Ransomware Resurgence and Emergence: Continued Analysis of RaaS Activity Since the Invasion of Ukraine
May 04, 2022
Ransomware on the Darknet Continues
In the days immediately following the invasion of Ukraine, the ransomware-as-a-service (RaaS) industry on the darknet experienced several high-profile interruptions with many popular RaaS affiliate programs impacted by their partners having to choose between their nationalistic alliances with Russia or Ukraine. Many wondered what impact this would have on the thriving ransomware ecosystem.
A security researcher leaked critical operational data, personally identifying information for threat actors, and sensitive private chats between members of the CONTI RaaS group. The data leak revealed the human side of some of the most prominent RaaS organizations with mentions of personal “visits to the dentist” and recommended songs to listen to on YouTube to pass the time while working on their exploit and attack campaigns.
From an operations perspective, we also learned the critical roles Bazarloader Botnet, Cobalt Strike, and Trickbot played in the long-term success of CONTI’s empire.
Shortly after the leaks emerged, CONTI’s leak site slowed in announcing victims from 10 through 16 March. However, during that same time STORMOUS announced they had compromised Ukraine’s Ministry of Foreign Affairs. Around the same time, Ukraine’s Vodafone network suffered a major cyberattack and was knocked offline.
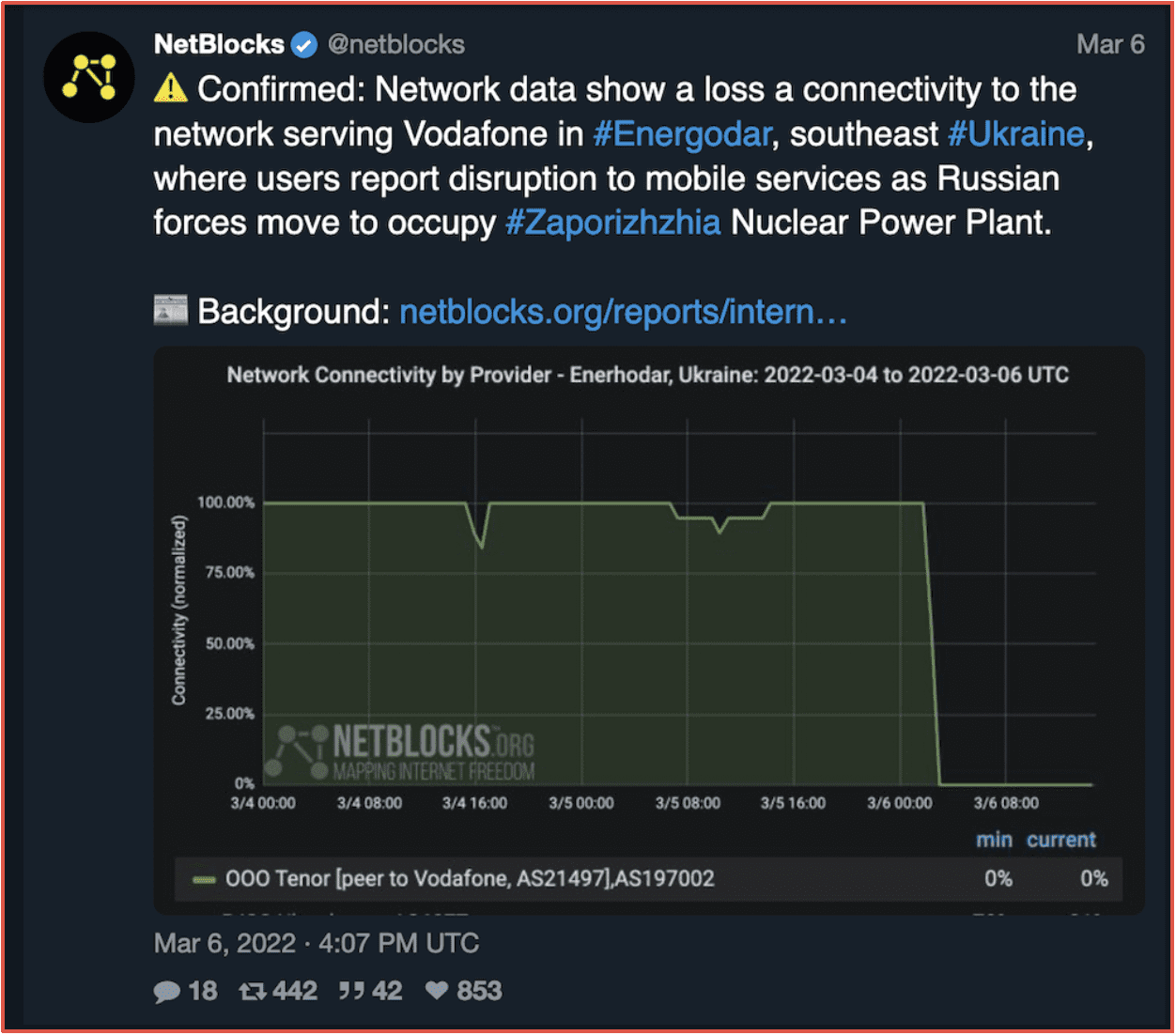
Figure 1: Netblocks Status of Vodafone, 6 March 2022
The interruption in victim announcements was more like a slow-down and did not last long with a quick ramp up from the major RaaS industry players: CONTI, Lockbit 2, and CL0P announcing dozens of victims during the month of April.
