The Darknet Economy of Credential Data: Keys and Tokens
May 26, 2022
In this blog, we review how sensitive, server-side access credential data – such as AWS private/secret keys, Django secret keys, and API tokens – are captured, circulated, and sold across darknet marketplaces and criminal communities.
Darknet Background
The darknet, which is also referred to as the dark web, is a segment of the internet that is only accessible by using specialized software or network proxies. Due to the inherently anonymous and privacy-centric nature of the darknet, it facilitates a complex ecosystem of cybercrime and illicit goods and services trade. Adjacent to the darknet is the deep web and instant chat platforms that play an increasing critical role in facilitating this illicit information availability. Pseudo-anonymous discussion forums and vendor marketplaces hosted on the deep web along with Telegram private and public channels provide additional platforms by which threat actors communicate and circulate sensitive and stolen credential data.
There are multiple types of underground criminal communities that are directly involved in the circulation of stolen credential data. The threat actors from these communities are often categorized as:
- Initial Access Brokers: specialize in providing direct access to organizational networks to conduct offensive cyber campaigns. Access is offered for sale on darknet malware discussion forums and exploit marketplaces.
- Database Brokers: specialize in exfiltration of large datasets from compromised organizations. Databases are traded and sold on darknet marketplaces and Telegram channels.
- Nation-State Sponsored / Cyber Criminal Gangs: these groups are intent on conducting cyber operational campaigns in fulfillment of geopolitical or military initiatives, cyber espionage, and/or information operations. Some gangs are also financially motivated and will extort the victim for financial payments once keys have been leverage for access and theft of sensitive data.
There is also the odd and less publicized ‘hacker skid’ or hobbyist hackers that will scour the darkest corners of the Internet for server-side credential data for simply the psychological thrill of the hunt. These threat actors do not have direct intent for monetary gain, nor even probable use, but seek to feed their egos and increase their personal clout by stealing keys and communicating their various levels of illegal access to high-profile criminal groups and hacking enthusiast communities and chat servers.
Critical Credential Data
This blog is focused on server-side credential data for development and cloud-based server assets. Credential data is also referred to as username/email-address and password combinations, which will not be discussed here.
There are several types of “keys” that threat actors are interested in obtaining:
- Amazon Web Service (AWS) Key Management Service (AWS KMS) Access Keys: ‘poweruser’ and administrator encryption keys for the managing Amazon-hosted services.
- AWS Identity Access Management (IAM) keys: consist of long-term credentials users will use to sign programmatic requests to AWS Command Line Interface (CLI) or AWS API.
- Azure Keys & Secrets: Credential data stored inside Azure Key Vault (KV). Data includes database connection strings, account keys, passwords, and JSON Web keys.
- Django SECRET_KEYs: secret key for a particular Django installation that is used to provide cryptographic signing.
- Google Key Management System (KMS) Customer Managed Encryption Keys (CMEK): project-id’s and private keys for service accounts on the Google Cloud Platform (GCP)
- API Keys: keys required for any number of application programming interfaces
Unfortunately, the threat actors do not always delineate types of keys they’ve obtained or are offering. Many times the threat actor simply advertises the platform and the word “key” in the forum post or marketplace advertisement.
Key Compromise
Commercial application developers have been guilty of copying and pasting keys in organizational Github repositories that are publicly accessible via automated web scrapers. Malicious threat actors actively hunt for such keys across software repositories and unprotected s3 buckets and then utilize the keys for malicious campaigns or trade in the darknet. Sometimes such exfiltrated data is stored on transient paste sites prior to distribution, that is captured by DarkOwl.
A recent example of a ‘dump’ of secret server keys is demonstrated in the figure below. These were discovered by simply using DarkOwl’s proximity search to find documents where the words ‘AWS’ and ‘key’ are within two words of each other.
