Cyber Risk Modeling: Introducing DarkSonar
April 18, 2023
Over the past few years, there has been an increase in global cyberattacks, with reports indicating that overall attacks were up 38% in 2022 from years previous. In the USA alone there was a 57% increase, while the UK experienced a 77% increase in cyberattacks. Many of these attacks result in data breaches and ransomware attacks, which cost organizations time and money, as well as long term negative effects such as loss of reputation.
On top of this, the average cost of a data breach has reached a record high of $4.35 million. The cost of a ransomware attack is $4.54 million, on average, not including the cost of a ransom payment. With cyberattacks on the rise, organizations need better intelligence to enable them to model risk and take mitigating actions, particularly small businesses which are three times more likely to be a target of a cyberattack.
Darknet data is a key source of insight into criminal and other nefarious activity. The darknet—or dark web as it is also referred to—is a layer of the internet that cannot be accessed by traditional browsers. Sensitive corporate information is regularly leaked or sold on the darknet. These sets of darknet data can be used to identify cybersecurity threats and calculate organizational risk. Understanding risk enables an organization to better be prepared for potential threats.
Cybersecurity Risk
Cybersecurity risk can be most simply described as the amount of potential the risk your organization faces against a cyberattack. The possibility of a cyberattack feeds several different corporate risk calculations. One of the biggest threats of a cyberattack poses is the loss or public exposure of data, which presents a significant risk to a company’s brand and reputation.
Stolen and leaked intellectual property can pose a significant risk to a company’s profit/finances/bottom line and competitive edge. In addition to loss of data, there is a direct risk to executives and key leadership from phishing attacks and stolen credentials. If the direct risk within a company wasn’t enough, there is also an indirect risk through third-party vendors and suppliers. To better map out cybersecurity risk, organizations need to model risk.
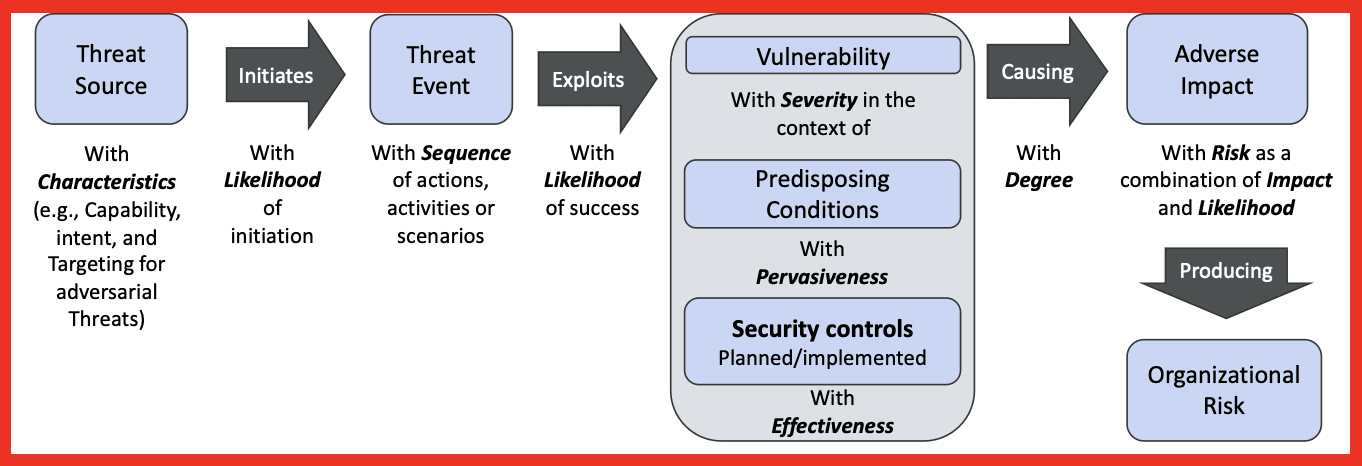
Figure 1: Generic Risk Model; Source: NIST
The figure above shows a generic risk model and the relationships between the components. In organizational risk calculations, threat includes anything that can cause harm to the organization. This includes threats from natural disasters, significant hardware or backup failure that triggers a disruption in services or production, and cybersecurity attacks by external malicious entities. Threat calculations are often tied to scenarios with likelihoods of occurrence that involve an adversary’s intent, capability, and targeting. To effectively model risk, organizations need to (1) model internal threats, (2) model external risk from third parties, and (3) determine the likelihood of specific scenarios. The risk is then calculated from a combination of impact and likelihood.
