What are Stealer Logs?
December 06, 2023
DarkOwl analysts have observed an increase in stealer log data available on the darknet in the past couple years. Stealer logs are logs of sensitive information that have been stolen from compromised victim devices. Data from stealer logs can be more damaging to victims in the hands of a bad actor than the credentials found in leaks and breaches. The data obtained through an infostealer allows a bad actor to get multiple kinds of information, such browser data, credentials, IP addresses, crypto accounts, about the victim rather than the limited information generally offered in a leak.
From email accounts to banking credentials, stealer logs can grab it all. This could result in a number of attacks such as identity theft, tricking individuals or institutions to transfer money (or drain accounts), account takeover, fraudulent purchases, and other forms of fraud. Many victims do not know that their machine is infected by stealer malware since they are often distributed by phishing emails, fake websites, fraudulent software and apps, and other social engineering methods. In this blog, DarkOwl analysts will break down what stealer logs are and how they work. As stealer logs start replacing the role of leaks and breaches, they will be the ones to look out for.
Stealers, Infostealers, and Stealer Logs
Stealer log-related terminology is defined below:
A stealer is another word for an infostealer, or information stealer. Per DarkOwl’s darknet glossary, a stealer is “a software-based program, typically malware, that is deployed on victim devices that when executed or downloaded is designed to take credentials, cookies, and sensitive information to take advantage of the victim financially, engage in fraud, and possibly identity theft.” After the stealer has covertly accessed stored information, it will transmit the data back to the cybercriminal.
Infostealers are commonly delivered by social engineering, such as malspam campaigns and phishing emails. Typically, attachments with malware are included in the email. The email likely has a “lure,” or a legitimate-looking trap to encourage victims to open the attachment or link and install the malware onto their device. Information stealers are on the rise and promise lucrative business opportunities for cybercriminals.
While researching for our piece “Pardon Me While I Steal Your Cookies – A Review of Infostealers Sold on the Darknets,” darknet analysts also learned many infostealers are offered in alignment with a malware-as-a-service (MaaS) or stealer-as-a-service (SaaS) rental model with subscriptions-based access to the malware executables and associated command and control C2 botnets.
Stealer logs are the logs that are extracted from what is generated from the information stealers. The logs contain credential data created after the information stealer has been installed on a device. After the malware (the infostealer) has gone through the system and extracted the valuable information, these logs are sent from the compromised machine to a C2 (command and control), controlled by the cybercriminal, and can be distributed from there, such as being sold on the darknet.
Autofill: a feature found in most browsers that will automatically populate previously entered information into form fields.
Cache: a cache is a system for the storage of temporary files such as web browsers and other media so that the page can be accessed without being downloaded again.
Cookie: text that is sent by a server to a web client, and returned by the client each time it uses that server. This technology is typically used for authentication of website users, session tracking, and also for maintaining information about the users.
Session Cookies: a file with a string of letters and numbers, known as an identifier, that is sent by a website server to a browser for use during a limited timeframe. A session cookie is sent with the browser request for a web page from a server. The session cookie communicates to the server which parts of a page the browser already has so that the server does not re-send them. When the browser is closed, the session cookies are deleted.
Persistent Cookies: persistent cookies are not deleted after the browser is closed and the sessions ends. Persistent cookies are data files that can give websites saved user preferences, information, settings, and login credentials.
Hardware Identifier: the Hardware Identifier is used by Microsoft in Windows. A hardware identifier is an identification string defined by the vendor used by Windows to match a device to a driver package. The particular HWID is produced when the operating system is installed.
Why do Stealer Logs Matter?
The information in stealer logs can give a cybercriminal the information they need for identity theft crime, financial crime, and could essentially result in a total online takeover in some cases.
Stealer logs can obtain everything that you do on your machine. How many applications have not been signed out of? How many accounts open directly without credentials? How many cookies have you accepted? Do you log out of Amazon every time? Is your credit card saved to your account? A bad actor using information from a stealer log can get acces to all of this and more. Everyday mundane actions on the technology that we’ve come to rely on in our daily lives can be accessed, stolen, and sold.
