[Webinar Transcription] Cowbell x DarkOwl: Into the Dark with a Flashlight
October 14, 2022
Or, Watch on YouTube
DarkOwl’s Chief Business Officer, Alison Halland, the Director of Strategic Alliances at Cowbell, Jessica Newman, and Cowbell’s Director of Risk Engineering, Manu Singh, sit down and discuss the building blocks of the darknet and organizational risk, what darknet data exposure means for small to medium sized businesses, how Cowbell uses DarkOwl’s darknet data to generate a dark intelligence scores for each of their policyholders. They also dive into the value-add of a Cowbell policy to their policyholders provided by Cowbell’s free reports from their risk engineering team utilizing DarkOwl’s darknet data to assess and mitigate cyber risk to businesses.
For those that would rather read the presentation, we have transcribed it below.
NOTE: Some content has been edited for length and clarity
Jessica: I want to welcome you all. We are really excited to have you on behalf of Cowbell and DarkOwl. We are here today to talk about the dark web, which is hopefully an interesting and fun topic of conversation. From what we hear, everyone typically perks up when the dark web is mentioned. It’s a topic that gets a lot of questions and a lot of interest. Our intention today is to arm you with enough information about the dark web and about how Cowbell uses the dark web to feel comfortable talking about the dark web with your customers.
Quickly I will introduce myself, my name is Jessica. It’s great meeting you and being with you today. I run point on our cybersecurity partnerships here at Cowbell… I’m going to let our panelists introduce themselves. We’re really excited to offer their expertise to you all today. Alison do you want to start by introducing yourself?
Alison: Absolutely. I’m Alison Halland with DarkOwl, and we’re based in Denver Colorado. I’ve been with the company for over 6 years and we are Cowbell’s darknet partner. We provide our darknet data to Cowbell and it’s been a great partnership. I’m excited to be here talking to all of you and hopefully you can walk away with a little more information about what the darknet is and how it can be helpful as you talk to your clients looking at getting policies.
Manu: Thanks Alison, thanks Jessica. Glad to be here today. I’m Manu Singh, and I’m the Director of Risk Engineering here at Cowbell. My team assists our policy holders through our continuous risk assessment process. That includes understanding our Cowbell cyber platform, our Cowbell factors, understanding how our AI and machine learning scans are used to develop insights and recommendations, as well as some of the data that we add off the dark web thanks to the assistance of DarkOwl. My team— ultimately our goal is to reduce the frequency and severity of data breaches and cyber incidents for our policy holders. We certainly do that by generating our dark web data reports, and again that is with the assistance of the data that DarkOwl is providing for us.
Jessica: Awesome. I want to kick things off. We’re going to have this be as interactive as possible so please feel free to ask questions, utilize that chat, if questions come up we want to make sure that we’re answering them. I want to kick things off with a question for those of you who are joining us today: I want to understand if the dark web is a topic is of interest to your customers today. Is this something that comes up a lot or do you see [the dark web] as an angle that you can use when you’re selling cyber insurance? There’s a question up there now: How confident are you at discussing the dark web with customers? Do you feel very confident, neutral, or that this is totally new to me? I’ll give you a second to place your vote…. there are some results showing that people are pretty neutral. This is actually really good news. My hope was that you don’t feel very confident in discussing dark web and that you’ll leave today feeling much more so. That gives us a really good place to start from.
Alison I’m going to kick it over to you if you can give our audience a quick overview of what is the dark web. I think having that basic understanding of what it is and what happens there will help us understand how we can then talk to customers about it.
