[Webinar Transcription] Countering Illegal Trade on Darknet Marketplaces
November 08, 2022
Or watch on YouTube.
David Alley of DarkOwl FZE and Ivan Kravstov of Social Links dive into the topic of harnessing OSINT to expose illegal trade on the darknet. They outline the black-market landscape of the darknet and showcase a range of methods for fighting illegal trade and approach the topic of darknet marketplaces from different angles. In this webinar, they cover:
- The nature of the dark web and how it is accessed by users
- The functional make-up of darknet marketplaces
- User deanonymization methods
- Advanced darknet data extraction and analysis techniques
Attendees learn how to break through the perceived anonymity of the dark web and crypto transactions to identify criminal actors and track illegal trade and illicit activity.
For those that would rather read the presentation, we have transcribed it below.
NOTE: Some content has been edited for length and clarity
Ivan: Greetings everyone, today we will be hosting a joint webinar with David Alley of DarkOwl FZE and the topic will be countering illegal trade on darknet marketplaces or more broadly dark web research in general.
David could you tell us a bit about DarkOwl?
David Alley: Absolutely. It’s really great to be here and thank you to everyone for joining from all around the world. I know that we always fight the various time zones to get everyone here, so a special thanks to the Social Links team for hosting this webinar. They’ve been super helpful in getting this excellent presentation together for us.
A little bit about DarkOwl – we are American company, and our headquarters is in Denver, Colorado also known as the Mile High City. We originally started off as a cybersecurity company with a focus on penetration testing. And at that time we would do research on the darknet to see if we could find credentials to help with our pentesting work. We were really successful at that, we had a very high rate of penetrations for the pentests. We said, “why don’t we change this and actually go into being just a pure darknet company only?” That was really the birth of DarkOwl. Since then we’ve had a lot of great team members with us at DarkOwl and we’ve built a very good collection capability for us to go onto the darknet and pull out that data that is really difficult to get to.
We have a great collections team that does all of this hard work and makes it much easier for our partners like Social Links to do the next part. Which is, that once they’ve looked at that data, to make sense of it and decide what does is it mean? And how do we use it? And how do we fight crime that is emanating from the darknet?
We have a couple of claims to fame. The one we use the most is that we have the largest commercially available darknet data lake in the world. And that’s just because we have been doing it for longer than everyone else. We’ve had some very special team members over the years that have had a very unique access and understanding of the Tor Network. At one point we actually had the co-founder of Tor on our team and so it’s a really unique company. We are highly niche and highly skilled and that’s why great companies like Social Links and ours like to work together because we are complimentary. We work a lot with OSINT analysts as well, but we also provide APIs and Datafeeds for partners and that’s how we work with Social Links. I think you’re going to be pretty amazed at what the team has to show you today. I’m always impressed with what they’re able to come up with; they have a superior team. Leveraging great data from DarkOwl with great analysts from Social Links you’ll always be happy with the results. I’ll turn it back over to you Ivan.
Ivan: Thank you very much for the introduction David. A bit about us: the company was founded in 2015 we have 80 + employees at the moment with HQ in the US and EU offices in the Netherlands and the R&D office in Riga, Latvia. What we do is provide software for data-driven investigations. You can see that we have a good rating on Gartner Peer Insights and that we have received a number of
industrial awards in the past years.
Here we have a very brief slide about the average pricing of various goods on the dark web. Ranging from stolen credit cards to out of the box ransomware Trojans.

A concept that I’m sure everybody is familiar with is that there is a division into what is known as the clear web or the surface web, something which is indexed by conventional search engines, then there is the deep web which can include many different things that are not [indexed by conventional search engines] and that it takes a bit more effort to find and then there is a space commonly known as the dark web which include the Tor Network but also additional ones such as I2P, Freenet, and Zeronet.
The general principal of Tor browser network is that the traffic goes from the user through several nodes and then reaches a specific server at the end. The current total Tor network bandwidth is 400 gigabytes per second.
One of the technologies that is also utilized quite often within the platforms of communication is PGP encryption. The basic concept being that the user sends an encrypted message that can only be accessed and read with the use of a private key held by the recipient.
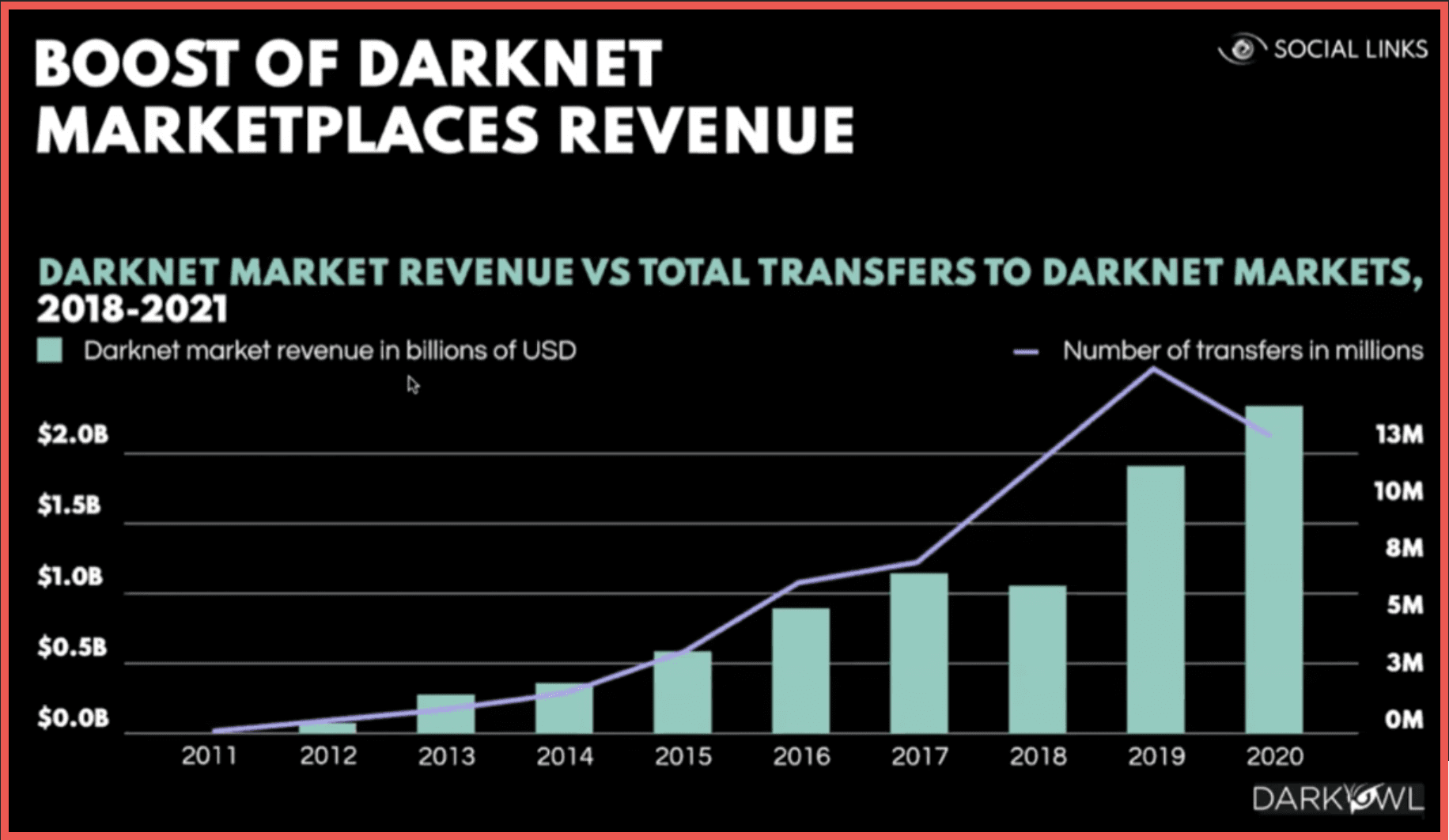
Now here we can see the boost of darknet marketplaces revenue from 2011 with the first precedent being the Silk Road up to 2020 [revenue] which is quite substantial.
