Darknet Marketplace Snapshot Series: Styx Market
June 21, 2023
In DarkOwl’s Darknet Marketplace Snapshot blog series, our researchers provide short-form insight into a variety of darknet marketplaces: looking for trends, exploring new marketplaces, examining admin and vendor activities, and offering a host of insights into this transient and often criminal corner of the internet. This edition features Styx market.
Don’t forget to subscribe to our blog at the bottom of this page to be notified as new blogs are published.
What is Styx Market?
Styx is a darknet marketplace selling illegal techniques for committing fraud, money laundering, and access to stolen data. Chatter on the darknet around Styx market first appeared in 2020 before the marketplace officially opened in mid-January 2023.
Figure 1: Captcha to Styx Market; Source: Styx Market
Styx market offers stolen data as well as a variety of products for conducting illegal cyber activities. Examples include 2FA/SMS bypass, Business Full Info/Tax, Installs for stealer, Anti-detect browsers, laundry services, FB/Google logs, Cashout Banks/VCC, Credit Cards (CC), Crypto-mixer, Stealer services, Look up BG/SSN/DOB, RDP (remote desktop protocol)/ VDS (virtual detected server) /VPS (virtual private server), and many more. Table of definitions can be found at the bottom of this blog, here.
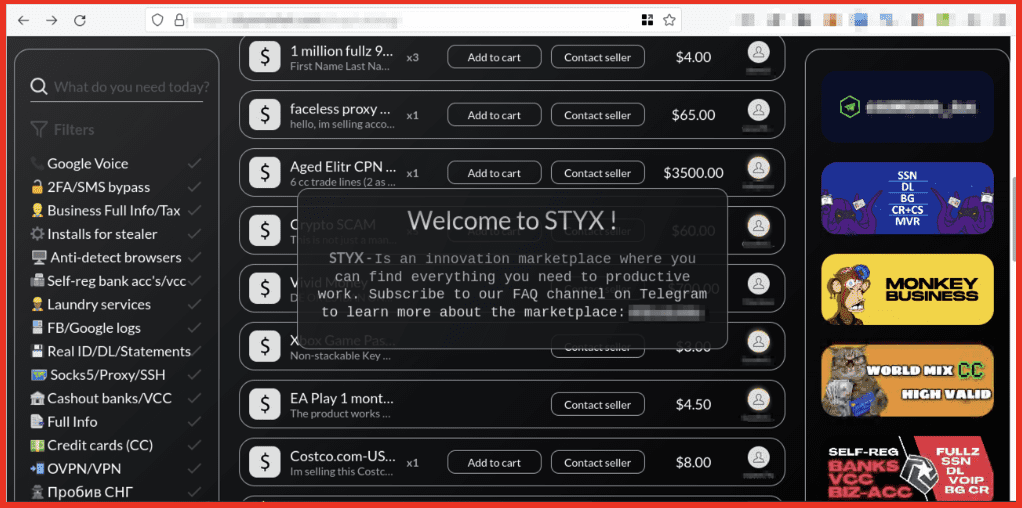
Figure 2: Homepage of Styx Market; Source: Styx Market
Infrastructure of Styx Marketplace
Styx marketplace is divided into five main sections: the main page, trusted sellers, auto ESCROW, news, and a filters section to search for specific products on the left side.
The main page of the marketplace has posts by users advertising what they sell on the market. The users have usernames that are not assigned and can be personalized. The majority of the site is in English and therefore easy to navigate for English-speakers. However, many listings and names of vendors are in Russian. This includes vendors on the Trusted Sellers page. Vendors on a trusted sellers page have typically been vetted by the administration running the site, and therefore are more “trustworthy”.
DarkOwl analysts assess many sophisticated darknet actors are Russia-based. Therefore, the fact that some vendors and their listings are Russia-affiliated adds to the legitimacy of the marketplace. There are noticeable spelling errors throughout the site in some of the listings posted by vendors. In some cases, a listing will include both a Russian and English translation. Some of the filters that can be used to search for specific products or goods offer a Russian translation right next to them.
Many kinds of stolen or leaked data for sale are offered in listings. Listings can be found on the main page, under News, and certain kinds of data can be searched for with the filter bar. Looking at individual listings, the personal data available sold is noticeably mostly from the West. The kinds of data for sale are typically PII (personal identifiable information) and credentials – information that can be used for fraud and scams. For example, a hacked database of U.S. payday loans is available for $90. There are also national Spanish identification cards available. Many foreign governments issue national identification cards to their citizens which are used while voting, traveling, applying for government benefits, and are used by law enforcement for identification purposes. Other personally identifiable information from the EU such as credentials are offered in multiple listings. However, multiple APAC (Asia Pacific) countries and Middle Eastern countries are also present on the site.
