Q1 2023: Product Updates and Highlights
April 13, 2023
Read on for highlights from DarkOwl’s Product Team for Q1, including new product features and collection stat updates!
Data and Product Updates
New Search Templates and Search Blocks:
This quarter, the DarkOwl Team added 14 new search templates using new chat operators. Refreshed search templates to incorporate new query structures that leverage our tokenization options.
Several of the new template additions make it easier to search for leaked passports by adding regex templates for passports from unique countries. We also added several other that make it easier to find aliases via member page URLs and profile titles.
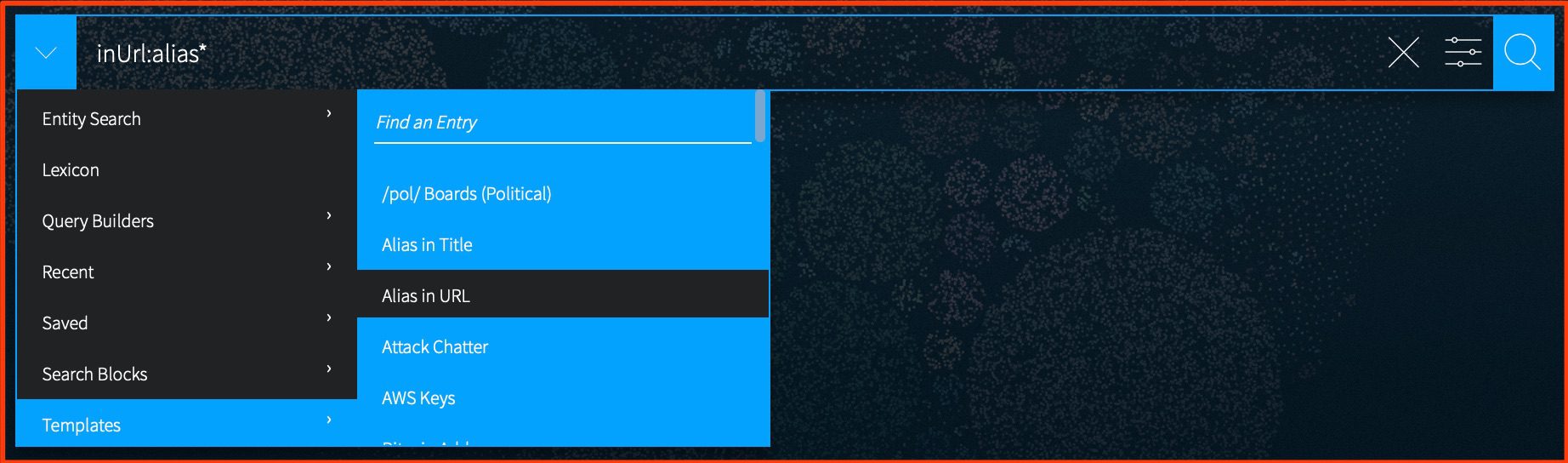
Our product team also added several new search blocks – including an updated block for “attack chatter”. Others enhancements include a better search for company/organization information, and other blocks that utilize frequently used hacking keywords.
CVE Tokenization:
Based on feedback from our customers, CVEs are now being identified and tokenized within our indexed documentation collection. Users can now search for results containing a specific CVE number, as well as for results containing any number of CVEs.
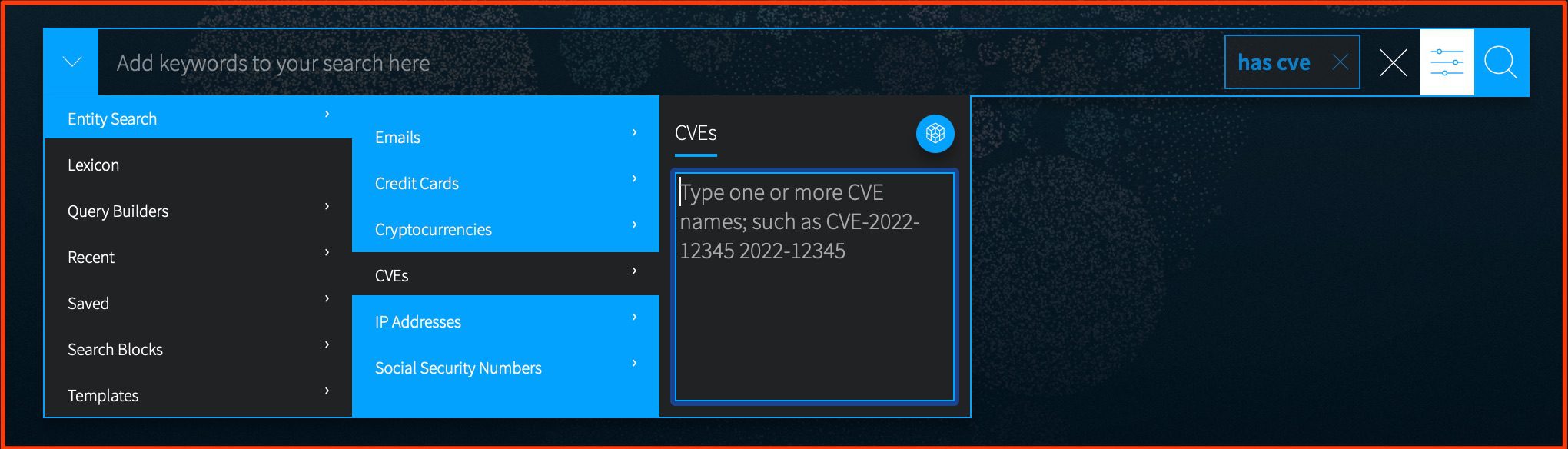
CVE tokenization will make it easier to search for CVEs along side keywords or other entities such as onion domains or threat actor aliases.