Alison: Excellent. So as Jessica said let’s step back and define the darknet so that you all are all operating under the same kind of information. At this point in time it’s a buzz word that we’ve all heard, especially if you’re paying attention to media or newspapers. It usually comes along with an image of someone in a black hooded sweatshirt with all sorts of code in the background. I want to unravel that a little bit and talk through exactly what the darknet is.
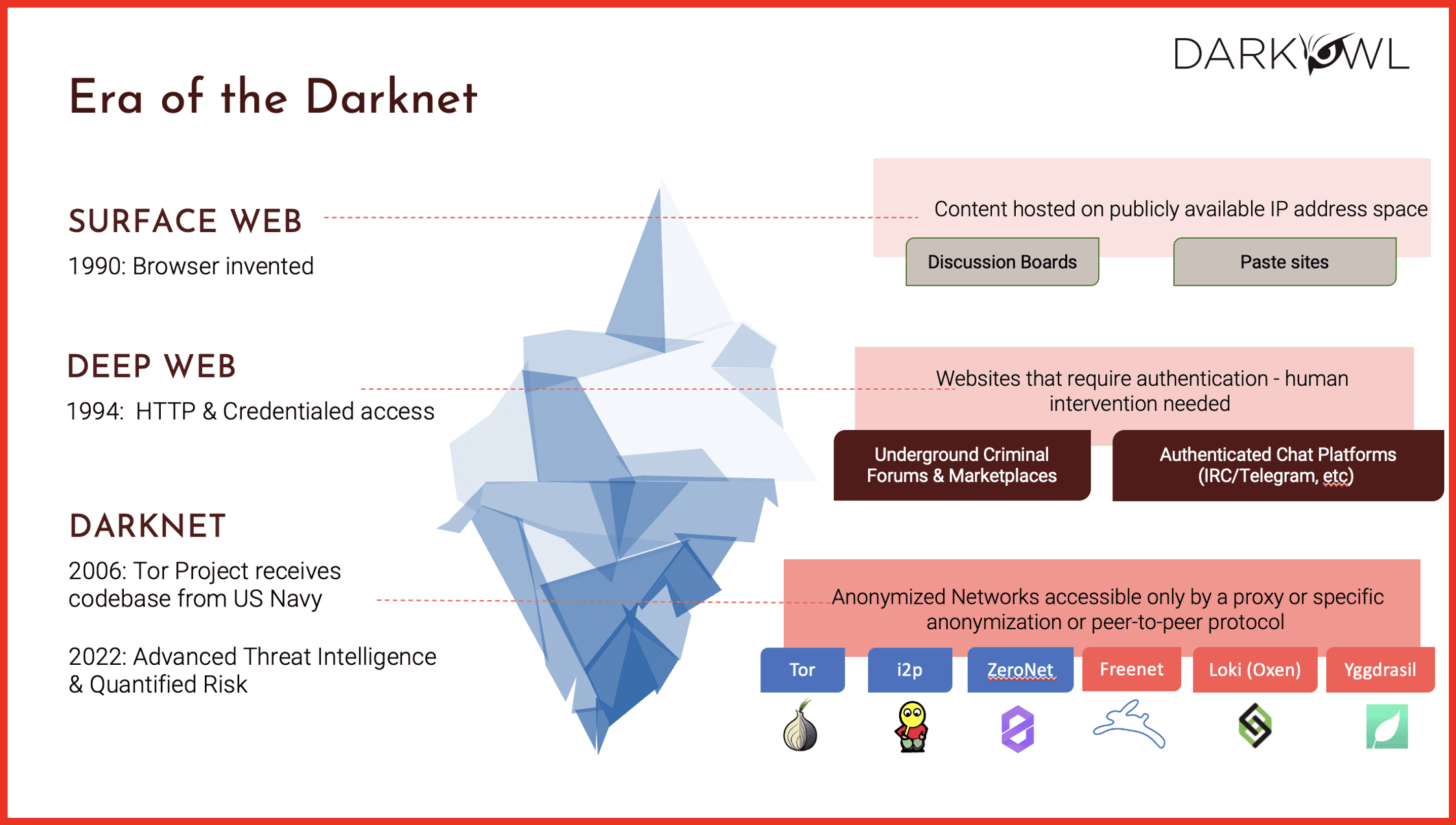
We at DarkOwl consider the surface web to be anything that’s indexed by a search engine. Think about when you open up Google, you put in a search term, you hit enter. All of those results are by definition the surface web. They are indexed and you can click on them. And interestingly despite hundreds of thousands of results coming up on Google that only represents about 5% of the internet. Hence the iceberg analogy this is the tiny piece that is above the surface of the water.
The deep web makes up essentially the other 95%. The deep web is nothing scary or dangerous. In fact, I guarantee that everyone on this call was on the deep web today or yesterday. The deep web is content that sits behind a username and a password –or content that is not indexed by a search engine. What I mean by that is if I go into Google, I might not be able to pull up the deeds on all the houses in Denver within the search engine. But if I go to denver.gov I can find that information. Or, for instance, I logged into my bank website this morning and I paid my water bill. That is deep web content – I can get there with a username and password but all of you can’t access my bank account. That is where the majority of the internet resides. There’s so much that sits behind usernames and passwords.
The darknet, where DarkOwl specializes, sits below both of those. It is an undefined and hard to quantify space, but, in comparison to the deep web and the surface web it is much, much smaller in volume. The reason it’s important and significant is that by definition the darknet allows you to remain anonymous. That is the darknets defining feature. If you want to nerd out over it, the darknet was actually developed by the US Naval Research Laboratory in the 90s to allow folks serving to remain anonymous. As we all know, what does anonymity bring? It brings an opportunity to do things without being found. Hence the illegal activity that happens on the darknet. But I want to be very clear that the darknet in itself is not a bad thing. It is not illegal to go onto the darknet. You do need to download special software. Some of you may have been on Tor.
The key takeaways here are: for the darknet you have to download special software, its kind of a pain get onto it, however, it is not illegal, and anyone is able to access it, and the defining feature is that you are able to remain anonymous when interacting on the darknet. And the best way to visualize this –and you all will know what generation I was born in by my analogy- when you used to watch the Price is Right you’d have that show with the little ship that would go down through all the slots. That’s essentially what’s happening on the darknet with your IP address. The ability to track someone back to an IP address is almost impossible on the darknet whereas if I go to Cowbell.com, Cowbell has an awesome marketing team, they most likely know where I came from, what my IP address was, what pages I looked at, and how long I stayed there. Those same tracking metrics do not exist on the darknet.
Why do we care about the darknet? Why is it something that we are all on the phone to talk about? The takeaways here are usage on the dark web. I go interchangeably between dark web and darknet – we use them interchangeably at DarkOwl. But there was an 80% increase in usage over the last 3 years. Millions of users are connecting through the Tor browser, which is the best-known darknet out there. This is a very lively and active community of folks. It may not be as big in quantity compared to the deep web or the surface web, but there’s a lot of activity going on there. That’s why we are all focused on it, and that’s why we DarkOwl are in business.
