The Fraud Files: What is Fraud on the Darknet?
Due to the vast number of scams and scam-attempts that most of us encounter on a daily basis, today’s society has largely become desensitized to fraud as we understand it on the internet. However, very few understand how this criminal economy thrives extensively across the darknet where it takes on a variety of different formats that target individuals and corporations alike.
Darknet forums and marketplaces are replete with how-to guides, mentors, bank drops, and sensitive PII and credit card databases for sale. Straightforward as it may seem to understand the current fraud landscape – especially with these listings and discussions being so common – the reality is not so simple. Navigating this underground territory requires an understanding of terms and concepts that apply across the darknet landscape that not everyone might be familiar with.
As such, we’re beginning our “Fraud Files” with an introduction or educational primer on the types of fraud most prevalent and regularly discussed terms and topics across the deep web and darknet.
The Language of Fraud
Over the course of crawling and exploring fraud on the darknet and deep web, DarkOwl discovered a unique language across vendors and key fraud cybercriminals operating in this sphere. Darknet marketplace advertisements of counterfeit and digital goods include numerous types of data for sale. Fraudsters are in the business of monetizing anything they can get their hands on and DarkOwl has observed frequent mentions of CVVs, bins, dumps, fullz, and bank drops – commodities which present varying degrees of financial returns.
Card Verification Values (CVVs)
In the carding industry – one of the largest fraud segments of the darknet – the card verification values or CVVs are a precious commodity to fraudsters. The CVV appears on credit and debit cards and consists of a three-digit number on the back of Visa, Mastercard, and Discover card brands or a four-digit numeric sequence located often on the front of American Express credit card brands. These numbers are also sometimes referred to as card security codes (CSC). There is also a second generation of card verification values known as CVV2 generated by a secondary process that makes them slightly harder to guess. (Source)
Bank Identification Numbers (BINs)
BINs or Bank Identification Numbers (a.k.a. Issuer Identification Number (IINs)) are another critical commodity of the fraud industry, especially with criminals focused on carding. The first six numbers on credit and debit cards identify the bank issuing the card, the country of issuance, the card type, and category. The ISO Register of BINs/IINs for US banks is managed by the American Bankers Association and is not generally available to the public; yet an open-source database has been setup and available for limited personal search and mentioned frequently on the deep web. (Source)
Dumps/“Dumpz”
Dumps or “dumpz” are one of the most popular and readily traded commodities in the darknet and across the deep web, consisting of large pre-compiled lists of stolen financial data. Most often, dumps consist of credit card data of varying completeness such as: a) credit card dumps or CC dumps consisting of datasets of credit card numbers with expiration and bank information, b) CVV dumps consisting of a list of known credit card numbers with expiration and CVV and c) Pin dumps consisting of a list of known credit card numbers with expiration and personal pin identifiers known only to the cardholder and bank for additional security.
Dumps may also include whether or not the credit card is VBV, which is Visa’s “Verified By Visa” additional security measures for online purchases, often consisting of a security pass phrase or key answer to a personal security question only know to the cardholder and the financial institution. Non-VBV Visa credit cards are preferred in the fraud community.
