Importance of Darknet Data in CyberSecurity Programs for Small and Medium Businesses
September 07, 2022
DarkOwl CEO Mark Turnage and Symbol Security Co-Founder and President Craig Sandman discuss the darknet, key elements of cyber surveillance utilizing darknet intelligence, their partnership, and why darknet data is an essential part of Cybersecurity programs in the SMB market.
For those that would rather read the presentation, we have transcribed it below.
NOTE: Some content has been edited for length and clarity.
Mark: Let me talk a little bit about DarkOwl. We’re a company that’s about five years old based in Denver, Colorado. We specialize in collecting, aggregating, indexing, and supplying data from the darknet. And we’re very specialized and focused just on the darknet. There are other companies, there are other threat intelligence companies that provide other types of data. But our specific expertise is simply in the darknet. We’re very proud of the fact that we have more female employees in the business than most tech companies do, I think we’re just under 30% right now. In the past, we’ve been as high as 40%, and we’re very proud of that fact.
But to the point of darknet we have built over the 4 or 5 years of the company’s existence, we built what we believe is the largest darknet database in the world. And let’s just talk a bit about what I call definitional ambiguities. What is the darknet? What is the deep web? The surface web is what everybody sees as the top of that iceberg on the right. That’s where we spend all our time. It’s accessible by Google. You can get information and that’s where the vast majority of the world spends most of its time on the web. The deep web are authenticated websites. So, for example, your bank account information – Mark Turnage cannot get to your bank account information from my browser. I might be able to get to your bank’s sign in page, but I can’t get to your information because I lack the authentication and the credentials to get there. Ironically, that’s where the bulk of all the data that is held on the internet is actually stored.
Where we specialize is in the darknet. These are anonymized networks that reside below the level of the surface sites, surface web and the deep web. And they generally require specialized browsers to get access to. And it generally requires some type of specialized knowledge, although not in all cases. If you look at this slide, what we’re talking about is at the bottom of that slide, Tor i2p, Zeronet, other new darknets that have been created, these are darknets where DarkOwl is on a daily basis collecting data and supplying that data to our partners and now including Symbol. And that data is full of information that is relevant to measuring the risk of organizations and understanding the risk and addressing that risk.
