Darknet Data: Use Cases for Law Enforcement and Intelligence Agencies
September 01, 2022
In this blog, DarkOwl analysts outline top use cases for intelligence agencies, law enforcement, and government, where darknet data often plays a critical role. These examples of DarkOwl’s software-as-a-service (SaaS) darknet data platform help identify and describe how key data sources in the criminal underground can be leveraged to facilitate analysis and reporting required across intelligence agencies entities’ security departments.
Cyber Investigations
DarkOwl’s darknet data can significantly augment cybercriminal investigations by providing key additive informational components – often in conjunction with other OSINT like social media activity. Data from the darknet often creates a more comprehensive picture of the case itself, the criminal’s behavior, and psychological intentions. The resulting darknet intelligence (or DARKINT) fills in critical intelligence gaps that solidify evidence such that indictments and subsequent legal action may be executed.
Using DarkOwl in conjunction with other open sources and utilities, an investigator can easily identify and a track threat actor’s digital fingerprints and subsequent virtual breadcrumbs, such as social media accounts, usernames, aliases, avatars, email addresses, PGP keys, and cryptocurrency wallet identifiers.
The snapshot example below details how DarkOwl identified and tracked a Portuguese-speaking threat actor involved in mobile device malware development. The lower third of the graphic, consisting of evidence collected from the darknet and DarkOwl Vision – confirmed the suspect’s activities across various underground communities in the darknet and a leaked IP address provided a potential physical location of João Pessoa, Brazil.
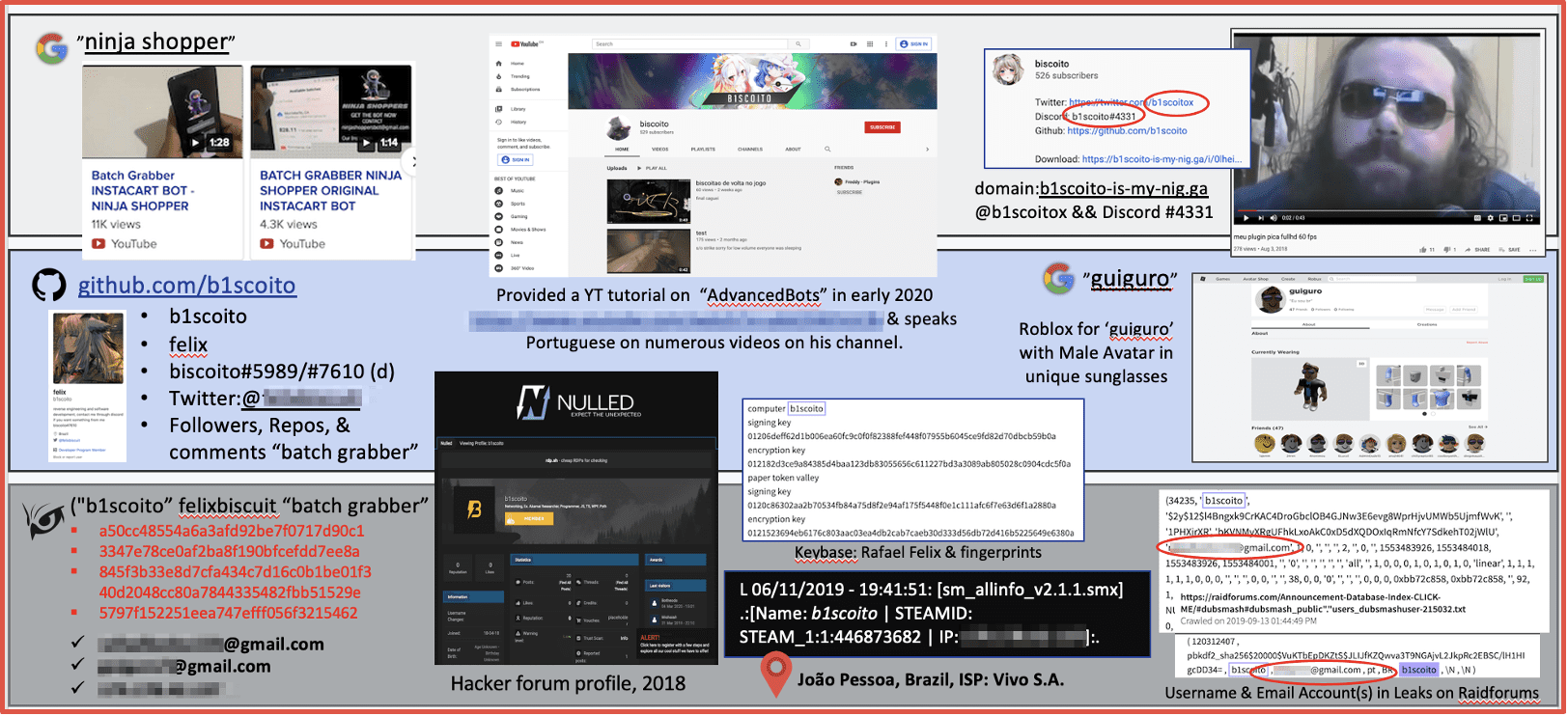
Figure 1: Source DarkOwl Analyst, July 2020
Situational Awareness
Russia’s late February military invasion of Ukraine and on-going offensive operation was preceded by numerous opportunities for geopolitical situational awareness prior to the invasion, and subsequent monitoring of the conditions is available with a surge of new Telegram channels documenting live events ‘on-the-ground’ and conversations between users that have unique perspectives of the conflict.
DarkOwl detected members of popular deep web hacking forums sharing and discussing the leak of large databases containing sensitive Ukrainian citizen data weeks prior to the actual kinetic military activity. Further analysis revealed state-sponsored threat actors from Russia had performed extensive covert cyber campaigns against Ukraine prior to any official military operation, troop or vehicle movement across the border.
