Brief primer on voter registration info on the darknet
For the last two years, U.S. voter registration information has been widely circulated across darknet forums and channels for potentially nefarious purposes. Earlier this year, DarkOwl detected U.S. voter registration databases for the states of Michigan, Florida, North Carolina, and Colorado being shared freely. Some databases are packaged in sets of key states and sold on popular deep web forums and marketplaces by popular darknet vendors such as GoldApple.
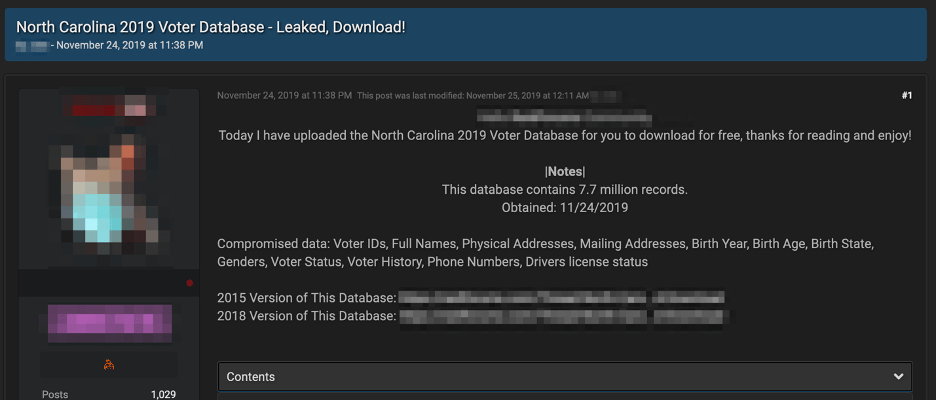
This is certainly not the first exposure of U.S. voter registration data on the darknet en mass:
-
In December 2015, millions of personal voters’ information was exposed on the darknet, when security researcher Chris Vickery and databreaches.net discovered over 191 million U.S. voters’ data available after a marketing firm supporting one of the political campaigns had a mis-configured database. The owner of the database was never identified. (Source)
-
In summer 2017, another 198 million voters’ information was exposed after researchers discovered an unprotected AWS S3 bucket containing the voter rosters. The voter information had been archived by Deep Root Analytics, TargetPoint Consulting, Inc., and Data Trust, three data mining companies supporting the Republican Party. Rosters of statewide voter data are made readily available to political campaigns and their marketing affiliates for free for targeted campaigning and canvasing. The value of such databases, especially one containing hundreds of millions of U.S. voters’ personal data would be worth several hundred thousand dollars to darknet cyber criminals who could leverage the information for traditional financial cyber crime.
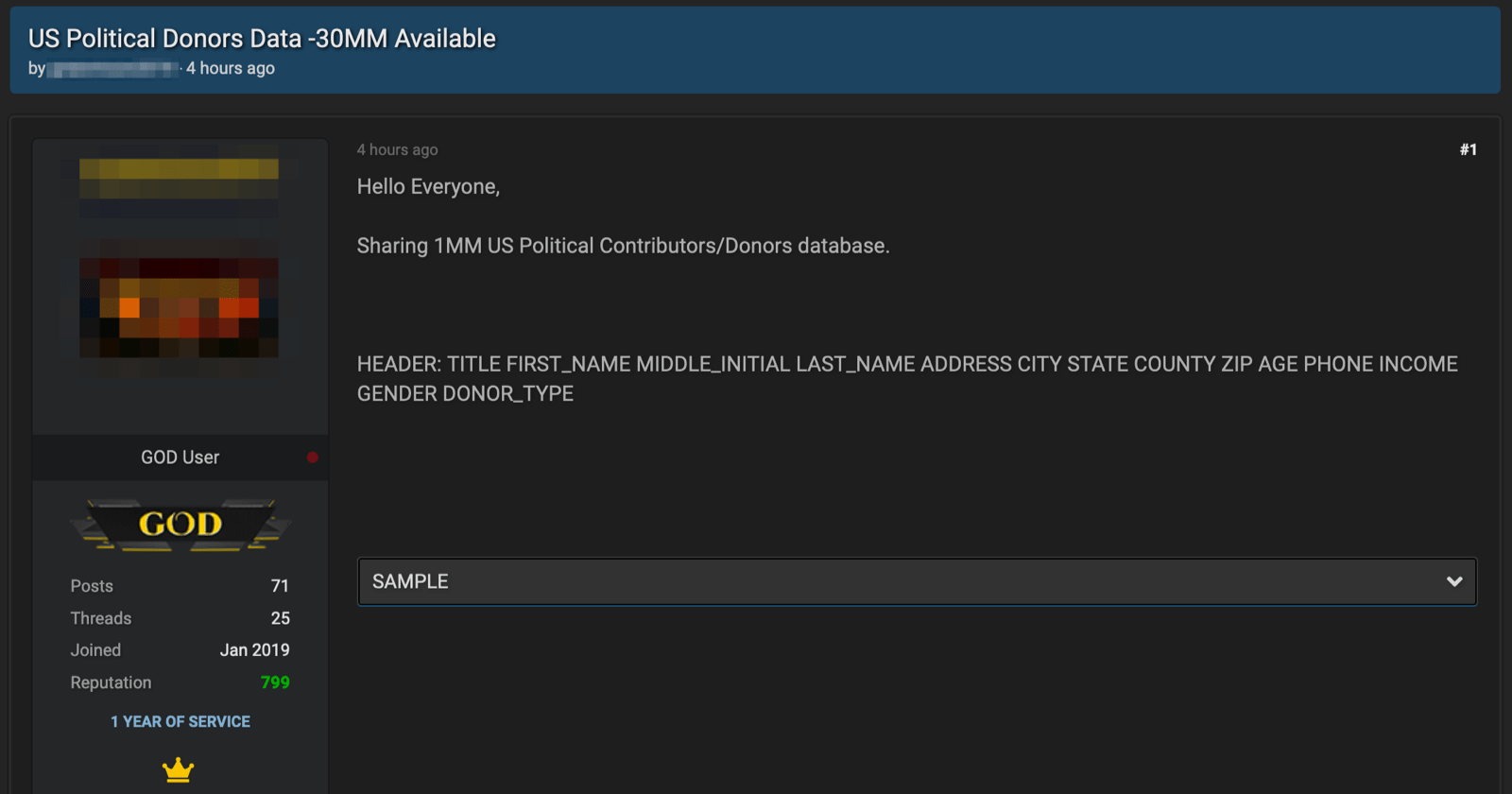