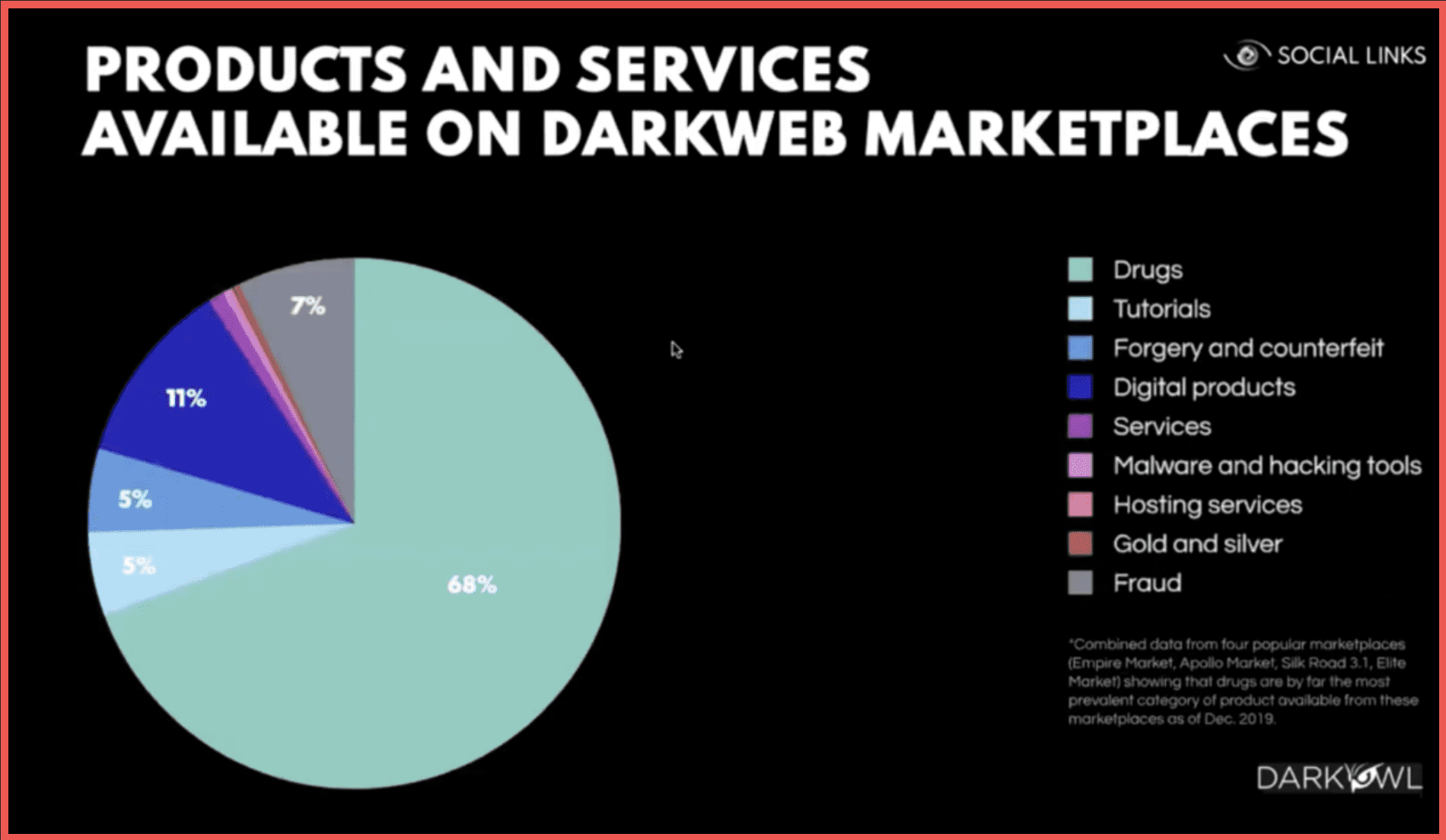
The products and services available on those marketplaces range from drugs to tutorials, forgery, various kinds of illicit services, malware hosting, and fraud. The majority of those being drugs.
The general principle of how a marketplace works is that a buyer exchanges currency for any kind of specific cryptocurrency accepted by the marketplace. Which is predominantly Bitcoin at this moment but there is a shift towards alternative ones such as Monero or Z cash. The buyer then transfers the
Bitcoin into markets account and makes a purchase. The crypto is held in the market’s ESCROW account until the order is finalized with the market taking a commission. After the finalization of the deal the vendor is paid. Then the vendor may move the Bitcoin from the market account and potentially exchange it.
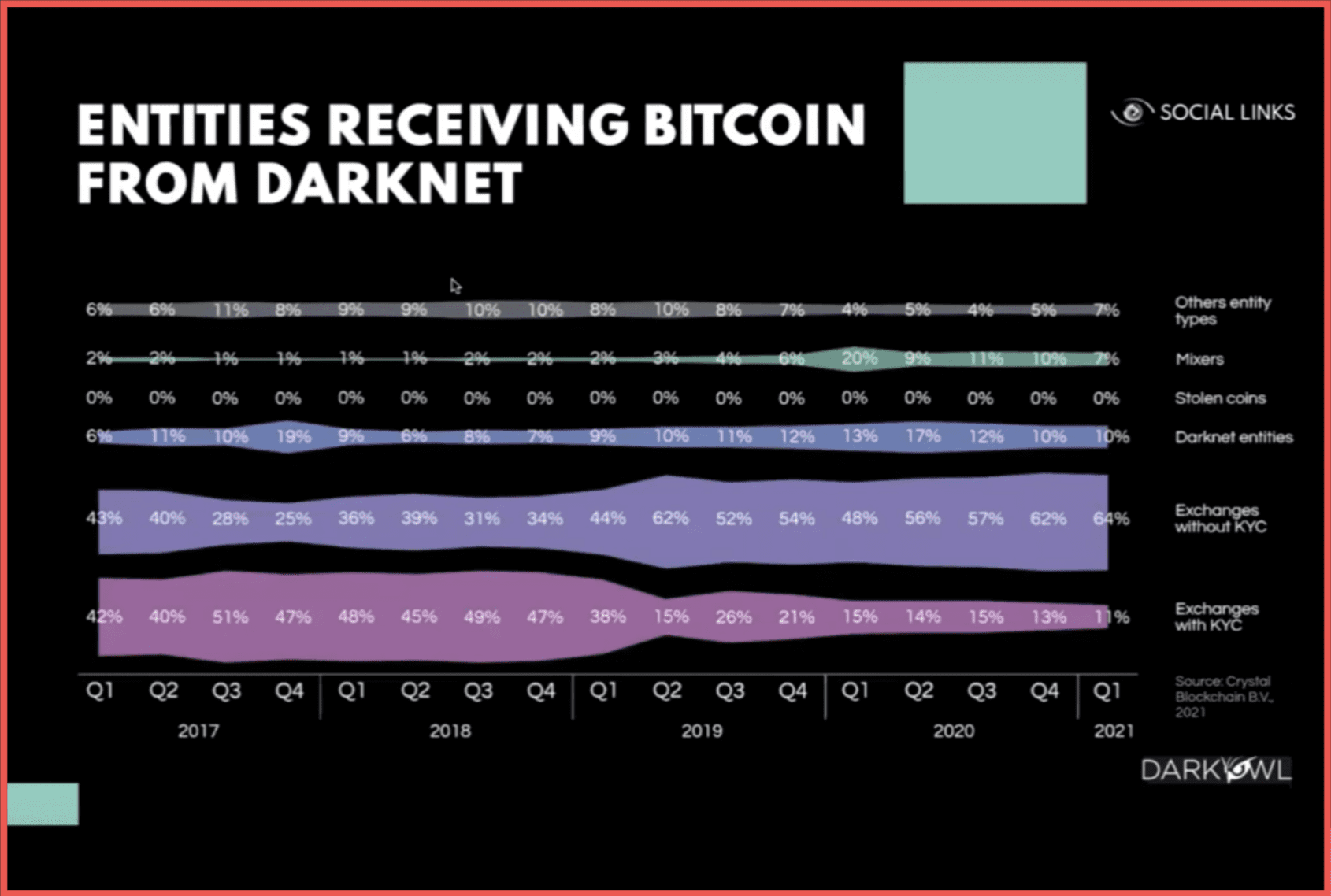
Here we see an infographic of types of entities receiving Bitcoin from dark web sources which can be KYC and for exchanges enforcing KYC or exchanges more liberal with their KYC processes. Those can also be mixing services and other entity types.
David, if you could tell us about DarkOwl’s differentiation?
David: Absolutely. As we’ve seen here we’re talking a lot about the crypto piece. And I want to talk about how DarkOwl differentiates itself and helps you with this. It is because we are able to go into these markets that we’re talking about today and were able to pull that data out for you. A lot of the Blockchain tools that you’ll be familiar with will allow you to see various wallets as they’re being tumbled and where they’ve been mixed or how they’re being exploited. But what they have difficulty doing is tying wallets to a very specific illegal activity. And that’s one of the main things that makes us different for these types of investigations. We are continuously out there crawling these darknet sites and these markets that we are in. Someone asked a question: how do we differ from our competitors? It’s just a real question of scale and scope. Many of them are in about 400 sites and we’re collecting from over 95,000 sites and about another 20,000 to 30,000 mirrors every day. It’s this massive amount of unmatched darknet content discovery that we’ve got and inside of that content is where all of these cryptocurrency wallets are which can be tied to illegal activity. You want to buy your MDMA in London? Here you go – use this bitcoin wallet or this Monero wallet.