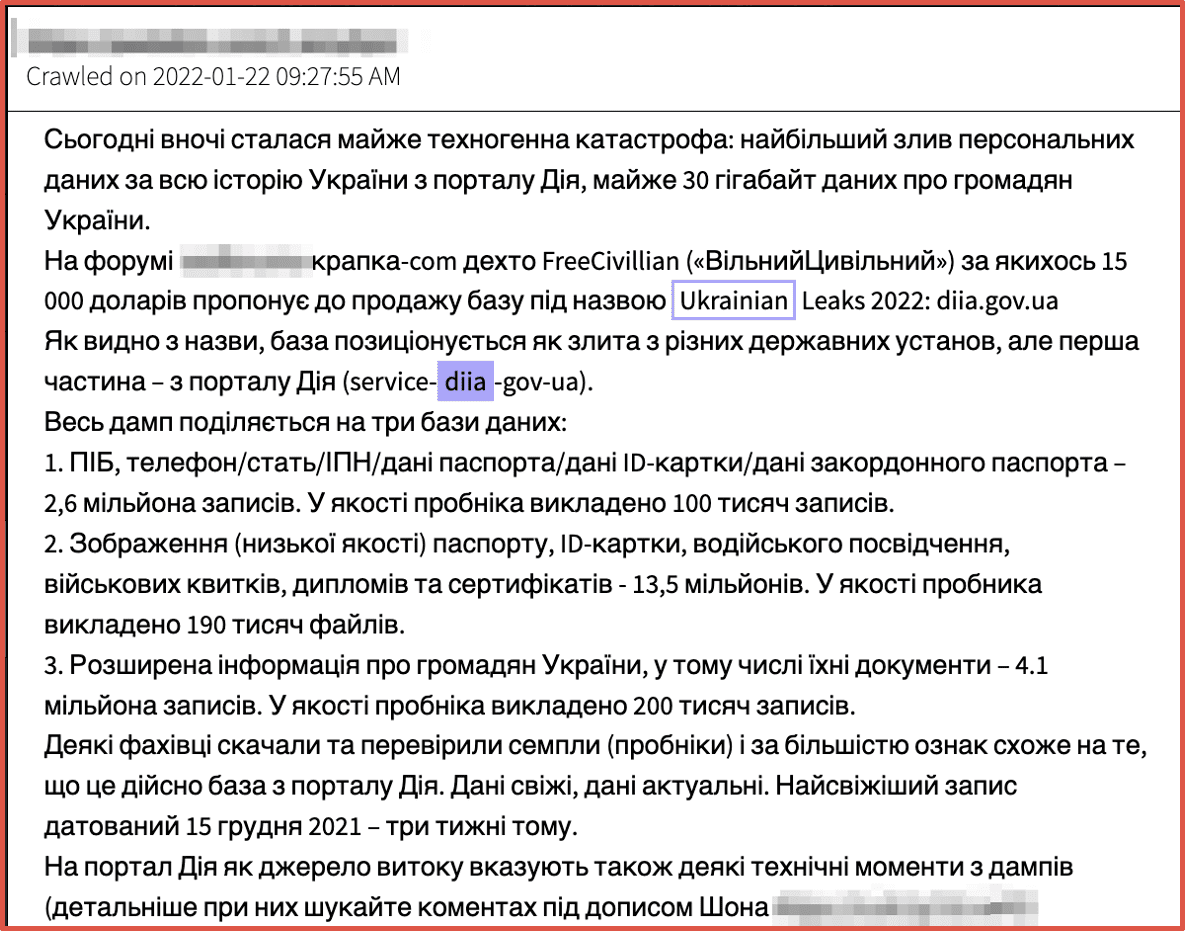
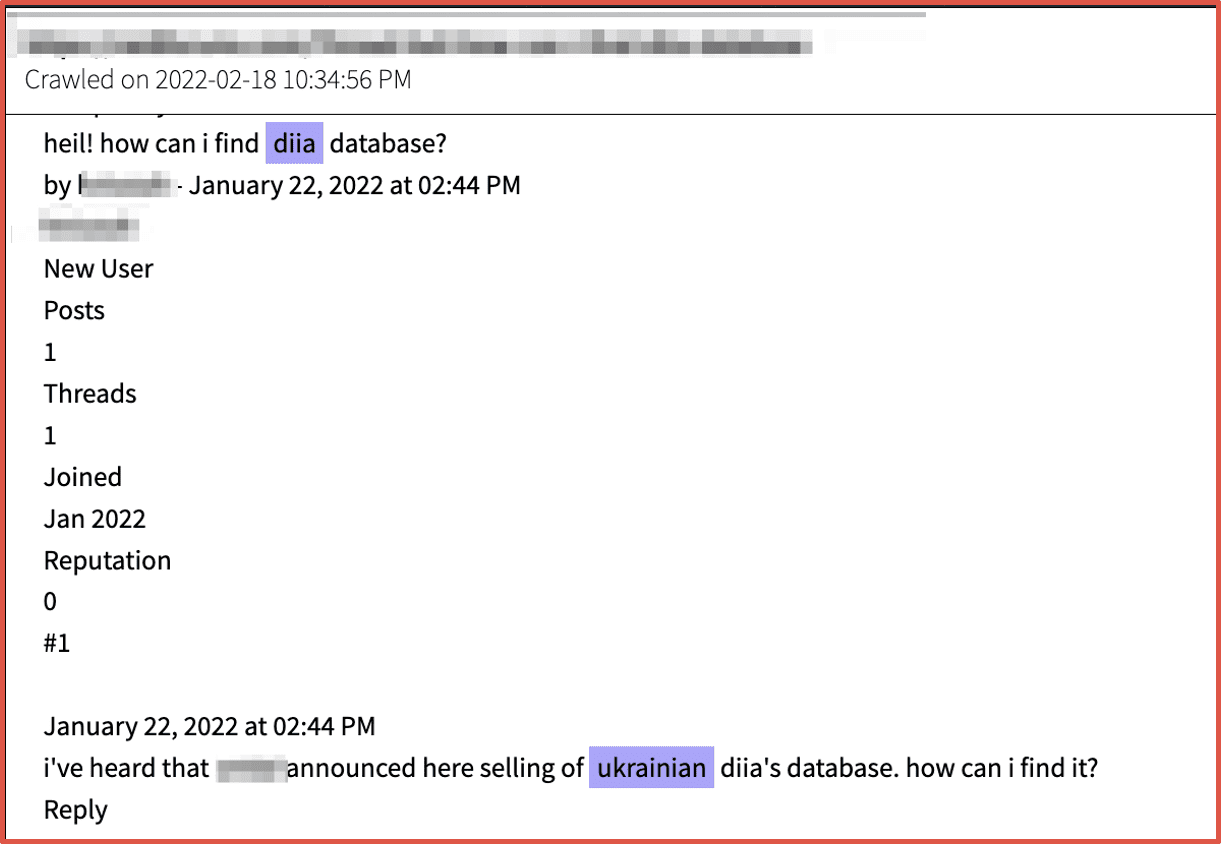
Figures 2 and 3: Source DarkOwl Vision
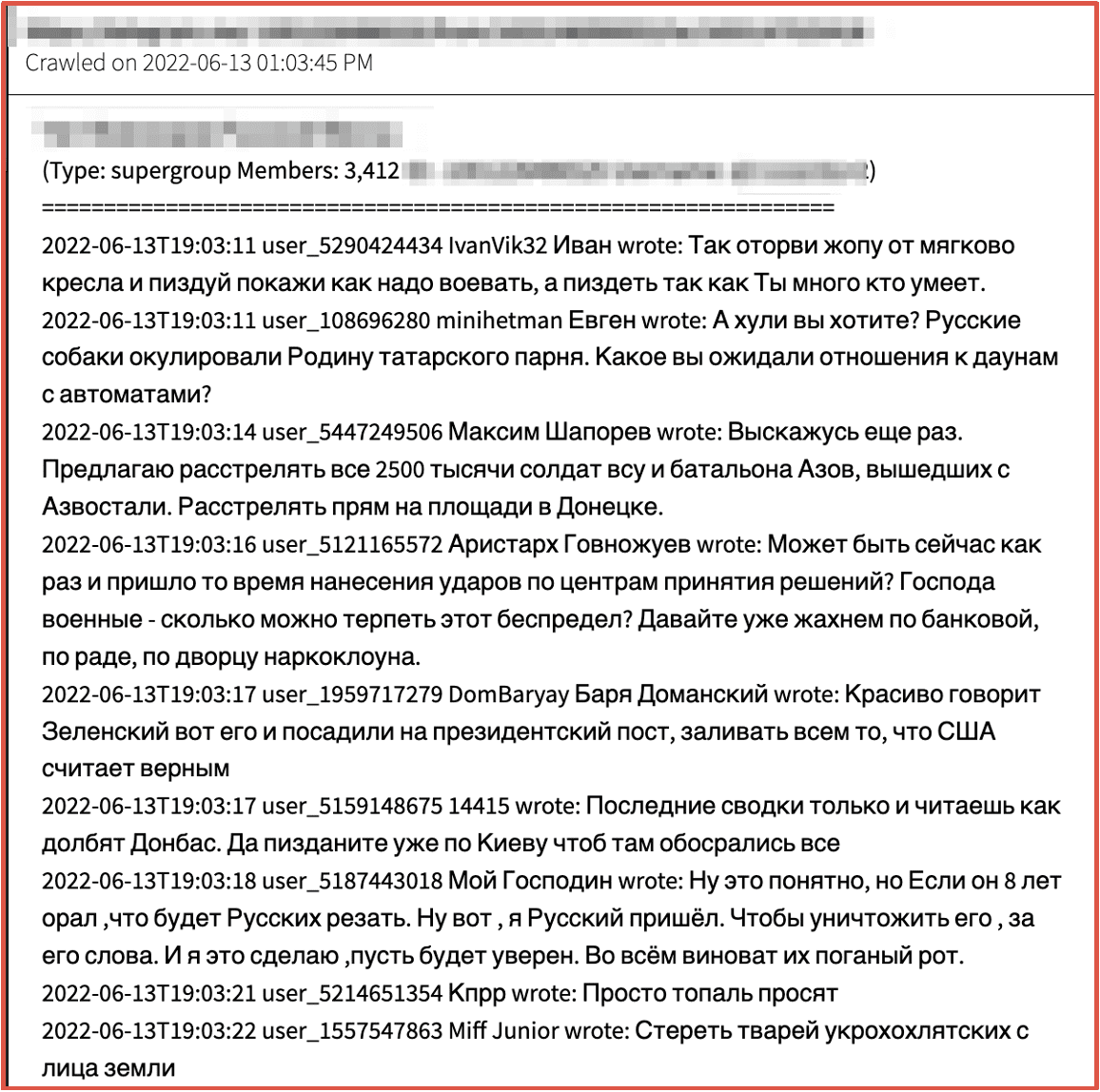
Figure 4: Source DarkOwl Vision
[TRANSLATION OF FIGURE] note: the following contains some explicit language
2022-06-13T19:03:11 user_5290424434 IvanVik32 Ivan wrote: So tear your ass off the soft chair and show me how to fight, and fuck like You know a lot of people.
2022-06-13T19:03:11 user_108696280 minihetman Eugene wrote: What the fuck do you want? Russian dogs have been oculating the Tatar guy’s homeland. What kind of attitude did you expect to downs with automatic machines?
2022-06-13T19:03:14 user_5447249506 Maxim Shaporev wrote: I’ll say it again. I propose to shoot all 2,500 thousand soldiers of the Armed Forces of Ukraine and the Azov battalion who left the Azvostali. Shoot them right on the square in Donetsk.
2022-06-13T19:03:16 user_5121165572 Aristarkh Govnozhuyev wrote: Maybe now is the time to strike at decision-making centers? Gentlemen of the military – how long can this lawlessness be tolerated? Let’s already hit the bank, the rada, the narco-clown palace.
2022-06-13T19:03:17 user_1959717279 DomBaryay Barya Domansky wrote: Zelensky speaks beautifully, so they put him in the presidential post, pouring everything that the United States considers true
2022-06-13T19:03:17 user_5159148675 14415 wrote: The latest reports are just reading how the Donbass is being hammered. Yes, fuck already in Kiev so that everyone shits there
