Blackpanda x DarkOwl: Leveraging Dark Web Expertise to Respond to Cyber Incidents
April 20, 2022
Learn how DarkOwl’s darknet intelligence platform plays a critical role in how Blackpanda supports customers bounce back from an attack, providing robust darknet data to fully understand customers’ risk profile and asses threats. Plus, dive into a case study and see the platform in action.
For those that would rather read the conversation between CEO of DarkOwl, Mark Turnage, and Director of Strategic Development at Blackpanda, Mika D., we have transcribed the presentation below.
NOTE: Some content has been edited for clarity.
Mika (Blackpanda): Thank you, everyone, for coming to this Blackpanda, DarkOwl information session. Very excited to be partnered with DarkOwl, Blackpanda being an incident response firm. We’re going to get into more of that. Today we really wanted to present the value to end users, customers, large companies, and organizations of this partnership that we’ve developed. So with that, we’ll jump into some introductions. Mark is the CEO and founder of DarkOwl with a very, very long list of credentials and much experience, I will hand it over to him to do a bit of introduction.
Mark (DarkOwl): Great, thank you for having us, Mika, and delighted to be here. My background is as an entrepreneur in the security space. All the companies that I’ve run have been security related companies, most recently DarkOwl, which we founded five years ago. My co-founder and I and are very pleased to be here and looking forward to this conversation.
Mika: Great, thank you, Mark. I’m representing Blackpanda, Director of Strategic Development. I was also the founding incident response member of the Blackpanda Group that’s based out of Singapore and Hong Kong. We address special risks from incident response malware, business email compromise, different kinds of cyber attacks all the way down the cycle to cyber insurance. So, risk transfer and mitigation ahead of time to try to prepare the environment in the event that something happens. My background is primarily in national security and a full range of cybersecurity services, products, and a little bit of time in the intelligence community. So excited to jump into this webinar and give you a better idea of how our incident response services and deep web threat intel work together a bit on the cyber incident response side of the house. We hyper focus on digital forensics, the investigation, and cyber crimes, and we are stationed in different cities across Southeast Asia so that we have a local presence in all of these markets if and when an incident occurs.
A bit about the incident response lifecycle because it’s confusing what happens exactly when an organization is hacked and how does that move forward? How do we work with our partners, especially when something happens?
Essentially, incident response starts with a call, an alert or an automated indicator that comes from one of our intelligence platforms, be it DarkOwl or an endpoint detection and response tool or our own proprietary software. Once we receive that alert or notification, we will then determine the validity and extent of the attack. So it’s kind of like scoping out what happened and what resources do we need to deploy in order to address it? We prepare the team and we proceed to a triage process where we’re gathering evidence. We’re looking for indicators of compromise, we’re collecting a plan of action, and we work with the client in order to basically stop the infection from spreading any further. Then we move into the containment phase. Within the first 48 hours, we’ve figured out roughly what’s going on, who is the threat actor, and question what assets could be at risk and what data is at risk.
The customer always wants to know, has data been leaked? What kinds of emails or passwords or proprietary files might be out and be in the dark web? And at that point, we will then turn to some of our partners, such as DarkOwl, in order to enhance that information. So, as we’re containing the malware, we’re also providing the suite of the environment to look for extended attacks. This could be second stage payloads, which would be if the attacker first gets in and spreads more malware, or they’re looking to steal credentials or steal certain files. So, we’re really examining both inside the organization as well as from outside what might have left the organization.
And then, finally, once everything’s been contained, we feel comfortable that the organization can get back online, we prepare a report and present lessons learned. We also try to assemble any and all information that could have been leaked because that’s where regulation and compliance comes into play. So that’s essentially the incident response lifecycle and is one of Blackpanda’s areas of expertise.
Now onto DarkOwl.
Mark: Thank you, Mika. And as Mika mentioned, we are involved in both the frontend and the backend of the incident response cycle with Blackpanda. Just a bit about DarkOwl and what we do. Darkowl has built a platform that actively and continuously monitors the darknets, many darknets, and makes that data searchable by our clients. Among the darknets that we monitor are ToR, I2P, Zeronet, a range of other darknets. And I should say, that we call it the darknet, because in most of these forums and most of these darknets, user identity is obfuscated and traffic is encrypted. So, it’s a very difficult environment to monitor, and we have built a platform that does that across 25 to 30,000 darknet sites a day and it archives that data so that not only will you look and see what was happening today and on a continuous go forward basis, but you also have an archive to see what has happened in the past.You’ll see some of the some of the numbers of records that we have available in our database today.
