[Webinar Transcription] What Role Does Darknet Data Play in API Security?
November 10, 2022
Or, watch on YouTube
Mark Turnage, CEO and Co-Founder of DarkOwl, and Anusha Iyer, CTO and Co-Founder of Corsha, discuss how API Security professionals can benefit from darknet data in forming a more comprehensive understanding of malicious threat actor (TA) tactics, techniques, and procedures (TTPs) and providing effective detailed security recommendations, remediations, and product solutions. API Security related topics, like “API hacking”, “stolen API tokens”, and “API MITM attacks” are regularly discussed in detail in darknet forums, tokens sold and traded in underground digital marketplaces, and API exploitation code shared amongst threat actors.
For those that would rather read the presentation, we have transcribed it below.
NOTE: Some content has been edited for length and clarity.
Kathy: Hi, everybody. Thank you for joining today’s webinar.
Before we begin, I want to take a moment and introduce our speakers. Anusha Iyer, President, CTO, and Co-Founder of Corsha, and Mark Turnage, CEO and Co-Founder of DarkOwl, both of whom have many years of experience working in the cybersecurity industry. Anusha is a Carnegie Mellon alum. She started in the Washington, DC area at the Naval Research Lab. At NRL her focus was on reverse engineering and tactical edge networking. She started Corsha with a friend a few years ago and is passionate about helping organizations get API security right, and making security accessible, easy to adopt, and even self-assuring. Mark is a graduate of Yale Law School, Oxford University, and the University of Colorado, Boulder. He serves on numerous corporate and nonprofit boards, and is a private investor in technology, software, and manufacturing startup companies. He is also a senior advisor to the Colorado Impact Fund and a technology advisor to the Blackstone Entrepreneurs Network. And now I’d like to turn it over to Anusha to begin our webinar.