DarkOwl Data
DarkOwl provides a variety of data to model risk and threats to an organization:
Leaks/Data Breaches: Leaks, or data breaches, are aggregate data files of information obtained without the owner’s consent. This can consist of internal email records, usernames and passwords, personally identifiable information (PII), financial records, and more. Leaks are often sold for profit on the darknet, though they are sometimes posted and leveraged by criminal actors for means other than financial gain.
Dark web search data: Vision UI provides access to a variety of darknet and deep web resources. Additional capabilities enable the user to search for cve’s, construct searchblocks, etc. The platform provides the ability to fully customize darknet searches based on individual priorities and focus areas. Approximately 10-15 million pages/targets are crawled daily, with updated content becoming accessible to users in near-real time.
Entities: In addition to being able to search all collected darknet data, DarkOwl extracts entities such as IP addresses, credit card numbers, bank identification numbers, crypto addresses, email addresses, and credentials. This enables an organization to search specifically for relevant entities, such as server IP addresses and email addresses.
Group data: Vision UI enables a user to search for groups. Groups include chan, ransomware, forum, market, and paste data. Ransomware and forum data are particularly useful for determining organizational risk. Discussions of relevant software and exploitability of specific CVEs can assist an organization in determining potential unpatched vulnerabilities.
Telegram and Chat Platforms data: Telegram and other chat platforms data consists of encrypted, semi-encrypted, and open-source chats. DarkOwl has over 400 thousand telegram chats. Discussions between threat actors can be found on these chat platforms.
DarkSonar: DarkSonar is a risk metric based on darknet intelligence and measures an organization’s credential exposure on the darknet. It provides a relative risk rating for an individual email domain. The metric is based on email exposure using three parts of email entities: unique plaintext credentials, unique hashed credentials, and total unique email address volume with no credentials.
DarkOwl’s data can assist an organization with threat modeling, managing third party risk, and potentially predicting the likelihood of an attack.
Threat Modeling
Identifying threats involves creating threat scenarios consisting of threat events exploits caused by threat sources which exploit vulnerabilities which are weaknesses in systems. Vulnerabilities can be internal, such as an unpatched server or poor employee awareness, or external, such as a third-party vendor.
Threat vectors refer to the vulnerability pathway that cyber attackers take to gain access to an organization’s network. Regardless of the actor or the motivation, they will utilize one or more threat vectors to gain access to a system. Below, Table 1 gives a list of common threat vectors used by an adversary. Also included are the associated solutions that DarkOwl data offers to help to model risk and mitigate damage for each of these different threat vectors.
Table 1: The Most Common Threat Vectors
| Threat Vectors | Statistics | DarkOwl Data |
| Phishing Emails | – 61% increase in rate of phishing attacks in the six months ending October 2022 compared to the previous year and attacks are getting more sophisticated. – 90% of IT professionals believe email phishing is the top cyber threat to their organization due to sharp increase in email phishing. – 92% of malware was delivered through email in 2021. Phishing emails in particular were responsible for 90% of 2021’s data breaches. | – DarkSonar: Risk Signal – Entities: Emails, Credentials |