The data from stealer logs can be so useful to bad actors because of the types of data it can target and exfiltrate, including browser data and cookies. Browsers save information such as sites visited, search histories, cookies, cache, and autofill data.
Browsers are the applications such as Chrome, Safari, and others used to access the internet. Browsers save browser histories, which is a record of the sites the user has visited. Browsers save cookies, search history, download history, and cache. Browsers will also save usernames, passwords, credit card information, addresses, and more if the user elects for the browser to save that information.
This information also comes from autofill data saved to browsers. Exfiltrated browser data in a stealer log can give a bad actor a trove of PII (SSN, dates of birth, addresses, phone numbers) as well as financial information (credit cards) and credentials (usernames and passwords). A bad actor can combine this data and use if for theft and fraud against the victim.
Cybercrimninals can access accounts by recreating credentialed sessions using cookies taken from victim devices by infostealers. If a bad actor has the cookie from an authorized credentialed session, they can re-create account access and get to the account. Even if the bad actor does not have the username and password to a site, if they have the cookie from the browser they can use that cookie to take the credentialed session to clone access to the account. The browser may recognize the credentialed cookie session as the victim logging in, not the bad actor. Email services and banks may not raise a red flag when a bad actor logs in with stealer log cookie data, because with cookies the actor is accessing the credentialed session.
Another reason why stealer log data is so valuable to cybercriminals is because stealer log data tends to be more timely. Leaks and breaches can occur years after a user initially registered, and therefore the credentials (such as passwords) may not be up-to-date. However, stealer log data will contain the victim’s most recent details. A stealer log pulls the most recent passwords and credentials from the victims machine rather than the third pary where the account was registered.