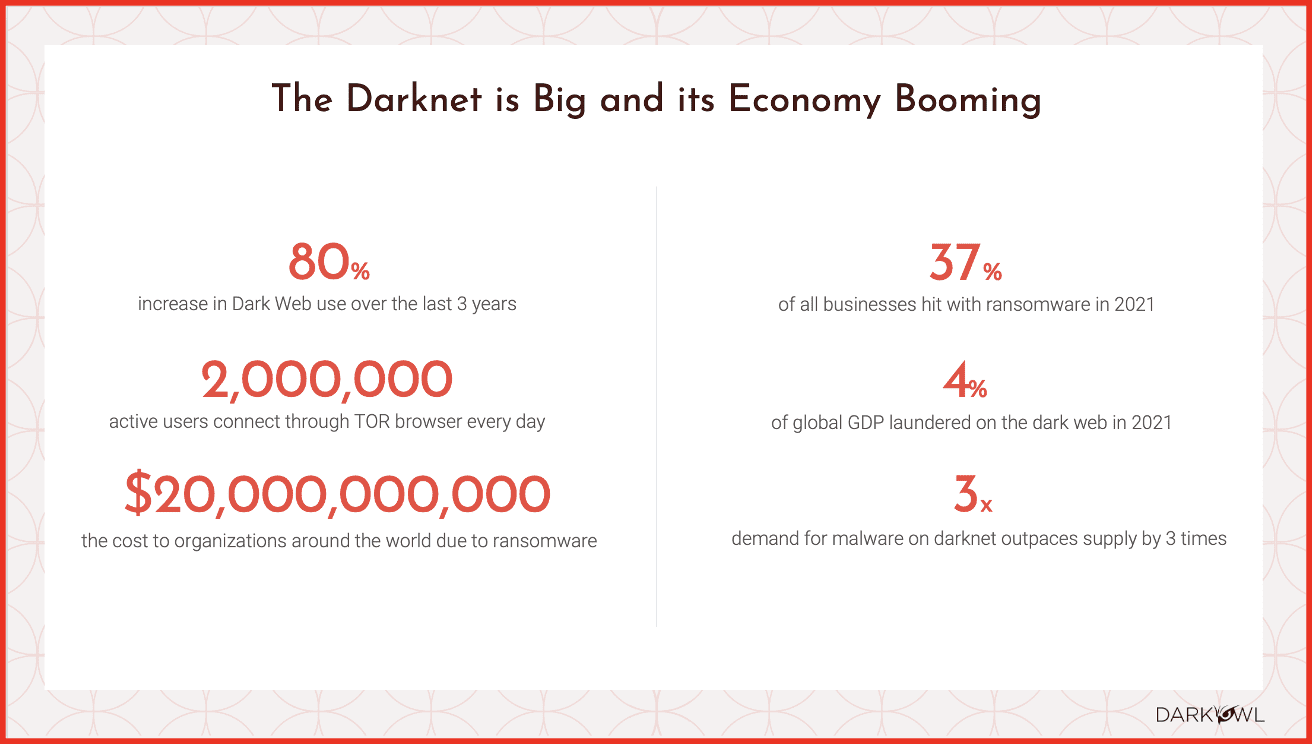
Obviously all of you are in the insurance space –so why is it important to understand what DarkOwl does and what darknets exist out there? The kind of stuff you are going to see on the darknet is exposed credentials, you are going to see IP addresses, you are going to see people buying and selling social security numbers, people trading gift cards, people posting ransomware, and people selling services to conduct malicious activity against organizations. You name it and it is being transacted on the darknet.
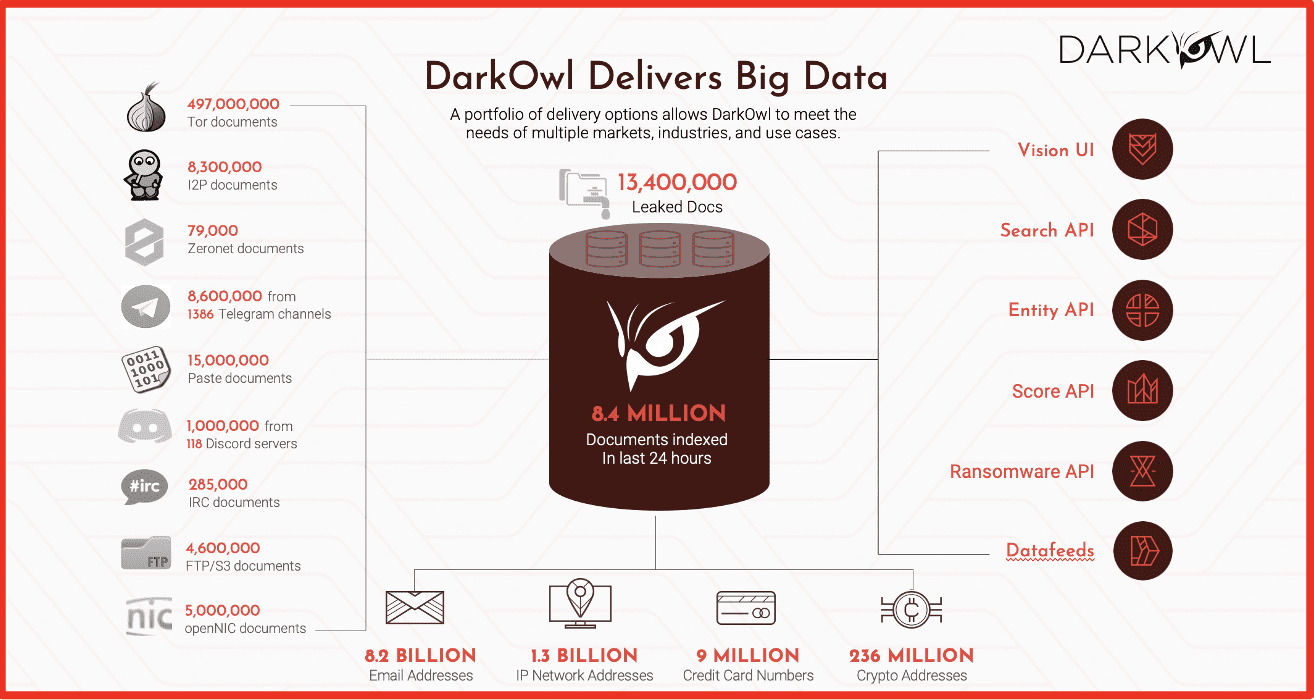
As a company, whether you are tiny or humongous, you need to understand what that looks like for your own organization. Jessica and Manu and I think a lot about: how can this data be helpful for our respective clients? And the best way to think of it is as an exposure vector. Most people on the darknet are there because they are doing something illegal and taking advantage of the ability to remain anonymous. If you as an organization have content on the darknet, whether it is emails or trade secrets or anything – that is a concern. That is why we’re all on this call today. We’re going to get into how Cowbell uses that information and what you can all leverage to help inform your clients why it is important for them to understand their darknet presence.
