Shiny Leaks and Criminals: SolarWinds, Seller13 and ShinyHunters
During review of recent darknet hidden service domains collected from Tor, DarkOwl analysts discovered a new ‘leaks-focused’ marketplace called “Dark Leaks Market” featuring a wide range of leaked databases and documents from recently ransomed corporate organizations. An underground forum user, using the alias “Seller13” shared the URL for the marketplace while promoting their most recent acquisition of documents identified as “Solar Winds Data Leak” consisting of critical client information related to SolarWinds customers.
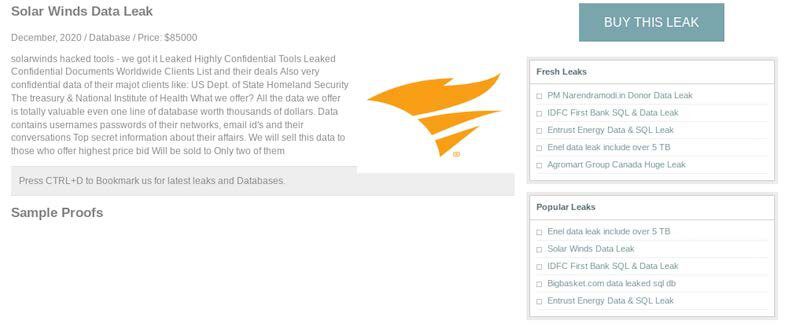
In late December 2020, DarkOwl discovered an advertisement identified as “The Solar Winds Data Leak” on the Dark Leak Market for $85,000 USD. The database was listed as including “highly confidential tools leaked documents with worldwide client list and their deals” as well as “usernames passwords of their networks, email id’s and their conversations – [including] Top secret information about their affairs.”
While the database is listed for sale for $85,000 USD the advertisement further states they are offering to sell this data to those who offer highest price bid and will be sold to only two of them. As of January 3, 2021, the price had dropped to 0.5 BTC, or approximately $16,000 USD according to historical Bitcoin prices during the same time.
Who is Seller13?
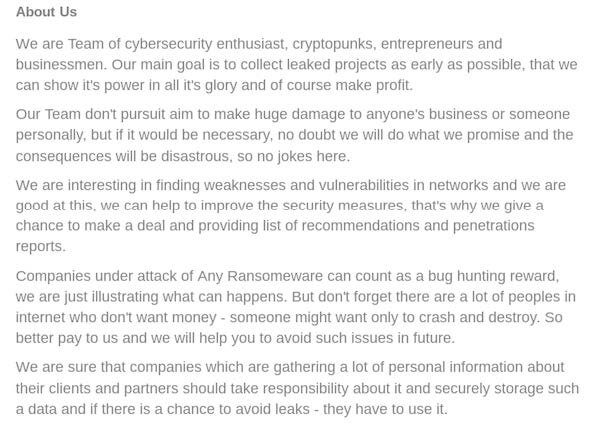
The “Who Are We” section of the market identifies the group as a “team” of “cybersecurity enthusiasts, cryptopunks, entrepreneurs and businessmen” who are clearly non-English speaking cyber criminals as apparent by the significant number of grammatical and spelling errors throughout their operations’ description. This suggests that “Seller13” is not a lone-wolf style cybercrime enthusiast, but instead a group of criminals working together to infiltrate commercial networks and capitalize on crimes across the darknet.
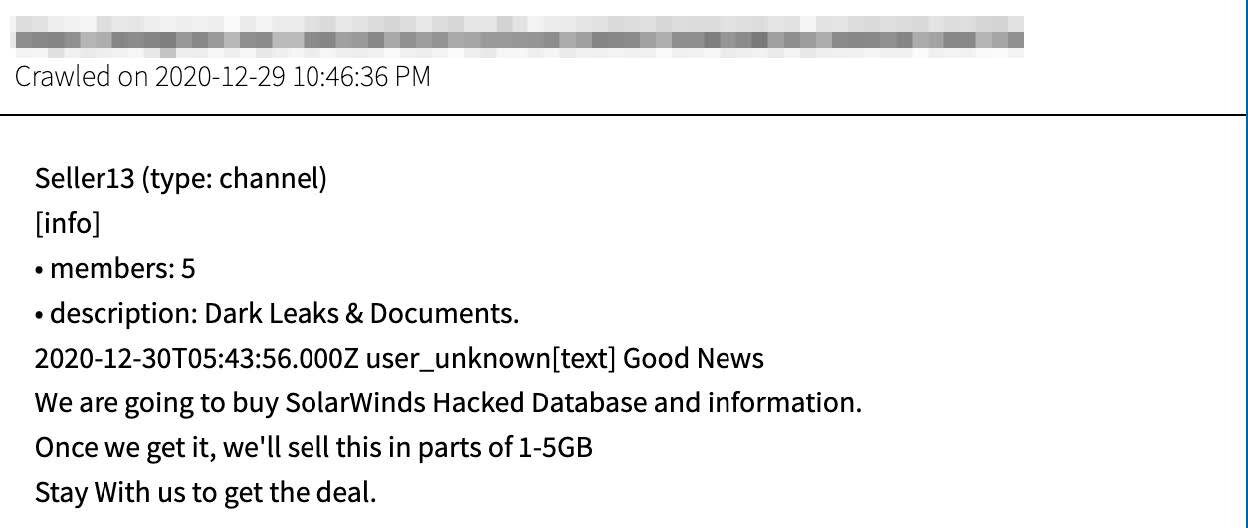
DarkOwl also uncovered an encrypted chat channel, hosted by Seller13 and only accessible by invitation, where they are even more exuberant about their acquisition of SolarWinds related leaks. Their latest comments, posted in the early hours of the week before New Year’s, suggests that they were in the process of purchasing SolarWinds “hacked database and information” and were going to resell it in parts of 1 to 5 GB increments.