I second the comments that we’re seeing a shift from Bitcoin into some of the other coins out there. We’ll even pick up coins in our collection that are not even on the chain yet. They’re brand-new wallets that are being used. We’re seeing that shift away from the traditional way of using the same wallet over and over to now criminals will create a new wallet put it up on the site for their drugs or their CSAM material or whatever it is they’re trying sell and have the payments into the air before the Blockchain tools can even detect them. You’ll see coins get recycled and because of our unique archival capability it goes back to almost 9 year’s worth of data. You can also do those deep investigations into darknet transactions that happened years ago. All of that together gives you the content that makes investigations very strong and that combined with the ability to do leak analysis as you can see from our Social Links partners is a very powerful tool. To give you an idea of what we actually have in the collection, it’s about the numbers.
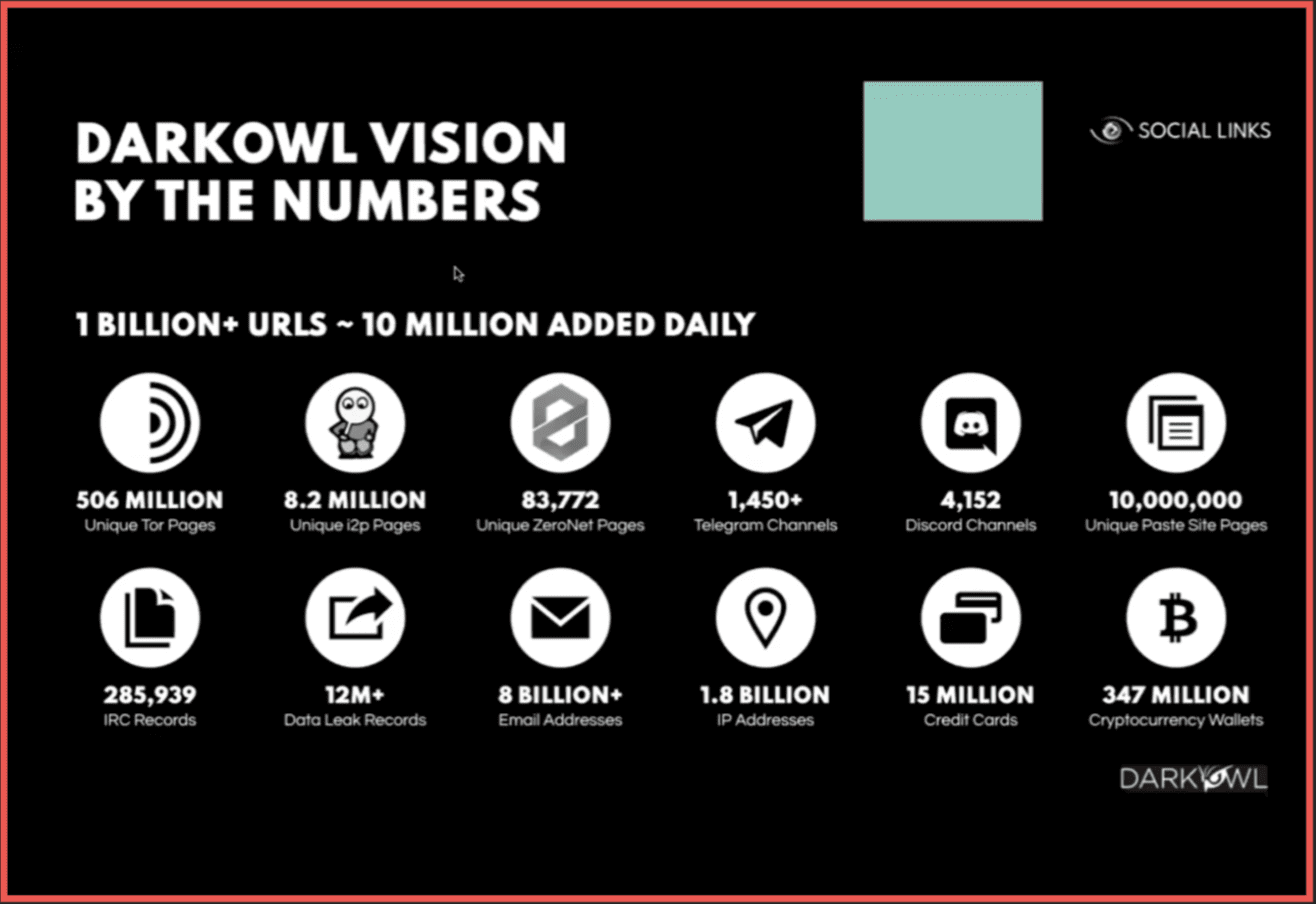
It is a lot of Tor. Tor is the largest of the darknets. We also have a very large collection of from I2P and from ZeroNet. Those are the three major darknets that we collect on. And there’s some very technical reasons behind that. We also are having a lot of success picking up cryptocurrency transactions off of Telegram channels. As we know Telegram is very popular with a lot of different hacking groups and black hat hacking groups. It’s easier to use than a darknet channel. We see that a lot of hackers are also gamers, and they use Discord for communications. We see some in paste as well. What should really be focused on [in this slide] is the lower right-hand corner. That’s 347 million cryptocurrency wallets pulled out of our darknet collection. It’s a pretty big number, and every time I see a cryptocurrency wallet on a darknet site it’s always doing something bad. I’d say it’s a 99.9% probability that if you’re using Social Links and you pull out a cryptocurrency wallet from the darknet data, you’ve already done one of the hardest steps which is identifying some form of suspicious activity. I’ll turn it back over to our Social Links partners to take you through the rest of the demo.
Ivan: It may make sense to note that with Telegram and Discord channels there is indeed substantial overlap. Much more substantial obviously then with the traditional mainstream social media platforms. Telegram and Discord aren’t really called social media, but they have a significant social networking element. Telegram especially in the past few years. It is about cybercrime groups but also apart from that it could just be local, regional, or even macro-regional drug vendors. It could be people engaged with child grooming, especially on Discord, or extremist groups as we previously covered in one of our webinars with a German expert on extremism research. Now we will go into the actual examples that we have.
First we should dedicate a few minutes to talk about the method of dark web research. In this case that would mean focused on researching an individual. It makes sense to use all of this in conjunction.
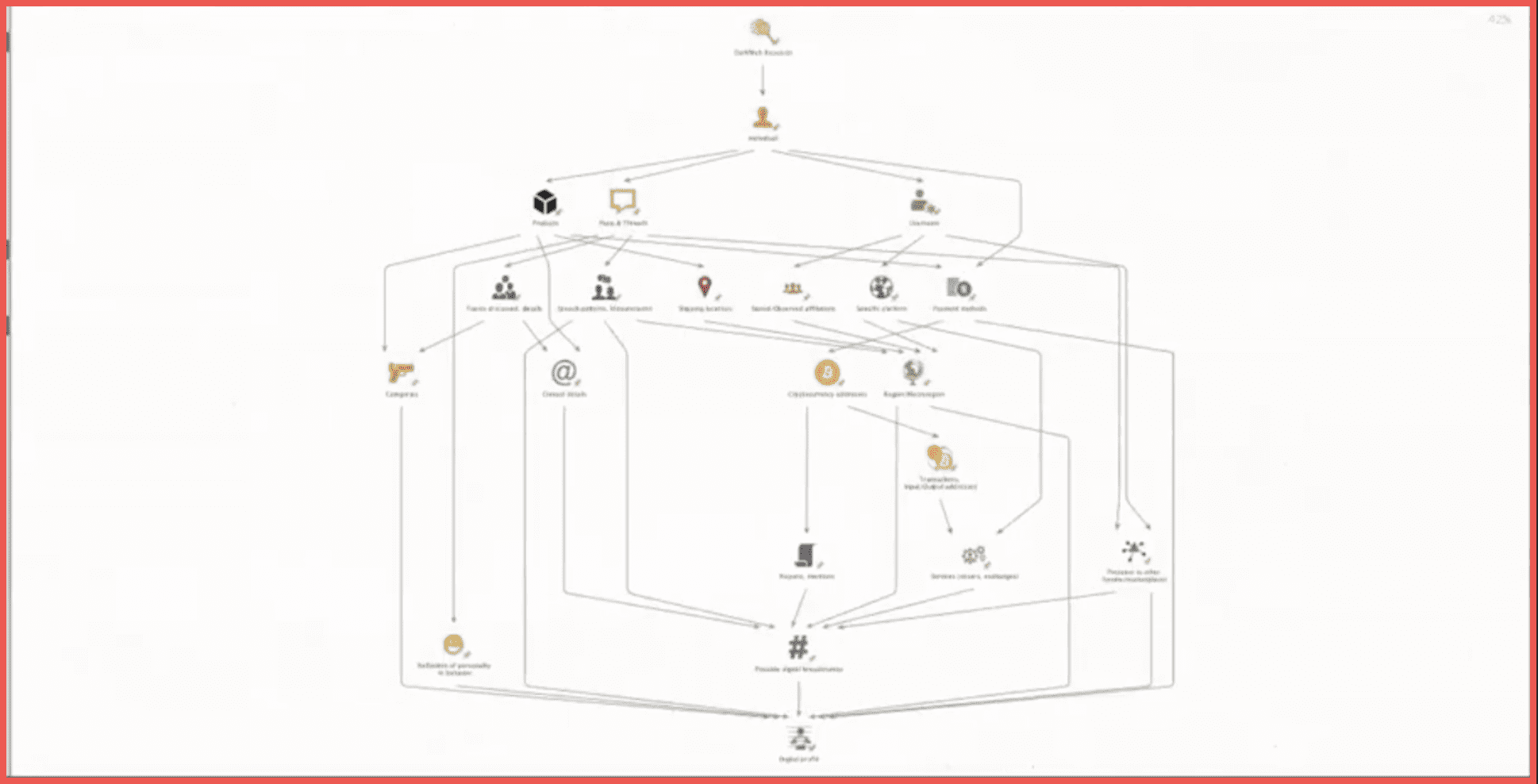
From the username we can get the specific platform within this interface where the vendor or forum member is present. That can also give us insights into their stated or observed affiliations. Those are the payment methods, the posts and threads and the products. From the posts and threads you can examine the topics discussed in the details which can also tell you more about what exactly they are doing, what kind of merchandise they are dealing in, what kind of categories, and if they have a specific focus. As well as the speech patterns of the idioms and idiosyncrasies used by the individual and the shipping locations. And of course, the products also tell us more about the proper categories and sometimes product cards can contain contact details within them. Objects within this schema such as the speech patterns, the stated shipping locations of the products, the affiliations, and the specific platform can point us to assumptions about a certain region or macro-region.
