Using DarkOwl Vision to Protect Brand Value and Reputation
May 10, 2022
This blog discusses how DarkOwl’s software-as-a-service (SaaS) product suite – Vision App, Search API, and Entity API, can be utilized to protect corporate brand reputation and value.
Darknet Background
The darknet – also referred to as the dark web – is a segment of the Internet, hidden by the novice user, that is only accessible by using specialized software or network proxies. Due to the inherently anonymous and privacy-centric nature of the darknet, it facilitates a complex ecosystem of cybercrime and illicit goods and services trade. The most common darknet to date is “The Onion Router” or simply, Tor.
The deep web is a collection of websites that do not require anonymization software to access but require unique knowledge of the URL or account curation and authentication for entrance. While a personal banking account portal is technically in the deep web, much of the deep web facilitates cybercrime through criminal marketplaces and discussion forums.
DarkOwl defines darknet-adjacent networks, such as servers and channels from Telegram, IRC, and Discord as instant-messaging chat platforms featuring real-time communications (or “chatter”) of on-going criminal activity and active cyber operations.
Decentralized Darknet Marketplaces
The darknet is home to decentralized darknet marketplaces (DNM), e-commerce platforms where buyers and sellers transact directly with each other through peer-to-peer networks or the Tor network. Marketplaces usually employ cryptocurrency-based escrow built into the marketplace to facilitate secure and anonymous deals between the buyers and vendors.
One of the first and most well-known darknet marketplaces is the Silk Road, established in 2012 by its founder, “Dread Pirate Roberts” – Ross Ulbricht. Upon its shutdown and for years after, the US government seized an estimated of $1 billion USD in Bitcoin connected to Silk Road.
The seizure of Silk Road and the lifetime sentence of Ulbricht has not deterred criminals from continued illicit goods trade in the darknet. As of time of writing, DarkOwl has knowledge of 30 large-scale decentralized markets currently online and hundreds of smaller single-vendor operated or single-product marketplaces in operation across the darknet and deep web.
Forms of Brand Mentions in the Darknet
Corporations and organization, along with their key leadership, are regularly targeted and ‘mentioned’ in the darknet – across marketplaces, discussion forums, and transient paste sites. Many times, the references are specific to a cyber campaign to target the company while others are perfectly-matched counterfeited goods marketed by underground counterfeiters and resold on darknet decentralized marketplaces.
The most common types of critical brand mentions in the darknet include:
- Derogatory Mention by a Disgruntled Customer or Employee
- Personal Dox of Corporate Leadership and/or Board Members
- Targeting Data in association with Malicious Cyber Operations
- Leaked Critical Company Data
- Cracked Software Distribution
- Pirated Media and Streams
- Counterfeit Product Sales
Examples of Corporate Brand Mentions in Vision
Using the common forms listed above, this section provides real-examples of brand mentions in the darknet, deep web, and darknet-adjacent platforms and captured by DarkOwl’s autonomous content crawlers.
A disgruntled employee of Wells Fargo states that the company is ‘scandalous’ and ‘corrupt.’ They also highlight a major cyber risk for the company, where they have been instructed to use other employee’s logins to do their job.
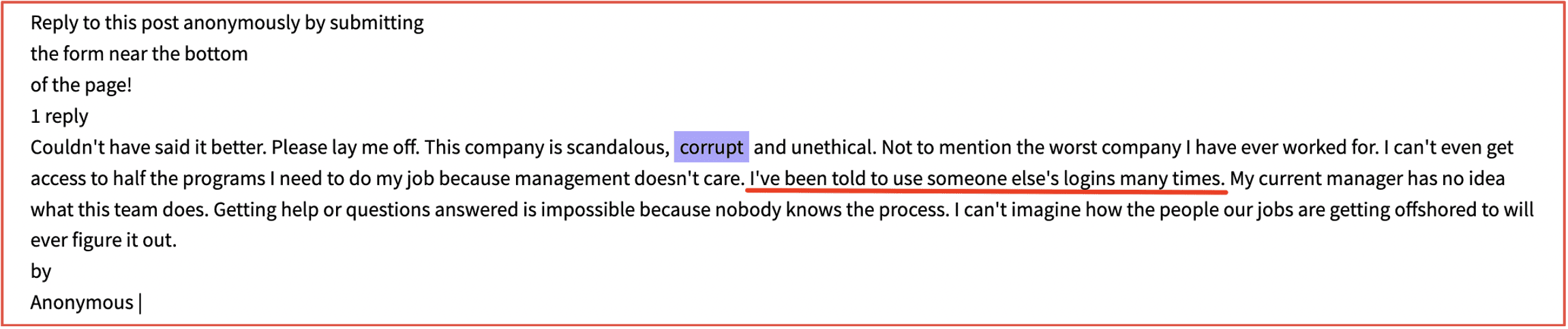
Figure 1: Source DarkOwl Vision DocID: 7f32e227c2590d5c2e04fd0b3e5d051042940641
An employee at Amazon compares tradeoffs NBA players must perform with the harsh working conditions at Amazon corporate (not warehouses).