For payment, Styx market has its own ESCROW-enabled payment system. According to the terms and conditions of the marketplace’s auto-ESCROW, the maximum amount a transaction can be is $1,000,000 USD. The ESCROW system can also be used by buyers and sellers for dispute resolution. They can invite an Arbitrator by clicking on a support button. The Arbitrator takes 4% of each arbitration, and their decision is final.
The infrastructure of Styx Market relies heavily on a Telegram component.
In some cases, the “contact seller” button on the marketplace will lead directly to a Telegram channel. Vendors who rely on Telegram will typically have multiple channels tied to their vendor shop– one for administrative support and another for selling their products.

Figure 3: Trusted Sellers of Styx Market; Source: Styx Market
Focus on Financial Crime
The majority of services on the marketplace appear to be financial. Customer information for digital banking services such as Chime and PayPal are listed as well as more traditional banks including Capital One Bank, Wells Fargo, Citi Bank, and Old National Bank, among others. Access to cryptocurrency exchanges and Bitcoin platforms are prevalent across the site; sites such as Crypto[.]com, Coinbase, BitRue, Kraken, and others are listed by sellers to offer access to compromised accounts or to facilitate cashing out illicit funds. It’s unclear from research which these accounts are offered for, but historically we have seen them used for both.
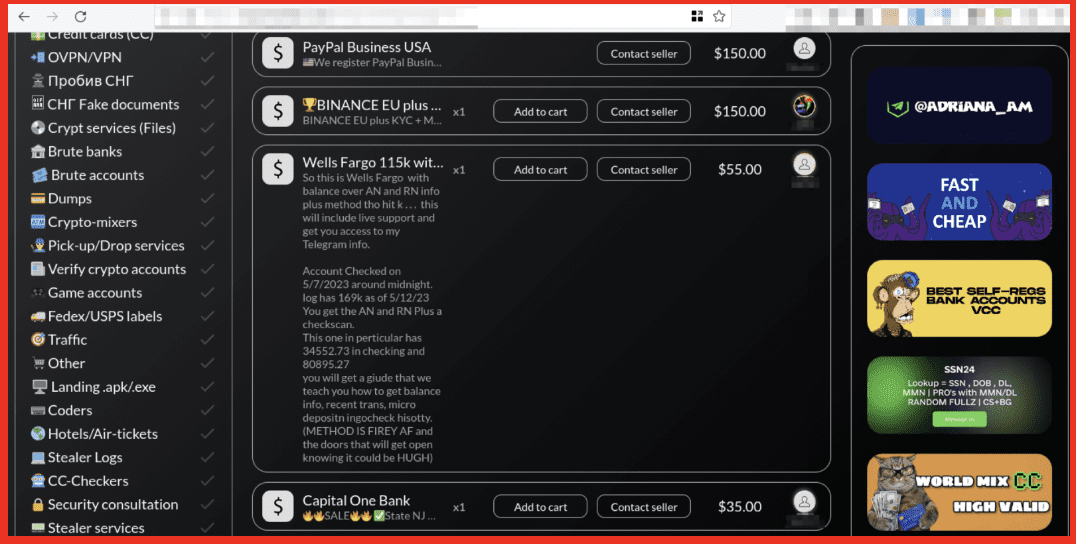
Figure 4: Wells Fargo Account; Source: Styx Market
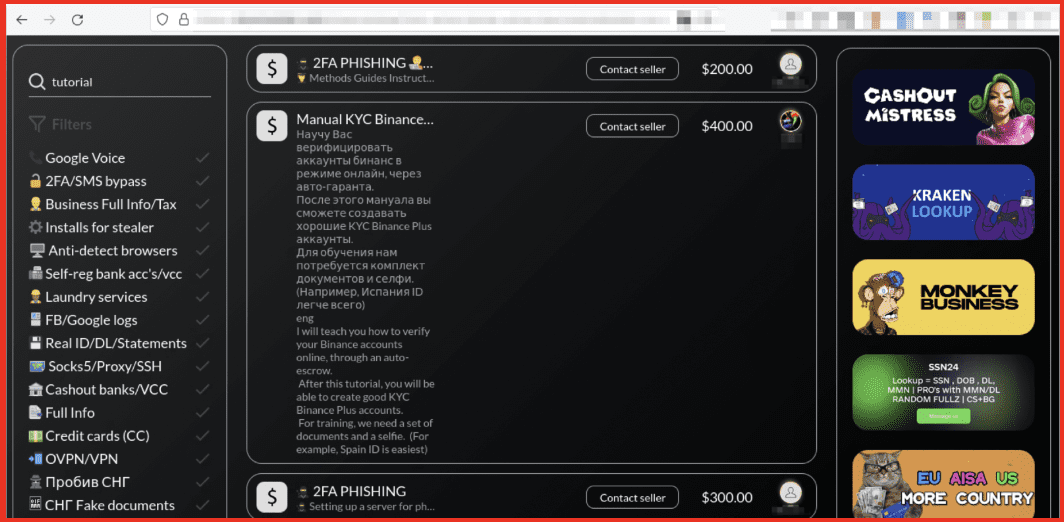
Figure 5: KYC Binance Tutorial; Source: Styx Market