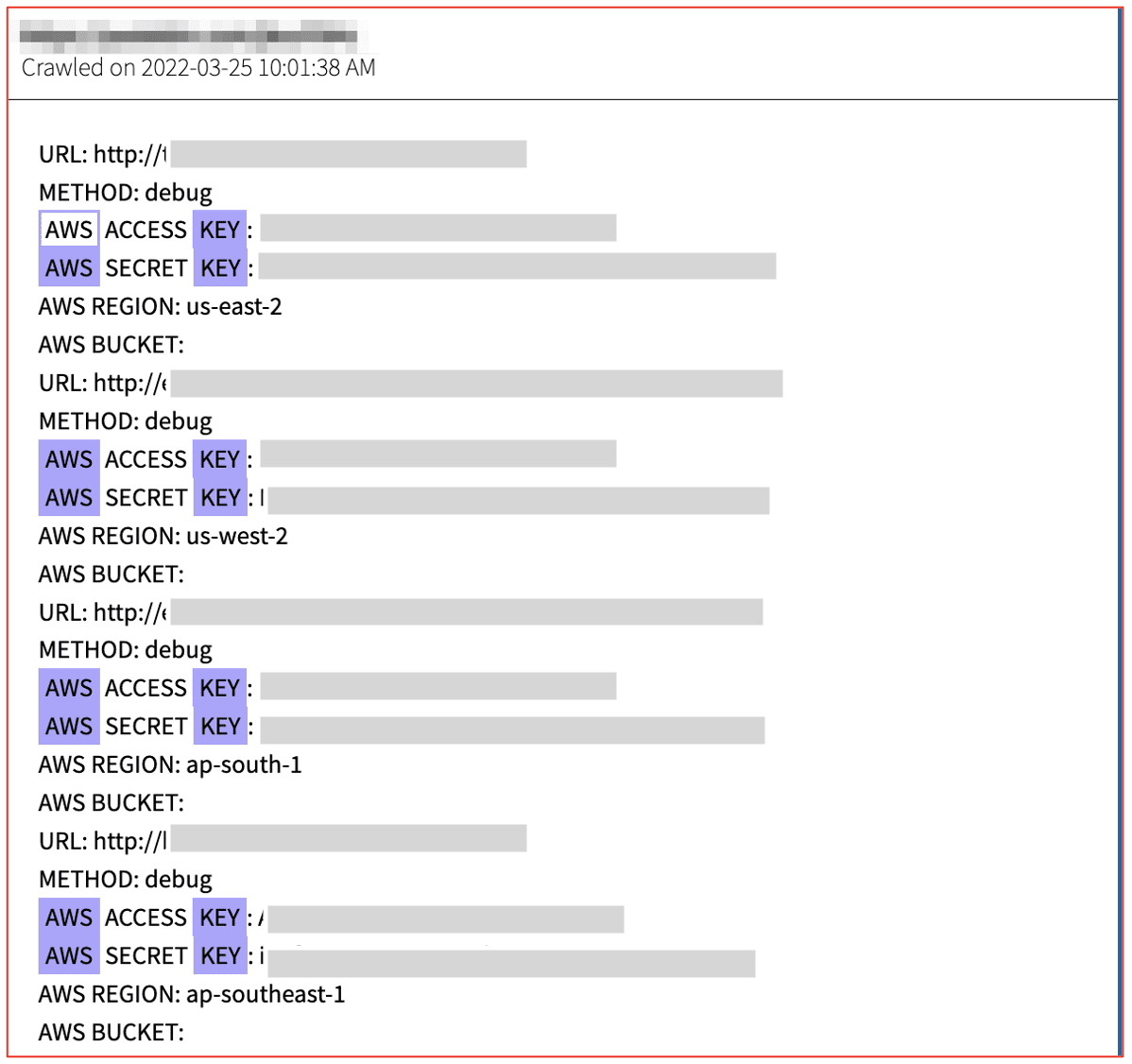
Figure 1: Source DarkOwl Vision
Some threat actors offer zero-days on malware-centric Telegram channels and darknet discussion forums that facilitate the scanning of Gitlab and Github. In early 2021, a user on AIO Crime, using the moniker soapceo, offered a 0day for searching private repositories for AWS keys for $10K USD.