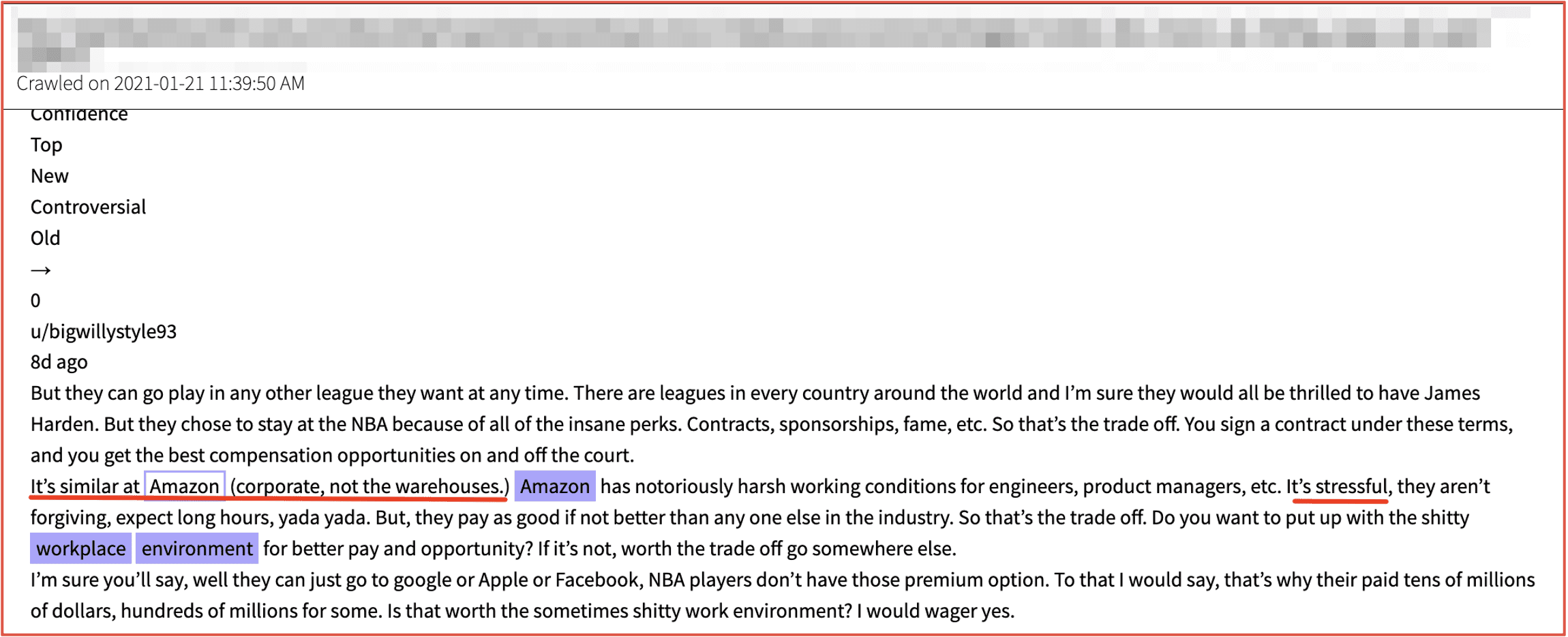
Figure 2: Source DarkOwl Vision DocID: 136d898fde08e2217c8bf43c26930f1fd7356bd1
A dox (also doxx) is a detailed public record of someone’s identity. To ‘dox’ someone is to publish private information about that person – as a form of public shame and generated to enact revenge on the company or person for some perceived wrongdoing. The dox presents a significant security threat to the company and the individual, with detailed information such as their mobile phone numbers, residential address, social media accounts, bank accounts, and familial associations publicized and subsequently targeted for phishing, fraud, and even kidnapping for murder or extortion.
Every ‘dox’ has a reason for publishing the information to a public record.
Corporate leadership, members of the board of directors, and key figures related to many brands and international entities are regularly targeted for ‘doxing’ in the darknet.

Figure 3: Source DarkOwl Vision DocID: d8ba881fd4f01f8e691a7fcfada1b4ad3ebc7d64
Threat actors identify Gazprom’s subdirectories, subdomains, and IP addresses in preparation for a concerted attack against the oil and gas supplier in retaliation for Russia’s invasion in Ukraine.
Less than a month later, a significant volume of data from Gazprom and its subsidiary, Gazprom Linde Engineering was leaked on the darknet including 768,000 emails from the joint Gazprom-Linde Microsoft Exchange server.
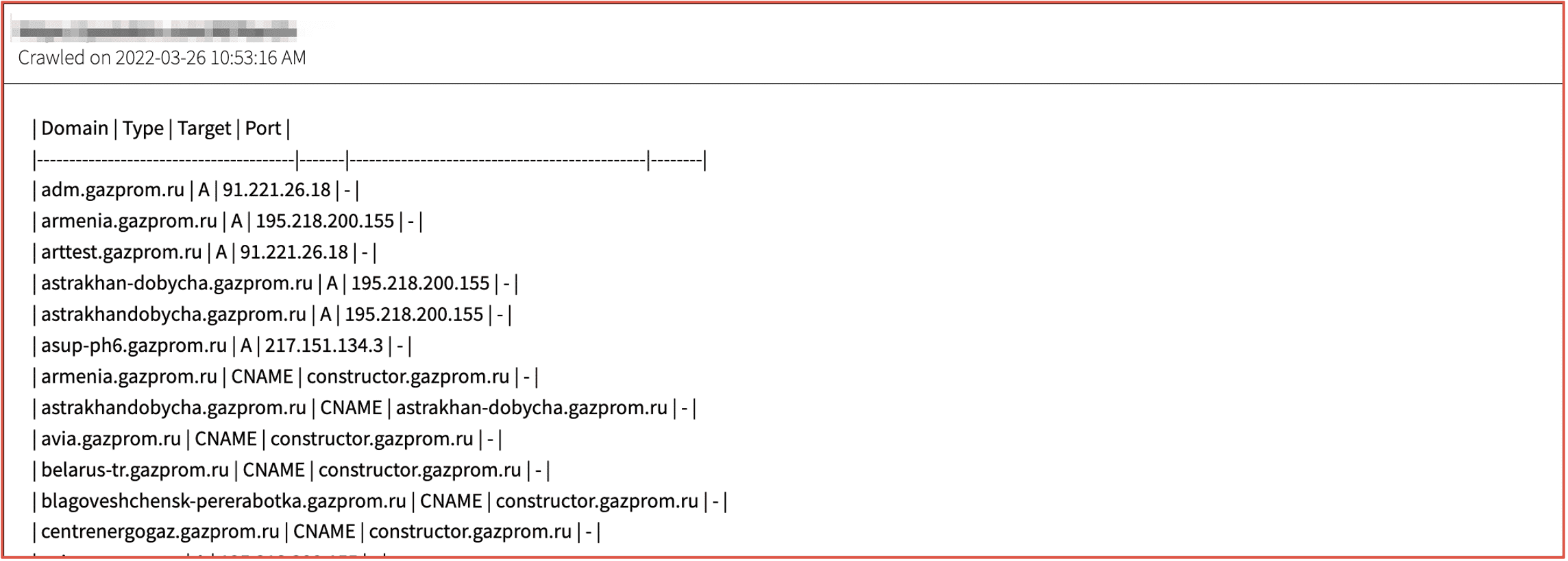
Figure 4: Source DarkOwl Vision DocID: 77be2205969371938bb235f463f94fa32cb4552d
Hacktivists regularly target companies and brands in support of geopolitical and social injustice initiatives.