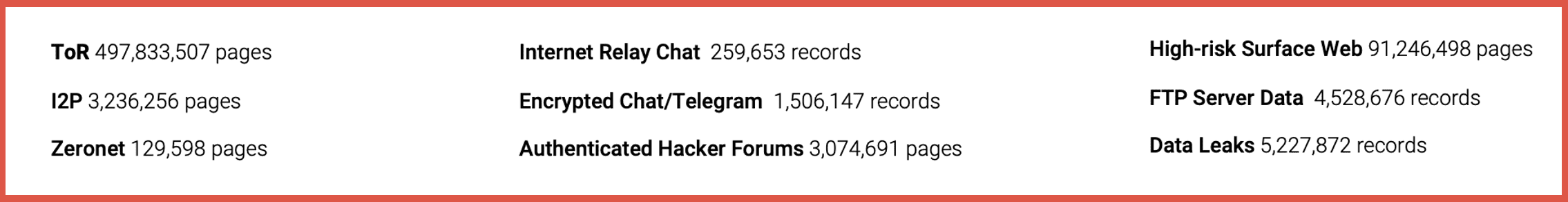
Records available in DarkOwl database as of April, 2022
Just to talk a little bit about what is in the darknet, why is it important for both an incident response team and then more broadly. Among the types of data that are found in the darknet are very large quantities of personally identifiable information credentials, compromised accounts, malware, ransomware. There’s a lot of chatter among a variety of different forums between threat actors. There are lots of vendor and supply risk indicators as well. Most recently, in the context of the Ukraine Russia war, we are finding significant indicators of risk among vendors, supply chain vendors and supply chains that have presence in Ukraine, Belarus, and Russia. A lot of that chatter, a lot of those indicators show up in the darknet and in our platform. A lot of our platform is very intuitive to use. We can deliver data a number of ways what you’re looking at here is our vision platform search UI.
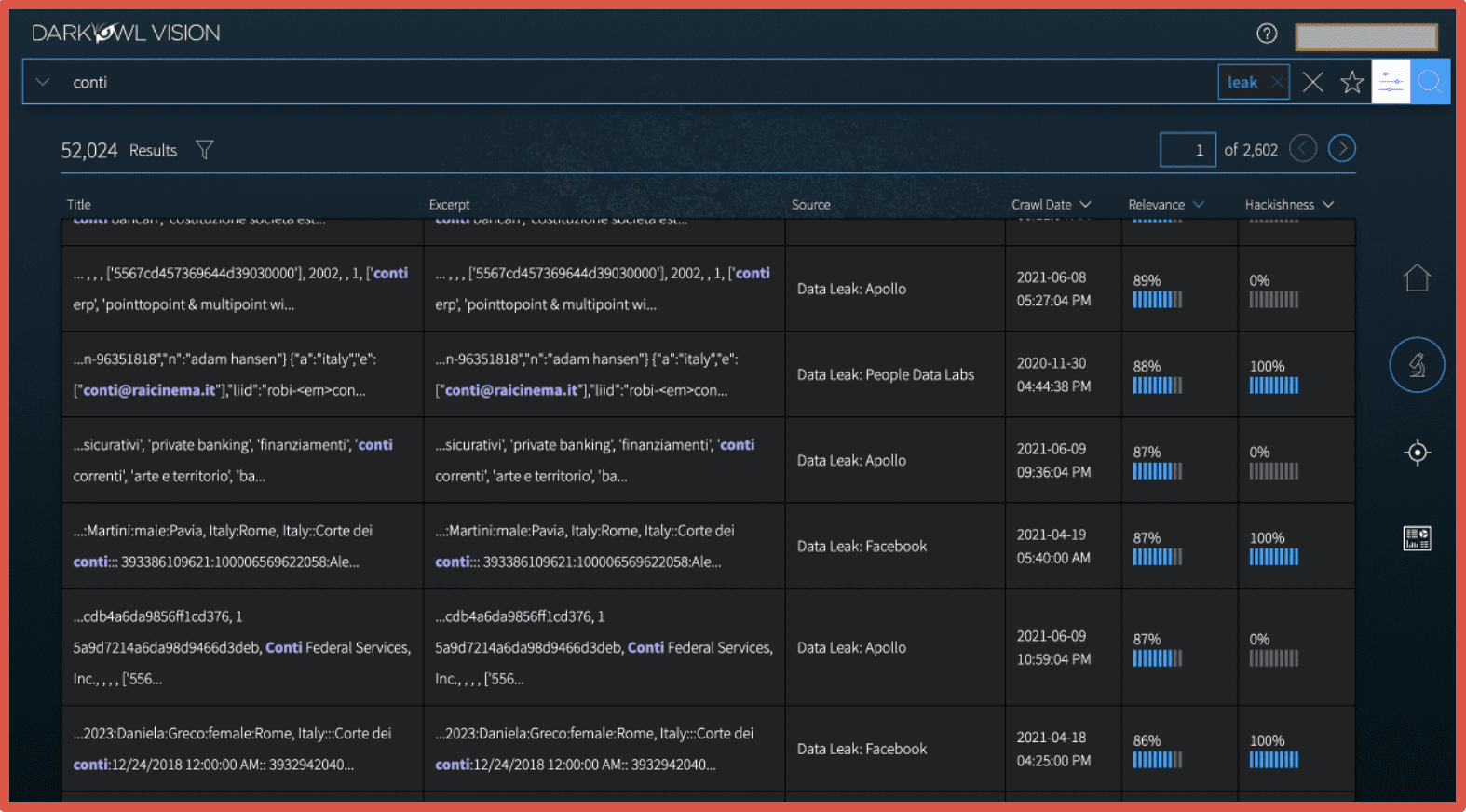
Screenshot of DarkOwl Vision UI platform
And actually, later in this webinar, I’ll do a quick tour. But you can see from looking at the top of this, it’s a very simple search bar. We can look for whatever you’re looking for in the darknet, at any given time. You can see there’s a search loaded on this slide for Conti, one of the threat actors out of Russia, and there are 52,000 results. We see 52,000 pages in the darknet at the time this search was run talking about Conti or mentioning Conti, or where Conti is participating in it in a forum. So, it’s a comprehensive platform to monitor the darknet and in the context of an incident response team, it can both alert you to a breach or to an incident and then it can provide you with the intelligence, as Mika said, to assess that breach and then really remediate it.
Mika: And I was just going to jump in exactly on that point. We’ve dealt with several Conti breaches, and once we see indicators that that might be the malware in use the threat actor in use, not only are we on the hard drive examining the forensic artifacts of the system to pull out what time they got in, what they’ve taken and basically any signs of lateral movement or their actions on objectives, we’re also coming over here and plugging in the exact threat actors names. They have handles, they have email addresses, they have IP addresses, so whatever we find in the environment, this search platform is kind of where we go to see what’s happening on the outside as opposed to just on the inside of the organization across the systems.