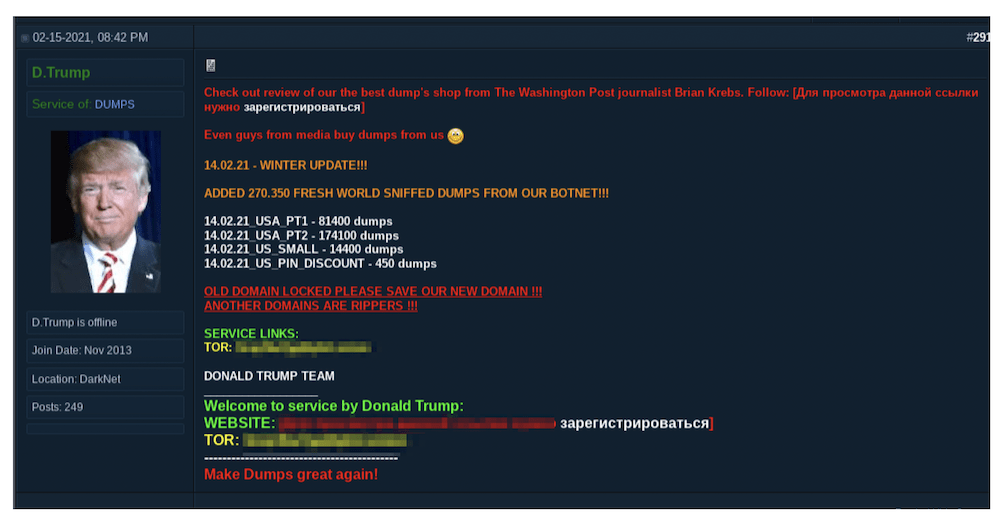
Popular darknet “dumps” provider, D. Trump advertising dumps for sale on a darknet forum
One popular “dumps” provider is known on the darknet as D. Trump, observed advertising their services across various deep web and darknet hidden services since Trump’s Presidential election back in 2016. Their forum posts insinuates that the compiled dumps data is “sniffed from their botnet” and their advertisements include a twist on Trump’s MAGA-theme with the catchphrase, “Make Dumps Great Again.”
Fullz
“Fullz” is a general term that indicates a comprehensive package of information to create a “full” picture of the subject matter. A highly coveted underground criminal commodity, fullz often consist of large, pre-compiled lists of stolen financial information along with critical personally identifiable information (PII), needed for account verification and criminal manipulation. The PII often includes the full name of the victim, billing address with zip code (for U.S. addresses), and phone numbers. Even more lucrative fullz also include personal pin codes. the victim’s mother’s maiden name for enhanced security. Sometimes fullz will include answers to security questions for accessing banks web customer portal or mobile app. Some fraudsters include deceased people in their fullz offerings as families rarely think to cancel the credit of dead relatives.
There are several darknet hidden services and deep web domains that specialize in trading “fullz”. One market known as “FullzBuy” with logo design using the yellow pricetag like Best Buy has fullz lists ready to purchase to include state driver’s license databases, social security numbers, and one listing stated it was stolen from a loan company, increasing the value and likelihood the data is recent.
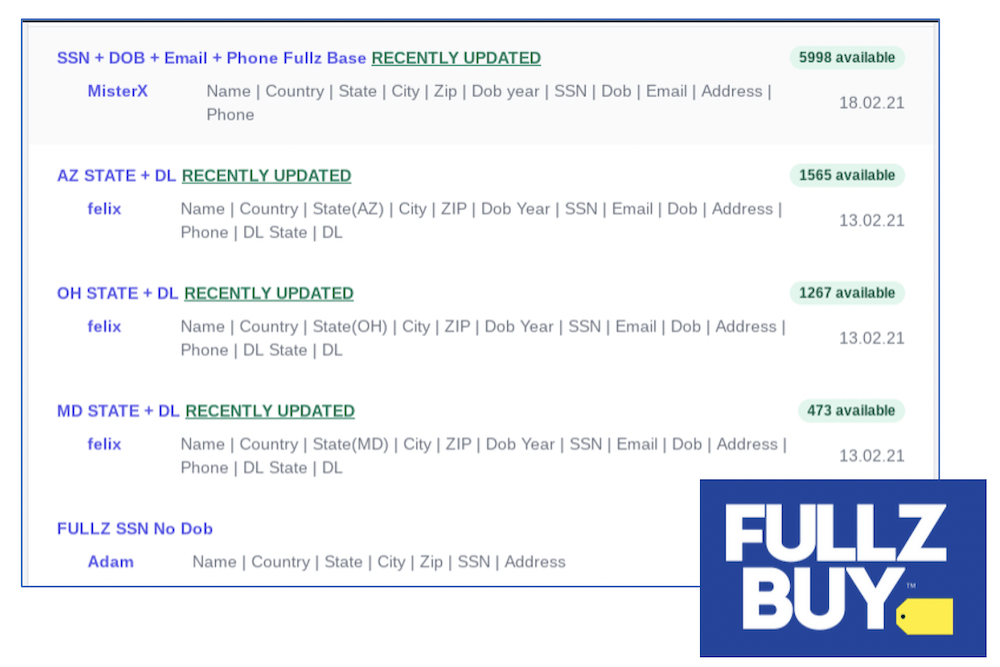
Example “fullz” captured directly from the deep web site, Fullz Buy.