Chat Channel and Usernames: We’re making it easier to find channels and usernames in chat platforms.
We are excited to announce a new utility that will provide additional user and channel metadata for our chat content, and enhance searching based on that information. For all of our chat content, our team was able to identify consistent components such as channel names, and make filterable fields for these entities.
Now, when you use any of these new tokenized chat fields, Vision is able to correlate that search to that entity. In other words, Vision will know to look for a username or user ID, not just a keyword. Applicable entities include usernames, channel names, UserID (numeric), channel ID (numeric).
This can be particularly helpful in trying to identify users who use multiple aliases. For example, In Telegram, Usernames can change, but UserIDs are persistent—so it can help you find different aliases for the same user. The screenshot below shows an example of a user that is associated multiple usernames, identified via their Telegram UserID.
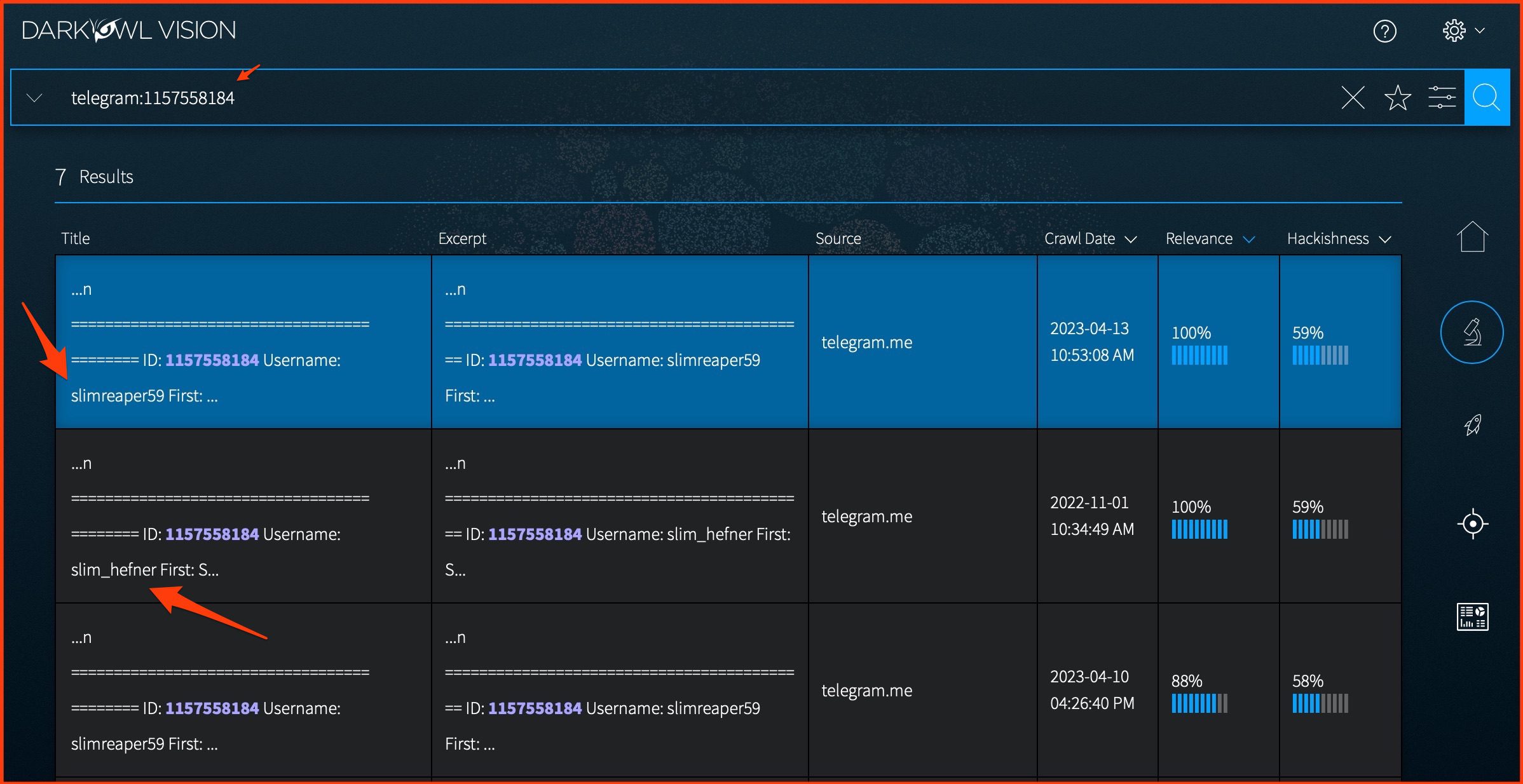
This new feature enables you to associate UserIDs with usernames on platforms such as Telegram, enabling analysts to uncover multiple aliases associated with the sake UserID.