Even if a user is following healthy cyber-hygiene practices and changing their password every 90 days, a stealer log can make those efforts moot. Furthermore, a victim may not be aware an information stealer has infected their device even if they use antivirus software. When a user authorizes the action to download the malware, antivirus software will not be able to prevent the infection. Since stealers are typically downloaded by accident, can bypass antivirus software, can be difficult to locate unless by an expert, and give the most up-to-date information, they are incredibly valuable to cybercriminals.
Breaking Down a Stealer Log
The following sections will break down the different components of a stealer log. Data is obtained from a stealer log found in DarkOwl Vision.
Browser Data
Many browsers will ask users if they want to save information that has been entered into forms (e.g. remembering a password for a website) while on that browser. A stealer log can exfiltrate saved browser information from a victim device and send it back to a bad actor.
Figure 1 from DarkOwl Vision displays some of the browser data that can be found in a stealer log. In the example below phone numbers, dates of birth, usernames, and passwords have all been taken from saved browser data by a stealer log.
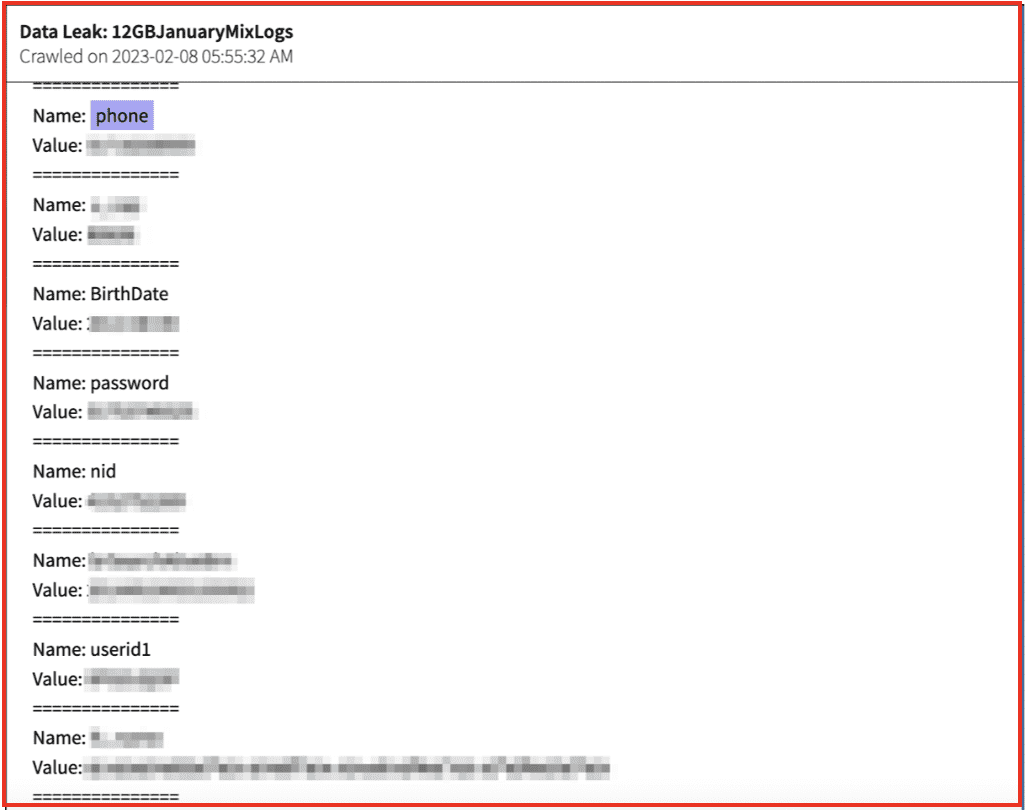
Figure 1: Source: DarkOwl Vision
Browser Data and Cookies
Technological cookies are text that is sent by a server to a web client, and returned by the client each time it uses that server. This technology is typically used for authentication of website users, session tracking, and also for maintaining information about the users. DarkOwl analysts have observed cookies in stealer logs from the darknet.
A bad actor who has access to cookies could use those cookies to recreate a victim’s credentialed session—meaning after they have signed in—to gain account access. Below data of a stealer log taken from DarkOwl Vision shows saved cookie information in stolen browser data from a stealer log.
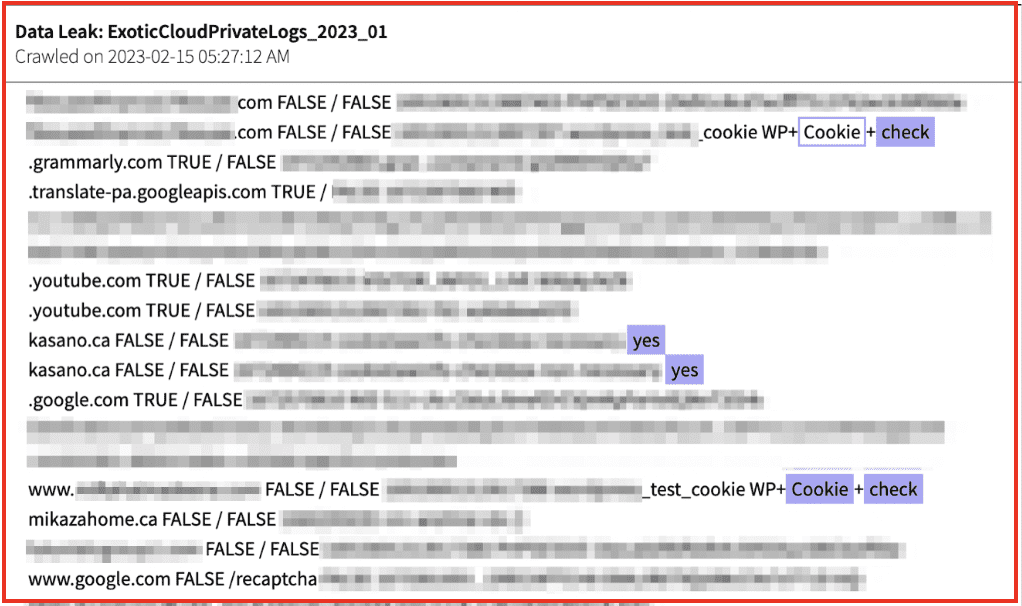
Figure 2: Source: DarkOwl Vision
Autofill Data
The autofill data taken from a browser in Figure 3 gives a victim’s username and password to multiple accounts as well as the URL and application used. The username and password for the Google account as well as the scholarships.gov credentials could be used to impersonate and financially harm the victim. Additionally, any financial credentials saved on other sites with compromised usernames and passwords, such as Trip Advisor, could be leveraged by a cybercriminal.