Bank Drops
Bank Drops are another popular commodity on the darknet, especially for cyber criminals and fraudsters looking to turn their hacked bank credentials into cash. While some carding enthusiasts take dumps and fullz and turn them into fake credit cards to purchase goods or debit cash from an ATM, others exploit compromised account information through quiet bank transfers to bank drops via money mules.
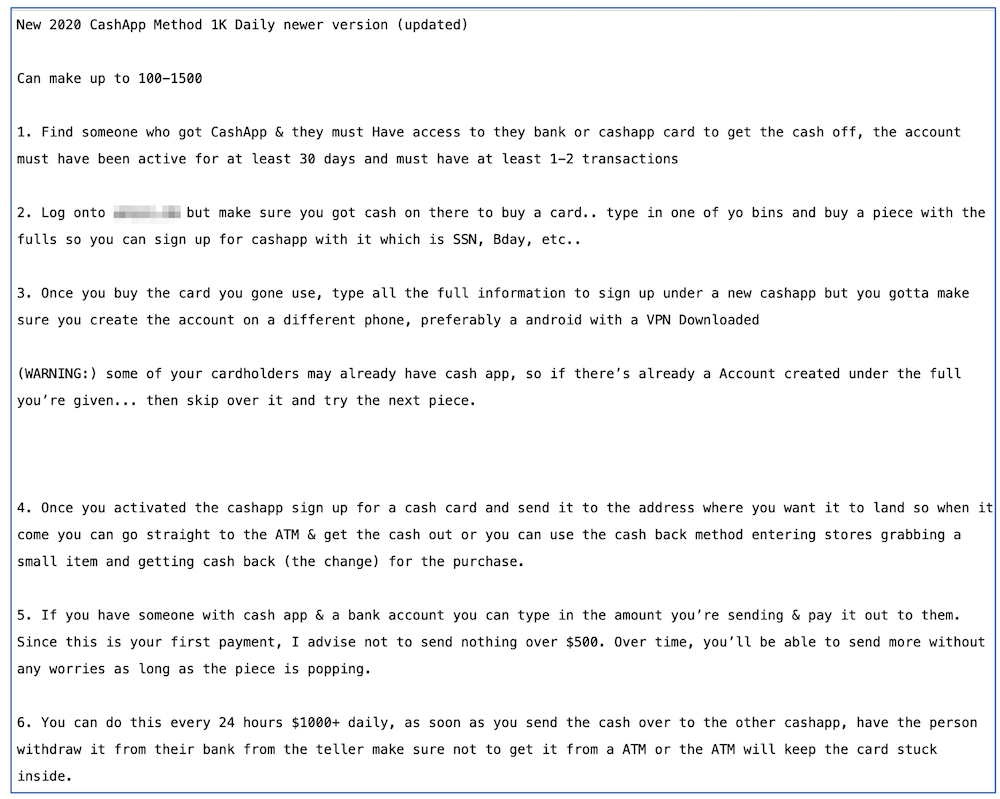
In the last year, fraudsters discovered how to successfully leverage a mule’s mobile money transfer app such as Venmo and Cashapp to transfer cash directly from the stolen fullz account, removing upwards of $1000 USD daily from the victim, often without their knowledge.
Money Mules
Money Mules or simply, “Mules” are individuals recruited by “mule herders” to help conceal the originating identity of the cybercriminal or fraudster and often key to turning the fraudulently acquired credit card and bank information into cash.
Many mules operate in lengthy fraud mule chains and networks and mules sometimes are completely unaware they are participating in a complex criminal enterprise. Many mules innocently respond to an innocuous “work from home” solicitation to help a so-called legitimate company send and receive funds from foreign customers, in exchange for a percentage of the transfer. In actuality, the company website and job posting is all fake, including the signed work contract, and their accounts are obscuring the identities of cyber financial criminals around the world.