Anusha: Thank you Kathy and thanks to everyone for joining. We have an exciting agenda today. We’re going to look at API security and specifically API credentials and what an API security related incident looks like. We’ll tell you a little bit about Corsha as well as DarkOwl. We’ll go into why API security is so critical, some mechanisms to combat some of the threats and the attacks that we’re seeing, how the darknet can provide insights on this problem. Then [I’ll] turn it over to Mark to talk about DarkOwl and what is the darknet, how DarkOwl can deliver darknet data and give you more insights and analytics into where information is showing up on the darknet. And particularly with respect to APIs, what are threat actors saying about APIs on the darknet? And then we look forward to your questions and final thoughts.
DarkOwl and Corsha actually met a few months ago at Black Hat and had an interesting conversation around the proliferation of API credentials and how they are increasingly being used to gain unauthorized access to systems and services.
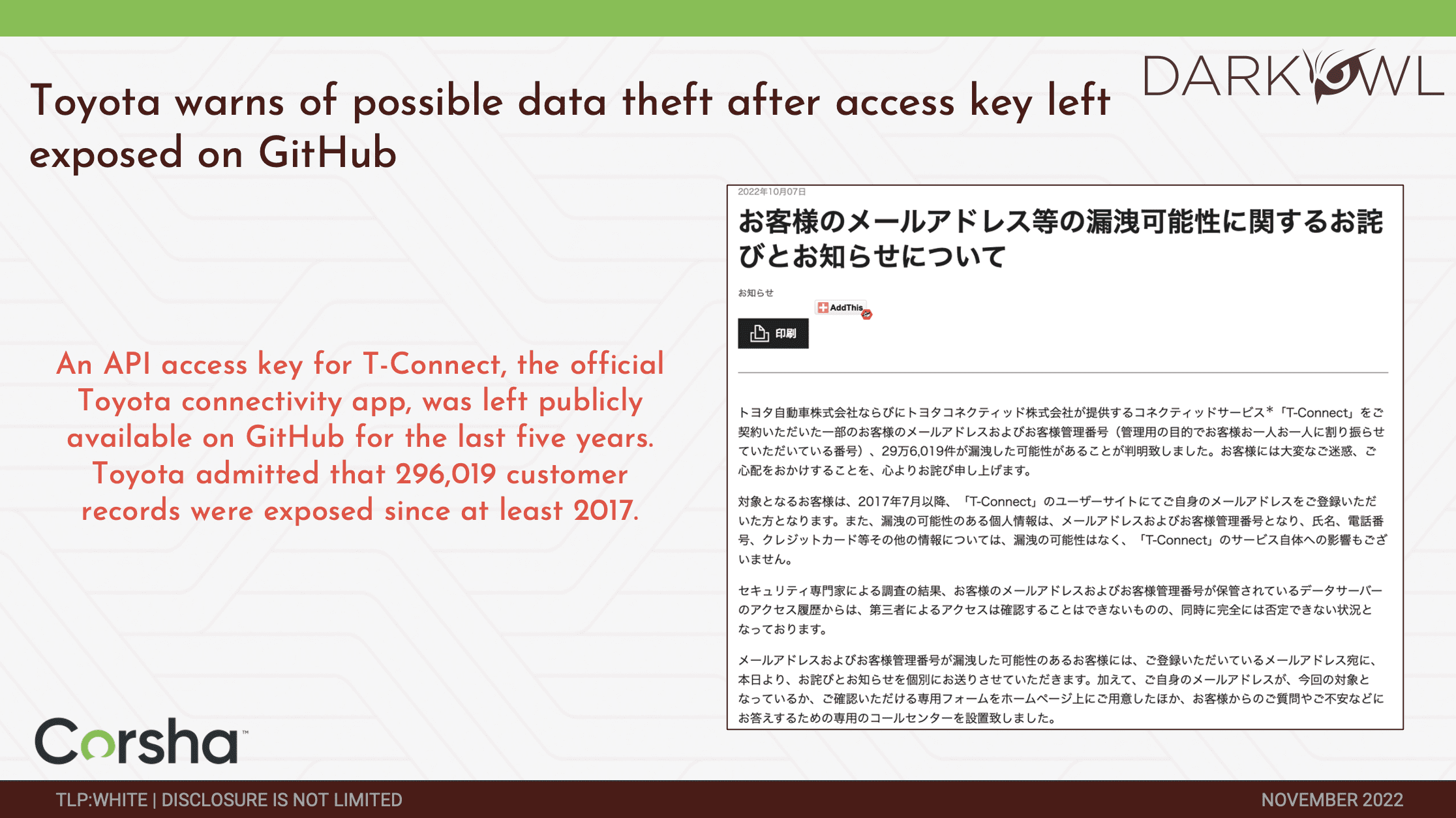
Increasingly we are seeing these types of data showing up on the dark web and being leveraged to execute breaches against organizations, like Toyota. Recently Toyota was notified of a breach where they had an API access key for T connect system. That’s part of their connectivity app to give things like wireless access and so forth to vehicles, and apparently, they had inadvertently checked in a hard-coded API secret into a repo about five years ago. It’s been available for five years in a public repo. And then they just released that over 2,900 records were exposed since then, giving access to customer names, customer information, and so forth. This is one example of what the threat landscape looks like and what the implication can be of API credentials getting into the wrong hands.
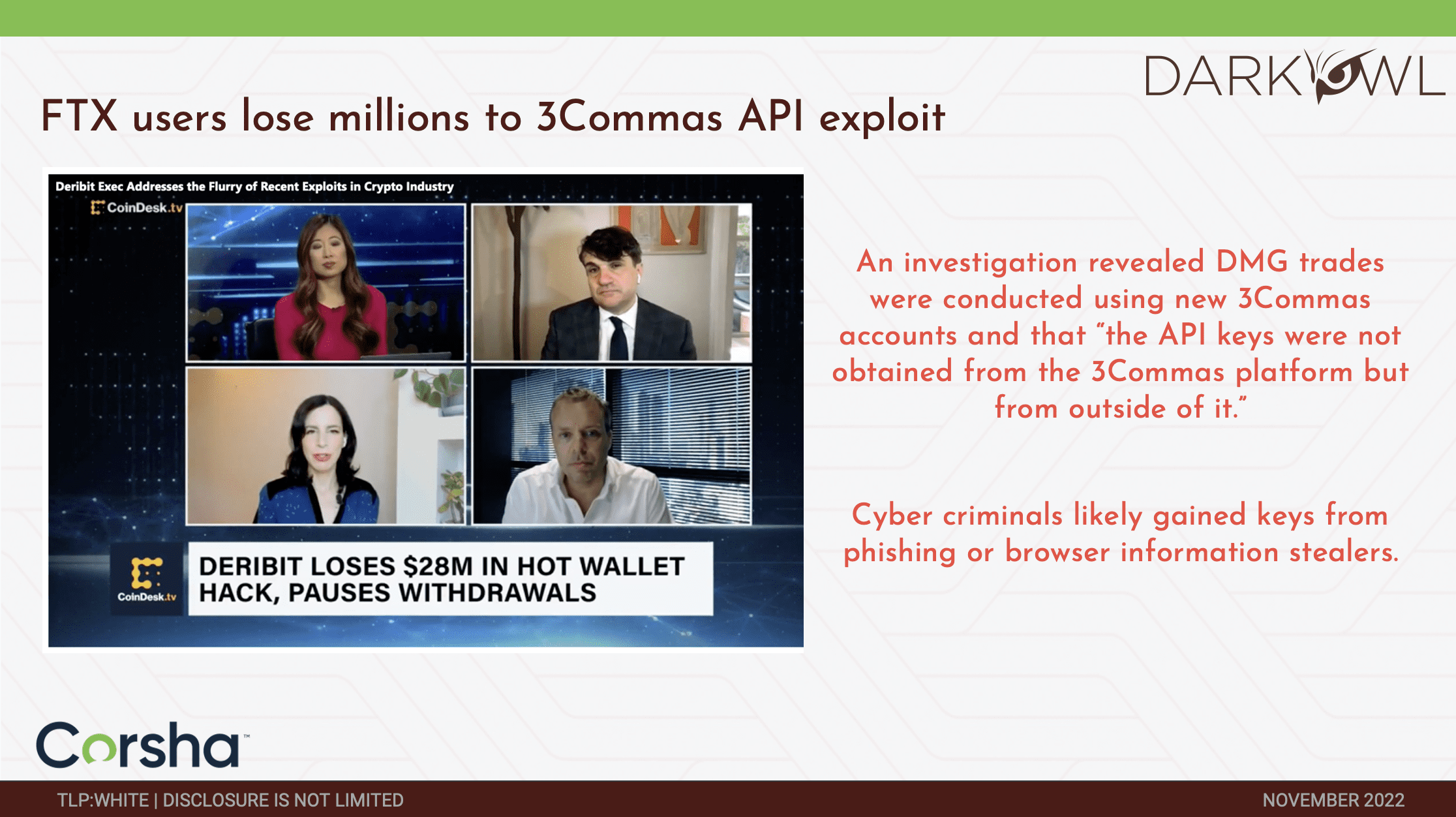
Similarly, recently FTX and 3Commas revealed that an API exploit was used to actually make illegitimate transactions, to FTX transactions. And this was done using API keys that were obtained from essentially users and phishing attacks actually accessing other systems. Right, so 3Commas, the platform came out and said that the API keys were obtained from outside of the platform, but certainly still pose the risk of being able to then be used off-environment, unauthorized, to then make financial transactions. These trades were basically from keys that were gained from phishing and browser information stealers.
Kathy: We’ve had a questions come in on these first couple of slides. Someone would like to know, is the fact that APIs are being targeted – is that a relatively new phenomenon?