The image below includes an announcement on Telegram by pro-Ukrainian hackers calling for the boycott of purchasing Nestle products due to their continued operation in Russia and subsequent economic support for the Putin-backed Kremlin.
In the days following the post on Telegram, prominent darknet threat actor group, KelvinSec compromised Nestle’s company network and leaked sensitive databases containing their customers, transaction, and shipping data.
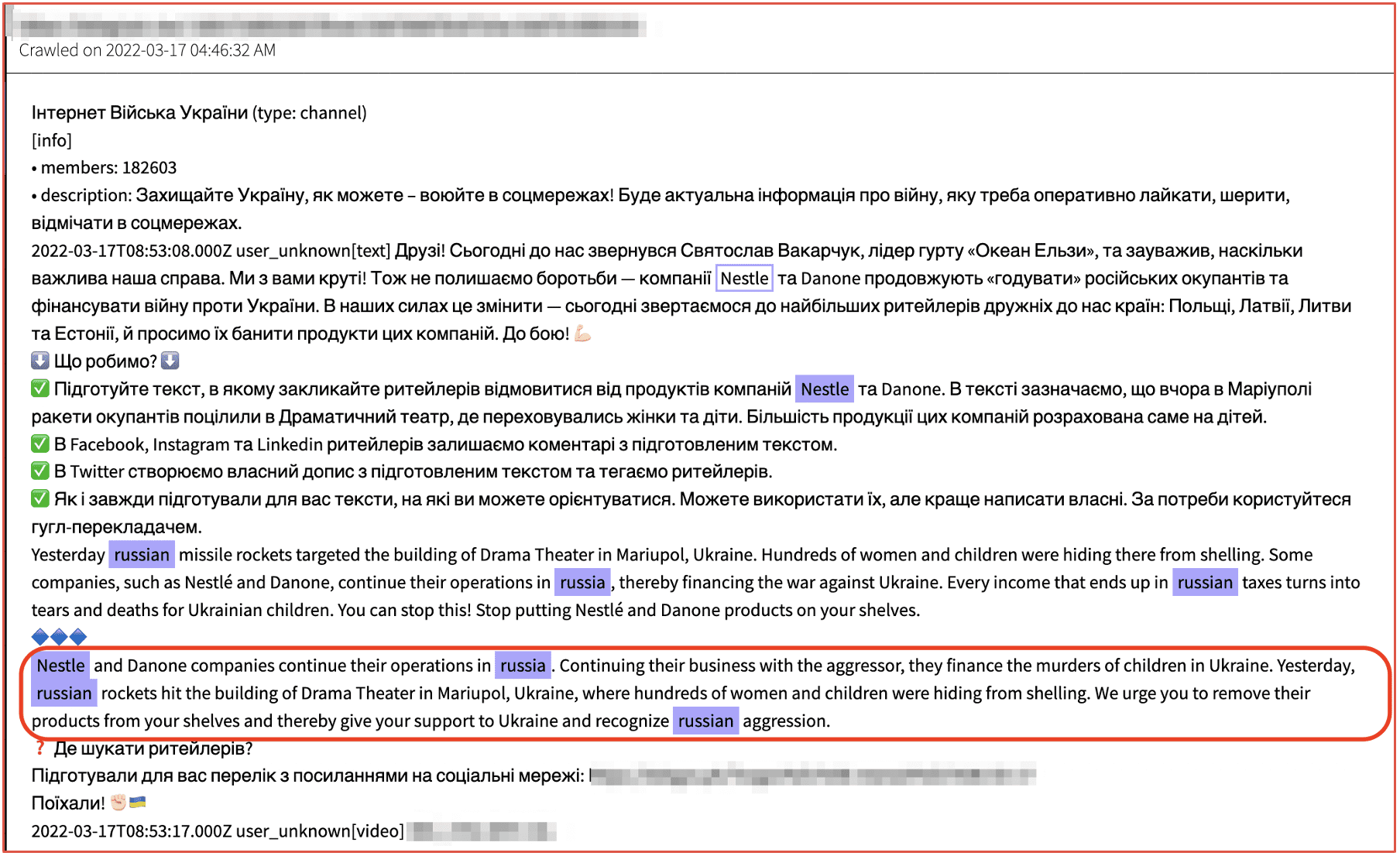
Figure 5: Source DarkOwl Vision DocID: 9b5dde8629bcb38002c81e3d19a47470ebddd263
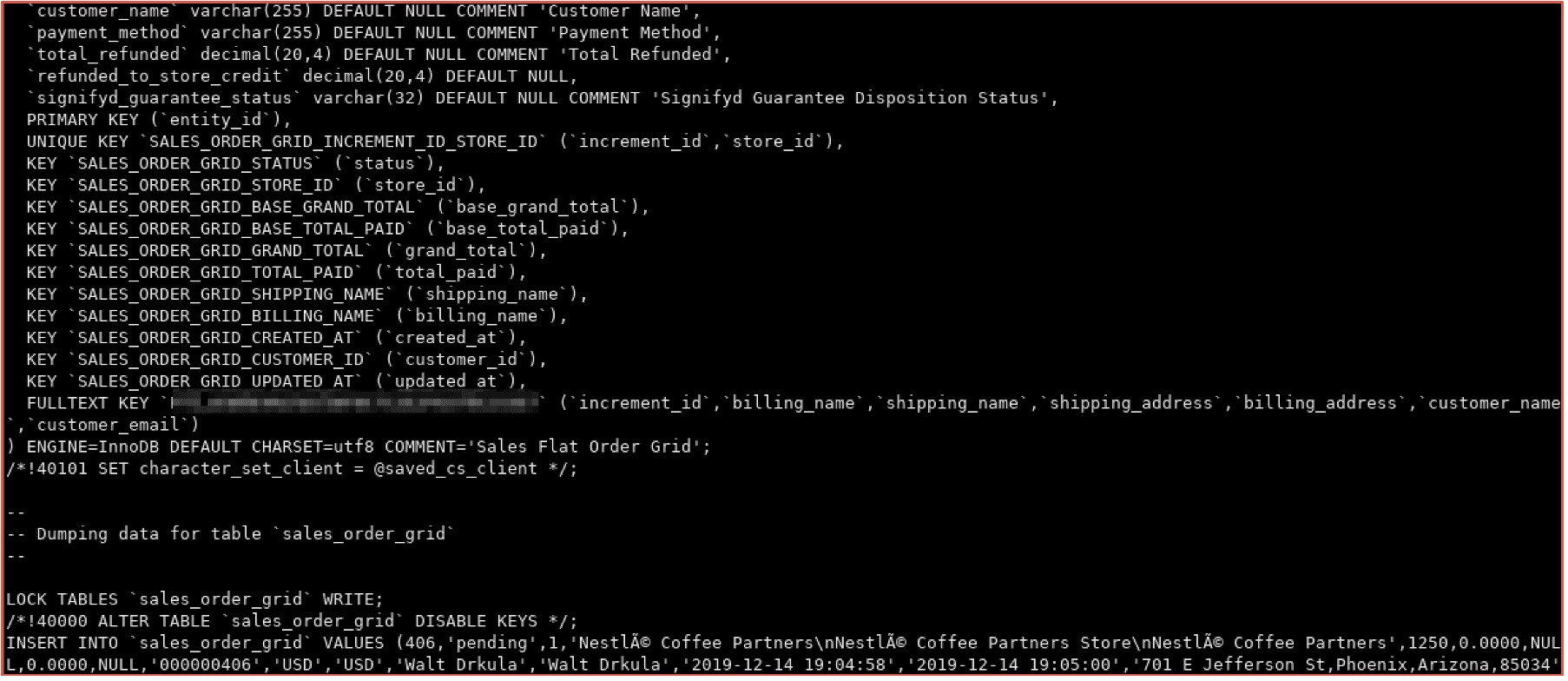
Figure 6: Screenshot from the actual database leaked from Nestle, consisting of customer entity data, orders, payment information, and passwords (10GB total)