Other mules knowingly assist in the fraud and set up a series of bank accounts, receiving funds from the fraud chain, cash out the transfers and send the monies along to the intended recipients using services such as Western Union.
The S’s of Fraud
Curiously, there have been an increase in fraud advertisements discussing techniques and malware delivery methods that coincidentally start with the letter ‘S’ – Notably: Swiping, Smishing, SIM Swapping and Skimming.
Swiping
Swiping is a term used by many of the younger-aged fraudsters which involves using stolen merchant account information or credit card data to make fraudulent purchases and having them delivered to an address, sometimes referred to as a “drop” (usually not associated with the criminal or the victim) where no one is home and the goods are then collected by the would-be swiping cybercriminal.
Swiping may also refer to the process of using stolen debit card information to collect cash out of an ATM. Variations of this process have been popularized across deep web enthusiasts in the hip hop culture spurring a completely new genre of “scam rap” where the technique is woven into the lyrics of rap songs. DarkOwl has observed this with young scam-rappers such as Teejayx6, as shown in the video below.
Smishing
Smishing is a form of phishing via SMS where cybercriminals hope the victim will click on malicious links in SMS text messages. There are numerous anonymous SMS spam services that will deliver these links readily for a small charge advertised across the darknet.
These smishing texts can take many forms such as a bank notification, mobile service cancellation scam, or fake delivery notice that leads the victim to providing personal information that will be traded on the darknet or install malware to spy and remotely control the victim’s mobile device.
SIM Swapping
SIM Swapping (a.k.a. SIM Splitting, port-out scam, or simjacking) occurs when a criminal takes over the mobile phone account of its victim often through directly social engineering the mobile carrier using publicly available PII of the victim compromised and leaked on the darknet. The phone number’s text messages and calls are then rerouted to a different sim and device controlled by the criminal in order to further breach the security of 2-factor authentication (2FA) security services that can lead to email, bank, and cryptocurrency account compromise and theft. In these times of uncertainty and rampant digital crime, authentication apps such as Authy, Lastpass, and even Google or Microsoft Authenticators are safer than relying solely on SMS 2FA for secondary security.
Signs Your Sim has been Swapped
This list originated from Norton Security.
-
You’re unable to place calls or texts. The first big sign that you could be a victim of SIM swapping is when your phone calls and text messages are not going through. This likely means fraudsters have deactivated your SIM and are using your phone number.
-
You’re notified of activity elsewhere. You will know you’re a victim if your phone provider notifies you that your SIM card or phone number has been activated on another device.
-
You’re unable to access accounts. If your login credentials no longer work for accounts like your bank and credit card accounts, you likely have been taken over. Contact your bank and other organizations immediately.
Skimming
Skimming is a type of credit card information theft that involves installation of a small device attached to a legitimate credit card transaction device, such as a credit card machine at a merchant, gasoline pump, or ATM. When the card is inserted or swiped for the legitimate transaction, the card data including the full number, expiration, and card holder’s name is harvested and rerouted to the malicious cybercriminal’s computer or networked server. The information is then used to make fraudulent transactions digitally or with a counterfeit credit card. A skimmer device installed on a gas pump or ATM is often noticeable as the hardware will protrude out past the payment key panel as the device must sit on top and affixed to the installed credit card reader. Many pumps in the U.S. now include a visible security label that will change colors or provide noticeable indication if it has been tampered with. Often fraudsters specializing in skimming turn the skimmed magnetic data into dumps for resale in the darknet. Skimming devices are also sold on darknet forums and marketplaces.
Fraud is Hardly Simple
Many of us associate the idea of fraud with the Nigerian Prince email scam tricking the most vulnerable population to send money via wire transfers to businesses and persons that do not really exist or have the needs that they have begged for help with.
While that is one form of limited wire fraud, the fraud industry has evolved into a complex darknet ecosystem with numerous categories and potential financial outlets to target including: personal identity fraud, bank fraud, carding and counterfeiting, merchant-level fraud, and government-program fraud.
According to a Federal Trade Commission’s report published in late 2020, imposter scams and online shopping fraud present the highest reported financial losses to businesses and individuals. The origins of their fraud data between darknet, deep web, and surface web) was not specified in this impact report.