Anusha: That’s a great question. It is an increasingly leveraged phenomenon. I wouldn’t say that it is new necessarily, but it is increasingly leveraged. Because APIs tend to be an underserved element with respect to cybersecurity postures of most enterprises. Increasingly organizations are relying on APIs. As they look towards digitally transforming application ecosystems into microservices, APIs end up forming the backbone of communication and application ecosystems. And further, more and more organizations are moving towards cloud, moving towards ephemeral scale, and that just creates a proliferation of environments where these credentials are potentially obtainable.
Mark: And that’s echoed by what we’re seeing in the darknet where discussions around API exploits, API keys, stealing API keys, and selling them is a relatively new phenomenon in the darknet over the last couple of years. We’re seeing the same thing from the criminals’ perspective that Anusha is observing in real life.
Anusha: Absolutely. I would come at it from the perspective that we see the movement of organizations using more APIs, but you’re absolutely right from an exploit perspective. It is fairly new. And it makes a lot of sense, they tend to be large types of information. With the automation it’s easy to lose track of what’s legitimate and what’s not. Great question.
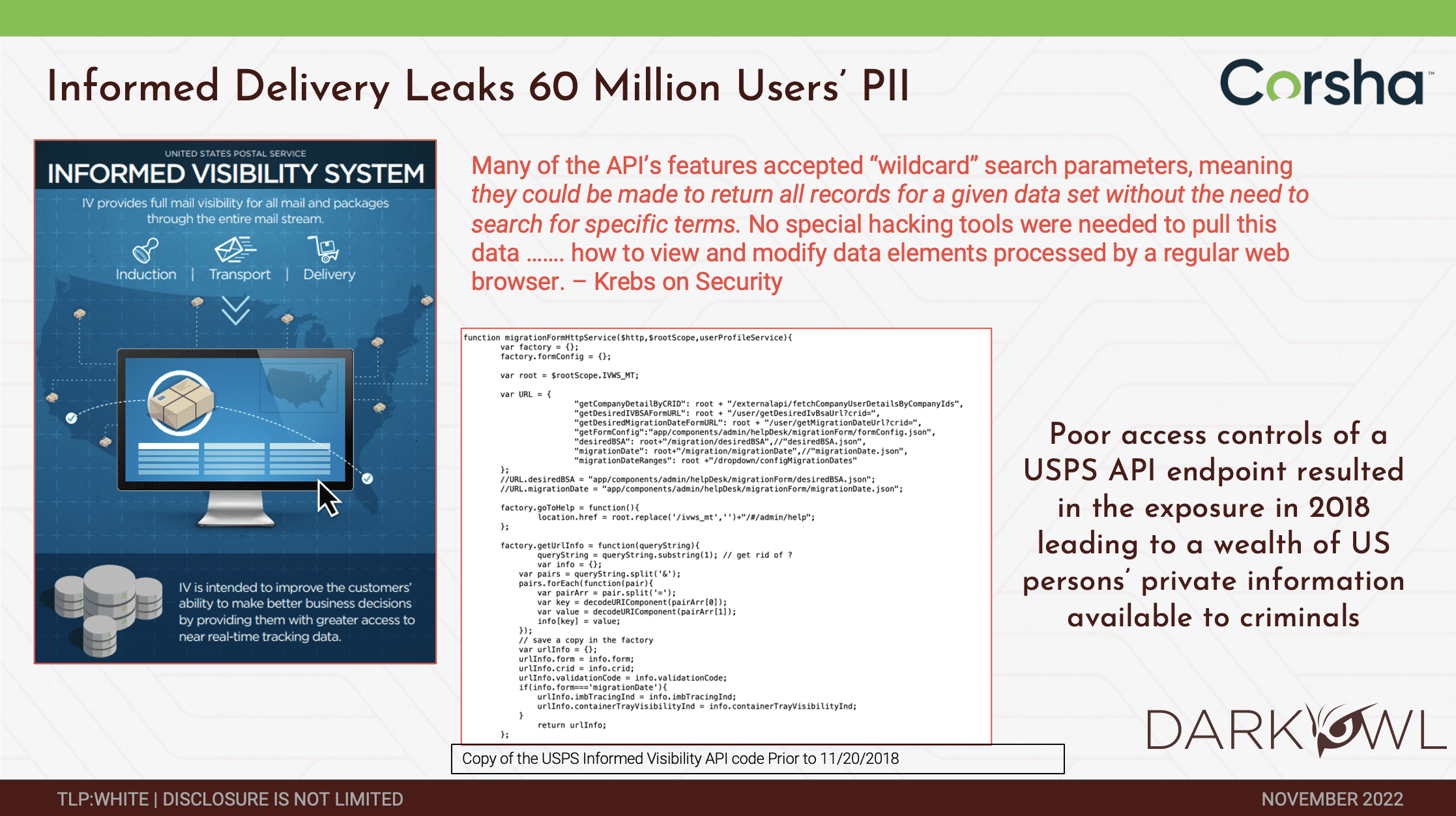
Another one, this one was actually a 2018 leak where it was the USPS API endpoint. And in this instance, it was more of an authorization vulnerability where if someone has a USPS account they could actually change search parameters and do a much more expansive search and essentially get records for an entire data set without being limited to exactly what they should be seeing. It’s both on the authentication side but also on the authorization side in terms of how these credentials are provisioned, leveraged, and so forth.
With that, let me hop into Corsha and tell you about our story and why we’re going after this problem space. Both myself and my co-founder come out of the DoD intelligence world. We’re focused on: how do we stop these breaches? How do we prevent unauthorized access to sensitive systems and services? And [we] decided to start course at the intersection of