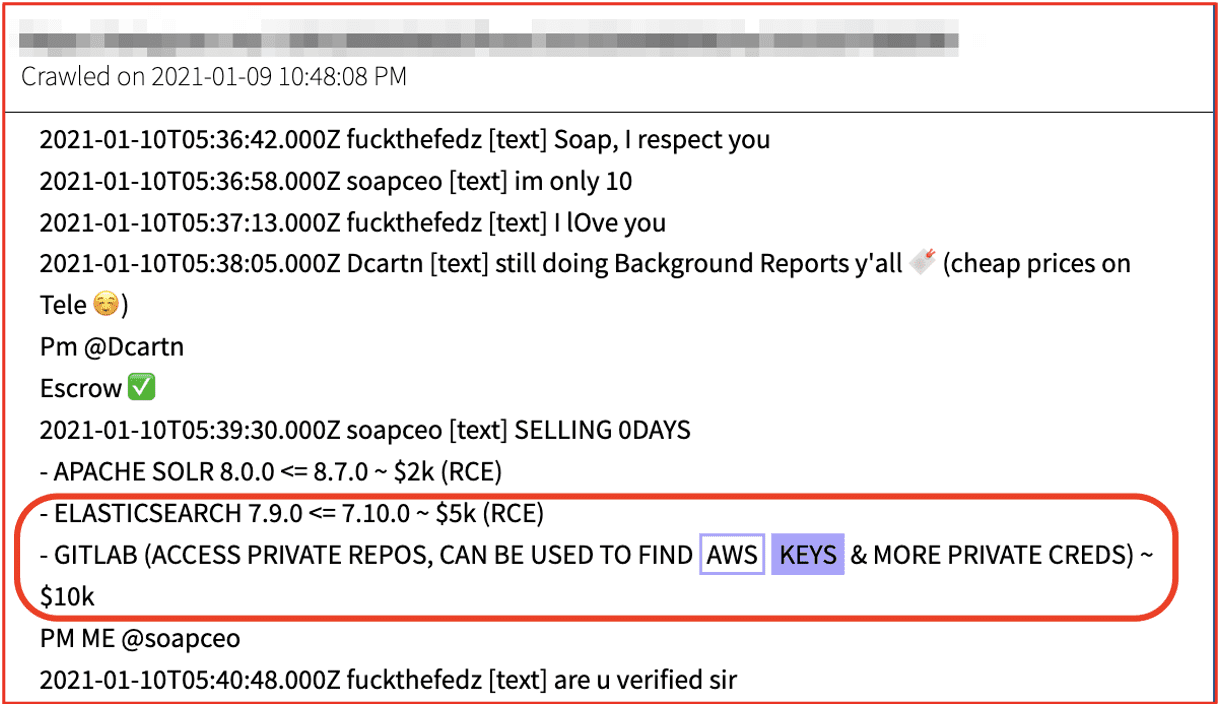
Figure 2: Source DarkOwl Vision
Other malicious actors employ malware, such as information stealers (a.k.a. infostealers) to steal session tokens and keys. Infostealers such as Redline, Jester, and Eternity – often installed onto victim devices via malicious email campaigns – covertly log and exfiltrate sensitive data from the victim’s device to cause additional harm.
According to open-sources, information security researchers have identified similar information stealer malware in the wild, such as TeamTNT_AWS_Stealer that specifically targets virtual/cloud platforms to exfiltrate sensitive AWS keys on Kubernetes and Docker clusters adjacent to the compromised container.
DarkOwl identified malware called Laravel Monster that is advertised as an “all-in-one grabber” that exfiltrates AWS keys “and more” offered on a popular Russian-speaking forum. The malware also includes a built-in AWS checker that validates whether the keys harvested are active and live and could be used to compromise the server.
