Dark Web Exposure of Popular E-Learning Companies
March 21, 2023
The darknet is home to a complex economy that is largely built off of the illicit exchange of digital goods such as MTV (Malware Toolkits and Viruses) and compromised credentials. Threat actors exploit these assets for a variety of reasons, many of which take some form of fraud. While many threat actor tactics seem to be purely for financial gain, dark web adjacent sites such as Telegram contain multitudes of other listings that may serve a more unexpected user group – including those looking to continue their education with illicitly obtained accounts for E-Learning tools.
Sites such as Codeacademy have long established themselves as having a successful model that many other E-Learning companies follow today. Most offer a “freemium” model, meaning select courses or certificates can be gained for free, with more advanced or specialized certificates priced on a tiered scale. After seeing a number of postings on the darknet from users soliciting hacks or compromised credentials for various E-Learning accounts, our analysts took a look at the exposure of several popular companies in this industry using our industry leading darknet data platform, DarkOwl Vision.
Coursera
DarkOwl Vision has indexed a high quantity of email addresses with the domain coursera.org in recent years – likely as the result of a data breach. At the time of writing, DarkOwl Vision contains 2,058 total coursera emails, and 811 unique emails. However, only 9 of these emails have been associated with plain text passwords.
While Coursera does offer free learning tracks, their more premium offerings range anywhere from 39$-59$ per month, with more specialized certificates typically costing on the higher end. The most common type of offering being exchanged on darknet forums is for methods to obtain these pricier certificates for free.
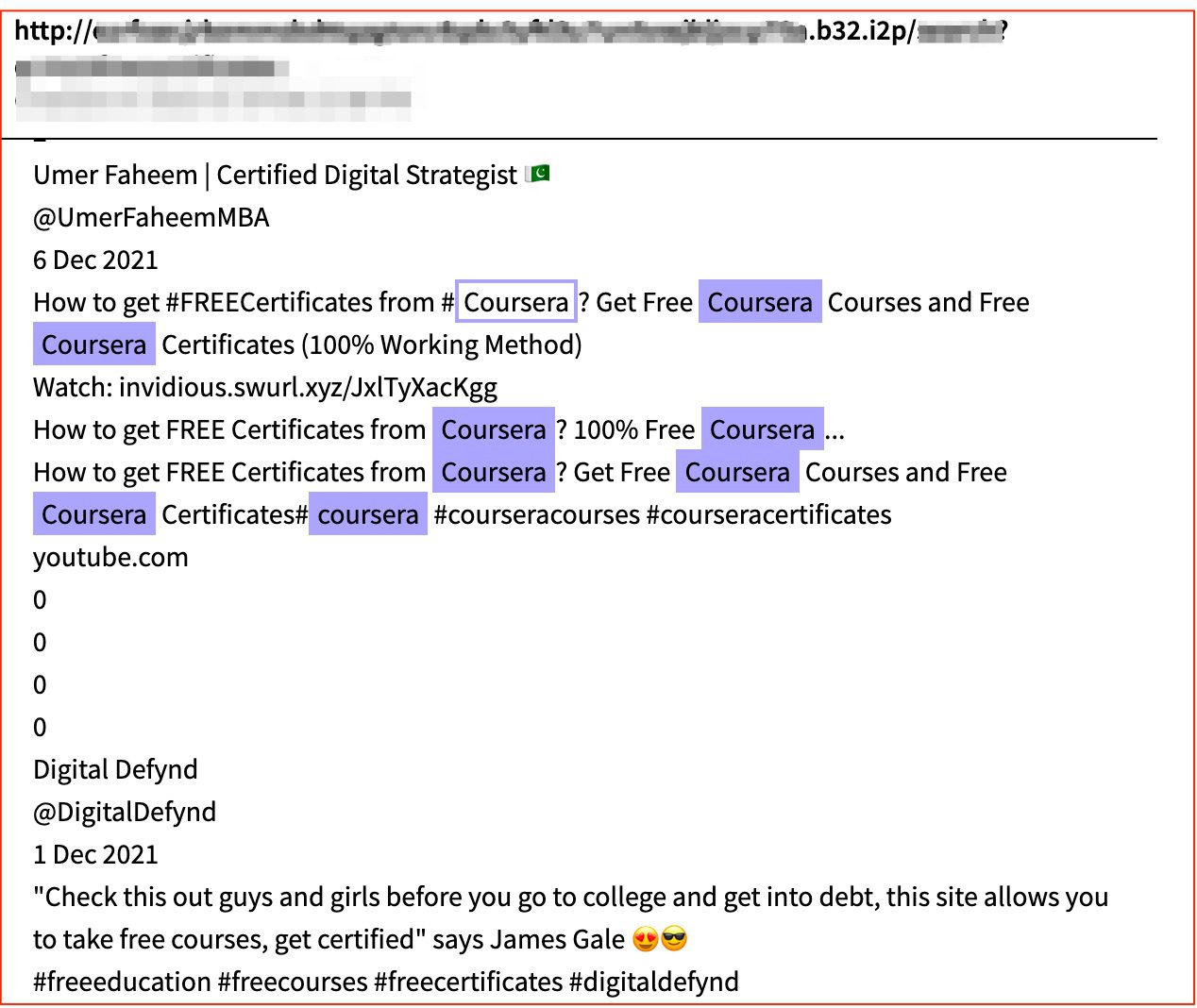
Figure 1: Advertisements an I2P site for methods to scam Coursera and obtain free certificates, Source: DarkOwl Vision
In the following example, stealer log for coursera.org is being sold for as little as $10 US dollars. The listing also contains ISP (internet service provider) information – potentially to indicate to the purchaser that they should use a VPN when logging into the stolen E-Learning account so as not to have their IP blocked.
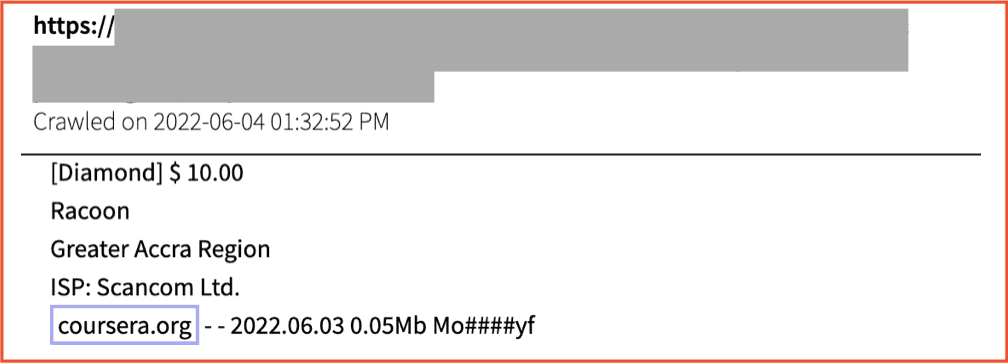
Figure 2: Raccoon Stealer logs for coursera.org being sold for $10 USD on Russian Market, Source: DarkOwl Vision
Other offerings include a python script that allows users to download Coursera courses and obtain valuable certificates for paid tracks free of charge.