2022-06-13T19:03:18 user_5187443018 My Lord wrote: Well, it’s understandable, but if he’s been yelling for 8 years that he will cut Russians. Well, I’m a Russian. To destroy him, for his words. And I will do it, let it be sure. Their rotten mouth is to blame for everything.
2022-06-13T19:03:21 user_5214651354 Kprr wrote: Just topal asking
2022-06-13T19:03:22 user_1557547863 Miff Junior wrote: Wipe the creatures of the ukrokhokhlyatsky off the face of the earth
Counterterrorism
While the darknet is less active with concerted terrorist related recruitment, propaganda distribution, and activity from groups like ISIS, there are an increasing volume of lesser-known terrorist cells using the darknet and adjacent platforms like Telegram to communicate and coordinate their attacks. DarkOwl supports collecting content in over 52 languages and raw data is indexed in the original language of the author as in-platform translation services might corrupt nuances of the original language. The Vision app user interface and API endpoints support in-language search queries and non-English characters.
For example, DarkOwl uncovered documents related to an anti-Israel terrorist group located in Palestine discussing how they and members of Hamas were planning to target military personnel from the Israeli Defense Force (ISF) for digital blackmail and extortion. The group also listed an email address for direct contact and a Bitcoin address for donations to support the group’s cause. (Source: DarkOwl Vision)
Similarly, DarkOwl has also detected online discussions regarding terrorist activity from international groups of concern and their public statements about their involvement in attacks against specific geopolitical targets.