Feature refreshes and user customization options:
The DarkOwl Product team has also added several Exclusion Options to the Research Quick Filter Tool. These exclusion options, particularly the Search Blocks, are frequently recommended query additions by Product Support, to help reduce noisy results. These are all Starter Search Blocks—you can see their content on the Search Block page. While we were at it, we also removed extra space on this menu, to make it shorter.
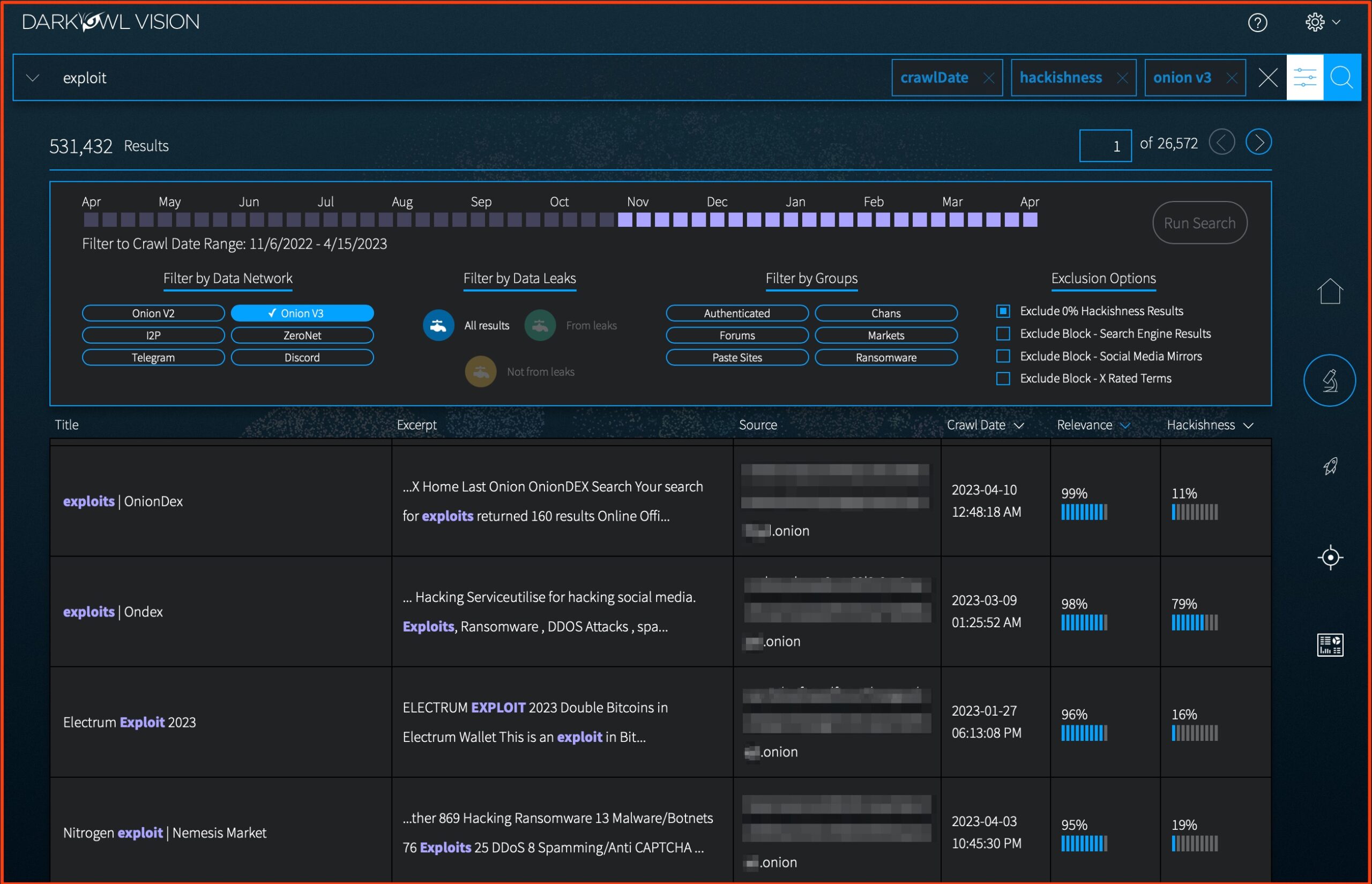
The most popular exclusion parameters including popular exclusion search blocks (directory sites/wikipedia mirrors) and zero hackishness results.
We also enabled a new preference option for users to change their default landing page views so that users can choose where to begin their workflow based on their dashboard of preference.
Collection Stats and Initiatives

This past quarter showed tremendous growth, due in part to advancements in our crawling technology and focus on emerging areas of activity.
Highlights
This quarter we added 340 new chat channels, 25 chat servers, and 5 unique data leaks at the request of customers. Most of these our team was able to obtain and index within 24 hours of the incoming request.
Our chat platform collection continues to grow. Currently, we have coverage of 2003 in channels and 233 servers across multiple chat platforms.