For example, there is a higher probability of a vendor or a forum member on an Eastern European marketplace to be from somewhere in Eastern Europe. Payment methods can be different as well as various types of e-money, but here we’ll focus more on cryptocurrency addresses. A transaction derived from an address can tell us about the interactions it has with other addresses for groups of those. And it can tell us about the services that they are using such as mixers or exchanges. A mixing service may also have theoretically some kind of interactions in some kind of partnership program for a specific marketplace. They can also be mentioned in various reports or forums. All of those can possibly lead us to digital breadcrumbs, and that in conjunction with the assessment of the presence of the user in other forums and marketplaces and the way their personality may be reflected in their online behavior and the kinds of merchandise that they are dealing in and the kind of payment methods that they’re using is all part of an attempt to create a digital profile of an individual.
Now here we will start with the first example where we will go from an alias. We will run our first transform search for users under this alias. Here we can see some details in the properties, one of those being the side name Tochka Market. “Tochka” is a Russian word standing for point or place. We search for the products related to this vendor and we also extract their PGP open key which is quite often used by vendors. Next, we will use the products and extract the locations they are to be shipped to and from.
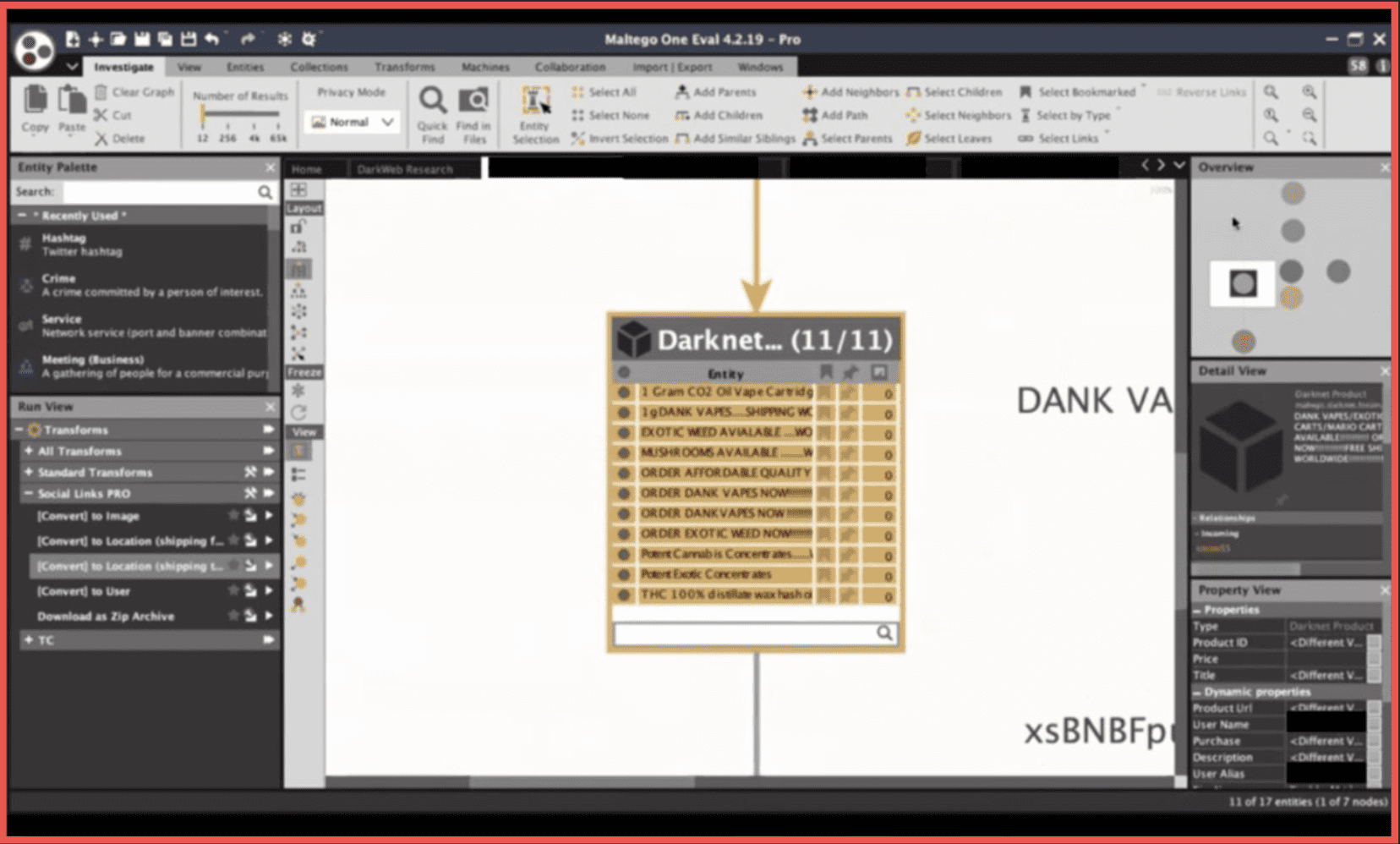
We can see here that those are mostly recreational drugs shipped to the United States. From a PGP open key it is sometimes possible for us to go to the email address. Not in a hundred percent of cases, which can also be said about some of the other methods that we will be applying here. Here we see a Gmail and from that we can further try to see if there are any social media profiles and any accounts connected to that email address. There is also the possibility to get reviews if it’s a Gmail account. We can see that there are accounts within Facebook, Firefox, Gravatar, Pinterest, Samsung, and Twitter connected to the email and we see several profiles within Gravatar, LinkedIn, and Skype from which we can extract additional details. In reviews we also see a cannabis dispensary seemingly located in the United States and a bar in Cameroon which matches with the location that we see here within the LinkedIn account [redacted account name] connected to the Gmail address. There is also a post promoting the sale of marijuana on a surface web source stated by the account holder to be safe and secure. Now here we can use some of the Maltego functionality to go into more data about that specific domain. The WHOIS data gives us the name of [redacted name] as a registrant and the company name [redacted company name]. [Redacted names] are both something that we have seen within the social media footprint derived from the email address. Now of course an analyst won’t be as lucky as in this instance in 100% of cases, but this is real data related to a real individual. It is possible because people do tend to make mistakes.
Now we will go through another alias. This [alias] gives us 4 accounts with the same username and it’s something that vendors to do to maintain a commercial reputation with the customer base. Now we can ask for specific platforms. We can see the Dread forum, the Hub forum, the Apollon market, and the Wall Street Market. Now we also see a single PGP key used by three out of four of those accounts and we will further ask for the posts and products. We can see that there is a certain focus on Europe. In this instance the goods are more likely shipped from Europe to locations worldwide. The principles of working with the posts are similar to the way a user of Social Links Pro or a SOC tool in general can work with social graphs. The graphs of social interactions within the digital space. From each of those we go into the thread. From the thread we can go to the other posts within it, and the other users that have been participating in those conversations.