As of January 3, 2020, Seller13 stated they were uploading the SolarWinds data to mega.nz.
Using DarkOwl Vision, analysts discovered that a user with the pseudonym of “Seller13” has an extensive history of activity on the darknet, including a deep web forum discussing weapons popular with native Russian speakers.
DarkOwl detected advertisements from early as 2011 on a deep web forum selling various small arms and accessories, including MMG Thompson M1 and the RP 46. This suggests that not only is Seller13 possibly from Eastern Europe, they have a history of criminal activity and extensive connections with cyber criminal organizations that have been historically active across the darknet and deep web.
Compromised commercial website data shared on popular deep web forum, RaidForums links the alias “Seller13” to several email addresses, such as: [email protected], [email protected], and [email protected]. DarkOwl has little to no confidence that the email address: [email protected] is connected to the darknet actor, Seller13, based on the commercial website where it was obtained. However, the hotmail.de email was more interestingly associated with the pseudonym “Seller13” in a data breach called “l33t crew members” from 2017.
A connection to REvil?
Ironically many of the databases offered for sale on the Dark Leak Market and advertised on Seller13’s Telegram channel have been previously observed as data obtained via ransomware attacks by the ubiquitous REvil criminal organization out of Eastern Europe. DarkOwl analysts recorded victims such as Kenneth Copeland and Agromart, as previously advertised on the “Happy Blog” darknet hidden service published by the REvil group back in 2020.
It is unconfirmed whether Seller13 is a legitimate darknet vendor of actual criminally obtained data or just another darknet scammer who is in the business of capitalizing on popular commercial datasets, such as SolarWinds and will simply take their customer’s cryptocurrency and never deliver any meaningful data. DarkOwl has surmised several possibilities around Seller13’s ultimate intentions and how they obtained the data they have listed on their hidden service: did Seller13 obtained the data via purchase with intent to resale? Are they acting as an agent of REvil, given the negative publicity received by the ransomware group? Lastly, is Seller13 a legitimate member of the REvil team that has spun off to start the Dark Leak Market?
Regardless of who they really are, the advertised databases outside of REvil confirms that once a victim has been compromised there is no assurance that their data will stay with the group that stole it.
Seller13 Rebranding as ShinyHunters Affiliate
Since the initial detection of Seller13 on the darknet and Telegram, DarkOwl recently discovered the threat group launching a concerted rebranding of their cybercriminal commercial operation from “Seller13” to “S# Hunters.” Their activity across Telegram and the darknet now references @Omn1p0t3nt for additional contact and speaks of the availability of numerous “Shiny Leaks” on offer. Their current and historical advertisements on public darknet hidden services alludes to the availability of “ransomware setup, source codes, and dark web marketplace scripts” for sale further connecting this group of threat actors to ransomware criminal groups.
ShinyHunters is a pseudonym affiliated with an infamous darknet threat actor group who has released significant volumes of databases from compromised commercial websites around the world – databases containing millions of leaked email addresses and passwords, and personally identifiable information (PII) such as full names, addresses, credit card data, and IP address. News of their most recent database leak, from online dating service, MeetMindful was discussed in recent information security open-source reporting.