The products and data available on Styx can be used to help a cybercriminal at every stage in the process of financial fraud. This could start with social engineering emails targeting CEOs, using lookup services to find and collect data on targeted individuals as reconnaissance such as a mother‘s maiden name or the name of a family pet and past addresses to help access accounts, and creating accounts to drop and launder money. Lookup services are used by cybercriminals and bad actors for reconnaissance. They use lookup service information to help them pass verification and authenticate their victim’s identity when they are committing fraud.
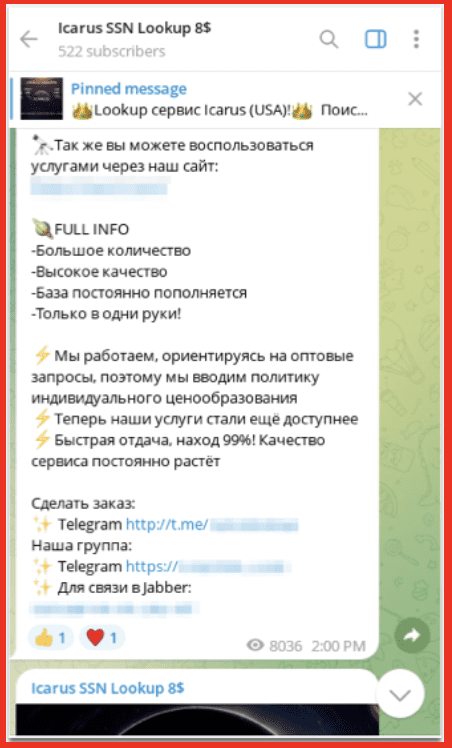
Figure 6: Telegram Channel for a Lookup Service on Styx Market; Source: Telegram
[TRANSLATED IMAGE]
☀️Search manually:
DL ($8)
SSN ($8)
DOB ($2)
EIN ($10)
☀️Search via API:
DL ($8)
SSN ($8)
⚙️Connect to the API and search 24/7
Styx market also provides cash out and money laundering services. Multiple vendors claim to provide this service, and each has their own requirements. For example, the vendor “Verta” typically charges a 50% commission. They also have requirements for the minimum amount of money needed for a transfer: $15,000 minimum per transfer to a personal account and $75,000 minimum per transfer to a business account.
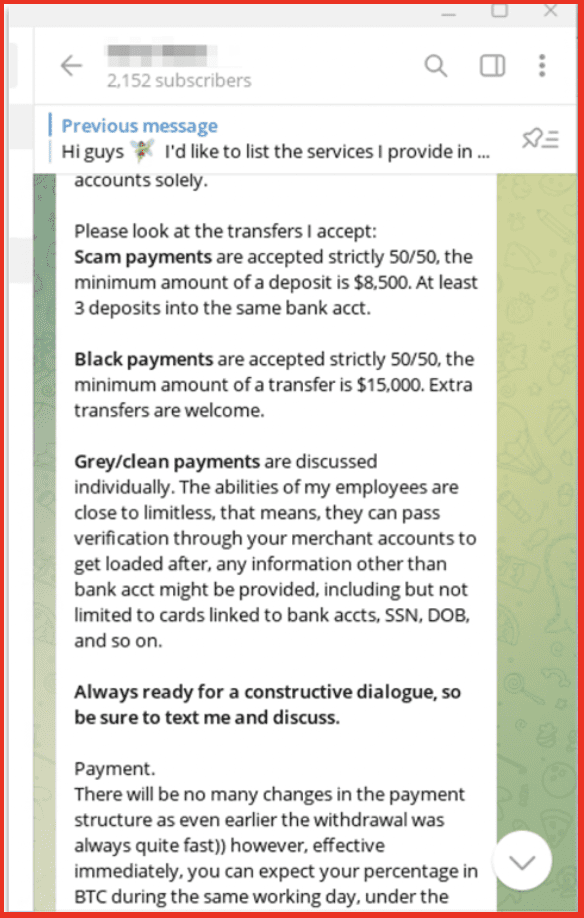
Figure 7: Verta Requirements; Source: Telegram
Facilitating financial crime appears to be a major component of the services offered on Styx marketplace. Cash out vendors require significant minimums of money for their services. Cash out services are used to turn illicit Bitcoin into fiat currency. This can be an issue if the service, such as Coinbase, requires users to use their real identity and to prove that the crypto funds are legal —neither of which a darknet actor would do.
