What is Bullet Proof Hosting?
September 21, 2023
Bullet proof hosts (BPH) are web hosting providers that are less regulated with the services they allow compared to traditional Internet Service providers (ISPs), hardly restricting any kind of content. BPH services are frequently used by online casinos and actors who intentionally spam or run other illicit online activities. They generally take all the material and practices that legitimate hosting services prevent (fraud, abuse, pornography, gambling, and hate speech, to name a few) and permit it. Just as legitimate businesses rely on ISPs, criminal and malicious threat actors (including state-sponsored advanced persistent threat [APT] groups) rely on the resilience of bullet proof hosting to conduct their operations.
While traditional ISPs aim to combat cybercriminals and online fraud and abuse, BPH actually empower and aid the criminal ecosystems, offering resilient infrastructure and avoidance of law enforcement operations. Even when there are takedown requests, abuse reports, or law enforcement actions, such as subpoenas, BPH ignore them. BPH will create shell companies or simply move IP ranges to keep questionable activity up and running. In some cases, BPH will even tip subpoena activity or takedown requests to the actors using their infrastructure, which gives them time to react, move their operations and prevent losing financial assets. For these reasons, BPH are crucial to the continuation of the cybercriminal ecosystem.
The geographical component is essential to the success of a BPH operation. Bullet proof hosts usually establish themselves in areas which have vague or lenient cyber laws and policies towards these practices. Furthermore, they ensure to operate in areas which have no extradition to the Five-Eye countries: The United States, Canada, Australia, New Zealand, and The United Kingdom. Locations that commonly allow for and host BPH include: China, Romania, Bulgaria, Estonia, Panama, and the Seychelles, among others. In China, spamming is a completely sanctioned activity, whereas in the US, the FTC established tight guidelines to differentiate between “spamming” and authorized business activities, such as sending cold emails for business purposes. BPH also rely on the pseudonymity of cryptocurrency payments to operate. In this way, they almost facilitate a “don’t ask, don’t tell” mentality for the criminal underground, allowing actors to carry out nefarious operations while turning a blind eye or pleading ignorance.
Another term for BPH is DCMA-ignored hosting. The Digital Millennium Copyright Act is geared to protect copyright holders from theft of their material and aid in combating copyright infringement online. It only applies to specific ISPs who meet certain regulations. Most BPH do not meet these standards and regulations. The most effective way to combat the material hosted by BPH is to blacklist their entire IP block.
In August of 2023, researchers in the cyber threat field broke the news that Cloudzy, a New York company actually run out of Tehran, Iran, was providing infrastructure to both nation state and criminal cyber actors. Researchers estimated that 40 – 60% of Cloudzy activity was malicious. Like other BPH, Cloudzy takes payment in cryptocurrency and claims to protect the privacy of its users. Cloudzy also ignored takedown requests and abuse reports. However, Cloudzy goes above and beyond a normal BPH profile, hiding its company ties to known governments and criminal conglomerates worldwide and masquerading as a legitimate provider. In addition to known nation state actors tied to using Cloudzy infrastructure, ransomware affiliates and initial access brokers were observed using Cloudzy services in their operations.