LockBit2 – a gang that “claimed” neutrality in the Russian-Ukraine war – has the highest number of total victims since the 24th of February at 280. That’s an average of 4.5 victims per day by a single group.
DarkOwl is currently tracking 25 active ransomware groups. Across those groups, the total number of victims – just since 24 February – totals 813, presenting an even more worrisome average of 11.8 victims per day.
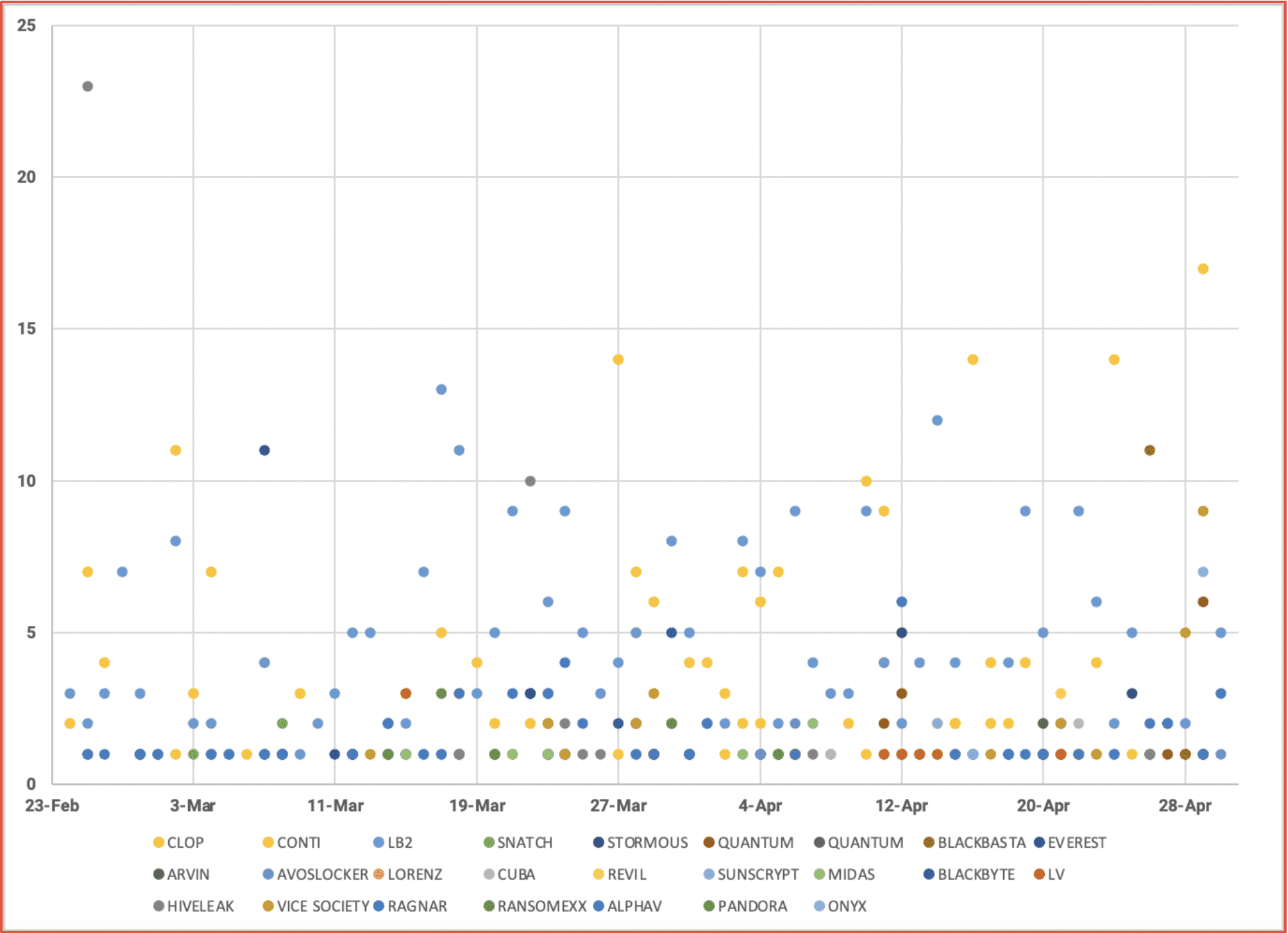
Figure 2: Scatter plot distribution of daily ransomware victims per RaaS gang
Critical Infrastructure Targeted
Unsurprisingly, victims include several US and NATO-based critical infrastructure organizations and suppliers including local government municipalities, electrical and alternative power providers, water, telecommunications, and transportation suppliers.