Digital Theft – Stolen Identities
As we mentioned earlier, data is money and cyber-fraudsters are readily targeting individuals to increase their earnings by stealing from victim’s bank, credit and online-merchant accounts. This is achieved through hijacking or performing an “account takeover” of the victim’s bank or credit account and liquidating the funds via bank drops and money mules.
Other forms of personal identity fraud occur when key personally identifiable information of a victim, such as one’s U.S. social security number, home address, and mother’s maiden name is used to open new lines of credit or even worse, mortgages compromising the victim’s credit score in the process. This is why regular monitoring of one’s credit score, particularly to watch for any “known addresses” listed in the report that do not belong to the credit holder, is a strategic action to take in detecting identity fraud.
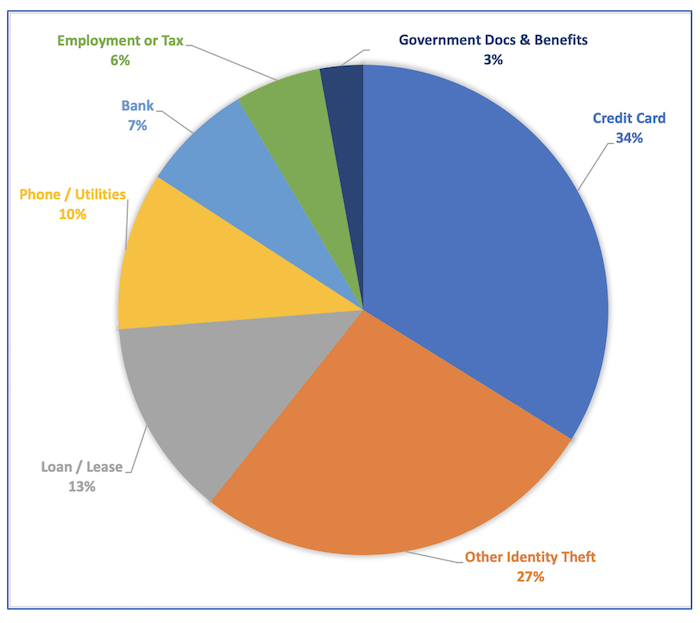
FTC’s assessment of identity fraud by categories for data through 2019. DarkOwl assesses fraud against government docs, benefits, and employment will increase since the pandemic.
The same 2020 FTC report states that credit card fraud is the most common type of identity theft in their dataset, occurring in over 30% of all identity theft reports. Bank, lease/loan, utilities, and government programs were also included in this list. DarkOwl assesses these financial distributions will shift with Government Programs and Employment Benefits compromising a larger percentage of fraud given the pandemic climate and rampant fraud methods available.
Carding – Unauthorized Purchases by Fraudsters
As we mentioned earlier, data is money and cyber-fraudsters are readily targeting individuals to increase their earnings by stealing from victim’s bank, credit and online-merchant accounts – account data that trades readily on the darknet as dumps, fullz, and CVVs. In the simplest of terms, carding involves the illegal use of a card by unauthorized persons to purchase a product and there are a couple of different paths a cyber-fraudster can take with this information they’ve purchased or found in the underground.
-
Some fraudsters might use the account information such as web login username or the account number to employ blackhat criminal hijacking of the victim’s account with the merchant online and making fraudulent purchases
-
Others take the stolen card numbers (dumps, fullz, bins) and make purchases illegally digitally and have the goods shipped to a drop address. Many of these purchases, especially if they are of low dollar value go completely unnoticed by the victim as few people actually review their purchases on their credit card statement each month.
-
Some more sophisticated criminals will take the data and create counterfeit credit cards for use in-person directly at a merchant. Often the fraudsters purchase large quantities of high-end electronics and expensive goods for resale or trade.
Many of the card list contain card numbers that have already been flagged as stolen or deactivated; for this reason, many darknet carding services often advertise their dumps or fullz are “fresh”, meaning the numbers have been acquired recently and less likely to be deactivated. There are several deep web sites solely setup for the purchase of card verification (alive or dead). There is also a special Skype number carding fraudsters call to verify the card is active via an automated service.