Cybercriminals often leak large sets of company-proprietary and sensitive data obtained via ransomware attack or malware infection of a company’s network. Critical corporate data might include – but is not limited to – software source code, sensitive email communications, employee W2 verification data, identity documents such as driver’s licenses and passport images, and financial statements.
The example below is source code exfiltrated by LAPSUS$ threat actors after a major cybersecurity incident against the SAMSUNG corporation.
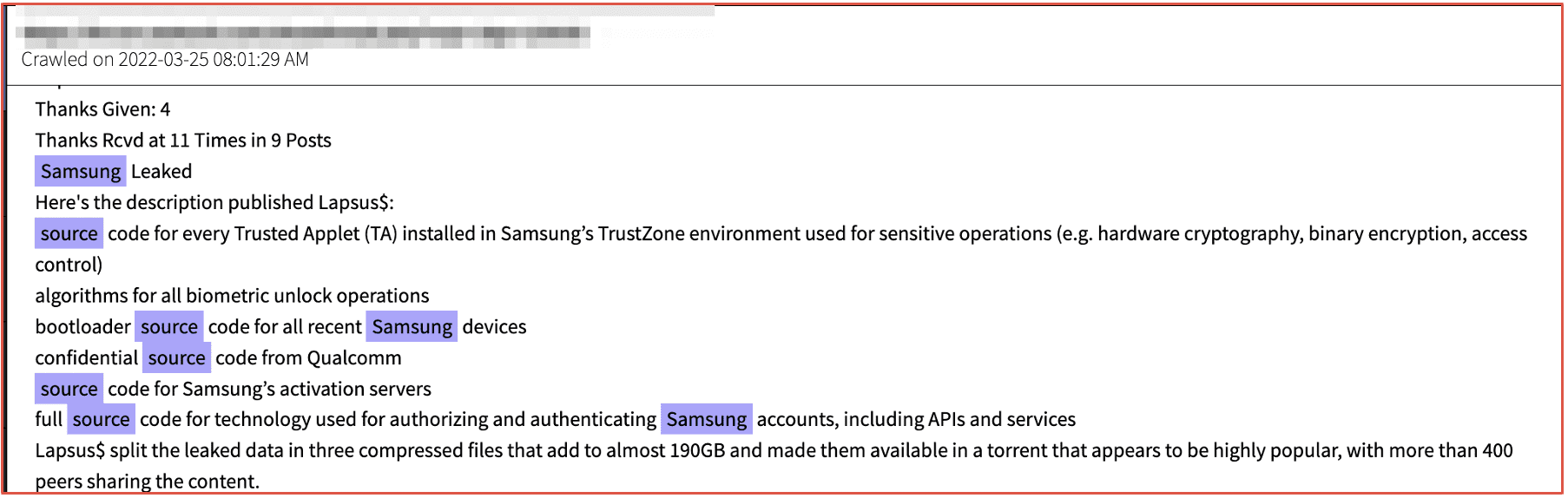
Figure 7: Source DarkOwl Vision DocID: f7d9d309d34853f0b1236d437ef1314460b54223
“Cracking” is a broad term used by darknet and deep web threat actors to describe the process of breaking into something, more often bypassing software licenses and passwords required by computer software programs.