Jessica: You can see here the quantity of data that DarkOwl has, DarkOwl being Cowbells partner for dark web intelligence. What we want to impress upon our customers is that with Cowbell, it’s not just a cyber insurance policy that you are getting. You’re getting all the intelligence that Cowbell has from our partners as well. And DarkOwl is the crème de la crème of dark web intelligence. This is a value-add that’s above and beyond what other cyber insurance carriers might offer. And that’s a huge piece of information to keep in mind when talking to customers. The dark web is not just one place, it’s several different places. Many of you may have heard of platforms like Telegram or Discord. These are encrypted chat spaces that DarkOwl collects information from as well.
Alison, quick question for you: most people think to themselves, I am a small business, my information is probably not on there, and if it is on there what can someone really do with it? Can you speak to the amount of exposure you see for small businesses? Let’s say a bad actor has access to an email address, what could they even do with it?
Alison: Right. We get that question quite a lot. The answer is contrary to what most folks think. The vast majority of attacks, whether it’s ransomware attacks or cyber incidents, are targeted at small and medium businesses. Part of that is because that’s an easier feeding ground. A lot of those small to medium businesses don’t have the tech staff or the budget to have cybersecurity tools in place. Yes, you read in the front of the Wall Street Journal that a Fortune 500 company experienced a huge breach. But the ones you don’t necessarily hear about are all the small and medium businesses that are getting targeted day-in and day-out. The risks can be higher for those small and medium businesses… An IBM is going to be able to weather that storm whereas a small or medium business – they could not in a position to deal with a huge ransomware attack. The first question you ask Jessica – it absolutely is important for anyone whether you are a business of two people or two billion.
And the second question is what can they do with an email address? Quite frankly they can do a lot. They can find their way into that organization. A lot of content we see on the darknet will have passwords associated with it. Think about a hacker that has stolen information. And a small to medium business’ employee uses that same password for their Spotify account that they do internally for work. Because of password re-usage, that hacker can access the internal systems of the small to medium business and take down information. The business could be vulnerable to social engineering. We see a lot of executives targeted at small to medium-sized businesses. There are many vectors present on the darknet that threat actors could use to get into the organization from a technological standpoint or to social engineer their way in.
Jessica: That’s the perfect segway over to Manu which is the “so what?” What does Cowbell do with this data? How do we understand at what level of risk a company faces when it comes to dark web exposure? Manu, if you wouldn’t mind, give us an understanding of how Cowbell uses this data and what is available to customers above and beyond what they see in their dashboard? In their Cowbell portal on the platform.
Manu: Absolutely. The way we look at it, DarkOwl’s data is directly aggravated from forums off the dark web. This is valuable data to Cowbell since we’ve created a dark intelligence score for each one of our policyholders in the form of a Cowbell factor. This score helps us determine what the level of risk is associated with the organization’s exposure on the dark web. If we determine that there is organizational data exposed on the dark web, we’re able to quickly identify the number of documents exposed, and then we notify those Cowbell policyholders to potentially take action through our own platform. Now how does that really affect Cowbell factors, and what we can do for our insurers?
Our dark intelligence telefactor is impacted directly by the number of exposed data points that have surfaced on the dark web. The more exposed documents we identify and the more credentials or passwords that are leaked are associated as a high-risk. The severity of those exposed data points is categorized by low, medium, high, or very high. For example, if we identify that there’s 50 documents exposed on the darkweb for a particular insurer and 25 of those documents were considered hack-worthy data, then we may categorize that as a medium-sized risk. If we go down to 20 exposed documents with only 5 that were considered hack-worthy data than that may be considered a low risk. Versus something where we might find 5,000 documents on a particular insurer and they have 250 documents that are considered hack-worthy data. That would be in either the high or very high category as well. At that point we identify that risk for our insurer on our Cowbell cyber platform. From there they can go ahead and request additional details, such as what’s behind those documents and what’s actually been exposed. That’s what tends to happen with policy holders. They reach out to the risk engineering team and then from there we create a report for them.
Jessica: So if I want to understand what’s behind the score, you’re saying that I can reach out to the risk engineering team and receive a report. What does that report have in it? Can you show us an example?
Manu: Absolutely, I have one right here… this is a sample report. For full disclosure this is not any actual data on a policy holder or any actual dark web information on a policy holder. This is all make-believe. With DarkOwl’s data, we organize that data into a report that is consumable by IT professionals, by security professionals, and a report that makes sense for management teams and the C-suite as well. We want everyone to be able to look at this report and say: I get it, I see what the risks are, I see what the exposure is.