Examples in DarkOwl Vision
After the Cloudzy research broke, DarkOwl analysts observed some of the latest trends for BPH in 2023. It is a competitive market where the actors using these services expect full time support, dedicated servers, and protection from online threats such as DDoS attacks, while also expecting protection from law enforcement. They want cheap and reliable service as well. Promises like live time are critical because of efforts to remove BPH from operation. It takes time for criminals to set up what they want to use the BPH for – if they are immediately taken down, that is lost revenue and opportunity for the cybercriminals. Several screenshots from DarkOwl Vision below:
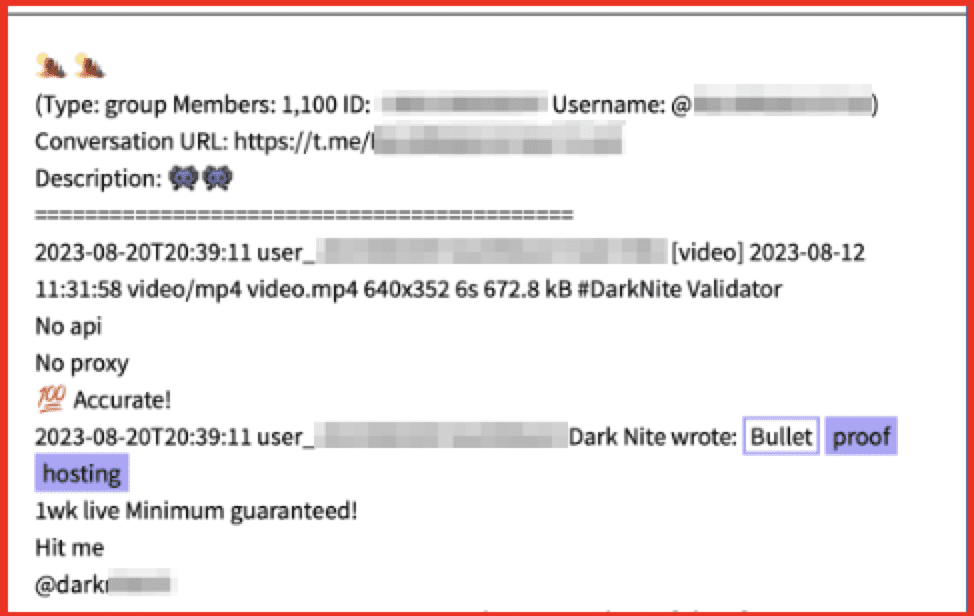
Figure 1: Threat actor “darknite23” advertises BPH services with a guaranteed live time; Source: DarkOwl Vision
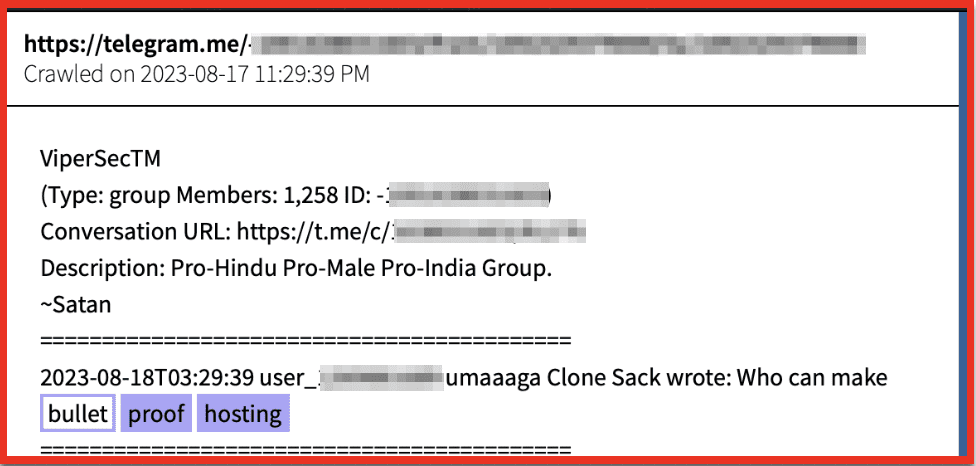