DarkOwl also observed an increase in manufacturing and construction-related companies with downstream victims including international lumber and steel processing companies mentioned quite frequently.
CONTI announced last week they successfully encrypted US-based MACK Defense, LLC a major parts supplier and sales organization attached to the MACK trucking company. This will likely cause further interruptions to an already encumbered and fatigued US ground-based supply chain.
Meanwhile, Snatch leaked over a gigabyte of data from a popular European travel website, TUI Group.
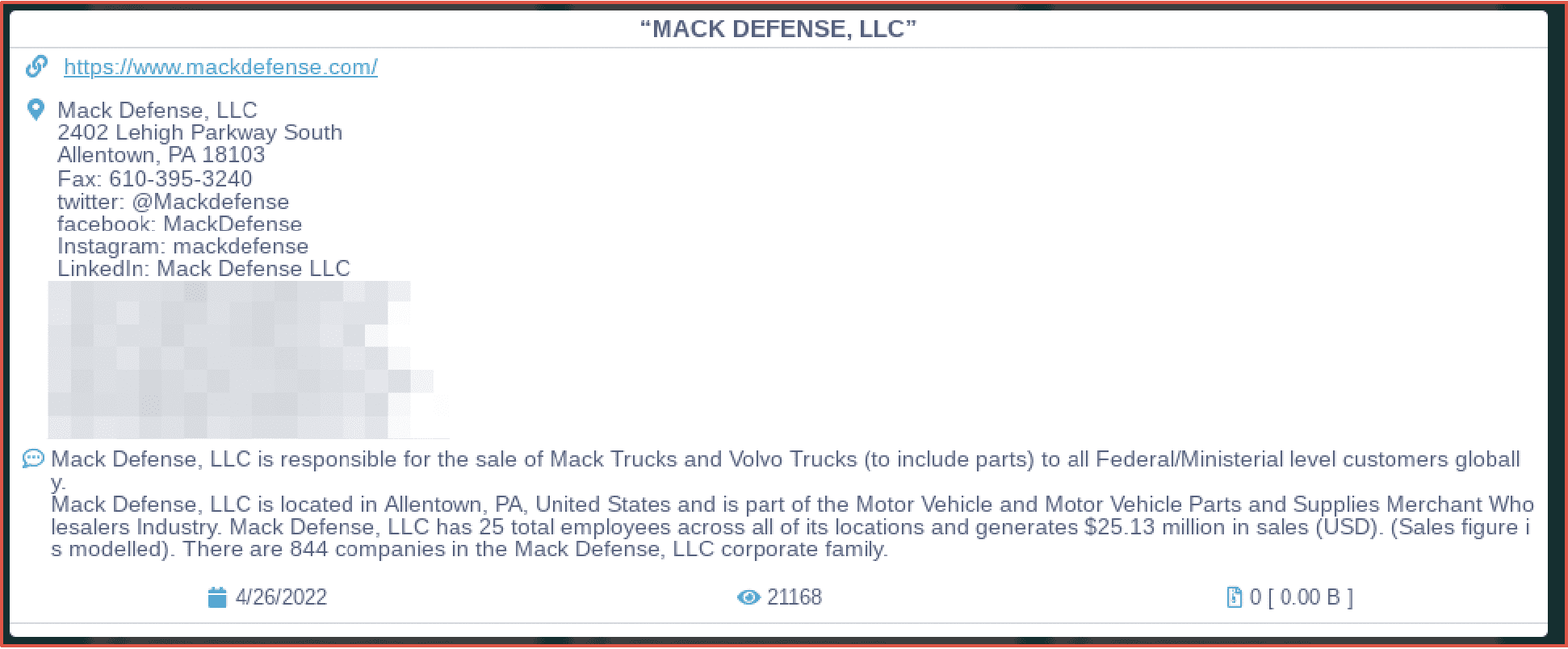
Figure 3: CONTI Announcement of Ransoming MACK Defense, LLC
Ransomware groups have announced at least half a dozen victims across electrical, water, or natural gas-affiliated suppliers the US, Canada, and Europe in the last 10 days.
