DarkOwl Releases Entity Explore to Boost Efficiency for Dark Web Threat Intelligence Analysts
November, 2022
DarkOwl Vision UI’s new “Entity Explore” enables end-users to gain more relevant insights from their vast dataset of dark web content.
As part of our continued effort to enhance our dark web data products with features geared towards analyst and threat intelligence teams, DarkOwl is excited to announce our newest product feature, Entity Explore. Launched in the form of a new dashboard within Vision UI, Entity Explore shows results for queries around tokenized objects with critical contextual information.
The dashboard also incorporates new features geared toward increasing analyst efficiency and functionality, enabling things such as ease of exporting and parsing of information to best lead users towards actionable intelligence.
Insight into Dark Web Data is of Increasing Importance
One of the most prevalent use cases for insight into the DarkOwl’s data is the recent persistent rise in ransomware activity, which largely presents itself on the dark web. In 2021, 37% of all business were hit with ransomware – the vast majority of which likely had their sensitive information leaked on underground forums. That same year, over 535M breached credentials associated with Fortune 1000 companies were reportedly circulated on the darknet.
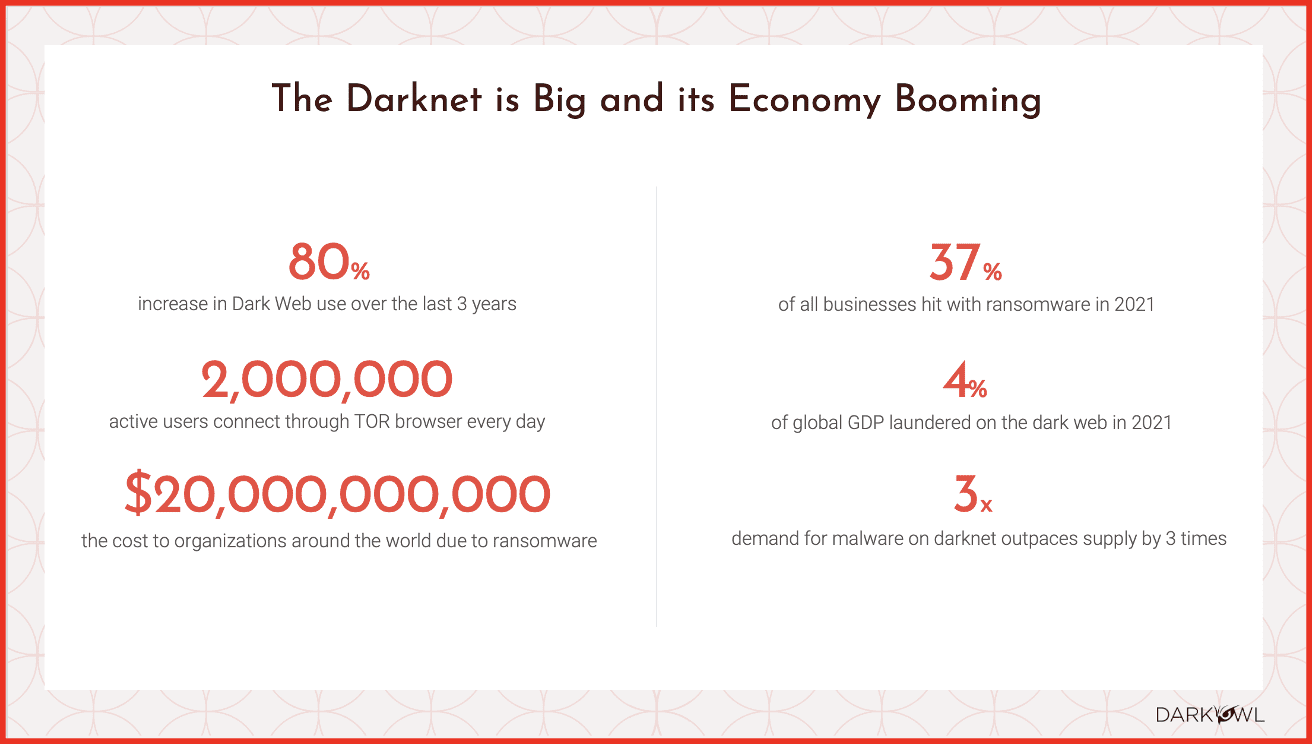
Other recent reporting from Kaspersky maintains that the most common attack vector for all ransomware attacks continues to be via account takeover utilizing stolen or brute forced credentials. The launch of Entity Explore will empower threat intelligence teams with the tools to determine when such account information has been compromised, and take remediation steps accordingly.
Analyst Feedback Leads to Entity Explore Development
Entity Explore was developed as the result of feedback from DarkOwl’s clients, who were seeking an easier way to drill into the dark web exposure and easily export that information for reporting and further analysis. In particular, a number of DarkOwl customers indicated that knowing whether or not a password was identified in tandem with an exposed email address – and having that information returned in the format it appears in its original source – would add value to what they return to their customers.
With Entity Explore, users are now able to extract data from DarkOwl’s collection in a format that has mainly been limited to DarkOwl’s API Customers, such as:
- Download or see all identified credentials for an email domain query in aggregate format, rather than having to go through individual pages to compile a list
- Identify all unique mentions of credit cards with a certain BIN
- Export results from breached data without exporting the entire context of the original dark web page – i.e. only export relevant data based on entity queries.