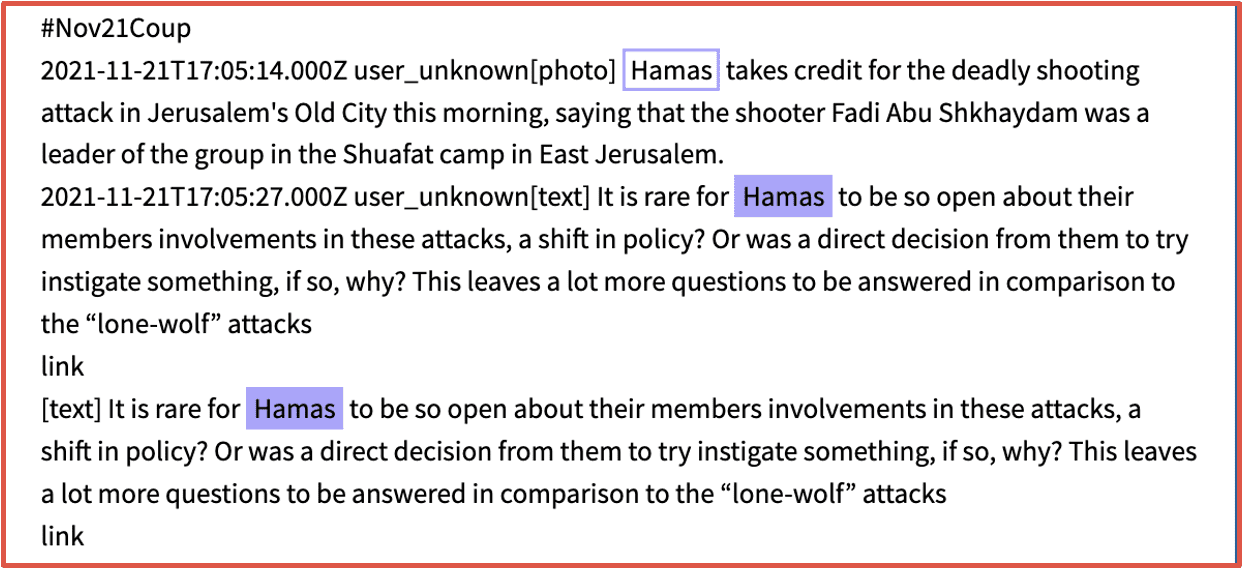
Figure 5: Source DarkOwl Vision
Counternarcotics
DarkOwl’s aggregated darknet data and near-decades long historical darknet archives are instrumental in supporting law enforcement drug-related investigations. DarkOwl has identified numerous darknet drug vendors selling illicit drugs, such as opioids, fentanyl, and cocaine, in bulk volumes for resellers on decentralized marketplaces and darknet vendor shops.
We have also identified a recent trend where many of the drug vendors advertise on discussion forums and marketplaces bulletin boards how to contact them on alternative platforms to complete their transactions, e.g. WickR, Whatsapp, and Telegram, for increased security and identity protection.
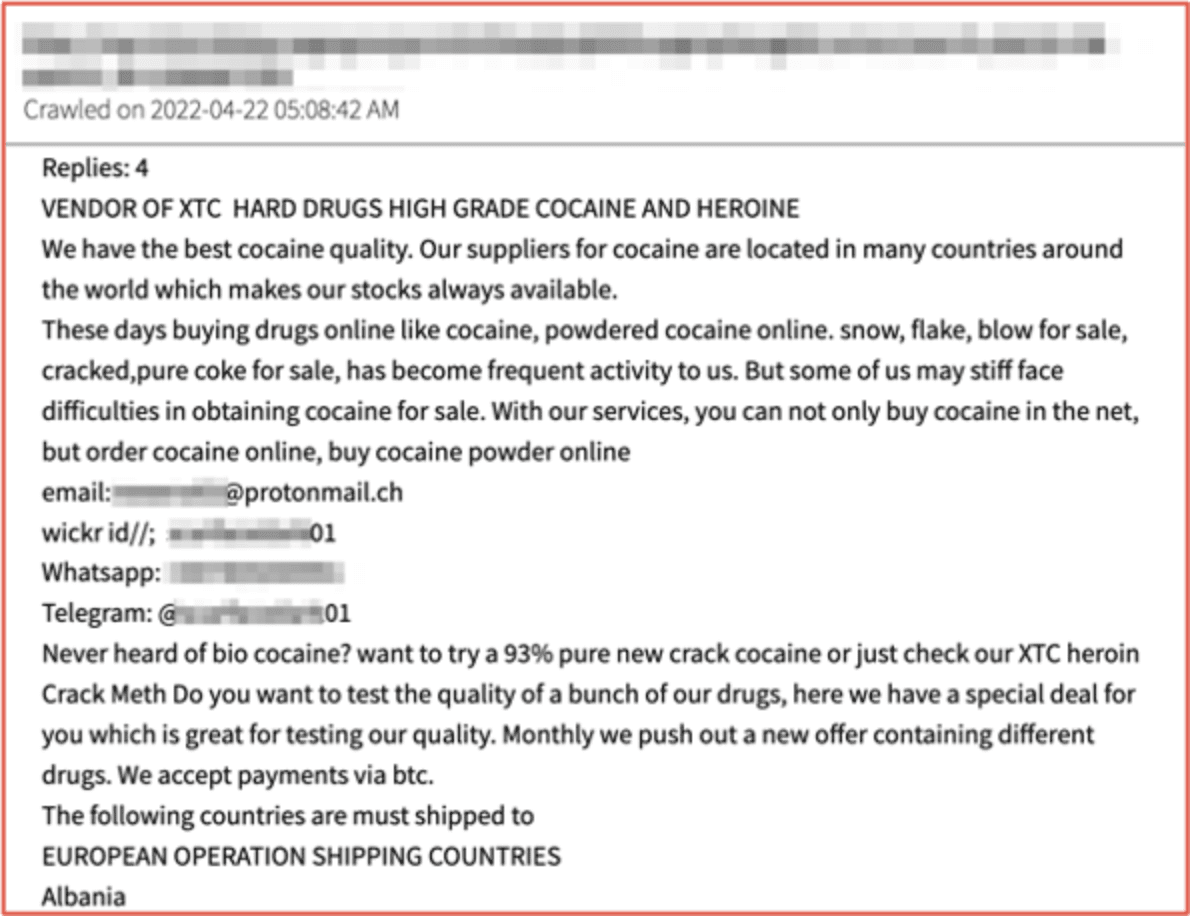
Figure 6: Source DarkOwl Vision
Targeting
DarkOwl’s near-decades long collection of historical darknet archives enables investigators to successfully uncover the identity of suspects involved in various segments of illicit crime. This includes human-trafficking, child exploitation, drug dealing, weapons proliferation, etc.
