Interview with DarkOwl’s Director of Product on Ransomware API
June 01, 2022

Sarah Prime, Director of Product Technology, continues to innovate new products that illuminate critical areas of the darknet. We spoke with Sarah to get the latest on DarkOwl’s new product, Ransomware API.
So Sarah, tell us about this product
Our new product is called Ransomware API, which is an endpoint designed to allow organizations to monitor and have insight into ransomware sites on the darknet.
What made you want to develop this endpoint?
We developed it as a direct response to what we were hearing from our customers. We know that our insight and historical perspective into the darknet is unique, and we wanted to make it easy for people to find this critical information about their vendors or clients.
With this API product, content on these sites – including organization mentions – can now serve as an important risk indicator for a variety of use cases.
Tell me more about these ransomware group sites
The sites available via our new Ransomware API are darknet sites where these groups will publish public announcements, as well as links to downloadable content – often in the form of stolen data. We retain all of the ransomware site content in our archive, as part of our darknet data collection, even after it’s taken down.
As we all know, ransomware as a criminal activity has really skyrocketed in the past few years. Ransomware groups have become significantly more sophisticated and organized from a business perspective, and have created their own underground economy. They commonly use advanced economic strategies such as affiliate networks, third party mediation consultants, and referral programs.
Part of the way groups bolster their clout and status as a reliable enterprise is by establishing a brand, which means they will launch a website just like a corporation might on the regular internet. They even gain income via ad revenue like any other website. Except, this is taking place in a criminal setting.
What would a company being mentioned on one of these sites mean?
It depends, but the vast majority of the time it would mean that the company has been successfully compromised as the result of a ransomware attack. There are certain exceptions, such as when a company has been targeted and the ransomware group posted a description of that company and it included a partner organization, for example. However, in that scenario, it would be important for that company to know that its partner had suffered a ransomware attack so that it could deploy appropriate cautionary and defensive measures within its own network.
After it has been targeted and compromised as the result of a ransomware attack, the context in which a company is mentioned can vary from case to case. In some circumstances, a RaaS group may publish a post stating that they have compromised company X, and If that company doesn’t pay up, they will publish all of their data on their website for free to whomever wants to download it. In other cases, they will sell off portions of a company’s data for profit, regardless of whether they had paid their ransom or not.
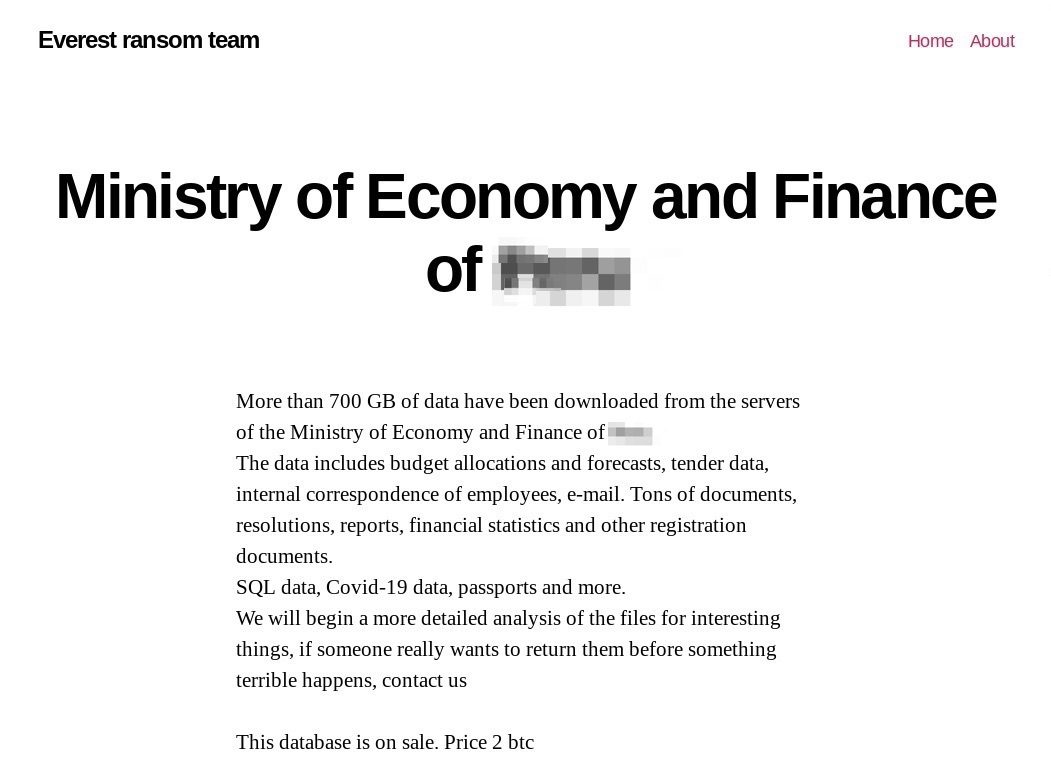
Image A: Screen capture of a ransomware group posting on the darknet that describes the data obtained from one of their victims
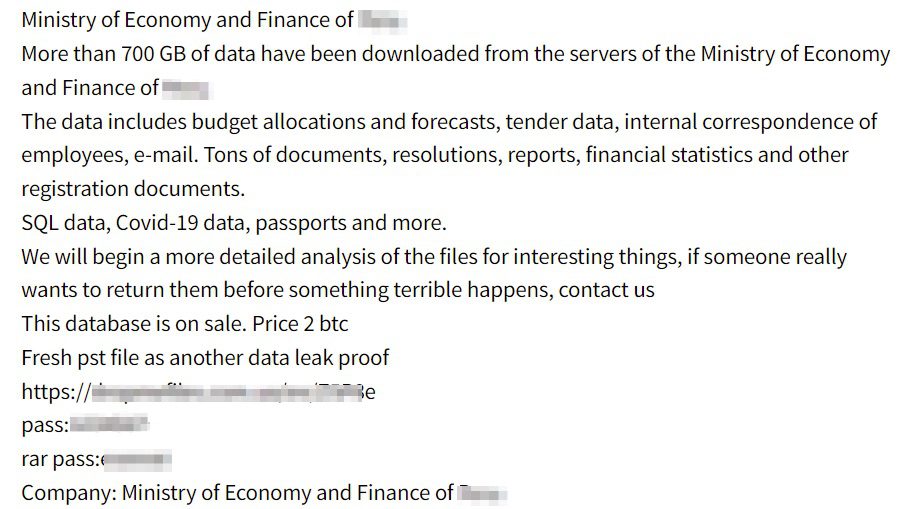
Image B: Screen capture of the same ransomware posting as Image A, as indexed within DarkOwl’s database and seen in Vision UI
If the attack has already happened, why does it matter?
It’s critical to know whether your customers or companies in your supply chain have been subjected to a ransomware attack. If one of your third-party vendors is compromised by a ransomware attack, you don’t want to wait until they’re able to officially inform you to find out – especially considering that their networks may still be inaccessible to them. They may not even be able to effectively inform their partners/clients right away. Similarly, a services provider can monitor their customer base for these attacks, both to assist in their reaction and also to be aware of the risk associated with the attack. Insurance underwriters and reinsurance companies have a need to monitor on an ongoing basis.