In March, German wind-turbine supplier Nordex suffered a severe cyber incident carried out by CONTI shutting down over 5,000 wind turbines across the country. On April 23rd, CONTI leaked 145GB of exfiltrated data related to the company, archived across 82 compressed data files. The Nordex cybersecurity incident was likely a critical infrastructure retaliation attack for Germany’s support of Ukraine.
HiveLeak and AlphaV’s activity also increased significantly with nearly 100 victims between the two RaaS gangs alone. Vice Society also leaked 20 victims in the last 10 days of April after previously having a relatively slow ransomware

Figure 4: Statement from Snatch Ransomware
The Resurrection of REvil
REvil’s “Happy Blog” suddenly appeared online and operational on April 20th on the Tor network, redirecting to a new URL which announced 5 victims. The last victim posted by the REvil group was in mid-October 2021 shortly before experiencing 404 errors and rumors emerged suggesting the FBI had seized the admin panel had deleted the Tor service using UNKN or another admin’s keys.
According to the BBC, members of the REvil RaaS operation were reportedly taken into custody by the Russian FSB after an international law enforcement operation last December.
The redirected URL includes a link to “Join Us” with a request for affiliates to contact them using a Tox address provided. The advertisement continues their historical 80/20 ransom split and states they have a “Тот же проверенный (но улучшенный) софт” [TRANSLATED] “The same proven (but improved) software.”
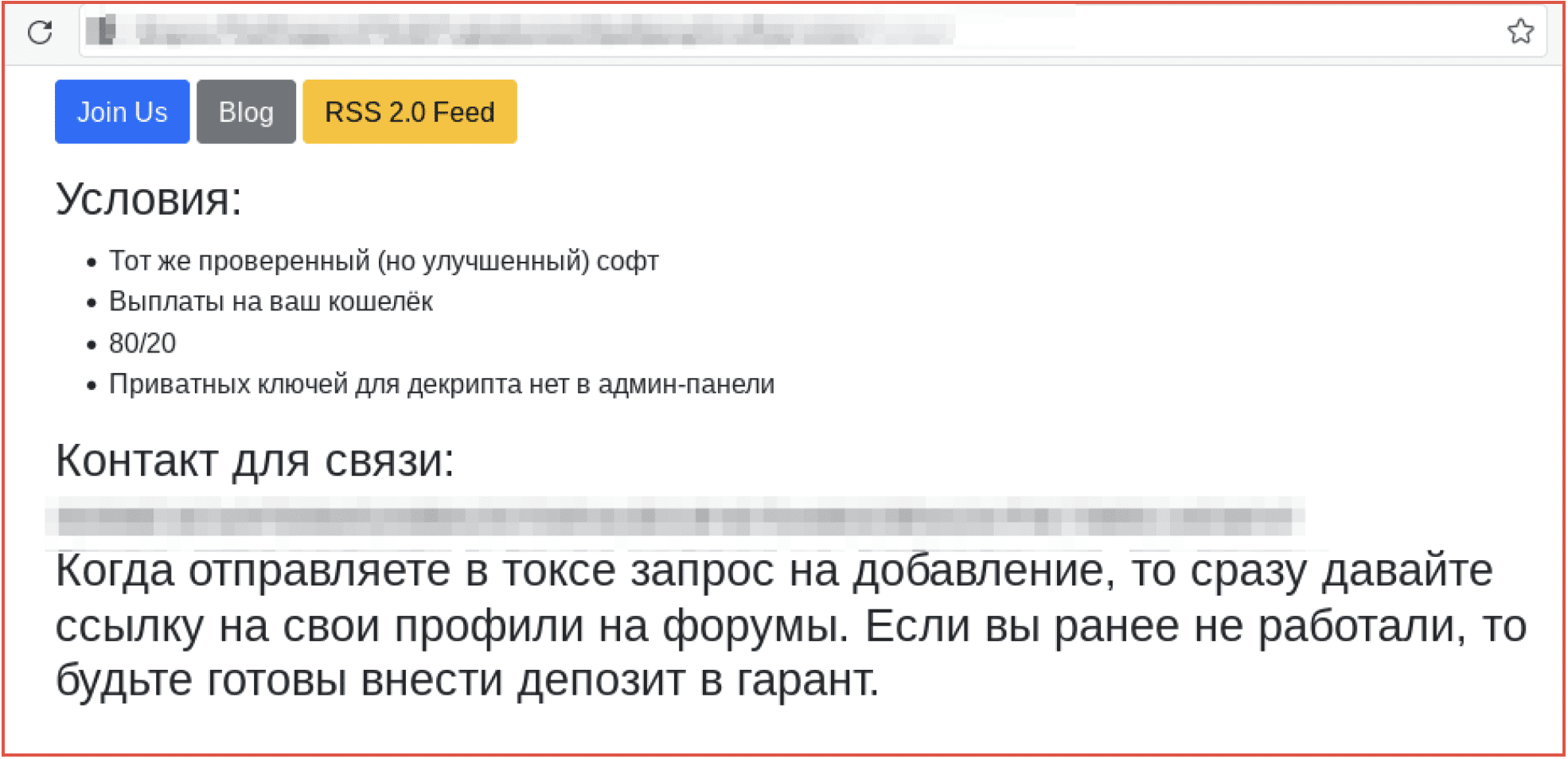
Figure 5: REvil’s Latest Call for Affiliate Partners