This is just at stage of gathering data and an analyst working on a real case will of course face the necessity to analyze this communication in depth. That’s why there’s a capability here to download the content within those posts and save the text content as a text archive. Now here we see a Proton mail account- [redacted email address] so they seem to be more conscious about their digital footprint and security, but potentially we can try to search for this alias in the social media platforms available. Here we’ll try with an Eastern European platform because [redacted name] [the alias] is obviously a reference to the famous assault rifle. Here we got an account with just the cat as a picture under the name [redacted name] and while it’s not something that we will state and something that we will accuse this person of, it could be a coincidence or it could not be a coincidence. The account is not very informative, is closed, and has a profile picture of a cat. So here we are less lucky than in the first example. In some instances it’s even more obscure. Here we see an individual with the alias [redacted name] focusing on the European Union. They have two email addresses and a statement in the product description that there is a possibility to contact the vendor on Discord. We see that there is a Discord account connected to their Proton mail address, and also a Skype account which states the location as Germany. This is all on the level of analyzing people and individuals or small groups of people, because several individuals can be behind one username.
This can also be done on a macro level. We can take several capital cities or countries within a certain macro region such as Asia-pacific or Latin America and run a search into the full spectrum of dark web sources available to us to see which products are shipped to and from those locations. Here we see that some countries have more activity within the spectrum of available sources, some countries have less, and we can potentially look for vendors that are focused on two or three specific countries at once. We can also see which marketplaces are more active within a given region. Here and in Latin America Tochka market is quite active. Additionally the Apollon and Nightmare markets and then several other ones have much less activity.
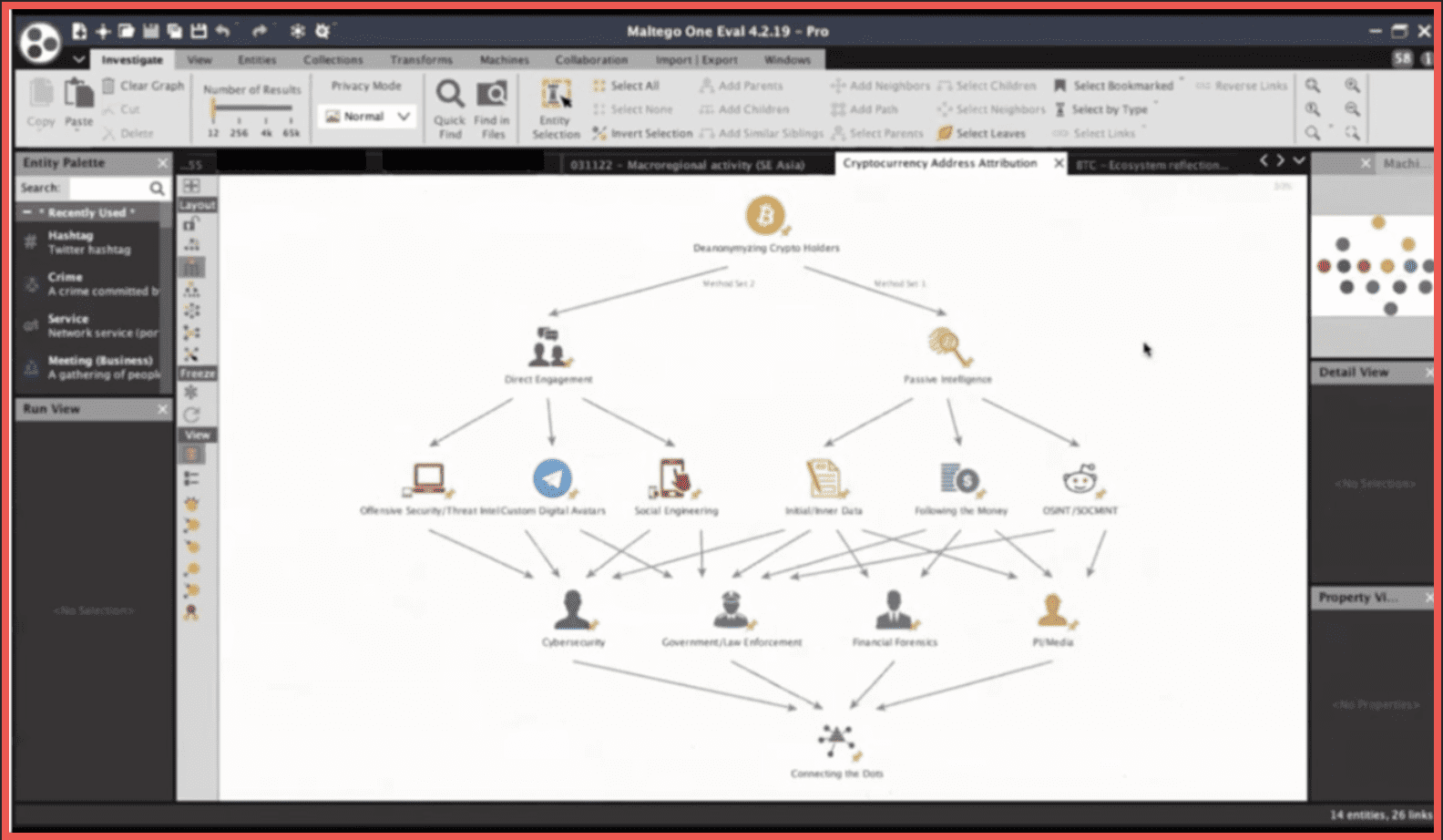
Now of course it makes sense to talk a bit about the cryptocurrency aspect within dark web research. Several of those graphs are something that we’ve shared previously in some of our previous webinars. The methods can be split into two sets: passive intelligence and direct engagement. Passive intelligence may include open-source and social media intelligence, the traditional following the money approach, and the enrichment of the initial entered data that the analyst or potentially a victim of a crime may have. Direct engagement is something that implies using custom digital avatars for social engineering and also in the case of enterprises, or state organizations, offensive security procedures or threat intelligence. Some of those methods are more customary to certain kinds of professionals, analysts, and organizations than others but in the end as is the case with any kind of investigation it is all about connecting the dots, the seemingly not connected entities in a broad sense that word.
Here is a small reflection of the situation within the Bitcoin ecosystem. There are a number of addresses here, some of those belonging to militant extremist groups such as the Palestinian Al-Qassam Brigades or Hay’at Tahrir al-Sham the fellowship operating in Syria. Some of those belong to dark web vendors such as Ross Ulbricht of the founder of Silk Road. Alexandre Cazes founder of Alphabay, or the administration of the Wall Street Market that exit scammed in 2019. Some of those were because of law enforcement, some of those were ransomware groups, and some of those were to legitimate exchanges.
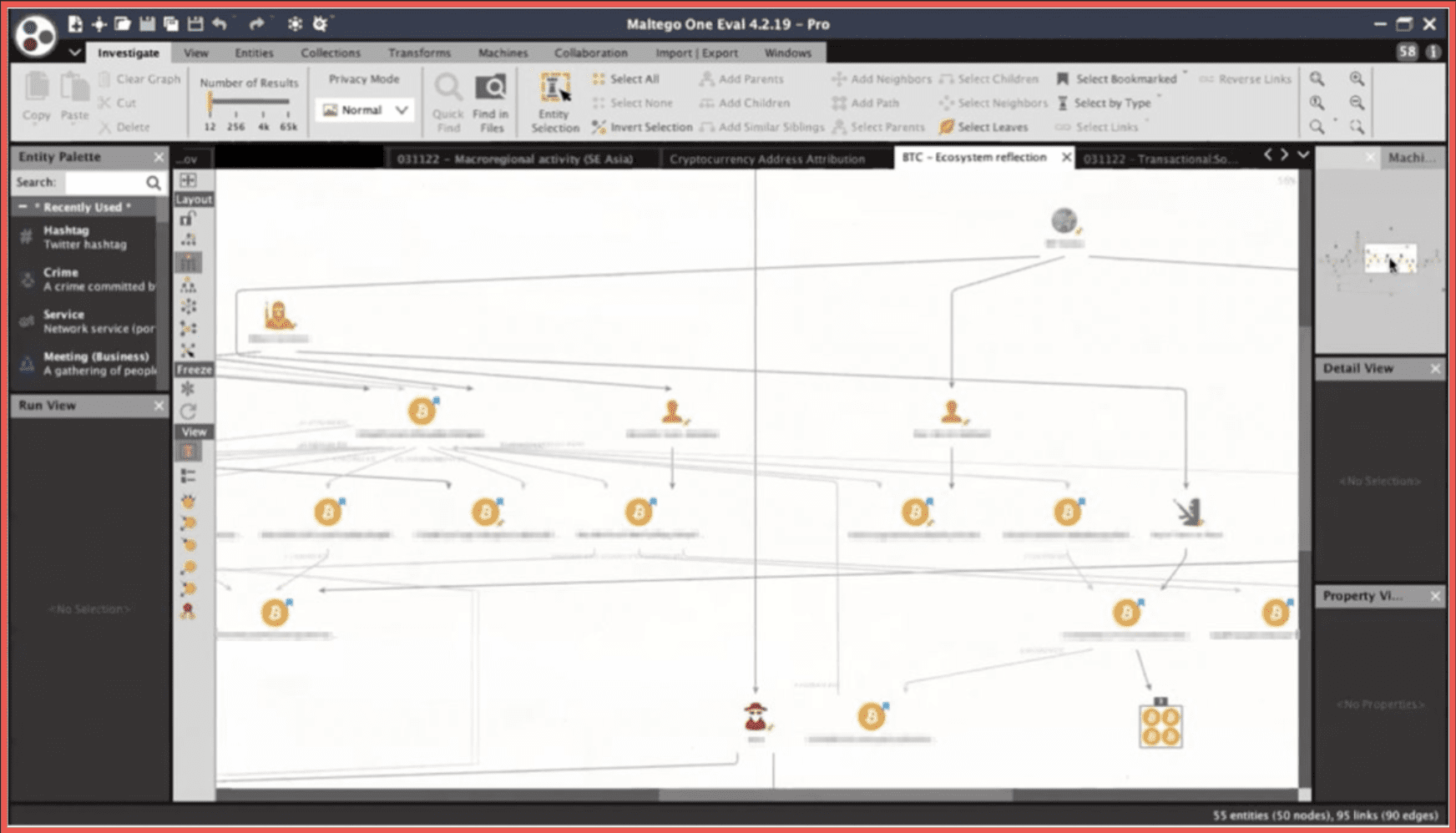
A way to perform this attribution to be 100% certain that a specific address belongs to a specific individual or a group is to run searches into the social media and dark web space and also into data that is provided by vendors such as DarkOwl And I must say that DarkOwl provides fascinating amounts of information of fascinating depth, and a number of these were done with the help of DarkOwl as well. Social Links is focused specifically on the Tor Network while DarkOwl, as David has mentioned, also pulls data from other sources such as I2P and Zeronet. Once you get this kind of entity you can further run the transform to get to the details and then examine the contents of those entities. The source of the networks and the date and time are also stated within the properties.