In cases where a company has not backed up their data, the records publicized by the criminals can be a means of understanding exactly what data was lost, what is being sold, and what missing records the group may be holding on to.
Who are the most prolific ransomware actors?
The LockBit 2.0 (LB2) ransomware group has the highest number of victims since the start of 2022. In our analysis of ransomware activity since the invasion of Ukraine in early May, we determined LB2 had successfully encrypted over 280 victims, averaging 4.5 victims per day.
CL0P and CONTI were the two next groups with the highest number of victims, but according to open source reporting, CONTI may be in the process of shutting down their operations due to the impact of Russian sanctions, or simply rebranding to lessen public pressure on the group. We’ve also witnessed AlphaV and HiveLeak demonstrate exponential growth in victim announcements in recent weeks.
How does DarkOwl track these groups?
What’s interesting is that ransomware is a uniquely darknet-based phenomenon. By that I mean, its origins are on the darknet, its perpetrators primarily reside on the darknet, and its economy is hosted on the darknet. We are also increasingly seeing RaaS groups opening splinter or parallel operations on darknet-adjacent networks, such as on chat platforms like Telegram.
We’ve been in the darknet space for a long enough time that our analysts have naturally been keeping tabs and in some cases gotten quite close to these networks, so that we’ve been able to maintain access. We’re also deeply familiar with the way in which these groups operate and are able to predict when new groups are gaining prominence, when popular groups are rebranding, when they might be launching new sites, and so forth.
Is there a particular use case that you think Ransomware API is a good fit for?
Any company that has a substantial vendor portfolio and is concerned about supply chain risk. It could also provide an important datapoint for cyber insurance underwriters who need to assess a company’s historical risk. In fact, because ransomware groups will often remove or delete their posts after a certain amount of time, this tool is one of the few – if not the only – that can provide an accurate picture of whether or not a company has been subject of a ransomware attack.
How is this different from our other API products?
This product provides information regarding a very specific use case that customers can use to build whatever they want, including monitoring functionality, auditing services, underwriting assessments, compliance tools, etc. While this is also possible with our other APIs, the targeted scope of this data makes it one of our more streamlined and scalable products.
What else makes this product special?
This product is built on dynamic data sources; as ransomware groups evolve, so does our data coverage. We can also track specialty groups upon request, so it will be interesting to see what kind of growth there is in coming months as we continually add new ransomware sites to our collection.
Anything to look forward to from DarkOwl team? What is the product team excited about?
Yes! We always have a lot going on, but the biggest thing on the horizon from the product team is the development of a new DARKINT scoring model. It’s showing a lot of early promise in identifying heightened risk, making it an even more comprehensive measure of an organization’s darknet exposure. This is critical for risk assessment, risk monitoring and rating efforts.
Where can people learn more?
To stay aware of ransomware group activity, I recommend keeping up with the research that our analysts publish regularly. Their latest piece, which is fascinating coverage RaaS group activity since the invasion of Ukraine, can be found here.
To learn more about Ransomware API, please reach out to schedule a demo with our sales and product teams.
View Ransomware API Product Page and Ransomware API Datasheet.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