The new REvil Tor service boasts an odd-mix of victims, including an oil and gas company in India, asphalt production company and a corporate signage company. By the end of the month, the service was offline and inaccessible. The intentions of revitalizing the REvil Tor service is unclear, but the timing was near coincident with the US closing diplomatic channels with Russia on cybersecurity.
The resurrection of REvil could indicate that President Putin has released arrested ransomware operators to carry out retaliatory attacks against critical targets in the US and Europe.
New Ransomware Groups and Patterns Emerge
A new RaaS group called Blackbasta appeared online and announced 11 new victims on the 26th of April. Blackbasta uses the ChaCha20 and RSA-4096 cipher, an upgrade from groups like Maze and Sekhmet that utilized ChaCha20 and RSA-2048 ciphers. They also call their Tor victim’s page, “Basta News” playing off the CONTI marketing strategy.
Figure 6: Blackbasta Tor Service “Basta News” 30 April, 2022
Another new group, Onyx ransomware started leaking their victim data on a Tor service titled, “Onyx News” with 7 new victims added at the end of April. The victims appear to be primarily small businesses and organizations, including a local US police office and a couple of family medical practices.
The x001xs ransomware group appears to have pivoted to a different underground industry with no victims announced since late January. Their Tor service also now redirects to a darknet credit card provider called “BitCarder.”
RaaS group activity across the whole industry has steadily increased over the last 10 days. When visualizing the various groups’ victim announcements as a function of post-date, they demonstrate quite noticeable “peaks and valleys” that suggest less publishing collectively occurs on weekends.
The outlier for this trend is CL0P who drops several groupings of victim announcements only around the weekends. The CL0P group was much less active in March with announcements only at the beginning and end of the month.