Mark: And connecting those dots is critical. If you don’t connect those dots, you’re only looking at one particular piece of relevant information. And we are delighted to be able to offer that level of intelligence to teams like your own.
Mika: Absolutely, and sometimes the crawl date will show a date that much precedes the actual incident. So, the event might have happened even before, and that also helps our forensics because it gives us pivot points in time so we might go back further to the first sign of chatter on a certain target.
Well, I guess this comes back around to how we work together. The reconnaissance phase is what we just mentioned, where a threat actor is mentioning a potential target, the threat actor has scoped out where they’re looking to go and what they’re looking to do, actions on objectives. During that reconnaissance phase, we might see chatter in the dark web. The cyber kill chain is a Lockheed Martin concept that helps explain the chronology of an attack. So, they’re scoping out the target, they’re preparing an exploit that could be used against a vulnerability at the organization, and then delivery exploitation installation is typically where the customer would pick up on the fact that something is happening. Command and Control is quite noisy and usually limited to just forensics and network analysis. But that’s where they are continuing to operate within the environment, using remote access to the organization. And, like we said, actions on objectives. This is where data is leaked or sold on the dark web. This is where they’re actually putting ransomware across systems and trying to extort the organization. All of this can either be incident response based, so in the event of an attack or a proactive service called compromise assessments, which is where we would continuously perform these darknet searches with DarkOwl and we would have software on the endpoints that allow us to perform advanced threat hunting. So, anything we’re seeing, like Mark said, there’s chatter and there’s also indicators across the internet of potential events that could be happening. We can sweep the environment and look for signs of that before something actually happens. So even though antivirus and anti-malware were just some percent of the time, there are advanced threats that don’t yet have signatures that nobody’s tracking yet across the board and these allow us this advanced threat hunting skills and darknet searches allow us to find signs of that much earlier.