Adobe Products are regularly targeted for ‘cracking’ due to steep costs for their software product licenses and subscriptions. Threat actors on Telegram detail how to install ‘cracked’ version of Photoshop and DLL manipulation to override licensing requirements.
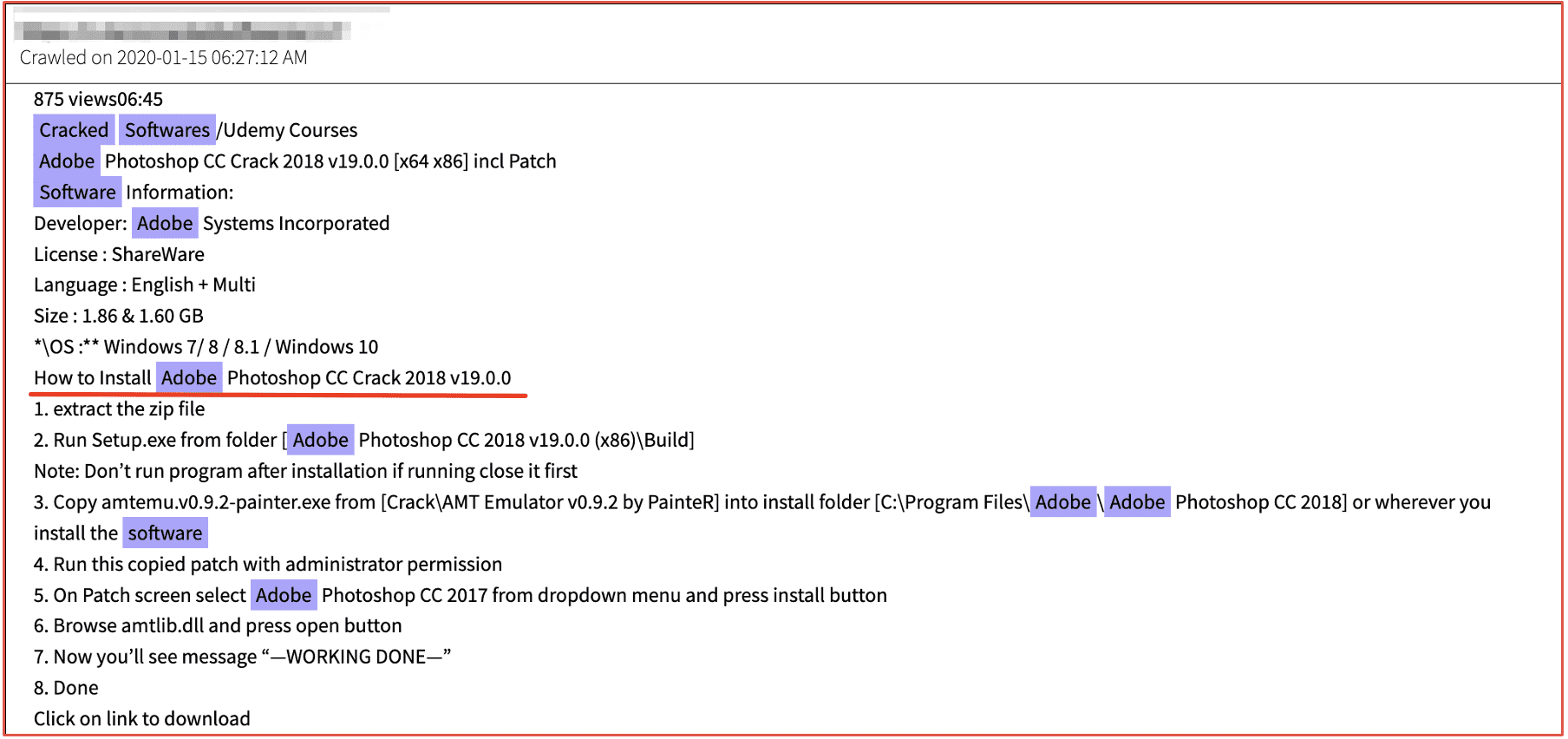
Figure 8: Source DarkOwl Vision DocID: 52401ddd38f3386b57b07bfc161d06813d6bd23d
Pirated media, movies, and streams have continued presence on the darknet. The Pirate Bay – considered the “most resilient BitTorrent site” on the Internet still circulates the latest movie titles.