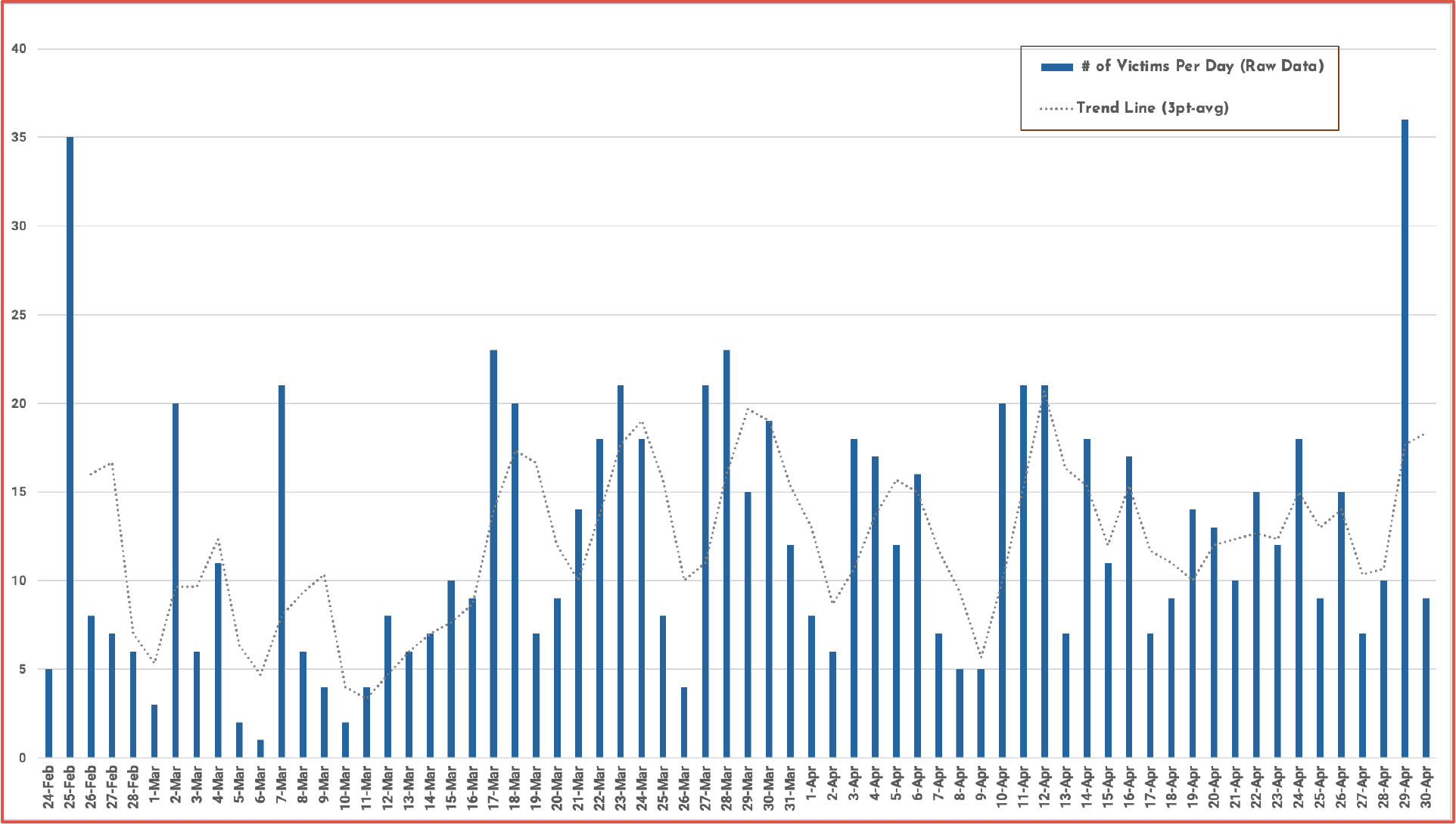
Figure 7: Daily Distribution of Total Victims Per Day Across All Groups, with 3pt Moving Average Filter
Ransoming Russia
Since the end of March, an Anonymous-linked, pro-Ukrainian cyber threat cell known as Network Battalion ’65 (or simply nb65) has carried out cyberattacks against Russian entities using ransomware. The group allege they are deploying a variation of the leaked CONTI ransomware source code, which surfaced shortly after the invasion. We have identified and downloaded at least half a dozen data leaks provided by the nb65 group that accompanied the group’s announcement of the CONTI code use.