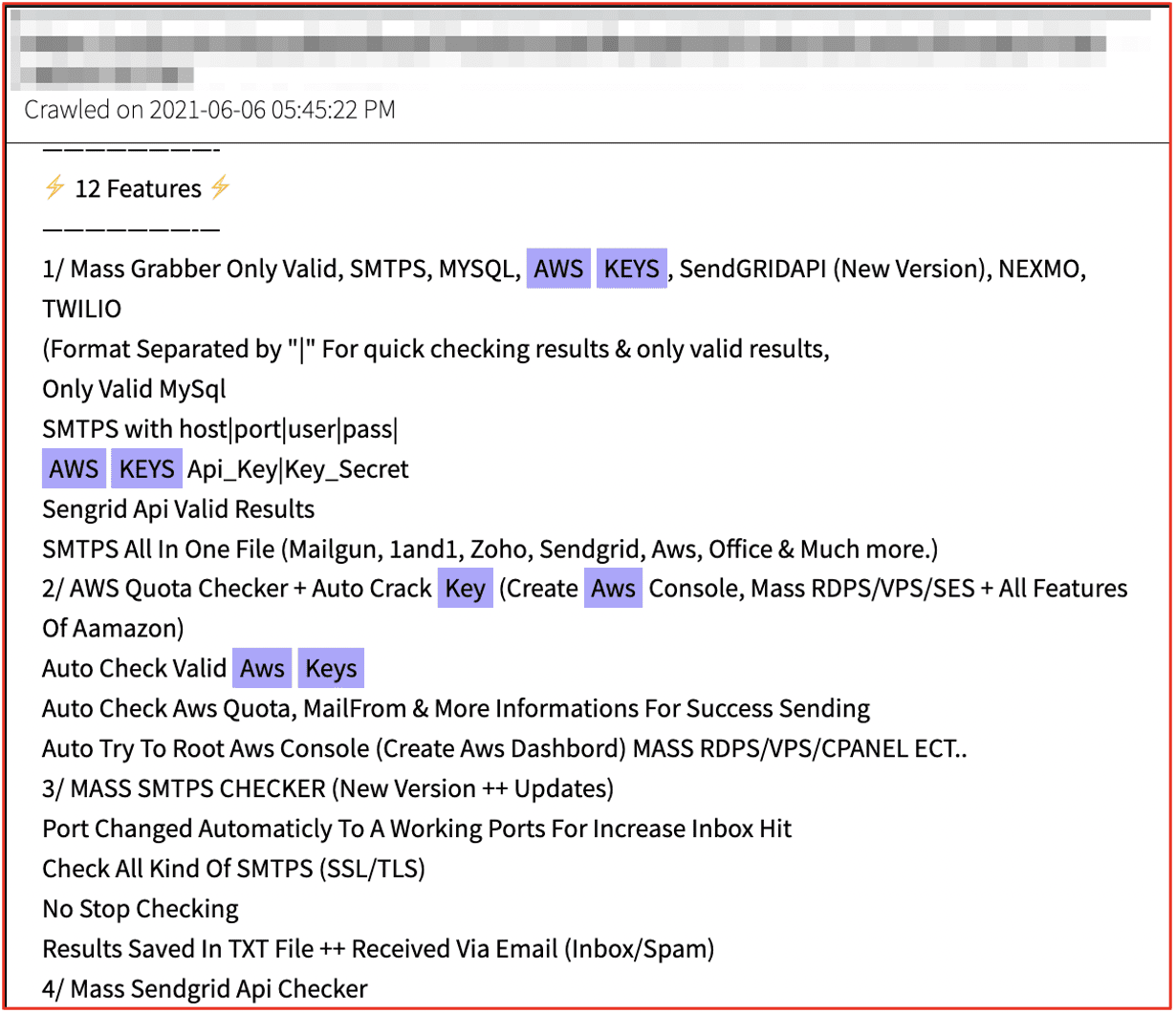
Figure 3: Source DarkOwl Vision
For reference, in early 2022, we observed another example of a “Git Scanner” malware is included from the exploit forum for $4K USD to $8K USD depending on the features of the software. A YouTube video demonstrating the software is also included in the post.
In April 2022, a user posted an offer on Telegram for something called, “INJECTOR V3” and a hacking guide known as “Amazon AWS SMTP Method 2022.”
It’s unclear what the details of this method entail (as we did not purchase it); however, other chatter on Telegram suggests it “cracks” AWS servers, uses the server to carry out malspam email campaigns, e.g. phishing, and may even harvest data while on the server.