Overall we’ve, added close to 100 new data leaks since the beginning of this year, including a number that are comprised of StealerLogs, which are becoming an increasingly popular threat vector.
Entity Numbers
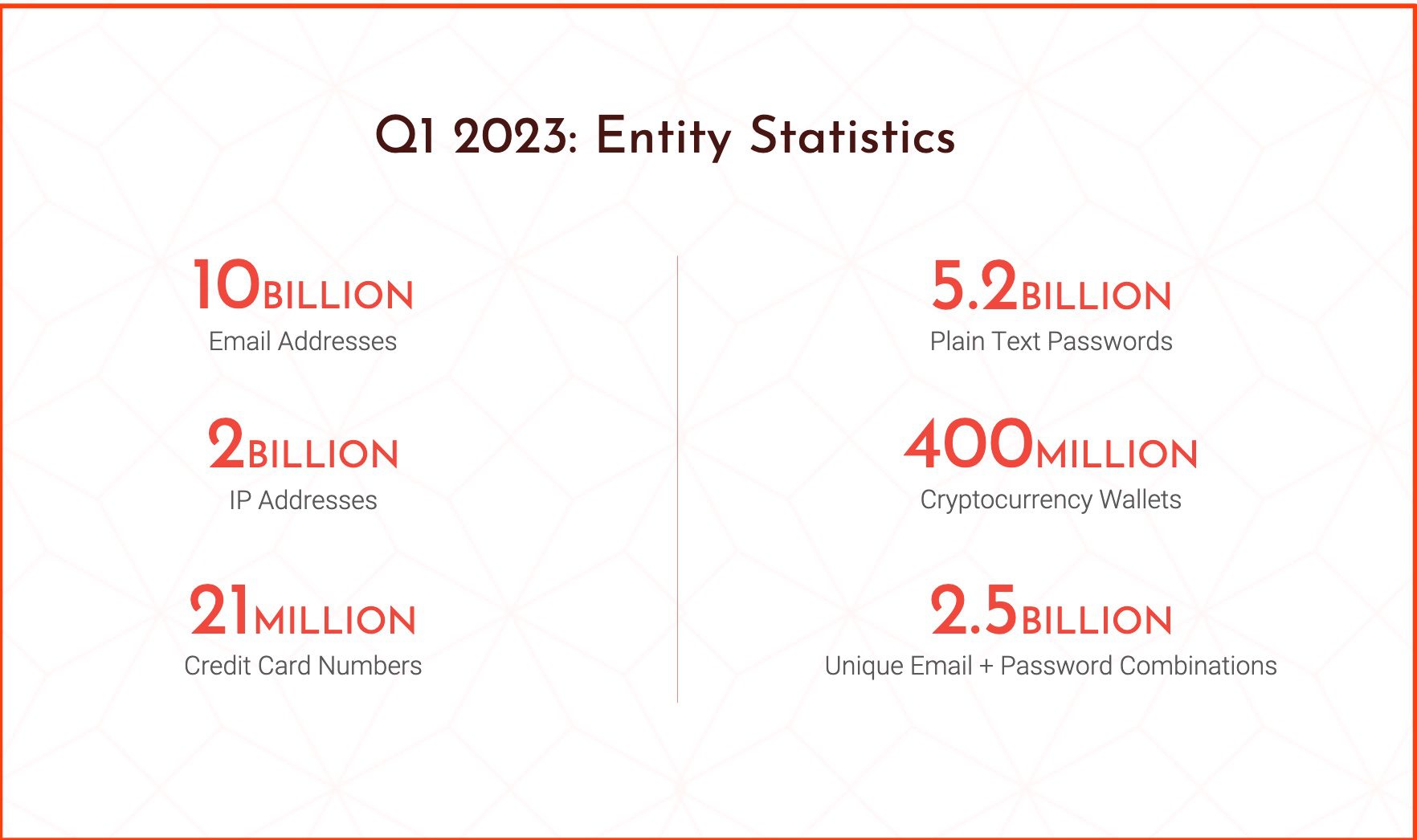
As of the beginning of Q2 this year, DarkOwl Vision has indexed the above number of critical entities.
Notable leaks added in Q1:
Twitter Breach
In January, the user data for approximately 200M Twitter users was leaked on BreachForums. The data contains user account metadata such as email addresses, screen names, first and last names, number of followers, and account creation date. When analyzed, the leak includes 461,943,786 emails (total); 215,251,326 are unique.