machine identity and API security. A lot of our early customers are out of the Department of Defense and we are working closely with Gartner to define this category and to define the space, if you will. What we’re finding increasingly is that API authentication, authorization, and security in general substantially lags behind all of the resources, effort, and human capital, put into human identity and access management. Now we need to think of these machines as entities, and as the same first-class type citizens as humans because they are accessing systems and services at a far greater rate and at a far greater impact even than just humans logging into accounts. So we started CORSHA and we’re very focused on how we can help with this API credential and API identity problem. I’m probably telling a lot of folks that are online something that they already know, which is that today API secrets are just glorified system passwords. They are largely static, often shared, rarely rotated, and don’t have a lot of good hygiene around them. They get leaked, sprayed, and sprawled across tons of environments. Mark, I’m sure you’re probably seeing this on the other end in terms of where they’re coming from, whether it’s CIC/D pipelines, whether it’s things like logs, deployment or cloud platforms, or even team collaboration sites. We already saw an instance with Toyota of GitHub. But I would venture to say that most organizations, just for the ease of sharing, probably inadvertently have leaked API keys, even internally, across systems. Because today the model of authentication is largely static, they’re ripe targets for adversaries.
Kathy: A question based off this slide: can’t secret managers like Vault or KeePass prevent these attacks from happening?
Anusha: It’s a great question. To some degree. They provide a secure mechanism to store the keys internally. But, oftentimes these APIs live in hybrid environments even in the control of hybrid parties. You may have an API that you expose to a partner, a vendor, or a customer. You would then have to rely on them properly leveraging a vault or a password manager or maintaining good hygiene around secrets to access your systems and services. So that’s part of the challenge here, is that vaults and password managers tend to be very environment or entity-controlled specific.