We can jump into a case study a little bit before Mark demos. But essentially, Blackpanda had a great success tracing down data leaks following a case in Southeast Asia. We were tasked to discover, analyze, and report stolen or misappropriated data related to client domains or keywords. This essentially means they thought they might have been breached. They hadn’t yet signed on for a compromise assessment, which is basically like a sanity check. Is there something going on? My antivirus didn’t check, and they came to us with the suspicion that something had happened. Over the course of this project, partnering with DarkOwl, and performing very targeted searches for their keywords we then pivoted to compare how this attack was similar to another found threat actor groups and different sites in the deep web that held their records. After about two months, we had 13,500,000 records related to this one company. That allowed them to report and take precautions, and follow on measures to contain the attack and also try to remediate the damage of that data leak. It was very important for them to know the extent and just how much data was actually released. And then we walked them through how to actually patch and repair the systems that led to that attack. So, what happens? How do we find 13,000,000 sum records, Mark?
Mark: Well, that’s a that’s a very good question, and we’ll show you a couple of searches to show you how we do that. It is not unusual for sizable companies to have that level of exposure in the darknet. They are usually the result of multiple leaks, multiple breaches that have occurred over the years. The risk, by the way, to this company and to other companies is that a substantial portion or even a small portion of those records are still alive. So many people will remember the Colonial Pipeline breach that occurred last summer here in the United States, shut down a saline supply to a large portion of the east coast for about a week. It has been publicly reported that the way the hackers got into the Colonial Pipeline network was in fact, via a credential that had been formerly used by an intern that was available widely in the darknet. In other words, there was no phishing that occurred. They just went into the darknet, pulled down a credential, discovered that it was live and walked right into the network into the Colonial Pipeline network. That is one of the risks that occurs. That’s exactly where Blackpanda can add significant value to any client.
Mika: Excellent. So we’ve already been through this kind of wave as to how we could either proactively identify those leaked credentials after a compromised assessment and prevent a lot of these from happening. There’s also the incident response where we get indicators and intelligence that we need to enrich and also check externally whether there’s any additional signs. So these are just more kind of snapshots of how this could work proactively. But, you know, in our reporting, we’re very thorough, this is sort of inside the organization. We’ve deployed a certain endpoint detection and response tool where we’re looking for signs of malware, signs of threats. These are all technical threats that would only be available given a view into the organization. These are all the kinds the strains of malware and hash values that might be in a report. And again, signs of these things can also be thrown into DarkOwl, or a platform that helps us enrich that intelligence. So what else do we know about a file with this hash values of the hash that is the unique signature of a single piece of digital information? Whether it’s a single document or a giant binary file, everything can be hashed to a unique value. So these are great ways to leverage DarkOwl as well. Has anyone else been talking about or posting about malware by this name or with this hash value? Are these websites places that this backdoor Trojan might be still sitting? Has anyone else talked about these particular indicators of compromise? IOCs across the deep web. So these are just a few of the ways that we would really get into DarkOwl and use it not only during an investigation, but proactively as well.
Mark: One of the strengths of the DarkOwl platform is that any of these terms can be inserted in and searched for on the platform. It’s a search tool. It has a fundamental search capability. And as Mika said, we can then identify the threat actors who are discussing it, whether there are future targets, whether there was there were discussions in the past about targeting this particular client’s environment. It’s a wealth of information that opens up once you have the ability to search across the entire dark web for any of these terms or any of these hash values.