Banks are wary of cryptocurrencies’ links to the darknet and will likely be hesitant to cash out large sums of crypto, or will raise a red flag and require additional documentation. Darknet cash out services help darknet actors cash out their illegal cryptocurrency by using their own methods to circumvent the system. Exact methods are hard to come by as vendors don’t publish what they are profiting from. However, one way includes using multiple Bitcoin wallets, running them through personalized mixers, and finding a Bitcoin buyer who gives cash in exchange. Another way is to send Bitcoin to a company that will charge a prepaid debit card.
Cash out services typically have minimums and high commissions, indicating that their customer base are actors with illicit cryptocurrency gains who have enough funds that the cash out will be helpful to them despite the high commission. These signals could indicate that Styx market has been designed and built for users who are already experienced in cybercrime, since they appear to have access to a high amount of illicit funds.
Unique Characteristics of Styx Market
DarkOwl analysts have observed a unique characteristic of Styx market is its interconnectedness with Telegram. For each listing, the user has the option to get in contact with the seller directly to purchase the item. A “Get in Contact” button will either bring the user to a page with a chat box on the marketplace itself, or the user will be taken to a Telegram channel. The Telegram channels are a mix of bots or direct access to the sellers themselves. Some Telegram channels, such as the money laundering service “Verta”, are used by the sellers to make public their terms of service and to publish positive reviews of their services. Positive customer reviews are key to gaining trust in the darknet community.
Limited descriptions of products are given on the site and users are often re-directed to a specific Telegram channel of that vendor. The Telegram channels are either a channel for direct messages to the seller or are the seller’s support Telegram channel.
A Telegram channel is used to broadcast information to a wide audience; only admins are able to post and there can be an unlimited number of subscribers. A public group is similar to a channel, but all subscribers can post in the chat. Public channels have a username, and anyone can join. Private channels are only accessible if a user is added by the owner or receives a private link to join. Analysts have observed that it is common for darknet vendors to have multiple Telegram accounts, where each is used for a different purpose. One may be just for support, one could be for posting new products, and yet another might be for direct messages to the admin.

Figure 8: Link to Deviant Shop’s Telegram from Styx Market; Source: Styx Market
In the Telegram channels, descriptions of products and availability are shared. Buyers can also get pictures of the kind of products they are looking to buy as proof.
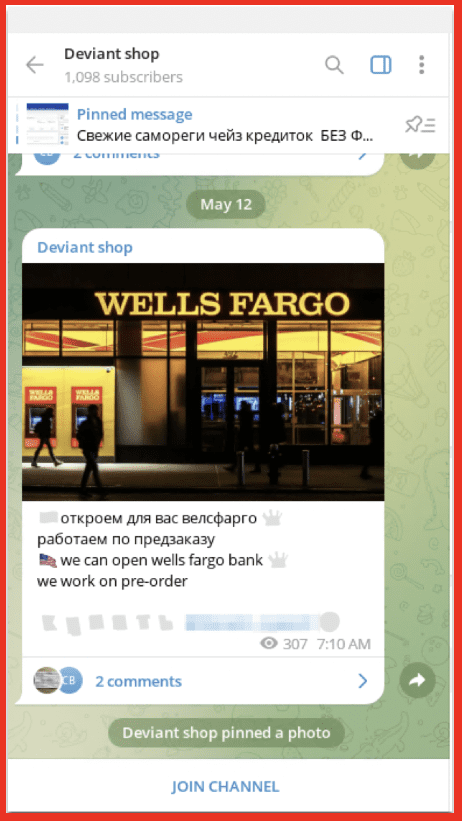
Figure 9: Deviant Shop Telegram Channel; Source: Telegram
A Look at the Vendors of Styx Market
To understand if a darknet marketplace is sophisticated, it is important to assess the legitimacy and level of sophistication of its vendors. Trustworthy darknet marketplaces are more likely to have vendors with a considerable darknet footprint. More legitimacy is afforded to a vendor if they have been selling for multiple years, across different marketplaces, and have been evaluated to be trustworthy and not a scammer. Using DarkOwl Vision, the darknet, and darknet-adjacent sites DarkOwl analysts looked at vendors from Styx market to review the vendor’s footprints across the darknet. The presence on the darknet of the vendors will likely indicate if vendors on Styx market are sophisticated hackers or skids.