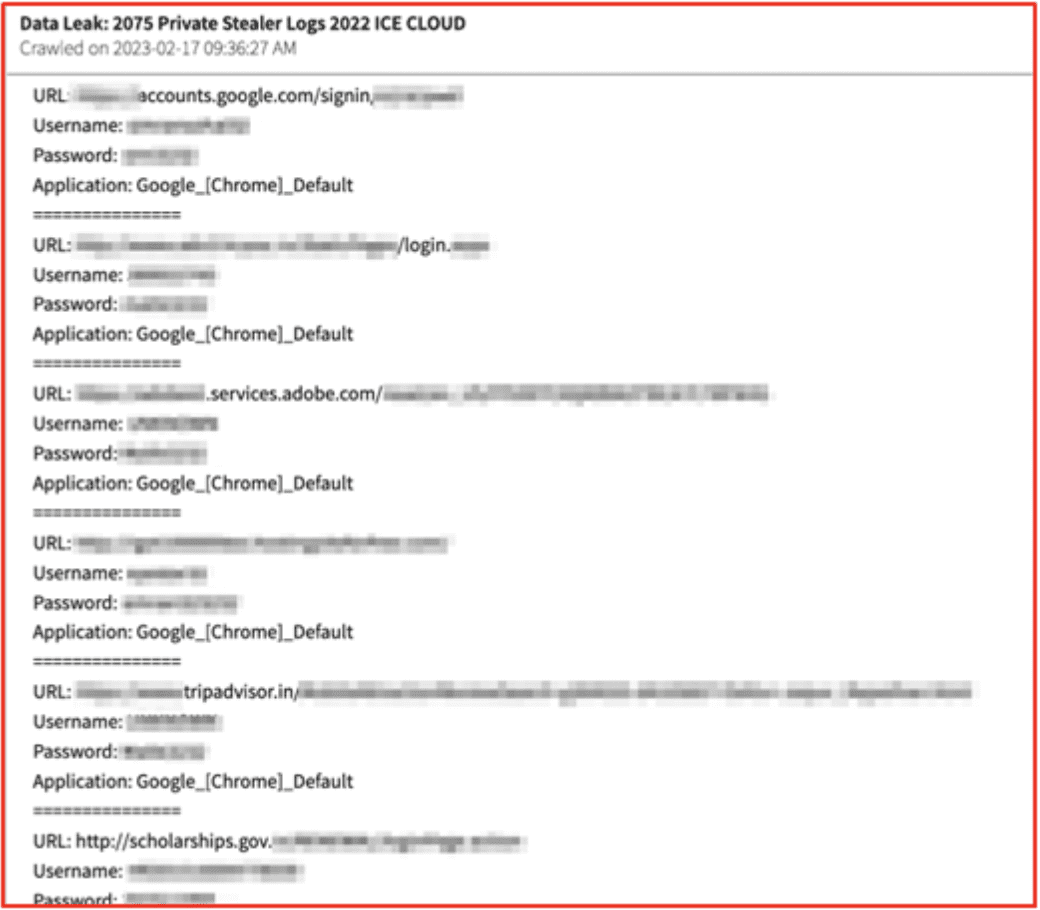
Figure 3: Source: DarkOwl Vision
In Figure 4, the autofill data from the stealer logs gives the victim’s phone emails, addresses, full names, dates of birth, and social security numbers.