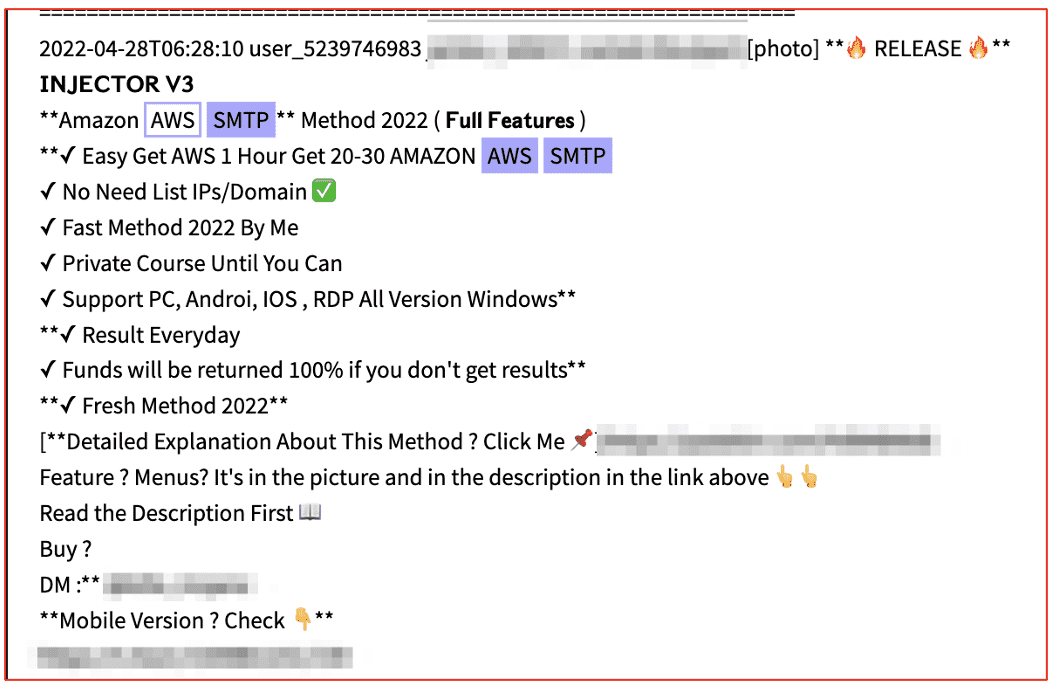
Figure 4: Source DarkOwl Vision
Keys on Offer
DarkOwl has observed sensitive credential data and keys on offer across the darknet and adjacent chat platforms known for facilitating cyber-crime. Darknet and deep web forums popular for discussing critical credential data, e.g. keys include many of the malware-specific forums such as XSS. Many times the mention is in relation to “how to exploit” what they’ve discovered on the compromised cloud asset, while others are offered “for sale” in the ACCESS section of the embedded marketplace in the forum.
Darknet threat actors utilize Jabber XMPP and Telegram services in conjunction with their accounts on malware discussion forums to communicate directly with their customers and/or provide more detail about their use of malware they’ve developed or are on offer.
Some threat actors have dedicated “public” Telegram channels where services and digital goods are offered for sale. DarkOwl has observed keys for sale on darknet