Mika: Absolutely, and that’s exactly how we enrich our intelligence and report on what really happened and what could be happening even outside the organization. With that again, DarkOwl traces and brings into their intelligence ecosystem a number of different breaches. So although this was particular to a certain client, you know, these breaches hold passwords of thousands and millions of users. They could be huge. They could be massive databases that are even sometimes an amalgamation of different breaches over time. So DarkOwl keeps us current on what else is happening. And with that, again, we’ve kind of been over the flow in a sense, but we extract indicators of compromise from the evidence we received by going through the forensic intake and triage process. Then we enrich across dark web intelligence sources and perform forensic analysis on the actual system itself. So getting timestamps, trying to bring it back to the root cause. So when did this happen? Why did this happen? And then our reporting can be very robust as a result of us having this level of intelligence. So I guess it’s time to see it in action.
Mark: Well, thank you. If you could let me share my screen, I will switch over. What you see in front of you is the landing page for DarkOwl Vision, our user interface. It’s quite intuitive. There’s a search bar and you can search for any term. As mentioned, they can be hash terms, they can be nicknames, they can be user handles, they can be combinations of all of the above. I’m going to do a quick search and I’m going to pick on AT&T for no good reason. I apologize if anyone from AT&T is going to see this. I’m going to do a search for AT&T .com, and I am going to search for any mentions of AT&T .com in the darknet, meaning any page that has a credential or mention of AT&T .com domain on it. And as you can see, there are almost half a million pages in our database in the darknet mentioning AT&T .com. The results are presented here. If you scroll down, you’ll notice that M.J. Matthews of AT&T .com has, as mentioned, a range of email addresses that are mentioned here, and the results are can be sorted and presented in a number of different ways. If I search, if I sought these results, these half million results by crawl date, for example, and there are a lot of results, so this will take a second. You’ll see that the most recent of these results was extracted from the darknet about an hour and a half ago. So this is a very recent result, and I can then sort them by relevance and hackishness, is a term we use to date to determine how dangerous those results are. So, for example, I won’t click on it, but down here, my guess is this is 100 percent hackishness because there’s a password associated with that particular domain. So it’s very intuitive, it’s very easy to use. As Mika mentioned, a team that is looking for a specific term or an actor in the darknet can very easily and very intuitively jump onto this platform and see what’s happening and then say, what were they doing most recently? And you can sort by crawl date. I want to show one other feature that is relevant to what Mika has been talking about, which is our dark and exposure scores. I can create a score for any domain, any domain in the world, and I’ve just randomly selected. You can see even there’s a dark score here if I click on this AT&T score. This is a score of how exposed AT&T, since I just did the search, is in the darknet and you’ll see the score changes and you’ll see as I move my cursor, the score changes in proportion to how much data is available in the darknet at any given point in time around AT&T. And I’ll take the example of BlackBerry here. BlackBerry on the 5th on the 14th of May of last year had a score just above 10, and overnight their score jumped to just under 14. That’s a massive jump in our scoring metric and in our scoring algorithm. And the reason is somebody released a bunch of data around BlackBerry. In fact, a terrific amount of data around BlackBerry. If you’re a user of the platform or a partner like Blackpanda, this is an indicator that something’s gone wrong. There has been a major compromise. We need to investigate this very quickly. So this provides a very quick back of the envelope way to monitor clients, to monitor your own environment, to see what’s going on and to compare how you are doing relative to, say, your competitors or other peoples, other people who are in your sector. The platform comes with a range of other ways that you could pass data, search data, and make use of data, including an alerting platform, so that if, for example, AT&T is a client or you are AT&T and you’re monitoring your own environment, you can be alerted by email to any critical elements that show up in the darknet at any given time. So that a very quick demo, Mika, and thank you for allowing me to do that. But you can see it’s a very intuitive platform. It has direct usage in the incident response phase, and we’re delighted, as I said earlier, to partner with Blackpanda.
Mika: I think that’s our last topic, just on that again, it’s been very powerful for us to be able to show again every, every organization that’s been hacked. It’s the worst day. It’s a terrible event. But in the event that we get those early indicators and we’re able to stop something before something even worse happens, you know, at the sign of chatter or proactively by finding initial indicators of an intrusion and correlate that with deep web intelligence and then stop this thing before it happens. It’s just a very powerful solution. So we’ve been thrilled to partner with DarkOwl. And if there are any questions after the webinar by all means, we’ll provide contact details in posting this this recording.
Curious about something you read? Interested in learning more? Contact us to find out how darknet data applies to your use case. You can also reach out to Blackpanda here.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