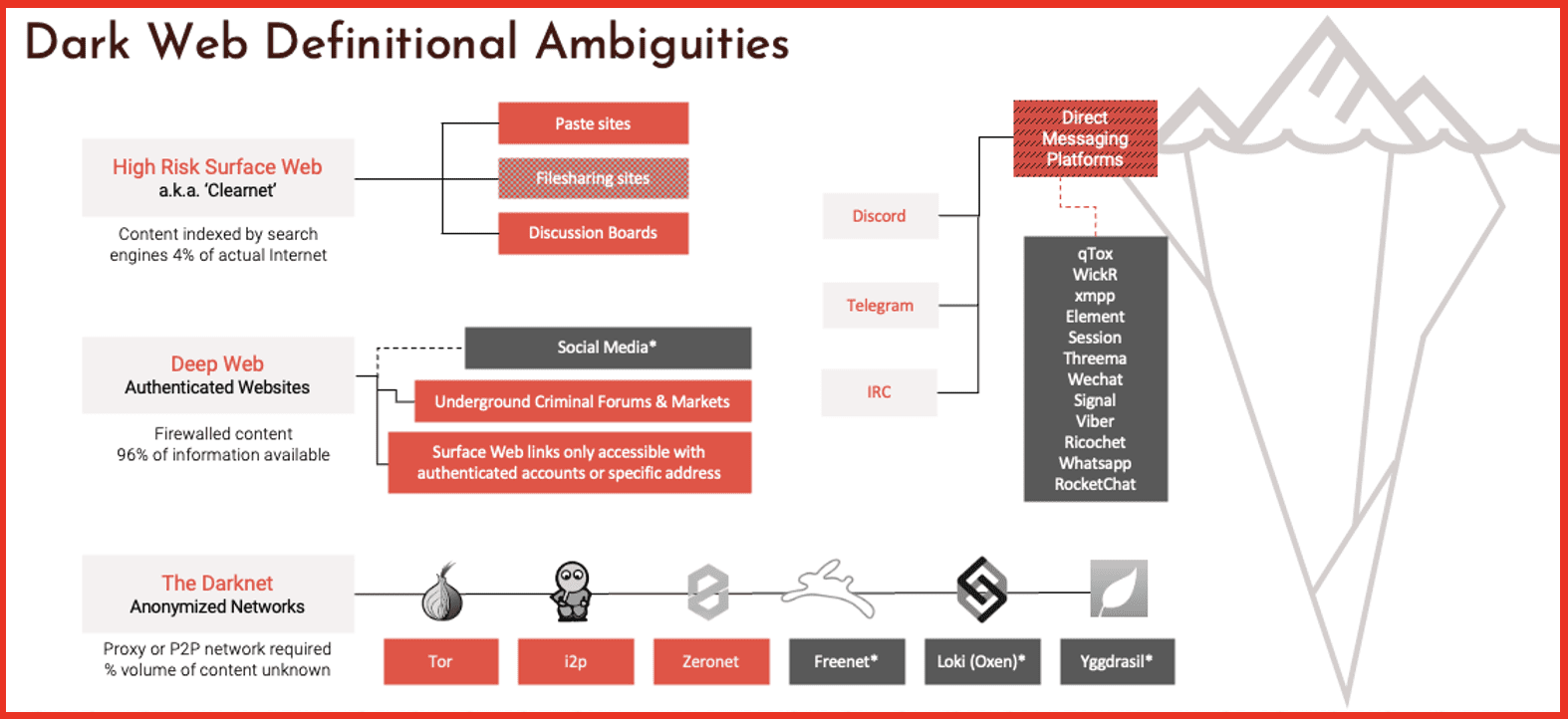
We also do collect data and supply it from certain high risk surface websites, pay sites, and some discussion boards, as well as some deep websites, some underground criminal forums and so on. All of that we describe as the darknet database. And again, we’re collecting it so that organizations can understand what data of theirs is in the darknet, what exposure they have in the darknet.
Kathy: Mark, real quick – a couple of questions have come in on that last slide that you just shared. The first one is “How big is the darknet?”
Mark: That is a really good question and nobody particularly knows the answer. When we started collecting data from the darknet, the darknet was Tor, the Tor network. There are now probably half a dozen darknets that exist and we collect data, as this slide shows from it, and Zeronet. We’re moving into other darknets as well. But there is no easy way to measure the darknet. And the simple reason for that is that the darknet is generally distributed around the world. The Tor network is a network of between 15,000 and 20,000 servers around the world that serve that. There’s no easy way to measure it. But to give you a sense, DarkOwl collects data from somewhere between 25,000 and 30,000 darknet sites a day. That’s before you get to the high-risk surface websites and the deep websites. So that’s a lot of data. These darknets are growing and usage on these darknets is growing great.
Kathy: And there’s also a question as to “How do you know when a company is being targeted on the dark web?”
Mark: Well, generally indicators of the fact that a company is being targeted in the darknet show up. Either the company is mentioned by name or their IP range, it shows up in a targeting website, let’s say a hacker forum where somebody says, here are some IP ranges where I’ve discovered certain vulnerabilities, or I’m selling access to this company’s server network. Or you will see things like credentials and passwords for sale for individual companies that allow hackers or ransomware actors or other actors to drive straight into the network and be inside the network. So there are lots of indicators of risk of companies that show up in the darknet. Using our database and using Symbols database, you can search for those indicators of risk that may exist with respect to your individual organization.