The vendor shop “Valera888” sells PII, such as national identification documents, on Styx market. Using DarkOwl Vision, this same vendor’s username was found on darknet carding sites, a popular darknet Russian hacking forum, and more darknet marketplaces dating back to 2019. Although the same username on Styx has been used across darknet marketplaces in the past there is no way to tell if the same person is behind those accounts. In the past they have been associated with selling CVVs and private software. The username could be connected to the same user since they seem to follow a pattern selling personal information, but this is unconfirmed.
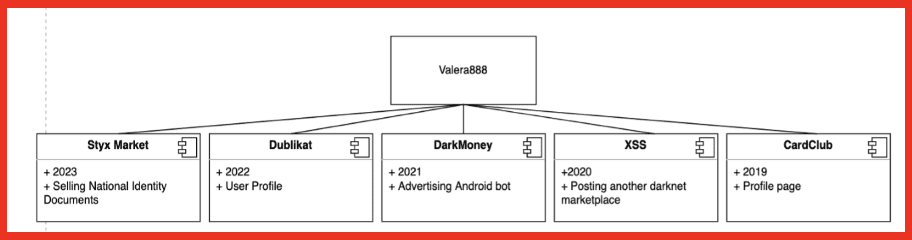
Figure 10: Mapping Valera 888 with information from DarkOwl Vision
“337 Diller” is a vendor on the trusted vendors page of Styx marketplace. This vendor offers lookup services.
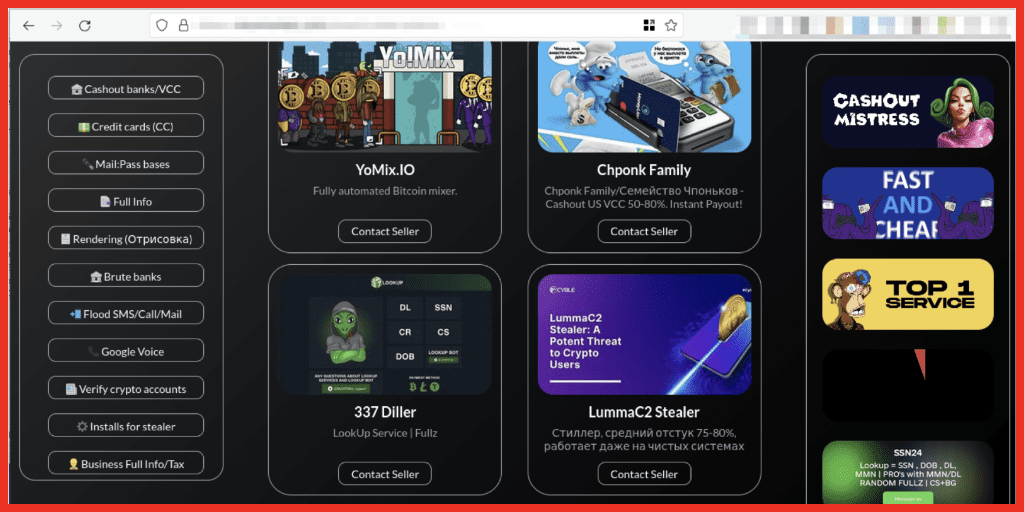
Figure 11: Vendor Profile of 337 Diller on Styx Market; Source: Styx Market
There are two Telegram channels immediately associated with this vendor on Styx marketplace. Further research reveals other channels run by a vendor with the same name selling similar products on Telegram. One of the Styx-market associated channels advertises data for sale and recruitment posts. Purchases of the data posted on this site can be made through their linked Telegram bot channel. A support channel is also linked within this channel. The other channel consists of reviews of the vendor.