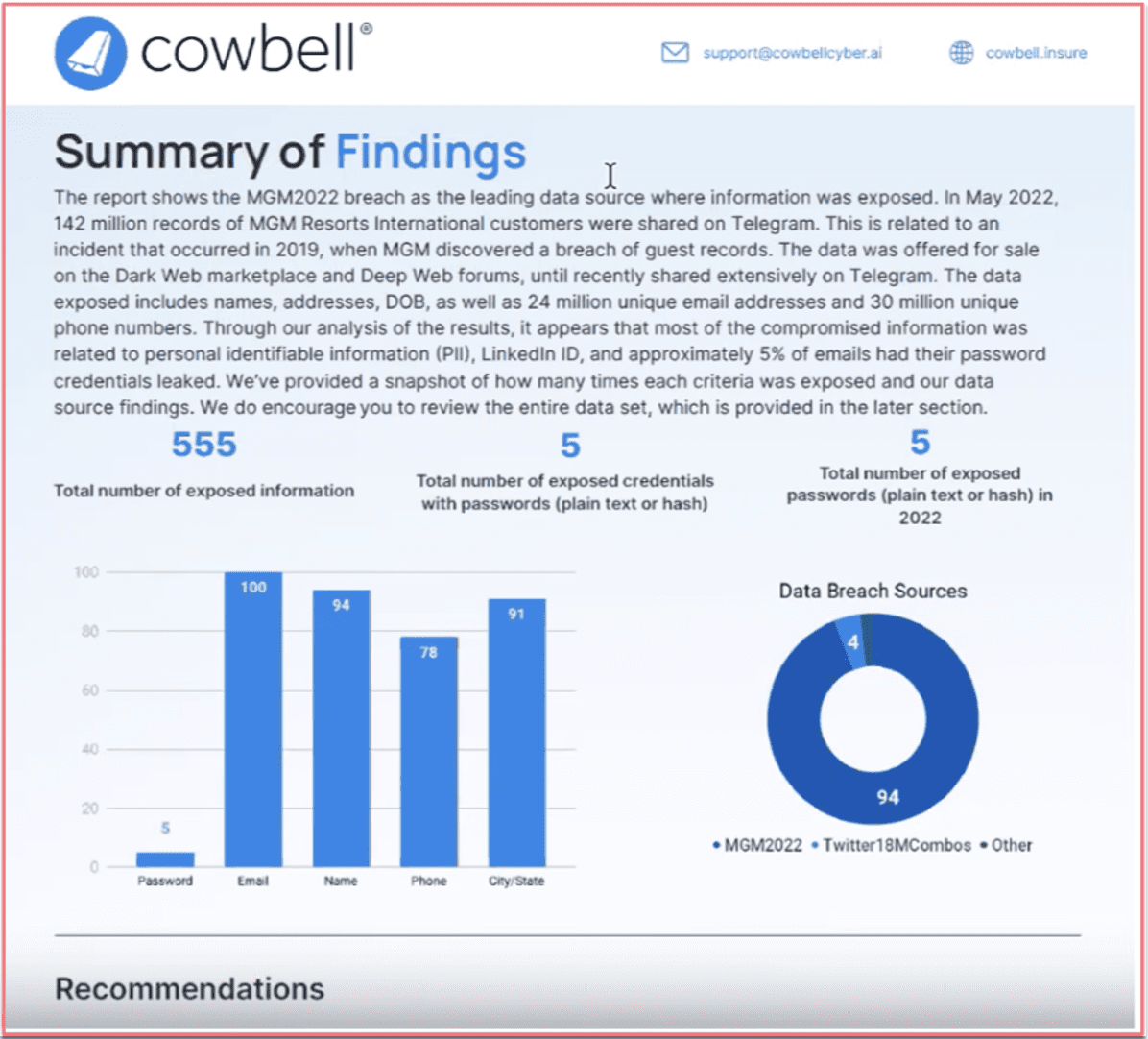
Our risk manager has done a great job of aggregating that data into a report that’s consumable by all. On the top you’ll see that summary of findings found through the help of DarkOwl’s platform. It will quickly summarize where this data was exposed. This report says the data was exposed in the MGM 2022 breach as well as the leading data source where all types of information was exposed. In this one it highlights the PII that may have been exposed such as date of birth, email addresses, names, actual physical addresses. This was happening for over 142 million records from the MGM breach in 2022. From there the report goes into some of the categories that we have found. The total number of exposed documents that have surfaced on the dark web for this particular insurer will be listed.
We have 555 exposed documents. From there it goes into how many of those are actually exposed credentials with passwords listed whether is plain text passwords, so that would be the actual password, versus something that’s hashed which would be more of a coded password and more difficult for a bad actor to take advantage of. It has listed 5 there. And then 5 is the total number of exposed passwords. This is passwords without a credential associated with it. This will also list out the most recent data that was listed, so you may find data that was listed in 2021, 2020, 2019. This data is as of this year so that makes it even more crucial for an organization to understand that this is a direct exposure, this is a recent breach, and this could be a recent password that an employee is using.
Down here we have a couple of charts. It will tell you the amount of passwords and some of the other data that is exposed such as email, names, phones, and physical address which is conveyed here for a policy holder.
Scrolling down we get into the recommendations that we want some of our policy holders to follow if they do have data exposure, such as what you can do next and how you can mitigate some of the exposure. We have listed some of the best practices and security controls policyholders can apply.