DarkOwl analysts regularly observe criminals identified by name by other darknet users and security researchers out of revenge or to disrupt the person’s online activities on popular deep web sites like doxbin[.]org. For example, shortly after the invasion of Ukraine, over two dozen members of the Russia-aligned ransomware group Conti/Ryuk – and its closely associated Trickbot malware development partners – were all doxxed.
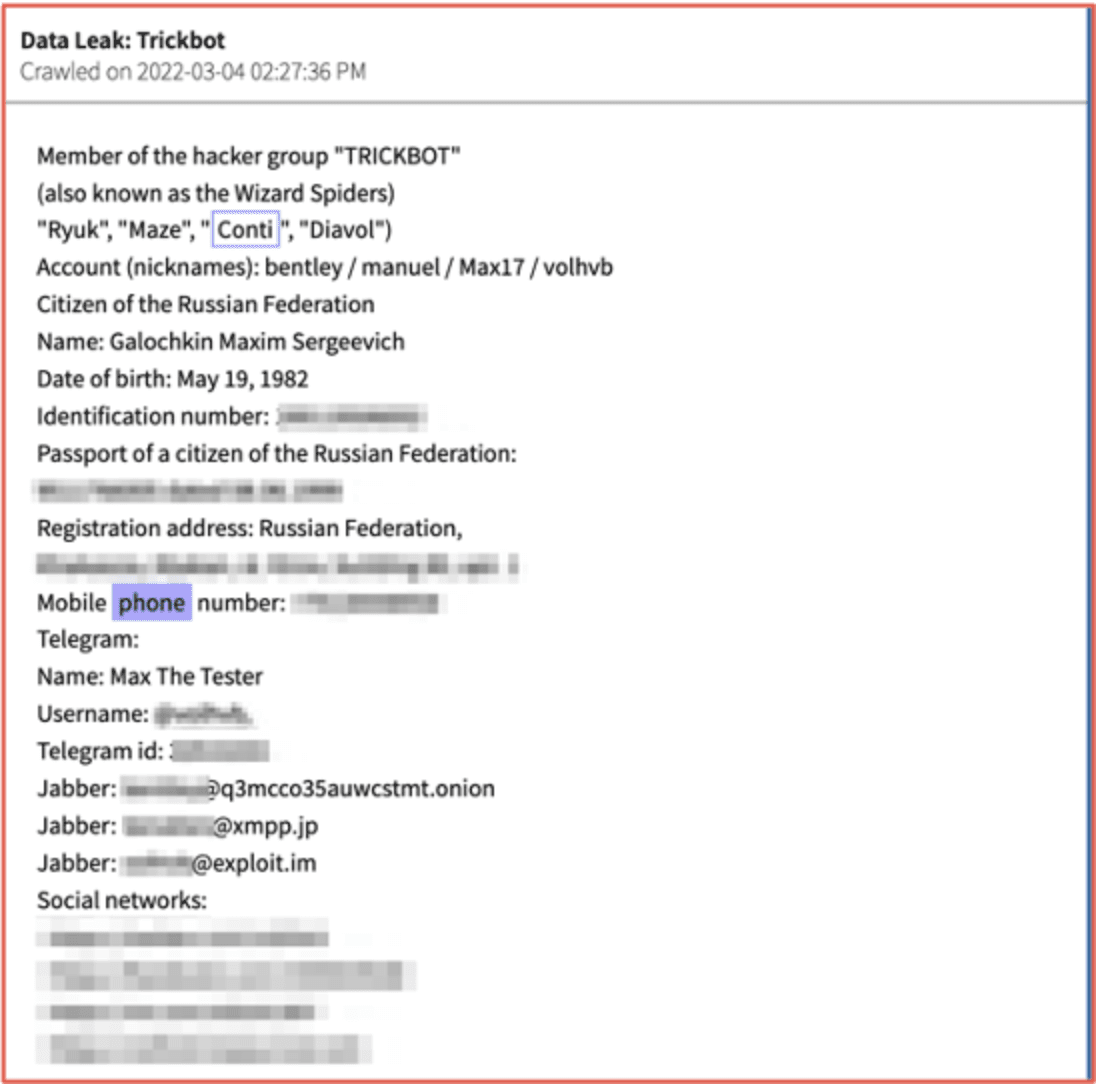
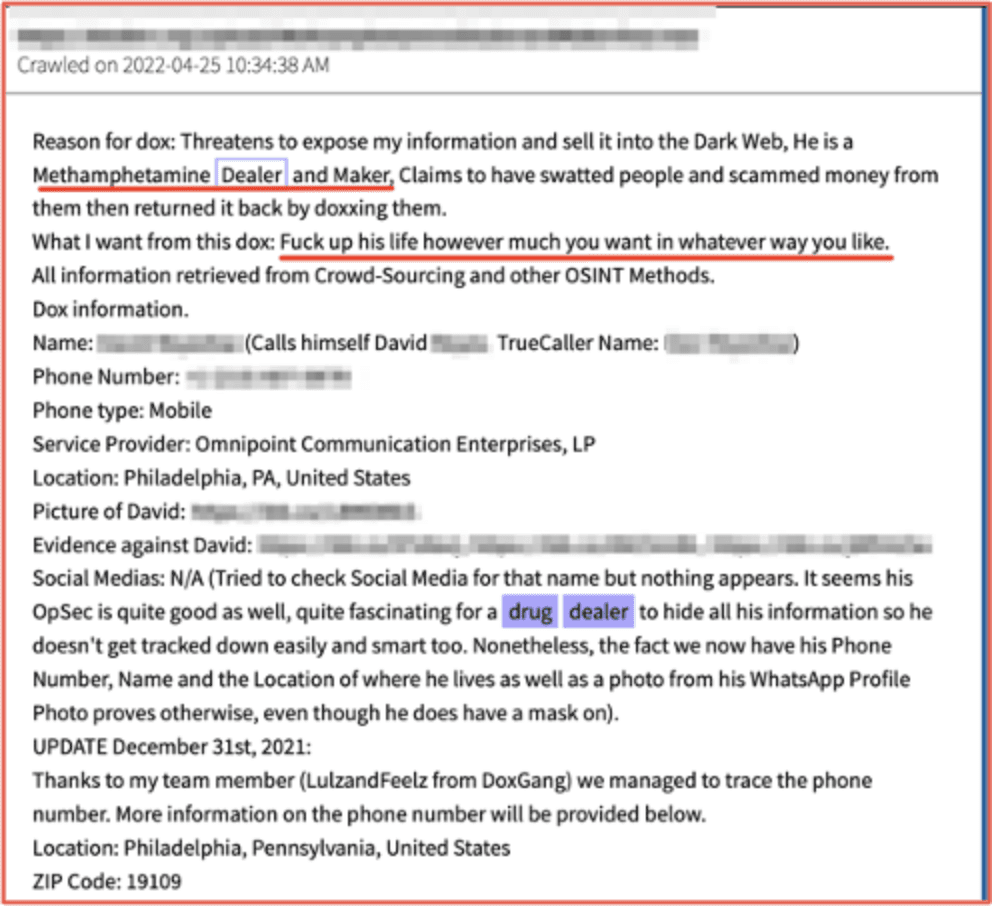
Figures 7 and 8: Source DarkOwl Vision
Cyber Espionage
Data captured by DarkOwl Vision database is often used to detect existing cyber espionage activity and be potentially leveraged by nation states and intelligence agencies for future cyber espionage campaigns.