Mark: I’m going to finish on this slide I mentioned earlier. We’ve built what we think is the world’s largest database of darknet content. This gives you a sense of some of the locations that we collect from Telegram, ITP, Tour, zero net, pay sites, and so on. And it will give you a sense of just what we’ve indexed in the last 24 hours. The slide shows 8.4 million documents have been indexed into our database in the last 24 hours. If you look along the bottom, it will give you a sense of what we have collected over the years of our existence. We have somewhere north of 8 billion email addresses in our database. We have somewhere north of a billion IP addresses, 9 million credit cards, 236,000,000 crypto addresses. That gives you a scale and sense of the scale of what exists in the darknet and exists by virtue of having access to our platform.
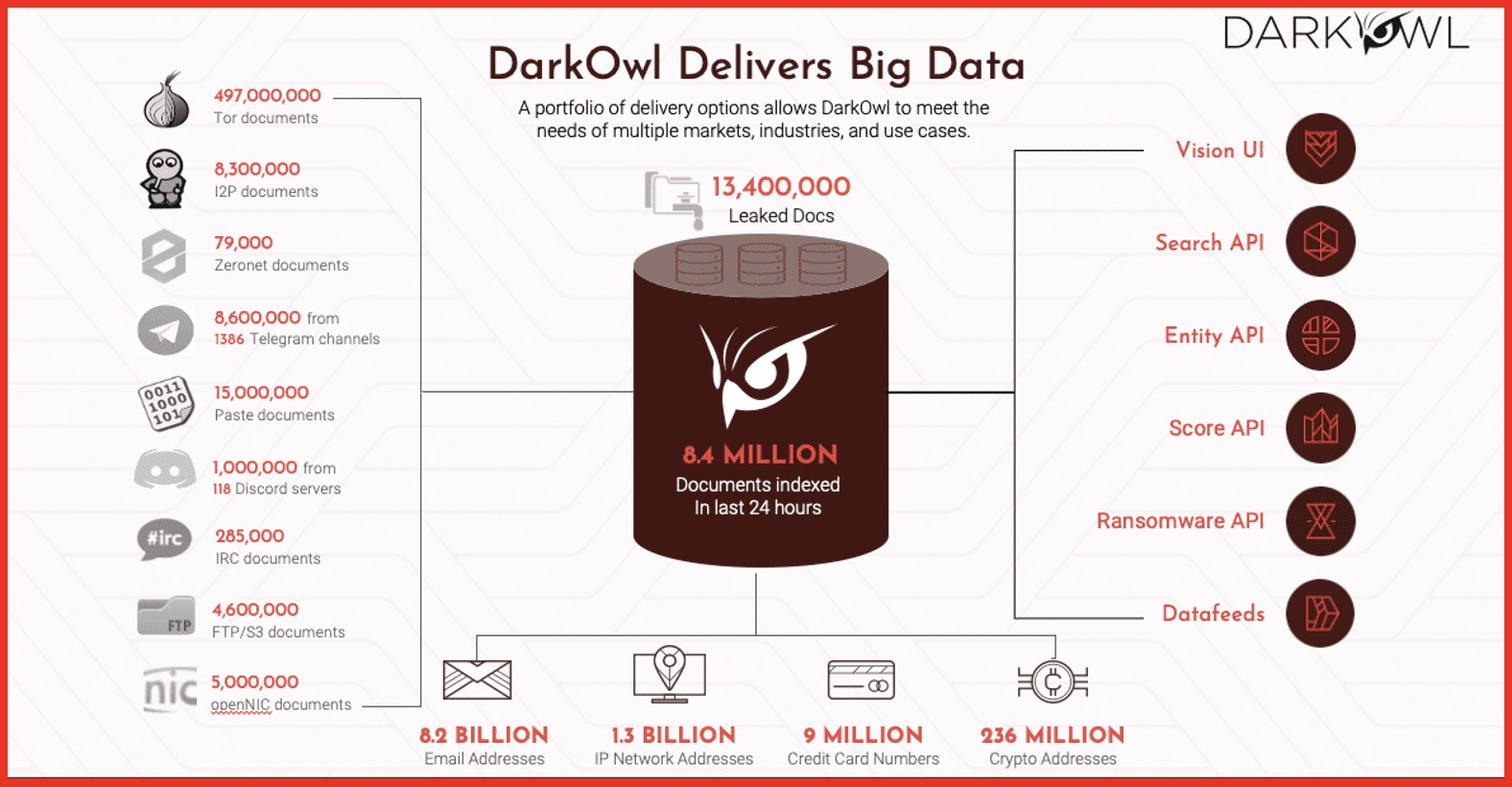
We provide that data a number of different ways and are delighted to partner with Symbol and now I’m going to turn it over to Craig.
