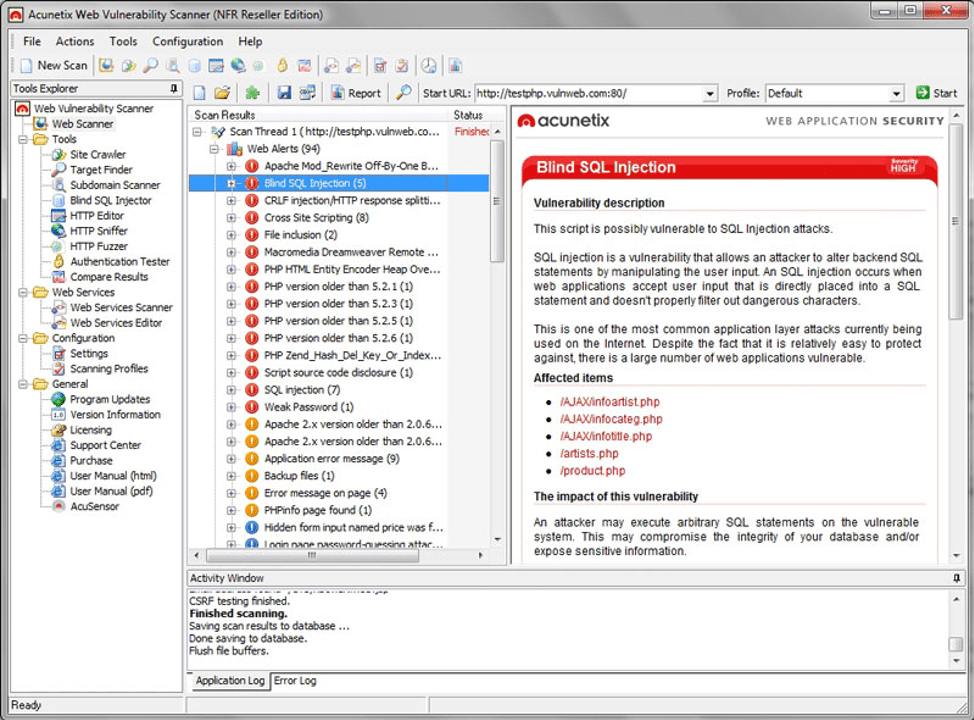
Figure 5: Acunetix Web Vulnerability Scanner in Action
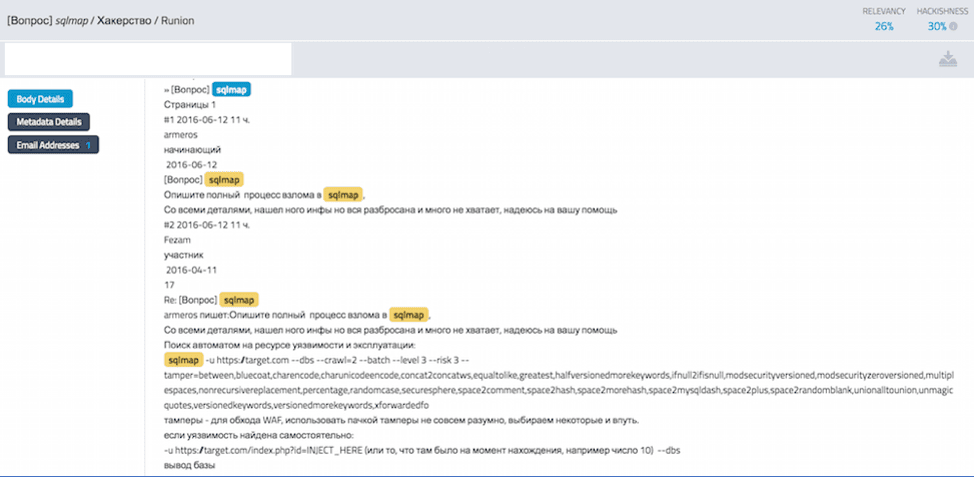
Figure 6: Discussion of how to use SQLMap against a target network on a Russian forum
(DarkOwl Vision Doc ID: 53e19c5fbe5c7d9c6e625e668d660617)
For the past few years, millions of US voter registration data with full names, address, and voting data have appeared on offer for sale on darknet hacking forums and marketplaces. DarkOwl has observed data from over 30 states ranging from $250 to $5000 USD per state including: Colorado, Ohio, Connecticut, Florida, Michigan, North Carolina, New York, Pennsylvania, Rhode Island, Washington, Kansas, Wyoming, Oklahoma, Maryland, Arkansas, Nevada, Montana, Louisiana, Delaware, Iowa, Utah, Oregon, South Carolina, Wisconsin, Georgia, New Mexico, Minnesota, Kentucky, Idaho, Tennessee, South Dakota, Mississippi, West Virginia, Alabama, Alaska, and Texas.