In the fallout of the global cyberwar between Ukraine and Russia, hundreds of corporations and government organizations in Russia were targeted and/or compromised by an international army of cyber hacktivists supporting Ukraine . Data leaks from ‘ministerial’ organizations of Russia, e.g. Ministry of Finance, Ministry of Foreign Affairs, etc.; academic and research institutions, such as, the Joint Institute of Nuclear Research (JINR) and the Russian Federal Institute of Science, were among the groups targeted. Also included was data from critical infrastructure suppliers of energy, water, and transportation, which can be utilized for future cyber espionage purposes. Key individuals from those organizations and their personal data have also been released providing opportunities for targeted social engineering attacks to recruit and/or exploit for political and technical intelligence espionage and critical diplomatic initiatives.
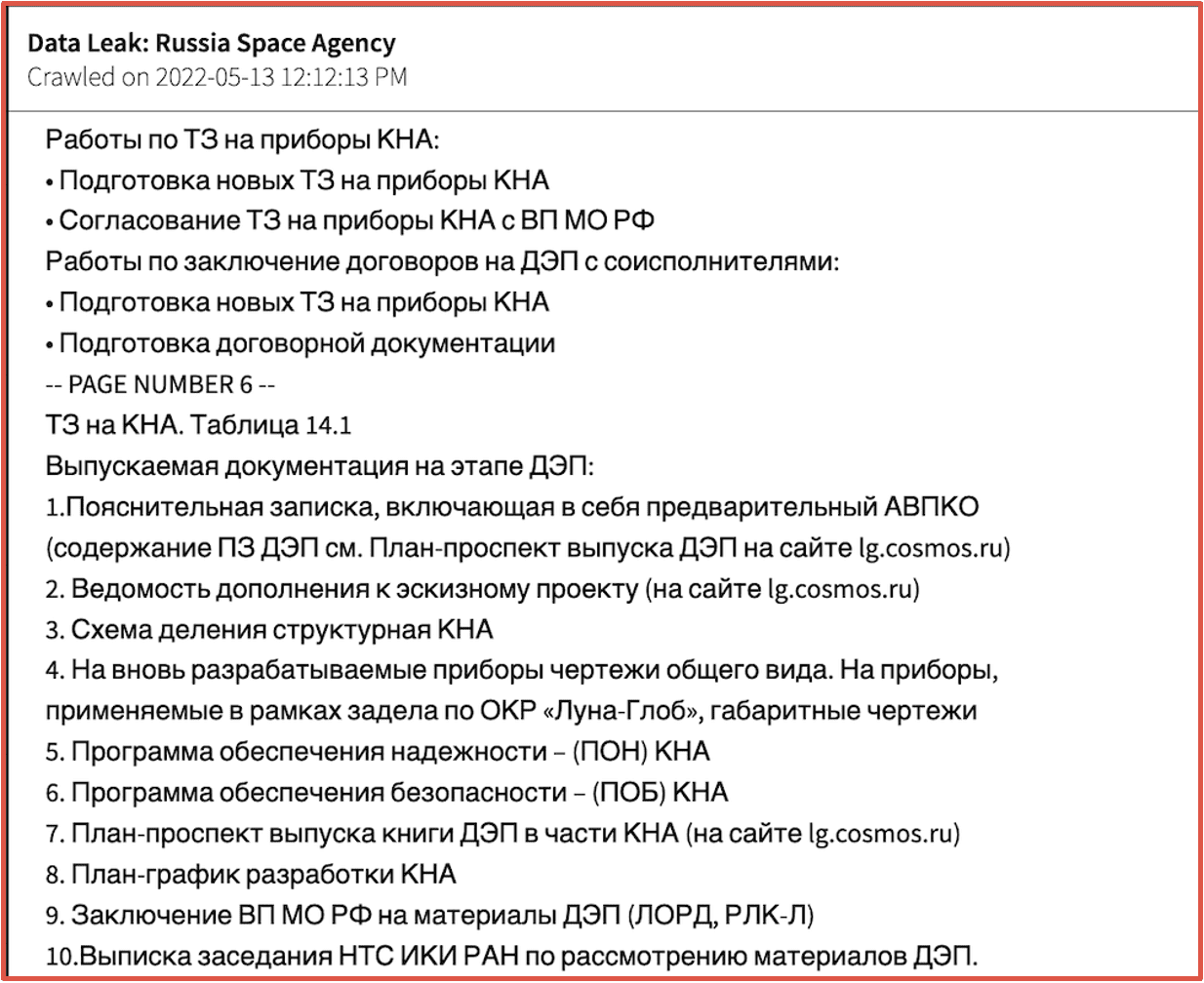
Figure 9: Source DarkOwl Vision
The graphic below contains some of the names of Russian organizations that appeared in leaks released on the darknet from hacktivists supporting Ukraine in the war. You can find the full infographic here.
Figures 10: Source DarkOwl Vision
Domestic Extremism
In recent years the United States has experienced an unprecedented rise in domestic extremism, with members of alt-right paramilitary groups like the Oath Keepers and Proud Boys indicting leading the insurrection against the US Capitol in attempt to keep President Trump in office. Many of these groups congregate and collaborate in darknet forums, chatrooms, and Telegram channels. It is well known that deep web’s imageboards like 8kun are a sanctuary for right-wing conspiracy groups like Qanon to congregate and flourish.