Craig: Great. Thanks, Mark. Appreciate it. Great job. Mark did a great overview of darknet, deep web and the surface web. Certainly it’s a squirrel space and a big space. So let me tell you a little bit about Symbol Security and we’ll kind of pull into this how we managed to get together with DarkOwl and deliver some of these darknet cyber surveillance services to the SMB market.
Symbol Security is a provider of predominantly security awareness training services. As you probably know, security awareness training is something that’s been hot in terms of a way to address and mitigate the attacks of cybercrime and it’s also in regulated environments. And we’re talking now close to 800-850 regulations, laws and other statutes that require businesses show evidence of security awareness training. So it’s becoming a nonstarter for businesses, even if you didn’t feel like it was a good use of your time or argued the fact that it made your company safer or not. Independent of that, it’s a requirement in so many regulations, it’s becoming a nonstarter.
One of the things we do a little bit differently than most companies is we deliver a managed program. So a lot of the security training services and the implementation falls down in just that, in the implementation of it. So they may buy the software, but do they actually properly implement or even get to implement the service? We know how things go in the small to mid-size business. Everybody’s 150% subscribed in terms of their time and it’s difficult to execute on everything you have to do. So things fall to the bottom of the list. One of the things that typically will fall to the bottom of the list is security awareness training. We look at security awareness training and security awareness as targeting human risk. So how do we identify human risk and how do we mitigate human risk? Through education. We do more than just training videos and phishing stimulations. We look at email and domain threats. So email threats would be breach alerts and things like that. Is your email address compromised in any way? Domain threats look at the potential of doppleganger and lookalike domains being manipulated and used potentially against you, just helping give access and visibility to your thread envelope.
From a training perspective, we have really great trainings, very good simulations, and we make things quite easy because we’re typically focusing on the SMB market and through SMB distribution points like managed service providers and managed security service providers. And we’ve added cyber threat surveillance now to this platform into the bundle. And I’ll talk about why in a moment, but it plays into the extension of threat awareness for the individual and for the small business that’s how and why we’ve tied it in.
And we’ll talk now about what cyber threat surveillance is to us and to the SMB market space. So essentially, as Mark indicated, there’s a lot of different things that you can pick up on the darknet and on the deep web that are very valuable in terms of being proactive in your cyber awareness strategy. So reactive would be we’ve seen a breach alert for a particular email address. Now we go in and change username and password so it can’t be further manipulated, but the breach has already happened. We’re reacting in that case and there’s other instances where we’re simply reacting to things that have already happened.
We’re flipping a script here and allowing for darknet visibility and deep web visibility to provide proactive awareness. So when might things begin to look strange or suspicious that we need to act on, rather than we already know there’s a problem? We’ve probably already been hacked or attempted to have been hacked, and now we’re going to mitigate post that event. The concept of brand protection falls in there if there’s potential issues in and around your brand or people are slandering your brand or lining up your brand for an attack or any kind of negative event. VIP email monitoring we talk about a lot as well. So if you have individuals that are perhaps tightly associated with your brand, obviously any kind of reputational damage, there could be a cyber issue or a damaging issue for your organization. And then monitoring chat rooms. And just as part of the entirety of the deep and dark web chat room, visibility is included in there, as well as looking over products and domains. So those are also places where organizations want to protect their assets. What we’ve done here is taken a service and a feed that is typically consumed by government entities, large agencies and Fortune 100 companies, and we boiled it down to a simplified package so that the SMB can consume it.