forum threads and Telegram channels. Many offers on Telegram include offers for keys to simply increase their credibility in the space and encourage customers to do business with them.
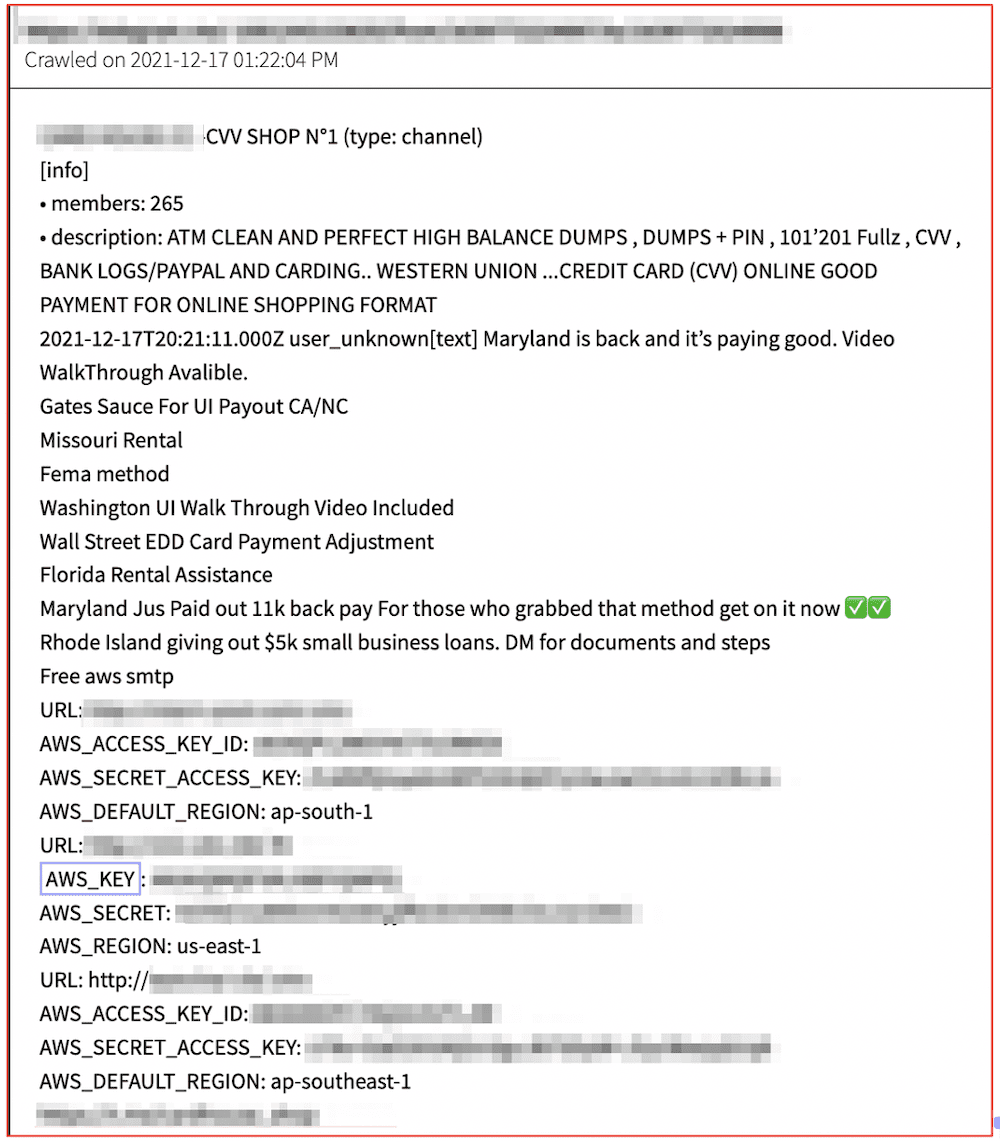
Figure 5: Source DarkOwl Vision
While many keys are captured via the methods mentioned above, sensitive SDK API keys are often stolen during organizational cybersecurity incidents, and then circulated by groups on the darknet and in Telegram channels. In summer of 2021, the Electronic Arts (EA)’s FIFA software servers were compromised by a cybercriminal gang, and the data is still in circulation.
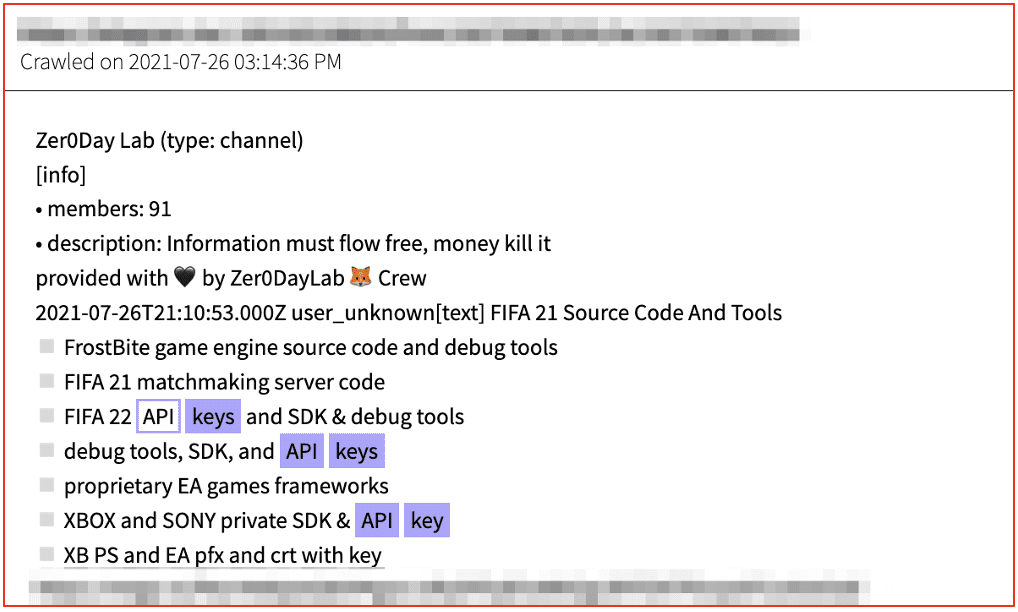
Figure 6: Source DarkOwl Vision
Sometimes a discovered or stolen key is utilized to access a cloud or platform panel and the threat actor offers the ‘panel’ for sale. In late 2021, a Telegram market, known as “The Grand Exchange” advertised an Azure panel on offer for sale. The advertisement references a deep web marketplace for the vendor.