DarkOwl’s darknet data platform allows investigators to monitor for activities from these groups and assist investigations by correlating a suspect’s engagement on social media and anonymous networks. Users of imageboards regularly discuss emotionally charged and controversial topics like assault weapon bans and “replacement theory.”
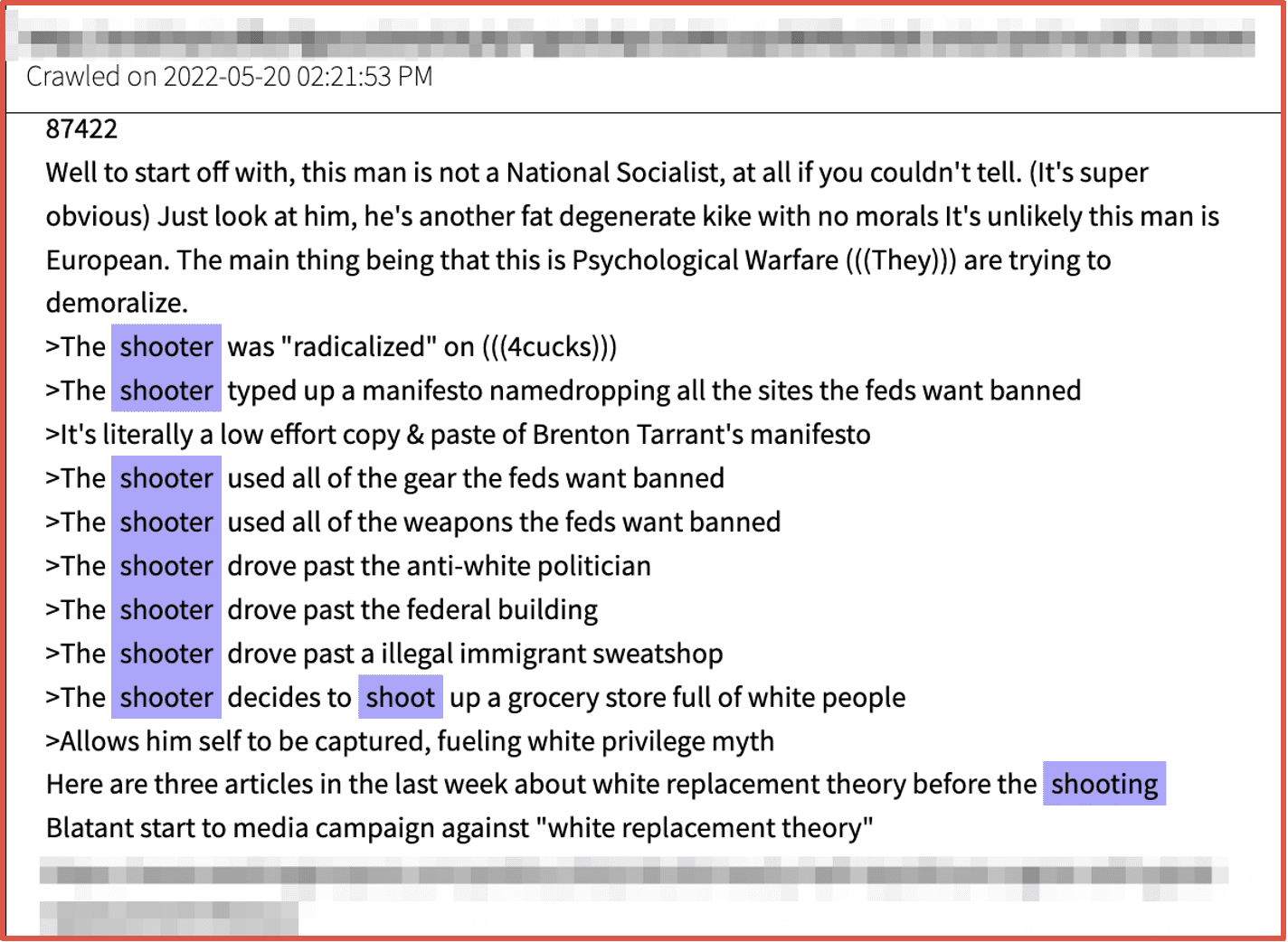
Figures 11 and 12: Source DarkOwl Vision
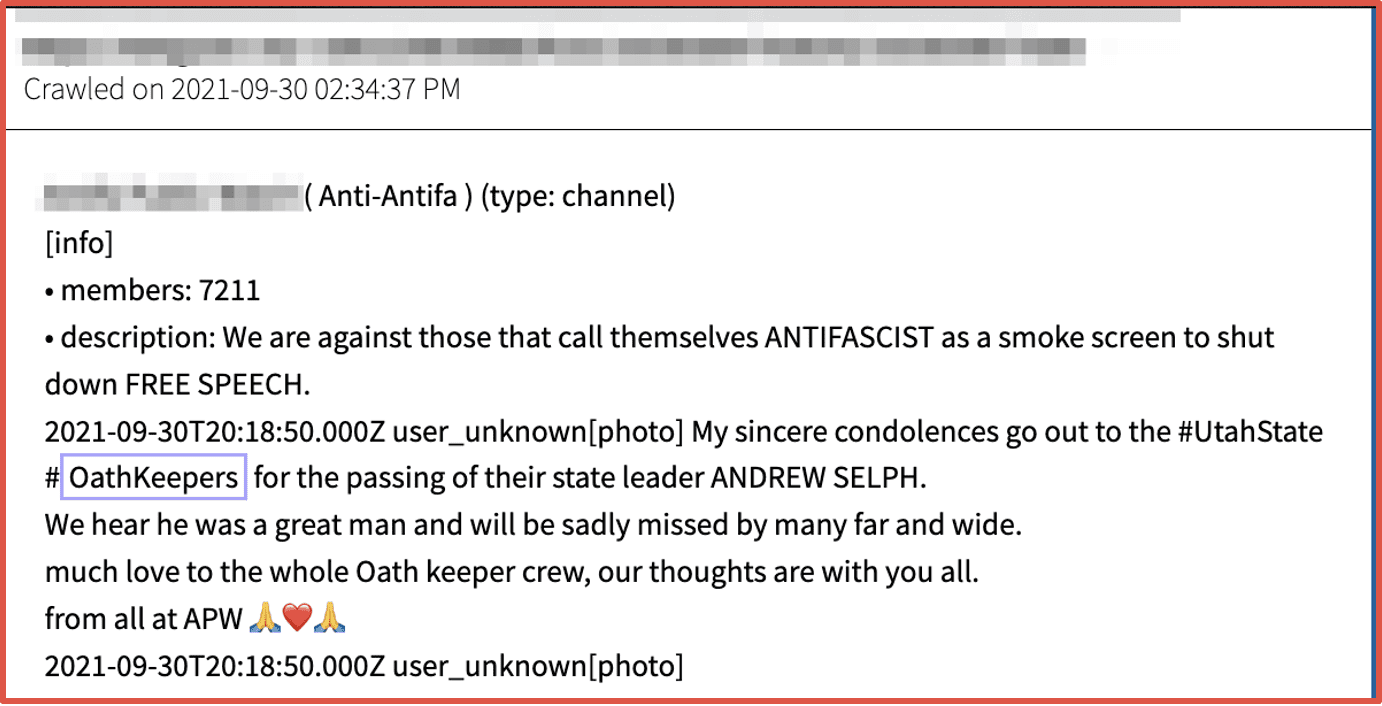
Figure 13: Source DarkOwl Vision
Critical Infrastructure Protection
DarkOwl’s darknet data can be utilized for monitoring mentions of the development of malware to target critical infrastructure. This includes tracking the activity of threat actors who specialize in attacks against industrial control systems (ICS). It also can be used to monitor for mentions of specific critical infrastructure targets that threat actors, terrorist groups, and nation-state sponsored actors are intent on conducting cyberattacks against.