That’s what was missing before. Right. We have incredible service provider in DarkOwl and some really great layers around that the entities in the market use in order to consume this data. But when it gets to the SMB, it’s too complicated and or too expensive for most budgets. So that’s really what we need when we say SMB packaged. And as part of that, we’ve broken it down into really keyword and email monitoring and we’ve integrated it into our cyber awareness reporting for the small to medium business.
Kathy: “Don’t threat actors only come after large companies? And what is the top cybercrime for small businesses of under 50 employees?”
Craig: First question, definitely a misnomer in that cybercrime happens most often with large businesses. It’s equally prevalent in small businesses. Obviously, big businesses might offer a bigger return from a cybercrime business perspective. But at the same time, the small businesses are generally less able to defend themselves and so they become quick hits. And if cybercriminals can get a 10,000, 20,000, 50,000 dollar return on investment for a crime, they’ll do it. And so there’s case after case after case of small businesses getting swindled out of 10,000, 50,000, $100,000 at a time through direct targeted cybercriminal attempts.
The second question was what is the top cybercrime that small businesses under 50 employees face. Cybercrime can be broken into many different buckets, probably not too surprising. The execution is typically ransomware that finds its way into all business sizes. How it gets in there is sometimes varied. So we focus a lot on fishing training and sort of mimicking phishing attacks. We can teach users to at least recognize and for that entry point for ransomware. But obviously ransomware can be delivered a number of different ways. That is the most prevalent situation. We do see wire fraud work its way into small businesses as well. That might be some kind of action sometimes from a phishing email that says something along the lines of, hey, please wire funds from this account to that account, where the secondary account isn’t something that’s owned by the small business. But certainly locking up files and then extortion from a ransomware perspective is, I’d say, the most common across probably most business segments.
Mark: Let me add something to Craig’s good answer to your first question of our SMBs targeted. To the same degree that large companies are targeted, we have found that oftentimes SMBs are targeted in favor instead of larger companies. Larger companies have a lot of money they can spend on hardening their defenses. SMBs oftentimes are softer targets for hackers and for malicious actors. So we have found that in some cases they go deliberately after SMBs versus going after larger actors. But that’s exactly right, Craig. I mean, I think the types of attacks that you’re seeing amongst your client base, it mirrors exactly what we see as well.