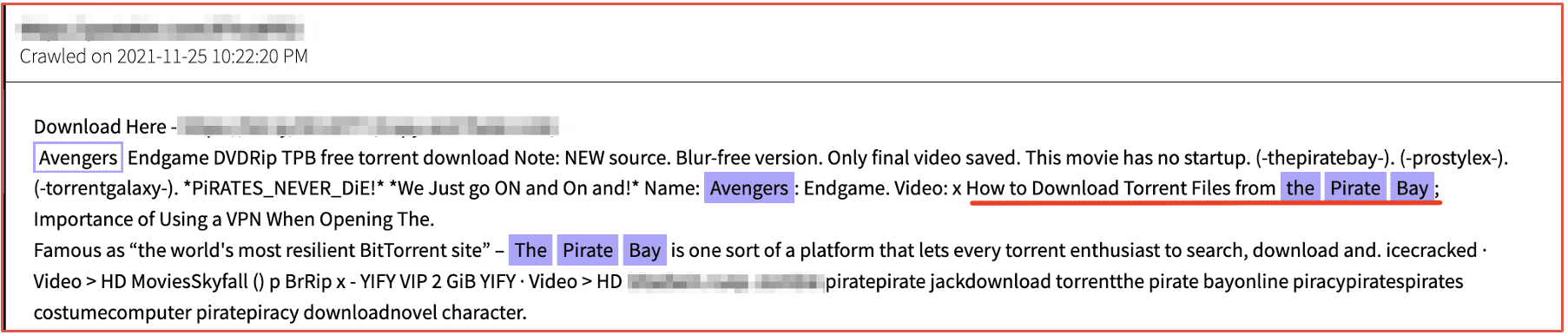
Figure 9: Source DarkOwl Vision DocID: db4dda0c5ab85082b2c6b98c5948f1ad60c162ba

Figure 10: The Pirate Bay BitTorrent Download Landing Page
The illicit trade of counterfeit goods is a multi-billion-dollar international industry – which continues to be led by China. According to Europol, surface web monitoring helps crack down on the major counterfeit goods suppliers, but many sophisticated networks simply shift to the darknet and use decentralized darknet markets to sell their counterfeited items.
Many darknet marketplaces feature a section of “counterfeit goods” that encompasses physical counterfeited items, a buyer can purchase and have sent to them directly. Watches and fine jewelry are the most common physical goods offered on underground marketplaces.
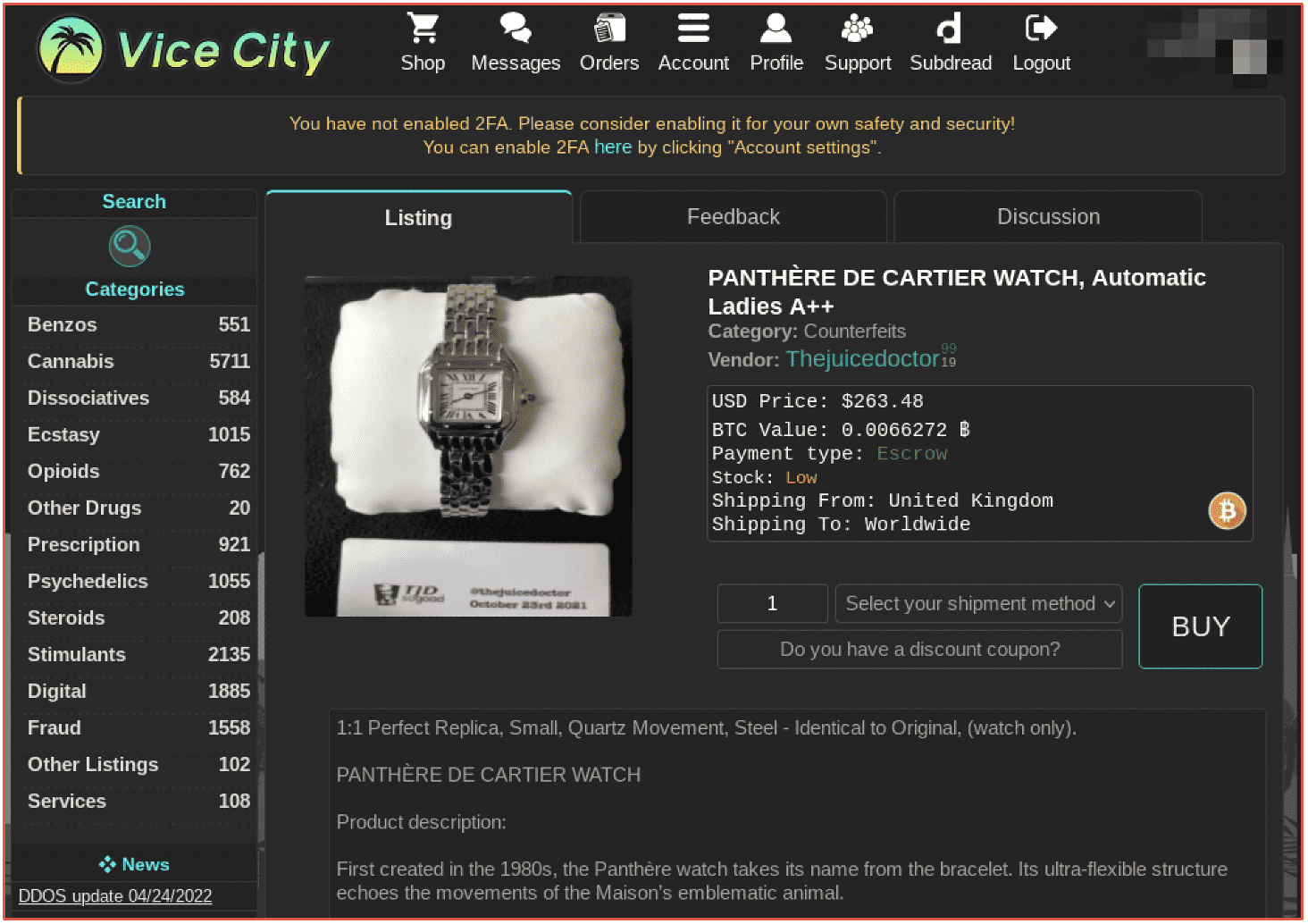
Figure 11: Active Listing for a Counterfeit Ladies’ Panthere de Cartier Watch on Vice City
Marketplaces are more commonly known for their diverse and extensive selection of drugs available for purchase. DarkOwl has witnessed the defamation of many brands in affiliation with common street drugs.