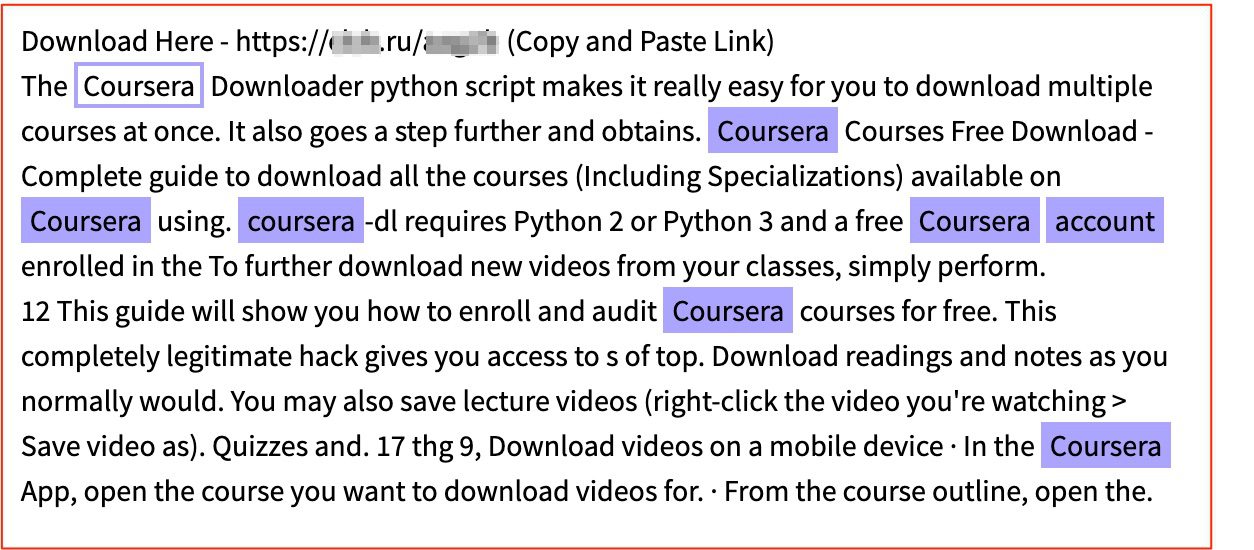
Figure 3: Advertisement on a Russian paste site for a python script that allows users to obtain certificates on Coursera for free, Source: DarkOwl Vision
SkillShare
While Skillshare has a relatively smaller darknet footprint to Coursera by way of quantity, their results in DarkOwl Vision return a higher number of passwords associated with leaked emails with a Skillshare domain. In this case, these credentials are unlikely to be used for account takeover, as they more likely belong to Skillshare employees. These credentials pose a higher risk because they could potentially be exploited and used to access Skillshare’s corporate networks. In total, of the 202 unique emails detected, 18 of them came with a plain text password.
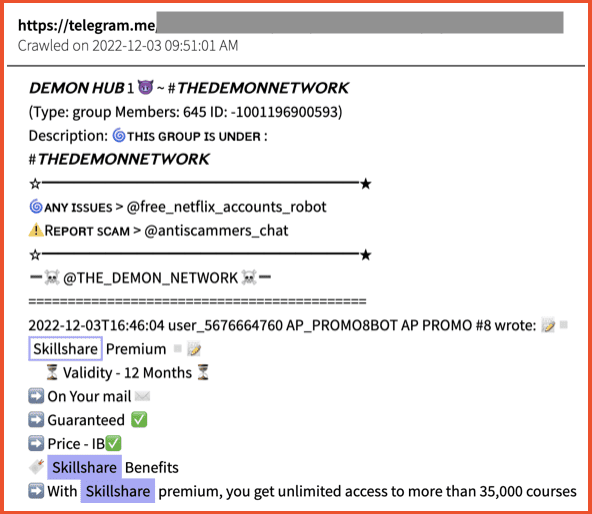
Figure 4: Premium Skillshare accounts being sold on Telegram, Source: DarkOwl Vision
The below listing was indexed from 2easy shop, a popular dark web marketplace that has a large Russian language user base. In this case, credentials for the mentioned URLs were harvested using the stealer malware Redline. For 10$, the purchaser can gain access to the Skillshare account of the compromised target that the Redline malware was used on. Thus, with these types of listings, there is no guarantee of the value of the E-Learning account itself.
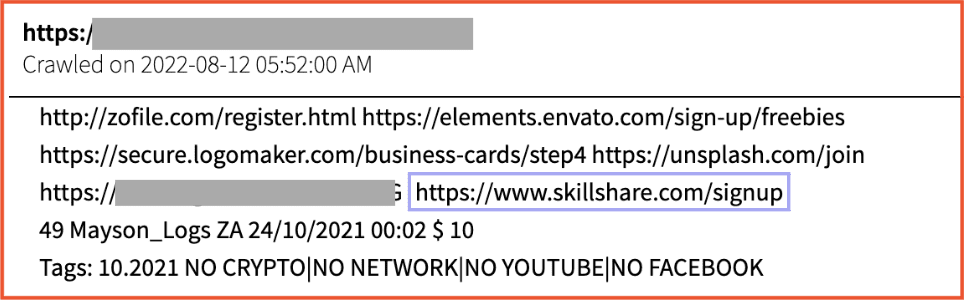
Figure 5: Redline stealer logs of Skillshare on 2easy shop, Source: DarkOwl Vision
LinkedIn Learning
The size and scope of LinkedIn reaches well beyond E-Learning, so it is no surprise that their exposure exceeds other in this category by means of market coverage alone. Clocking in at over one thousand unique email address and nearly as many plaintext passwords exposed in DarkOwl Vision, their risk for internal network exploitation is significant.