Craig: Absolutely.
Craig: And so from a cyber threat surveillance perspective, we’re not going to get into a demo today, just kind of short on time, but I wanted to give you at least a screenshot so I can talk through how this operationalizes itself into our platform.
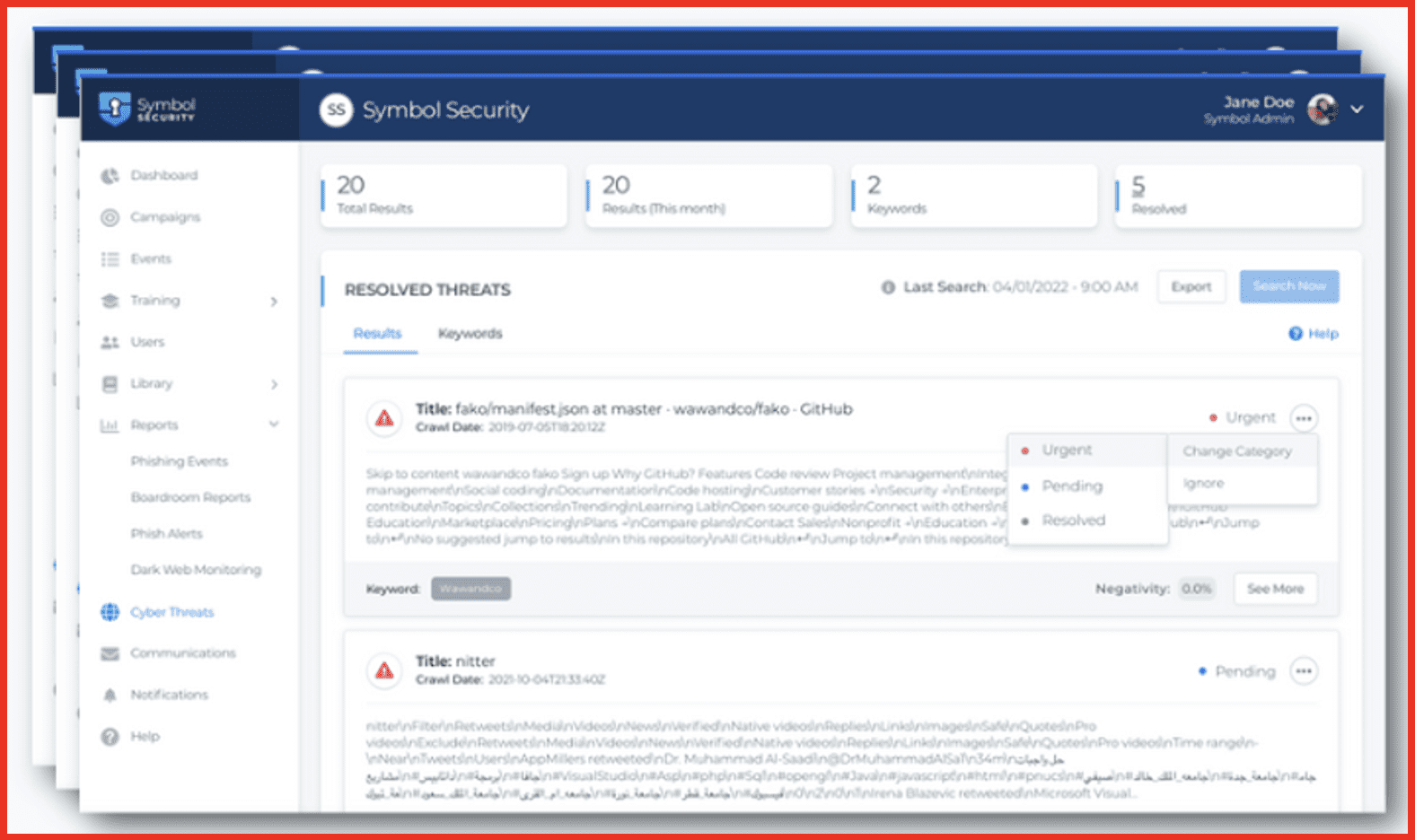
Essentially, we provide we provide daily updates on darknet findings that are pertinent to your organization. And we’ve really structured the input so that it’s simple. We’re looking for keywords and potentially VIP emails we can also as mark alluded to. We can enter things like credit card information or IP addresses as well. From an advertise level, we really focus on keywords, which would be a business name, a product name, a brand name, an affiliate name, and then we are also looking at what we call VIP email protection as well. But again, we can pivot to incorporate some of those other items as well. We integrate the results directly into reporting and a dashboard. So as you saw on the last screen, briefly we’ll intake the findings. If your keyword or your VIP email is found, we’re going to give you plenty of surrounding context. It may be thousands of characters of additional data around the keyword that we found. You’ll get full context of not only the fact that this VIP email or keyword, maybe your brand name, your company name was found on the darknet, but you’ll see the entirety of the discussion around it in addition to the location that it occurred on. You’ll also get email alerts when these things happen. So administrators are going to get notified.
There’s a nice portal to allow you to track and categorize these incidents. You can categorize them as urgent, you can categorize them as resolved or just leave them in a pending state. Also of interest too is we provide some sentiment tracking as well. So based on what we see, we’re going to give an analysis of sentiment or negativity around a particular finding. So if it may be benign, there’s plenty of benign information on the dark web that’s really not pertinent, not meaningful, certainly not hurtful. You’ll see those results, but we’ll prioritize and we’ll flag as urgent results that hit a high negativity level. So we kind of take care of some of the analysis for you, although response remediation planning around what to do if you do find something is really up to you as an organization or perhaps a security provider that you’re partnered with.