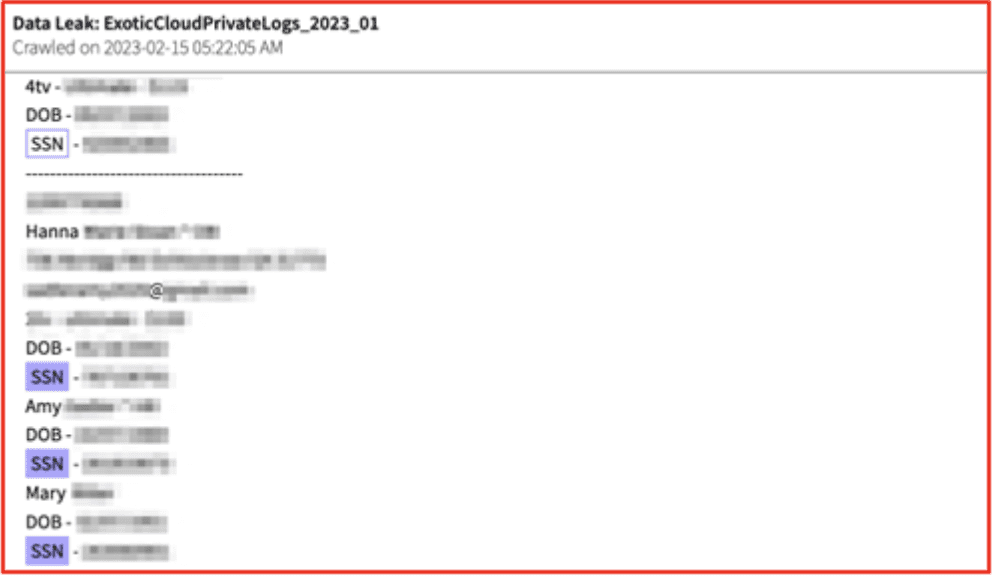
Figure 4: Source: DarkOwl Vision
Another file from the stealer log in Figure 5 distinguishes the most important autofill data. This way the most beneficial auto-filled data is readily available for a cybercriminal to use, and they don’t have to waste time searching for it.
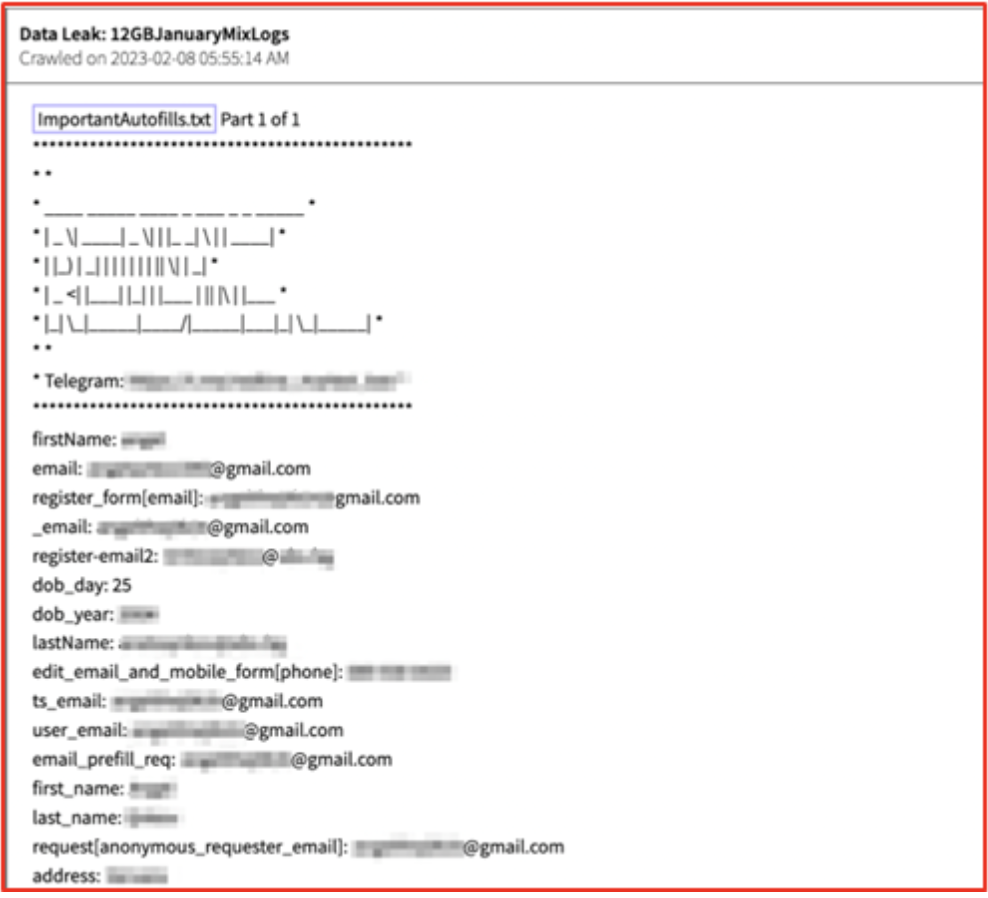
Figure 5: Source: DarkOwl Vision
Domain Detects
A file found in stealer logs observed by DarkOwl analysts contains a “DomainDetects.txt” file. This file gives access to the highest priority domains found in the log.