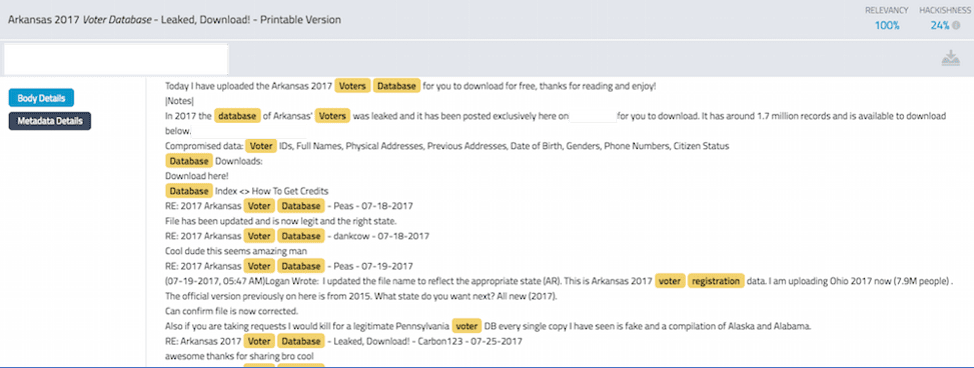
Figure 7: Deep Web Forum post with Content of Arkansas’s Voter Registration Database
(DarkOwl Vision Doc ID: 6e235a3bab7e4e3f293fb2f0f57c6cae)
Many of the posted state databases are older, i.e. Alabama and Alaska’s voter registration information is from 2015; however, many of these databases were on offer back on the infamous Alphabay darknet marketplace in 2016 as well.
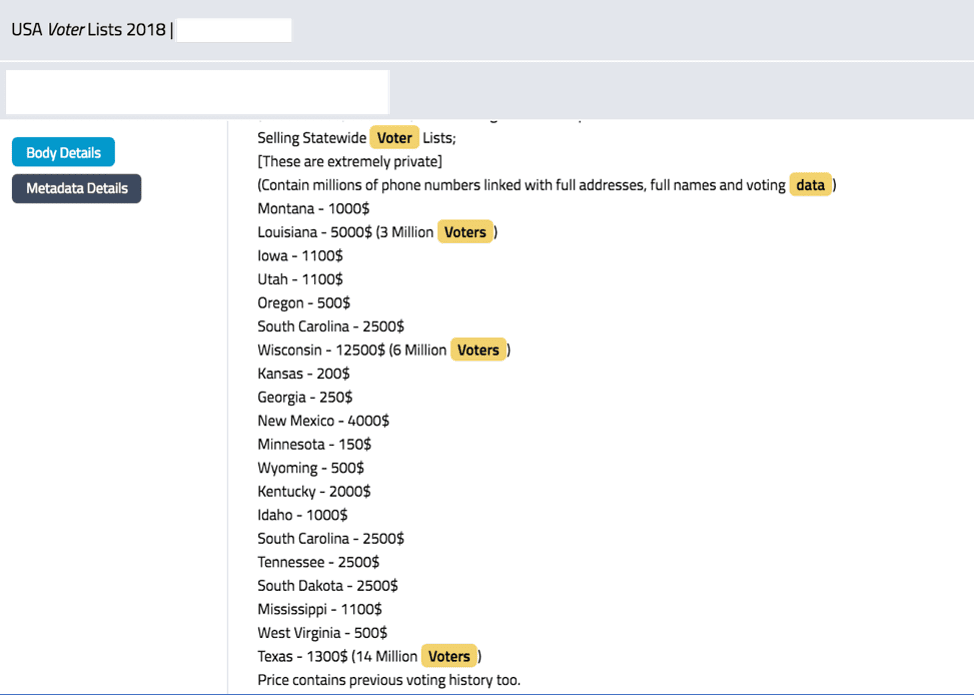
Figure 8: A recent offer for several US State’s Voter Lists for sale as archived by DarkOwl Vision
(DarkOwl Vision Doc ID: cfae62df845b99fc173c42bd3b529303)
In recent weeks, comments from the vendor suggests that the voting records hacker has setup persistent access to the states’ databases, posting, “Besides data is refreshed each Monday of every week, once you request the data from me you will receive the freshest possible data from that state.” The fact this data is on the darknet is no surprise, as it is publicly available, open source information. It is a surprise anyone would actually pay for access to the information they could easily obtain themselves. Links to some of the state’s databases have appeared on some darknet forums as is, without any access payment required.
The hacker on the forum identifies themselves as a white male software engineer from the United Kingdom and “apathetic human-being” with other information that could be easily pivoted to the surface web. There is no indication he is affiliated with Russian government sponsored hackers.
Russia-affiliated threat actors and hackers, whether lone wolf or operatives of a major government-led cyber offensive, have more than sufficient tools and resources across the deep web and darknet to successfully exploit and profit from network and/or server vulnerabilities. Utilizing commercially available penetration testing resources and exploits circulated and sold on the darknet, hackers regularly infiltrate networks while completely evading detection or knowledge of the system’s administrators. Next time we will review some of the Russia-specific marketplaces and forums where these attack techniques are planned and coordinated.
Curious about something you’ve read on our blog? Want to learn more? Please reach out. We’re more than happy to have a conversation.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