Average price – so we will talk about price here for our service falls 4,000 to 15,000 dollars per year. It’s obviously a large range, but it really just depends on how much you want us to monitor for you. So I wanted to give that too because the average price point, entry level price point for the service is generally three to four times the high end that I’ve referenced there. And so in those cases, the access to this data typically outstretches an SMB budget. We fit it squarely in a range where SMBs can afford this service and most times we’re addressing clients that also have other needs around security awareness, training, password management services. We’re able to bundle those elements together and give them a nice SMB cybersecurity suite. As I mentioned, we will sell these services through managed security service providers as well. So we have a portfolio of managed service providers that will deliver many more services bundled together. Additionally, we can deliver these as a single suite and more of a point solution to organizations as well. All right, any other questions that we want to get to before we close it out here?
Kathy: Yes, we have had a couple more come in. “Can you please give an example for a small business where information from the dark web could help protect the brand reputation?”
Craig: Yeah, I can. Mark, I’m sure you probably can as well. But one of the things that comes to mind is a couple of things really I address this earlier in the conversation when I start talking about executives that are really tied to the brand of the company. And in some cases, if either those executives are being targeted or perhaps they are involved in some nefarious activity and that gets picked up, it’s not going to be a good ending. But at least an organization has time to prepare and plan and take action before an event has occurred. And that might be public relations type planning or perhaps getting out in front of any potential negative activity. Additionally, if there is some really slanderous and hateful discussions about a particular organization, that would be a cause of concern and you can use your imagination on what those things might be, these will get picked up if they’re happening on the dark web and on the darknet. So those are two situations that are certainly ones that the surveillance will help identify, which if you had typical reactive cybersecurity services, you’re not going to see those things until an event is inbound or incoming. Mark, I don’t know if you have anything to add to that.
Mark: That’s an exceptionally good answer. I would just add that in addition to VIP information slanderous activity, I would start by saying there is almost no mention of your organization in the darknet that couldn’t potentially affect your brand. So if you’re breached in a ransomware attack, if you’re being targeted in addition to the slanderous statements that are being made, ultimately that’s going to affect your brand negatively. Everybody knows about what happened to large companies that have been breached and their brand being tarnished as a result. The same is true for SMBs. And so all of the categories that Symbol monitors on behalf of its clients, all of them have some capacity or some capability to damage the brand.
Kathy: “So Symbol covers what is on the darknet, but what about other cyber risks?”
Craig: Yeah, that’s a great question. I mentioned some of our partner organizations. Obviously, the landscape of cyber risk is significant. These services that we provide, provide great coverage across the things that we’re specialists in, which should be training and some visibility around potential cyber threats that cross the dark web and potentially into domain names and breached email addresses and things like that. Of course there’s many more things to cover and we highly recommend, especially in the SMB space, security consultants, virtual CISOs. If you don’t have a CISO on board or maybe can’t afford one, those kind of fractional consultants are great and we have a number of really good managed security service providers that can provide a large breadth of cybersecurity type services from a single organization. Best of breed. Best practices and things of that nature. So we can certainly sit as a point of reference for helping you find those things and for the pieces that we cover today, we’re happy to deliver those directly as well. But yeah, there’s a lot more to it for sure.
Thank you so much for joining us today.
About Symbol Security:
Symbol Security’s SaaS platform helps customers reduce their cyber risk, and adhere to industry compliance requirements. Through authentic simulated phishing exercises, interactive training content, and awareness of risk data across domain registries, and the dark web, Symbol helps companies identify and act on potential points of cyber risk. Symbol can be operated by company administrators with ease or leveraged by Managed Security Service Providers as part of their security offerings. Visit their website: https://symbolsecurity.com/
To get in touch with Symbol Security email [email protected]
About DarkOwl
DarkOwl uses machine learning to automatically, continuously, and anonymously collect, index and rank darknet, deep web, and high-risk surface net data that allows for simplicity in searching. Our platform collects and stores data in near realtime, allowing darknet sites that frequently change location and availability, be queried in a safe and secure manner without having to access the darknet itself. DarkOwl offers a variety of options to access their data.
To get in touch with DarkOwl, contact us here.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