A Most Unusual Financial Opportunity
In late January, one creative carding criminal posted on a darknet criminal forum the offer to sell 180 GB of audio stolen from a merchant’s phone payment processing system collected over the last 6 years. At least 70% of the recorded calls supposedly include exploitable PII such as, first name, last name, registered address, phone number, e-mail, date of birth, card number, expiration date, and CVV.
The fraudster only asked for $2,400 USD in cryptocurrency for the entire dataset and subsequently lowered the price in the following weeks after receiving criticism for the “valids” and very little interest from the community.

[ENGLISH TRANSLATION] I will sell about 180 GiB (200k files) of conversation records merged from the server of the service for processing orders by phone (YUS). Calls made between 2015 and 2021, mp3 format, distributed in folders with the date of the call. Also, almost every folder has a txt or csv with a list of caller names. The caller's phone number is used as the file name. Calls in English and not much in Spanish(no more than 5%). Not all calls contain complete information on the holder and CC, but about 70% of the call records contain information such as, first name, last name, address, phone number, mail, date of birth, card number, expiration date, cvv. Of course, there are a lot of overdue CC's in the calls made in 2015-2019. Also, the total valid for CC is 10-15%, at least I did it so I rewrote a couple of hundred calls in text form to check the valid. Walid did not meet my expectations, and this is the reason for the sale. I want $2,400 for everything. I accept BTC, ETH, and XMR. If you need sample files, I will ask you to put money in the guarantor or deposit, as I am happy to conduct transactions through the guarantor.I am ready to answer any questions in the PMMerchants and banks have had to increase their insurance to account for the increasing criminal activity around carding. When a victim does discover their information has been compromised and illegal purchases made, they often report the unauthorized purchase to the credit card company – who will often freeze the account and issue a new card – prior to cancelling the illegal transaction from the credit statement as a part of the financial institution’s zero liability guarantee, established with the Fair Credit Billing Act in the U.S. Sometimes it’s helpful to also contact the merchant and notify them that a claim has been submitted with the credit company.
Taking Money Directly From “Big Brother”
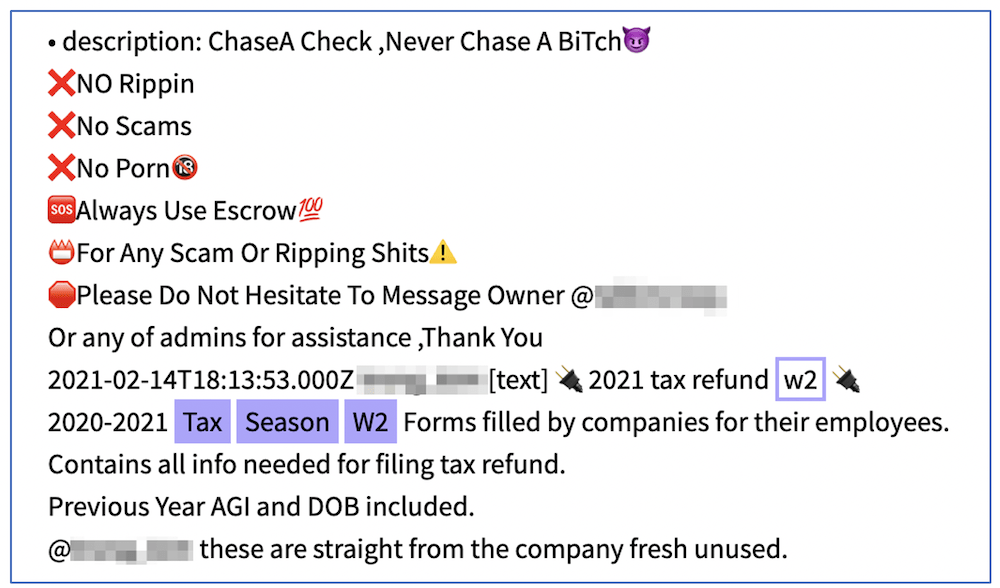
W2 Tax Forms for Sale to Commit Tax Fraud (Source: DarkOwl Vision)
Since the COVID-19 pandemic hit the U.S. and suddenly millions of citizens were out of work, DarkOwl analysts have observed an increase in government-specific fraud against government subsidized programs such as State Unemployment, Pandemic Unemployment Assistance, the Small Business Association, and even personal Stimulus Payments from the Internal Revenue Service (IRS). Many cyberfraudsters view themselves as cyber vigilantes and are personally more willing to scam the government out of funds instead of their neighbor next door. In December, USA Today reported there had been an estimated $36 Billion USD stolen across U.S. unemployment benefits.
