Insights From the Darknet: API Security
January 12, 2023
API Security professionals can benefit from darknet data in forming a more comprehensive understanding of malicious threat actor Tactics, Techniques, and Procedures (TTPs) in order to inact effective detailed security recommendations, remediations, and product solutions.
API Security related topics, such as “API hacking”, “stolen API tokens”, and “API MITM attacks” are regularly discussed in detail in darknet forums. Similarly, API tokens are frequently sold and traded in underground digital marketplaces, as is API exploitation code is shared amongst threat actors.
Considering that API security incidents affected 95% of organizations in the last year (Source), it is more important than ever that the information security community remain aware of shifts in threat actor discussions regarding APIs and the various TTPs that threat actors use to exploit them.
Examples of API Security Incidents
Recent security incidents impacting APIs highlight the need for increased awareness and protection of digital supply chain assets. For example, in 2018, a vulnerable USPS Informed Visibility API endpoint leaked over 60 Million US residents information. USPS performed and published an audit that detailed some of the issues that resulted from the incident, although many of the key data is redacted.
More recently, in April 2022, Github admitted that attackers targeted private repositories using the Github API using stolen OAuth tokens. This was likely via a Microsoft OAuth flaw that occurred in December 2021.
Toyota warns of possible data theft after access key left exposed on GitHub
Recently, Toyota was notified of a breach that happened as the result of an API access key for T-Connect, the official Toyota connectivity app, being left publicly available on GitHub. Their T-Connect connectivity app powered utilities like wireless access to vehicles.
Toyota has since announced that over 2,900 records were exposed since then, giving access to customer names, customer information, and so forth. This is one example of what the threat landscape looks like and what the implication can be of API credentials getting into the wrong hands.
FTX users lose millions to 3Commas API exploit
Similarly, recently, FTX and 3Commas revealed that an API exploit was used to make illegitimate FTX transactions. This was done using API keys that were obtained from users via phishing attacks that enabled them access to lateral systems. Eventually, the platform 3Commas came forth publicly to admit that the API keys were obtained from outside of their platform, but the implication still posed a risk to their users. Risk of user account exploitation included threat actors being able to make offsite, unauthorized financial transactions.