| Third Party Vendors/Supply chain | – 48% of organizations deem third-party relationship complexity as their main problem. – 54% of businesses do not vet third-party vendors properly and do not have a complete list of all the third parties who have access to their network. – 59% of companies experienced a third-party data breach. Only 16% say they effectively mitigate third-party risks. – 65% of firms have not identified the third parties that have access to their most sensitive data. | – DarkSonar: Risk Signal |
| Weak or compromised login credentials | – 80% of hacking incidents caused by stolen and reused login information. – 82% of data breaches involves a human element, including phishing and the use of stolen credentials. | – DarkSonar: Risk Signal – Entity Emails: Credentials |
| Brute Force Attacks | – Brute force is the most widely used initial vector to penetrate a company’s network. – Brute force attacks increased from 13% to 31% in 2021. – Over 80% of breaches caused by hacking involve brute force or the use of lost or stolen credentials. | – Vision UI: Company mentions – Entity Emails: Credentials: available data for credential stuffing for brute force |
| Unpatched vulnerabilities | – 60% of breach victims admitted they were breached due to an unpatched known vulnerability where the patch was not applied. 62% claimed they weren’t aware of their organizations’ vulnerabilities before a breach. – 75% of attacks in 2020 used vulnerabilities that were at least two years old. – 84% of companies have high-risk vulnerabilities on their external networks, more than half of these could be removed simply by installing updates. – 87% of organizations have experienced an attempted exploit of an already-known existing vulnerability. | – CVE Mentions: for relevant software and combination CVE mentions for 0-days – Forum data: discussions of malware development |
| Cross-site scripting (XSS) | It is estimated that more than 60% of web applications are susceptible to XSS attacks, which eventually account for more than 30% of all web application attacks. | – Entity IP addresses – CVE mentions: for exploitable web server vulnerabilities |
| Man-in-the-middle (MITM) | Nearly 58% of all posts on criminal forums and marketplaces contain banking data of others collected by MITM or other attack types. | – Vision search: company mentions – Entity IP addresses – Forum data |
| DNS Poisoning | A six year study of DNS data showed that DNS spoofing is still rare, occurring only in about 1.7% of observations, but has been increasing during the observed period, and that proxying is the most common DNS spoofing mechanism. | Entity IP addresses |
| Malicious Apps/Trojans | 46% of organizations have had at least one employee download a malicious mobile application which threatens their networks and data. | DarkSonar: for phishing attacks which often include links or attachments of malicious apps/trojans |
| Insider Threat | – Insider threats increased by 47% between 2018 and 2020. – 70% of organizations witnessing more frequent insider attacks. | Vision Search: searchblocks for insider targeted searches |
Examples
Email Exposure
DarkSonar provides a metric to chart an organization’s relative risk ratio over time. To demonstrate this, we have included several case studies using actual organizations that experienced cyberattacks. The example below looks at AMD, who publicly announced that they experienced a cyberattack in June of 2022 (as illustrated by the dotted line).
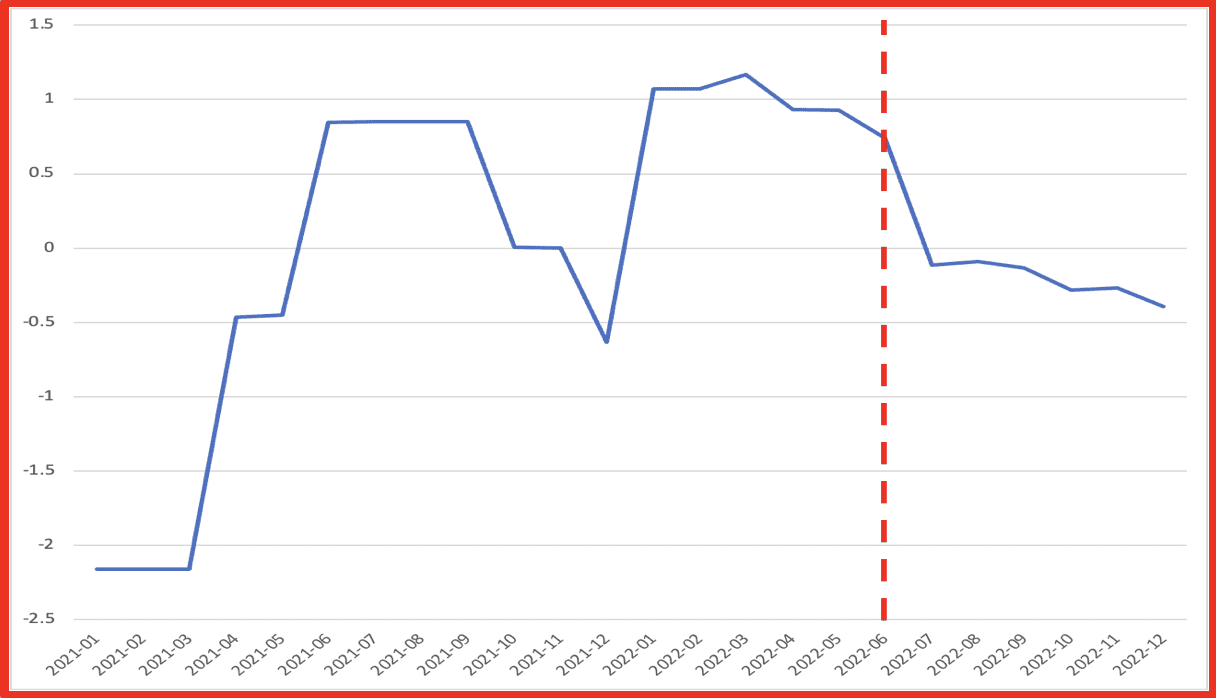
Figure 2: DarkSonar exposure for AMD over time
Figure 2 above shows that DarkSonar detected an elevated risk signal for AMD from January to April. This figure shows an elevated risk from January to April of 2022. An elevated score indicates that the exposure on the darknet has dramatically increased, which translates to higher risk. In this example, DarkSonar forecasts the attack that ultimately transpired with an elevated signal in the months preceding the incident.