Premium LinkedIn accounts are also rather expensive, so the market for access to premium LinkedIn accounts (including to LinkedIn Recruiter) has remained active. In the example below, a recent result from Telegram advertises to have a variety of premium LinkedIn accounts for sale, including LinkedIn Learning premium. These are being offered $10 a month in individual quantities, or for as low as $5 a month when bought in bulk quantities of 100 or more.
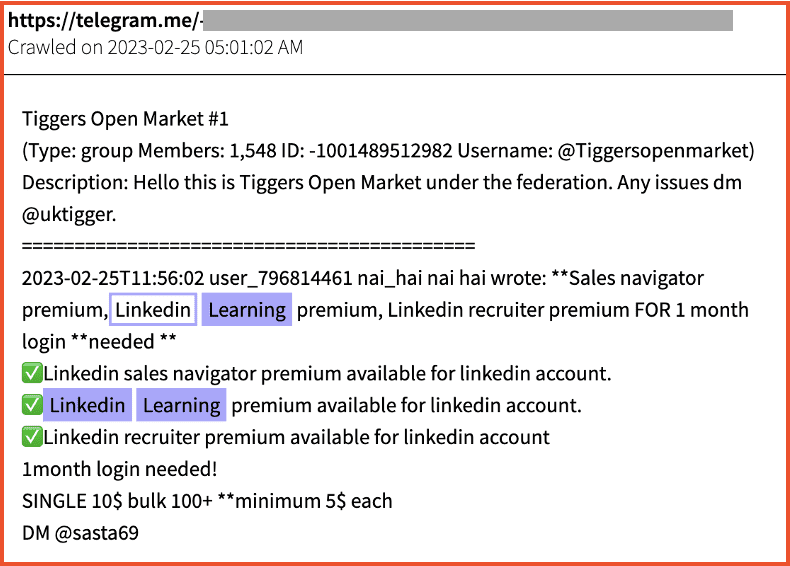
Figure 6: Premium Linkedin Learning accounts offered on a Telegram forum, Source: DarkOwl Vision
Udacity
Search results for udacity.com email domain mentions in DarkOwl Vision returned over 700 unique email addresses, which is considerably more than its peers. However, only one of these was associated with a plain text password. Thus, their dark web exposure from an internal threat perspective is on the relatively low side compared to other E-Learning companies.
On the account takeover and fraud end, our analysts found numerous results similar to the listing below. As pictured, the post contains plain text email addresses and passwords that can be easily checked and verified by those willing to put in a bit of extra work to obtain free Udacity accounts. Published to Telegram, the post also solicits screenshots from those who are able to successfully log in to any of these accounts. This is likely so that they can use those screenshots as a means of validating their services and gaining reputation status as a legitimate vendor.
