The Hidden Economy of Credentials on the Darknet
March 28, 2023
Earlier this month, DarkOwl contributed to the State of Secrets Sprawl 2023 report by GitGuardian. In this blog, we highlight our contributions. Check out the full report here.
When it comes to secrecy, there is one place that cannot be ignored: the darknet.
Darknet 101
The darknet, also referred to as the dark web, is a layer of the internet designed specifically for anonymity. It is more difficult to access than the surface web and is accessible only via using specialized software or network proxies – specifically browsers supporting special protocols. Users cannot access the darknet by simply typing a dark web address into a web browser. Adjacent to the darknet are other networks, such as instant messaging platforms like Telegram and the deep web (non-public web).
Due to its inherently anonymous and privacy-centric nature, it facilitates a complex ecosystem of cybercrime and illicit goods and services trade. The dark web is a thriving ecosystem within the global internet infrastructure that many organizations struggle to incorporate into security posture. Still, it is an increasingly vital component for organizations with forward-thinking strategies.
“Secret” data, including tokens and keys found on open repositories such as GitHub, are easily re-sold (or sometimes shared for free) on the darknet and deep web.
How Does It Work?
In some cases, such as that of the deep web site BreachForums, leaked data is offered for download via vendor-specific currency in the form of generally inexpensive credits. Another way to accrue credits is to share other breached data for users to download. Users can also gain credits to purchase these stolen data packets by commenting on and engaging with other user posts. Both of these aspects of the darknet breach economy encourage discovering and re-sharing of sensitive user data and creativity in exploiting previously-exposed information.
Consequently, an extensive amount of sensitive information is available for download on the darknet and deep web, ranging in prices from free to several thousands of dollars. While such free exchanges may challenge the use of the word “economy’” – it is crucial to remember how this stolen information is used. The vast majority of cases result in hackers gaining illicit access to user accounts and either exploiting them for financial gain or using them to pivot into corporate network access to carry out more large-scale attacks.
Examples
Verizon
The below screenshots demonstrate a typical database leak offering. Note: the top of the second image breaks down the extent of the data available per Verizon user. This breached information has been offered entirely free (no digital currency or credits are required to download).

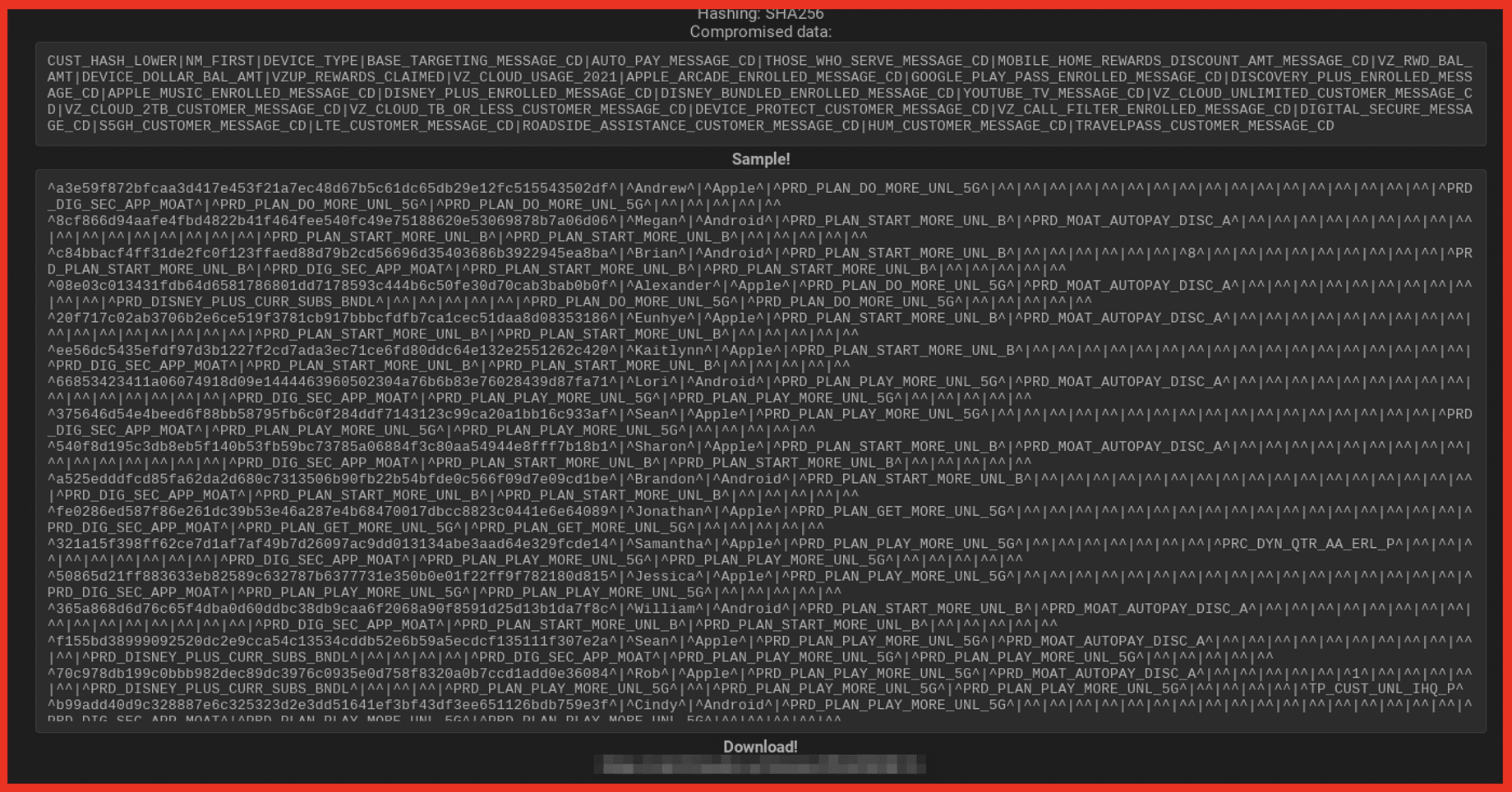
Another way to accrue credits is to share other breached data for users to download. Users can also gain credits to purchase these stolen data packets by commenting on and engaging with other user posts. Both of these aspects of the darknet breach economy encourage discovering and re-sharing of sensitive user data and creativity of exploiting previously-exposed information.