For example, the Warner Bros (WB) entertainment brand has been extensively used by drug dealers on the darknet in the advertisement of “WB-shaped” ecstasy (XTC) pills and their comic-book heroes and cartoon franchises exploited in the distribution of marketed Batman, Superman, and Looney Toons-specific drugs.
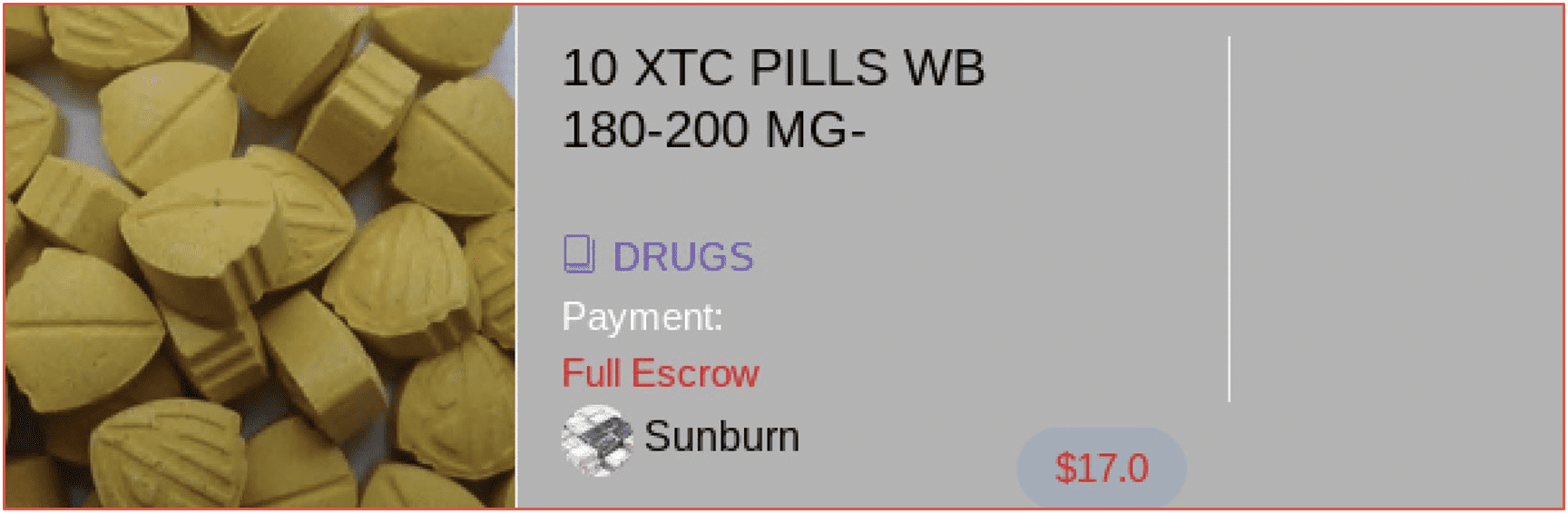
Figure 12: Screenshot of Offer Captured in DarkOwl Vision DocID: 1411b1671a1aeedae7c1add5b996d769
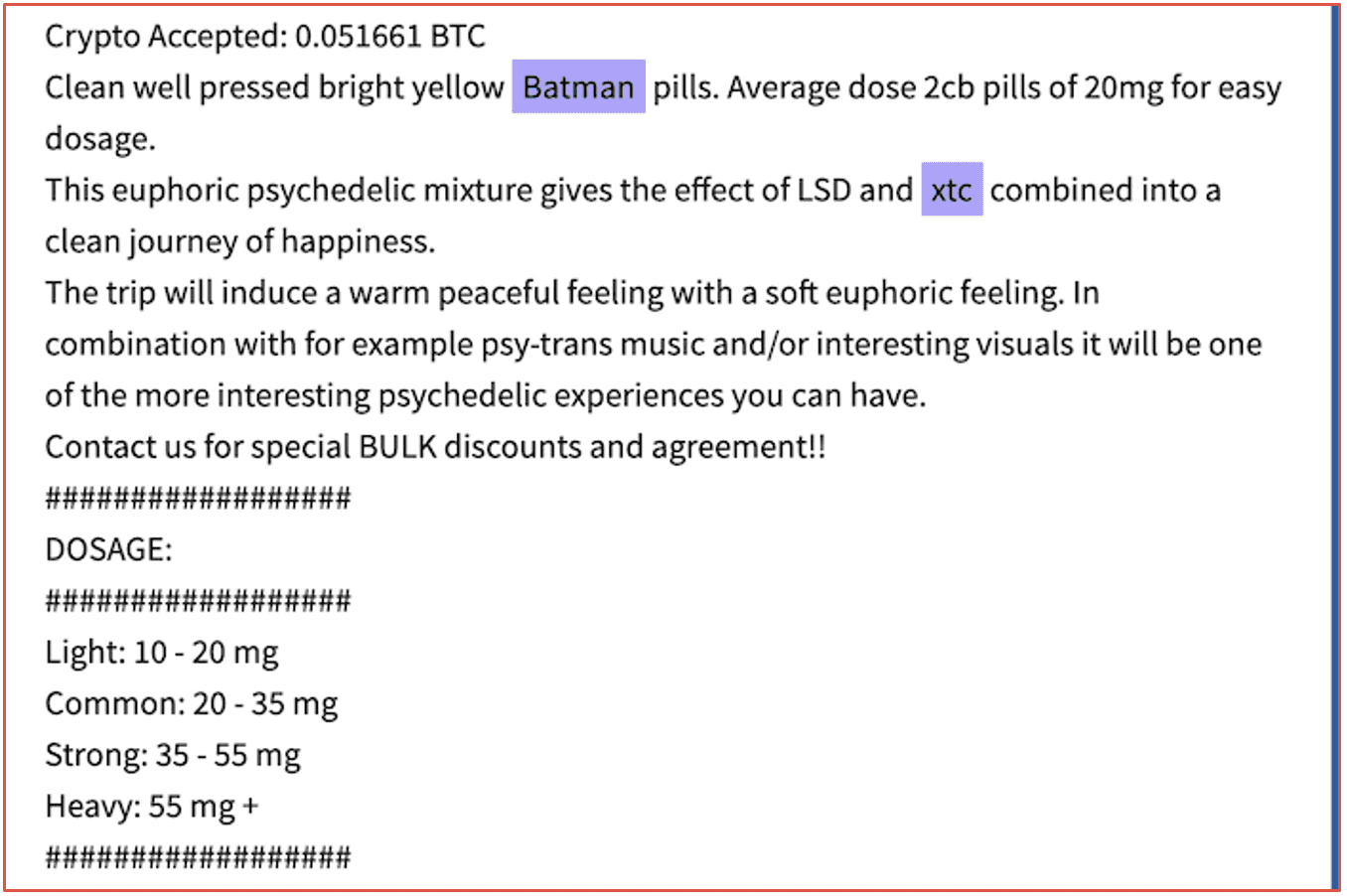
Figure 13: Source DarkOwl Vision DocID: 58f39ef647bfdb931f6b8d147cd86b85
DarkOwl Solutions for Brand and Reputation Management