Learn more about the Twitter Breach
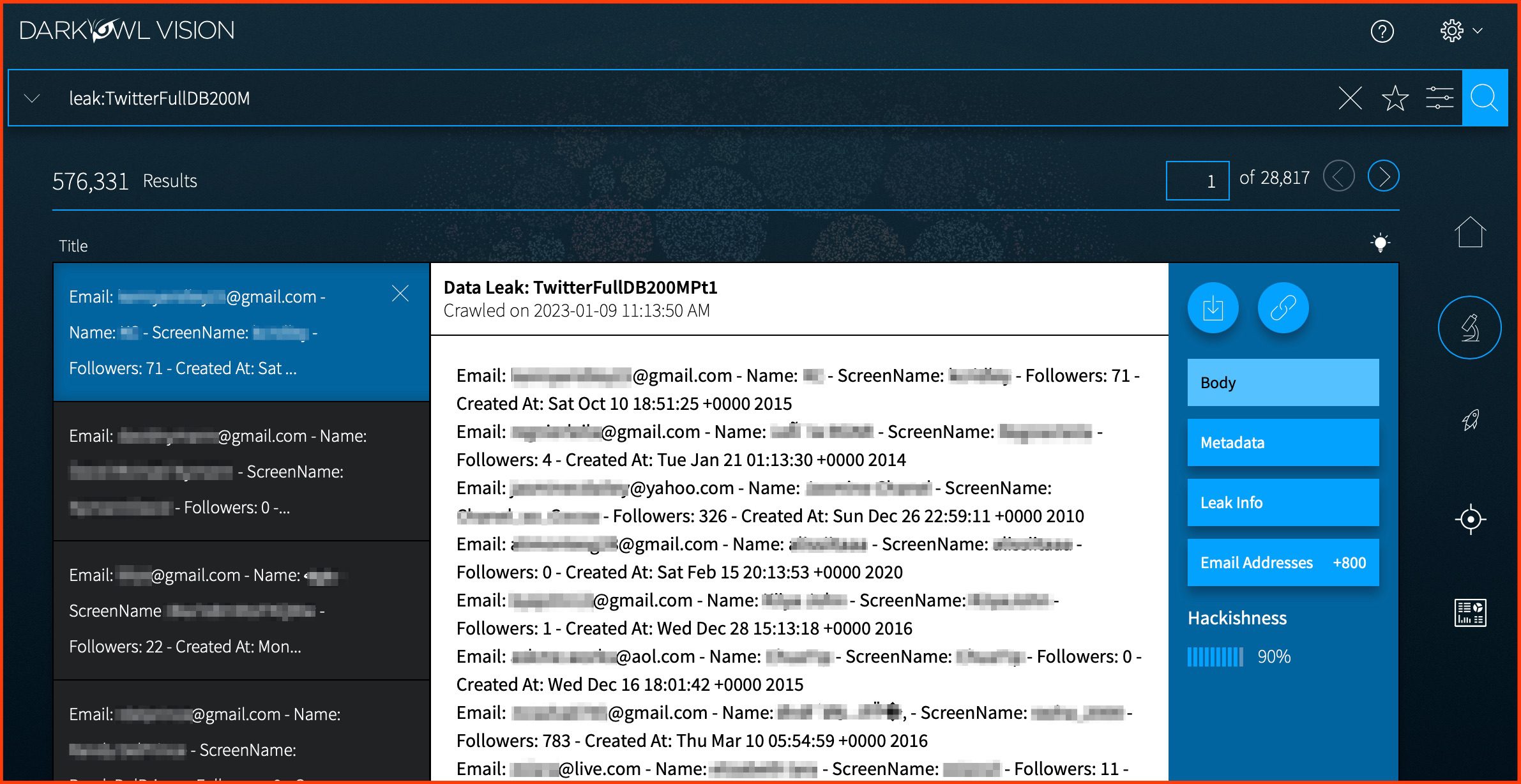
After Twitter refused to pay 200,000$ after hackers breached their networks in December of last year, posted on Breach Forums.
Data from Deutsche Bank Breach
In March, the threat actor ‘Alliswell’ advertised 60GB of Deutsche Bank data for sale “to the highest bidder” on a BreachForums thread on March 13, 2023. The actor listed several samples in the post. This sample in DarkOwl Vision includes three files: capital.markets.00565489.dat (a public SSL cert for Citibank Switzerland), interpol.00454378934.data.report.003834923 (a public SSL cert for Interpol), and DataBank.sql (a SQL table of bank names, indexed in 11 parts).