Entity Explore
Entity Explore provides information about entities in DarkOwl’s entity database. Using the Entity Explore or the Entity API allows an organization to see all emails, IPs, credit card and bin numbers, and crypto addresses. Additionally, when viewing emails, all plaintext and hashed passwords can be sorted and analyzed. For financial institutions, credit card numbers and bin numbers provide a notion of financial exposure for their risk calculations. Organizations can also search for IP addresses of their sensitive infrastructure points to determine if and how those IP addresses are being discussed on the darknet.
The example below looks at Entity results for Honda.com and illustrates how a company can use Entity Explore to assess their credential exposure within Vision UI.
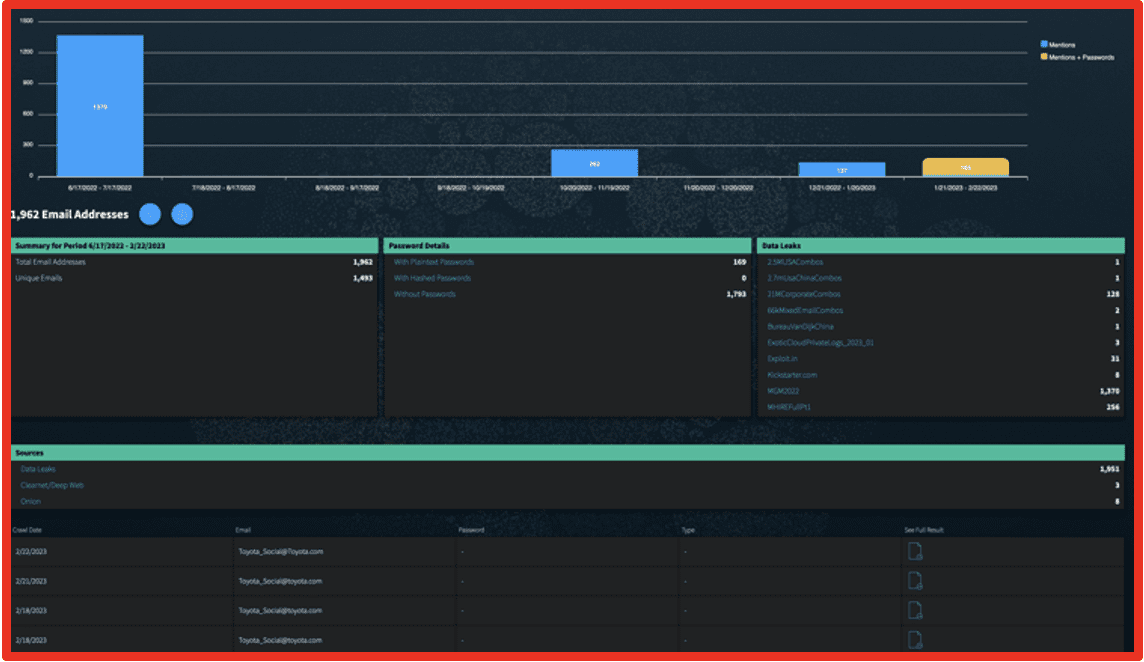
Figure 3: Email Entities for honda.com; Source: DarkOwl Vision
Vision Searches
Additionally, DarkOwl Vision UI provides tools to focus an organization’s search of darknet content. Group searches enable an organization to focus on forums and ransomware sites. Similarly, queries can focus on specific sources, such as telegram content. Search blocks provide terms that can be used to focus on insider attacks and exclude results from search engines.