Here we have another simple example of building a timeline with the timestamps from within the transactions related to a specific address and the timestamps of the mentions of that address on a dark web forum.
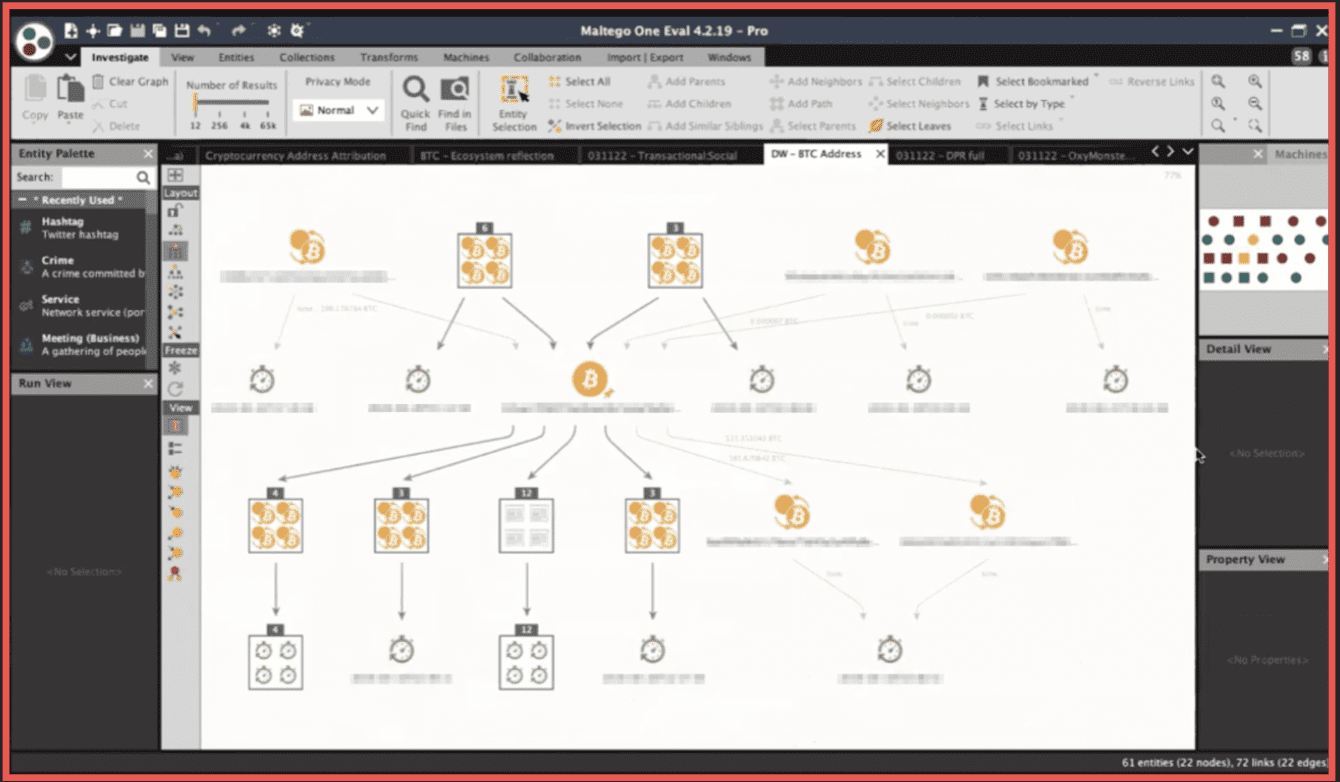
All of this above is related to the situation around the exit scam performed by the Wall Street Market administration. You can see that all of the transactions and all of posts take place in the second half of April 2019.
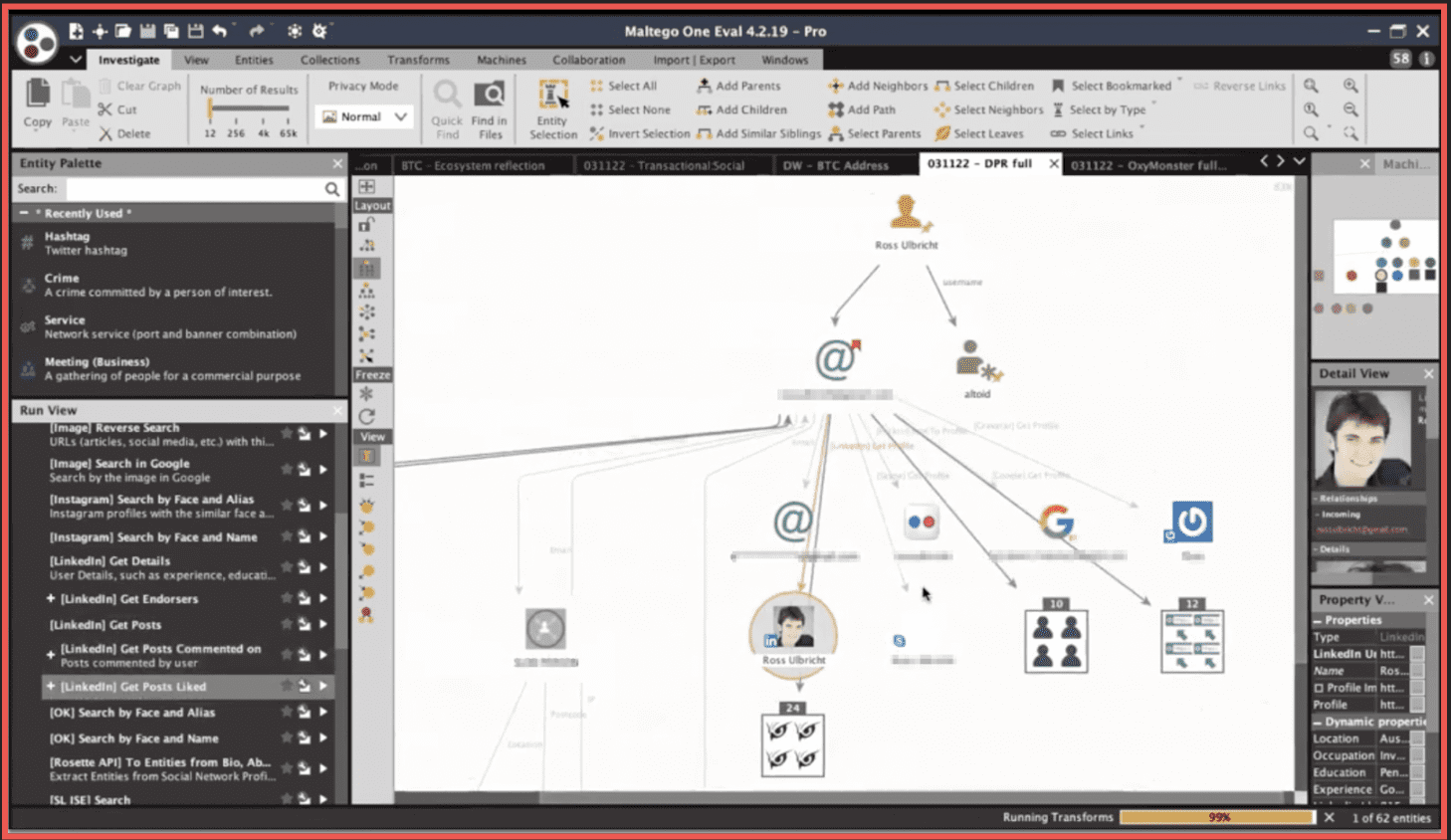
If we talk about profiling, there been there are a number of quite famous cases that have been solved by law enforcement and by analysts within those types of organizations related to de-anonymizing an owner or a senior administrator of a dark web marketplace. There is the famous Ross Ulbricht who was using the alias Dread Pirate Roberts and a clear web alias Altoid which was the key thing that led the American law enforcement towards then. We can gather the different data from the full spectrum of sources or potentially we could very carefully try to profile the individual based on the way they interact with the customers, the way they interact with vendors, the way they behave online within the platform. Or we can try to profile those people in retrospect to see what is common between the individuals who have been involved in such activities that have been uncovered historically. We can see that the portrait of the criminal has changed over time to this day in 2022. All of those –Mr. Ross Ulbricht, Mr. Gal Vallerius and Mr. Alexandre Cazes are educated individuals in different fields. For instance, Mr. Cazes has a degree in computer science. They tend to share certain views such as being Libertarian. Libertarianism was something very much associated with the motives of the founder of Silk Road, but similar motives can be speculated about other members of that community. In the case of Mr. Alexandre Cazes, the key input was an email address that was a source of messages to newcomers within the Alphabay Marketplace which was 10 times the size of Silk Road at its peak. The support emails were to new vendors and new members.