Figure 2: An actor solicits BPH services in a Telegram channel; Source: DarkOwl Vision
Actors on discord discuss the merits of having either a virtual private server (VPS) or dedicated BPH, and name CrazyRDP and Privatealps as bonafide BPH. A VPS can be easily moved or relocated in the instance of abuse or if they are targeted by law enforcement:
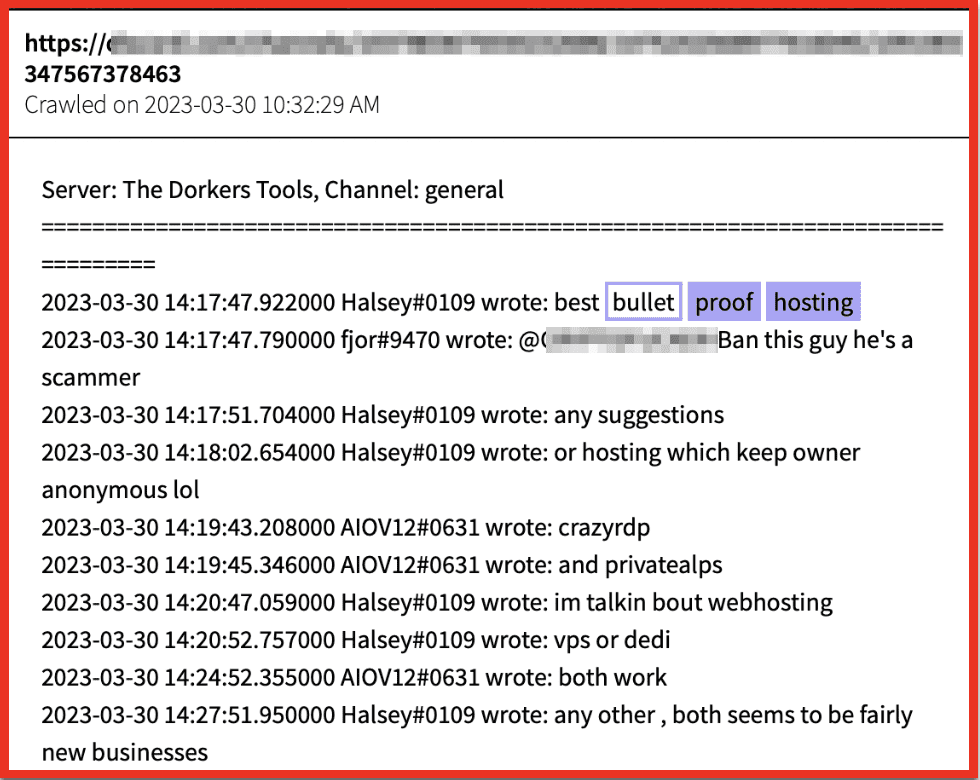
Figure 3: Actors on a chat platform server discuss some of the believed better BPH service providers; Source: DarkOwl Vision
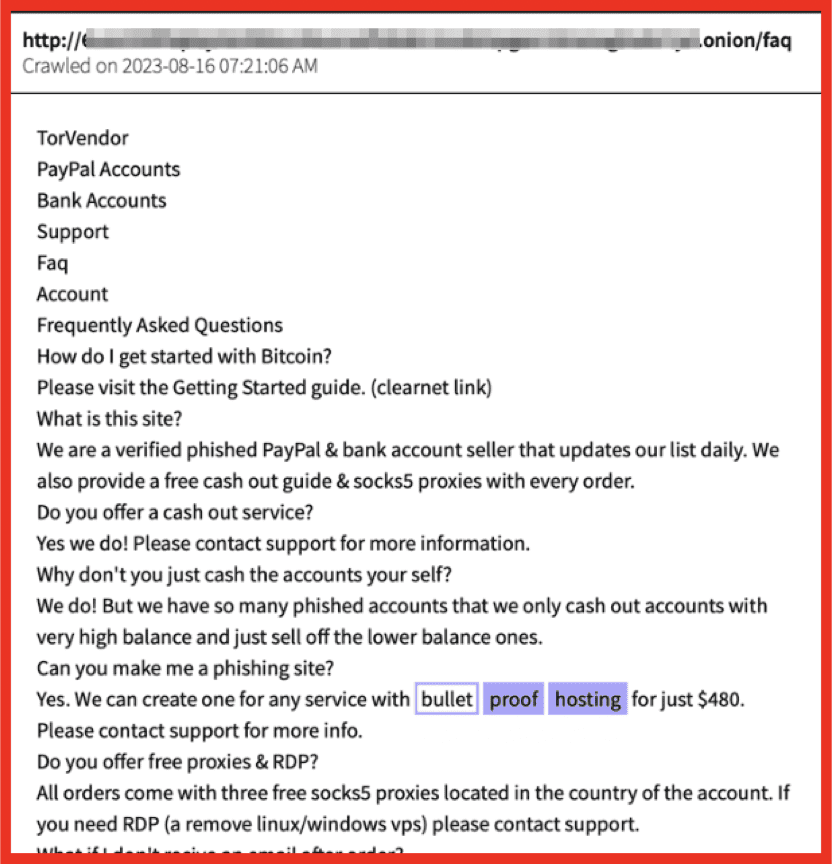
Figure 4: Actors discuss BPH costs and services to use in their various operations; Source: DarkOwl Vision
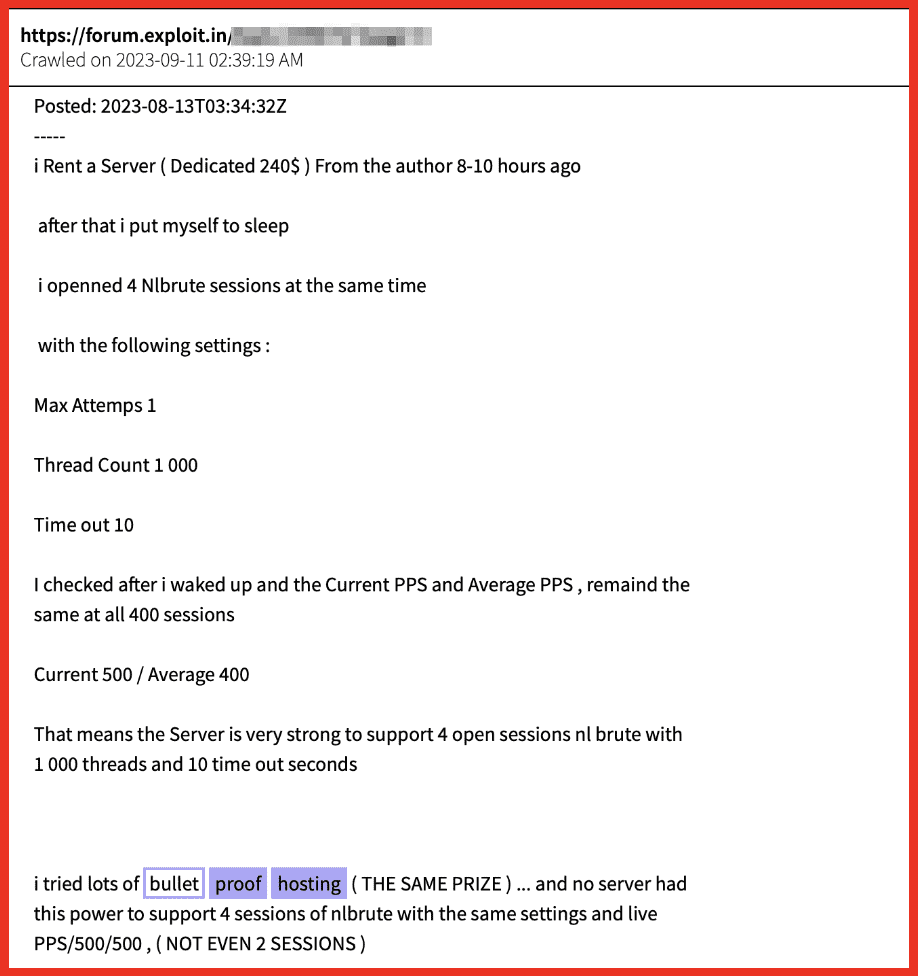
Figure 5: Users discuss merits of a BPH on Exploit, one of the top criminal markets; Source: DarkOwl Vision
Conclusion
Bullet proof hosting providers are known to facilitate the cybercriminal underground, their actors, front companies, and all types of illicit activities. In an ever-connected world where humans are looking to express themselves, promote their causes, cling to freedom of expression, or even make extra money, balancing online freedom and preventing invasions of privacy is crucial. However, freedom of expression cannot be lumped in with inciting violence, promoting continuing online hate, terrorism, and violent campaigns, in addition to attempting to compromise and extort businesses, critical infrastructure bodies, and government entities. Bullet proof hosts facilitate and enable some of the worst actors in the space. They must be studied and observed in order to prevent them from gaining more momentum and enabling additional compromising activities online.
Questions or comments? Put me in touch!
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