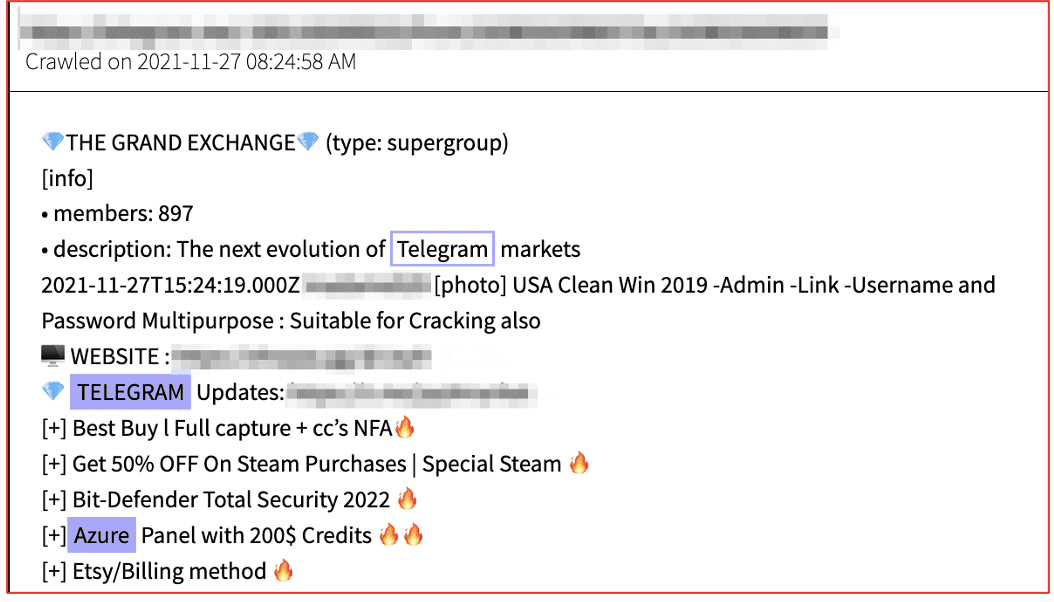
Figure 7: Source DarkOwl Vision
Many API keys in circulation on the darknet are offered for free. DarkOwl has observed several recent software API keys offered for free on popular commercial-accounts-trading Telegram channels.
In 2020, a Telegram channel user states they have a Binance API key they obtained via information stealer malware.
In March 2021, an initial access brokers advertised sensitive credential data and cloud access AWS “root” keys for a USA company on a popular darknet malware development forum. The keys were on sale for $80K USD and the threat actor included the revenue estimates for the company and AWS bills to justify the cost of the keys in correlation to the potential ransomware extortion values.