DarkOwl detected an offensive cyber group known as the “Jerusalem Electronic Army” (JEA) targeting agricultural water and heating systems in the northern area of “Negev” or the “Gaza Envelope” near Lakish using ICS/Supervisory Control and Data Acquisition (SCADA)-based attacks to poison the region’s water supply.
Another Telegram channel that advertises support for attacks against Israel – and associated with Team Majhidoon (فريق_مجاهدون) and Team AES (فريق_A-E-S) declared campaigns to penetrate Israel’s solar energy systems in Tel al-Rabiya were successful.
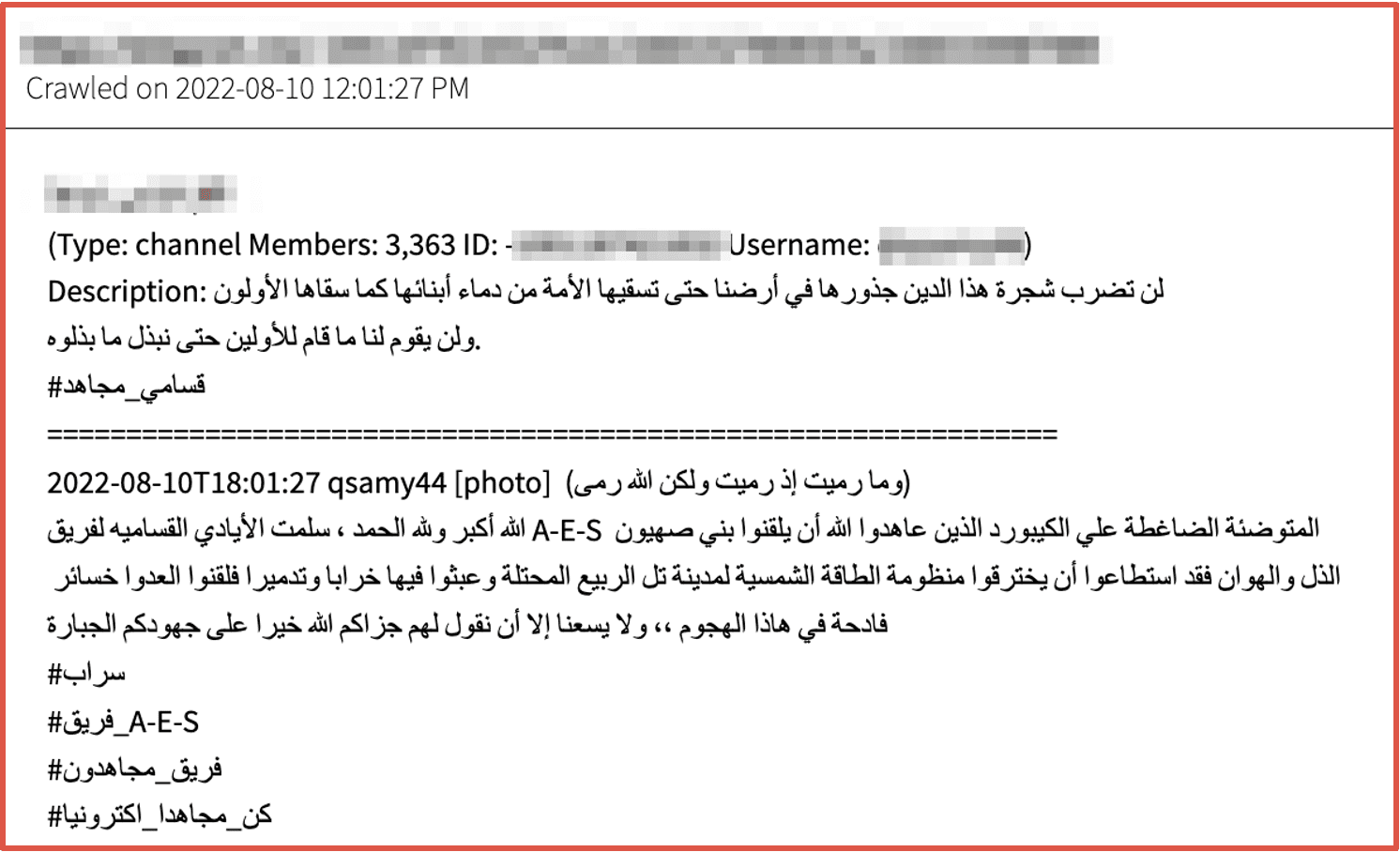
Figure 14: Source DarkOwl Vision

Figure 15: Source DarkOwl Analyst, JEA Telegram Channel
[IMAGE TRANSLATION]
Place:
Lakish, which is the occupied area of the northern Negev or “the Gaza Envelope”
Target:
Agricultural water and heating systems
The Details:
The high command has published and revealed the degree to which we have penetrated the water and agricultural system. The water temperature increased as did the amount of sodium acid, which can pollute and poison the water and can destroy all
agriculture.
DarkOwl uses machine learning to collect automatically, continuously, and anonymously, index and rank darknet, deep web, and high-risk surface net data that allows for simplicity in searching.
Our platform collects and stores data in near real-time, allowing darknet sites that frequently change location and availability, be queried in a safe and secure manner without having to access the darknet itself.
To learn more about darknet use cases and how to apply them to your business, contact us.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