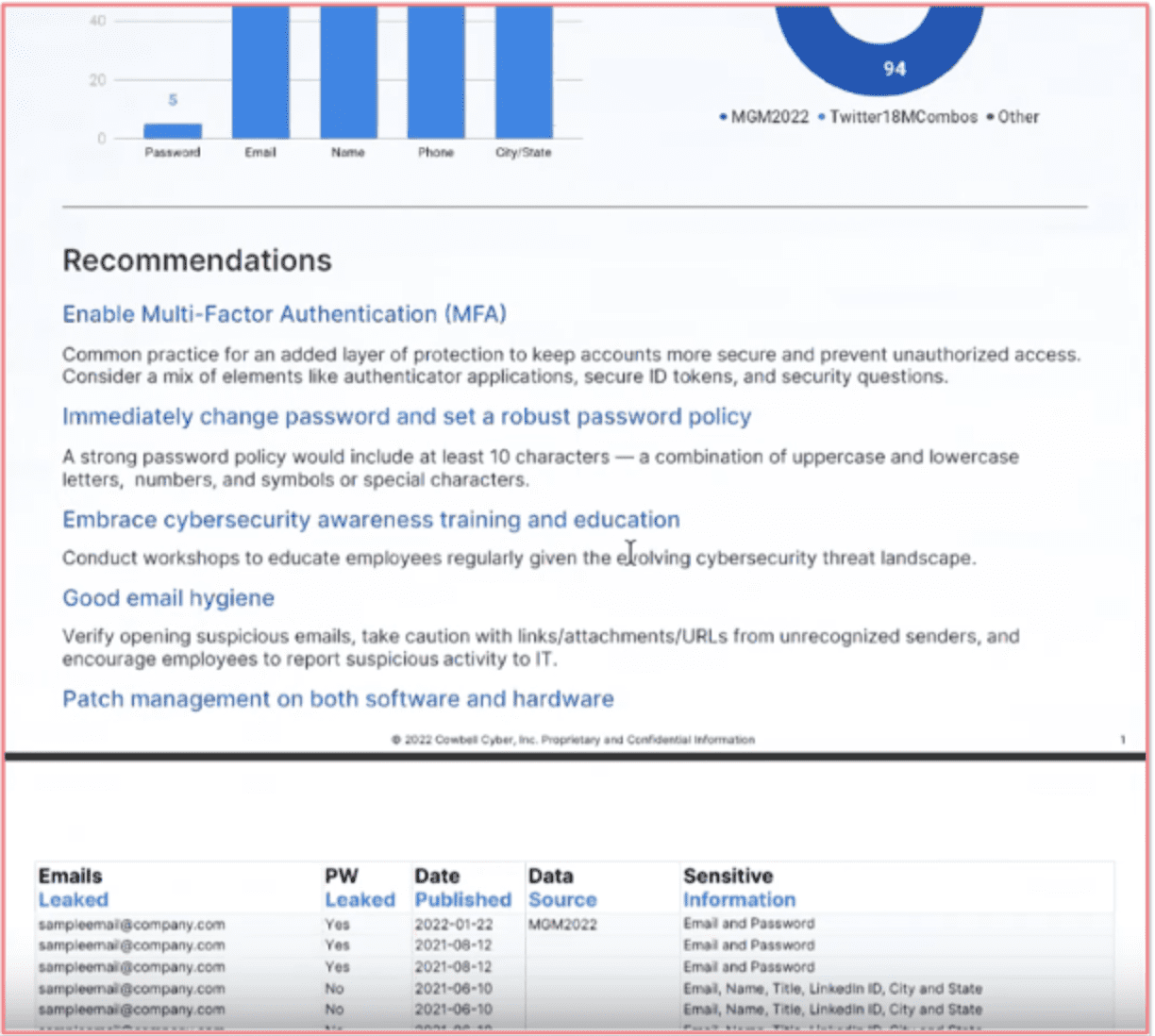
Everything from applying multi-factor authentication to those email accounts that may be exposed, to changing those passwords, creating robust password policies, requiring employees to have alphanumeric passwords, and passwords of at least 10 to 12 characters. That’s the standard right now. With special characters included. Training your employees to identify phishing attempts, having good email hygiene, and not clicking on links if you don’t know who the sender is are what we recommend to our policy holders to apply if they do have any exposure.
Jessica: I want to note that somebody in the chat asked: Is it hard to remove your information if it is on the dark web? Alison thanks for answering it [in the chat function]. In fact, it is impossible to erase information once it is on the dark web. There are two things to keep in mind here. Number one is this set of recommendations. If a customer is highly exposed, however, they are acting on some of these recommendations the exposure will go down with time. The more time that passes the lesser the importance of the exposure, such as if they are old passwords or passwords that are no longer in use or if there’s multi-factor authentication enabled. That’s going to disable a bad actor from using this information to do anything bad.
Manu: And the answer is yes. It is hard to remove that data. We can’t simply call the bad guys and say “hey look can you please delete my data off the dark web?,” they just won’t do it. Once it’s on the dark web it’s most likely on there for good. It’s going to be bought and sold. It’s going to be reposted on other forums for bad actors to buy, for actors to attempt to deploy phishing attempts against, to employ brute force attempts against, so it will always be on there. What the organization should do at that point is mitigate. Be proactive in your approach. Apply best practices. These are some of the recommendations that we initially want the insurer to take advantage of and quickly apply within their environment.