An investigation revealed that DMG trades were conducted using new 3Commas accounts and that “the API keys were not obtained from the 3Commas platform but from outside of it.” This suggests that cyber criminals likely gained keys from phishing or browser information stealers, which are frequently discussed and advertised on the darknet.
Informed Delivery Leaks 60 Million Users’ PII
Poor access controls of a United States Postal Service (USPS) API endpoint resulted in a wealth of US persons’ private information available to criminals
In 2018, a vulnerable USPS Informed Visibility API endpoint leaked over 60 Million US residents information. USPS performed and published an audit that detailed some of the issues that resulted from the incident, although much of the sensitive data is redacted.
USPS Informed Visibility API Code prior to November 20, 2018
Darknet Threat Actors Readily Discuss API Security
On the darknet, stolen API secrets, keys, and session tokens are shared openly and in closed communities. Authenticated darknet discussion forums on Tor, transient paste sites, and Telegram especially popular with API attack enthusiasts.
Examples from DarkOwl Vision: Stolen API Keys & Security Tokens
Pinnacle, Telnyx, and other API tokens are frequently offered for purchase on darknet forums such as DARKMONEY and similar ‘hacking’ Telegram channels.
Telegram groups offer ‘key checkers’ – where the API key is tested ahead of time on behalf of the threat actor. Another example shows Twitter tokens being offered for sale on ‘cracking’ Telegram group.
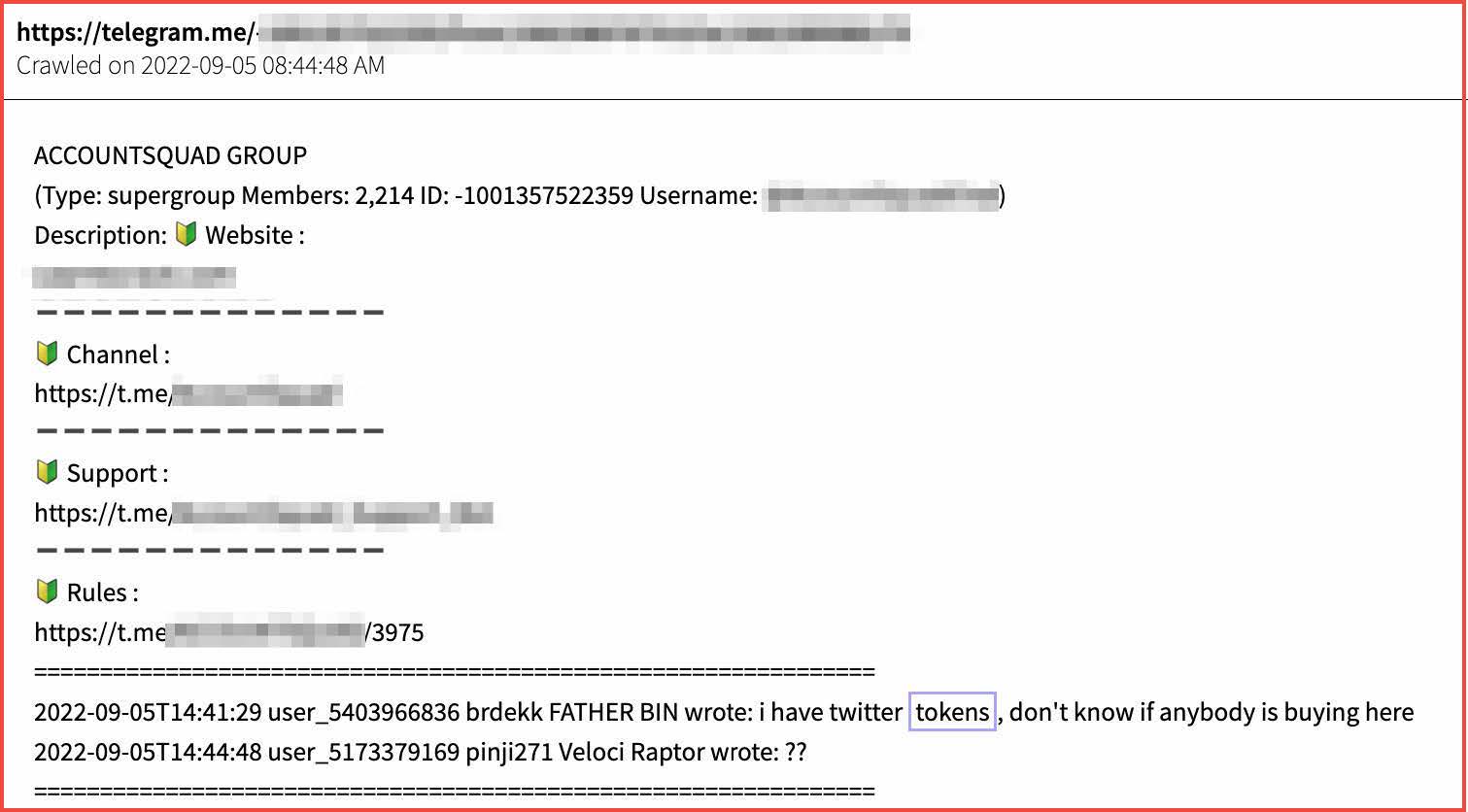
Example of Twitter tokens for sale on Telegram (Source: DarkOwl Vision)
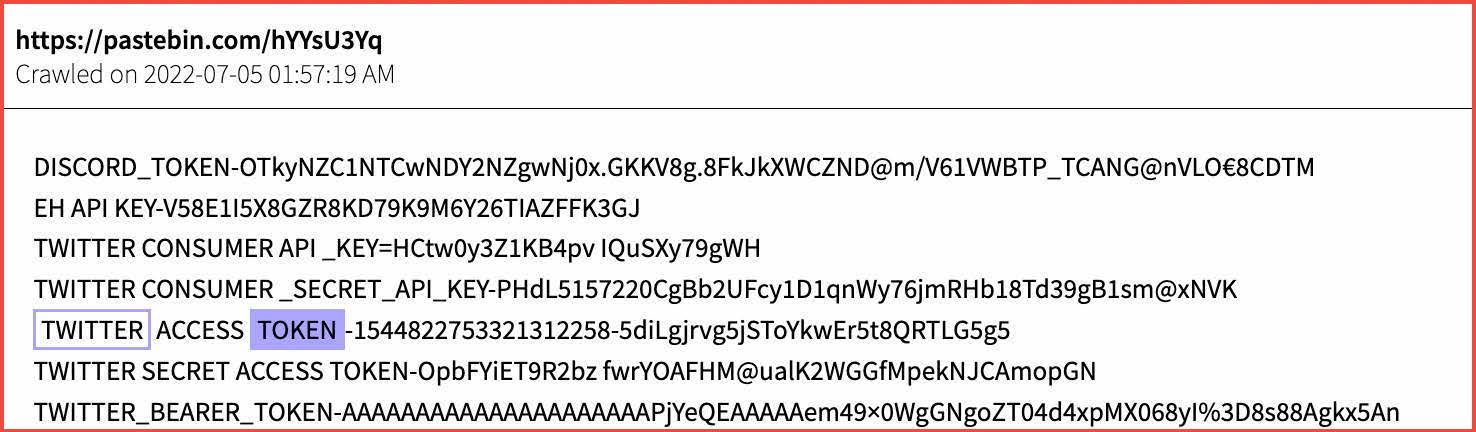
Twitter and Discord tokens are shared on transient paste sites, like pastebin.com (Source: DarkOwl Vision)
In another example, DarkOwl analysts have observed a TikTok API token generator for username scanning. Below is a translation of the listing:
“This tool will generate and validate TikTok API tokens, also known as session IDs. This is useful if you are checking usernames through the TikTok API and you have run out of IDs with no speed limit! I advise using 30-100 streams and would definitely turn on a Vpn, because your IP address can be limited very quickly, be careful!”