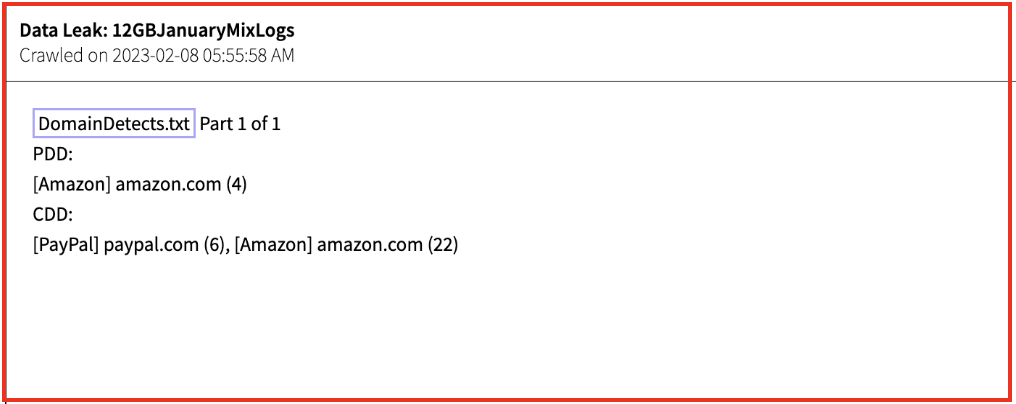
Figure 6: Source: DarkOwl Vision
Installed Browsers
A specific file shows all of the installed browsers and versions of those browsers from the victim device.

Figure 7: Source: DarkOwl Vision
Installed Software
Another file has all of the applications on the victim’s compromised machine.
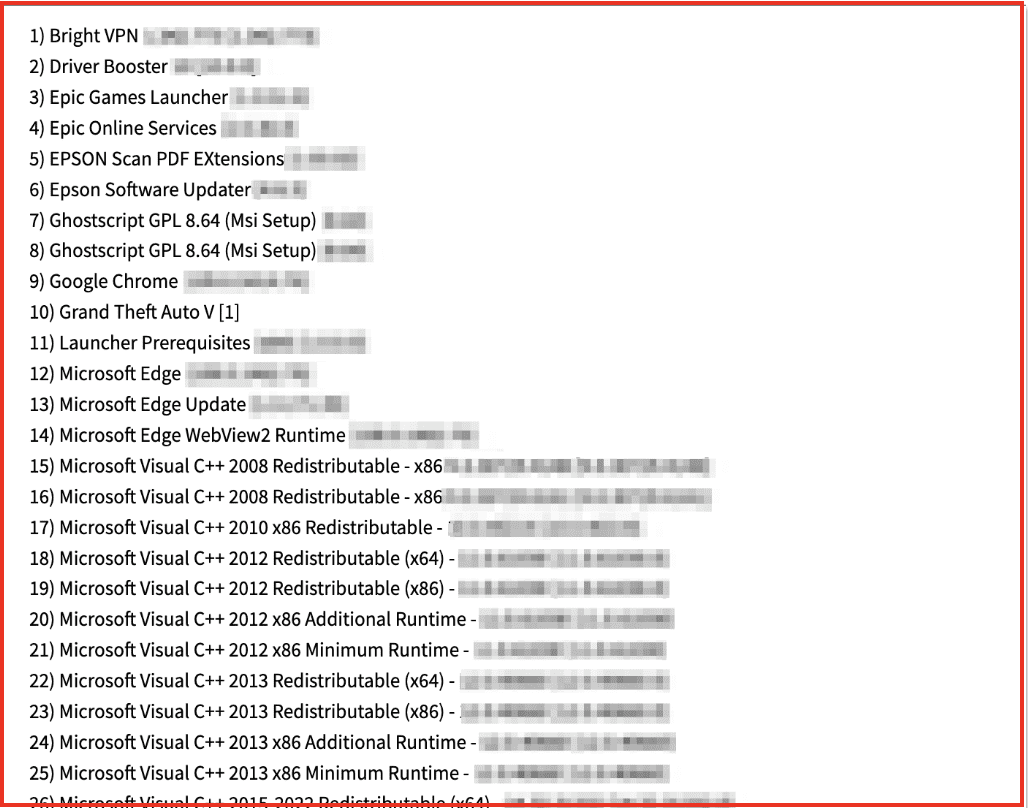
Figure 8: Source: DarkOwl Vision
This kind of information is especially helpful to investigators, as they can see what VPNs are being used. A bad actor could also leverage some of the information for advanced social engineering—from this entry we can see that the device has games including Grand Theft Auto and an Epic Games Launcher.
User Information
Finally, the stealer log contains a file called UserInformation with details about the victim’s device. This includes IP address, country, zip code, HWID (hardware ID), language, the height and width of the screen, time zone, operating system, UAC (user account control), keyboards, hardware’s, anti-viruses, and storage (RAM, MB, bytes).
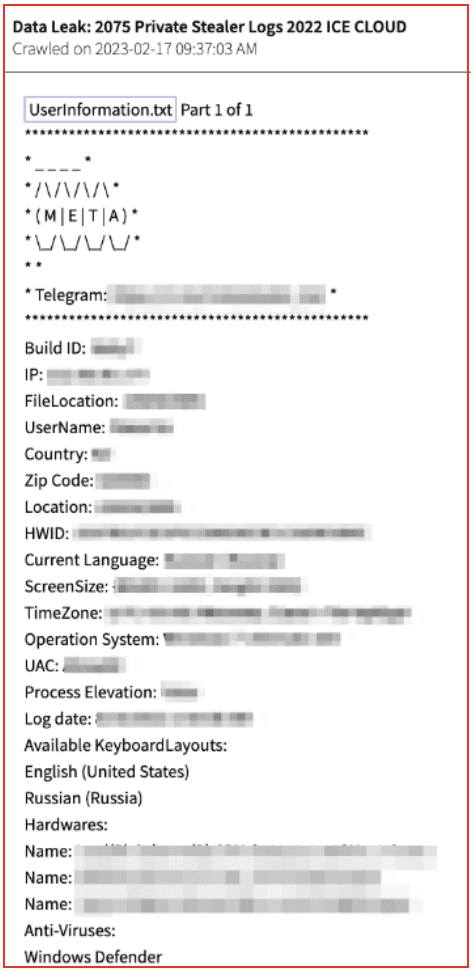
Figure 9: Source: DarkOwl Vision
Information taken by stealer logs can be used to defraud people in general and to identify specific individuals and machines. Individuals can be identified if their social security number is taken by the stealer. A machine can be specifically identified by certain kinds of hardware, including a HWID (Hardware Identifier) that is redacted but pictured in Figure 9.
Final Thoughts
Stealer logs are a reminder how fragile online identities and accounts are. At any moment, with the few wrong clicks of a button, everything could be taken over usually unbeknownst to the victim. Stealer logs are becoming more prevalent on the darknet and may soon replace leaks and breaches as cybercriminals’ preferred method for stealing credentials. The data is generally fresher than credential data found in leaks and breaches and individuals tend to be an easier target than a corporation with a security team. However, cybercriminals can also be victims of infostealer malware which could be very useful to investigators.
Don’t miss any research from the DarkOwl team. Subscribe to email here.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