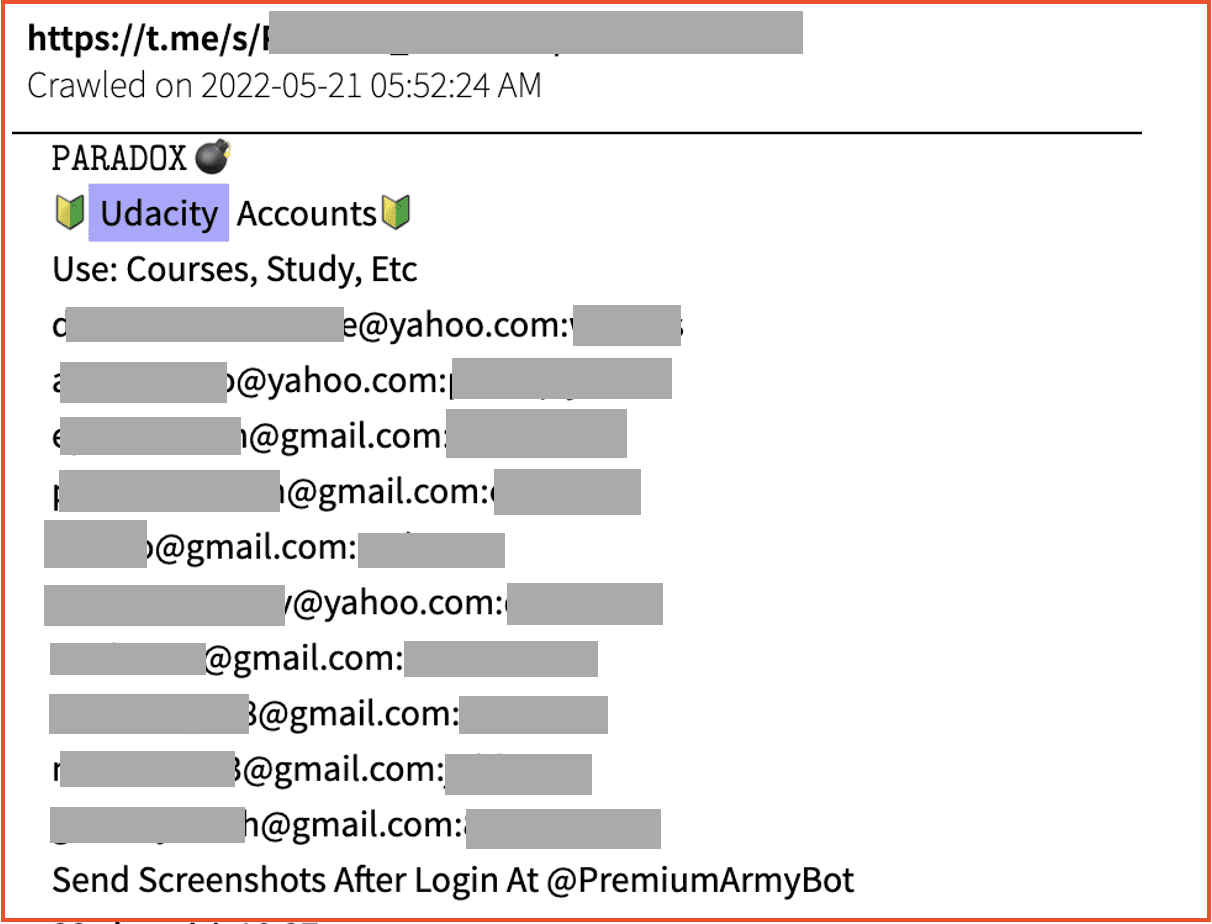
Figure 7: Telegram listing containing plain text credentials for Udacity accounts, Source: DarkOwl Vision
Codeacademy
From a credentials perspective, Codeacademy’s footprint within DarkOwl Vision fell in par to other E-Learning companies. Overall, results for their domain amounted to 508 total email addresses, of which 167 were unique and 8 were associated with plain text passwords.
There were numerous advertisements on Tor that advertised a variety of Codecademy accounts and hacking tools that could help exploit them. This includes listings for the E-Learning accounts themselves, as well as “crackers,” or “checkers” which are scripts that cross reference credentials against a service to see A. if the credentials are able to successfully log in, and B. what type of account the credentials now have access to.
In the result below, detected by DarkOwl Vision in January this year, a listing for one of these “checkers” advertises that “It captures premium status and the number of enrolled courses and also saves free and premium accounts.” Using this type of tool, a threat actor could run credentials in vast quantities against the Codecademy log in portal and potentially uncover many successful log in combinations for valuable Codecademy accounts.