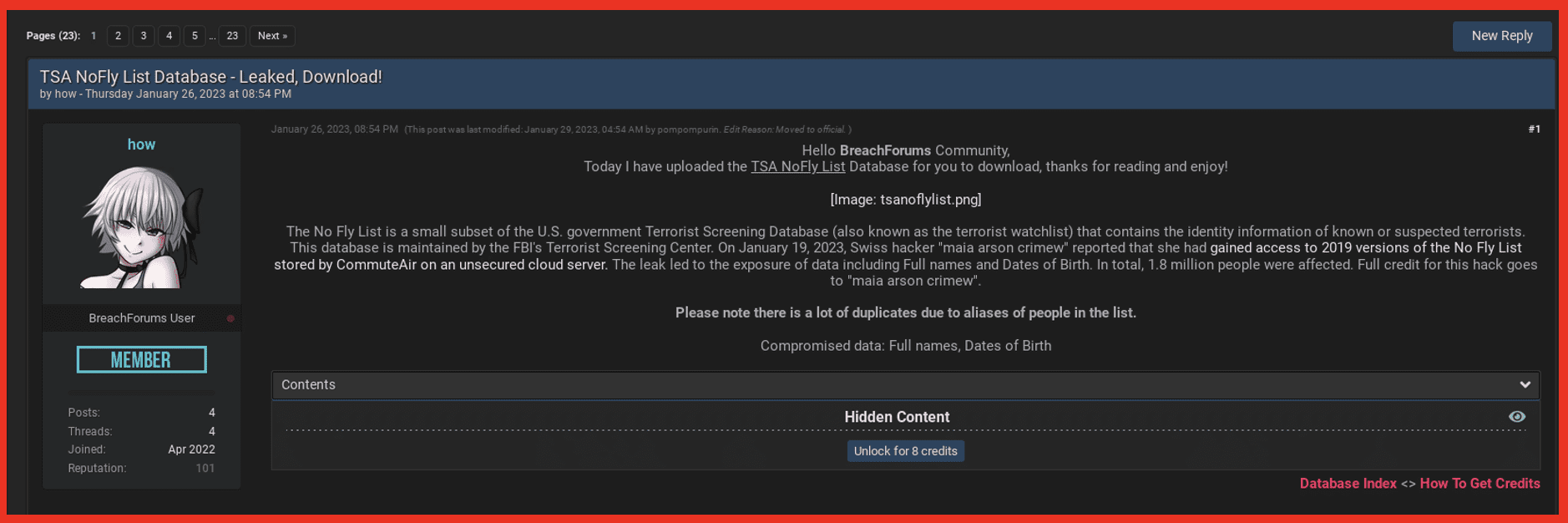
TSA No-Fly List
The recently hacked US TSA No-Fly list is offered for credit tokens on a deep web forum.
DoorDash User Account
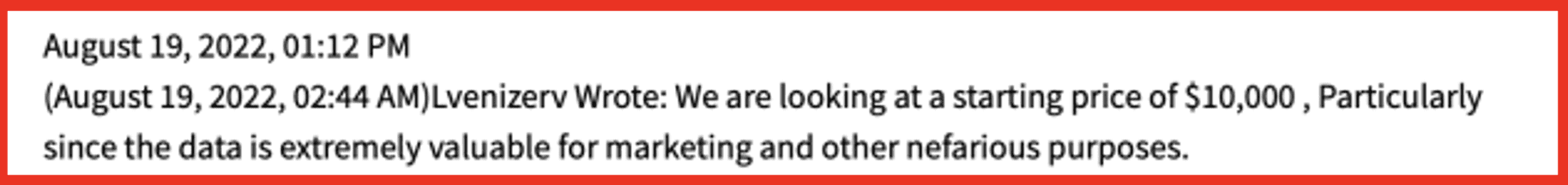
While the token or credit-based nature of the darknet economy does support “free” or more covert methods of exchanging Secret data (such as credits), this is not always the case. For example, as demonstrated by this DoorDash database of username and password combos for over 650,000 individuals was offered at a starting bid of 10,000 USD in August 2022.