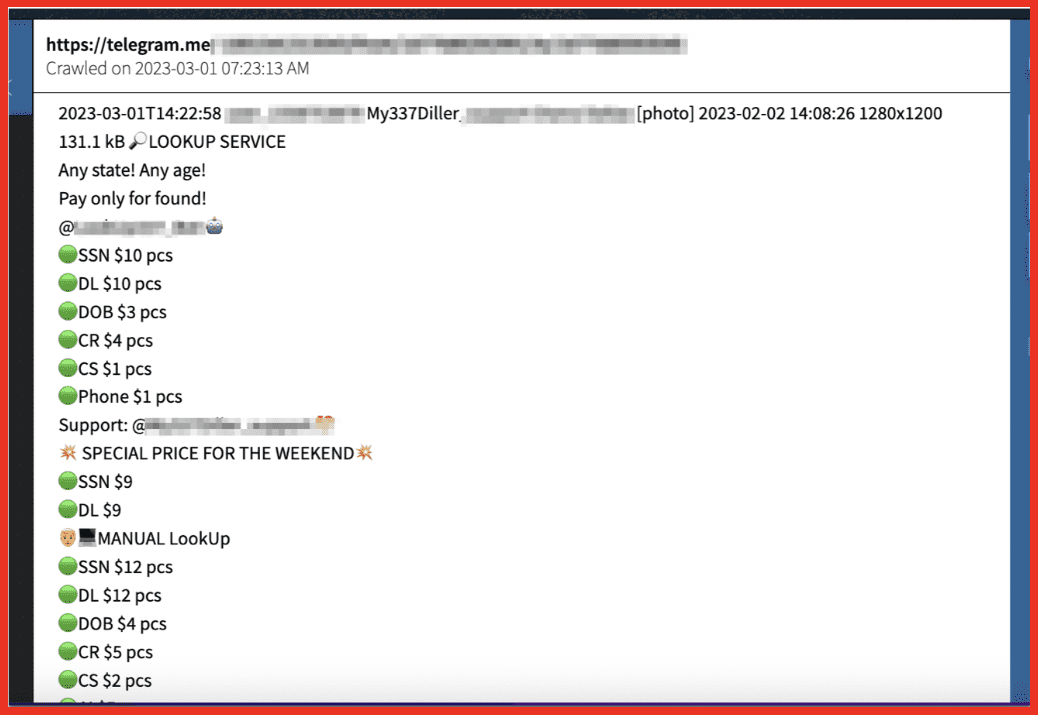
Figure 12: 337 Diller selling services on Telegram; Source: DarkOwl Vision
Research from DarkOwl Vision indicates this vendor has been offering lookup services and fullz since at least 2021 both via Telegram and on popular darknet marketplaces and forums.
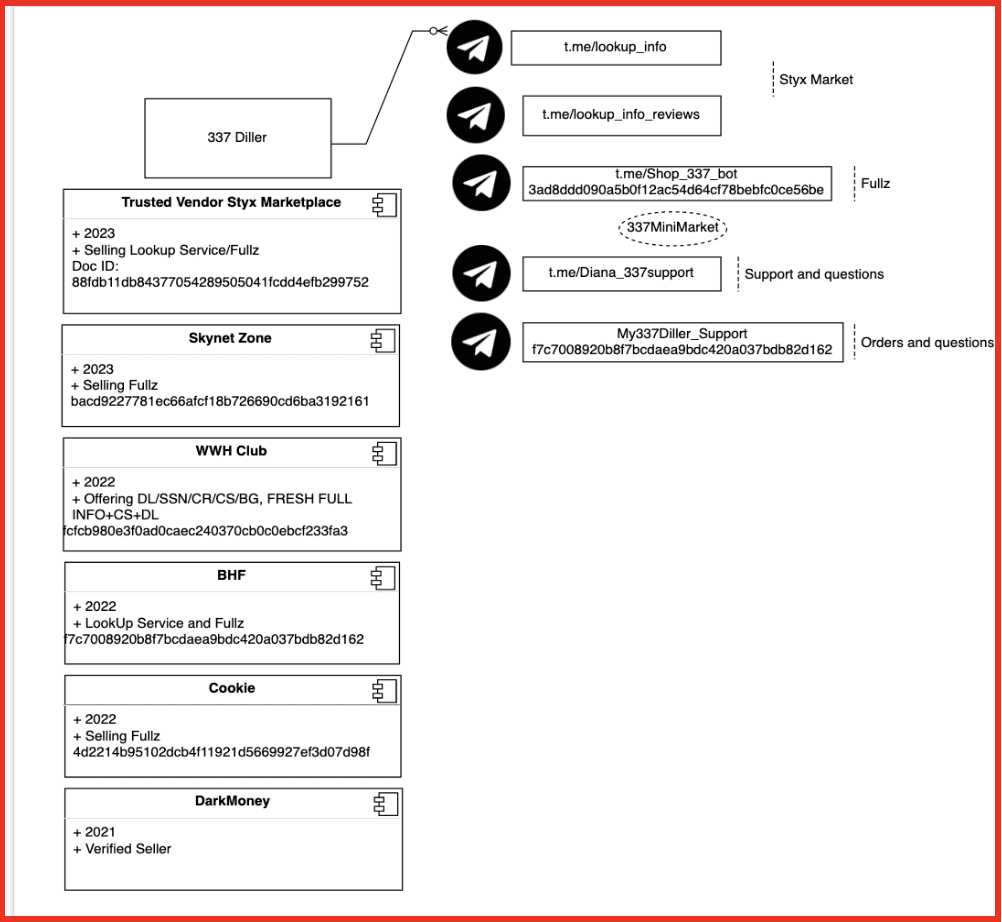
Figure 13: Mapping 337 Diller using data from DarkOwl Vision
“Podorozhnik” sells drawing services as a vendor on Styx market where a user can get in touch with them via the chat feature offered on the site. In addition to their presence on Styx, they also offer their fake documents for sale via dedicated Telegram channels. Drawing services is a term used for forged documents and fake documents. “Podorozhnik” advertised their drawing services on the darknet site DarkMoney in 2021. No Telegram channels are linked directly on Styx market, but there are multiple public channels connected to ”Podorozhnik” on Telegram. For example, they have a Telegram channel dedicated to reviews. These show communication between customers and “Podorozhnik” of successful verifications. A Telegram channel advertising “Podorozhnik” claims they had over 900 positive reviews on a popular Russian Forum.