DarkOwl has also increasingly observed API penetration testing utilities – like GoBuster or Wfuzz – discussed in detail by non-english speaking darknet users. Similar technical discussions are now appearing on malware developer centric surface web sites, such as CSDN.
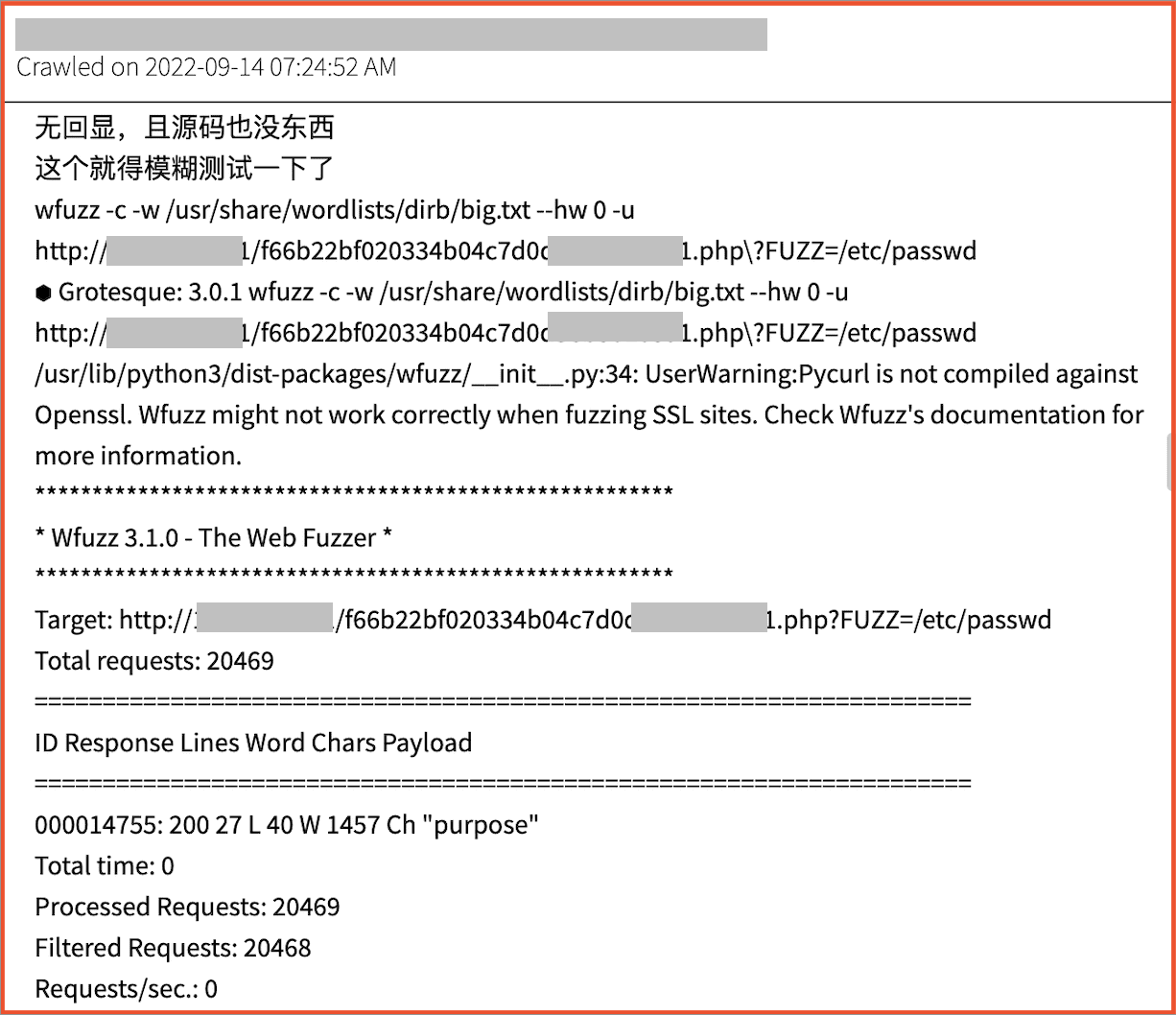
Threat actor activity/discussions surrounding API penetration tools (Source: DarkOwl Vision)
Why API Security is so Important
APIs tend to be an underserved element with respect to cybersecurity postures of most enterprises. However, as organizations continue to make efforts to digitally transform their application ecosystems, enterprise services increasingly rely on APIs. As a result, APIs are emerging as the backbone of modern communication and application ecosystems. As more organizations move towards the cloud and similar API technologies, having visibility into any and all credentials that could be exploited is exceedingly crucial.
This shift towards dependency on APIs in the commercial landscape echoes what DarkOwl analysts are seeing in the darknet. Discussions around API exploits, API keys, stealing API keys, and selling them is a relatively new phenomenon in the darknet over the last couple of years, that we expect to continue to grow.
Interested in learning more about how darknet data informs API security? Check out our webinar on this topic that we hosted with our partner Corsha for more real-world examples and predictions regarding the future of API security.
Watch the webinar
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