Going onto the next page this will be the actual raw data that we notice from DarkOwl’s aggregation. We’ll list out the email that was leaked and posted on the dark web. It will be the company email most likely. From there we’ll also post whether any password was leaked. In this case the password was leaked. The answer could be yes, no, or could be a hashed password. From there we want to give the policyholders the date that it was published on the dark web. We think that’s important because the more relevant data for the bad actor to take advantage of and to use to compromise your organization will be the most recent data that was posted. We tend to see that with credentials that they get from the current year – those passwords may still be current. Employees may still be using those passwords to login to those accounts. Threat actors take quick advantage of that. Then we’ll list out the data source as well just so the policy holder can understand: was I compromised, or was this from a third party where my data might have been sitting somewhere and the bad actors had access to it that way? If there are any of other types of information included –so email addresses and passwords for this one –you can see some of these emails have a lot more PII associated with them, such as email addresses, names, titles, their LinkedIn IDs, and where they’re living.
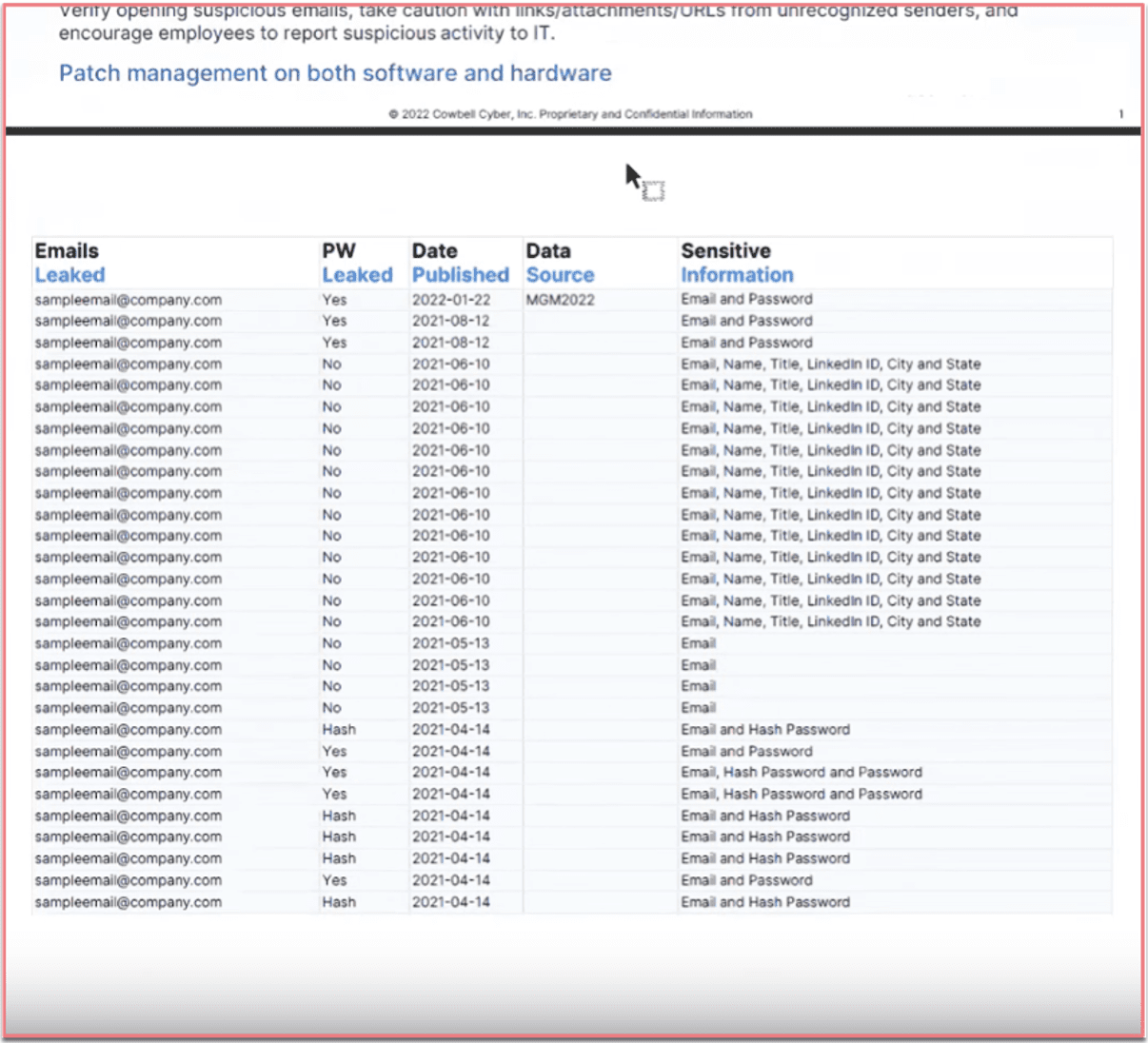
Alison: That context that Manu just went over is extremely valuable and I don’t want that to be lost in the details. There are other darknet providers who might be able to say yes, that company has exposure on the darknet. But then it’s end of sentence. And you don’t get the context. Being able to share with that client that these exact email addresses with these exact passwords were a part of this breach is so much more powerful. Think about the mitigation if you are a small-medium sized business and this report comes back and there’s three email addresses on it and three of those employees are no longer with the company and left 4 years ago. You’re not concerned. Or, you come back and this report has 5 email addresses listed on it and every one of those employees was attending a conference last week together – that’s going to be a very different mitigation strategy for that business than the former. The context and the fact that Cowbell can pass that on to you to pass onto the policy holder… is extremely important because it allows them to act on it versus “well there’s information out there, good luck.”
Jessica: Alison when you say valuable, I want to press upon that. A lot of DarkOwl’s customers are cybersecurity companies. They might charge thousands of dollars to a customer per year to provide this in-depth information. Manu, do our customers have to pay for this report?