Are Hackers Exchanging Secrets on the Darknet?
The shift towards everything-as-an-API in the commercial landscape echoes what DarkOwl analysts see in the darknet.
Discussions around stealing API keys and selling them is a relatively new phenomenon in the darknet over the last couple of years that we expect to continue to grow. Threat actors who are looking to facilitate the wider distribution of malware through supply chain compromises have also discussed credentials and pivot points sourced from open repositories.
Developers and security researchers worldwide have been equally appalled and conflicted by the intentional sabotage of an open-source software package. Many are particularly concerned about the reputational damage these incidences cause to the open-source software development movement.
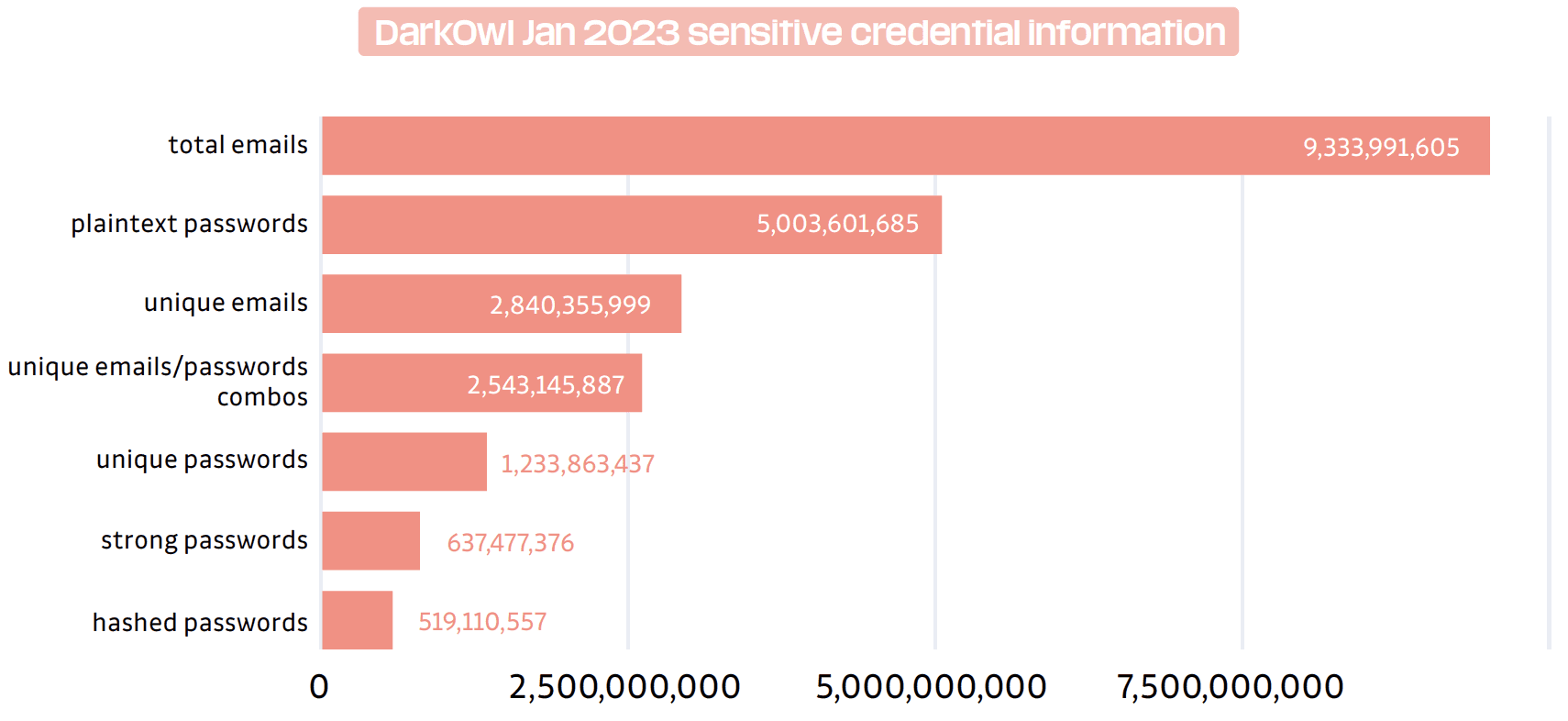
How Many Credentials are for Sale on the Darknet?
While it is impossible to grasp the total size of the underground digital economy, DarkOwl does have insight into certain entities that indicate the potential for exploitation, including sensitive credential information. DarkOwl’s AI and analyst-augmented database is updated in near real-time and collects from hard-to-aces reaches of the darknet, including authenticated forums, ransomware sites, chat platforms, open server databases, and breach/leak exchanges. As of January 2023, our records detected:
Interested what and how darknet data applies to your business? Contact us.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