Interestingly, just earlier this month another darknet user also shared a database containing the personal information for millions of political contributors and donors on a popular hacking forum. The information in the database included the full name of the donor, physical address, age, phone number, income, gender and donor type. The user did not specify which campaign this data was stolen from. The post was removed by forum moderators as other users suggested the author was a “criminal hacker” and this data was acquired through malicious intrusions of a political database. The post did not specify where the information originated or which campaign it was from.
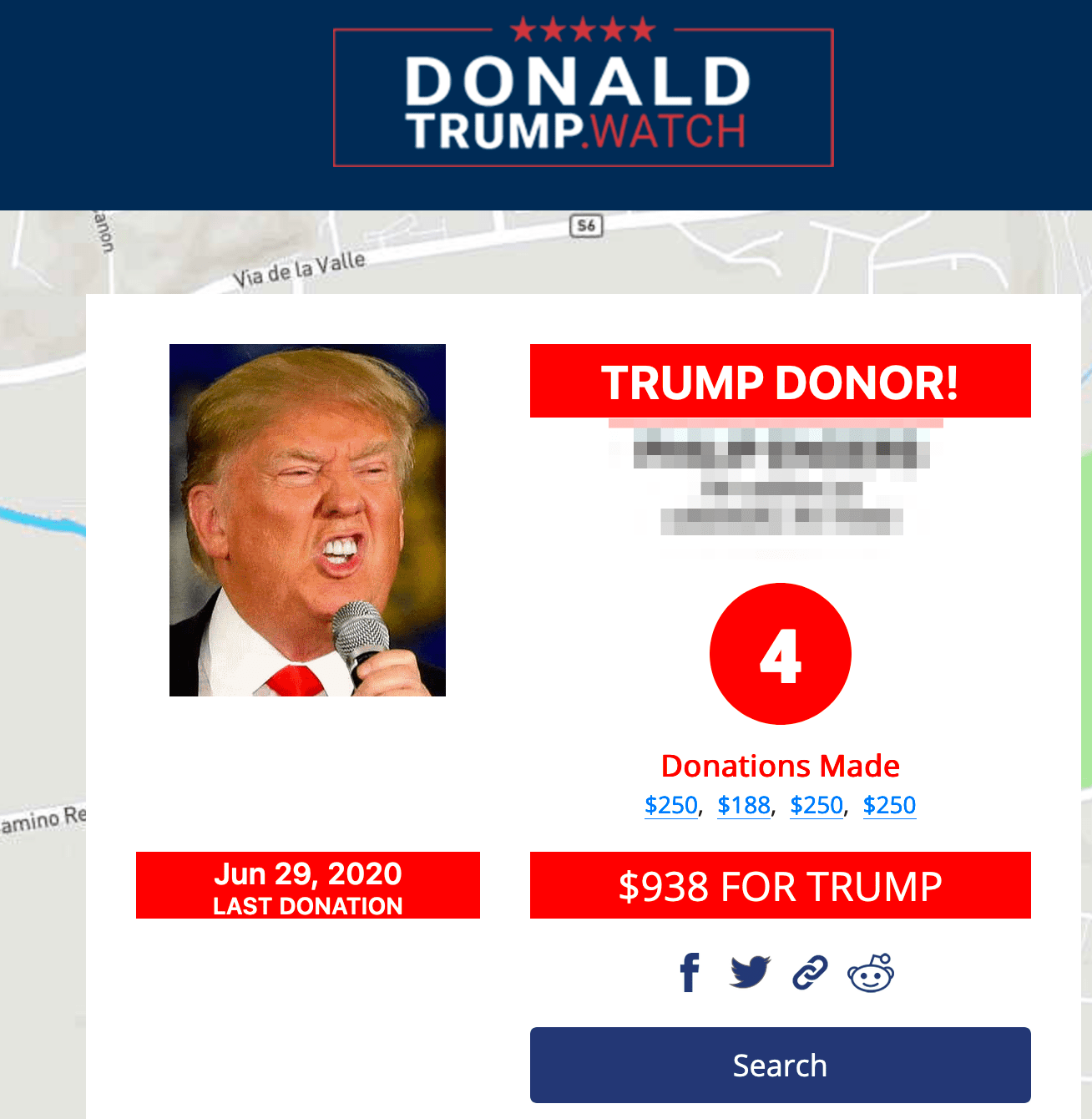
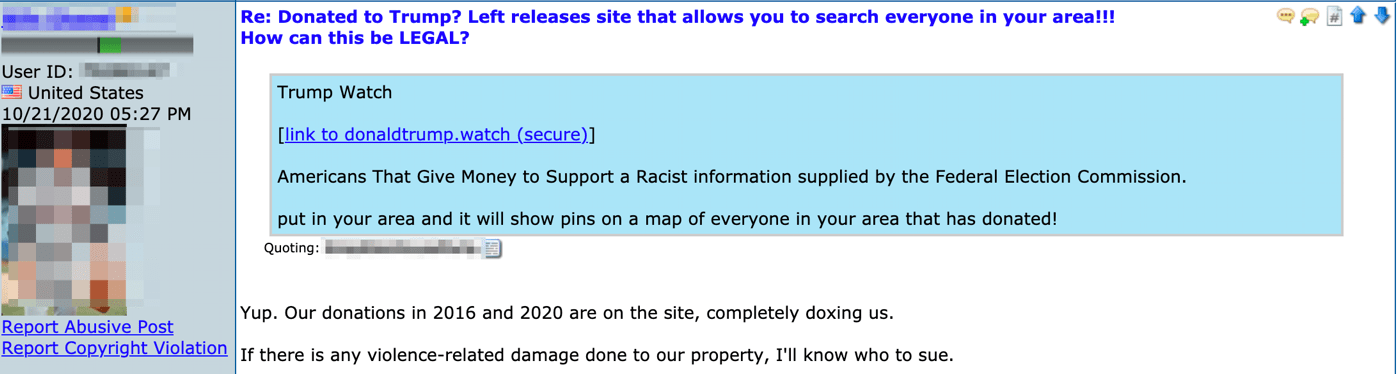
In the meantime, DarkOwl analysts have witnessed several conversations on popular right-wing leaning deep web discussion boards regarding the domain: http://donaldtrump.watch. Anonymous users and supporters of Trump stated the domain was active and contained personally identifiable information of the President and GOP financial contributors. WHOIS domain history has a redacted owner for privacy and suggests a 2018 creation date; archives of the website from late 2019, suggested it was created in response to the President’s Impeachment and is simply a “Donor locator map for the impeached Chief Executive Donald J. Trump. – Data Provided by the FEC.gov.” The Federal Election Commission does record all contributions made to any candidate, campaign contributions are not private, and the data held by the FEC can be requested typically for marketing and canvasing use.
The website is setup with an alphabetized address and name search capability indentifying contributors by name, their address, the specific dollar amount of their donations, and last donation date. There are numerous postive and negative comments about the Trump donor website across deep web and darknet discussion groups. Some commented on their neighbor’s donations.
Huh, two of the neighbors I like each donated about a grand to Trump. I didn't take either of them for Trump supporters. One guy in my neighborhood is unusually enthusiastic, it would seem.
Many users stated the information on the website was false, incorrect or dated back in 2016, while other users confirmed their families’ information was correct on the website and expressed concern about potential property damage. Analysis of the donations suggests the information is accurate up through August 31, 2020.
Regardless of exactly when the website appeared and the motive behind its author’s, the website information could be used to target, intimidate and frighten Trump supporters similarly to how earlier this month the FBI announced attribution to Iran for an email campaign sent to non-Trump supporters in Florida, threatening them to vote for Trump and signed by the controversial right-wing extremist group, The Proud Boys.
The BlueLeaks files, released earlier this year and containing files from hundreds of police departments, speak of how state voter registration data could be misused and specifically mentions how a malicious actor could leverage voter names, e-mail addresses, and telephone numbers to connect with new audiences and market personalize advertisements according to their views on specific topics, propensity to vote, and other factors. This information coupled with a foreign adversary’s disinformation campaign could be utilized to register fake social media accounts, seed content, and amplify distribution of content of interest to targeted audiences. [READ MORE]
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