Because we’re using these static, essentially bearer model credentials, for authentication and even authorization, they are almost acting as proxies for machine identity. And the challenge is that they’re not very strong proxies because they are static and they’re difficult to maintain hygiene around. Whether it’s a key, or a token –like an O-auth token, a JSON web token, or even a PKI certificate –because they essentially prescribed that bearer model of authentication where “as long as I hold it, I can leverage it, it doesn’t matter where I’m coming from,” they turn into ripe targets for adversaries. I’ll stop here and say that when we talk about a machine, what are we really talking about? In our terminology we like to think of it from the zero-trust approach to it where it’s a non-person entity. Anything where you’re trying to access a system or service and there isn’t a human identity to back that access is where the API authentication approach breaks down a little bit. Whether that’s a Kubernetes pod, a docker container, VMs, even physical IoT devices –those tend to all be areas where static credentials end up getting leveraged in some way, shape, or form. Increasingly we’re seeing that these are the new attack sector vector that is increasingly in vogue.
To give you a very quick overview of what we are doing at Corsha, what we’ve done is we’ve come up with an API security platform where we can pull some lessons learned from the human identity and access management space. And we’ve come up with a way to not only do dynamic machine identity for API clients, but then leverage that to do fully automated MFA for machines. Think of a second dynamic factor where you can make sure that API calls are going with one time use MFA credentials. This gives you a lot of those nice benefits that we’ve seen on the human side with MFA where now you can pin access to only trusted machines. Even if a key inadvertently gets checked into a public GitHub repo, if MFA is enforced as a secondary factor, you’re okay there. That’s the idea: to elevate these API clients as first-class citizens, regardless of what their form factor in a way that is easy to adopt, easy to integrate, no code change, so that it doesn’t place burden on DevSecOps teams and make their day to day easier. So that they’re not having to worry about things like credential rotation as part of their workflows.
Just very high level, the essence of what we are trying to provide is security, visibility, control, even the ability on a fine-grained level to do things like start and stop access for a client. That’s a little bit of a difference with, say, this approach and say a vault. Because if you give an API key to a third party, you don’t necessarily have control over their vault. But with machine-driven or an identity-first approach to it, you can say, okay, from a control plane I’m going to dynamically start and stop API access for this collection of machines. And in that way have the expectation of access matching your threat surface. That’s a quick overview of CORSHA and the product and the problem space. I would love to turn it over to Mark and hear more about DarkOwl and what you’re seeing on the Darknet.
Mark: Thank you. The darknet is an interesting place and DarkOwl was set up specifically to allow organizations to monitor the darknet for threats to their core missions. As you can see in the lower right hand corner, our clients include many of the world’s largest cybersecurity companies who effectively use our platform and use our data to monitor on behalf of their clients. We also work, as does Corsha, with various agencies in the US Government. What we do is we go into the darknet at scale and we extract data at scale from tens of thousands of darknet sites on a daily basis. We index that data, we store that data, and we make that data available to our clients and make it searchable to our clients.