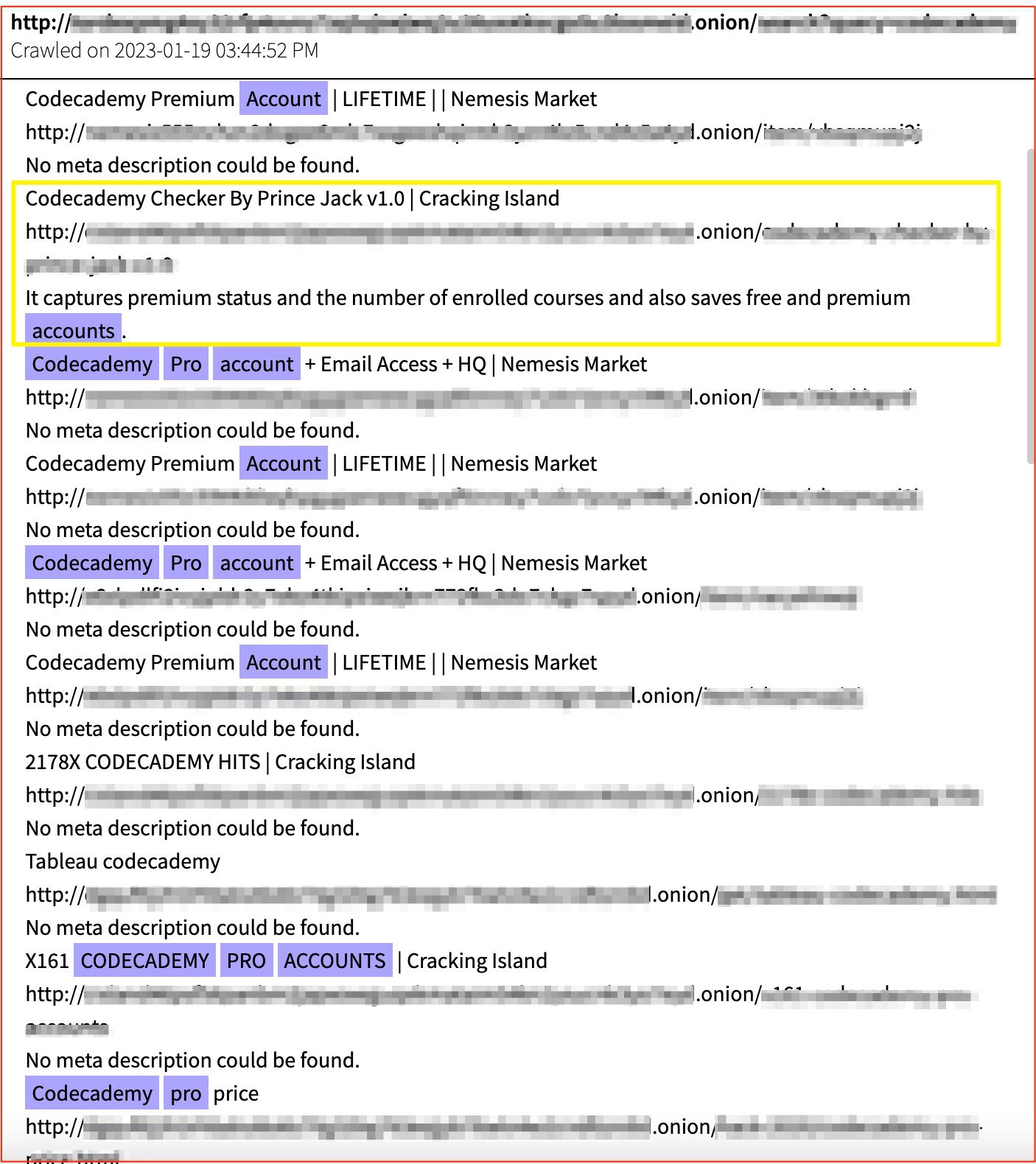
Figure 8: A Variety of Codecademy account-cracking resources, including credentials and “checker” tools, listed on Tor, Source: DarkOwl Vision
This listing also contains listings for Codecademy Pro accounts, as well as some the ensure both emails access “+ HQ”. Each of these listings directed to a separate vendor and were amongst dozen of similar advertisements.
Final Thoughts
Interestingly, during the course of this research, our analysts observed a disproportionate number of discussions from sources in DarkOwl Vision , including IRC channels, Telegram, and darknet forums – discussing Codecademy in the context of genuine further education. This included discourse around the value of various courses, advice for professional development, further learning recommendations, and so on. This could signal that those seeking and purchasing E-Learning assets may find Codecademy more applicable to the coding skillset needed amongst users who operate on the darknet and deep web.
Having insight into darknet activity means staying one step ahead of potential risks and costly threats to your company. To learn more about how DarkOwl’s data products can assist your threat intelligence initiatives, contact us.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