The upcoming tax-season is another market for opportunistic fraudsters who have obtained sensitive PII from the darknet. Some fraudsters with access to SSNs and fullz data, will file taxes ahead of the victim and steal the refund payment from the government. This complicates the victim’s standing with the IRS considerably as they attempt to recover their refund and their account with the IRS.
One popular darknet vendor using the pseudonym, “@OsamaFBG” has been selling a COVID-19 stimulus check template and method for as little as $50 USD over the last year, since the IRS first started distributing checks to U.S. Citizens. Source: 62f077c9fbf3185ab831ac578f46d117. Another offered a method guaranteed to fraud upwards of $100,000 USD “easily” from the SBA’s relief grant program for as little as $300 USD.
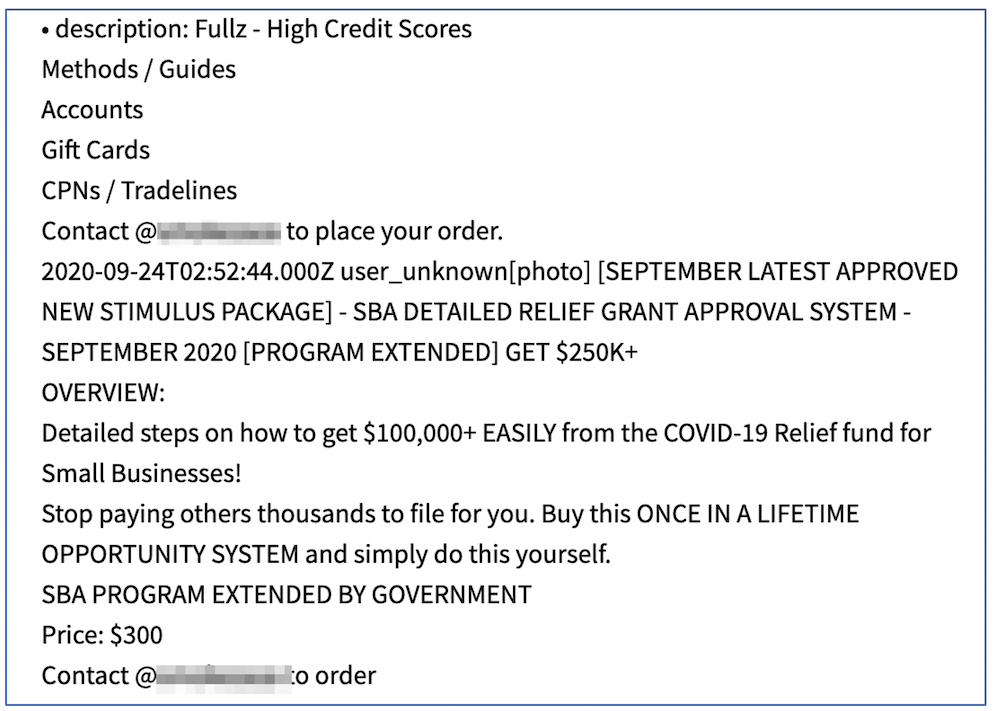
Offer for a method to Fraud the Small Business Administration’s COVID Relief Grants Vision (Source: DarkOwl Vision)
Conclusions
The fraud industry is a vibrant and thriving ecosystem across the darknet and deep web. Financial cyber criminals will continue to exploit vulnerabilities across all financial systems and continue to trade and sell victim’s personal data and accounts for continued financial gain. Scams and carding fraud are key segments of this market while government benefits and unemployment system fraud have skyrocketed in the pandemic.
Curious to learn more? Check out our “Fraud on the Darknet” webinar to see live fraud-related searches using our darknet analyst dashboard.