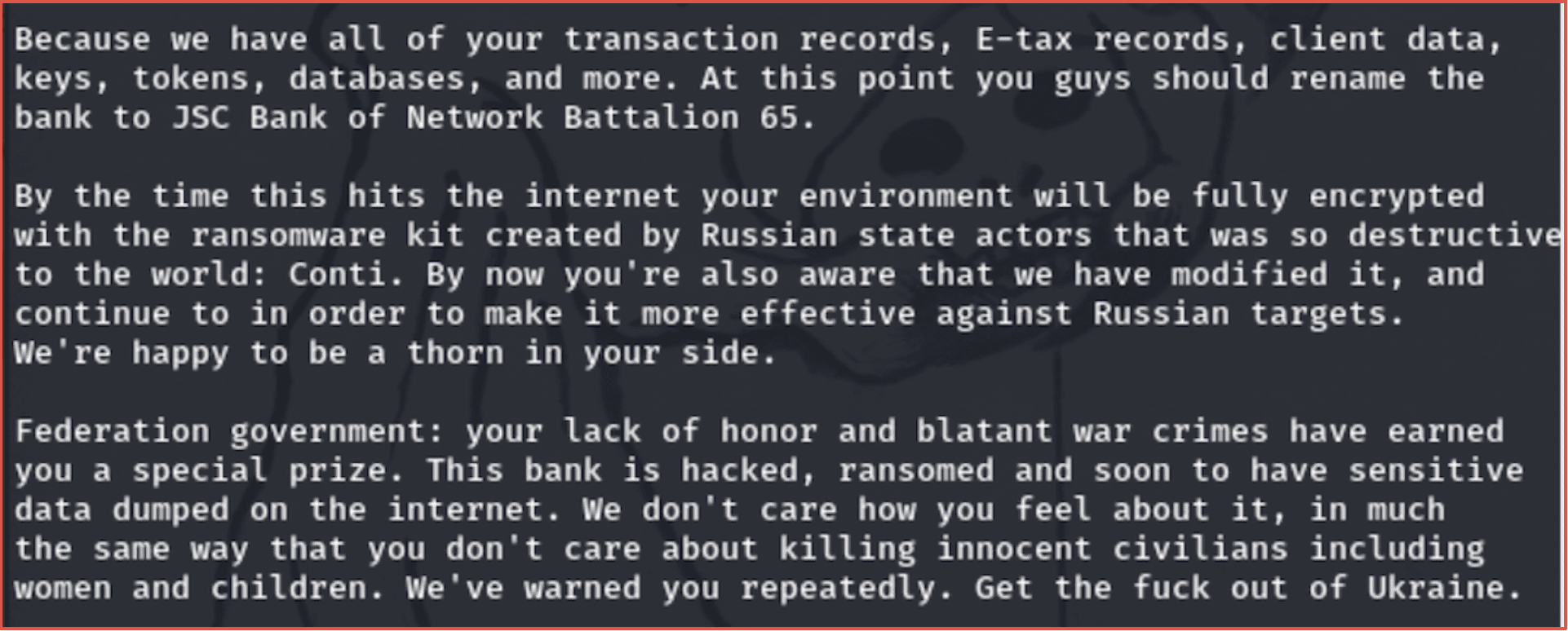
Figure 8: nb65 Announces Use of CONTI ransomware Against JSC Bank of Russia
Hackers Hacking Hackers
On 20 March, Arvin Club published a data leak associated with the pro-Russian aligned STORMOUS ransomware gang. Arvin claimed the group poorly configured their ‘new’ Tor service after mirroring their Telegram content to the anonymous network. It was unclear whether this was motivated by malice or geopolitical alliances.
In early March, STORMOUS posted an official statement to their Telegram channel stating they did not intend to attack Ukraine but could not sit back and watch attacks against the country [Russia] that “means so much to us.” They also included CONTI’s logo and the handshake emoji with their respective hashtags, symbolizing some level of partnership.