DarkOwl’s SaaS product suite of its Vision App, Search API, and Entity API are designed to help augment surface web monitoring for brand mentions like those discussed and outlined in this document.
In the Vision App, analysts can create automated monitors and alerts to notify when critical corporate information or counterfeited products are circulated in darknet paste, discussions forums, or marketplaces.
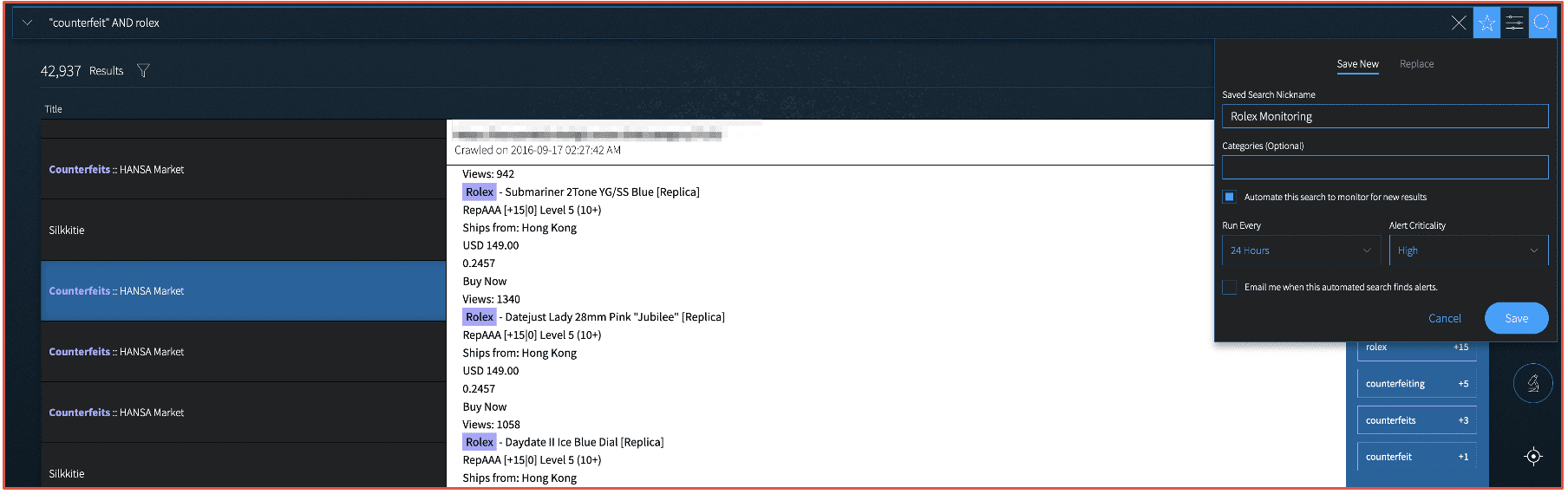
Figure 14: Screenshot from DarkOwl Vision’s Search, Monitoring, and Alert Features
Curious about something you read? Interested in learning more? Contact us to find out how darknet data applies to your use case.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