Manu: No, this is a value-add for being a Cowbell policy holder. It’s one of the many value-adds that we bring to our policy holders, and it’s one of the most frequently requested value-adds that we provide. If you notice that you had an exposure on the dark web, within the same day or within 24 hours we can turn around a report and get it over to your risk managers and your security folks. There’s no added cost associated with utilizing this service.
Alison: I would leverage that highly. When we were prepping for the webinar, Jessica was asking me how I would position it if I was in all of your shoes. I think about comparing different car insurances. If you make that analogy over to cyber insurance, this is the equivalent of getting free oil changes and engine checks. This is a huge value-add especially for small-medium businesses that may not have an IT staff who can be looking on the darknet. I think it’s a freebee that they can take advantage of.
Jessica: Absolutely. Manu, can you answer for us: what are some of the most common questions or trends that you get from customers about the dark web? Is there a common misconception, myth, or concern that your team fields most often?
Manu: The number one question we get after an organization realizes that their data was on the dark web is: “have we suffered a data breach or a cyberattack?” In most cases that we’ve seen the answer is no, it’s just the circumstances – it tends to be that the compromise happened at a third party, and they were storing your data in some capacity and threat actors gained access to it and they posted it on the dark web. Sometimes a bad actor will even mention the data source that they aggregated the data from. There are some cases where it could be direct exposure to your organization, and this indicates a breach. But what we tend to see is that it’s most likely a third-party breach and your data has been posted on the darknet. I would say the next question that we receive often is: “how can I reduce my risk?” and “this data is out there, what do I do?” and “how do I make sure that I don’t get hacked, how do I make sure that I don’t become a target?” It goes back to being proactive to applying those recommendations that we spoke about. Between MFA, email security, training your employees, and having strong passwords –all of that is very important. Those are probably the top two questions we get from policy holders once they notice that they have had some exposure.
Jessica: Manu this question (from the chat) is going to come to you. Do we also use this data as we underwrite and determine premium rates for prospective customers, and if so, is there a way to get a sample of some exposure for clients in advance as we help them consider the value of a Cowbell policy?
Manu: It is factored into the underwriting process if there is exposure on the dark web, however, we do give policyholders a chance to let us know what they are doing to be proactive to reduce their risk. Once underwriting understands [what they are doing to reduce risk] we get comfortable enough with the risk to move forward in the underwriting process.
Alison: Can they share it with their prospective clients?
Manu: Yes. We can certainly provide that data to prospective clients as well.
Jessica: So a broker could reach out in advance and understand what the exposure is so that they can guide that client potentially into a Cowbell policy or elsewhere?
Manu: Yes. As far as sending the actual data over we wouldn’t do that. We would just let them know if there is exposure and the amount of documents we’ve noticed as hack worthy data on the dark web. Then the actual data that is exposed would be shared with the policyholder or the potential client.
Jessica: So the dark web report that you shared is a post-buying experience for the policy holder. Any final comments? Alison and Manu thank you so much for being here. Do you have any closing thoughts for the audience?
Alison: We’re here and as you can tell we are doing a ton of work in the background and by “we” I mean Cowbell and DarkOwl to try and make this a much more robust policy than some other folks out there so don’t be afraid to come to us, ask questions, and if you have any personal interest in learning more about the darknet, there’s a lot on our website at DarkOwl. We’re just here to help.
Manu: Thanks Alison and I would say that if there’s exposure on the dark web and if you don’t know what to do –come to us, ask, go on the platform and see if there is any indication. And if there is exposure as us to generate a report for you. Again, it’s a value-add for our policy holders so certainly take advantage of it. This helps in several ways. It will help reduce the organization’s chance of suffering a cyber incident related to that exposed data. It also helps underwriters better understand your security posture, and then they can more accurately rate your organization as a safer risk, and that includes during the renewal process as well.
The organization can show Cowbell that they have been proactive, that they have reached out, that they have mitigated against some of these exposures, and they can show us that they are in a strong place for a renewal. Take advantage of the value-add from DarkOwl and Cowbell; it only helps reduce your risk and make your organization a stronger cybersecurity organization.
Jessica: Thank you. Hopefully we’ve given you some things to think about today that you can turn around today, tomorrow, the next, and directly relay to your customers as to why Cowbell… is different in the market than other carriers. We’re using data sources that are absolutely the best in class to help define risk and rate risk. Beyond that we have Manu and his team who are here to help you, guide you, and provide extra information and context throughout the entire lifecycle of a policy.
Cowbell is the leading provider of cyber insurance for small and medium-sized enterprises (SMEs) and the pioneer of Adaptive Cyber Insurance. Cowbell delivers standalone cyber coverage tailored to the unique needs of each business. Our innovative approach relies on AI for continuous risk assessment and continuous underwriting while delivering policyholders a closed-loop approach to risk management with risk prevention, risk mitigation, incident preparedness and response services. To learn more, visit: https://cowbell.insure/
DarkOwl uses machine learning to collect automatically, continuously, and anonymously, index and rank darknet, deep web, and high-risk surface net data that allows for simplicity in searching. Our platform collects and stores data in near real-time, allowing darknet sites that frequently change location and availability, be queried in a safe and secure manner without having to access the darknet itself. DarkOwl is unique not only in the depth and breadth of its darknet data, but also in the relevance and searchability of its data, its investigation tools, and its passionate customer service. Our passion, our focus, and our expertise is the darknet.
Interested in how darknet data applies to your use case? Contact us.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















