Threat Actor Spotlight: Scattered Lapsus$ Hunters
January 20, 2026
The Start
Scattered Lapsus$ Hunters, is reported to be a hybrid threat actor group forged from three separate groups, who collectively emerged onto the scene in 2025 and quickly made their mark on the cybersecurity world. Announcing their existence following ShinyHunters alleged social engineering campaign that purportedly resulted in the theft of 1.5 billion Salesforce records, the group consists of threat actors from ShinyHunters, Scattered Spider, and Lapsus$ extortion members.
The three factions were all heavily active in 2024, resulting in a series of arrests of members of the group Scattered Spider in 2024. The group remerged in April 2025 with an attack on UK retailers Marks and Spencer. Due to the significant attacks carried out by the individual groups in recent years, the convergence of their members has introduced even greater chaos into an already volatile landscape.
Salesforce October Deadline
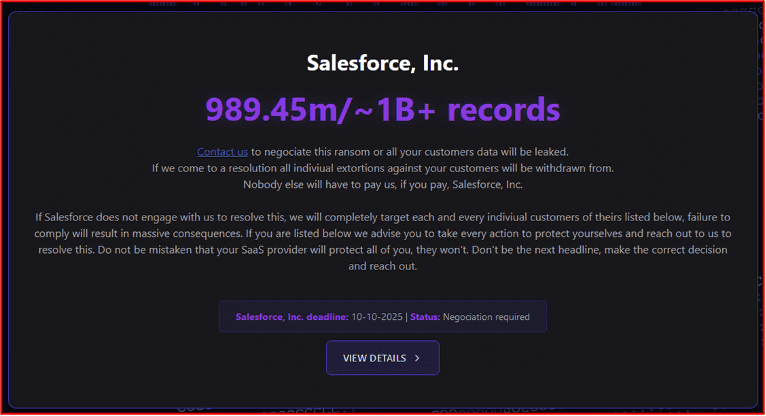
On October 03, 2025,Scattered Lapsus$ Hunters launched a data leak site extorting 39 companies that were impacted by the Salesforce breaches. The companies extorted in the link include Disney/Hulu, FedEx, Google, McDonald’s and more. A separate entry on the site requested that Salesforce pay a ransom to prevent impacted customers (approximately 1 billion records containing personal information) from being released. The group set an October 10 deadline for Salesforce to pay the ransom, or for potentially affected companies to contact the group to secure their data. Salesforce refused to negotiate with the threat actors, believing their threats were unsubstantiated and offered support to any of their affected clients.
While the group had threatened to release all information if their demands were not met, eventually they only leaked data from six companies. The victims included Albertsons, Engie Resources, Fujifilm, Gap, Qantas, and Vietnam Airlines. Qantas and Vietnam Airlines each had more than five million customer records exposed. The group later announced on its Telegram channel that it would not release any additional information until 2026, stating that it was unable to leak further data, though no specific reason was provided. The limited amount of victim information leaked during the October extortion attack led some individuals to question the extent of the data the group possesses. This behavior appears to indicate the group believes it can still extract a substantial payment from Salesforce or the affected individuals.
Following the partial leak, Scattered Lapsus$ Hunters posted a Telegram announcement threatening the remaining victims and Salesforce. The statement urged Salesforce to “put down your pride/ego” or their next campaign will be more “destructive” and they have the time and resources to ensure this fate. They warn against policies that mirror Australia’s “Cyber Security Act of 2024” which introduced mandatory reporting of ransomware and cyber extortion payments, as well as strongly discouraging complying with threat actors demanding ransom. The group identified themselves as businesspeople and rejected the label of terrorists or attackers.
The post was signed “We will never stop, see you all in 2026” indicating the group will return with further activity in the new year.

Forecast
In November 2025, the group announced the development of a Ransomware-as-a-Service (RaaS) platform named, ShinySp1d3r. On a Telegram channel used by the group, they claimed the ransomware was in development and will be led by ShinyHunters but operated under the “Scattered Lapsus$ Hunters” brand. Previously, these threat actors have used ransomware encryptors such as Qilin, RansomHub, and DragonForce. Victims of ShinySp1d3r will receive a note that they have “three days to begin negotiations before the attack is made public on the data leak site”.
Samples of the ransomware have been uploaded to VirusTotal and show a mix of common features and new features developed by the group. The encrypted files will contain “information on what happened to a victim’s files, how to negotiate the ransom, and a TOX address for communications”.
ShinyHunters claims that organizations in the healthcare sector, including pharmaceutical companies, hospitals, clinics, and insurance providers, are excluded from being targeted by its encryptor. However, researchers report that many groups have made similar assurances in the past, only for those self-imposed restrictions to be routinely ignored or violated.
Conclusion
Scattered Lapsus$ Hunters are expected to remain active this year, leveraging both new and familiar tactics to cause disruption across the cyber landscape. The combination of the three groups demonstrates the shift for cybercriminal branding, appearing to highlight credibility and visibility. Given their broad range of targets, effective information sharing between organizations will be critical to countering this threat actor. To mitigate the risks posed by Scattered Lapsus$ Hunters and similar groups, organizations must prioritize monitoring these dark web activities.
To ensure your organization is taking the necessary steps to mitigate threats from these groups, contact us.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