After a recent product update, Vision now allows users to more easily search for specific CVEs. This enables an organization to find discussions of exploiting vulnerabilities relevant to software they run on their network. Figure 4 shows a forum discussion about an exploit for CVE-2022-30190, which is a Microsoft office vulnerability that hackers can leverage for remote code execution.
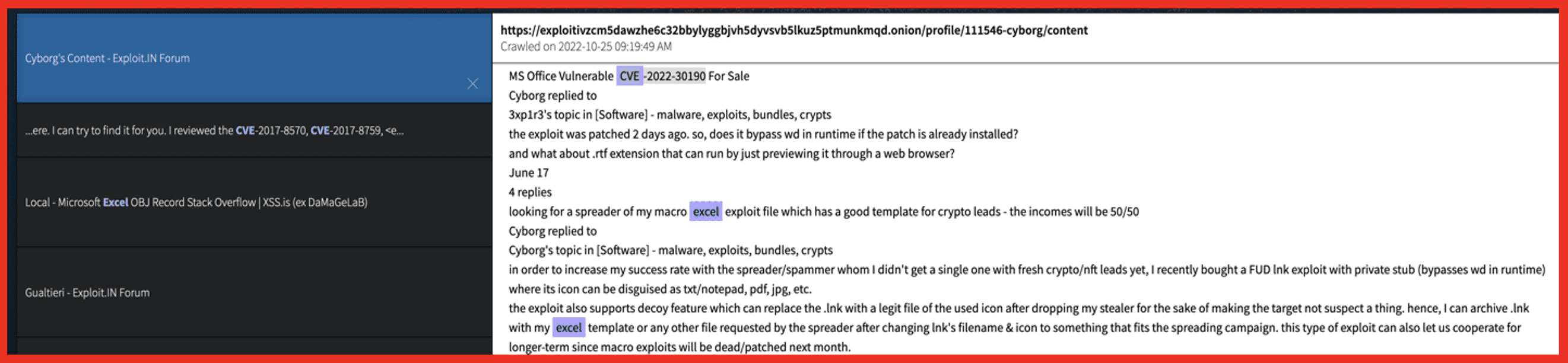
Figure 4: DarkOwl Vision search reveals an exploit based on CVE-2022-30190; Source: DarkOwl Vision
Manage Third Party Risk
As per the data shown in Table 1, third-party vendors pose a significant risk to businesses of all sizes. Most organizations don’t even know who has access to their sensitive information. This is in part due to the fact that, typically, an organization does not have adequate insight into the types of protection mechanism a third party takes to protect their data.
To fill in this gap, DarkSonar provides an organization with a risk metric for their third-party vendors based on email exposure on the darknet. This enables an organization to better understand the risk of a third-party.
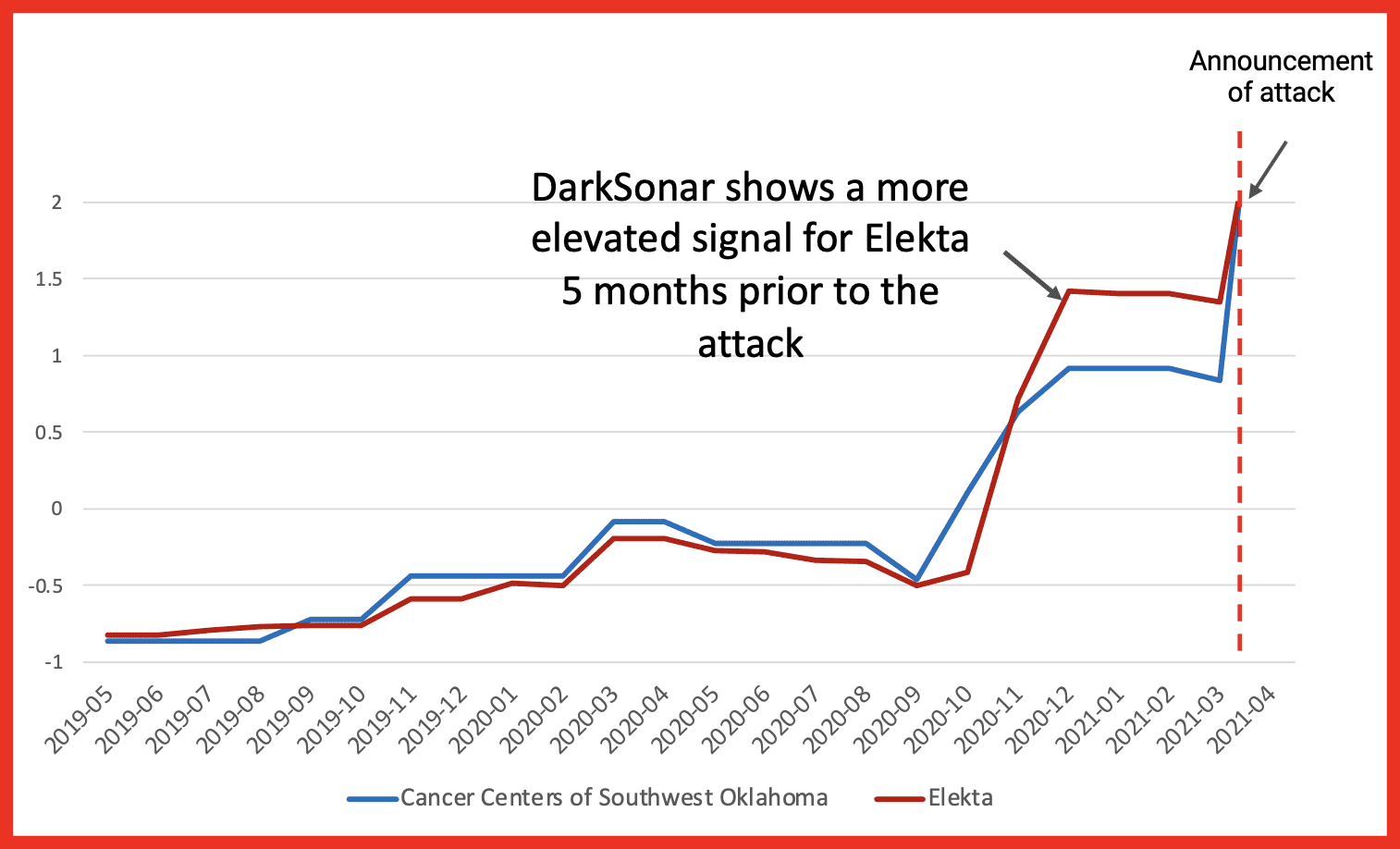
Figure 5: Example of a third-party vendor attack, where the Cancer Centers of Southwest Oklahoma’s data was compromised through third party cloud provider Elekta. While Both companies exhibit an increase in their DarkSonar signal, Elekta’s is elevated higher 5 months prior to the attack.
Figure 5 gives another case study example of how DarkSonar can be used to forecast a third-party attack. In this case, the Cancer Centers of Southwest Oklahoma’s third-party cloud-based storage provider, Elekta, was the victim of a data breach in April 2021.
During the attack, unauthorized personnel accessed the protected health information of 8,000 oncology patients from the Cancer Centers of Southwest Oklahoma. While both companies experienced an increase in DarkSonar by the time of the attack, the third-party vendor, Elekta, was elevated higher for longer prior to the attack.
Help Determine the Potential Likelihood of Threat with DarkSonar
Calculating organizational risk is a combination of the likelihood of a threat and the adverse impact it may have on your organization. Overall, DarkSonar exposure signals can help to indicate when the likelihood of a particular attack increases. In fact, in a study of 237 publicly disclosed data breaches and ransomware attacks from 2021 and 2022, DarkSonar was shown to have an elevated score within several months for 74% of the attacks.
Given that such a large percentage of cyberattacks start with an email, DarkSonar can be particularly beneficial to an organization in determining the likelihood of an attack.
Conclusions
Darknet data includes a variety of information relevant to organizational risk. Utilizing DarkOwl’s data sources enhance an organization’s ability to understand threats posed to their organization, manage third-party risk, and potentially determine the likelihood of a threat. Modeling risk enables an organization to both understand their weaknesses and take mitigating actions to protect their organization from loss of data, profits, and reputation.
Contact us today to learn how to monitor your darknet exposure.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