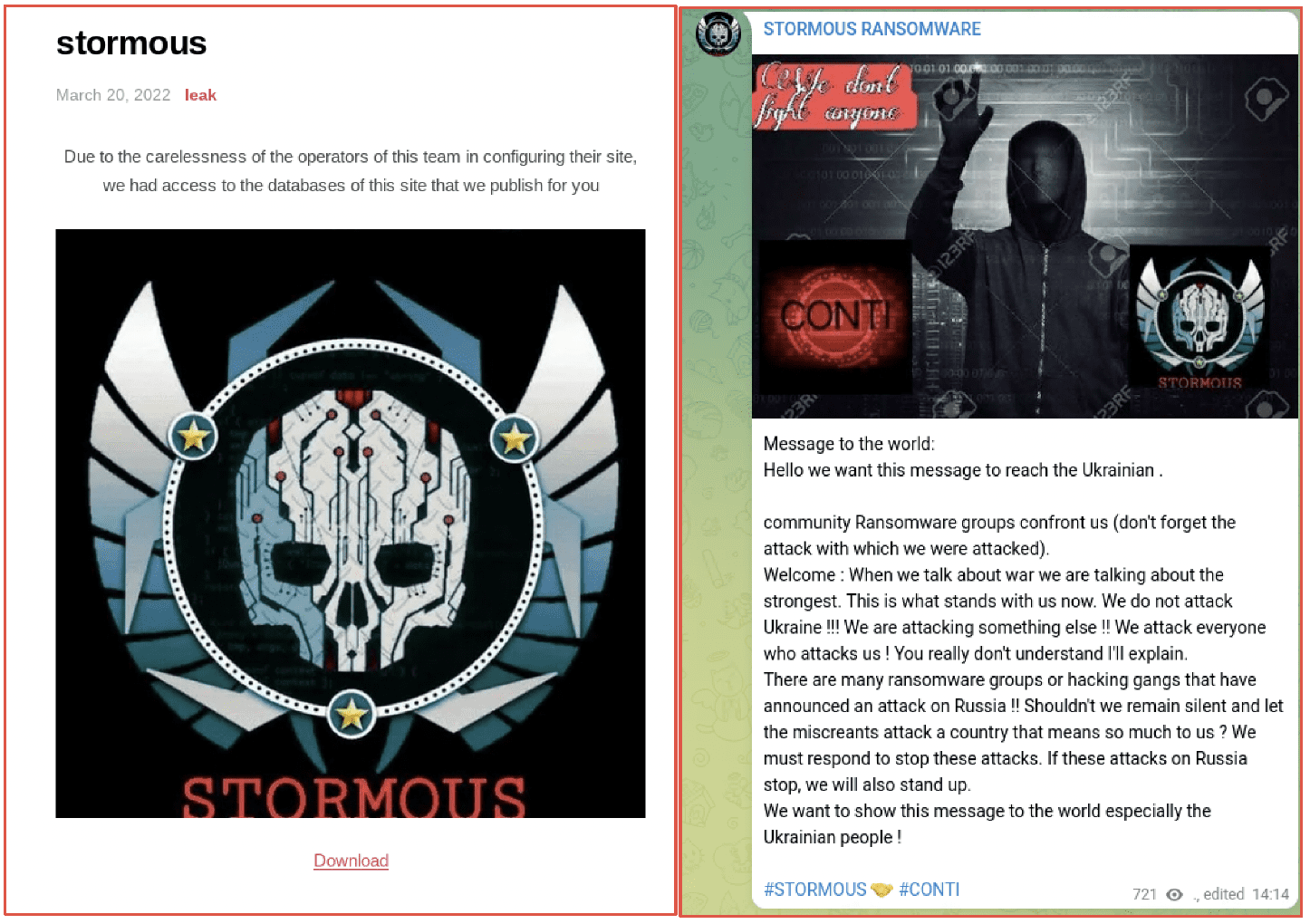
Figure 9: Arvin Club Leak of STORMOUS Info on Tor | STORMOUS World Announcement
In the last month, Russian ransomware groups and threat actors are actively targeting pro-Ukrainian cybersecurity researchers and Anonymous-linked cyber cells. Many researchers have been doxed and threatened across social media and Telegram in vendetta-like attacks.
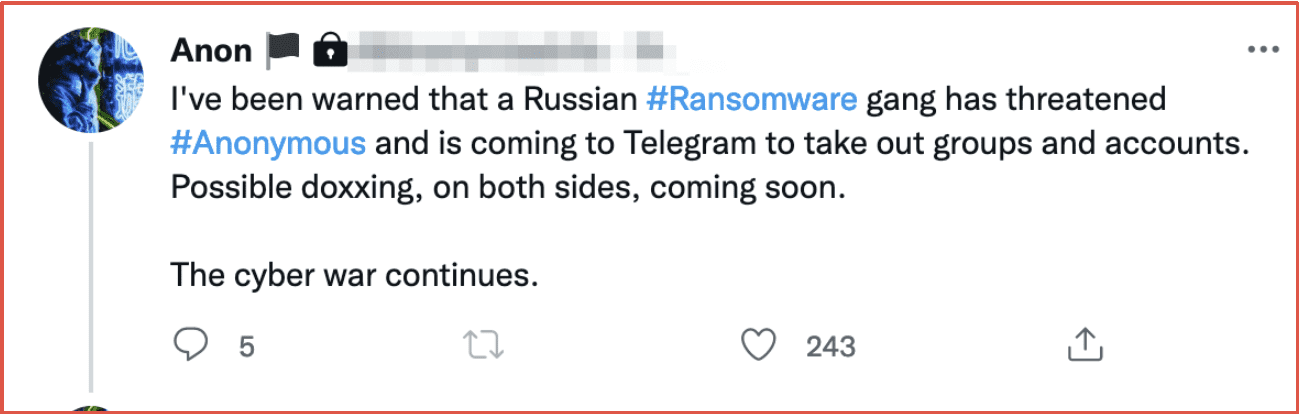
Figure 10: Twitter Post Warning Anons that Russian Ransomware Gangs are Targeting the Anonymous Collective
Curious about something you read? Interested in learning more? Contact us to find out how darknet data applies to your use case.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