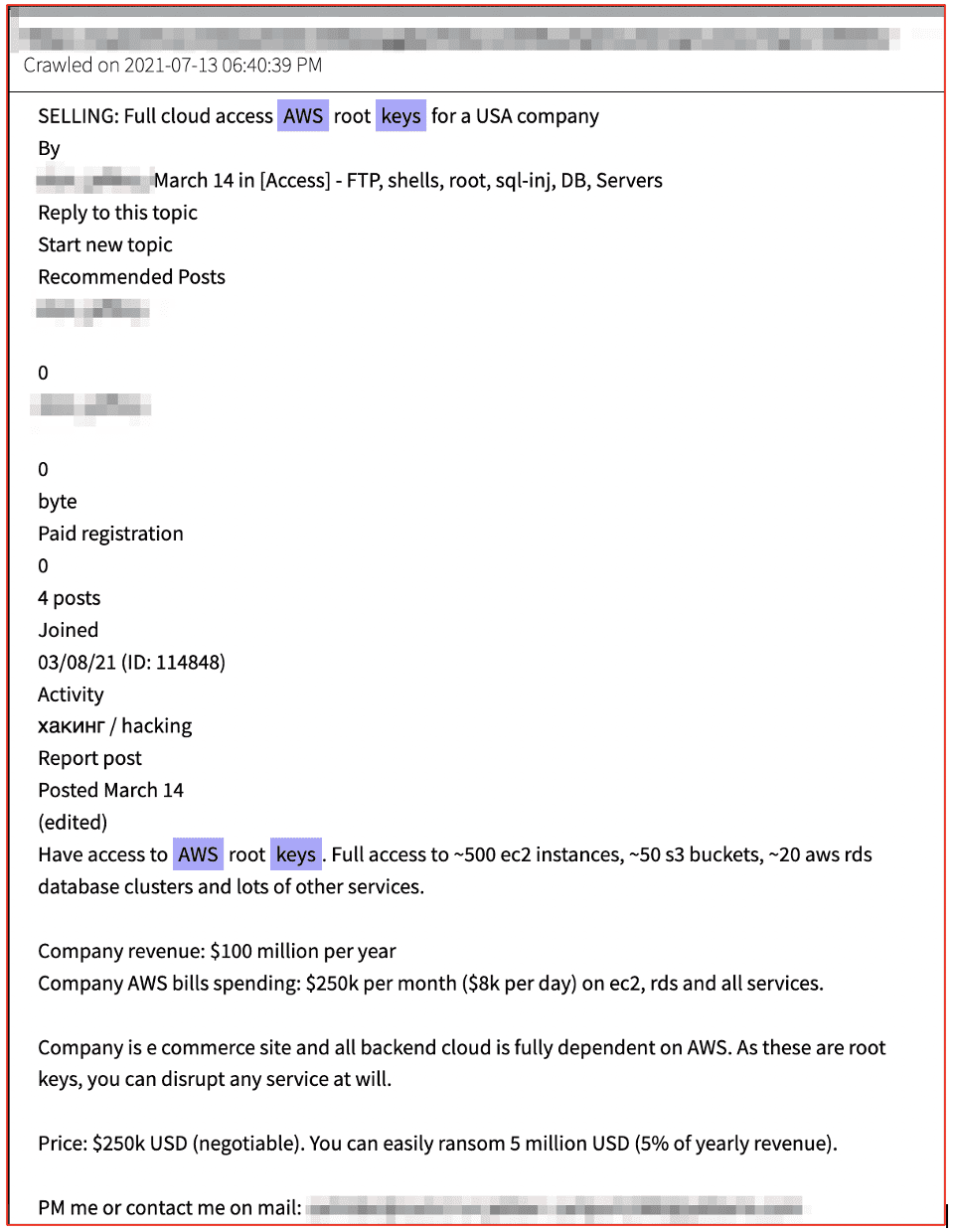
Figure 8: Source DarkOwl Vision
DarkOwl has observed API keys for sale on darknet discussion forums and adjacent Telegram live chat platforms. Both Raidforums and its newest reincarnation, Breached Forums have included such offers on their sites. The figure below is an example of Raidforums user on Telegram offering to sell a Coinbase Pro API key for malicious access. How the API key was obtained is unclear.

Figure 9: Source DarkOwl Vision
DarkOwl has observed threat actors offering sell access to “logs on darknet marketplaces, such as Russian and Genesis. Such logs are obtained via stealer malware variants and include session tokens and keys obtained from victim devices.
Databases of stealer logs that may include API tokens and sessions are also offered for sale and trade on deep web forums such as Breached Forums.
Curious about something you read? Interested in learning more? Contact us to find out how darknet data applies to your use case.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