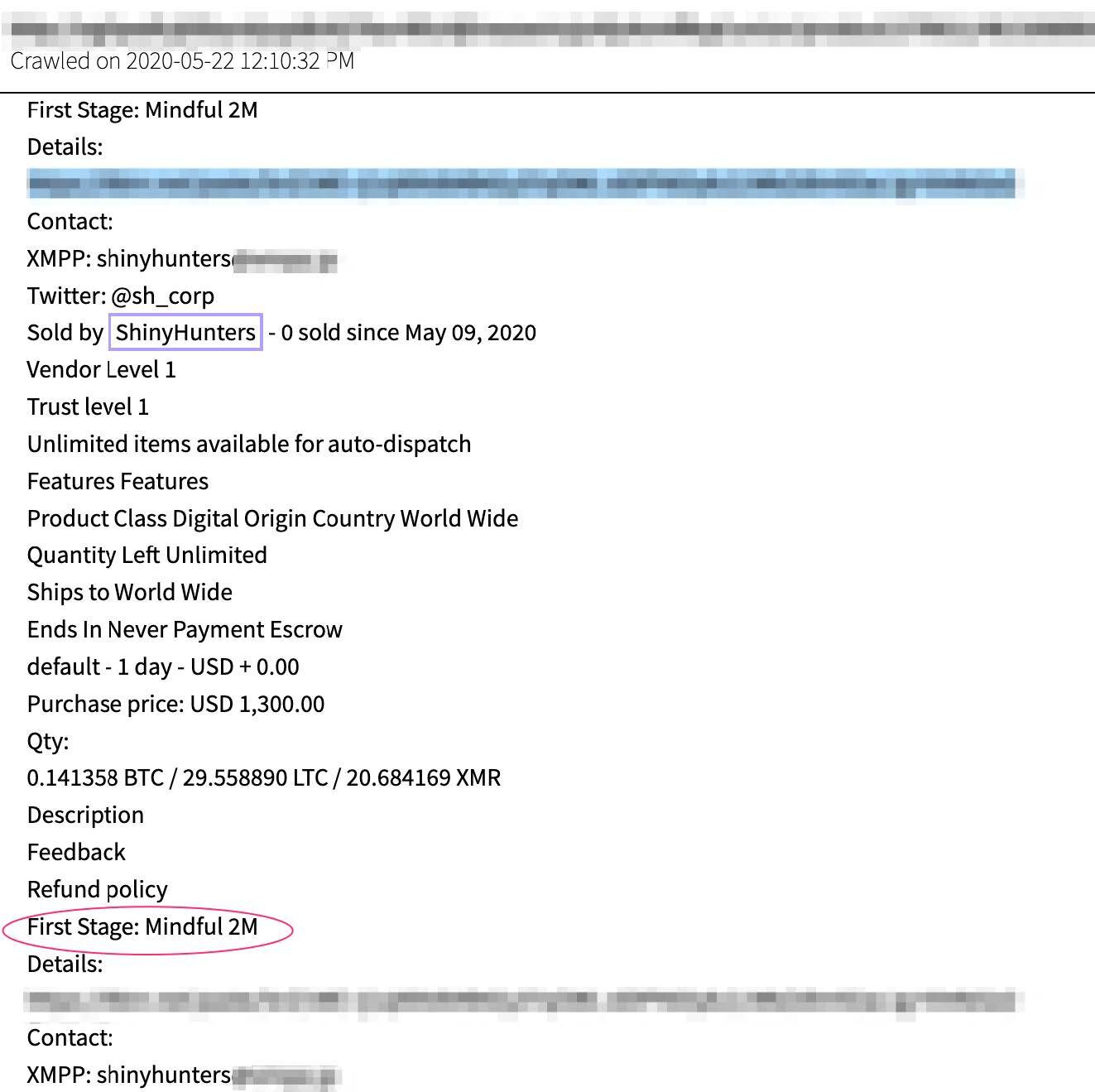
ShinyHunters has been extremely active across many Russian and English speaking darknet and deep web networks and communications, including Telegram for the last couple years. DarkOwl has also observed the group actively selling leaked databases on Empire Market where an offer for “First Stage Mindful 2M” – likely affiliated with the MeetMindful database leak, was offered for sale as early as May 2020 for $1300 USD.
According to some darknet sources, ShinyHunters has supposedly also previously used the moniker, Prosox, who has been active since at least 2018 with a “team of Moroccan hackers” across the deep web, Telegram, and Discord. They are most notorious for defacing YouTube titles via a zero-day vulnerability now patched by the content provider.
After careful review of the Dark Leak Markets and the advertisements for “Shiny Leaks” the threat actor now calling themselves “S# Hunters” has posted across various hidden services on Tor, there is strong probability this threat actor is merely scammer, capitalizing on the public media attention the real “ShinyHunters” darknet cybercriminal group is receiving.
In some of their most recent posts, they refer and give credit to a Telegram user known as @Omn1p0t3nt, who they state acquired hacked “Fire Eye Tools” presumably from the SolarWinds and Sunburst exploits. This pseudonym is extremely similar to another popular deep web threat actor and administrator of RaidForums, knowns as “Omnipotent” without the “l33t” spelling, further suggesting a scammer’s psychological game is in the works.
DarkOwl will continue to follow as more information is available.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