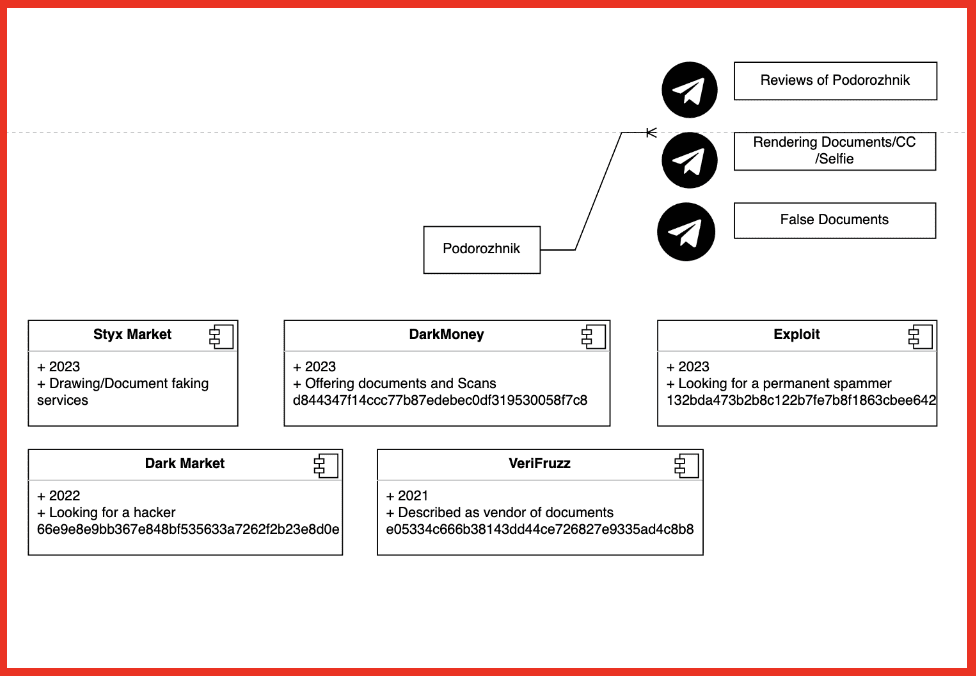
Figure 14: Mapping Prodorozhnik using data from DarkOwl Vision
As each of the three vendors researched appear to have been present on darknet forums and marketplaces for years before joining Styx, they are more likely to be sophisticated and legitimate vendors. Vendor reviews are an essential component to establishing trust on darknet marketplaces and reassuring potential buyers of the legitimacy of the vendor. Two of the three vendors have reviews readily available for potential buyers to evaluate. These include Telegram channels dedicated to reviews. These reviews point to trust in the vendor. They have also embraced using Telegram for selling products and services and as a support system for customers. Telegram continues to grow as a main avenue for buying and selling darknet-related goods. Some of the Telegram channels associated with Styx marketplace vendors were created as early as 2021, while others have been created within the last year.