The full leak, which is reportedly 60GB large, is not publicly available at this time. Note: DarkOwl does not purchase illegally obtained data
Learn more about the Deutsche Bank Breach
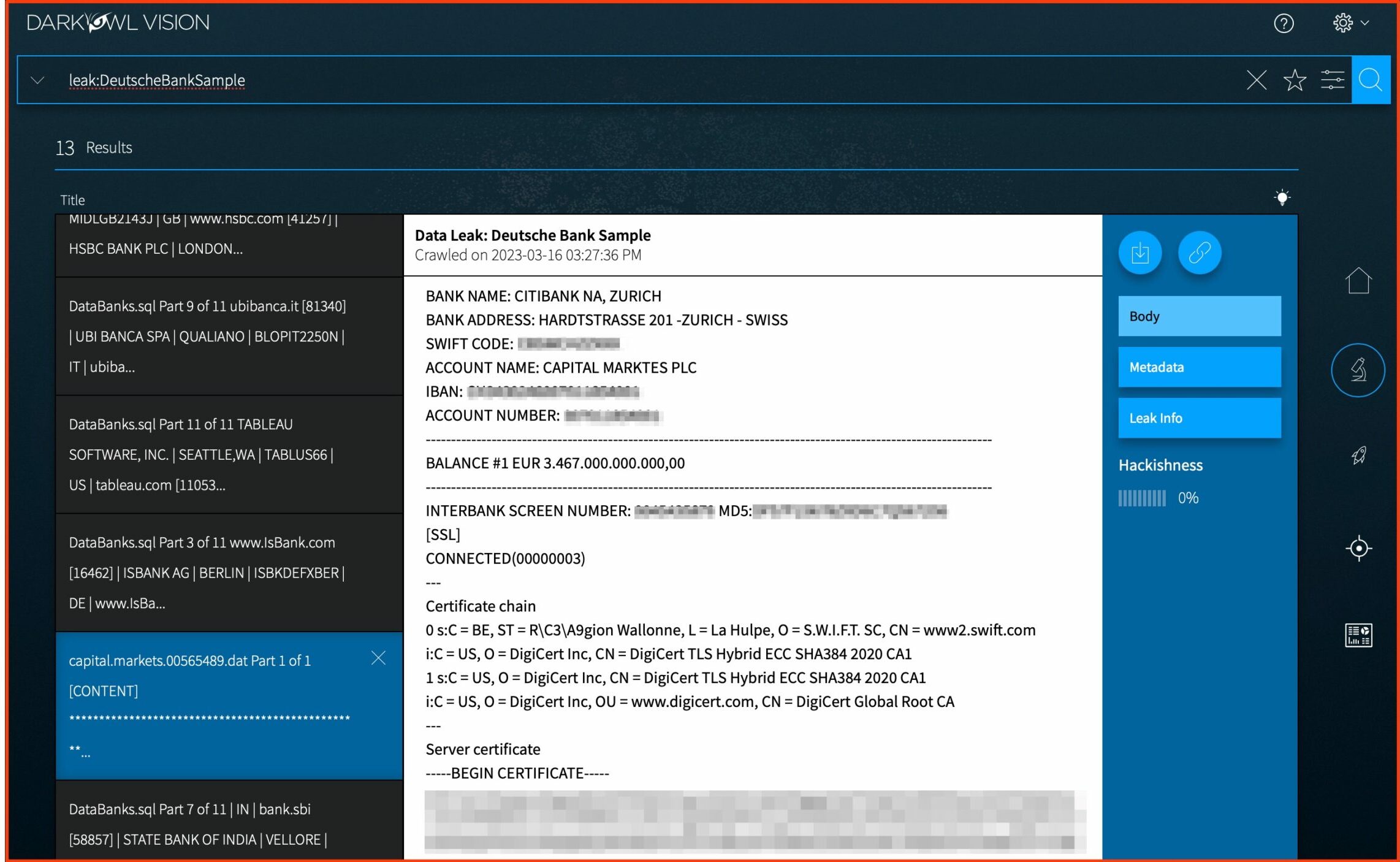
Result from DarkOwl Vision from Deutsche Bank Leak that appears to contain interbank transfer document that records a cash transaction from one bank to another.
BidenCash Market Credit Card Dump
In late February, the darknet carding shop BidenCash announced its one-year anniversary. To commemorate the event, the administrators of BidenCash shared a text file of 2.1 million compromised credit cards for free. DarkOwl’s crawler picked up the posting almost immediately, and it was indexed and available to all users within hours.
Learn more about the most recent BidenCash Market credit card dump