- Enhanced reporting functionality centered around ransomware and credential leak content
- Quickly extract all the email/password combinations for a client
- Identify and export cryptocurrency addresses for cross-referencing with other internal datafeeds
Per DarkOwl’s CEO Mark Turnage, “Today’s cybersecurity analysts have the burden of juggling a growing number of potential threat vectors that could pose a risk to their organization. Entity Explore makes it simpler to assess what information has been exposed, and what remediation is required as a result.”
Key Features of Vision UI’s Entity Explore
Like other functionalities based on DarkOwl’s Entities, users are able to explore information from the dark web regarding six distinct tokenized objects: Email Domain, Email Address, Credit Card, Bank Identification Number, IP Address, or Cryptocurrency.
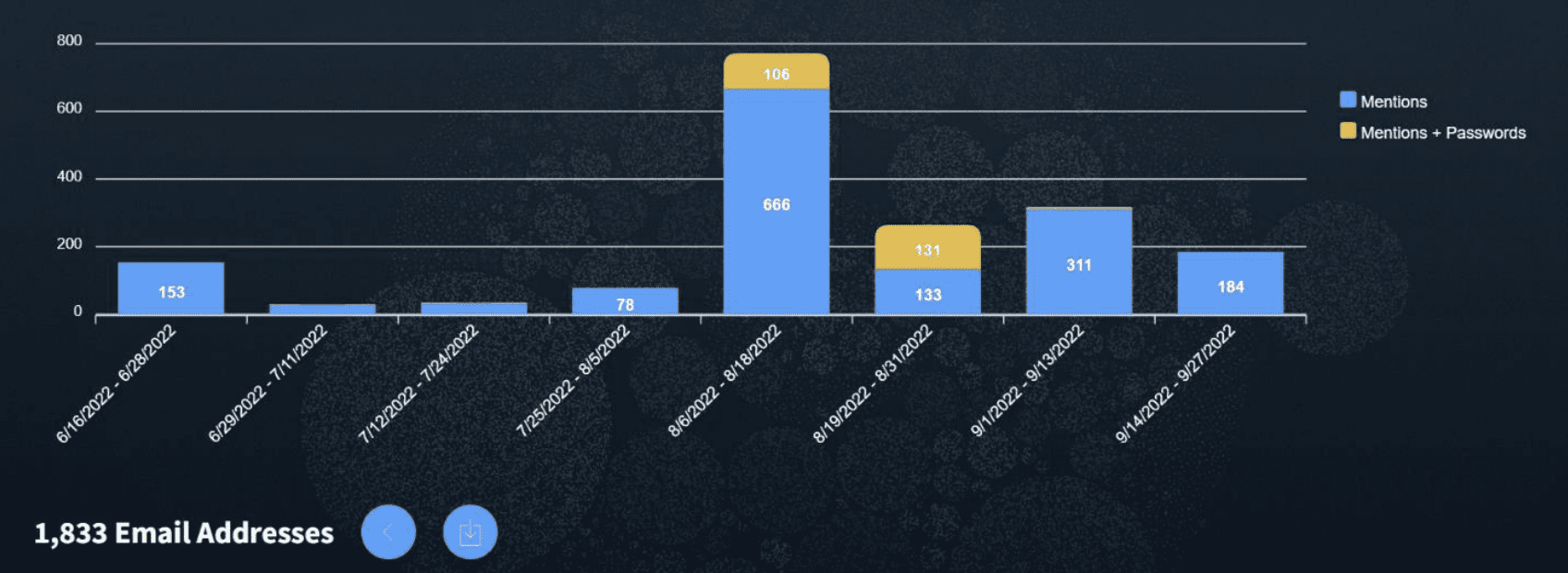
Additional highlights from Entity Explore include:
- Contextual information email queries regarding password data, such as whether a password appears and if it was in plain text or hashed
- Timeline display depicting results for the queried entity by month
- Historical look-back for queried data
- Quantity of results from identified data leaks
- Overview of source data – e.g. results for this query came from a combination of data leaks and deep web sources
- Enhanced exporting features to enable easy access to targeted or full result data
- Simplified dashboard with key information, including crawl date, email, password (if found) and password type (plain text or hashed), link to full result
- Contextual information regarding credit cards, including a breakdown of unexpired cards, cards with cvv and/or exp date, and cards without details
As of early October, DarkOwl Entity API uncovered and archived over 9 billion emails, 16 billion credit card numbers, almost 2 billion IP addresses and over 390 million cryptocurrency addresses in the past year.
More Features Geared Towards Threat Intel Teams to Come
Ultimately, the DarkOwl product team understands that our end users need an overall situational awareness of their business’ and client’s dark web footprint. Now, by adding this new explorer feature, threat intel teams can better understand when immediate action needs to be taken on specific accounts, or when they need to triage and flag other related items of importance.
For those in charge of monitoring for critical information regarding their business or their customers, having access to DarkOwl data means access to near real-time data from exclusive dark web sources including authenticated forums and emerging chat networks. For more information about our data or data products, contact us today.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