Final Thoughts
The products sold on Styx marketplace are hacker and financial-crime oriented. The market caters to sophisticated cybercriminals. Vendors offer access to multiple online banking and e-commerce sites. Money laundering services are strict and only for those who can pay meet the dollar minimum. While money laundering is risky, therefore requiring a minimum for payments, vendors have been successful enough to continue offering the service. And despite the high price there appear to be customers who are willing to pay. Financial institutions and the banking sector will need to continue to be wary given the account identity authentication techniques available for sale on Styx market. These include NFC Bins (NFC is what allows for contactless payment on cards) and vendors offering to set up funnel accounts which can be used as a drop service to “drop” stolen financials. Much like cash out vendors, drop services are used for money laundering illegally earned funds. For now, Styx market will provide a valuable outlet for cybercrime on the darknet as cybercriminals go after the online components of banking and come up with new methods for money laundering.
Subscribe to email to receive the latest research directly into your inbox every Thursday and don’t miss our next Darknet Marketplace Snapshot.
Table of Definitions
| Word | Definition |
| 2FA/SMS Bypass | 2FA is two-factor authentication and is used to help secure accounts. SMS text messages are a common way to use 2FA many times by using one-time codes. Cybercriminals can achieve SMS bypass by SIM swapping or intercepting networks. |
| Business Full Info/Tax | Business full into consists of detailed PII that could be utilized by a cybercriminals to commit fraud or identity theft. Coupled with tax information, the bad actor would possibly be able to commit many forms of financial fraud such as fraudulent wire transfers. |
| Installs for stealers | Some stealers are sold as pay-per-install services. A user can pay to download the malware and install it on compromised systems of their choice |
| Anti-detect browsers | Anti-detect browsers can be used for privacy and anonymity online as they avoid detection from online web-tracking technologies. |
| Laundry Services | Laundry services are money laundering services to “clean” cash received from illegal activities and get the cash into the legal banking system. |
| FB/Google Logs | Logs are records of activity that take place on computer systems. Using a record of activity such as Facebook posts and Google searches, a bad actor could use this information for phishing texts, emails, and sophisticated social engineering campaigns. |
| Cashout Banks/ VCC | VCC stands for virtual credit cards. Cashing out bank accounts and cashing out virtual credit cards can be used to steal funds or for money laundering. |
| Crypto-mixer | Crypto-mixers are used for obfuscation. They mix the cryptocurrencies of many users together to obfuscate where money comes from and who it belongs to. The money is later withdrawn to new addresses belonging to each user. |
| Stealer Services | Stealer services are the stealer-as-a-service market. Actors offer their stealer malware for sale for a customer to essentially rent to then compromise and access a device on their own. This way a customer with very little technical know-how can have access to sophisticated stealer malware. These are aimed at less-sophisticated users. |
| BG/SSN/DOB | Background check, Social Security number, and Date of Birth. This information can be used for identity theft, fraud, and social engineering. |
| RDP | RDP, remote desktop protocol, is a Windows interface that allows users to connect with another computer or server over the internet. Bad actors will sometimes use open RDP ports to install their ransomware onto the victim’s system. |
| VDS | VDS stands for Virtual Dedicated Server and is essentially leasing a dedicated server that the user controls completely because it is not shared with other customers. A VDS is the conglomerate of a server, its hardware, and the operating system run by a remote access component allowing the user to access their server over the internet. |
| VPS | VPS is a Virtual Private Server, and they are used for web hosting. Nation-state actors are known to use these in attacks as a proxy or bridge between the real server and the target as well as other methods like hosting RDPs, VPN, and proxy gateways to hide the location of the command and control servers. They are used to hide locations so as hide from security systems on targeted devices and to obfuscate the true IP addresses and locations. |
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