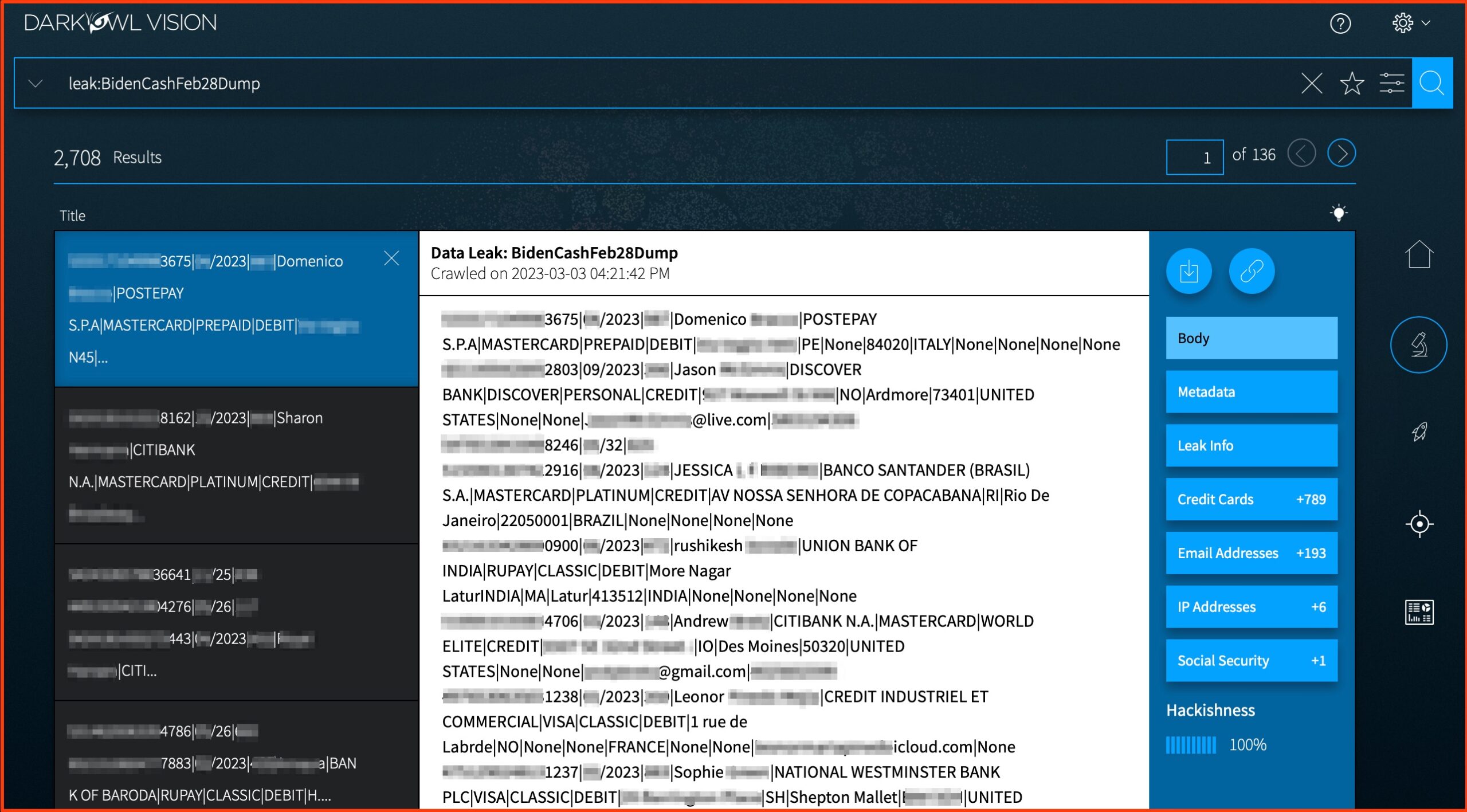
The BidenCash Market Credit Card Dump contains a wealth of associated PII including CVV numbers, and card holder’s full names and addresses.
Other Highlights and Coming Soon
Another noteworthy update from this past quarter includes our engineering team’s improvements on our ability to circumvent bot preventions measures to gain and maintain access to authenticated sites.
We’re also actively staying on top of the ransomware ecosystem and have added several new groups emerging on the scene. In just the last week, we’ve added coverage of ransomware groups such as Darkbit101, Money Message, Abyss, and Dark Power.
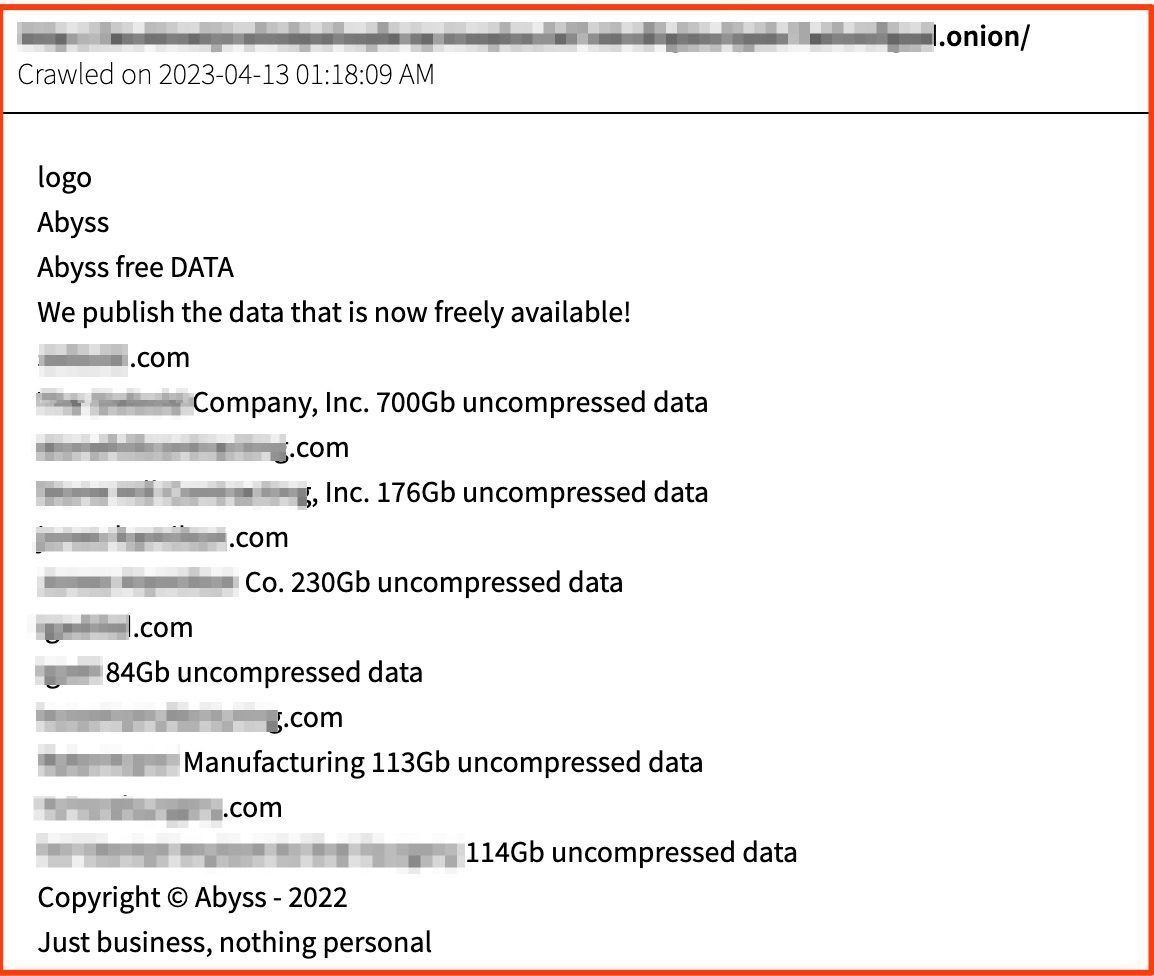
Posting from the ransomware group Abyss that lists multiple recent victims and their compromised data.