Here we can try an example of enriching that identifier to build this graph from scratch. This can be done with the help of something called a machine within Maltego which can automate those queries under a specific logic.
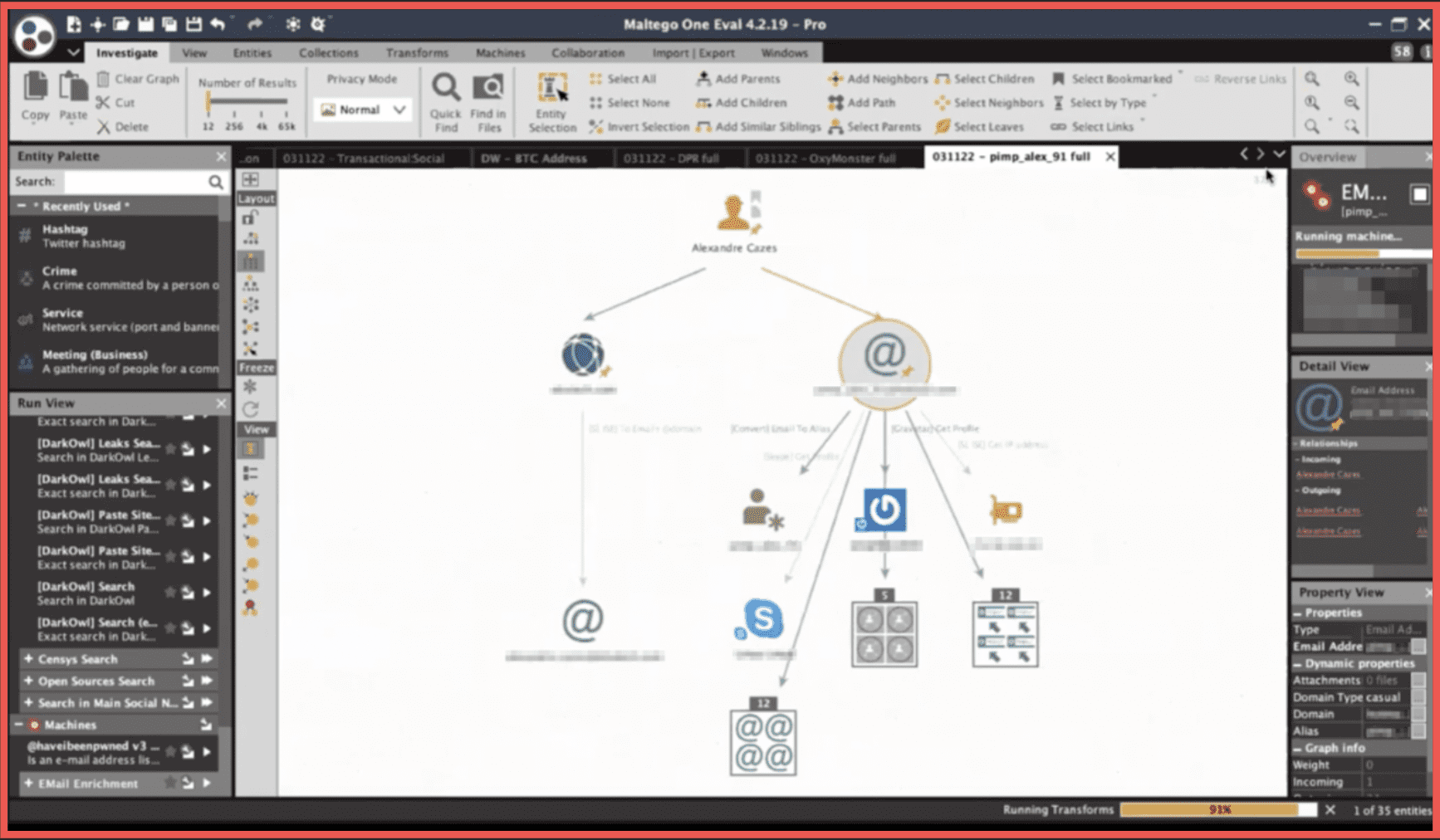
Here at this moment it gives us an IP address from a leaked database, it gives us an account on Gravatar –[redacted account name] an account on Skype, and a number of email addresses with similar passwords. And also a number of additional database records that contain the email in the string. The IP address is further resolved into a Canadian netblock and that is resolved to an autonomous system number. Now we can try to do the same with the second email that we have here. This is giving us two Skype accounts and two additional IP addresses. Of course, we can run a search into the data lake of DarkOwl. From which we will try to extract additional details. Here this gives us the family name, it gives us the name of another individual, and a number of IP addresses and phone numbers. The IP address issue may be just a minor technical problem on the side of Social Links with integrating this, but you get the point. This gathering and structuring process is something that is done in retrospect, so this person has already been uncovered, already been arrested, and already committed suicide while in jail. But I think it’s obvious how beneficial industrial automated tools such as DarkOwl and Social Links can be in researching such individuals and investigating and doing criminal intelligence within those types of sources.