The question I get is what really is the darknet or the dark web? The two terms are conflated.
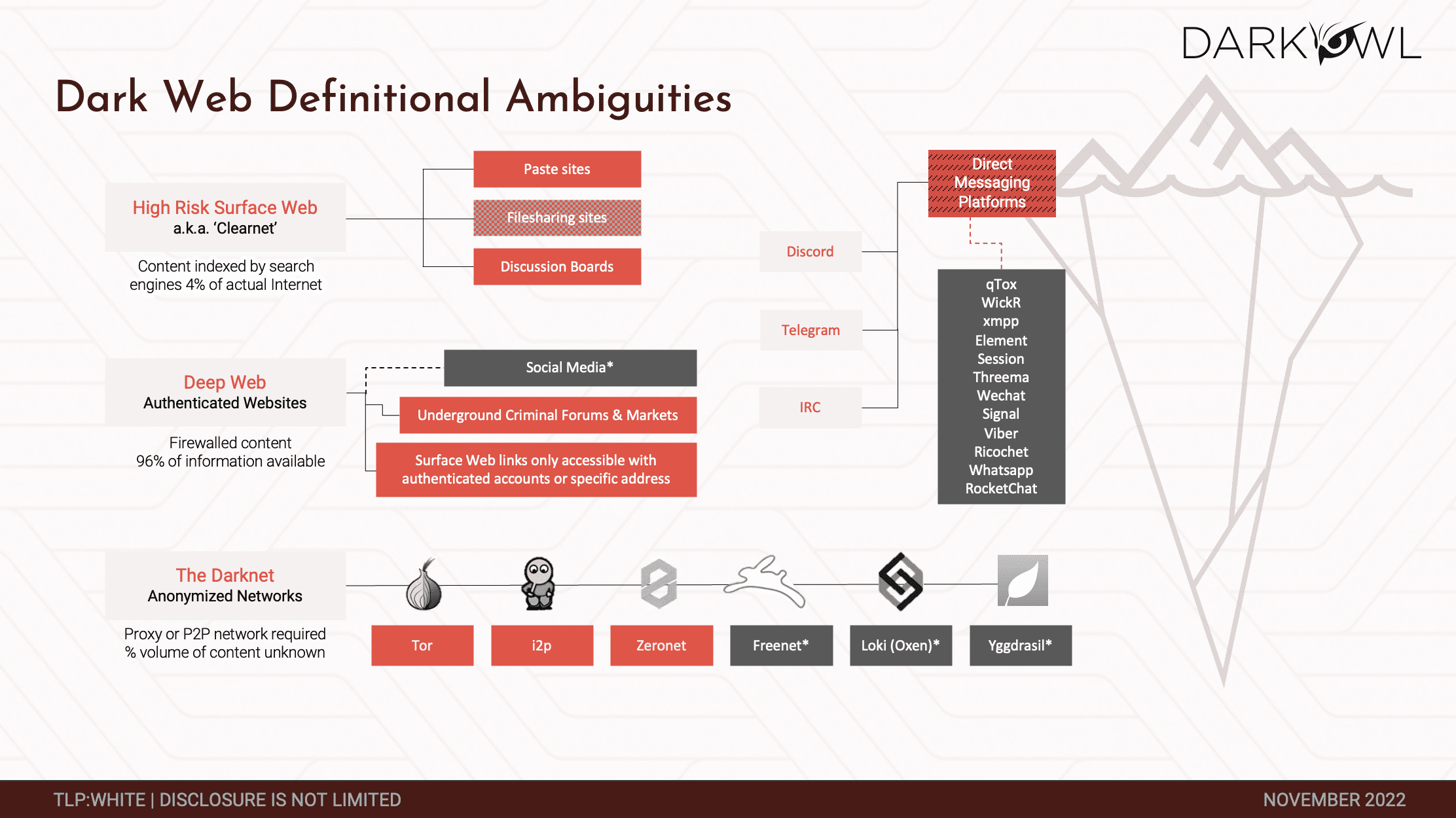
We all spend most of our time in the surface web. What you can search for off of your Google browser is effectively the search web. It represents a relatively small percentage of the data that is available by the internet, in spite of the fact that if I search for any term I’m going to find thousands, if not tens of thousands of results on my Google browser. It’s actually a relatively small percentage of the data that’s out there. Most of the data is fire-walled and it’s in what we call the deep web. My bank account information is available to me because it’s authenticated, I have the credentials, but it’s not available to Anusha and vice versa. By volume, most of the data that’s available via the internet is actually in the deep web. We specialize in the darknet, which is below the deep web. The darknet is dark for two reasons. It’s dark because you can’t get there from your Google browser. It usually requires a specialized browser or specialized access. What it does is it obfuscates user identity. Oftentimes the traffic is itself encrypted. And because of that, it is the perfect environment for criminals to operate in. Anusha and I can conduct a transaction, we can have a conversation, we can conduct a criminal transaction, buy or sell exploits with each other, drugs – there are any number of other things that we can do. A law enforcement agency could be sitting in the middle of that and see the transaction go through and see the discussion and never understand who I am and who Anusha is. And if you add in cryptocurrency on top of that, we could pay each other in an anonymous fashion. As a result, the darknet has become a haven for criminal elements.
At the bottom of that page, you’ll see Tor, I2P, Zeronet. Everything in red is data that we at DarkOwl collect from. We also collect from certain deep websites and some surface websites which enrich our darknet data. Increasingly, especially with the Ukraine-Russia war, these direct messaging platforms, such as Telegram and IRC are becoming destination points for criminals to operate in and we collect data from those as well.
Kathy: Mark, before you move on, an attendee would like to know, how big is the darknet?
Mark: I wish I had an answer to that question. We don’t know how big it is. We do know that Tor was the original darknet. It is now one of many darknets. The Tor project actually publishes data on users, number of users, numbers of connections to the Tor network, and number of sites.
Year on year, it continues to grow significantly. There are a number of sites like I2P, Zeronet, Freenet, and these other new sites that have grown. We don’t know how large it is. We have been told that DarkOwl has the largest commercially available archive of darknet data that’s available. I couldn’t prove that to you because I don’t know what the denominator is. But we know that the darknet is growing in terms of both customer usage and transactions that take place.
Very briefly, this is the kind of data that we collect. The data that most people are familiar with is at the bottom of this slide. We hold somewhere around 9 billion email addresses that we’ve collected over the years, 1.8 billion IP addresses. Those are oftentimes IP addresses or networks that are being targeted. A range of credit cards, crypto addresses, and so on. It’s a big database that we have, and it’s updated continuously and has been since we stood the company up five years ago. Then we make our data available by a number of APIs as well as a user interface for the analyst community as well. But to give you a sense, just in the last 24 hours we’ve indexed and put into our database 1.3 million documents. That gives you a sense of the scale of the type of documents that we’re dealing with.