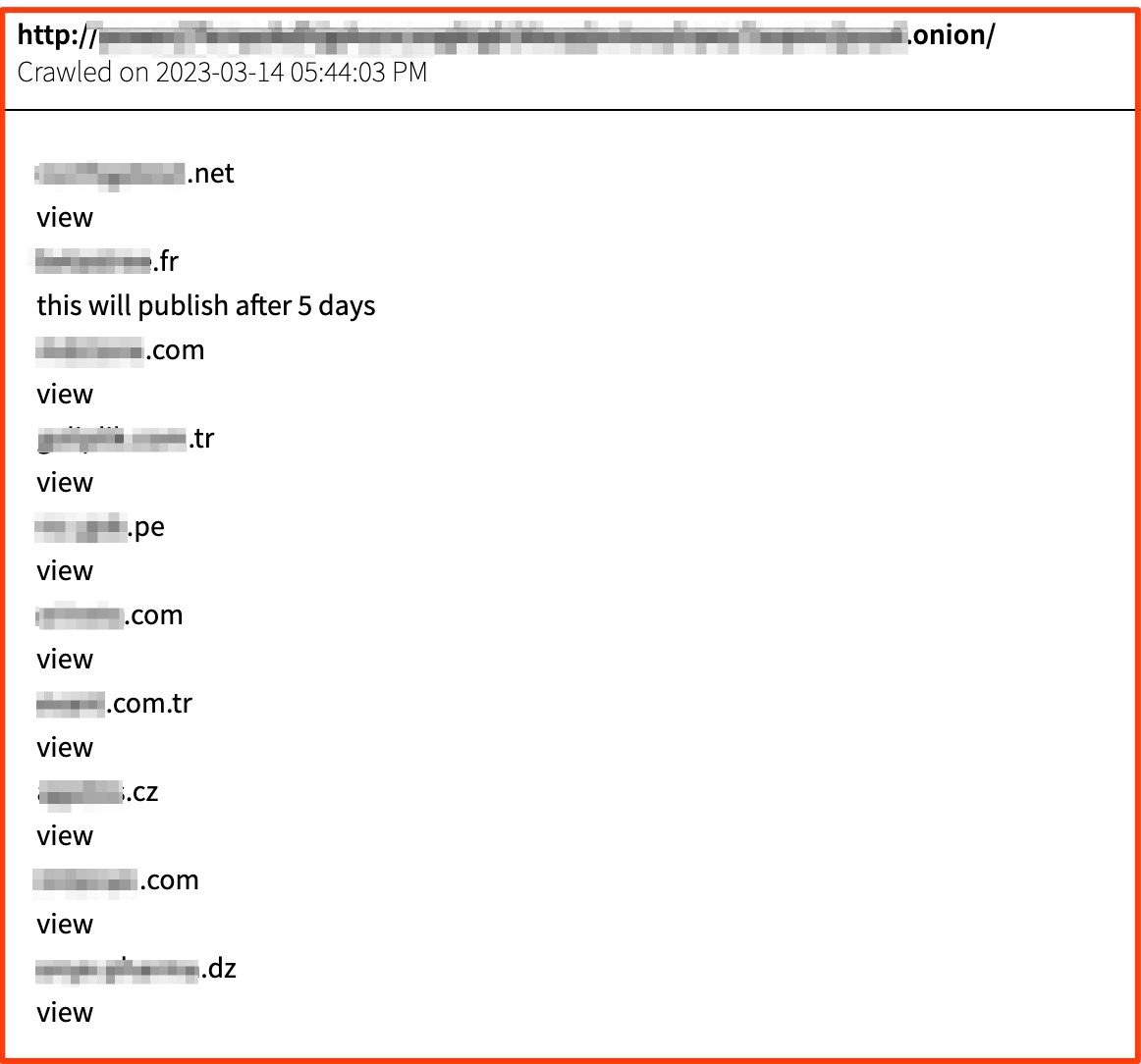
Posting from the ransomware group Dark Power that lists multiple recent victims and their compromised data, as well as victims whose data is pending – likely depending on whether or not they pay the ransom demand.
We will continue to expand our chat platform coverage, as we see more and more threat activity occurring on these platforms.
On the horizon
Stay tuned for an exciting announcement from the DarkOwl team! We are about to launch a whole new product that is a first-of-its kind relative risk rating based on darknet exposure. To get a preview of this new release, schedule a time to speak to one of our team members.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