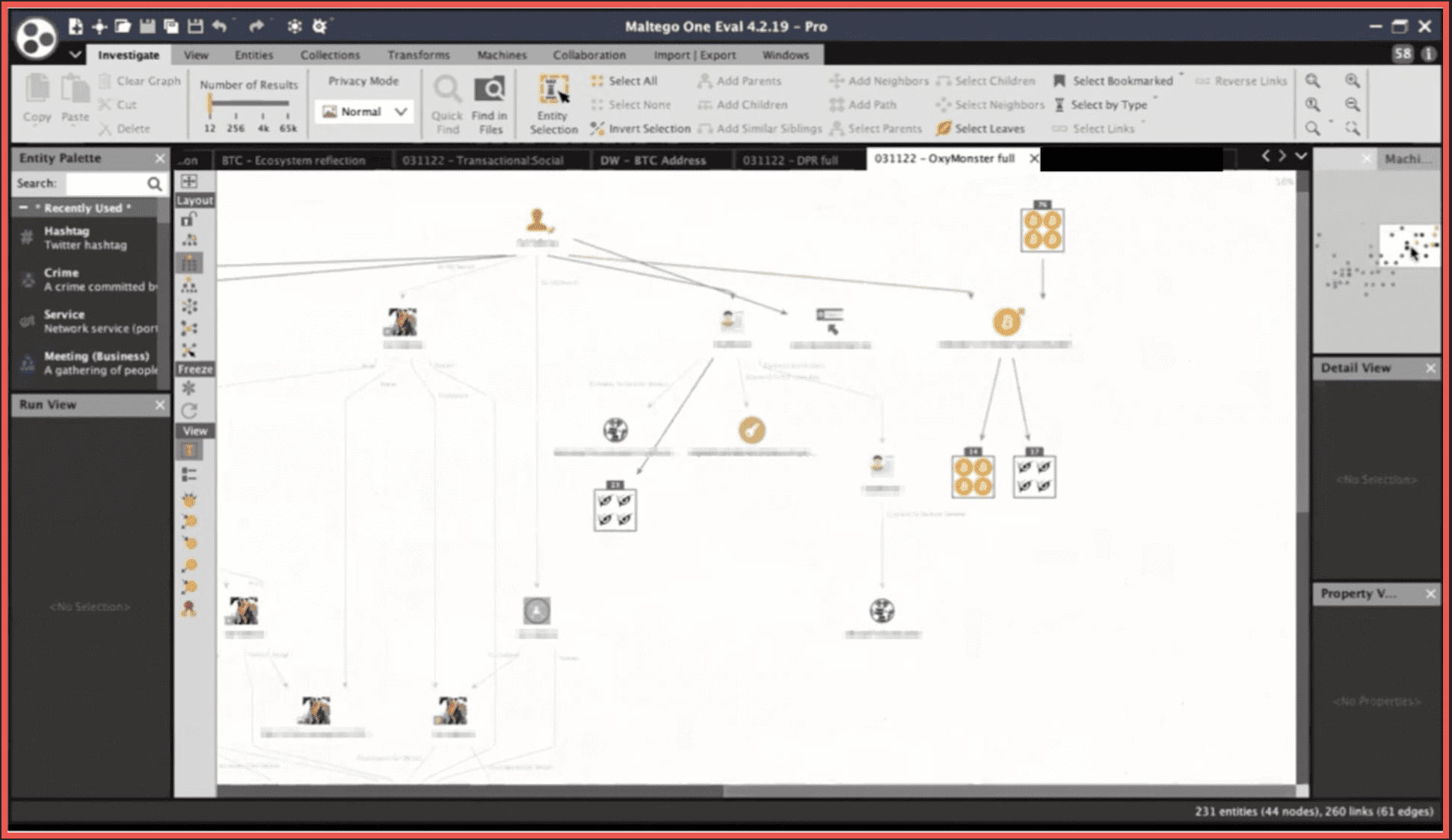
With Oxymonster, the alias that belonged to Mr. Gal Vallerius an Israeli-French individual, the initial input point that investigators had was this vanity Bitcoin address for which they traced output, a number of outgoing transactions to a number of addresses all leading to an account on a peer-to-peer platform [redacted address][.]com under the username Vallerius. That is exactly what we were talking about when we said speech patterns and idioms and idiosyncrasies. The investigators further compared the speech of Mr. Gal Vallerius on Instagram and Twitter accounts that are no longer in existence but we do have a Foursquare profile here with that of the user Oxymonster and there was a certain match in the patterns. Now here we can extract additional things from the DarkOwl entities that we have as well.
In another example with an email of Mr. Ross Ulbricht which was found from one of the posts on the Bitcointalk forum which was initially found a by matching the username Altoid with the first-ever mention of the Silk Road marketplace on [redacted address].org. We can also try to use those transforms to see what is connected to those identifiers.
Here we go to what is more commonly associated with Social Links. Social Media intelligence is our strongest side so far even though we’ve diversified the sources that we have and the methods available for them in the standard procedure of mapping out the digital footprint of an individual. If we return to the initial logical schema of those processes it is a necessity not just to focus on the user account or on the group or on the marketplace within the Tor Network or any of the other darknets. The process of investigation and analysis will take the analyst, if they’re lucky of course, into other kinds of domains which may include conventional social media.
There is another instance for a potential use of OSINT tools in a similar scenario, but it would make sense to use in the case of the Berlusconi Market and their administrator John Kohler Racino . The way that they were uncovered was something far more in line with the traditional work of law enforcement. They were eventually closed down as a result of the operation by the Italian Guardia de Finanza, but it was the result of operatives having ordered number of goods from the marketplace as part of an experiment and having noted that they all came from the same post station from within a small town in Italy. Here we see an example of what can potentially be found from the usernames and the accounts under the usernames that were operated by Mr. Lucino. There are two of them: one that had presence in the Dread forum and was involved in discussions around the Berlusconi Marketplace and another one on several marketplaces including Berlusconi, two of those sharing a single PGP open key with the pattern of the goods being shipped from Italy worldwide. There is some output from the Social Links identity search engine that also gives us a number of email addresses and IP addresses. Operations such as this can be advanced with the use of DarkOwl.
That is all of my part so far with the functional demonstration of the capabilities.
Another topic which we haven’t really focused on today but which is quite relevant here is the usage of those kinds of tools and the exploration and the research by professionals in the field of corporate security. The cases that we’ve shown now –they’re somewhat more in the domain of law enforcement work and criminal intelligence analysts, but the monitoring of sources, aggregating leaked databases, data breaches, are also a topic relevant to the practice within the corporate sector.
How we use those tools to detect human trafficking is a very good question and there is an organization that we have done a webinar with previously called the Anti-Human Trafficking Intelligence Initiative with very brilliant people working in that area. They have a solution of their own that works by a slightly different principal than Social Links and DarkOwl, but yes such solutions do exist and such practices do exist and they have been successful uncovering numerous instances of human trafficking and the distribution of CSAM.
David: Absolutely. Ivan, I just want to jump in and congratulate you on a really excellent presentation. As far as the human trafficking pieces, we are seeing a growth in the kind of communications and coordination that happens on the darknet for human trafficking and even more broadly for the CSAM types of materials. I would like to talk about one of the other questions that has been brought up, and it talks about the companies that have been involved in ransomware incident response. The amount of chatter that we see happening on the darknet for the different ransomware gangs has increased exponentially over the last two years, and we’ve tried to focus on it for quite some time. We’ve really seen how well they have taken their software to market. You can see that ransomware as a service programs have been proliferating widely through markets on the darknet. As far as identifying specific ransomware families, I think we have about 30 or 40 of them that we’ve already curated. Including what cipher they are using, when we first saw them appear on the darknet, and you can use it to gather some of the pricing data that you need.
Ivan: Thank you for that David. One thing that is easy to see even from this simple graph which is just a reflection of the current state of affairs in the cryptocurrency industry and specifically in the Bitcoin ecosystem is that it is very Wild West-esque at the moment. [There is] the obvious pattern of large a number of interactions with people involved in terrorism and ransomware and the trades in illicit goods in the dark web space and human trafficking and CSAM as well, although those two categories are not reflected here. The people at the Anti-human Trafficking Intelligence Initiative know much more about that topic. Interacting with legitimate exchanges such as Binance, Gemini, and Coinbase.
David: There’s a question from Andrew and it says: do DarkOwl and Social Links have the tech to crawl the deep and dark web? Almost all of our collection is technical-automated. There is a combination of techniques that you use to gain access, but then you cannot collect at scale just using human beings so it’s a combination of both. We use both for this kind of collection. Then there was one question about risk management targeted profiling and Customs control. Absolutely, specifically for the for the drugs portion…most of drug shipments that we see happening on the darknet are international transactions. The largest shipper of drugs worldwide is the United States Postal Service because it takes a federal warrant to get into a box being shipped. We see some law enforcement agencies do controlled buys. They use these tools to identify who the vendors are, how do you enter and interact with them, and it’s about the speed – how do you get ahead of this and then do controlled buys. When it comes into your country you will figure out which one of your Customs agents is taking bribes from people to let those packages in. It’s both useful for looking at criminal activity and also from an internal counter-intelligence perspective.
Ivan: Thank you David and thank you for visiting we are always glad to see you here.
David: Andrew we don’t leave you hanging out there I see your question, you’ve asked how they might go seize the ransomware payments. I don’t have any direct knowledge of how that happened, but most of these payments have to go through some form of exchange to move the money around and they likely had access to one of those exchanges that could tell them. Because remember there are some exchanges that are working with and cooperating with law enforcement and international law enforcement agencies and if they get a valid warrant from a law enforcement agency to block the transaction, they can do that. Just like it would work in the international Swift system for blocking bank transactions through the Federal Reserve Bank of New York. I would imagine that probably something like that is how it was done.
Ivan: Yes, I actually think there was an Eastern European mixing service there.
This is it on our part for today thank you everybody very much for participating and we hope that you will contact us to talk with us further about how our solutions can be implemented into your business processes. We will be very glad to see you and will be expecting you on our further webinars that are to come. David thank you for co-hosting.
About Social Links
Corsha is on a mission to simplify API security and allow enterprises, developers, and DevSecOps teams to embrace modernization, complex deployments, and hybrid environments with confidence. Our core technology is dual use, designed for widespread adoption, and easy to configure and deploy to both commercial and government customers. Corsha has a strong engineering team with deep expertise in distributed ledgers, cryptography, security principles, orchestration technologies, and software design.
About DarkOwl
DarkOwl uses machine learning to collect automatically, continuously, and anonymously, index and rank darknet, deep web, and high-risk surface net data that allows for simplicity in searching. Our platform collects and stores data in near real-time, allowing darknet sites that frequently change location and availability, be queried in a safe and secure manner without having to access the darknet itself. DarkOwl is unique not only in the depth and breadth of its darknet data, but also in the relevance and searchability of its data, its investigation tools, and its passionate customer service. Our passion, our focus, and our expertise is the darknet.
Interested in how darknet data applies to your use case? Contact us.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