More relevant to this conversation, though, is the next slide, which is, what are we seeing in the darknet that is relevant to the issue around API security? And the answer is a lot. We’re seeing that threat actors in the darknet are discussing stolen API secrets, keys, they’re trading the session tokens, and they’re openly discussed in these closed communities. This is a hot topic for the criminal elements in these communities. There are man in the middle attacks, there are injection methods being discussed and actually traded. Anusha and I would get into one of these forums, we’re both criminal actors, and we would discuss how I mounted a successful attack using this method. And she’ll say, can I buy that method from you or can I borrow it? Let me try it on a target that I’m thinking about. We see that ongoing. JWT authentication bypass methods are oftentimes discussed in detail. That’s been a real wake up call for me personally, seeing how creative criminals are being in these methods that they’re developing. Tools are shared.
Interestingly enough, and not particularly relevant, but the DDoS services are sold. API DDoS services are sold for cheap. One of the things we’re seeing broadly in the darknet across all sorts of threat actors is the migration of threat actors to actually selling out their services and renting them out on a monthly basis. This is just an example. We’ve seen Kubernetes targeted especially. It’s a distributed environment, so there are some vulnerabilities that the threat actors are using. Then hacking courses on and on and on.
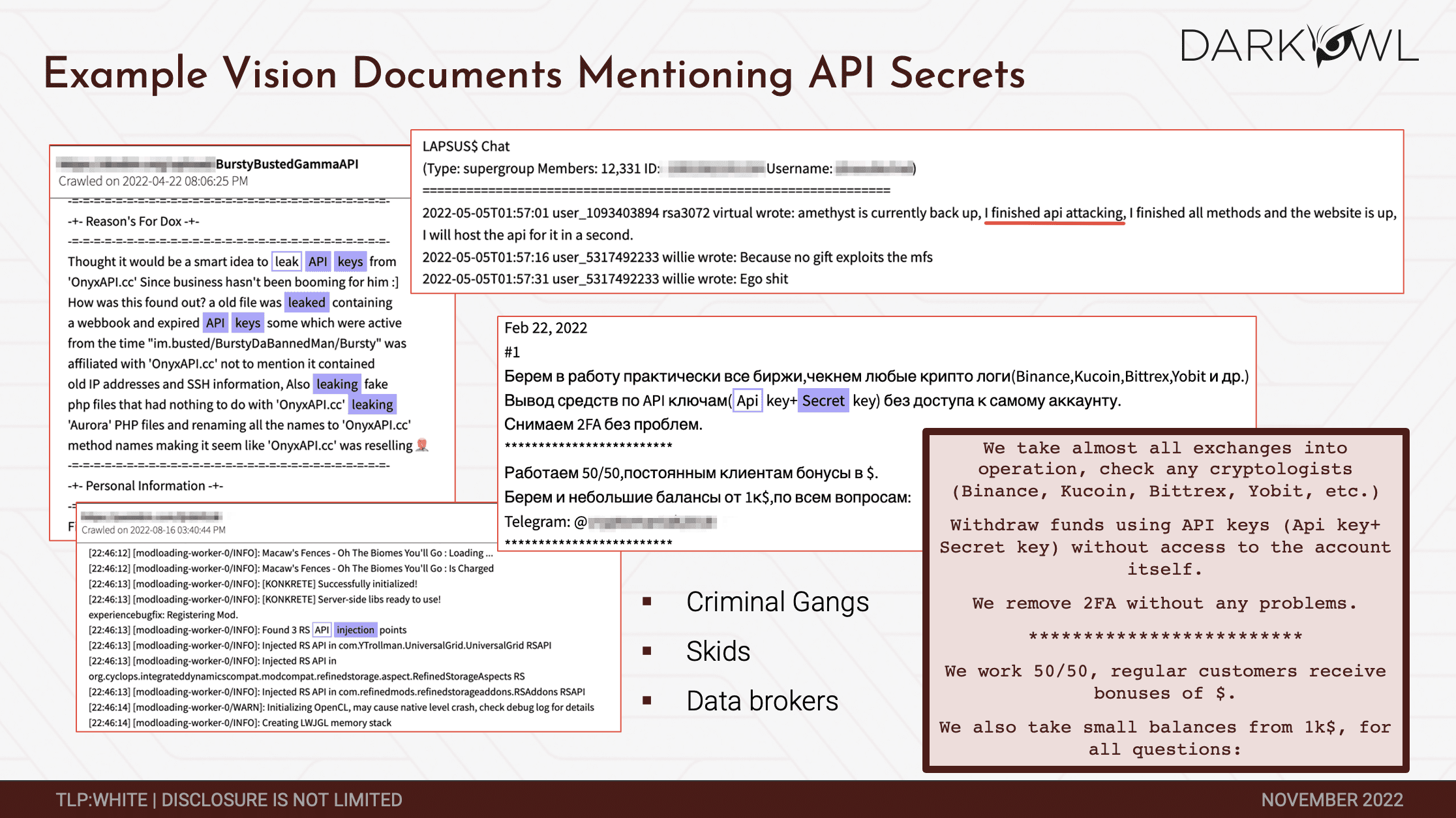
These are some screenshots of some of the discussions that we have seen in the darknet. In the upper left you’ll see this discussion around leaking API keys. In the middle of the slide, you’ll see Russian threat actors describing API keys as well as the secret keys and making the secret keys available. I think those were stolen. In the lower right. I love this. You know, we figure out a way to withdraw funds using API keys without access to the account itself and on and on and on. If you get onto our platform and search for any of these terms, you’re going to find quite a lot of discussion among the threat actors and the criminal gangs around this. And you’ll see data brokers actually selling keys. Selling actual access to networks. The conclusion is that Darknet is rife with discussion around the very threats that Corsha is targeting and that was set up to respond to. Anytime you see this kind of activity, any time you kind of see this discussion going on in the darknet, you know you’re on to something. So your customers made some smart choices here in new shows.
Anusha: We appreciate that, Mark. I will say it is very interesting to see all of the discussion and the activity around Kubernetes. I think that might be even a fun double click into another session to do, because it is turning into a foundational layer of most organizations transforming their application ecosystems. It would be fantastic if we could get ahead of that.
Mark: I’d actually like to talk to the founders back at Google. It was right around 2014, if I’m correct, about Kubernetes, and ask them whether they ever had a conversation around security right at the outset. Because most people, most developers won’t. And it’s not a criticism. It’s that just most developers won’t do it. They’re thinking about how to build a scalable environment for whatever their mission is. They’re not thinking about how five or six or seven or eight years down the road, somebody’s going to be trying to attack that environment.
Kathy: We’ve actually had a few questions come in. One of our attendees would like to know: what specifically can be done from a security perspective to prevent an API attack?
Anusha: Some of it is obviously having good hygiene around primary credentials. Having policies in place for things like rotation. Certainly using a platform like Corsha as a layered defense so that you have a way to uniquely identify and control each API client. Is a very sound approach to a lot of this activity that we are seeing on the darknet. Other things like making sure that API access is least privileged, so having notions of authorization in there. Just like when you have a given user, you give them roles, and not all users have access to the same information and services on the system, APIs and API clients have to be dealt with the same way. And having ways to revoke secrets and revoke access are very important. It’s about drawing a lot of those parallels that we have with human identity and access management but into the world of APIs.
Kathy: Thank you. We also have a question of: how can security or engineering teams get better visibility into how their API secrets are being used?
Mark: One way to do that is to use a platform like DarkOwl’s platform to actually monitor the environment on an active basis. Oftentimes, you will see threat actors discussing targets by name or by IP range or by other things. Look in the upper left hand side of this slide, right there is a discussion around a very specific key from a very specific
My point is, any time you’re thinking about security more broadly, there are a number of hygiene elements that have to go into place. One of those hygiene elements is monitoring this environment where criminals are actually plotting attacks in a wide variety of different contexts, not only in the API environment. We see active threats, active exploits under way. We see targets being identified and threat actors saying, all right, that’s great, I’m going to hit them. You have to have some eyes on that environment.
Kathy: Thank you. We did have one more question come in, and that is, what should a team do today if an API secret is compromised?
Anusha: That is where having a good platform for observability in place is really important because you want to know where that API secret could have been leveraged right and have the ability to quickly revoke and rotate it. It’s both understanding impact of the leakage or the stolen credential and then mitigation strategy of how to revoke it, how to rotate it, with obviously a little downtime as possible. I think for observability using a platform like DarkOwl is really helpful because you can see the extent to which it may have been leaked or compromised as well.
Mark: Thank you, Anusha. It’s a pleasure doing this. Let’s do another one in the future once we find more threats.
Anusha: Absolutely. That would be fun. Thanks so much for the time. And thanks to everyone for listening in.
About Corsha:
Corsha is on a mission to simplify API security and allow enterprises, developers, and DevSecOps teams to embrace modernization, complex deployments, and hybrid environments with confidence. Our core technology is dual use, designed for widespread adoption, and easy to configure and deploy to both commercial and government customers. Corsha has a strong engineering team with deep expertise in distributed ledgers, cryptography, security principles, orchestration technologies, and software design. Contact Corsha.
About DarkOwl:
DarkOwl uses machine learning to automatically, continuously, and anonymously collect, index and rank darknet, deep web, and high-risk surface net data that allows for simplicity in searching. Our platform collects and stores data in near realtime, allowing darknet sites that frequently change location and availability, be queried in a safe and secure manner without having to access the darknet itself. DarkOwl offers a variety of options to access their data.
To get in touch with DarkOwl, contact us here.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















